1 of 37
Download to read offline














Ad
Recommended
CompTIA Network+ Lesson
CompTIA Network+ LessonPhoenix TS
?
The document provides an overview of a Network+ course led by instructor Rose Asutaku, detailing housekeeping information, course structure, and today's objectives. Key topics include the representation of decimal numbers in binary, conversion techniques between decimal and binary, and the format of an IPv4 address. The course includes expectations for participation, an examination format, and interactive examples for practice.PACE-IT: Introduction to IPv4 (part 1) - N10 006
PACE-IT: Introduction to IPv4 (part 1) - N10 006 Pace IT at Edmonds Community College
?
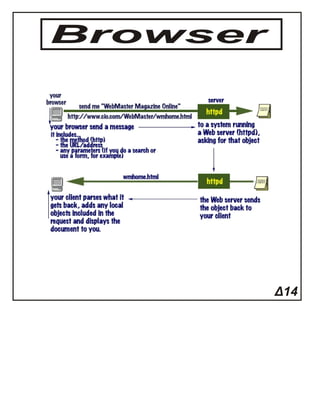
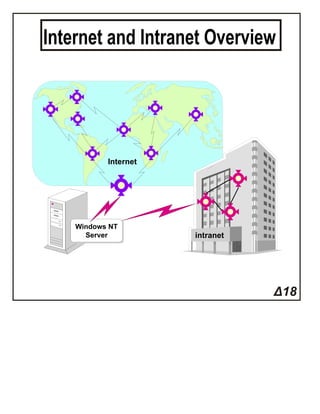
The document introduces IPv4 addressing, explaining its structure as a 32-bit binary number with over four billion possible combinations. It outlines the use of subnet masks to differentiate between network and node portions of IP addresses. Additionally, it emphasizes the logical nature of IP addressing, allowing for easier modifications compared to physical MAC addresses.Networking Chapter 11
Networking Chapter 11mlrbrown
?
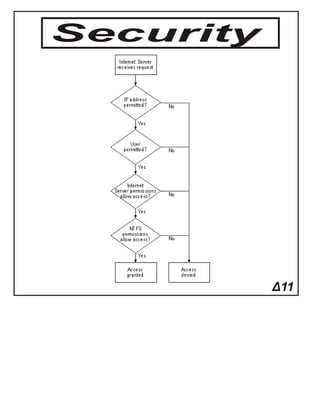
This document discusses securing TCP/IP networks. It covers four main areas of TCP/IP security: encryption, non-repudiation, authentication, and authorization. Encryption involves scrambling data so it can only be unscrambled by the intended recipient. Common encryption standards discussed include asymmetric key algorithms which allow secure key exchange. Secure TCP/IP applications then use these standards and tools to protect data in transit, such as HTTPS which uses SSL/TLS encryption for web traffic security.A¦Î¦É¦Ï¦Ë?¦Ã¦Ç¦Ò¦Ç ¦Ó¦Ï¦Ô ¦Å¦Ê¦Ð¦Á¦É¦Ä¦Å¦Ô¦Ó¦É¦Ê¦Ï? ?¦Ñ¦Ã¦Ï¦Ô
A¦Î¦É¦Ï¦Ë?¦Ã¦Ç¦Ò¦Ç ¦Ó¦Ï¦Ô ¦Å¦Ê¦Ð¦Á¦É¦Ä¦Å¦Ô¦Ó¦É¦Ê¦Ï? ?¦Ñ¦Ã¦Ï¦ÔSakis Karakousis
?
A¦Î¦É¦Ï¦Ë?¦Ã¦Ç¦Ò¦Ç ¦Ó¦Ï¦Ô ¦Å¦Ê¦Ð¦Á¦É¦Ä¦Å¦Ô¦Ó¦É¦Ê¦Ï? ?¦Ñ¦Ã¦Ï¦ÔCompTIA International Trends in Cybersecurity
CompTIA International Trends in CybersecurityCompTIA
?
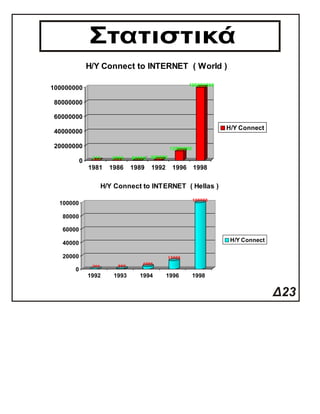
The April 2016 report on international trends in cybersecurity indicates a growing priority for IT security, with 79% of businesses expecting it to increase over the next two years. Key drivers for changing security approaches include changes in IT operations and reports of breaches at other firms, while the top security concerns are malware, hacking, and data loss. Human error is increasingly identified as a significant factor in security breaches, with 61% of firms reporting at least one serious breach in the past year.1¦Ï ¦¥¦°¦¡¦« ¦ª¦Á¦Ó¦Å¦Ñ?¦Í¦Ç? / 2008-09
1¦Ï ¦¥¦°¦¡¦« ¦ª¦Á¦Ó¦Å¦Ñ?¦Í¦Ç? / 2008-09Sakis Karakousis
?
