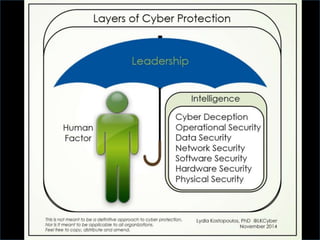
Layers of Cyber Protection
Download as pptx, pdf0 likes280 views
This is meant to illustrate one perspective of layers of cyber protection and not meant to be a definitive approach to cyber protection, nor is it meant to be applicable to all organizations. Feel free to copy, distribute and amend.
1 of 1
Downloaded 10 times
Ad
Recommended
Securing the C-Suite: Cybersecurity Perspectives from the Boardroom
Securing the C-Suite: Cybersecurity Perspectives from the BoardroomIBM Security
?
The document summarizes the findings of a survey of over 700 C-suite executives from 29 countries and 18 industries regarding their perspectives on cybersecurity. Some key findings include: 75% of CxOs believe a comprehensive cybersecurity program is important; however, over half may be overstating the likelihood of a significant cybersecurity incident. Additionally, while CxOs acknowledge some risks, they understate risks from insiders and overstate risks from external threats. The C-suites were clustered into three groups based on their cybersecurity effectiveness: not prepared, progressing, and cybersecure. The cybersecure C-suites were more likely to have robust cybersecurity governance and collaboration.Beyond Lifeguards Layers of Protection
Beyond Lifeguards Layers of ProtectionSuncoastMeetings
?
Beyond Lifeguards outlines layers of protection for preventing drownings, including lifeguards, codes of conduct, and changing behaviors. It discusses the need for lifeguards to be rescue ready, positioned to protect, and focused on safety by actively scanning water areas. The presentation advocates stopping the practice of asking lifeguards to look for drowning victims and instead emphasizes multiple protective layers through codes and empowering lifeguards.New York State Department of Financial Services Expands Its Cyber Focus to In...
New York State Department of Financial Services Expands Its Cyber Focus to In...NationalUnderwriter
?
The New York State Department of Financial Services (DFS) is expanding its cybersecurity requirements for insurers, mandating a comprehensive risk assessment related to cybersecurity practices. This assessment includes questions on governance, data protection, vendor management, and adherence to established cybersecurity frameworks, with responses due by April 27. Although not enforcing specific standards, DFS's inquiries imply best practices and could lead to enforcement actions based on insurers' responses.C-Suite Guide to Cybersecurity
C-Suite Guide to CybersecurityMICHAEL MOSHIRI
?
The document is a C-suite guide to cybersecurity, emphasizing the importance of understanding and managing cyber risks for executives. It outlines five key principles for effective cybersecurity: identifying risks, protecting critical assets, detecting deviations from normal activity, responding rapidly to security incidents, and continuously assessing risks. The guide highlights the increasing frequency and cost of security breaches, urging leaders to implement industry-standard frameworks and controls to safeguard their organizations.cybersecurity-in-the-c-suite-a-matt
cybersecurity-in-the-c-suite-a-mattYigal Behar
?
Cybersecurity risks affect all senior executives in an organization. While the CEO may want to delegate cybersecurity to the CTO, effective programs require input from multiple stakeholders. A comprehensive understanding of technical, financial, and regulatory risks is needed to develop an appropriate strategy. Regular communication to the CEO should focus on trends, risks, and major incidents rather than technical details. Quantifying potential financial losses from data breaches can help obtain support for necessary security investments.New York DFS proposed cybersecurity regulations
New York DFS proposed cybersecurity regulationsBrunswick Group
?
The proposed cybersecurity regulations from the New York Department of Financial Services would impose significant new compliance responsibilities on over 4,000 financial institutions in New York. The regulations set the most prescriptive standards among any state or federal agency and would require companies to establish comprehensive cybersecurity programs, designate cybersecurity personnel, and report any cyber incidents within 72 hours. The regulations have major implications for communications professionals in developing robust cybersecurity response plans, preparing for potential leaks, and ensuring effective employee training on cybersecurity awareness.NYS DFS CyberSecurity Regulations
NYS DFS CyberSecurity RegulationsJon Bosco
?
The document outlines the New York Department of Financial Services (NYDFS) cybersecurity regulations, detailing requirements for financial services entities to establish robust cybersecurity programs. Key elements include risk assessments, multi-factor authentication, the appointment of a Chief Information Security Officer (CISO), and strict incident reporting protocols. It also specifies exemptions for smaller entities and emphasizes the importance of comprehensive cybersecurity policies and third-party vendor practices.Improving Cyber Security Literacy in Boards & Executives
Improving Cyber Security Literacy in Boards & ExecutivesTripwire
?
The document discusses the importance of enhancing cyber security literacy among boards and executives, suggesting that cyber issues should be integrated into business decision-making processes. It emphasizes the necessity for senior level representation from information security and the need for organizations to adopt multiple frameworks to effectively assess security. Additionally, it highlights that understanding future threats requires a shift in mindset for security professionals, advocating for innovative communication strategies with executives to address evolving risks.Security Onion: peeling back the layers of your network in minutes
Security Onion: peeling back the layers of your network in minutesbsidesaugusta
?
Security Onion is a Linux distribution for intrusion detection and network security monitoring. It contains tools like Snort, Suricata, Bro, Sguil and more. The easy setup wizard allows users to quickly build a distributed sensor network. It provides alerts, asset data, network sessions and full packet captures from multiple data sources in a centralized interface for analysis and pivoting to packet captures. The project has seen over 30,000 downloads and provides ongoing support through its website and mailing lists.Future of Cybersecurity 2016 - M.Rosenquist
Future of Cybersecurity 2016 - M.RosenquistMatthew Rosenquist
?
