Learn Hacking With Gflixacademy
- 1. Gflixacademy A Steps Towards Success
- 2. 2
- 3. INTRODUCTION/OVERVIEW In this tutorial, we will take you through the various concepts of Ethical Hacking and explain how you can use them in a real-time environment. This tutorial has been prepared for professionals aspiring to learn the basics of Ethical Hacking and make a career as an ethical hacker. Before proceeding with this tutorial, you should have a good grasp over all the fundamental concepts of a computer and how it operates in a networked environment. 3
- 4. 1. Ethical Hacking –overview 2. Ethical Hacking –Types Of Hacker 3. Ethical Hacker – Terminologies 4. Ethical Hacking – Tools 5. Ethical Hacking – Process 6. Ethical Hacking – Reconnaissance 7. Ethical Hacking – Footprinting 8. Ethical Hacking – Sniffing 9. Ethical Hacking – ARP Poisioning 10. Ethical Hacking – DNS Poisioning 11. Ethical Hacking – Exploitation 4
- 5. 11. Ethical Hacking - Enumeration 12. Ethical Hacking - Metasploit 13. Ethical Hacking – Trojan Attack 14. Ethical Hacking – TCP/IP Hijacking 15. Ethical Hacking – Password Hacking 16. Ethical Hacking – Wireless Hacking 17. Ethical Hacking - Socail Engineering 18. Ethical Hacking - DDOS Attack 19. Ethical Hacking – Cross Site Scripting 20. Ethical Hacking – SQL Injection 21. Ethical Hacking – Pen Testing 5
- 6. Hacking is an attempt to exploit a computer system or a private network inside a computer. Hacking is the unauthorised acces to or control over computer network security systems for some illicit purpose . Hacking refers to activities that seek to compromise digital devices , such as computers , smartphones , tablets And even entire networks. 6 WHAT IS HACKING
- 7. White hat hackers are authorized or certified to hack the systems. These White Hat Hackers work for governments or organizations by getting into the system. White hat hackers are also known as ethical hackers. WHITE HAT HACKER Black hat hackers are also knowledgeable computer experts but with the wrong intention. They attack other systems to get access to systems where they do not have authorized entry. On gaining entry they might steal the data or destroy the system. BLACK HAT HACKER The intention behind the hacking is considered while categorizing the hacker. The Gray hat hacker falls in between the black hat hackers and white hat hackers. They are not certified, hackers. These types of hackers work with either good or bad intentions. The hacking might be for their gain. GREY HAT HACKER It is a known fact that half knowledge is always dangerous. The Script Kiddies are amateurs types of hackers in the field of hacking. They try to hack the system with scripts from other fellow hackers. They try to hack the systems, networks, or websites . SCRIPT KIDDIES 7 TYPES OF HACKER Computers and the Internet have changed the work environment of the world beyond imagination. Computers on taking over a major part of our lives, all our data has got transferred from records and ledgers to computers. Though this kind of shift in working has reduced the physical burden on workers it has also increased the chances of data theft. People involved in stealing data or harming the systems are knowledgeable people with wrong intentions known as Hackers. There are different types of hackers. Let’s take a look at how many types of hackers are there and the types of hacker attacks and techniques.
- 8. 8 Adware − Adware is software designed to force pre-chosen ads to display on your system. Attack − An attack is an action that is done on a system to get its access and extract sensitive data. Back door − A back door, or trap door, is a hidden entry to a computing device or software that bypasses security measures, such as logins and password protections. Bot − A bot is a program that automates an action so that it can be done repeatedly at a much higher rate for a more sustained period than a human operator could do it. For example, sending HTTP, FTP or Telnet at a higher rate or calling script to create objects at a higher rate. Botnet − A botnet, also known as zombie army, is a group of computers controlled without their owners’ knowledge. Botnets are used to send spam or make denial of service attacks.