¦°¦Á¦Ñ¦Ï¦Ô¦Ò?¦Á¦Ò¦Ç ¦Ó¦Ï¦Ô 1¦Ï¦Ô ¦¥¦°¦¡¦« ¦ª¦Á¦Ó¦Å¦Ñ?¦Í¦Ç? ¦Ò¦Ó¦Á ¦Ð¦Ë¦Á?¦Ò¦É¦Á ¦Ó¦Ï¦Ô ¦Ð¦Ñ¦Ï¦Ã¦Ñ?¦Ì¦Ì¦Á¦Ó¦Ï? Comenius 2008-10 ¦Ò¦Ó¦Ç ¦«¦Å¦Ó¦Ï¦Í?¦Á - ¦¢¦Å¦Í¦Ó¦Ò¦Ð¦É¦Ë?Comp tia n+_session_09
Comp tia n+_session_09Niit Care
?
The document discusses several methods for securing networks and remote access, including network authentication, data encryption, and remote networking architectures. It describes common authentication methods like strong passwords, Kerberos, and EAP. It also outlines various data encryption techniques and technologies such as key-based encryption systems, DES, digital certificates, and IPSec. Finally, it mentions remote networking implementations and terminal services.PACE-IT: Network Cabling (part 3) - N10 006
PACE-IT: Network Cabling (part 3) - N10 006 Pace IT at Edmonds Community College
?
The document outlines areas of expertise and qualifications in network cabling, emphasizing the importance of using quality tools such as crimpers, wire strippers, and cable testers for effective network management. It also highlights the role of media converters in transitioning between different types of cabling, specifically between fiber optic and copper networks. Additionally, it mentions funding from the U.S. Department of Labor for the program and confirms the institution's commitment to equal opportunity and accommodating students with disabilities.IBM BladeCenter Fundamentals
Introduction
IBM BladeCenter Fundamentals
Introduction
Dsunte Wilson
?
The document provides an overview of IBM BladeCenter fundamentals, detailing its components, chassis types, and dynamic infrastructure capabilities. It outlines various models, their specifications, power requirements, cooling systems, and redundancy features. Additionally, it emphasizes the benefits of BladeCenter in cost reduction, risk management, and service improvement across IT environments.CompTIA Network+ Objectives
CompTIA Network+ Objectivessombat nirund
?
The document provides an overview of the CompTIA Network+ certification exam objectives. It outlines the five domains covered in the exam: network concepts, installation and configuration, network media and topologies, network management, and network security. For each domain, it lists specific objectives and knowledge/skills expected of candidates, such as networking fundamentals, installing and configuring routers/switches, troubleshooting connectivity issues, and implementing basic security measures.SYMANTEC ENDPOINT PROTECTION Administration Introduction
SYMANTEC ENDPOINT PROTECTION Administration IntroductionDsunte Wilson
?
Symantec Endpoint Protection is a comprehensive client-server solution that provides protection against malware on various devices including laptops, desktops, and servers. It combines virus and spyware protection, network threat protection, and proactive threat protection to address known and unknown vulnerabilities. Key features include real-time scanning, a firewall, intrusion prevention systems, and device control to prevent data leakage.Introduction to oracle primavera
Introduction to oracle primaveraDsunte Wilson
?
This three-day training course covers the fundamentals of using Oracle Primavera, including the project management lifecycle, navigating and customizing layouts, creating projects and work breakdown structures, scheduling activities with relationships and constraints, assigning resources and costs, optimizing and baselining project plans, tracking project execution, and reporting performance. Topics to be covered include the enterprise project structure, activity networking, resource leveling, baseline tracking, progress updating, and creating project web sites.CCNA PPP and Frame Relay
CCNA PPP and Frame RelayDsunte Wilson
?
The document discusses PPP and Frame Relay networking fundamentals. It describes how PPP provides encapsulation and authentication over various physical interfaces. Frame Relay uses virtual circuits identified by DLCI numbers to transmit data over WAN links. Routers establish Frame Relay maps using Inverse ARP or static configuration to associate remote IP addresses with DLCIs. The document provides instructions for configuring PPP and Frame Relay on Cisco routers.CCNA Access Lists
CCNA Access ListsDsunte Wilson
?
The document discusses access lists in Cisco networking. It describes how standard IP access lists filter based on source IP addresses while extended IP access lists can filter on source, destination, protocol and port. It provides examples of creating standard and extended IP access lists and applying them to interfaces to filter traffic. It also covers using access lists to restrict VTY line access and creating access lists using the Security Device Manager user interface.CCNA Network Services
CCNA Network ServicesDsunte Wilson
?
The document discusses network services including network address translation (NAT), Dynamic Host Configuration Protocol (DHCP), and Domain Name Services (DNS). It describes how NAT allows private IP addresses to access the internet using public IP addresses through static NAT, dynamic NAT, or port address translation (PAT). DHCP automatically assigns IP addresses to devices on a network, while DNS translates names to IP addresses. The document also discusses configuring these services on Cisco routers using both CLI commands and the Cisco Security Device Manager web tool.CCNA Advanced Switching
CCNA Advanced SwitchingDsunte Wilson
?
The document discusses advanced switching concepts including the Spanning Tree Protocol (STP), virtual LANs (VLANs), and the VLAN Trunking Protocol (VTP). STP builds a logical topology to prevent loops, elects a root bridge, and puts ports in different states. VLANs segment broadcast domains and provide benefits like security and flexibility. VTP manages VLAN configurations across trunk links within the same VTP domain.CCNA Router Startup and Configuration
CCNA Router Startup and ConfigurationDsunte Wilson
?
The document describes the startup process and configuration of Cisco routers. It explains that routers go through a boot process including hardware tests, loading the bootstrap and Cisco IOS. IP and routing can then be configured on interfaces. Connectivity can be tested using tools like ping, telnet and show commands. The document also covers topics like CDP, passwords, firmware and using SDM for security configurations.CCNA Router and IOS Basics
CCNA Router and IOS BasicsDsunte Wilson
?
