Streamline CI/CD with Just-in-Time Access
0 likes42 views
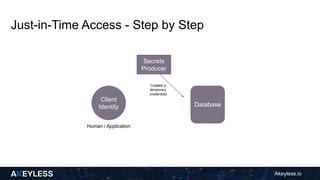
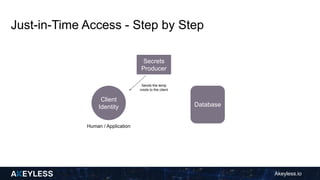
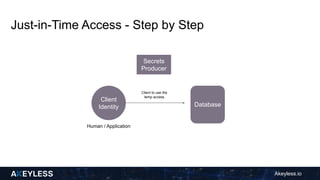
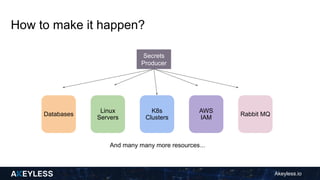
Akeyless.io introduces a just-in-time access model to streamline CI/CD processes by automatically creating temporary credentials for various resources on demand. This model enhances security by ensuring no permanent access is given and credentials are deleted after use, reducing manual intervention. The document outlines the step-by-step process for implementing this access model and its benefits, including improved operational hygiene and efficiency.
1 of 16
Download to read offline










Ad
Recommended
Stopping the Hassle of SSH keys by using SSH certificates - Community Summit ...
Stopping the Hassle of SSH keys by using SSH certificates - Community Summit ...Akeyless
╠²
This document discusses using SSH certificates as an alternative to SSH keys for secrets management and remote access. It notes that SSH keys require ongoing management as team members join and leave. SSH certificates were introduced over 10 years ago and provide auditability, expiration to remove standing permissions, and avoid issues with lost or stolen keys. However, SSH certificates require some PKI knowledge and infrastructure setup. The document provides steps to set up a basic certificate authority and configure a server to use SSH certificates for login.The Rise of Secrets Management
The Rise of Secrets ManagementAkeyless
╠²
Akeyless Security Ltd. outlines its zero-knowledge secrets management SaaS platform, emphasizing the importance of secure data encryption, identity validation, and privileged access management. The document highlights trends increasing the use of secrets in various industries and presents strategies for managing secrets in a hybrid cloud environment. It concludes with an invitation for further inquiries regarding their solutions.Secure Secret Management on a Budget: Reasoning about Scalable SM with Vault ...
Secure Secret Management on a Budget: Reasoning about Scalable SM with Vault ...Mary Racter
╠²
This document presents a talk by Mary Racter on secure secret management for digital solutions at Praekelt.org, emphasizing the importance of managing secrets in cybersecurity, particularly within open-source environments. It discusses risks associated with current secret management practices, particularly using environment variables and Git for storing sensitive credentials, and introduces HashiCorp's Vault as a solution for securely creating, storing, and distributing secrets. The talk also outlines lifecycle management of secrets, highlighting the use of dynamic secrets and lease management to enhance security at scale.Secrets as Code
Secrets as CodeJohann Gyger
╠²
The document discusses the challenges of secrets management in software development, emphasizing the disconnect between developers, operations, and security teams. It suggests automating secrets management through tools like HashiCorp Vault and provides strategies for protecting secret information, such as using version control and encryption. The conclusion encourages the use of Vault for automated secrets management while acknowledging the complexities involved.Automation Patterns for Scalable Secret Management
Automation Patterns for Scalable Secret ManagementMary Racter
╠²
The document discusses the importance and challenges of secret management in computing, particularly in the context of continuous deployment and scaling. It highlights the need for secure handling of secrets, the use of secret management services, and best practices for automation to reduce manual processes. Furthermore, it emphasizes the significance of integrating secret management into deployment workflows and maintaining security through principles like least privilege and dynamic secrets.The Key to Strong Cloud Security
The Key to Strong Cloud SecurityAkeyless
╠²
The document discusses the challenges and solutions related to secrets management in cloud security, emphasizing the importance of privileged access, identity validation, and data encryption in the hybrid and multi-cloud environments. It highlights the role of Akeyless's secrets management platform, which aids enterprises in managing machine identities, secrets, keys, and certificates securely and effectively. Additionally, it addresses the risks associated with unprotected secrets and outlines best practices for ensuring secure access control and compliance.Let's get started with passwordless authentication using windows hello in you...