The document outlines cybersecurity predictions for 2016, emphasizing the expanding role of governments, the intersection of life safety and cybersecurity, and the increasing expectations from enterprises and consumers. It highlights how attackers are evolving, the rising costs of cybersecurity, and the growing challenges posed by a lack of security talent in the industry. Overall, it stresses the need for organizations to adapt strategically to emerging cyber threats and risks.Privacy & Data Protection in the Digital World
Privacy & Data Protection in the Digital WorldArab Federation for Digital Economy
?
The document discusses the importance of data privacy and protection, outlining its significance in the context of the UAE's initiatives to enhance personal identity management. It emphasizes the potential risks and legal frameworks surrounding data privacy, while highlighting the role of government and organizations in upholding these protections. The conclusion reflects on the evolving nature of data security in light of technological advancements and the need for continued regulation and awareness.How to Raise Cyber Risk Awareness and Management to the C-Suite
How to Raise Cyber Risk Awareness and Management to the C-SuiteSurfWatch Labs
?
The document discusses the need for the C-suite to prioritize cybersecurity as part of their business strategy, emphasizing that neglecting cybersecurity can lead to severe consequences. It highlights the rising costs associated with cyber breaches and the importance of tracking cyber risks through key performance indicators. Additionally, it suggests adopting a business intelligence approach to improve communication and decision-making about cybersecurity within organizations.Securing the Cloud by Matthew Rosenquist 2016
Securing the Cloud by Matthew Rosenquist 2016Matthew Rosenquist
?
The document discusses the advantages and risks of cloud architecture and services, emphasizing their cost-effectiveness, flexibility, and proximity to customers while also highlighting security, privacy, and operational challenges. It outlines key security measures such as identity and access management, data loss prevention, and the importance of early engagement with security experts in adopting cloud solutions. The conclusion stresses the need for accountability, ethical adherence, and proactive planning to ensure beneficial utilization of cloud technologies.CSE 2016 Future of Cyber Security by Matthew Rosenquist
CSE 2016 Future of Cyber Security by Matthew RosenquistMatthew Rosenquist
?
The conference discussed the evolving landscape of cybersecurity, emphasizing the convergence of physical and cyber security as critical for addressing emerging risks. It highlighted the increase in cyber threats and the importance of leadership in navigating the challenges posed by innovations such as IoT devices. Additionally, the document pointed out the significant talent shortages in the cybersecurity sector, which hinder effective responses to these escalating threats.NIST Cybersecurity Framework Intro for ISACA Richmond Chapter
NIST Cybersecurity Framework Intro for ISACA Richmond ChapterTuan Phan
?
Trusted Integration, Inc. is an Alexandria-based cybersecurity company founded in 2001 that focuses on creating adaptive and cost-effective governance, risk, and compliance solutions. The company received Golden Bridge awards in 2013 for its government compliance and governance, risk, and compliance solutions. The document then provides an overview of the NIST Cybersecurity Framework, including its goals to improve cybersecurity risk management, be flexible and repeatable, and focus on outcomes. It describes the framework's core, profiles, and implementation tiers and maps the framework to other standards like ISO 27001. [END SUMMARY]Top 10 cybersecurity predictions for 2016 by Matthew Rosenquist
Top 10 cybersecurity predictions for 2016 by Matthew RosenquistMatthew Rosenquist
?
1. The document outlines 10 predictions for cybersecurity challenges in 2016 and beyond, including the expanding roles of governments, continued evolution of nation-state cyber offenses, and the intersection of life safety and cybersecurity in connected devices.
2. It predicts security expectations will increase while security technologies improve but remain outpaced by adaptable attackers. Attacks targeting trust and integrity will escalate.
3. A continued lack of cybersecurity talent will hinder the industry from effectively addressing evolving threats. New threat vectors are expected to emerge as technologies advance.Cyber Security
Cyber SecurityNeha Gupta
?
Cybersecurity involves securing information systems and networks through ensuring availability, integrity and confidentiality of data. The goal is to protect operations and assets from attacks, accidents and failures. It is important to learn cybersecurity as information systems and networks are vulnerable, and understanding security measures can help protect against cyber crimes and their consequences.Introduction to NIST Cybersecurity Framework
Introduction to NIST Cybersecurity FrameworkTuan Phan
?
This document provides an introduction to the NIST Cybersecurity Framework. It discusses the goals and key parts of the Framework, including the Framework Core with its functions, categories and subcategories. It also covers the Framework Profile and Implementation Tiers. The document then demonstrates how Trusted Integration's software maps to the Framework and can be used to assess an organization's cybersecurity activities.Cyber Security 2017 Challenges
Cyber Security 2017 ChallengesLeandro Bennaton
?
Leandro Bennaton, an expert in cybersecurity, highlights the critical challenges and concerns related to cyber risks in 2017. He discusses the importance of a comprehensive approach to cybersecurity, including threat detection and response strategies. Bennaton emphasizes the value of open-source intelligence and various tools to prevent, identify, and mitigate cyber threats.How to Approach the NYDFS Proposed Cybersecurity Requirements
How to Approach the NYDFS Proposed Cybersecurity RequirementsKyle Brown
?
The document outlines the New York Department of Financial Services' cybersecurity regulations, emphasizing the need for compliance among financial institutions to mitigate risks associated with data breaches and cyber threats. It highlights key requirements for cybersecurity programs, including risk identification, protection of nonpublic information, and employee training. Additionally, it underscores the importance of a compliance culture and the use of industry best practices in managing cybersecurity effectively.Cyber crime ppt
Cyber crime pptMOE515253
?
