Audio Watermarking - JIIT noida 2013-14 by Vaibhav Arora and Isha Garg
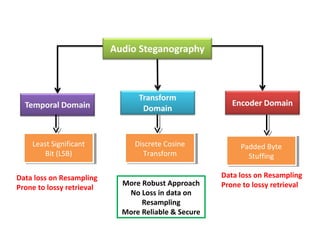
- 1. Least Significant Bit (LSB) Least Significant Bit (LSB) Discrete Cosine Transform Discrete Cosine Transform Padded Byte Stuffing Padded Byte Stuffing Data loss on Resampling Prone to lossy retrieval Data loss on Resampling Prone to lossy retrievalMore Robust Approach No Loss in data on Resampling More Reliable & Secure
- 2. DCT- Discrete Cosine Transform DCT- Discrete Cosine Transform
- 3. Embedding in Dual Channel ŌĆō More SecurityEmbedding in Dual Channel ŌĆō More Security Audio Sample Right Channel Left Channel Synchronization Code Selects the Channel Watermarked Audio Track Watermarked Audio Track
- 4. Inverse Discrete Cosine Transform Audio DataAudio Data Block 1 Block 1 Block 2 Block 2 Block 3 Block 3 Block n Block n Discrete Cosine Transform DCT Data DCT Data DCT Data DCT Data DCT Data DCT Data DCT Data DCT Data DCTŌĆÖ Data DCTŌĆÖ Data DCTŌĆÖ Data DCTŌĆÖ Data Watermark Embedded in AudioWatermark Embedded in Audio Selecting Mid-Range of DCT BlockSelecting Mid-Range of DCT Block ŌĆ” Mid Range ŌĆ” ŌĆ”
- 5. 5 6 7 8 1 2 3 4 13 14 15 16 9 10 11 12 8 5 6 7 4 1 2 3 16 13 14 15 12 9 10 11 1 2 3 4 13 14 15 16 9 10 11 12 5 6 77 8 Original Watermark Circular Shifted Watermark- Type 1 Circular Shifted Watermark- Type 2 Circular Shifting of Original Watermark Circular Shifting of Original Watermark
- 6. Application of Detecting Distributor of unauthorized copy of Audio file based on the Algorithm Application of Detecting Distributor of unauthorized copy of Audio file based on the Algorithm APPLICATION
- 7. Watermark generation for client (unique key) Upload Audio Add Client for Audio Watermarked Audio is sent to client Unique Watermark stored in database for theft detection Login Panel Enter Client Details PUBLISHER MODULE
- 8. Watermark Extraction from audioUpload Audio Client Information DisplayedClient Information Displayed Fetching from Database [ FOUND ] DETECTION & TRACKING MODULE Login Panel KEY BASEDKEY BASED







![Watermark Extraction from audioUpload Audio
Client Information DisplayedClient Information Displayed
Fetching from
Database
[ FOUND ]
DETECTION & TRACKING MODULE
Login Panel
KEY BASEDKEY BASED](https://image.slidesharecdn.com/vaibhavaroraishagargmajor-jiitnoida2013-14-140529014928-phpapp02/85/Audio-Watermarking-JIIT-noida-2013-14-by-Vaibhav-Arora-and-Isha-Garg-8-320.jpg)