The document discusses the basics of Cisco routers and the Cisco IOS. It describes the router user interface, including different access methods and configuration modes. It also covers router components, passwords, and the functions of ROM, flash memory, NVRAM, RAM and interfaces.SYMANTEC ENDPOINT PROTECTION Interfacing the SEPM with Protection Center
SYMANTEC ENDPOINT PROTECTION Interfacing the SEPM with Protection CenterDsunte Wilson
?
The document describes the integration and functionality of Symantec Endpoint Protection with Protection Center, allowing centralized management of Symantec products. It explains the setup and configuration of virtual and physical appliances and outlines the workflows available for managing endpoint tasks. Additionally, the document covers the user interface and configuration tasks within Protection Center, enhancing usability and management efficiency.CCNA Advanced Routing Protocols
CCNA Advanced Routing ProtocolsDsunte Wilson
?
This document summarizes key concepts about advanced routing protocols including classful and classless protocols, RIPv2, EIGRP, and OSPF. It describes how classful protocols like RIPv1 summarize networks based on major boundaries and cannot be used with VLSM, while classless protocols carry subnet mask information and allow routing in discontiguous networks. It provides details on configuring and components of RIPv2, EIGRP, and OSPF such as authentication, metrics, neighbor discovery, and link-state advertisements.CCNA Network Devices
CCNA Network DevicesDsunte Wilson
?
This document summarizes network devices and concepts from a CCNA guide. It describes how repeaters, hubs, wireless access points, bridges, switches and routers segment networks and control traffic. It also defines Ethernet, Fast Ethernet and Gigabit Ethernet standards, and explains half and full-duplex communication modes. The summary provides an overview of common network devices and technologies for local area networks.CCNA TCP/IP
CCNA TCP/IPDsunte Wilson
?
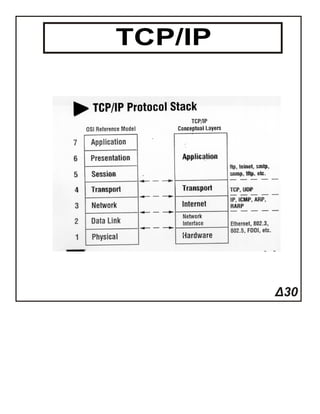
The document summarizes key concepts about TCP/IP from Chapter 3 of a CCNA guide. It discusses the origins of TCP/IP from projects by DARPA and the inclusion of TCP/IP in UNIX. It also describes the four layers of the TCP/IP model including the application, transport, internet, and network interface layers. Finally, it provides an overview of common protocols at each layer such as TCP, UDP, IP, ARP, and how packets are transmitted between hosts and routers.CCNA Routing Protocols
CCNA Routing ProtocolsDsunte Wilson
?
The document discusses routing protocols and summarizes:
- It differentiates between nonroutable, routed, and routing protocols and describes common examples like NetBEUI and TCP/IP.
- It explains interior and exterior gateway protocols and the two types of interior gateway protocols: distance-vector and link-state routing protocols.
- It provides details on RIP, a common distance-vector protocol, including how to enable and configure it.CCNA IP Addressing
CCNA IP AddressingDsunte Wilson
?
This document provides an overview of IP addressing concepts including:
- The structure of IP addresses including classes, subnet masking, and CIDR
- Techniques for subnetting networks and creating more subnets and hosts including VLSM
- The transition from IPv4 to IPv6 to address the limited address space of IPv4CCNA Basic Switching and Switch Configuration
CCNA Basic Switching and Switch ConfigurationDsunte Wilson
?
This document provides an overview of basic switching concepts and Cisco switch configuration. It explains Ethernet and how switches work to segment networks and reduce collisions. Switches operate at the data link layer and learn MAC addresses to forward frames efficiently. The document discusses switch configuration using commands like hostname, interface, duplex, and port security. It compares switching methods like store-and-forward and cut-through forwarding. The summary reiterates how switches divide collision domains to improve performance over shared-medium Ethernet.E¦Ð¦Á¦Í¦Á¦Ë¦Ç¦Ð¦Ó¦É¦Ê?? ¦Á¦Ò¦Ê?¦Ò¦Å¦É? ¦Ã¦Ë?¦Ò¦Ò¦Á? 2¦Ç? ¦Å¦Í?¦Ó¦Ç¦Ó¦Á? "¦±?¦Ó¦Á ¦Ó¦Ï ¦Í¦Å¦Ñ? ¦Ó¦É ¦Ó¦Ñ?¦Ö¦Å¦É" ¦£¦Ë?¦Ò¦Ò...
E¦Ð¦Á¦Í¦Á¦Ë¦Ç¦Ð¦Ó¦É¦Ê?? ¦Á¦Ò¦Ê?¦Ò¦Å¦É? ¦Ã¦Ë?¦Ò¦Ò¦Á? 2¦Ç? ¦Å¦Í?¦Ó¦Ç¦Ó¦Á? "¦±?¦Ó¦Á ¦Ó¦Ï ¦Í¦Å¦Ñ? ¦Ó¦É ¦Ó¦Ñ?¦Ö¦Å¦É" ¦£¦Ë?¦Ò¦Ò...¦§¦Ë¦É?¦Ä¦Ç? ¦§¦Ë?¦Á?
?