Cyber crime is a growing problem in India. Some common cyber crimes reported in India include phishing, hacking of government websites, and identity theft. India ranks 11th globally for reported cyber crimes, which are increasing due to factors like rapid growth of internet users. Common cyber crimes involve unauthorized access to systems, data theft and alteration, and using computers to enable other illicit activities. While laws like the IT Act 2000 have been enacted to tackle cyber crimes, enforcement remains a challenge as only a small percentage of crimes are reported. Techniques like antivirus software, firewalls, and educating users can help address the problem.FFCOI Imagination Dilemma Presentation
FFCOI Imagination Dilemma Presentationlkcyber
?
This presentation includes selected highlights from the book "Imagination Dilemma: tools to overcome it and thrive through disruption" and was delivered to the US Federal Foresight Community of Interest on February 20th, 2025.
It covers how to think in an era of exponentiality, the technology butterfly effects, why reimagining our identity is so critical and the imagination telescope. Workshop: Your Imagination is worth more than you imagine
Workshop: Your Imagination is worth more than you imaginelkcyber
?
The document presents a workshop by Dr. Lydia Kostopoulos on exposure therapy, focusing on the facets of imagination, mindset, and the challenges posed by exponential change and polycrisis. It discusses the need for innovative thinking in various sectors, including digital economy, construction, and environmental sustainability. The workshop aims to enhance understanding of imagination as a driving force for future opportunities and solutions.Versatility at the Tip of the Spear: Food Security and the Utility of SOF
Versatility at the Tip of the Spear: Food Security and the Utility of SOFlkcyber
?
The document discusses the critical role of food security as a core issue of global conflict exacerbated by current events such as the Russo-Ukrainian war and climate change. It emphasizes the unique capabilities of Special Operations Forces (SOF) in addressing food insecurity, particularly through unconventional warfare and local partnerships. The authors argue for a comprehensive strategy that integrates military, diplomatic, and economic approaches to tackle the compound security dilemmas impacting food systems worldwide.The Corporate Social Responsibility of Artificial Intelligence
The Corporate Social Responsibility of Artificial Intelligencelkcyber
?
Lydia Kostopoulos, PhD, is a senior strategy and emerging technologies advisor with extensive experience across various sectors, including consulting for organizations such as the UN and NATO. Her work includes exploring the intersection of artificial intelligence and corporate social responsibility, with a focus on mitigating risks such as misinformation and data bias. Additionally, she leads the Nof1 longevity project, showcasing individual journeys toward longevity.The Longevity Dividend: What advancements in longevity science mean for indiv...
The Longevity Dividend: What advancements in longevity science mean for indiv...lkcyber
?
The document discusses advancements in longevity science and their implications for individuals, society, the economy, and the military, emphasizing the potential for significant improvements in healthspan and the economic benefits of addressing chronic diseases. It highlights the urgent need for policy changes to support longevity research and market development, including the identification of aging as a disease. Dr. Lydia Kostopoulos presents the notion of a 'longevity dividend,' advocating for proactive measures and innovative technologies to enhance human prosperity and well-being.Letter from the Frontline in 2050
Letter from the Frontline in 2050lkcyber
?
In the fictional story set in 2050, a member of a secret U.S. military unit reflects on a high-stakes mission to thwart the advances of a rogue nation, Norak, known for acquiring dangerous AI technologies. The narrative reveals the use of cutting-edge enhancements, including genetic modifications and advanced communication technologies, which give the soldiers unique capabilities in their operations. As the protagonist navigates through perilous scenarios in an attempt to destroy an AI lab and save a kidnapped scientist, she uncovers the evolution of warfare in a world where technology and biology intersect.Concept: Metaverse Center for Women's Human Performance, Healthy Aging and Lo...
Concept: Metaverse Center for Women's Human Performance, Healthy Aging and Lo...lkcyber
?
The document proposes the concept of a Metaverse Center for Women's Human Performance, Healthy Aging & Longevity. It identifies modern life challenges to healthy aging and human performance as a problem. The proposed solution is a revenue-generating metaverse center that offers wellness programs, partnerships, and a marketplace utilizing web3 technologies like NFTs, DAOs, and digital twins to track user health data. The goal is to create a global community dedicated to helping women optimize health and longevity through the lens of human performance.Imagination Performance: Thinking Beyond GPT
Imagination Performance: Thinking Beyond GPT lkcyber
?
The document discusses the concept of 'imagination performance' in the context of an exponential mindset and the impact of technology on business and human identity. It emphasizes the need for individuals and organizations to adapt creatively and empathetically in a rapidly changing environment shaped by digital technologies. Additionally, it highlights the importance of cultural fluency and authentic connections in a world abundant in information yet lacking in meaningful engagement.Decoupling Human Characteristics from Algorithmic Capabilities
Decoupling Human Characteristics from Algorithmic Capabilitieslkcyber
?
Dr. Lydia Kostopoulos addresses the need to decouple human characteristics from algorithmic capabilities, emphasizing the importance of understanding the limitations of AI systems. She warns against anthropomorphic biases that could misrepresent AI's potential and advocates for maintaining human autonomy in decision-making. The discussion aims to foster better communication regarding AI's capabilities and risks, promoting a dialogue on how technology should enhance rather than undermine human experience.More Related Content
Viewers also liked (13)
Security Onion: peeling back the layers of your network in minutes
Security Onion: peeling back the layers of your network in minutesbsidesaugusta
?