Let's get started with passwordless authentication using windows hello in you...Chris Ryu
╠²
The document discusses advancements in passwordless authentication, emphasizing the use of FIDO protocols and strong cryptographic methods to enhance security and user experience. It highlights the limitations of traditional passwords, such as vulnerability to phishing and the difficulty in mobile usability. Additionally, it outlines the features of a digital certificate solution called 'anypin', which supports secure device verification and protects data integrity in client-server communications.Kubernetes Secrets - The Good, The Bad, and The Ugly - Akeyless
Kubernetes Secrets - The Good, The Bad, and The Ugly - AkeylessAkeyless
╠²
The document discusses Kubernetes (k8s) secrets, outlining their functionality, security concerns, and potential mitigations. It highlights issues with secrets being stored in non-encrypted forms and easily accessible within pods, emphasizing the importance of implementing just-in-time secrets. The presentation advocates for adopting unified secrets management solutions for enhanced security across cloud and DevOps environments.Introduction to vault
Introduction to vaultHenrik H├Ėegh
╠²
Vault is a tool for securely managing secrets like API keys, passwords, and certificates. It allows users to securely store and tightly control access to tokens, passwords, certificates, API keys and other secrets. Vault handles the lifecycle of secrets, including creation, rotation, revocation and more. It also integrates with Kubernetes to securely provide secrets to pods. Vault uses a client-server architecture and supports authentication through various methods like Kubernetes service accounts.Kubernetes Secrets Management - Securing Your Production Environment
Kubernetes Secrets Management - Securing Your Production EnvironmentAkeyless
╠²
The document discusses the importance of securing Kubernetes secrets in production environments using Akeyless's secrets management platform. It highlights key challenges like the insecure storage of secrets, the need for pod and namespace segregation, and cluster access management. The solution proposed includes a robust secrets management platform that enables controlled access and enhances security through decryption at the application level and trusted identities.Hashitalks 2021 - How the Dynamic Duo of Vault and Puppet Tame SSL Certificates
Hashitalks 2021 - How the Dynamic Duo of Vault and Puppet Tame SSL CertificatesNick Maludy
╠²
This document discusses how HashiCorp Vault and Puppet can be used together to dynamically manage SSL/TLS certificates across platforms. Vault's PKI secrets engine is used to sign certificates while Puppet distributes the certificates and keys to servers and configures services to use the certificates. On Linux, Puppet writes certificates to the filesystem and reloads services. On Windows, a Puppet function is used to embed certificates in the catalog so their thumbprints can be retrieved and used to configure services in the certificate store. This dynamic duo of Vault and Puppet enables centralized signing of certificates, auto-renewal, cross-platform distribution, and integration with services.IBM Secret Key management protoco
IBM Secret Key management protocogori4
╠²
1. The document describes an IBM secret key management protocol that provides secure communication between servers and terminals.
2. It uses a tamper-resistant cryptographic facility to securely store the most important keys used to generate encryption keys.
3. The protocol establishes a master key that is used to generate session keys for encryption in a similar manner to the scheme described in a 1978 paper.Global Azure Bootcamp 2017 - Azure Key Vault
Global Azure Bootcamp 2017 - Azure Key VaultAlberto Diaz Martin
╠²
Alberto Diaz Martin is the Chief Technology and Innovation Officer at Encamina, with over 14 years in the IT industry focusing on Microsoft technologies. The document discusses Azure Key Vault, emphasizing its features for managing and securing cryptographic keys and secrets, encryption methods, and cost. It outlines workflows for using Azure Key Vault and its role in protecting sensitive data and credentials in various applications.Recipe for good secrets management
Recipe for good secrets managementKevin Gilpin
╠²
The document provides a recipe for good secrets management. It outlines requirements like separation of duties, least privilege, leak resistance, and auditing. It recommends having separate security environments for staging and production, designing for "robot" actors with limited access, rotating credentials, and automatically recording system activity. Configuration management and orchestration should provision robots and bootstrap machine identity by assigning credentials from an identity server. Secrets should be fetched from a secrets manager and stored separately from application data to satisfy compliance standards.Hardening Kubernetes Cluster
Hardening Kubernetes ClusterKnoldus Inc.
╠²
The document presents a comprehensive overview of hardening Kubernetes clusters, highlighting crucial aspects such as securing the cluster, authentication, authorization, image security, and secrets management. It emphasizes best practices like limiting API and dashboard exposure, using role-based access control, and implementing secure image storage and container management. The content is aimed at enhancing the security posture of Kubernetes environments within the context of software development lifecycle (SDLC).Securing sensitive data with Azure Key Vault
Securing sensitive data with Azure Key VaultTom Kerkhove
╠²
The document discusses the Azure Key Vault as a solution for securing sensitive data by storing it in hardware security modules (HSM) and providing customers with control over the key lifecycle and access management. It highlights the importance of moving away from storing sensitive data in plaintext and emphasizes the role of Audit Logs and Access Control based on Azure Active Directory. Additionally, it outlines the features and pricing of Azure Key Vault, including secrets and keys management, disaster recovery considerations, and future updates for broader availability and enhanced tooling.Azure key vault
Azure key vaultRahul Nath
╠²
Azure Key Vault is a cloud service that securely stores keys, secrets, and certificates. It allows storing cryptographic keys and secrets that applications and services use while keeping them safe from unauthorized access. Key Vault uses hardware security modules to encrypt keys and secrets. Typical applications would store secrets like connection strings in Key Vault rather than configuration files for improved security and management. Key Vault integrates with Azure Active Directory for authentication so applications can access secrets securely.ITProceed 2015 - Securing Sensitive Data with Azure Key Vault
