Top Vulnerabilities Of 2014
0 likes144 views
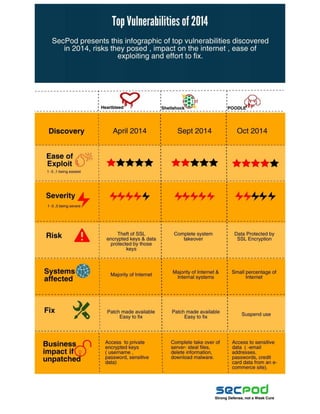
Take a look at the top vulnerabilities of 2014, risks posed by them, their impact on internet and the ease of exploiting and fixing them.
1 of 1
Download to read offline
Recommended
How BlueHat Cyber Uses SanerNow to Automate Patch Management and Beyond



How BlueHat Cyber Uses SanerNow to Automate Patch Management and BeyondSecPod Technologies
?
It°Øs widely known that patch management is a major pain point for most businesses. IT teams struggle to keep systems patched and secure. Cyber-attacks are continuous and anti-virus protection alone isn°Øt effective.
Cyber hygiene best practices need to be followed to keep organizations secure and to prevent security breaches.
In this webinar, Chandrashekhar - SecPod°Øs Founder & CEO, Douglas Smith - BlueHat Cyber°Øs Senior Sales Director, and Greg Pottebaum - SecPod°Øs VP OEM & Strategic Alliances, demonstrate:
- How to efficiently reduce the cyber-attack surface of your business
- Simple strategies to improve your security management
- How Blue Hat Cyber uses SanerNow to automate patch management and secure their customer°Øs endpoints
Request a FREE Demo of SanerNow platform at:
www.secpod.com
About SecPod
SecPod is an endpoint security and management technology company. SecPod (Security Podium, incarnated as SecPod)
was founded in the year 2008. SecPod°Øs SanerNow platform and tools are used by MSPs and enterprises worldwide.
SecPod also licenses security technology to top security vendors through its SCAP Content Professional Feed.
Facebook: https://www.facebook.com/secpod/
LinkedIn: https://www.linkedin.com/company/secp...
Twitter: https://twitter.com/SecPod
Email us at info@secpod.com to get more details on how to secure your organisation from cyber attacks.8 Types of Cyber Attacks That Can Bother CISOs in 2020



8 Types of Cyber Attacks That Can Bother CISOs in 2020SecPod Technologies
?
What are cyber attacks?
In simple terms, cyber attacks are attempts of disabling or stealing information from other computers, by gaining access to admin privileges to them.
Why should businesses be worried?
An average ransomware attack costs a company $5 million. Attackers target all types of businesses, small and large, healthcare, banking & finance, manufacturing, education, even government. The internet has made life a lot easier for business owners, at the same time it has made them easier to get hacked.
Security threats



Security threatsSecPod Technologies
?
Human threats pose the greatest risk to organizations, costing over $100 billion annually worldwide through hacking and social engineering. Network security threats like malware, viruses, and phishing attacks are common, with over 45% requiring user interaction via email. Physical security is often overlooked despite threats from theft, sabotage, and terrorism. Software threats can attack through logic bombs, trojans, worms and viruses.Hacking Internet of Things (IoT)



Hacking Internet of Things (IoT)SecPod Technologies
?
The document discusses vulnerabilities in IoT devices and provides examples of potential threats, including hacking a Jeep remotely and changing the target of a smart sniper rifle. It then summarizes challenges in securing IoT devices like limited resources, difficulty upgrading firmware, and lack of security software. Guidelines are provided for vendors, developers, and users to improve IoT security, such as using encryption, patching vulnerabilities, and educating users. Finally, the document demonstrates hacking a DTH set-top box by disturbing service, recording shows without permission, and stealing recordings.WHY MSSPs LOVE OUR SOLUTION



