May 09 2009 Solar
Download as doc, pdf0 likes94 views
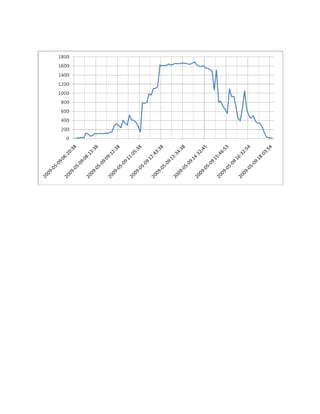
Solar Energy Production for May 9, 2009 for Erik and Heather
1 of 1
Download to read offline
Ad
Recommended
Sentence Validation by Statistical Language Modeling and Semantic Relations
Sentence Validation by Statistical Language Modeling and Semantic RelationsEditor IJCATR
╠²
The document discusses a paper on sentence validation in natural language processing (NLP), focusing on two approaches: statistical language modeling using n-gram techniques and semantic analysis to evaluate sentence validity. It details the training of a database with sample sentences from the Brown corpus, comparison of three models, and the challenges of validating sentences in natural language. The paper emphasizes the importance of integrating various approaches to improve the accuracy of NLP applications and provides insights into potential future developments in the field.historia del internet y de la webbYrOn
╠²
La Web fue creada en el CERN en Suiza a principios de los a├▒os 90 por Tim Berners-Lee como una forma de compartir informaci├│n de manera universal entre investigadores. Introdujo conceptos como el hipertexto que permiten acceder a informaci├│n de forma sencilla desde cualquier ordenador. Esto llev├│ a un crecimiento exponencial de Internet ya que permiti├│ a usuarios novatos acceder f├Īcilmente a recursos en todo el mundo.Protecting Global Records Sharing with Identity Based Access Control List
Protecting Global Records Sharing with Identity Based Access Control ListEditor IJCATR
╠²
This paper analyzes security threats in Mobile Ad Hoc Networks (MANETs) and discusses various types of attacks across different protocol layers, including application, transport, network, MAC, and physical layers. It also presents detection techniques such as Intrusion Detection Systems (IDS) that localize and respond to anomalies, aiming to improve the security framework in MANETs. The study addresses both active and passive attacks, emphasizing the importance of maintaining confidentiality, integrity, and availability of communication within these networks.Cifra City De Sara Bareilles
Cifra City De Sara BareillesFabricio Navarro
╠²
This document provides lyrics to the song "City" by Sara Bareilles. The song describes a night out at bars filled with people and perfume, but the singer does not feel like singing and wants to leave. The chorus reflects on how it's easy to get lost in a big city at night, and the singer is looking for any reason to escape. However, she wonders if she could find someone to hold onto before she fades away in the city lights.Ap Review1
Ap Review1H L
╠²
The document contains 11 multiple choice questions about cardiovascular system anatomy and physiology. Questions cover topics like hypertension, strokes, arterial walls, blood vessels associated with the heart, what gives blood its red color, oxygen transport by hemoglobin, and the structure of arteries.Software Architecture Evaluation of Unmanned Aerial Vehicles Fuzzy Based Cont...