ITProceed 2015 - Securing Sensitive Data with Azure Key VaultTom Kerkhove
╠²
This document discusses securing sensitive data using Azure Key Vault, highlighting its role in managing encryption keys, secrets, and access control. It outlines the benefits of Azure Key Vault, including secure storage, control over key lifecycle, and monitoring capabilities. The document also addresses potential security flaws and emphasizes the importance of encryption in protecting sensitive data.Azure Low Lands 2019 - Building secure cloud applications with Azure Key Vault
Azure Low Lands 2019 - Building secure cloud applications with Azure Key VaultTom Kerkhove
╠²
The document discusses the importance of using Azure Key Vault for secure management of sensitive information, including cryptographic keys, secrets, and certificates. It highlights features such as centralized secret management, the ability to revoke access, and authentication via Azure Active Directory or Managed Service Identity. The document emphasizes best practices for security, including using multiple Key Vault instances per security domain and managing permissions carefully.Secret Management with Hashicorp Vault and Consul on Kubernetes
Secret Management with Hashicorp Vault and Consul on KubernetesAn Nguyen
╠²
The document discusses secret management with Hashicorp Vault and Consul on Kubernetes. It begins with an overview of secret management and why it is important. It then discusses traditional insecure approaches to secret management versus modern secure approaches. Hashicorp Vault is introduced as a tool for modern secret management that provides encrypted secret storage, access control, auditing and more. Features of Vault like leasing, dynamic credentials, authentication methods and enterprise features are covered. The document concludes with demos of using Vault with legacy and new applications on Kubernetes.SQL Server 2017 CLR
SQL Server 2017 CLREduardo Piairo
╠²
This document discusses SQL Server 2017 Common Language Runtime (CLR) integration. It begins by explaining what CLR is and how it allows .NET code to be executed in the SQL Server context. It then covers enabling CLR, security models using Code Access Security and host policies, and a breaking change in SQL Server 2017 regarding CLR strict security. The document concludes with references and an offer for questions.SQL Server 2017 CLR
SQL Server 2017 CLREduardo Piairo
╠²
The document discusses SQL Server 2017 CLR integration. It begins by explaining that CLR allows .NET code to be executed in the SQL Server context. It then covers enabling CLR, defining the host policy security levels (SAFE, EXTERNAL_ACCESS, UNSAFE), and the 2017 breaking change requiring all assemblies be treated as UNSAFE with the new "clr strict security" option. It concludes with references and an offer for Q&A.Toronto MuleSoft Meetup: Virtual Meetup #3
Toronto MuleSoft Meetup: Virtual Meetup #3Alexandra N. Martinez
╠²
The document provides an overview of a virtual meetup focused on SSL implementation in Mule, detailing the significance of SSL/TLS protocols for secure computer connections. It discusses the anatomy of certificates, the roles of keystore and truststore, and outlines one-way and two-way SSL handshake processes. Additionally, the meetup included organizers' introductions, a Q&A session, and information about future events.Avoiding damage, shame and regrets data protection for mobile client-server a...
Avoiding damage, shame and regrets data protection for mobile client-server a...Stanfy
╠²
The document discusses data protection strategies for mobile client-server architectures, emphasizing the importance of secure programming to mitigate eavesdropping and data breaches. Key recommendations include implementing HTTPS, SSL pinning, and forward secrecy, while avoiding common vulnerabilities such as weak ciphers and improper key management. The document also outlines practical steps for enhancing app security, like encrypting data in motion and at rest, and utilizing reputable libraries for cryptographic functions.Apache HDFS Extended Attributes and Transparent Encryption
Apache HDFS Extended Attributes and Transparent EncryptionUma Maheswara Rao Gangumalla
╠²
The document discusses extended attributes (xattrs) and transparent encryption in Apache Hadoop, detailing how xattrs allow users to associate additional metadata with files and enforce access permissions. It outlines the implementation of transparent encryption, ensuring data is encrypted at rest and in transit without performance bottlenecks, and includes examples of user and admin operations for creating and managing encryption keys. The presentation emphasizes collaboration efforts in developing next-generation big data technologies through open-source initiatives.Centralize and Simplify Secrets Management for Red Hat OpenShift Container En...
Centralize and Simplify Secrets Management for Red Hat OpenShift Container En...DevOps.com
╠²
This document provides an overview of a webinar on integrating OpenShift and Conjur for DevOps. It discusses containers and Kubernetes, and how they are not enough on their own for DevOps without additional components like networking, image registries, metrics/logging, deployment automation, application lifecycles, services, and self-service portals. It then outlines how OpenShift addresses these needs and how Conjur can integrate to provide secrets management and access control when using OpenShift for DevOps. The integration goals, components, deployment within OpenShift, and detailed flow are described to securely provide secrets to applications in a scalable and robust manner.PuppetConf 2017: Securing Secrets for Puppet, Without Interrupting Flow- Ryan...
PuppetConf 2017: Securing Secrets for Puppet, Without Interrupting Flow- Ryan...Puppet
╠²
The document discusses securing secrets for Puppet infrastructure without slowing down automation. It acknowledges that many organizations manually copy secrets or store them insecurely due to time pressures. However, exploits are increasingly targeting insecure secrets. The document proposes using the open source CyberArk Conjur tool to authenticate and authorize machine identities to retrieve secrets in a secure workflow. It provides an example of updating Puppet manifests to use Conjur for dynamic secrets retrieval without overhauling existing code. Overall, the document advocates aligning security and velocity through identity-based secrets management to reduce risks and costs from security incidents.Various Types of OpenSSL Commands and Keytool