Security Onion is a Linux distribution for intrusion detection and network security monitoring. It contains tools like Snort, Suricata, Bro, Sguil and more. The easy setup wizard allows users to quickly build a distributed sensor network. It provides alerts, asset data, network sessions and full packet captures from multiple data sources in a centralized interface for analysis and pivoting to packet captures. The project has seen over 30,000 downloads and provides ongoing support through its website and mailing lists.Future of Cybersecurity 2016 - M.Rosenquist
Future of Cybersecurity 2016 - M.RosenquistMatthew Rosenquist
?
The document outlines cybersecurity predictions for 2016, emphasizing the expanding role of governments, the intersection of life safety and cybersecurity, and the increasing expectations from enterprises and consumers. It highlights how attackers are evolving, the rising costs of cybersecurity, and the growing challenges posed by a lack of security talent in the industry. Overall, it stresses the need for organizations to adapt strategically to emerging cyber threats and risks.Privacy & Data Protection in the Digital World
Privacy & Data Protection in the Digital WorldArab Federation for Digital Economy
?
The document discusses the importance of data privacy and protection, outlining its significance in the context of the UAE's initiatives to enhance personal identity management. It emphasizes the potential risks and legal frameworks surrounding data privacy, while highlighting the role of government and organizations in upholding these protections. The conclusion reflects on the evolving nature of data security in light of technological advancements and the need for continued regulation and awareness.How to Raise Cyber Risk Awareness and Management to the C-Suite
How to Raise Cyber Risk Awareness and Management to the C-SuiteSurfWatch Labs
?
The document discusses the need for the C-suite to prioritize cybersecurity as part of their business strategy, emphasizing that neglecting cybersecurity can lead to severe consequences. It highlights the rising costs associated with cyber breaches and the importance of tracking cyber risks through key performance indicators. Additionally, it suggests adopting a business intelligence approach to improve communication and decision-making about cybersecurity within organizations.Securing the Cloud by Matthew Rosenquist 2016
Securing the Cloud by Matthew Rosenquist 2016Matthew Rosenquist
?
The document discusses the advantages and risks of cloud architecture and services, emphasizing their cost-effectiveness, flexibility, and proximity to customers while also highlighting security, privacy, and operational challenges. It outlines key security measures such as identity and access management, data loss prevention, and the importance of early engagement with security experts in adopting cloud solutions. The conclusion stresses the need for accountability, ethical adherence, and proactive planning to ensure beneficial utilization of cloud technologies.CSE 2016 Future of Cyber Security by Matthew Rosenquist
CSE 2016 Future of Cyber Security by Matthew RosenquistMatthew Rosenquist
?
The conference discussed the evolving landscape of cybersecurity, emphasizing the convergence of physical and cyber security as critical for addressing emerging risks. It highlighted the increase in cyber threats and the importance of leadership in navigating the challenges posed by innovations such as IoT devices. Additionally, the document pointed out the significant talent shortages in the cybersecurity sector, which hinder effective responses to these escalating threats.NIST Cybersecurity Framework Intro for ISACA Richmond Chapter
NIST Cybersecurity Framework Intro for ISACA Richmond ChapterTuan Phan
?
Trusted Integration, Inc. is an Alexandria-based cybersecurity company founded in 2001 that focuses on creating adaptive and cost-effective governance, risk, and compliance solutions. The company received Golden Bridge awards in 2013 for its government compliance and governance, risk, and compliance solutions. The document then provides an overview of the NIST Cybersecurity Framework, including its goals to improve cybersecurity risk management, be flexible and repeatable, and focus on outcomes. It describes the framework's core, profiles, and implementation tiers and maps the framework to other standards like ISO 27001. [END SUMMARY]Top 10 cybersecurity predictions for 2016 by Matthew Rosenquist
Top 10 cybersecurity predictions for 2016 by Matthew RosenquistMatthew Rosenquist
?
1. The document outlines 10 predictions for cybersecurity challenges in 2016 and beyond, including the expanding roles of governments, continued evolution of nation-state cyber offenses, and the intersection of life safety and cybersecurity in connected devices.
2. It predicts security expectations will increase while security technologies improve but remain outpaced by adaptable attackers. Attacks targeting trust and integrity will escalate.
3. A continued lack of cybersecurity talent will hinder the industry from effectively addressing evolving threats. New threat vectors are expected to emerge as technologies advance.Cyber Security
Cyber SecurityNeha Gupta
?
Cybersecurity involves securing information systems and networks through ensuring availability, integrity and confidentiality of data. The goal is to protect operations and assets from attacks, accidents and failures. It is important to learn cybersecurity as information systems and networks are vulnerable, and understanding security measures can help protect against cyber crimes and their consequences.Introduction to NIST Cybersecurity Framework
Introduction to NIST Cybersecurity FrameworkTuan Phan
?
This document provides an introduction to the NIST Cybersecurity Framework. It discusses the goals and key parts of the Framework, including the Framework Core with its functions, categories and subcategories. It also covers the Framework Profile and Implementation Tiers. The document then demonstrates how Trusted Integration's software maps to the Framework and can be used to assess an organization's cybersecurity activities.Cyber Security 2017 Challenges
Cyber Security 2017 ChallengesLeandro Bennaton
?
Leandro Bennaton, an expert in cybersecurity, highlights the critical challenges and concerns related to cyber risks in 2017. He discusses the importance of a comprehensive approach to cybersecurity, including threat detection and response strategies. Bennaton emphasizes the value of open-source intelligence and various tools to prevent, identify, and mitigate cyber threats.How to Approach the NYDFS Proposed Cybersecurity Requirements
How to Approach the NYDFS Proposed Cybersecurity RequirementsKyle Brown
?