- 9. 9
- 10. DDoS ‚àí Distributed denial of service attack. Exploit Kit ‚àí An exploit kit is software system designed to run on web servers, with the purpose of identifying software vulnerabilities in client machines communicating with it and exploiting discovered vulnerabilities to upload and execute malicious code on the client. Exploit ‚àí Exploit is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability to compromise the security of a computer or network system. Firewall ‚àí A firewall is a filter designed to keep unwanted intruders outside a computer system or network while allowing safe communication between systems and users on the inside of the firewall Malware ‚àí Malware is an umbrella term used to refer to a variety of forms of hostile or intrusive software, including computer viruses, worms, Trojan horses, ransomware, spyware, adware, scareware, and other malicious programs 10
- 11. Keystroke logging ‚àí Keystroke logging is the process of tracking the keys which are pressed on a computer (and which touchscreen points are used). It is simply the map of a computer/human interface. It is used by gray and black hat hackers to record login IDs and passwords. Keyloggers are usually secreted onto a device using a Trojan delivered by a phishing email. Master Program ‚àí A master program is the program a black hat hacker uses to remotely transmit commands to infected zombie drones, normally to carry out Denial of Service attacks or spam attacks. Phishing ‚àí Phishing is an e-mail fraud method in which the perpetrator sends out legitimate-looking emails, in an attempt to gather personal and financial information from recipients. Spam ‚àí A Spam is simply an unsolicited email, also known as junk email, sent to a large number of recipients without their consent. 11
- 12. Spoofing ‚àí Spoofing is a technique used to gain unauthorized access to computers, whereby the intruder sends messages to a computer with an IP address indicating that the message is coming from a trusted host. Spyware ‚àí Spyware is software that aims to gather information about a person or organization without their knowledge and that may send such information to another entity without the consumer's consent, or that asserts control over a computer without the consumer's knowledge SQL Injection ‚àí SQL injection is an SQL code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). Threat ‚àí A threat is a possible danger that can exploit an existing bug or vulnerability to compromise the security of a computer or network system. 12
- 13. Trojan ‚àí A Trojan, or Trojan Horse, is a malicious program disguised to look like a valid program, making it difficult to distinguish from programs that are supposed to be there designed with an intention to destroy files, alter information, steal passwords or other information. Virus ‚àí A virus is a malicious program or a piece of code which is capable of copying itself and typically has a detrimental effect, such as corrupting the system or destroying data. Vulnerability ‚àí A vulnerability is a weakness which allows a hacker to compromise the security of a computer or network system. Worms ‚àí A worm is a self-replicating virus that does not alter files but resides in active memory and duplicates itself. Cross-site Scripting ‚àí Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications. XSS enables attackers to inject client-side script into web pages viewed by other users. 13
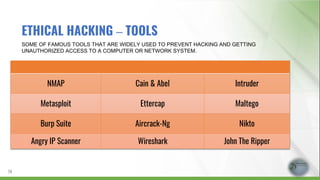
- 14. NMAP Cain & Abel Intruder Metasploit Ettercap Maltego Burp Suite Aircrack-Ng Nikto Angry IP Scanner Wireshark John The Ripper SOME OF FAMOUS TOOLS THAT ARE WIDELY USED TO PREVENT HACKING AND GETTING UNAUTHORIZED ACCESS TO A COMPUTER OR NETWORK SYSTEM. 14 ETHICAL HACKING – TOOLS
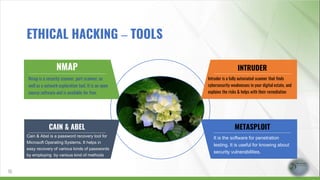
- 15. NMAP Nmap is a security scanner, port scanner, as well as a network exploration tool. It is an open source software and is available for free. CAIN & ABEL Cain & Abel is a password recovery tool for Microsoft Operating Systems. It helps in easy recovery of various kinds of passwords by employing by various kind of methods INTRUDER Intruder is a fully automated scanner that finds cybersecurity weaknesses in your digital estate, and explains the risks & helps with their remediation METASPLOIT It is the software for penetration testing. It is useful for knowing about security vulnerabilities. 15 ETHICAL HACKING – TOOLS
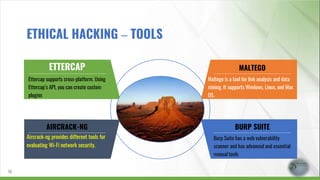
- 16. ETTERCAP Ettercap supports cross-platform. Using Ettercap’s API, you can create custom plugins AIRCRACK-NG Aircrack-ng provides different tools for evaluating Wi-Fi network security. MALTEGO Maltego is a tool for link analysis and data mining. It supports Windows, Linux, and Mac OS. BURP SUITE Burp Suite has a web vulnerability scanner and has advanced and essential manual tools 16 ETHICAL HACKING – TOOLS
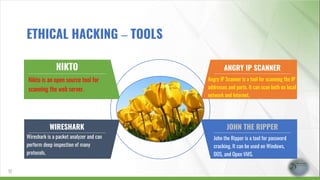
- 17. NIKTO Nikto is an open source tool for scanning the web server. WIRESHARK Wireshark is a packet analyzer and can perform deep inspection of many protocols. ANGRY IP SCANNER Angry IP Scanner is a tool for scanning the IP addresses and ports. It can scan both on local network and Internet. JOHN THE RIPPER John the Ripper is a tool for password cracking. It can be used on Windows, DOS, and Open VMS. 17 ETHICAL HACKING – TOOLS
- 18. COMPANY NAME - GFLIXACADEMY ADDRESS – NEW DELHI EMAIL – ADMIN@GFLIXACADEMY.COM PHONE - +91-8527734087 WWW.GFLIXACADEMY.COM THANK YOU INSPIRATIONAL QUOTES "No one can make you feel weak without your mental acceptance. So be strong and don't give the chance to anyone to make you feel weak" ………To Be Continued 18 CONTACT