WHY MSSPs LOVE OUR SOLUTIONSecPod Technologies
?
Managed security service providers (MSSPs) value the Saner Business endpoint security solution for its ability to:
1) Find and eliminate vulnerabilities across networks in an automated and simple way.
2) Offer discrete security services and support regulatory compliance standards through continual assessment and remediation.
3) Provide continuous monitoring and detection of advanced threats that other solutions may overlook.Many products-no-security (1)



Many products-no-security (1)SecPod Technologies
?
The document discusses the challenges of managing IT security with many individual point products that have overlapping functionality and features. It introduces the SecPod SanerNow platform as a single platform approach for provisioning various security and endpoint management tools on demand to address specific tasks in a simpler and more cost-effective manner. Key benefits highlighted include reducing costs by up to 60%, easing management and improving security through continuous monitoring, vulnerability assessment, and threat detection and response capabilities.SanerNow Endpoint Management



SanerNow Endpoint ManagementSecPod Technologies
?
SanerNow Endpoint Management (EM) is a cloud-delivered
service that allows complete control over all your endpoint
systems. It provides visibility into the status of endpoints and
equips you with hundreds of built-in checks. SanerNow
Endpoint Management provides necessary features for
managing endpoints.SanerNow Asset Management



SanerNow Asset ManagementSecPod Technologies
?
SanerNow Asset Management (AM) is a cloud-delivered
service that tracks assets installed on hosts, the open
vulnerabilities in the OS and applications, their patch or update
levels, and prioritizes remediation tasks - all critical to the
deep visibility required to prevent attacks and data breaches.SanerNow Patch Management



SanerNow Patch ManagementSecPod Technologies
?
SanerNow Patch Management (PM) is a cloud-delivered
service that identifies and automatically rolls out patches
according to rules and jobs defined by the user. If necessary, it
automatically reboots systems after applying patches and can
roll back installed patches. SanerNow°Øs patch management
process is timely, responsive and systematically managed.
SanerNow Vulnerability Management



SanerNow Vulnerability ManagementSecPod Technologies
?
SanerNow Vulnerability Management (VM) is a cloud delivered
service that performs an automated daily vulnerability scan. Organizations can discover their threat and vulnerability risk in less than five minutes. SanerNow VM provides continuous visibility into IT systems. Its time-testedSCAP Feed database delivers comprehensive vulnerability coverage.SanerNow platform-datasheet



SanerNow platform-datasheetSecPod Technologies
?
Many Products, No Security
So many products: Organizations invest in multiple products, many with overlapping
capabilities. And investments are huge when considering the cost of products,maintenance, professional services, training and vendor management.Many products-no-security



Many products-no-securitySecPod Technologies
?
Expensive products with complicated and
overlapping functionality aren°Øt meeting today°Øs
security and system management needs.SanerNow a platform for Endpoint security and systems Management



SanerNow a platform for Endpoint security and systems ManagementSecPod Technologies
?
Endpoint security can be more effective and less costly by simplifying management through a unified platform rather than multiple point products. Currently, organizations invest heavily in numerous security products yet still struggle with attacks, complexity, and high costs. A single platform called SanerNow provides tools to automate tasks like vulnerability management, patching, and threat detection through continuous monitoring from the cloud. It aims to reduce security costs by up to 60% by addressing issues holistically rather than relying on numerous specialized products with overlapping functionality.Healthcare's Fight Against Ransomware 



Healthcare's Fight Against Ransomware SecPod Technologies
?
Healthcare industry is becoming a popular victim to ransowmare attacks. The following infographic based on some study and statistics depicts the healthcare industry's fight against ransomware.Take a sneak peek into Saner 2.0



Take a sneak peek into Saner 2.0SecPod Technologies
?
SecPod Saner is an endpoint security solution that provides continuous visibility and control over endpoints. It proactively remediates risks and detects and responds to threats using vulnerability management, patch management, compliance management, and endpoint threat detection and response. Saner allows administrators to gain wide visibility into endpoint activities, create rules to monitor for deviations and fix issues, manage transient devices to keep them protected and up-to-date, create and enforce security compliance policies, and view real-time status reports.Msp saner 2.0