The document outlines the New York Department of Financial Services' cybersecurity regulations, emphasizing the need for compliance among financial institutions to mitigate risks associated with data breaches and cyber threats. It highlights key requirements for cybersecurity programs, including risk identification, protection of nonpublic information, and employee training. Additionally, it underscores the importance of a compliance culture and the use of industry best practices in managing cybersecurity effectively.Cyber crime ppt
Cyber crime pptMOE515253
?
Cyber crime is a growing problem in India. Some common cyber crimes reported in India include phishing, hacking of government websites, and identity theft. India ranks 11th globally for reported cyber crimes, which are increasing due to factors like rapid growth of internet users. Common cyber crimes involve unauthorized access to systems, data theft and alteration, and using computers to enable other illicit activities. While laws like the IT Act 2000 have been enacted to tackle cyber crimes, enforcement remains a challenge as only a small percentage of crimes are reported. Techniques like antivirus software, firewalls, and educating users can help address the problem.More from lkcyber (20)
FFCOI Imagination Dilemma Presentation
FFCOI Imagination Dilemma Presentationlkcyber
?
This presentation includes selected highlights from the book "Imagination Dilemma: tools to overcome it and thrive through disruption" and was delivered to the US Federal Foresight Community of Interest on February 20th, 2025.
It covers how to think in an era of exponentiality, the technology butterfly effects, why reimagining our identity is so critical and the imagination telescope. Workshop: Your Imagination is worth more than you imagine
Workshop: Your Imagination is worth more than you imaginelkcyber
?
The document presents a workshop by Dr. Lydia Kostopoulos on exposure therapy, focusing on the facets of imagination, mindset, and the challenges posed by exponential change and polycrisis. It discusses the need for innovative thinking in various sectors, including digital economy, construction, and environmental sustainability. The workshop aims to enhance understanding of imagination as a driving force for future opportunities and solutions.Versatility at the Tip of the Spear: Food Security and the Utility of SOF
Versatility at the Tip of the Spear: Food Security and the Utility of SOFlkcyber
?
The document discusses the critical role of food security as a core issue of global conflict exacerbated by current events such as the Russo-Ukrainian war and climate change. It emphasizes the unique capabilities of Special Operations Forces (SOF) in addressing food insecurity, particularly through unconventional warfare and local partnerships. The authors argue for a comprehensive strategy that integrates military, diplomatic, and economic approaches to tackle the compound security dilemmas impacting food systems worldwide.The Corporate Social Responsibility of Artificial Intelligence
The Corporate Social Responsibility of Artificial Intelligencelkcyber
?
Lydia Kostopoulos, PhD, is a senior strategy and emerging technologies advisor with extensive experience across various sectors, including consulting for organizations such as the UN and NATO. Her work includes exploring the intersection of artificial intelligence and corporate social responsibility, with a focus on mitigating risks such as misinformation and data bias. Additionally, she leads the Nof1 longevity project, showcasing individual journeys toward longevity.The Longevity Dividend: What advancements in longevity science mean for indiv...
The Longevity Dividend: What advancements in longevity science mean for indiv...lkcyber
?
The document discusses advancements in longevity science and their implications for individuals, society, the economy, and the military, emphasizing the potential for significant improvements in healthspan and the economic benefits of addressing chronic diseases. It highlights the urgent need for policy changes to support longevity research and market development, including the identification of aging as a disease. Dr. Lydia Kostopoulos presents the notion of a 'longevity dividend,' advocating for proactive measures and innovative technologies to enhance human prosperity and well-being.Letter from the Frontline in 2050
Letter from the Frontline in 2050lkcyber
?
In the fictional story set in 2050, a member of a secret U.S. military unit reflects on a high-stakes mission to thwart the advances of a rogue nation, Norak, known for acquiring dangerous AI technologies. The narrative reveals the use of cutting-edge enhancements, including genetic modifications and advanced communication technologies, which give the soldiers unique capabilities in their operations. As the protagonist navigates through perilous scenarios in an attempt to destroy an AI lab and save a kidnapped scientist, she uncovers the evolution of warfare in a world where technology and biology intersect.Concept: Metaverse Center for Women's Human Performance, Healthy Aging and Lo...
Concept: Metaverse Center for Women's Human Performance, Healthy Aging and Lo...lkcyber
?
The document proposes the concept of a Metaverse Center for Women's Human Performance, Healthy Aging & Longevity. It identifies modern life challenges to healthy aging and human performance as a problem. The proposed solution is a revenue-generating metaverse center that offers wellness programs, partnerships, and a marketplace utilizing web3 technologies like NFTs, DAOs, and digital twins to track user health data. The goal is to create a global community dedicated to helping women optimize health and longevity through the lens of human performance.Imagination Performance: Thinking Beyond GPT
Imagination Performance: Thinking Beyond GPT lkcyber
?
The document discusses the concept of 'imagination performance' in the context of an exponential mindset and the impact of technology on business and human identity. It emphasizes the need for individuals and organizations to adapt creatively and empathetically in a rapidly changing environment shaped by digital technologies. Additionally, it highlights the importance of cultural fluency and authentic connections in a world abundant in information yet lacking in meaningful engagement.Decoupling Human Characteristics from Algorithmic Capabilities
Decoupling Human Characteristics from Algorithmic Capabilitieslkcyber
?
Dr. Lydia Kostopoulos addresses the need to decouple human characteristics from algorithmic capabilities, emphasizing the importance of understanding the limitations of AI systems. She warns against anthropomorphic biases that could misrepresent AI's potential and advocates for maintaining human autonomy in decision-making. The discussion aims to foster better communication regarding AI's capabilities and risks, promoting a dialogue on how technology should enhance rather than undermine human experience.Micro Journaling - Intermediate Cycle Tracker
Micro Journaling - Intermediate Cycle Trackerlkcyber
?