¦¥¦Ð¦Á¦Í¦Á¦Ë¦Ç¦Ð¦Ó¦É¦Ê?? ¦Á¦Ò¦Ê?¦Ò¦Å¦É? ¦Ã¦Ë?¦Ò¦Ò¦Á? 2¦Ç? ¦Å¦Í?¦Ó¦Ç¦Ó¦Á?
" ¦±?¦Ó¦Á ¦Ó¦Ï ¦Í¦Å¦Ñ? ¦Ó¦É ¦Ó¦Ñ?¦Ö¦Å¦É" ¦£¦Ë?¦Ò¦Ò¦Á ¦¤?
¦°¦Ç¦Ã?: e- selidesMore Related Content
Viewers also liked (20)
Comp tia n+_session_09
Comp tia n+_session_09Niit Care
?
The document discusses several methods for securing networks and remote access, including network authentication, data encryption, and remote networking architectures. It describes common authentication methods like strong passwords, Kerberos, and EAP. It also outlines various data encryption techniques and technologies such as key-based encryption systems, DES, digital certificates, and IPSec. Finally, it mentions remote networking implementations and terminal services.PACE-IT: Network Cabling (part 3) - N10 006
PACE-IT: Network Cabling (part 3) - N10 006 Pace IT at Edmonds Community College
?
The document outlines areas of expertise and qualifications in network cabling, emphasizing the importance of using quality tools such as crimpers, wire strippers, and cable testers for effective network management. It also highlights the role of media converters in transitioning between different types of cabling, specifically between fiber optic and copper networks. Additionally, it mentions funding from the U.S. Department of Labor for the program and confirms the institution's commitment to equal opportunity and accommodating students with disabilities.IBM BladeCenter Fundamentals
Introduction
IBM BladeCenter Fundamentals
Introduction
Dsunte Wilson
?
The document provides an overview of IBM BladeCenter fundamentals, detailing its components, chassis types, and dynamic infrastructure capabilities. It outlines various models, their specifications, power requirements, cooling systems, and redundancy features. Additionally, it emphasizes the benefits of BladeCenter in cost reduction, risk management, and service improvement across IT environments.CompTIA Network+ Objectives
CompTIA Network+ Objectivessombat nirund
?
The document provides an overview of the CompTIA Network+ certification exam objectives. It outlines the five domains covered in the exam: network concepts, installation and configuration, network media and topologies, network management, and network security. For each domain, it lists specific objectives and knowledge/skills expected of candidates, such as networking fundamentals, installing and configuring routers/switches, troubleshooting connectivity issues, and implementing basic security measures.SYMANTEC ENDPOINT PROTECTION Administration Introduction
SYMANTEC ENDPOINT PROTECTION Administration IntroductionDsunte Wilson
?
Symantec Endpoint Protection is a comprehensive client-server solution that provides protection against malware on various devices including laptops, desktops, and servers. It combines virus and spyware protection, network threat protection, and proactive threat protection to address known and unknown vulnerabilities. Key features include real-time scanning, a firewall, intrusion prevention systems, and device control to prevent data leakage.Introduction to oracle primavera
Introduction to oracle primaveraDsunte Wilson
?
This three-day training course covers the fundamentals of using Oracle Primavera, including the project management lifecycle, navigating and customizing layouts, creating projects and work breakdown structures, scheduling activities with relationships and constraints, assigning resources and costs, optimizing and baselining project plans, tracking project execution, and reporting performance. Topics to be covered include the enterprise project structure, activity networking, resource leveling, baseline tracking, progress updating, and creating project web sites.CCNA PPP and Frame Relay
CCNA PPP and Frame RelayDsunte Wilson
?
The document discusses PPP and Frame Relay networking fundamentals. It describes how PPP provides encapsulation and authentication over various physical interfaces. Frame Relay uses virtual circuits identified by DLCI numbers to transmit data over WAN links. Routers establish Frame Relay maps using Inverse ARP or static configuration to associate remote IP addresses with DLCIs. The document provides instructions for configuring PPP and Frame Relay on Cisco routers.CCNA Access Lists
CCNA Access ListsDsunte Wilson
?
The document discusses access lists in Cisco networking. It describes how standard IP access lists filter based on source IP addresses while extended IP access lists can filter on source, destination, protocol and port. It provides examples of creating standard and extended IP access lists and applying them to interfaces to filter traffic. It also covers using access lists to restrict VTY line access and creating access lists using the Security Device Manager user interface.CCNA Network Services
CCNA Network ServicesDsunte Wilson
?
The document discusses network services including network address translation (NAT), Dynamic Host Configuration Protocol (DHCP), and Domain Name Services (DNS). It describes how NAT allows private IP addresses to access the internet using public IP addresses through static NAT, dynamic NAT, or port address translation (PAT). DHCP automatically assigns IP addresses to devices on a network, while DNS translates names to IP addresses. The document also discusses configuring these services on Cisco routers using both CLI commands and the Cisco Security Device Manager web tool.CCNA Advanced Switching
CCNA Advanced SwitchingDsunte Wilson
?
The document discusses advanced switching concepts including the Spanning Tree Protocol (STP), virtual LANs (VLANs), and the VLAN Trunking Protocol (VTP). STP builds a logical topology to prevent loops, elects a root bridge, and puts ports in different states. VLANs segment broadcast domains and provide benefits like security and flexibility. VTP manages VLAN configurations across trunk links within the same VTP domain.CCNA Router Startup and Configuration
CCNA Router Startup and ConfigurationDsunte Wilson
?