Msp saner 2.0SecPod Technologies
?
This document discusses an endpoint security as a service offering that provides continuous endpoint visibility and control. It allows organizations to offer compelling security services by providing visibility into risks, automatically detecting and fixing vulnerabilities in real-time, and ensuring compliance. This increases client revenue through expanded services and introduces new services while also increasing profit margins by maximizing client value and minimizing technical resource costs. The document then introduces a new proactive approach to endpoint security using Saner, which provides real-time endpoint visibility, automatically fixes vulnerabilities and misconfigurations, and detects and responds to threats in seconds through prevention-first capabilities.Saner 2.0



Saner 2.0SecPod Technologies
?
Saner is an endpoint security solution that provides continuous visibility and control of endpoints. It takes a proactive approach to security by detecting threats and responding before exploits can occur. Saner collects security posture data from endpoints and correlates it with threat intelligence to detect risks and indicators of compromise in real-time. It then automatically fixes vulnerabilities, misconfigurations, and responds to incidents. The solution aims to simplify and automate endpoint security management while reducing costs and ensuring compliance.Saner 2.0 product sheet



Saner 2.0 product sheetSecPod Technologies
?
SecPod Saner provides continuous visibility and control for all endpoints. It proactively remediates risks and detects and responds to threats. Saner combines endpoint vulnerability, patch and compliance management with endpoint threat detection and response into one easy to manage solution.Ransomware - A look back



Ransomware - A look backSecPod Technologies
?
Ransomware has evolved since its origins in 1989 when the first known "AIDS" trojan spread via floppy disks. There are two main types - locker ransomware that denies access to devices, and crypto ransomware that encrypts files until ransom is paid. Notable examples like Cryptolocker and CryptoLocker have targeted home users, businesses, and public agencies on computers, servers, and mobile devices. Ransomware infects through malicious advertisements, spam emails, downloaders, botnets, and social engineering. Profits from ransomware have grown substantially, reaching over $18 million in 2015. Ransomware impacts many countries worldwide, with payments typically demanded through vouchers or bitcoins.Worst security data breaches till 2015 - SecPod



Worst security data breaches till 2015 - SecPodSecPod Technologies
?
The document summarizes major data security breaches from 2006 to 2015. It provides details on the impact and source of each breach. Some key breaches included:
- 2006: Personal information of 26.5 million veterans stolen from a Department of Veterans Affairs database stored on a stolen laptop and hard drive.
- 2007: A Fidelity National Information Services employee stole customer records of 3.2 million people.
- 2013: Hackers gained access to payment card information for up to 110 million Target customers through compromised third-party vendors.Our talk in Black Hat Asia 2015 Briefing 



Our talk in Black Hat Asia 2015 Briefing SecPod Technologies
?
In this whitepaper, presented at Black Hat Asia 2015 Briefing session, we highlight how even if the Security Content Automation Protocol (SCAP) federates a number of open standards that are used to enumerate software
flaws and configuration issues related to security, there is a need for having a unique common metadata schema to represent important aspects relevant for designing efficient search enginesChanging L andscape Of Cyber Attacks



Changing L andscape Of Cyber AttacksSecPod Technologies
?
Infographic on how landscape of cyber attacks have changed to become more effective and precise.Cost Of Cyber Crime



Cost Of Cyber CrimeSecPod Technologies
?
Infographic on the increasing cost of cyber crime and how it affects an organisation.Perception vs reality of cyber security



Perception vs reality of cyber securitySecPod Technologies
?
Infographic on how CISOs and IT Managers perceive their organization°Øs security and how different it is from reality.Vulnerabilities By Numbers



Vulnerabilities By NumbersSecPod Technologies
?
Infographic on the increasing number of vulnerabilities,where they reside, OS and the applications they affectVulnerabilities: Cause And Effect



Vulnerabilities: Cause And EffectSecPod Technologies
?
Take a look at the main cause for vulnerabilities to exploit endpoints, top industries it affects and how breached occur.Managing Compliance



