GRA, NIEM and XACML Security Profiles July 2012
- 1. POLICY CONTROL PROFILES WITH GRA AND NIEM James Cabral, David Webber, Farrukh Najmi, July 2012
- 2. EXECUTIVE OVERVIEW Managing information privacy and access policies has become a critical need and technical challenge. The desired solution should be ubiquitous, syntax neutral but a simple and lightweight approach that meets the legal policy requirements though the application of clear, consistent and obvious assertions. Today we have low-level tools that developers know how to implement with, and we have legal documents created by lawyers, but then there is a chasm between these two worlds. 2
- 3. LEGAL AND RULES TECHNOLOGIES The RuleML community has long understood this and developed and is developing new and improved methods and solutions. The challenge is in taking these approaches and being able to apply these to NIEM XML based information sources in a high level conceptual way that is accessible to information analysts and general NIEM practitioners, rather than the provence of specialized XML-programmers only. Then we also need these techniques to be broadly applicable, using existing open public software standards and tools so we can enable the widest possible adoption within the NIEM community. 3
- 4. APPROACH The solution we are introducing will: ’āÆ Provide a clear declarative assertions based method, founded on policy approaches developed by the rules community, ’āÆ Leveraging open software standards and tools and ’āÆ Enabling business information analysts to apply and manage the policy profiles Show illustrative design time and run time examples by: ’āÆ Visually assigning exchange components and rule assertions ’āÆ Show applying this to retrieval of documents stored with registry and repository services. 4
- 5. APPLICATION SCENARIO OVERVIEW Electronic Policy Statements 5 Policy Rules Portal User Dashboard 1 Apply Policy Rules to Requested Case Content 4 Users see only information permitted by their role and policy profile Request Output Templates Output Templates Information Requests 2 Case Management Registry Services 3 Output Templates Output Templates Case Documents XML Response Output Templates Output Templates Requested Information 5 User Profiles
- 6. PRESENTATION AGENDA ’āÆ Part 1 ’āēProblem introduction and policy methods overview ’āÆ Part 2 ’āēDesign time technical walkthrough of rule assertions example ’āÆ Part 3 ’āēRun time deployment with registry services
- 7. PART 1 ŌĆō PROBLEM INTRODUCTION Policy Methods Overview
- 8. USE CASE ŌĆō SAR CASE MANAGEMENT ’āÆ Three levels of information access ’āē Citizen level reporting - SAR statistics ’āē Local law enforcement officials - case review ’āē State and Federal - case management and coordination ’āÆ This means three profiles: ’āē Profile 1 - Registry query - statistics results ’āē Profile 2 - Local staff ’āē Profile 3 - Regional staff 8 SAR ŌĆō Suspicious Activity Report
- 9. POLICY GRANULARITY Electronic Policy Statements Coarse- Grained Role-based authorization of subjects. Access granted to coarse-grained data objects. E.g., ŌĆ£Permit law enforcement to access the NCIC Wanted Persons Database.ŌĆØ Fine-Grained Attribute-based authorization of subjects. Access limited to specific data objects based on attributes. E.g., ŌĆ£Permit law enforcement to access criminal history records if the records were created by the requesterŌĆÖs agency.ŌĆØ 9
- 10. ’āÆ Actions. RULE AND CONTEXT METADATA Electronic Policy Statements 10 Properties of the access rules and environment. ŌĆó Conditions. ŌĆō Subject. ŌĆō Resource. ŌĆō Policy. ŌĆó Obligations.