Various Types of OpenSSL Commands and KeytoolCheapSSLsecurity
╠²
The document provides a comprehensive overview of OpenSSL and Java Keytool commands used for generating, managing, and converting SSL certificates and keys. It covers common OpenSSL commands for generating CSRs and self-signed certificates, checking the validity of keys, and converting file formats. Additionally, it details Java Keytool commands for creating and managing keystores and certificates within a Java environment.Introduction to Just in Time Access - BrightTalk
Introduction to Just in Time Access - BrightTalkHaydn Johnson
╠²
The document discusses Just-In-Time (JIT) access, a security best practice that provides short-term access to resources like SSH and database credentials, enhancing security by reducing the attack surface. It highlights tools such as AWS Systems Manager and HashiCorp Vault to manage access efficiently while addressing the challenges of credential management. The importance of reducing open ports and improving operational and security perspectives of managing credentials is emphasized throughout the document.Gaining the benefits of risk reduction for your ssh key management project
Gaining the benefits of risk reduction for your ssh key management projectSSH Communications Security
╠²
The document discusses the risks associated with SSH key management, highlighting the lack of oversight and control due to SSH user keys allowing self-provisioning without expiration dates. It outlines strategies for mitigating these risks, emphasizing governance, continuous monitoring, and avoiding past mistakes in key management practices. Key topics include risk prioritization, stakeholder alignment, and setting effective access policies to enhance security in both on-premise and cloud environments.More Related Content
What's hot (20)
Introduction to vault
Introduction to vaultHenrik H├Ėegh
╠²
Vault is a tool for securely managing secrets like API keys, passwords, and certificates. It allows users to securely store and tightly control access to tokens, passwords, certificates, API keys and other secrets. Vault handles the lifecycle of secrets, including creation, rotation, revocation and more. It also integrates with Kubernetes to securely provide secrets to pods. Vault uses a client-server architecture and supports authentication through various methods like Kubernetes service accounts.Kubernetes Secrets Management - Securing Your Production Environment
Kubernetes Secrets Management - Securing Your Production EnvironmentAkeyless
╠²
The document discusses the importance of securing Kubernetes secrets in production environments using Akeyless's secrets management platform. It highlights key challenges like the insecure storage of secrets, the need for pod and namespace segregation, and cluster access management. The solution proposed includes a robust secrets management platform that enables controlled access and enhances security through decryption at the application level and trusted identities.Hashitalks 2021 - How the Dynamic Duo of Vault and Puppet Tame SSL Certificates
Hashitalks 2021 - How the Dynamic Duo of Vault and Puppet Tame SSL CertificatesNick Maludy
╠²
This document discusses how HashiCorp Vault and Puppet can be used together to dynamically manage SSL/TLS certificates across platforms. Vault's PKI secrets engine is used to sign certificates while Puppet distributes the certificates and keys to servers and configures services to use the certificates. On Linux, Puppet writes certificates to the filesystem and reloads services. On Windows, a Puppet function is used to embed certificates in the catalog so their thumbprints can be retrieved and used to configure services in the certificate store. This dynamic duo of Vault and Puppet enables centralized signing of certificates, auto-renewal, cross-platform distribution, and integration with services.IBM Secret Key management protoco
IBM Secret Key management protocogori4
╠²
1. The document describes an IBM secret key management protocol that provides secure communication between servers and terminals.
2. It uses a tamper-resistant cryptographic facility to securely store the most important keys used to generate encryption keys.
3. The protocol establishes a master key that is used to generate session keys for encryption in a similar manner to the scheme described in a 1978 paper.Global Azure Bootcamp 2017 - Azure Key Vault
Global Azure Bootcamp 2017 - Azure Key VaultAlberto Diaz Martin
╠²
Alberto Diaz Martin is the Chief Technology and Innovation Officer at Encamina, with over 14 years in the IT industry focusing on Microsoft technologies. The document discusses Azure Key Vault, emphasizing its features for managing and securing cryptographic keys and secrets, encryption methods, and cost. It outlines workflows for using Azure Key Vault and its role in protecting sensitive data and credentials in various applications.Recipe for good secrets management
Recipe for good secrets managementKevin Gilpin
╠²
The document provides a recipe for good secrets management. It outlines requirements like separation of duties, least privilege, leak resistance, and auditing. It recommends having separate security environments for staging and production, designing for "robot" actors with limited access, rotating credentials, and automatically recording system activity. Configuration management and orchestration should provision robots and bootstrap machine identity by assigning credentials from an identity server. Secrets should be fetched from a secrets manager and stored separately from application data to satisfy compliance standards.Hardening Kubernetes Cluster
Hardening Kubernetes ClusterKnoldus Inc.
╠²
The document presents a comprehensive overview of hardening Kubernetes clusters, highlighting crucial aspects such as securing the cluster, authentication, authorization, image security, and secrets management. It emphasizes best practices like limiting API and dashboard exposure, using role-based access control, and implementing secure image storage and container management. The content is aimed at enhancing the security posture of Kubernetes environments within the context of software development lifecycle (SDLC).Securing sensitive data with Azure Key Vault
Securing sensitive data with Azure Key VaultTom Kerkhove
╠²