The document describes the startup process and configuration of Cisco routers. It explains that routers go through a boot process including hardware tests, loading the bootstrap and Cisco IOS. IP and routing can then be configured on interfaces. Connectivity can be tested using tools like ping, telnet and show commands. The document also covers topics like CDP, passwords, firmware and using SDM for security configurations.CCNA Router and IOS Basics
CCNA Router and IOS BasicsDsunte Wilson
?
The document discusses the basics of Cisco routers and the Cisco IOS. It describes the router user interface, including different access methods and configuration modes. It also covers router components, passwords, and the functions of ROM, flash memory, NVRAM, RAM and interfaces.SYMANTEC ENDPOINT PROTECTION Interfacing the SEPM with Protection Center
SYMANTEC ENDPOINT PROTECTION Interfacing the SEPM with Protection CenterDsunte Wilson
?
The document describes the integration and functionality of Symantec Endpoint Protection with Protection Center, allowing centralized management of Symantec products. It explains the setup and configuration of virtual and physical appliances and outlines the workflows available for managing endpoint tasks. Additionally, the document covers the user interface and configuration tasks within Protection Center, enhancing usability and management efficiency.CCNA Advanced Routing Protocols
CCNA Advanced Routing ProtocolsDsunte Wilson
?
This document summarizes key concepts about advanced routing protocols including classful and classless protocols, RIPv2, EIGRP, and OSPF. It describes how classful protocols like RIPv1 summarize networks based on major boundaries and cannot be used with VLSM, while classless protocols carry subnet mask information and allow routing in discontiguous networks. It provides details on configuring and components of RIPv2, EIGRP, and OSPF such as authentication, metrics, neighbor discovery, and link-state advertisements.CCNA Network Devices
CCNA Network DevicesDsunte Wilson
?
This document summarizes network devices and concepts from a CCNA guide. It describes how repeaters, hubs, wireless access points, bridges, switches and routers segment networks and control traffic. It also defines Ethernet, Fast Ethernet and Gigabit Ethernet standards, and explains half and full-duplex communication modes. The summary provides an overview of common network devices and technologies for local area networks.CCNA TCP/IP
CCNA TCP/IPDsunte Wilson
?
The document summarizes key concepts about TCP/IP from Chapter 3 of a CCNA guide. It discusses the origins of TCP/IP from projects by DARPA and the inclusion of TCP/IP in UNIX. It also describes the four layers of the TCP/IP model including the application, transport, internet, and network interface layers. Finally, it provides an overview of common protocols at each layer such as TCP, UDP, IP, ARP, and how packets are transmitted between hosts and routers.CCNA Routing Protocols
CCNA Routing ProtocolsDsunte Wilson
?
The document discusses routing protocols and summarizes:
- It differentiates between nonroutable, routed, and routing protocols and describes common examples like NetBEUI and TCP/IP.
- It explains interior and exterior gateway protocols and the two types of interior gateway protocols: distance-vector and link-state routing protocols.
- It provides details on RIP, a common distance-vector protocol, including how to enable and configure it.CCNA IP Addressing
CCNA IP AddressingDsunte Wilson
?
This document provides an overview of IP addressing concepts including:
- The structure of IP addresses including classes, subnet masking, and CIDR
- Techniques for subnetting networks and creating more subnets and hosts including VLSM
- The transition from IPv4 to IPv6 to address the limited address space of IPv4CCNA Basic Switching and Switch Configuration
CCNA Basic Switching and Switch ConfigurationDsunte Wilson
?
This document provides an overview of basic switching concepts and Cisco switch configuration. It explains Ethernet and how switches work to segment networks and reduce collisions. Switches operate at the data link layer and learn MAC addresses to forward frames efficiently. The document discusses switch configuration using commands like hostname, interface, duplex, and port security. It compares switching methods like store-and-forward and cut-through forwarding. The summary reiterates how switches divide collision domains to improve performance over shared-medium Ethernet.E¦Ð¦Á¦Í¦Á¦Ë¦Ç¦Ð¦Ó¦É¦Ê?? ¦Á¦Ò¦Ê?¦Ò¦Å¦É? ¦Ã¦Ë?¦Ò¦Ò¦Á? 2¦Ç? ¦Å¦Í?¦Ó¦Ç¦Ó¦Á? "¦±?¦Ó¦Á ¦Ó¦Ï ¦Í¦Å¦Ñ? ¦Ó¦É ¦Ó¦Ñ?¦Ö¦Å¦É" ¦£¦Ë?¦Ò¦Ò...
E¦Ð¦Á¦Í¦Á¦Ë¦Ç¦Ð¦Ó¦É¦Ê?? ¦Á¦Ò¦Ê?¦Ò¦Å¦É? ¦Ã¦Ë?¦Ò¦Ò¦Á? 2¦Ç? ¦Å¦Í?¦Ó¦Ç¦Ó¦Á? "¦±?¦Ó¦Á ¦Ó¦Ï ¦Í¦Å¦Ñ? ¦Ó¦É ¦Ó¦Ñ?¦Ö¦Å¦É" ¦£¦Ë?¦Ò¦Ò...¦§¦Ë¦É?¦Ä¦Ç? ¦§¦Ë?¦Á?
?
¦¥¦Ð¦Á¦Í¦Á¦Ë¦Ç¦Ð¦Ó¦É¦Ê?? ¦Á¦Ò¦Ê?¦Ò¦Å¦É? ¦Ã¦Ë?¦Ò¦Ò¦Á? 2¦Ç? ¦Å¦Í?¦Ó¦Ç¦Ó¦Á?