- 11. ’āÆ Express policies in a structured language (e.g., XML) ’āÆ Identify requesters ’āÆ Compare data collection and release purposes ’āÆ Enforce retention rules ’āÆ Notify data owners and subscribers ’āÆ Verify compliance PRIVACY AND SECURITY ARCHITECTURES Privacy and Security Architectures 11
- 12. MAPPING TO DATA STANDARDS Privacy and Security Architectures 12 ŌĆóGFIPMUser Metadata ŌĆóNIEM ŌĆóGFIPM Content Metadata ŌĆóXACMLActions Electronic Policy Statements
- 13. ’āÆ A mechanism to specify policy rules in unambiguous terms ’āÆ XML Access Control Markup Language (XACML) ’āē Machine-readable ’āē Supports federated and dynamic policies POLICY AUTHORING LANGUAGE Privacy and Security Architectures 13
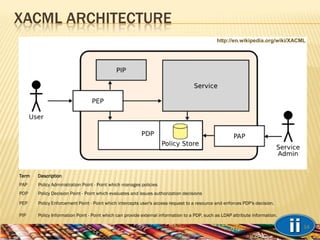
- 14. XACML ARCHITECTURE Privacy and Security Architectures 14 Term Description PAP Policy Administration Point - Point which manages policies PDP Policy Decision Point - Point which evaluates and issues authorization decisions PEP Policy Enforcement Point - Point which intercepts user's access request to a resource and enforces PDP's decision. PIP Policy Information Point - Point which can provide external information to a PDP, such as LDAP attribute information. http://en.wikipedia.org/wiki/XACML
- 15. XACML STATEMENTS Privacy and Security Architectures 15 PolicySets Policies Rules ŌĆóObligations ŌĆóFunctions Targets ŌĆóAttributes
- 16. Policy Matrix Rule XACML Statement Party Subject to Rule Subject Condition(s) Conditions. Subject(s) Subject(s). Subject Information Context Subject(s) attributes. Rule Action Action(s). Action(s) attributes. Data Resource Subject to Rule Target Resource(s) Resource(s). Other Resource Context Resource(s) attributes. Other Resource Conditions Conditions. Circumstances in Which the Rule Applies General or Action Policy Conditions Purpose(s). Obligations and Environments If [zero or more [Subject(s) Action(s) and/or Resource(s), and/or Environment(s) attributes) [Condition(s)] are met] with [zero or more Obligation(s) to be performed]. Rule Activity Deny/Permit by Statute/Policy Effect = PERMIT or DENY. Administrative Information Precedence PolicyCombiningAlgorithm(s), RuleCombiningAlgorithm(s). References PolicyID, RuleID. Linkages PolicyID, RuleID. Policy Matrix Editors Does not translate to XACML. ENCODING RULES INTO XACML Privacy and Security Architectures 16
- 17. PART 2 ŌĆō DESIGN TIME WALKTHROUGH Design Time Rule Assertions Concepts
- 18. USING POLICY TEMPLATES ’āÆ Traditional NIEM approach focuses on the information exchange data handling ’āÆ Uses XSD schema to define content structure and metadata ’āÆ Need is for a bridge between the NIEM schema, the XML information instances and the XACML rule assertion language ’āÆ Approach is based on visual content structure templates with declarative rule assertions 18
- 19. D E P L O Y E D APPROACH IN A NUTSHELL XACML Engine Rule Assertions P O L I C I E S Output Templates Output Templates Exchange Structures Policy Assertion Template 2 S C H E M A NIEM IEPD 1 XACML Generation Tool 3 XACML XML Script 4 Rules Asserted to Nodes in the Exchange Structure via simple XPath associations 19
- 20. SAR VISUAL TEMPLATE + RULE ASSERTIONS Rules Assertions associate and control access privacy to specific content areas in the SAR details structure Visual metaphor allows policy analysts to verify directly 20
- 21. Rule Assertions NIEM data flows NIEM / GRA OPERATIONAL SCENARIO XACML Engine Information Exchange 5 INTERFACES P O L I C I E S CAM Editor Visual Designer Output Templates Output Templates Exchange Templates 1 Information Exchange 3 INTERFACES 4 S C H E M A NIEM IEPD NIEM XML NIEM XML Generated XACML Rules 2 21
- 22. CAM TOOLKIT + CAMV ENGINE ’āÆ Open source solutions ŌĆō designed to support XML and industry vocabularies and components for information exchanges ’āÆ Implementing the OASIS Content Assembly Mechanism (CAM) public standard ’āÆ CAMV validation framework and test suite tools ’āÆ Development sponsored by Oracle CAM Editor resources site: http://www.cameditor.org 22
- 23. NEXT STEPS ’āÆ Enhance CAM Editor UI to provide wizards for policy rule assertion entry ’āÆ Provide XSLT to generate XACML from CAM template ’āÆ Enhance reporting tools to show policy details in plain English details ’āÆ Test with sample JPS NIEM exchange schema 23
- 24. PART 3 ŌĆō DEPLOYMENT WITH REGISTRY Illustrative deployment with XACML services and application
- 25. APPLICATION SCENARIO DETAILS Electronic Policy Statements 25 Policy Rules Portal User Dashboard 1 Apply Policy Rules to Requested Case Content (PDP Engine) 4Users see only information permitted by their role and policy profile Request Output Templates Output Templates Information Requests 2 Case Management + PAP Registry Services 3 Output Templates Output Templates Case Documents XML Response (PEP) Output Templates Output Templates Requested Information 5 User Profiles XMLXMLXML XACML
- 26. REGISTRY POLICY ENFORCEMENT Privacy and Security Architectures 26 PAP ŌĆóDefines policies. ŌĆóMonitors compliance. PDP ŌĆóReceives requests from the PEP. ŌĆóIdentifies policies that match each request. ŌĆóEvaluates request and environment attributes. ŌĆóDirects the PEP. PEP ŌĆóDiscloses or redacts the information or denies the request. ŌĆóLogs the request and action. ŌĆóNotifies of the request and action.