Software Architecture Evaluation of Unmanned Aerial Vehicles Fuzzy Based Cont...Editor IJCATR
╠²
This document surveys recent techniques for evaluating software architecture methods of unmanned aerial vehicles (UAVs) that utilize fuzzy control methodologies. It discusses various evaluation approaches, their limitations, and identifies open research issues such as risk evaluation, communication latency, and sensor performance. The paper highlights the need for systematic methods to enhance adaptability and clarify the autonomy evaluation of UAV systems.Duplicate Code Detection using Control Statements
Duplicate Code Detection using Control StatementsEditor IJCATR
╠²
This paper discusses the significance of code clone detection in software development and proposes new methods for identifying structural clones using control statement structures. The authors examine two approaches for detecting duplicate code based on the order of control statements and the execution flow, detailing their methodology and presenting experimental results. The study highlights the impact of duplicate code on software quality and offers insights into improving code maintenance through effective detection techniques.A Survey of Existing Mechanisms in Energy-Aware Routing In MANETs
A Survey of Existing Mechanisms in Energy-Aware Routing In MANETsEditor IJCATR
╠²
This document reviews energy-aware routing protocols in Mobile Ad hoc Networks (MANETs), highlighting the importance of energy-efficient routing due to the limited battery power of nodes. It discusses various existing protocols such as DSR and AODV, and introduces modifications made by researchers to enhance energy efficiency. The paper categorizes these protocols into reactive, proactive, and hybrid types, focusing primarily on reactive protocols and presenting various approaches to minimize energy consumption during routing processes.Data Mining in the World of BIG Data-A Survey
Data Mining in the World of BIG Data-A SurveyEditor IJCATR
╠²
The document discusses the challenges and opportunities associated with big data and big data mining, emphasizing the necessity of developing new techniques to handle large, complex, and unstructured data effectively. It outlines key characteristics of big data, including volume, velocity, and variety, and compares traditional data mining methods with those required for mining big data. Additionally, the paper highlights various challenges, such as scalability, accuracy, privacy, and the need for innovative algorithms to manage the unique demands of big data.Al Otro Lado Del Sollinda999999
╠²
El documento es una canci├│n que habla sobre un hombre que ha terminado de construir una barca y est├Ī listo para emprender un viaje por mar con su amada para encontrar un lugar donde puedan estar juntos lejos de la envidia y el desconcierto. El hombre le pide a su amada que se apresure a preparar el equipaje para zarpar con la marea a un nuevo d├Ła y navegar hacia el mar azul, llevando su amor al otro lado del sol.Dairy Products
Dairy ProductsIES La Azucarera
╠²
This document lists various dairy products including milk, cheese, yogurt, drinking yogurt, milk meringue, smoothies, custard, ice-cream, and creme caramel. It provides a high-level overview of different types of dairy items without additional context or details about each one.P S U Vguest23d429
╠²
El documento parece ser una lista de contactos que incluye el nombre, apellidos, documento de identidad, tel├®fono, correo electr├│nico, instancia y funci├│n de varias personas.A Review Study on Secure Authentication in Mobile System
A Review Study on Secure Authentication in Mobile SystemEditor IJCATR
╠²
This document summarizes authentication techniques for mobile systems. It discusses single-factor and multi-factor authentication using passwords, tokens, and biometrics. It also reviews RFID authentication protocols like SRAC and ASRAC for secure and low-cost RFID systems. Public key cryptography models using elliptic curve cryptography are proposed for mobile security. Secure authentication provides benefits like protection, scalability, speed, and availability for mobile enterprises. Both encryption and authentication are needed but encryption requires more processing resources so should only be used for critical information.A Novel Document Image Binarization For Optical Character Recognition
A Novel Document Image Binarization For Optical Character RecognitionEditor IJCATR
╠²
The paper presents a novel technique for document image binarization designed to accurately segment foreground text from poorly degraded document images using adaptive image contrast. The method combines local image contrast and gradient to address variations in text and background, employs Canny edge detection for stroke identification, and includes local thresholding for segmentation. This approach enhances binarization effectiveness with minimal parameter tuning, making it suitable for diverse document degradations.Pre K Week 1 09 10
Pre K Week 1 09 10daohoanu
╠²