The document discusses the Azure Key Vault as a solution for securing sensitive data by storing it in hardware security modules (HSM) and providing customers with control over the key lifecycle and access management. It highlights the importance of moving away from storing sensitive data in plaintext and emphasizes the role of Audit Logs and Access Control based on Azure Active Directory. Additionally, it outlines the features and pricing of Azure Key Vault, including secrets and keys management, disaster recovery considerations, and future updates for broader availability and enhanced tooling.Azure key vault
Azure key vaultRahul Nath
╠²
Azure Key Vault is a cloud service that securely stores keys, secrets, and certificates. It allows storing cryptographic keys and secrets that applications and services use while keeping them safe from unauthorized access. Key Vault uses hardware security modules to encrypt keys and secrets. Typical applications would store secrets like connection strings in Key Vault rather than configuration files for improved security and management. Key Vault integrates with Azure Active Directory for authentication so applications can access secrets securely.ITProceed 2015 - Securing Sensitive Data with Azure Key Vault
ITProceed 2015 - Securing Sensitive Data with Azure Key VaultTom Kerkhove
╠²
This document discusses securing sensitive data using Azure Key Vault, highlighting its role in managing encryption keys, secrets, and access control. It outlines the benefits of Azure Key Vault, including secure storage, control over key lifecycle, and monitoring capabilities. The document also addresses potential security flaws and emphasizes the importance of encryption in protecting sensitive data.Azure Low Lands 2019 - Building secure cloud applications with Azure Key Vault
Azure Low Lands 2019 - Building secure cloud applications with Azure Key VaultTom Kerkhove
╠²
The document discusses the importance of using Azure Key Vault for secure management of sensitive information, including cryptographic keys, secrets, and certificates. It highlights features such as centralized secret management, the ability to revoke access, and authentication via Azure Active Directory or Managed Service Identity. The document emphasizes best practices for security, including using multiple Key Vault instances per security domain and managing permissions carefully.Secret Management with Hashicorp Vault and Consul on Kubernetes
Secret Management with Hashicorp Vault and Consul on KubernetesAn Nguyen
╠²
The document discusses secret management with Hashicorp Vault and Consul on Kubernetes. It begins with an overview of secret management and why it is important. It then discusses traditional insecure approaches to secret management versus modern secure approaches. Hashicorp Vault is introduced as a tool for modern secret management that provides encrypted secret storage, access control, auditing and more. Features of Vault like leasing, dynamic credentials, authentication methods and enterprise features are covered. The document concludes with demos of using Vault with legacy and new applications on Kubernetes.SQL Server 2017 CLR
SQL Server 2017 CLREduardo Piairo
╠²
This document discusses SQL Server 2017 Common Language Runtime (CLR) integration. It begins by explaining what CLR is and how it allows .NET code to be executed in the SQL Server context. It then covers enabling CLR, security models using Code Access Security and host policies, and a breaking change in SQL Server 2017 regarding CLR strict security. The document concludes with references and an offer for questions.SQL Server 2017 CLR
SQL Server 2017 CLREduardo Piairo
╠²
The document discusses SQL Server 2017 CLR integration. It begins by explaining that CLR allows .NET code to be executed in the SQL Server context. It then covers enabling CLR, defining the host policy security levels (SAFE, EXTERNAL_ACCESS, UNSAFE), and the 2017 breaking change requiring all assemblies be treated as UNSAFE with the new "clr strict security" option. It concludes with references and an offer for Q&A.Toronto MuleSoft Meetup: Virtual Meetup #3
Toronto MuleSoft Meetup: Virtual Meetup #3Alexandra N. Martinez
╠²
The document provides an overview of a virtual meetup focused on SSL implementation in Mule, detailing the significance of SSL/TLS protocols for secure computer connections. It discusses the anatomy of certificates, the roles of keystore and truststore, and outlines one-way and two-way SSL handshake processes. Additionally, the meetup included organizers' introductions, a Q&A session, and information about future events.Avoiding damage, shame and regrets data protection for mobile client-server a...
Avoiding damage, shame and regrets data protection for mobile client-server a...Stanfy
╠²
The document discusses data protection strategies for mobile client-server architectures, emphasizing the importance of secure programming to mitigate eavesdropping and data breaches. Key recommendations include implementing HTTPS, SSL pinning, and forward secrecy, while avoiding common vulnerabilities such as weak ciphers and improper key management. The document also outlines practical steps for enhancing app security, like encrypting data in motion and at rest, and utilizing reputable libraries for cryptographic functions.Apache HDFS Extended Attributes and Transparent Encryption
Apache HDFS Extended Attributes and Transparent EncryptionUma Maheswara Rao Gangumalla
╠²
The document discusses extended attributes (xattrs) and transparent encryption in Apache Hadoop, detailing how xattrs allow users to associate additional metadata with files and enforce access permissions. It outlines the implementation of transparent encryption, ensuring data is encrypted at rest and in transit without performance bottlenecks, and includes examples of user and admin operations for creating and managing encryption keys. The presentation emphasizes collaboration efforts in developing next-generation big data technologies through open-source initiatives.Centralize and Simplify Secrets Management for Red Hat OpenShift Container En...
Centralize and Simplify Secrets Management for Red Hat OpenShift Container En...DevOps.com
╠²
This document provides an overview of a webinar on integrating OpenShift and Conjur for DevOps. It discusses containers and Kubernetes, and how they are not enough on their own for DevOps without additional components like networking, image registries, metrics/logging, deployment automation, application lifecycles, services, and self-service portals. It then outlines how OpenShift addresses these needs and how Conjur can integrate to provide secrets management and access control when using OpenShift for DevOps. The integration goals, components, deployment within OpenShift, and detailed flow are described to securely provide secrets to applications in a scalable and robust manner.PuppetConf 2017: Securing Secrets for Puppet, Without Interrupting Flow- Ryan...