" ¦±?¦Ó¦Á ¦Ó¦Ï ¦Í¦Å¦Ñ? ¦Ó¦É ¦Ó¦Ñ?¦Ö¦Å¦É" ¦£¦Ë?¦Ò¦Ò¦Á ¦¤?
¦°¦Ç¦Ã?: e- selidesE¦Ð¦Á¦Í¦Á¦Ë¦Ç¦Ð¦Ó¦É¦Ê?? ¦Á¦Ò¦Ê?¦Ò¦Å¦É? ¦Ã¦Ë?¦Ò¦Ò¦Á? 2¦Ç? ¦Å¦Í?¦Ó¦Ç¦Ó¦Á? "¦±?¦Ó¦Á ¦Ó¦Ï ¦Í¦Å¦Ñ? ¦Ó¦É ¦Ó¦Ñ?¦Ö¦Å¦É" ¦£¦Ë?¦Ò¦Ò...
E¦Ð¦Á¦Í¦Á¦Ë¦Ç¦Ð¦Ó¦É¦Ê?? ¦Á¦Ò¦Ê?¦Ò¦Å¦É? ¦Ã¦Ë?¦Ò¦Ò¦Á? 2¦Ç? ¦Å¦Í?¦Ó¦Ç¦Ó¦Á? "¦±?¦Ó¦Á ¦Ó¦Ï ¦Í¦Å¦Ñ? ¦Ó¦É ¦Ó¦Ñ?¦Ö¦Å¦É" ¦£¦Ë?¦Ò¦Ò...¦§¦Ë¦É?¦Ä¦Ç? ¦§¦Ë?¦Á?
?
More from Sakis Karakousis (6)
Hellenic educational system
Hellenic educational systemSakis Karakousis
?
The document summarizes the structure of the Greek educational system and provides details about the 1st EPAL Katerinis vocational high school. It notes that primary education spans grades 1-6, lower secondary 7-9, and upper secondary 10-12. The school has 550 students and 80 teachers across 30 classrooms, laboratories, and other facilities. Students choose between sectors like mechanical, electrical, or information technology in grade 2, and further specialize in grade 3. The information technology sector prepares students for jobs supporting IT systems. The school offers programs to improve vocational training and students can participate in activities and exhibitions.¦Ò?¦Ã¦Ö¦Ñ¦Ï¦Í¦Å? ¦Ì?¦È¦Ï¦Ä¦Ï¦É ¦Ä¦É¦Ä¦Á¦Ò¦Ê¦Á¦Ë?¦Á? Karakousis athanasios
¦Ò?¦Ã¦Ö¦Ñ¦Ï¦Í¦Å? ¦Ì?¦È¦Ï¦Ä¦Ï¦É ¦Ä¦É¦Ä¦Á¦Ò¦Ê¦Á¦Ë?¦Á? Karakousis athanasiosSakis Karakousis
?
¦²?¦Ã¦Ö¦Ñ¦Ï¦Í¦Å? ¦Ä¦É¦Ä¦Á¦Ê¦Ó¦É¦Ê?? ¦Ð¦Ñ¦Ï¦Ò¦Å¦Ã¦Ã?¦Ò¦Å¦É? ¦Ã¦É¦Á ¦Ó¦Ç¦Í ¦Á¦Í?¦Ð¦Ó¦Ô¦Î¦Ç ¦Ê¦Ñ¦É¦Ó¦É¦Ê??-¦Ä¦Ç¦Ì¦É¦Ï¦Ô¦Ñ¦Ã¦É¦Ê?? ¦Ò¦Ê?¦×¦Ç?
¦¥¦µ¦¡¦±¦¬¦¯¦£¦§ EFQM MODEL ¦²¦³¦§¦ ¦¥¦ª¦°¦¡¦©¦¤¦¥¦´¦²¦§
¦¥¦µ¦¡¦±¦¬¦¯¦£¦§ EFQM MODEL ¦²¦³¦§¦ ¦¥¦ª¦°¦¡¦©¦¤¦¥¦´¦²¦§Sakis Karakousis
?
¦¥¦µ¦¡¦±¦¬¦¯¦£¦§ EFQM MODEL ¦²¦³¦§¦ ¦¥¦ª¦°¦¡¦©¦¤¦¥¦´¦²¦§
¦°¦¯¦©¦¯¦³¦§¦³¦¡ ¦ª¦¡¦© ¦¥¦ª¦°¦¡¦©¦¤¦¥¦´¦²¦§ H ¦¡¦Ò¦Õ?¦Ë¦Å¦É¦Á ¦Ò¦Ó¦Ï ¦¤¦É¦Á¦Ä?¦Ê¦Ó¦Ô¦Ï ¦Ê¦Á¦É ¦Ò¦Ó¦É? ¦Í?¦Å? ¦Ó¦Å¦Ö¦Í¦Ï¦Ë¦Ï¦Ã?¦Å?
H ¦¡¦Ò¦Õ?¦Ë¦Å¦É¦Á ¦Ò¦Ó¦Ï ¦¤¦É¦Á¦Ä?¦Ê¦Ó¦Ô¦Ï ¦Ê¦Á¦É ¦Ò¦Ó¦É? ¦Í?¦Å? ¦Ó¦Å¦Ö¦Í¦Ï¦Ë¦Ï¦Ã?¦Å?Sakis Karakousis
?