The document outlines the daily schedule and activities for a pre-K class during the first week of school from August 24-28, 2009. Each day includes greetings, breakfast, morning meeting, bathroom breaks, outdoor time, lunch, story time, quiet time, guided discovery activities, and dismissal. The schedule introduces the children to classroom routines and rules while providing time for socialization, learning names, basic academic concepts like counting and patterns, guided play with materials, and outdoor physical activities.Feature Selection Algorithm for Supervised and Semisupervised Clustering
Feature Selection Algorithm for Supervised and Semisupervised ClusteringEditor IJCATR
╠²
This document reviews steganography techniques for hiding data in digital images. It discusses how the least significant bit insertion method can be used to embed secret messages in the pixel values of an image file without noticeably changing the image. The document also compares steganography to cryptography, noting that while cryptography encrypts messages, steganography aims to conceal even the existence of hidden communications. It proposes a novel approach that first encrypts data using cryptography before embedding it in images using least significant bit insertion and interpolation to increase capacity.Enhancing Data Staging as a Mechanism for Fast Data Access
Enhancing Data Staging as a Mechanism for Fast Data AccessEditor IJCATR
╠²
The document discusses enhancing data staging within data warehouses to address performance issues caused by growing data sizes and varied data formats from multiple sources. It proposes a deterministic prioritization approach to improve data access speed by managing and filtering significant data effectively during the extraction, transformation, and loading processes. The study emphasizes the need for a well-designed data staging framework to optimize the management of large datasets and improve decision-making efficiency in organizations.Detection of Anemia using Fuzzy Logic
Detection of Anemia using Fuzzy LogicEditor IJCATR
╠²
This document presents a fuzzy logic approach for detecting anemia using clinical test results. It describes developing a fuzzy expert system with 3 input variables (hemoglobin, mean corpuscular volume, mean corpuscular hemoglobin concentration) and 1 output variable (type of anemia). Fuzzy sets and rules are defined to classify anemia based on the input clinical values. The system was tested on sample input values and correctly classified the type of anemia based on the fuzzy logic rules. The approach aims to help doctors more accurately detect anemia using a fuzzy expert system compared to probabilistic logic or relying solely on symptoms.Kitchen Brochure
Kitchen Brochureguestf01504
╠²
This document advertises 3-D CAD home design services including kitchen and bath layouts with space planning, perspective, plan, and elevation views, and specialized rendering services available at reasonable pricing. The services are aimed at homeowners and contractors looking to design remodeling or new construction projects. Cabinet sales are also available from the company.More Related Content
Viewers also liked (17)
A Survey of Existing Mechanisms in Energy-Aware Routing In MANETs
A Survey of Existing Mechanisms in Energy-Aware Routing In MANETsEditor IJCATR
╠²
This document reviews energy-aware routing protocols in Mobile Ad hoc Networks (MANETs), highlighting the importance of energy-efficient routing due to the limited battery power of nodes. It discusses various existing protocols such as DSR and AODV, and introduces modifications made by researchers to enhance energy efficiency. The paper categorizes these protocols into reactive, proactive, and hybrid types, focusing primarily on reactive protocols and presenting various approaches to minimize energy consumption during routing processes.Data Mining in the World of BIG Data-A Survey
Data Mining in the World of BIG Data-A SurveyEditor IJCATR
╠²
The document discusses the challenges and opportunities associated with big data and big data mining, emphasizing the necessity of developing new techniques to handle large, complex, and unstructured data effectively. It outlines key characteristics of big data, including volume, velocity, and variety, and compares traditional data mining methods with those required for mining big data. Additionally, the paper highlights various challenges, such as scalability, accuracy, privacy, and the need for innovative algorithms to manage the unique demands of big data.Al Otro Lado Del Sollinda999999
╠²
El documento es una canci├│n que habla sobre un hombre que ha terminado de construir una barca y est├Ī listo para emprender un viaje por mar con su amada para encontrar un lugar donde puedan estar juntos lejos de la envidia y el desconcierto. El hombre le pide a su amada que se apresure a preparar el equipaje para zarpar con la marea a un nuevo d├Ła y navegar hacia el mar azul, llevando su amor al otro lado del sol.Dairy Products
Dairy ProductsIES La Azucarera
╠²