The document introduces an intermediate cycle tracking tool designed by Lydia Kostopoulos, PhD, to help women better understand their menstrual experiences through journaling. It offers structured sections for tracking sleep, mood, body sensations, and food cravings. Additionally, it encourages documenting related factors like sleep quality and environmental data for a comprehensive view of their health across the menstrual cycle.Decoupling Human Characteristics from Algorithmic Capabilities
Decoupling Human Characteristics from Algorithmic Capabilitieslkcyber
?
The document discusses artificial intelligence with a focus on three key aspects: starting with data, the algorithmic purpose, and algorithmic development. It outlines the foundational elements necessary for creating effective AI systems. Additionally, it emphasizes the importance of these factors in the overall success of artificial intelligence projects.Strategic Foresight: Sense-making in an Era of Rapid Change
Strategic Foresight: Sense-making in an Era of Rapid Changelkcyber
?
The document discusses sense-making in a rapidly changing world, focusing on systems thinking and the implications of complex systems on innovation. It outlines the evolution of industrial eras, emphasizing the transition from the extraction model to localized creation using advanced technologies like AI and blockchain. Furthermore, it highlights macro-trends such as climate change and water scarcity, illustrating how these factors interconnect within societal systems.Technological Surrogacy & Predictive Powers
Technological Surrogacy & Predictive Powerslkcyber
?
This document discusses technological surrogacy and predictive powers. It notes that algorithmic analytics can act as an expanded form of cognitive surrogacy, augmentation, assistance and support through data processing and algorithmic knowledge representation. However, this can also reinforce bias. The document also discusses grappling with complex challenges when employing algorithms, including issues like machine vision obstruction, weather degradation and payload sensitivity. It argues that predictive power comes with ethical duties to control for algorithmic bias through quality control and human oversight. The document stresses the importance of transparency around the data and algorithms used to help ensure explainable algorithms.Humans over Hardware: Posturing SOF for the Future
Humans over Hardware: Posturing SOF for the Futurelkcyber
?
Dr. Lydia Kostopoulos discusses the future of Special Operations Forces (SOF) in the context of the 4th Industrial Revolution, emphasizing the need for innovation and adaptability in warfare. The document outlines the shifting landscapes of conflict, highlighting the importance of advanced technologies, new talent acquisition, and a collaborative mindset to face emerging challenges. It stresses that successful operations require a mix of SOF and non-SOF support, along with an evolving approach to talent management and technological integration.The Mindset to Thrive in Uncertain, Turbulent & Exponential Times
The Mindset to Thrive in Uncertain, Turbulent & Exponential Timeslkcyber
?
The document discusses the mindset required to thrive in uncertain and rapidly changing environments, emphasizing resilience, emotional stamina, and a proactive approach to lifelong learning. It outlines the impact of technological advancements and demographic shifts on job markets while advocating for adaptive strategies like moonshot thinking and embracing multidisciplinary approaches. Key concepts include understanding emerging trends, managing expectations, setting ambitious goals, and nurturing curiosity to foster innovation and personal growth.Leadx: Public-Private Partnership Exercise Handout
Leadx: Public-Private Partnership Exercise Handoutlkcyber
?
This document outlines an exercise for developing strategic plans for public-private partnerships. The exercise was created by Dr. Lydia Kostopoulos and aims to help participants identify collaborative partnerships that could benefit their industry and country. Participants are prompted to list goals and key stakeholders, map stakeholder relationships, and draft timelines for engaging stakeholders including potential meeting dates, venues, and agendas. They are also asked to identify initial tasks to begin establishing the partnerships when returning to their home countries.Due Diligence Considerations for Scientists, Commanders, and Politicians As T...
Due Diligence Considerations for Scientists, Commanders, and Politicians As T...lkcyber
?
Dr. Lydia Kostopoulos discusses the implications of artificial intelligence in defense and security, emphasizing the need for due diligence, quality control, and human involvement in decision-making processes. She highlights challenges such as algorithmic bias, over-confidence in data solutions, and the potential hollowing out of human agency in lethal autonomous weapons systems. The presentation, made to the UN, calls for thoughtful conversations about the responsible implementation and oversight of emerging technologies.Part IV: Workwear Fashion, Human Anatomy, Transparency & Technology
Part IV: Workwear Fashion, Human Anatomy, Transparency & Technologylkcyber
?
This presentation discusses Lydia Kostopoulos's journey from her career in national security to founding a women's workwear company called Empowering Workwear by Lydia. The presentation is divided into four parts: 1) analyzing workwear fashion through the lens of human anatomy, 2) the importance of supply chain transparency for consumers and brands, 3) new technologies in the fashion industry, and 4) introducing Empowering Workwear by Lydia, which aims to provide functional, transparently sourced clothing that empowers women and encourages change in the industry. Kostopoulos draws from her experience in national security, technology, and education to create a purpose-driven business focused on empowering women through thoughtfulPart III: Workwear Fashion, Human Anatomy, Transparency & Technology
Part III: Workwear Fashion, Human Anatomy, Transparency & Technologylkcyber
?
The document outlines Dr. Lydia Kostopoulos's exploration of functional women's workwear by integrating workwear fashion with human anatomy, supply chain transparency, and technological advancements. It highlights various new fashion technologies such as 3D printing, biodegradable fabrics, and blockchain for enhancing transparency and sustainability in the fashion industry. Dr. Kostopoulos's background in national security and her fashion label, 'Empowering Workwear by Lydia,' underscores her unique perspective on the intersection of fashion and technology.Part II: Workwear Fashion, Human Anatomy, Transparency & Technology
Part II: Workwear Fashion, Human Anatomy, Transparency & Technologylkcyber
?