H ¦Á¦Ò¦Õ?¦Ë¦Å¦É¦Á ¦Ò¦Ó¦Ï ¦Ä¦É¦Á¦Ä?¦Ê¦Ó¦Ô¦Ï ¦Ê¦Á¦É ¦Ò¦Ó¦É? ¦Í?¦Å? ¦Ó¦Å¦Ö¦Í¦Ï¦Ë¦Ï¦Ã?¦Å? - H ¦¡¦Ò¦Õ?¦Ë¦Å¦É¦Á ¦Ò¦Ó¦Ï ¦¤¦É¦Á¦Ä?¦Ê¦Ó¦Ô¦Ï ¦Ê¦Á¦É ¦Ò¦Ó¦É? ¦Í?¦Å? ¦Ó¦Å¦Ö¦Í¦Ï¦Ë¦Ï¦Ã?¦Å?
H ¦¡¦Ò¦Õ?¦Ë¦Å¦É¦Á ¦Ò¦Ó¦Ï ¦¤¦É¦Á¦Ä?¦Ê¦Ó¦Ô¦Ï ¦Ê¦Á¦É ¦Ò¦Ó¦É? ¦Í?¦Å? ¦Ó¦Å¦Ö¦Í¦Ï¦Ë¦Ï¦Ã?¦Å?Sakis Karakousis
?
Ad
Recently uploaded (20)
CBUSDAW - Ash Lewis - Reducing LLM Hallucinations
CBUSDAW - Ash Lewis - Reducing LLM HallucinationsJason Packer
?
Columbus Data & Analytics Wednesdays, June 2025 with Ashley Lewis. A field guide to reducing LLM hallucinations.Unlocking Business Growth Through Targeted Social Engagement
Unlocking Business Growth Through Targeted Social EngagementDigital Guider
?
Facebook marketing allows businesses to connect with their ideal audience through precise targeting and engaging content. By leveraging advanced tools like custom audiences, Facebook Ads, and real-time analytics, brands can build strong relationships, increase visibility, and drive measurable results. It¡¯s not just about reaching people¡ªit¡¯s about reaching the right people and turning engagement into growth.
https://digitalguider.com/digital-advertising/facebook-advertising-services/
Timeline Infographics Para utiliza??o di¨¢ria
Timeline Infographics Para utiliza??o di¨¢riameslellis
?
Infografico com um tema bem interessante para ser utilizadorosoft PowcgnggerPoint Presentation.pptx
rosoft PowcgnggerPoint Presentation.pptxsirbabu778
?
rosoft PowcgnggerPoint Presentation.pptxrosoft PowcgnggerPoint Presentation.pptxrosoft PowcgnggerPoint Presentation.pptxcybercrime investigation and digital forensics
cybercrime investigation and digital forensicsgoverdhankumar137300
?
cybercrime investigation and digital forensics Dark Web Presentation - 1.pdf about internet which will help you to get to kn...
Dark Web Presentation - 1.pdf about internet which will help you to get to kn...ragnaralpha7199
?
Dark web inside the internet - understanding the TCP/IP protocol
inside the internet - understanding the TCP/IP protocolshainweniton02
?
Key factors on TCP/IP protocolDDos Mitigation Strategie, presented at bdNOG 19
DDos Mitigation Strategie, presented at bdNOG 19APNIC
?
Awal Haolader, Network Analyst / Technical Trainer at APNIC, presented on 'DDoS Mitigation Strategies' at bdNOG 19 held in Dhaka, Bangladesh from 21 to 24 May 2025.×îаæÃÀ¹úÍþ˹¿µÐÇ´óѧÂÌÍå·ÖУ±ÏÒµÖ¤£¨±«°Â³Òµþ±ÏÒµÖ¤Ê飩԰涨ÖÆ
×îаæÃÀ¹úÍþ˹¿µÐÇ´óѧÂÌÍå·ÖУ±ÏÒµÖ¤£¨±«°Â³Òµþ±ÏÒµÖ¤Ê飩԰涨ÖÆTaqyea
?
¼øÓÚ´Ë£¬¶¨ÖÆÍþ˹¿µÐÇ´óѧÂÌÍå·ÖУѧλ֤ÊéÌáÉýÂÄÀú¡¾qÞ±1954292140¡¿Ô°æ¸ß·ÂÍþ˹¿µÐÇ´óѧÂÌÍå·ÖУ±ÏÒµÖ¤(UWGB±ÏÒµÖ¤Êé)¿ÉÏÈ¿´³ÉÆ·Ñù±¾¡¾qÞ±1954292140¡¿°ïÄú½â¾öÔÚÃÀ¹úÍþ˹¿µÐÇ´óѧÂÌÍå·ÖУδ±ÏÒµÄÑÌ⣬ÃÀ¹ú±ÏÒµÖ¤¹ºÂò£¬ÃÀ¹úÎÄƾ¹ºÂò£¬¡¾q΢1954292140¡¿ÃÀ¹úÎÄƾ¹ºÂò£¬ÃÀ¹úÎÄƾ¶¨ÖÆ£¬ÃÀ¹úÎÄƾ²¹°ì¡£×¨ÒµÔÚÏ߶¨ÖÆÃÀ¹ú´óѧÎÄƾ£¬¶¨×öÃÀ¹ú±¾¿ÆÎÄƾ£¬¡¾q΢1954292140¡¿¸´ÖÆÃÀ¹úUniversity of Wisconsin-Green Bay completion letter¡£ÔÚÏß¿ìËÙ²¹°ìÃÀ¹ú±¾¿Æ±ÏÒµÖ¤¡¢Ë¶Ê¿ÎÄƾ֤Ê飬¹ºÂòÃÀ¹úѧλ֤¡¢Íþ˹¿µÐÇ´óѧÂÌÍå·ÖУOffer£¬ÃÀ¹ú´óѧÎÄƾÔÚÏß¹ºÂò¡£