PuppetConf 2017: Securing Secrets for Puppet, Without Interrupting Flow- Ryan...Puppet
╠²
The document discusses securing secrets for Puppet infrastructure without slowing down automation. It acknowledges that many organizations manually copy secrets or store them insecurely due to time pressures. However, exploits are increasingly targeting insecure secrets. The document proposes using the open source CyberArk Conjur tool to authenticate and authorize machine identities to retrieve secrets in a secure workflow. It provides an example of updating Puppet manifests to use Conjur for dynamic secrets retrieval without overhauling existing code. Overall, the document advocates aligning security and velocity through identity-based secrets management to reduce risks and costs from security incidents.Various Types of OpenSSL Commands and Keytool
Various Types of OpenSSL Commands and KeytoolCheapSSLsecurity
╠²
The document provides a comprehensive overview of OpenSSL and Java Keytool commands used for generating, managing, and converting SSL certificates and keys. It covers common OpenSSL commands for generating CSRs and self-signed certificates, checking the validity of keys, and converting file formats. Additionally, it details Java Keytool commands for creating and managing keystores and certificates within a Java environment.Similar to Streamline CI/CD with Just-in-Time Access (9)
Introduction to Just in Time Access - BrightTalk
Introduction to Just in Time Access - BrightTalkHaydn Johnson
╠²
The document discusses Just-In-Time (JIT) access, a security best practice that provides short-term access to resources like SSH and database credentials, enhancing security by reducing the attack surface. It highlights tools such as AWS Systems Manager and HashiCorp Vault to manage access efficiently while addressing the challenges of credential management. The importance of reducing open ports and improving operational and security perspectives of managing credentials is emphasized throughout the document.Gaining the benefits of risk reduction for your ssh key management project
Gaining the benefits of risk reduction for your ssh key management projectSSH Communications Security
╠²
The document discusses the risks associated with SSH key management, highlighting the lack of oversight and control due to SSH user keys allowing self-provisioning without expiration dates. It outlines strategies for mitigating these risks, emphasizing governance, continuous monitoring, and avoiding past mistakes in key management practices. Key topics include risk prioritization, stakeholder alignment, and setting effective access policies to enhance security in both on-premise and cloud environments.The Myth of SSH Key Rotation Mythcracker Webcast Series Part 3
The Myth of SSH Key Rotation Mythcracker Webcast Series Part 3 SSH Communications Security
╠²
The document discusses the challenges and myths surrounding SSH key rotation and management, highlighting common misconceptions about security improvements through key rotation and the complexity of implementing it effectively. It emphasizes the importance of continuous monitoring, proper key discovery, and automating key management processes to mitigate risks associated with unauthorized access. Furthermore, it outlines SSH Communications Security's role in providing solutions for access management and the governance of secure shell authentication.Application security meetup - cloud security best practices 24062021
Application security meetup - cloud security best practices 24062021lior mazor
╠²
The document outlines Akeyless Security Ltd.'s approach to cloud security, emphasizing its unique zero-knowledge KMS technology for secrets management. It discusses essential security steps, including data encryption, identity validation, and privileged access management within cloud infrastructures. Additionally, it highlights trends in secrets management, challenges of Kubernetes, and the necessity of robust audit trails and access controls to safeguard sensitive data.SSH Keys: Security Asset or Liability?
SSH Keys: Security Asset or Liability?Michael Thelander
╠²
The document discusses securing SSH keys in large enterprises. It notes that while SSH is ubiquitous and free, it can also pose high risks if not properly managed. A 2017 study found that over 90% of organizations have no complete inventory of their SSH keys and many do not enforce policies like key rotation for terminated employees. The document advocates for gaining visibility into SSH keys through discovery and inventory tools, gaining intelligence about vulnerabilities and risks, and automating key management best practices to reduce security risks from SSH.Application and Server Security
Application and Server SecurityBrian Pontarelli
╠²
The document outlines essential best practices for server and application security, emphasizing the importance of password security, two-factor authentication, and intrusion detection measures. It provides practical steps for configuring firewalls, remote access, and user permissions while also highlighting the significance of encryption techniques and protecting against SQL injection attacks. The author, a CEO with extensive experience in software development, stresses the urgency of implementing these security measures to prevent data breaches.Akeyless Security - The best cyber security company to watch 2022- The Silico...
Akeyless Security - The best cyber security company to watch 2022- The Silico...Philip c
╠²
Akeyless is a cloud-native SaaS platform designed for the centralized management and protection of secrets, crucial for modern enterprises operating in DevOps and hybrid environments. The platform addresses the rising security risks associated with secret sprawl by offering a unique zero knowledge solution, ensuring that even Akeyless cannot access customer secrets. Led by a team with extensive experience in security, Akeyless enables organizations to secure their workloads while ensuring compliance and regulatory standards.Securing SSH Access by Pavel Shukhman at OWASP Ottawa Meetup, August 2019
Securing SSH Access by Pavel Shukhman at OWASP Ottawa Meetup, August 2019Pavel Shukhman
╠²
The document discusses securing SSH access, highlighting various attack vectors such as brute-force attacks, man-in-the-middle vulnerabilities, and insider threats. It provides strategies for prevention, including using strong ciphers, implementing two-factor authentication, and employing bastion hosts for access. Additionally, it emphasizes the importance of managing private keys securely and maintaining a trusted administrative workforce.Securing Serverless by Breaking in
Securing Serverless by Breaking inC4Media
╠²
Guy Podjarny from Snyk gave a presentation on securing serverless applications. He demonstrated vulnerabilities in a sample serverless app and how to fix them. The main security issues discussed were vulnerable dependencies, denial of service attacks from regular expression denial of service (ReDoS) vulnerabilities, secrets in code, granular permissions and functions, and immutable servers being reused. Podjarny emphasized testing for vulnerabilities, using key management systems, deploying narrowly-scoped functions, and monitoring functions over time.Gaining the benefits of risk reduction for your ssh key management project
Gaining the benefits of risk reduction for your ssh key management projectSSH Communications Security
╠²
Ad
Recently uploaded (20)
OWASP Barcelona 2025 Threat Model Library
OWASP Barcelona 2025 Threat Model LibraryPetraVukmirovic
╠²
Threat Model Library Launch at OWASP Barcelona 2025
https://owasp.org/www-project-threat-model-library/Edge-banding-machines-edgeteq-s-200-en-.pdf
Edge-banding-machines-edgeteq-s-200-en-.pdfAmirStern2
╠²
ū×ūøūĢūĀū¬ ū¦ūĀūśūÖūØ ūöū×ū¬ūÉūÖū×ūö ū£ūĀūÆū©ūÖūĢū¬ ū¦ūśūĀūĢū¬ ūÉūĢ ūÆūōūĢū£ūĢū¬ (ūøū×ūøūĢūĀū¬ ūÆūÖūæūĢūÖ).