The document presents a multifaceted examination of women's workwear, focusing on the intersection of fashion, human anatomy, and technology as discussed by Dr. Lydia Kostopoulos. It emphasizes the necessity for supply chain transparency and the ethical responsibilities of brands, while promoting a new workwear concept. Additionally, it highlights Dr. Kostopoulos's substantial professional credentials and her commitment to educating and empowering fashion professionals.Ad
Recently uploaded (20)
Shivsrushti’s Special Summer Access Made Possible by Abhay Bhutada Foundation
Shivsrushti’s Special Summer Access Made Possible by Abhay Bhutada FoundationLokesh Agrawal
?
Abhay Bhutada Foundation’s contribution has made Shivsrushti’s immersive historical experience more inclusive. This presentation covers the summer ticket campaign, attractions like the Time Machine Theatre, and how visitors can take part before July 15, 2025.DFARS Part 236 - Construction and Architect - Engineer Contracts
DFARS Part 236 - Construction and Architect - Engineer ContractsJSchaus & Associates
?
2025 - JSchaus & Associates in Washington DC present a complimentary webinar series covering The DFARS, Defense Federal Acquisition Regulation Supplement. Learn about US Federal Government Contracting with The Department of Defense, DoD. Defense Contracting. Defense Acquisition. Federal Contracting.
Link To Video:
https://youtu.be/1VW0_RzfYPM
Subscribe to Our YouTube Channel for complimentary access to US Federal Government Contracting videos:
https://www.youtube.com/@jenniferschaus/videosRs 50 Entry at Shivsrushti Ongoing Till July 15, Thanks to Abhay Bhutada Foun...
Rs 50 Entry at Shivsrushti Ongoing Till July 15, Thanks to Abhay Bhutada Foun...Swapnil Pednekar
?
Shivsrushti, Pune’s premier historical theme park, is offering discounted entry tickets thanks to the Abhay Bhutada Foundation. Discover the initiative’s educational purpose, featured exhibits, and limited-time availability through this detailed walkthrough.
MiSST: Making Children’s Lives Better Through Classical Music
MiSST: Making Children’s Lives Better Through Classical MusicMark Lyttleton
?
MiSST (The Music in Secondary School Trust) was founded in 2013 and has now provided opportunities to more than 20,000 children, improving both social and educational outcomes through expert tuition and the provision of classical instruments. 最新版美国路易斯安那理工大学毕业证(尝补罢别肠丑毕业证书)原版定制
最新版美国路易斯安那理工大学毕业证(尝补罢别肠丑毕业证书)原版定制taqyea
?
一比一还原路易斯安那理工大学毕业证/LaTech毕业证书2025原版【q薇1954292140】我们专业办理澳洲大学毕业证成绩单,美国大学毕业证成绩单,英国大学毕业证成绩单,加拿大大学毕业证成绩单,新加坡大学毕业证成绩单,新西兰大学毕业证成绩单,韩国大学毕业证成绩单,日本大学毕业证成绩单。
【复刻一套路易斯安那理工大学毕业证成绩单信封等材料最强攻略,Buy Louisiana Tech University Transcripts】
购买日韩成绩单、英国大学成绩单、美国大学成绩单、澳洲大学成绩单、加拿大大学成绩单(q微1954292140)新加坡大学成绩单、新西兰大学成绩单、爱尔兰成绩单、西班牙成绩单、德国成绩单。成绩单的意义主要体现在证明学习能力、评估学术背景、展示综合素质、提高录取率,以及是作为留信认证申请材料的一部分。
路易斯安那理工大学成绩单能够体现您的的学习能力,包括路易斯安那理工大学课程成绩、专业能力、研究能力。(q微1954292140)具体来说,成绩报告单通常包含学生的学习技能与习惯、各科成绩以及老师评语等部分,因此,成绩单不仅是学生学术能力的证明,也是评估学生是否适合某个教育项目的重要依据!
我们承诺采用的是学校原版纸张(原版纸质、底色、纹路)我们工厂拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有成品以及工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!
【主营项目】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理毕业证|办理文凭: 买大学毕业证|买大学文凭【q薇1954292140】路易斯安那理工大学学位证明书如何办理申请?
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理美国成绩单路易斯安那理工大学毕业证【q薇1954292140】国外大学毕业证, 文凭办理, 国外文凭办理, 留信网认证
三.材料咨询办理、认证咨询办理请加学历顾问【微信:1954292140】路易斯安那理工大学毕业证购买指大学文凭购买,毕业证办理和文凭办理。学院文凭定制,学校原版文凭补办,扫描件文凭定做,100%文凭复刻。When History Became Affordable: Abhay Bhutada Foundation and the Shivsrushti ...
When History Became Affordable: Abhay Bhutada Foundation and the Shivsrushti ...Lokesh Agrawal
?
The Abhay Bhutada Foundation has enabled reduced ticket pricing at Shivsrushti with a ?51 lakh donation. This limited-time offer enhances cultural access through immersive historical learning in Pune.加拿大爱德华王子岛大学成绩单范本调鲍笔贰滨毕业完成信鲍笔贰滨成绩单防伪皑100%复刻
加拿大爱德华王子岛大学成绩单范本调鲍笔贰滨毕业完成信鲍笔贰滨成绩单防伪皑100%复刻Taqyea
?