Èç¹ûÄú´¦ÓÚÒÔϼ¸ÖÖÇé¿ö£º
¡óÔÚУÆڼ䣬Òò¸÷ÖÖÔÒòδÄÜ˳Àû±ÏÒµ¡¡Äò»µ½¹Ù·½±ÏÒµÖ¤
¡óÃæ¶Ô¸¸Ä¸µÄѹÁ¦£¬Ï£Íû¾¡¿ìÄõ½£»
¡ó²»Çå³þÈÏÖ¤Á÷³ÌÒÔ¼°²ÄÁϸÃÈçºÎ×¼±¸£»
¡ó»Ø¹úʱ¼äºÜ³¤£¬Íü¼Ç°ìÀí£»
¡ó»Ø¹úÂíÉϾÍÒªÕÒ¹¤×÷£¬°ì¸øÓÃÈ˵¥Î»¿´£»
¡óÆóÊÂÒµµ¥Î»±ØÐëÒªÇó°ìÀíµÄ
¡óÐèÒª±¨¿¼¹«ÎñÔ±¡¢¹ºÂòÃâË°³µ¡¢Âäת»§¿Ú
¡óÉêÇëÁôѧÉú´´Òµ»ù½ð
¡¾¸´¿ÌÒ»Ì×Íþ˹¿µÐÇ´óѧÂÌÍå·ÖУ±ÏÒµÖ¤³É¼¨µ¥ÐÅ·âµÈ²ÄÁÏ×îÇ¿¹¥ÂÔ,Buy University of Wisconsin-Green Bay Transcripts¡¿
¹ºÂòÈÕº«³É¼¨µ¥¡¢Ó¢¹ú´óѧ³É¼¨µ¥¡¢ÃÀ¹ú´óѧ³É¼¨µ¥¡¢°ÄÖÞ´óѧ³É¼¨µ¥¡¢¼ÓÄôó´óѧ³É¼¨µ¥£¨q΢1954292140£©Ð¼ÓÆ´óѧ³É¼¨µ¥¡¢ÐÂÎ÷À¼´óѧ³É¼¨µ¥¡¢°®¶ûÀ¼³É¼¨µ¥¡¢Î÷°àÑÀ³É¼¨µ¥¡¢µÂ¹ú³É¼¨µ¥¡£³É¼¨µ¥µÄÒâÒåÖ÷ÒªÌåÏÖÔÚÖ¤Ã÷ѧϰÄÜÁ¦¡¢ÆÀ¹ÀѧÊõ±³¾°¡¢Õ¹Ê¾×ÛºÏËØÖÊ¡¢Ìá¸ß¼ȡÂÊ£¬ÒÔ¼°ÊÇ×÷ΪÁôÐÅÈÏÖ¤ÉêÇë²ÄÁϵÄÒ»²¿·Ö¡£
Íþ˹¿µÐÇ´óѧÂÌÍå·ÖУ³É¼¨µ¥Äܹ»ÌåÏÖÄúµÄµÄѧϰÄÜÁ¦£¬°üÀ¨Íþ˹¿µÐÇ´óѧÂÌÍå·ÖУ¿Î³Ì³É¼¨¡¢×¨ÒµÄÜÁ¦¡¢Ñо¿ÄÜÁ¦¡££¨q΢1954292140£©¾ßÌåÀ´Ëµ£¬³É¼¨±¨¸æµ¥Í¨³£°üº¬Ñ§ÉúµÄѧϰ¼¼ÄÜÓëÏ°¹ß¡¢¸÷¿Æ³É¼¨ÒÔ¼°ÀÏʦÆÀÓïµÈ²¿·Ö£¬Òò´Ë£¬³É¼¨µ¥²»½öÊÇѧÉúѧÊõÄÜÁ¦µÄÖ¤Ã÷£¬Ò²ÊÇÆÀ¹ÀѧÉúÊÇ·ñÊʺÏij¸ö½ÌÓýÏîÄ¿µÄÖØÒªÒÀ¾Ý£¡3 years of Quarkus in production, what have we learned - Devoxx Polen
3 years of Quarkus in production, what have we learned - Devoxx PolenJago de Vreede
?
Quarkus has grown in popularity in the last years, but what¡¯s it really like to use it in large-scale, real-world business projects? In this session, we¡¯ll move beyond the basics of "Hello World" to explore how to build enterprise-level applications with Quarkus efficiently.
In this talk we will set up a multi-module project, incorporating integration tests and addressing the challenges with build times, while maintaining a high development velocity. Next, we¡¯ll tackle an upgrade scenario and splitting the application into multiple microservices. Along the way, we¡¯ll share hard-earned lessons, including what to avoid.
At the end of the talk, you should have a good understanding of how to efficiently set up a ¡°big¡± enterprise project with Quarkus and the confidence to get started.
Expository Text Translation WEASDSD.pptx
Expository Text Translation WEASDSD.pptxSURYAADIWINATA3
?
ASDFSEFSDFFSDFAFAFSAFAFSFERAF GRGCFAGARGRAGFDGACommon Pitfalls in Magento to Shopify Migration and How to Avoid Them.pdf
Common Pitfalls in Magento to Shopify Migration and How to Avoid Them.pdfCartCoders
?
Planning to migrate from Magento to Shopify? CartCoders offers reliable and error-free Magento to Shopify migration services, ensuring your store data, design, and SEO remain intact. Get expert migration with zero data loss and minimal downtime.Ad