ū×ūōūæūÖū¦ūö ū¦ūĀūśūÖūØ ū×ūÆū£ūÖū£ ūÉūĢ ūżūĪūÖūØ, ūóūō ūóūĢūæūÖ ū¦ūĀūś ŌĆō 3 ū×"ū× ūĢūóūĢūæūÖ ūŚūĢū×ū© ūóūō 40 ū×"ū×. ūæū¦ū© ū×ū×ūĢūŚū®ūæ ūöū×ū¬ū©ūÖūó ūóū£ ū¬ū¦ū£ūĢū¬, ūĢū×ūĀūĢūóūÖūØ ū×ūÉūĪūÖūæūÖūÖūØ ū¬ūóū®ūÖūÖū¬ūÖūÖūØ ūøū×ūĢ ūæū×ūøūĢūĀūĢū¬ ūöūÆūōūĢū£ūĢū¬.FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptx
FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptxFIDO Alliance
╠²
FIDO Seminar: Perspectives on Passkeys & Consumer AdoptionMastering AI Workflows with FME - Peak of Data & AI 2025
Mastering AI Workflows with FME - Peak of Data & AI 2025Safe Software
╠²
Harness the full potential of AI with FME: From creating high-quality training data to optimizing models and utilizing results, FME supports every step of your AI workflow. Seamlessly integrate a wide range of models, including those for data enhancement, forecasting, image and object recognition, and large language models. Customize AI models to meet your exact needs with FMEŌĆÖs powerful tools for training, optimization, and seamless integrationDown the Rabbit Hole ŌĆō Solving 5 Training Roadblocks
Down the Rabbit Hole ŌĆō Solving 5 Training RoadblocksRustici Software
╠²
Feeling stuck in the Matrix of your training technologies? YouŌĆÖre not alone. Managing your training catalog, wrangling LMSs and delivering content across different tools and audiences can feel like dodging digital bullets. At some point, you hit a fork in the road: Keep patching things up as issues pop upŌĆ” or follow the rabbit hole to the root of the problems.
Good news, weŌĆÖve already been down that rabbit hole. Peter Overton and Cameron Gray of Rustici Software are here to share what we found. In this webinar, weŌĆÖll break down 5 training roadblocks in delivery and management and show you how theyŌĆÖre easier to fix than you might think.FME for Good: Integrating Multiple Data Sources with APIs to Support Local Ch...
FME for Good: Integrating Multiple Data Sources with APIs to Support Local Ch...Safe Software
╠²
Have-a-skate-with-Bob (HASB-KC) is a local charity that holds two Hockey Tournaments every year to raise money in the fight against Pancreatic Cancer. The FME Form software is used to integrate and exchange data via API, between Google Forms, Google Sheets, Stripe payments, SmartWaiver, and the GoDaddy email marketing tools to build a grass-roots Customer Relationship Management (CRM) system for the charity. The CRM is used to communicate effectively and readily with the participants of the hockey events and most importantly the local area sponsors of the event. Communication consists of a BLOG used to inform participants of event details including, the ever-important team rosters. Funds raised by these events are used to support families in the local area to fight cancer and support PanCan research efforts to find a cure against this insidious disease. FME Form removes the tedium and error-prone manual ETL processes against these systems into 1 or 2 workbenches that put the data needed at the fingertips of the event organizers daily freeing them to work on outreach and marketing of the events in the community.No-Code Workflows for CAD & 3D Data: Scaling AI-Driven Infrastructure
No-Code Workflows for CAD & 3D Data: Scaling AI-Driven InfrastructureSafe Software
╠²
When projects depend on fast, reliable spatial data, every minute counts.
AI Clearing needed a faster way to handle complex spatial data from drone surveys, CAD designs and 3D project models across construction sites. With FME Form, they built no-code workflows to clean, convert, integrate, and validate dozens of data formats ŌĆō cutting analysis time from 5 hours to just 30 minutes.
Join us, our partner Globema, and customer AI Clearing to see how they:
-Automate processing of 2D, 3D, drone, spatial, and non-spatial data
-Analyze construction progress 10x faster and with fewer errors
-Handle diverse formats like DWG, KML, SHP, and PDF with ease
-Scale their workflows for international projects in solar, roads, and pipelines
If you work with complex data, join us to learn how to optimize your own processes and transform your results with FME.FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptx
FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptxFIDO Alliance
╠²
FIDO Seminar: Evolving Landscape of Post-Quantum CryptographyProviding an OGC API Processes REST Interface for FME Flow
Providing an OGC API Processes REST Interface for FME FlowSafe Software
╠²
This presentation will showcase an adapter for FME Flow that provides REST endpoints for FME Workspaces following the OGC API Processes specification. The implementation delivers robust, user-friendly API endpoints, including standardized methods for parameter provision. Additionally, it enhances security and user management by supporting OAuth2 authentication. Join us to discover how these advancements can elevate your enterprise integration workflows and ensure seamless, secure interactions with FME Flow.Enabling BIM / GIS integrations with Other Systems with FME
Enabling BIM / GIS integrations with Other Systems with FMESafe Software
╠²
Jacobs has successfully utilized FME to tackle the complexities of integrating diverse data sources in a confidential $1 billion campus improvement project. The project aimed to create a comprehensive digital twin by merging Building Information Modeling (BIM) data, Construction Operations Building Information Exchange (COBie) data, and various other data sources into a unified Geographic Information System (GIS) platform. The challenge lay in the disparate nature of these data sources, which were siloed and incompatible with each other, hindering efficient data management and decision-making processes.
To address this, Jacobs leveraged FME to automate the extraction, transformation, and loading (ETL) of data between ArcGIS Indoors and IBM Maximo. This process ensured accurate transfer of maintainable asset and work order data, creating a comprehensive 2D and 3D representation of the campus for Facility Management. FME's server capabilities enabled real-time updates and synchronization between ArcGIS Indoors and Maximo, facilitating automatic updates of asset information and work orders. Additionally, Survey123 forms allowed field personnel to capture and submit data directly from their mobile devices, triggering FME workflows via webhooks for real-time data updates. This seamless integration has significantly enhanced data management, improved decision-making processes, and ensured data consistency across the project lifecycle.ŌĆ£From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...