- 27. PRIVACY POLICY TECHNICAL FRAMEWORK Privacy and Security Architectures 27
- 28. PUBLISHING CONTENT (BULK IMPORT TOOL) Bulk loader will trawl server and folder location for content ŌĆō e.g. original SAR XML documents Bulk Publish of SAR documents 28
- 29. SAR DISCOVERY AND RETRIEVAL SAR Discovery Query (easily extended / tailored without code changes) allows rapid prototyping and verification of content and operations Results returned digest and content retrieval options 29
- 30. SUMMARY Review
- 31. KEY MESSAGES ’āÆ Dramatically simpler policies adoption ’āÆ Can be rapidly developed with existing tools ’āÆ Can be visually inspected and verified by policy analysts ’āÆ Enables use of dynamic contextual policies ’āÆ Supports international standards work 31
- 32. CONTRIBUTORS ’āÆ James E. Cabral Jr. ŌĆō IJIS/OASIS and MTGM LLC ’āÆ David Webber ŌĆō Oracle Public Sector NIEM team ’āÆ Farrukh Najmi ŌĆō OASIS ebXML RegRep, SunXACML project and Wellfleet Software 32
- 33. RESOURCES ’āÆ OASIS CAM and tools project site https://www.oasis-open.org/committees/cam http://cameditor.org (sourceforge.net) ’āÆ OASIS XACML and tools project site https://www.oasis-open.org/committees/xacml http://sunxacml.sourceforge.net/ ’āÆ OASIS ebXML RegRep and Implementing Registry https://wiki.oasis-open.org/regrep/ http://goo.gl/cEpnC 33















![Policy Matrix Rule XACML Statement
Party Subject to Rule
Subject Condition(s) Conditions.
Subject(s) Subject(s).
Subject Information Context Subject(s) attributes.
Rule Action Action(s). Action(s) attributes.
Data Resource Subject to Rule
Target Resource(s) Resource(s).
Other Resource Context Resource(s) attributes.
Other Resource Conditions Conditions.
Circumstances in Which the Rule Applies
General or Action Policy Conditions Purpose(s).
Obligations and Environments If [zero or more [Subject(s) Action(s) and/or Resource(s), and/or
Environment(s) attributes) [Condition(s)] are met] with [zero or more
Obligation(s) to be performed].
Rule Activity
Deny/Permit by Statute/Policy Effect = PERMIT or DENY.
Administrative Information
Precedence PolicyCombiningAlgorithm(s), RuleCombiningAlgorithm(s).
References PolicyID, RuleID.
Linkages PolicyID, RuleID.
Policy Matrix Editors Does not translate to XACML.
ENCODING RULES INTO XACML
Privacy and Security Architectures 16](https://image.slidesharecdn.com/ijis-xacml-security-profiles-july-2012-150121121601-conversion-gate01/85/GRA-NIEM-and-XACML-Security-Profiles-July-2012-16-320.jpg)
