This document lists various dairy products including milk, cheese, yogurt, drinking yogurt, milk meringue, smoothies, custard, ice-cream, and creme caramel. It provides a high-level overview of different types of dairy items without additional context or details about each one.P S U Vguest23d429
╠²
El documento parece ser una lista de contactos que incluye el nombre, apellidos, documento de identidad, tel├®fono, correo electr├│nico, instancia y funci├│n de varias personas.A Review Study on Secure Authentication in Mobile System
A Review Study on Secure Authentication in Mobile SystemEditor IJCATR
╠²
This document summarizes authentication techniques for mobile systems. It discusses single-factor and multi-factor authentication using passwords, tokens, and biometrics. It also reviews RFID authentication protocols like SRAC and ASRAC for secure and low-cost RFID systems. Public key cryptography models using elliptic curve cryptography are proposed for mobile security. Secure authentication provides benefits like protection, scalability, speed, and availability for mobile enterprises. Both encryption and authentication are needed but encryption requires more processing resources so should only be used for critical information.A Novel Document Image Binarization For Optical Character Recognition
A Novel Document Image Binarization For Optical Character RecognitionEditor IJCATR
╠²
The paper presents a novel technique for document image binarization designed to accurately segment foreground text from poorly degraded document images using adaptive image contrast. The method combines local image contrast and gradient to address variations in text and background, employs Canny edge detection for stroke identification, and includes local thresholding for segmentation. This approach enhances binarization effectiveness with minimal parameter tuning, making it suitable for diverse document degradations.Pre K Week 1 09 10
Pre K Week 1 09 10daohoanu
╠²
The document outlines the daily schedule and activities for a pre-K class during the first week of school from August 24-28, 2009. Each day includes greetings, breakfast, morning meeting, bathroom breaks, outdoor time, lunch, story time, quiet time, guided discovery activities, and dismissal. The schedule introduces the children to classroom routines and rules while providing time for socialization, learning names, basic academic concepts like counting and patterns, guided play with materials, and outdoor physical activities.Feature Selection Algorithm for Supervised and Semisupervised Clustering
Feature Selection Algorithm for Supervised and Semisupervised ClusteringEditor IJCATR
╠²
This document reviews steganography techniques for hiding data in digital images. It discusses how the least significant bit insertion method can be used to embed secret messages in the pixel values of an image file without noticeably changing the image. The document also compares steganography to cryptography, noting that while cryptography encrypts messages, steganography aims to conceal even the existence of hidden communications. It proposes a novel approach that first encrypts data using cryptography before embedding it in images using least significant bit insertion and interpolation to increase capacity.Enhancing Data Staging as a Mechanism for Fast Data Access
Enhancing Data Staging as a Mechanism for Fast Data AccessEditor IJCATR
╠²
The document discusses enhancing data staging within data warehouses to address performance issues caused by growing data sizes and varied data formats from multiple sources. It proposes a deterministic prioritization approach to improve data access speed by managing and filtering significant data effectively during the extraction, transformation, and loading processes. The study emphasizes the need for a well-designed data staging framework to optimize the management of large datasets and improve decision-making efficiency in organizations.Detection of Anemia using Fuzzy Logic
Detection of Anemia using Fuzzy LogicEditor IJCATR
╠²
This document presents a fuzzy logic approach for detecting anemia using clinical test results. It describes developing a fuzzy expert system with 3 input variables (hemoglobin, mean corpuscular volume, mean corpuscular hemoglobin concentration) and 1 output variable (type of anemia). Fuzzy sets and rules are defined to classify anemia based on the input clinical values. The system was tested on sample input values and correctly classified the type of anemia based on the fuzzy logic rules. The approach aims to help doctors more accurately detect anemia using a fuzzy expert system compared to probabilistic logic or relying solely on symptoms.Kitchen Brochure
Kitchen Brochureguestf01504
╠²
This document advertises 3-D CAD home design services including kitchen and bath layouts with space planning, perspective, plan, and elevation views, and specialized rendering services available at reasonable pricing. The services are aimed at homeowners and contractors looking to design remodeling or new construction projects. Cabinet sales are also available from the company.