1:1原版爱德华王子岛大学毕业证+UPEI成绩单【Q微:1954 292 140】鉴于此,UPEIdiploma爱德华王子岛大学挂科处理解决方案UPEI毕业证成绩单专业服务学历认证【Q微:1954 292 140】办理教育部学历认证,留学回国证明,爱德华王子岛大学毕业证、爱德华王子岛大学成绩单、爱德华王子岛大学文凭(留信学历认证+永久存档查询)办理本科+硕士+博士毕业证成绩单学历认证,我们一直是留学生的首选,质量行业第一,诚信可靠。
【爱德华王子岛大学成绩单一站式办理专业技术完美呈现University of Prince Edward Island Transcripts】
购买日韩成绩单、英国大学成绩单、美国大学成绩单、澳洲大学成绩单、加拿大大学成绩单(q微1954292140)新加坡大学成绩单、新西兰大学成绩单、爱尔兰成绩单、西班牙成绩单、德国成绩单。成绩单的意义主要体现在证明学习能力、评估学术背景、展示综合素质、提高录取率,以及是作为留信认证申请材料的一部分。
爱德华王子岛大学成绩单能够体现您的的学习能力,包括爱德华王子岛大学课程成绩、专业能力、研究能力。(q微1954292140)具体来说,成绩报告单通常包含学生的学习技能与习惯、各科成绩以及老师评语等部分,因此,成绩单不仅是学生学术能力的证明,也是评估学生是否适合某个教育项目的重要依据!
【主营项目】
一.毕业证【q微1954292140】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)Outreach Proramme on Sensitizing the Diductor for Better TDS / TCS Compliance
Outreach Proramme on Sensitizing the Diductor for Better TDS / TCS ComplianceCOLOURIMPRESSION
?
Outreach Proramme on Sensitizing the Diductor for Better TDS / TCS Compliance
Org By : Treasury BandaFinal Demonstration Three Branches of Government.pptx
Final Demonstration Three Branches of Government.pptxdanilynolinares
?
Demonstration on Three Branches of GovernmentStep 7_Investment Programming Invest.pptx
Step 7_Investment Programming Invest.pptxdanilynolinares
?
Investment Programming Government OrientationAbhay Bhutada Foundation Enables ?50 Entry to Shivsrushti
Abhay Bhutada Foundation Enables ?50 Entry to ShivsrushtiSwapnil Pednekar
?
Experience history without the high price. Shivsrushti’s ?50 entry, powered by the Abhay Bhutada Foundation, invites families and students to explore Shivaji Maharaj’s legacy like never before—offer ends soon!
Doc 9626.MANUAL ON THE REGULATION OF INTERNATIONAL AIR TRANSPORT
Doc 9626.MANUAL ON THE REGULATION OF INTERNATIONAL AIR TRANSPORTFaisalKhan876189
?
Presentation on MANUAL ON THE REGULATION OF INTERNATIONAL AIR TRANSPORTStrategic Planning for Grassroots Organizations 2025.pptx.pptx
Strategic Planning for Grassroots Organizations 2025.pptx.pptxJoyce Lewis-Andrews
?
Twenty-eight year nonprofit veteran, Joyce Lewis-Andrews’ strategic planning model provides a practical framework, relationship-building approach, and a focused process necessary to address four key goals of organizational sustainability.The Data City, United Kingdom - Fatima Garcia
The Data City, United Kingdom - Fatima GarciaOECD CFE
?
Presentation by Fatima Garcia Elena (Consultant Data Scientist, The Data City, United Kingdom) at the OECD TPI Orkestra conference "From analysis to action: Harnessing local policies to boost productivity" held in Trento, Italy on 5-6 June 2025.
More info: https://oe.cd/5ZDDFARS Part 235 - Reseach And Development Contracts
DFARS Part 235 - Reseach And Development ContractsJSchaus & Associates
?
2025 - JSchaus & Associates in Washington DC present a complimentary webinar series covering The DFARS, Defense Federal Acquisition Regulation Supplement. Learn about US Federal Government Contracting with The Department of Defense, DoD. Defense Contracting. Defense Acquisition. Federal Contracting.
Link To Video:
https://www.youtube.com/watch?v=puBw_ehen7Y
Subscribe to Our YouTube Channel for complimentary access to US Federal Government Contracting videos:
https://www.youtube.com/@jenniferschaus/videos定制鲍奥翱蹿蹿别谤英国华威大学毕业证范本,鲍奥学历证书
定制鲍奥翱蹿蹿别谤英国华威大学毕业证范本,鲍奥学历证书taqyed
?
鉴于此,办理UW大学毕业证华威大学毕业证书【q薇1954292140】留学一站式办理学历文凭直通车(华威大学毕业证UW成绩单原版华威大学学位证假文凭)未能正常毕业?【q薇1954292140】办理华威大学毕业证成绩单/留信学历认证/学历文凭/使馆认证/留学回国人员证明/录取通知书/Offer/在读证明/成绩单/网上存档永久可查!
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
【办理华威大学成绩单Buy The University of Warwick Transcripts】
购买日韩成绩单、英国大学成绩单、美国大学成绩单、澳洲大学成绩单、加拿大大学成绩单(q微1954292140)新加坡大学成绩单、新西兰大学成绩单、爱尔兰成绩单、西班牙成绩单、德国成绩单。成绩单的意义主要体现在证明学习能力、评估学术背景、展示综合素质、提高录取率,以及是作为留信认证申请材料的一部分。
华威大学成绩单能够体现您的的学习能力,包括华威大学课程成绩、专业能力、研究能力。(q微1954292140)具体来说,成绩报告单通常包含学生的学习技能与习惯、各科成绩以及老师评语等部分,因此,成绩单不仅是学生学术能力的证明,也是评估学生是否适合某个教育项目的重要依据!Ad