ŌĆ£From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...Edge AI and Vision Alliance
╠²
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/from-enterprise-to-makers-driving-vision-ai-innovation-at-the-extreme-edge-a-presentation-from-sony-semiconductor-solutions/
Amir Servi, Edge Deep Learning Product Manager at Sony Semiconductor Solutions, presents the ŌĆ£From Enterprise to Makers: Driving Vision AI Innovation at the Extreme EdgeŌĆØ tutorial at the May 2025 Embedded Vision Summit.
SonyŌĆÖs unique integrated sensor-processor technology is enabling ultra-efficient intelligence directly at the image source, transforming vision AI for enterprises and developers alike. In this presentation, Servi showcases how the AITRIOS platform simplifies vision AI for enterprises with tools for large-scale deployments and model management.
Servi also highlights his companyŌĆÖs collaboration with Ultralytics and Raspberry Pi, which brings YOLO models to the developer community, empowering grassroots innovation. Whether youŌĆÖre scaling vision AI for industry or experimenting with cutting-edge tools, this presentation will demonstrate how Sony is accelerating high-performance, energy-efficient vision AI for all.AI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D
╠²
This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.Floods in Valencia: Two FME-Powered Stories of Data Resilience
Floods in Valencia: Two FME-Powered Stories of Data ResilienceSafe Software
╠²
In October 2024, the Spanish region of Valencia faced severe flooding that underscored the critical need for accessible and actionable data. This presentation will explore two innovative use cases where FME facilitated data integration and availability during the crisis. The first case demonstrates how FME was used to process and convert satellite imagery and other geospatial data into formats tailored for rapid analysis by emergency teams. The second case delves into making human mobility dataŌĆöcollected from mobile phone signalsŌĆöaccessible as source-destination matrices, offering key insights into population movements during and after the flooding. These stories highlight how FME's powerful capabilities can bridge the gap between raw data and decision-making, fostering resilience and preparedness in the face of natural disasters. Attendees will gain practical insights into how FME can support crisis management and urban planning in a changing climate.OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC
╠²
The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.Bridging the divide: A conversation on tariffs today in the book industry - T...
Bridging the divide: A conversation on tariffs today in the book industry - T...BookNet Canada
╠²
A collaboration-focused conversation on the recently imposed US and Canadian tariffs where speakers shared insights into the current legislative landscape, ongoing advocacy efforts, and recommended next steps. This event was presented in partnership with the Book Industry Study Group.
Link to accompanying resource: https://bnctechforum.ca/sessions/bridging-the-divide-a-conversation-on-tariffs-today-in-the-book-industry/
Presented by BookNet Canada and the Book Industry Study Group on May 29, 2025 with support from the Department of Canadian Heritage.FME for Distribution & Transmission Integrity Management Program (DIMP & TIMP)
FME for Distribution & Transmission Integrity Management Program (DIMP & TIMP)Safe Software
╠²
Peoples Gas in Chicago, IL has changed to a new Distribution & Transmission Integrity Management Program (DIMP & TIMP) software provider in recent years. In order to successfully deploy the new software we have created a series of ETL processes using FME Form to transform our gas facility data to meet the required DIMP & TIMP data specifications. This presentation will provide an overview of how we used FME to transform data from ESRIŌĆÖs Utility Network and several other internal and external sources to meet the strict data specifications for the DIMP and TIMP software solutions.Kubernetes Security Act Now Before ItŌĆÖs Too Late
Kubernetes Security Act Now Before ItŌĆÖs Too LateMichael Furman
╠²
In today's cloud-native landscape, Kubernetes has become the de facto standard for orchestrating containerized applications, but its inherent complexity introduces unique security challenges. Are you one YAML away from disaster?
This presentation, "Kubernetes Security: Act Now Before ItŌĆÖs Too Late," is your essential guide to understanding and mitigating the critical security risks within your Kubernetes environments. This presentation dives deep into the OWASP Kubernetes Top Ten, providing actionable insights to harden your clusters.
We will cover:
The fundamental architecture of Kubernetes and why its security is paramount.
In-depth strategies for protecting your Kubernetes Control Plane, including kube-apiserver and etcd.
Crucial best practices for securing your workloads and nodes, covering topics like privileged containers, root filesystem security, and the essential role of Pod Security Admission.
Don't wait for a breach. Learn how to identify, prevent, and respond to Kubernetes security threats effectively.
It's time to act now before it's too late!The State of Web3 Industry- Industry Report
The State of Web3 Industry- Industry ReportLiveplex
╠²
Web3 is poised for mainstream integration by 2030, with decentralized applications potentially reaching billions of users through improved scalability, user-friendly wallets, and regulatory clarity. Many forecasts project trillions of dollars in tokenized assets by 2030 , integration of AI, IoT, and Web3 (e.g. autonomous agents and decentralized physical infrastructure), and the possible emergence of global interoperability standards. Key challenges going forward include ensuring security at scale, preserving decentralization principles under regulatory oversight, and demonstrating tangible consumer value to sustain adoption beyond speculative cycles.Security Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante
╠²
Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.June Patch Tuesday
June Patch TuesdayIvanti
╠²
IvantiŌĆÖs Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There weŌĆÖll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities. ŌĆ£From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...
ŌĆ£From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...Edge AI and Vision Alliance
╠²
Ad