Managing ComplianceSecPod Technologies
?
For an organization to function efficiently it is important to have security controls to ensure the protection of confidentiality, integrity and availability of information and systems. Compliance is the process of ensuring all systems in an organization met a set of predefined specific rules.
In this article we will address the need for compliance automation and how SecPod°Øs Saner provides enterprises the ability to automate compliance while minimizing time spent on non-compliant state.DevNexus - Building 10x Development Organizations.pdf



DevNexus - Building 10x Development Organizations.pdfJustin Reock
?
Developer Experience is Dead! Long Live Developer Experience!
In this keynote-style session, we°Øll take a detailed, granular look at the barriers to productivity developers face today and modern approaches for removing them. 10x developers may be a myth, but 10x organizations are very real, as proven by the influential study performed in the 1980s, °ÆThe Coding War Games.°Ø
Right now, here in early 2025, we seem to be experiencing YAPP (Yet Another Productivity Philosophy), and that philosophy is converging on developer experience. It seems that with every new method, we invent to deliver products, whether physical or virtual, we reinvent productivity philosophies to go alongside them.
But which of these approaches works? DORA? SPACE? DevEx? What should we invest in and create urgency behind today so we don°Øt have the same discussion again in a decade?SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOT



SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOTTanmaiArni
?
SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOTMore Related Content
More from SecPod Technologies (20)
SanerNow Patch Management



SanerNow Patch ManagementSecPod Technologies
?
SanerNow Patch Management (PM) is a cloud-delivered
service that identifies and automatically rolls out patches
according to rules and jobs defined by the user. If necessary, it
automatically reboots systems after applying patches and can
roll back installed patches. SanerNow°Øs patch management
process is timely, responsive and systematically managed.
SanerNow Vulnerability Management



SanerNow Vulnerability ManagementSecPod Technologies
?
SanerNow Vulnerability Management (VM) is a cloud delivered
service that performs an automated daily vulnerability scan. Organizations can discover their threat and vulnerability risk in less than five minutes. SanerNow VM provides continuous visibility into IT systems. Its time-testedSCAP Feed database delivers comprehensive vulnerability coverage.SanerNow platform-datasheet



SanerNow platform-datasheetSecPod Technologies
?
Many Products, No Security
So many products: Organizations invest in multiple products, many with overlapping
capabilities. And investments are huge when considering the cost of products,maintenance, professional services, training and vendor management.Many products-no-security



Many products-no-securitySecPod Technologies
?
Expensive products with complicated and
overlapping functionality aren°Øt meeting today°Øs
security and system management needs.SanerNow a platform for Endpoint security and systems Management



SanerNow a platform for Endpoint security and systems ManagementSecPod Technologies
?
Endpoint security can be more effective and less costly by simplifying management through a unified platform rather than multiple point products. Currently, organizations invest heavily in numerous security products yet still struggle with attacks, complexity, and high costs. A single platform called SanerNow provides tools to automate tasks like vulnerability management, patching, and threat detection through continuous monitoring from the cloud. It aims to reduce security costs by up to 60% by addressing issues holistically rather than relying on numerous specialized products with overlapping functionality.Healthcare's Fight Against Ransomware 



Healthcare's Fight Against Ransomware SecPod Technologies
?
Healthcare industry is becoming a popular victim to ransowmare attacks. The following infographic based on some study and statistics depicts the healthcare industry's fight against ransomware.Take a sneak peek into Saner 2.0



Take a sneak peek into Saner 2.0SecPod Technologies
?
SecPod Saner is an endpoint security solution that provides continuous visibility and control over endpoints. It proactively remediates risks and detects and responds to threats using vulnerability management, patch management, compliance management, and endpoint threat detection and response. Saner allows administrators to gain wide visibility into endpoint activities, create rules to monitor for deviations and fix issues, manage transient devices to keep them protected and up-to-date, create and enforce security compliance policies, and view real-time status reports.Msp saner 2.0



Msp saner 2.0SecPod Technologies
?
This document discusses an endpoint security as a service offering that provides continuous endpoint visibility and control. It allows organizations to offer compelling security services by providing visibility into risks, automatically detecting and fixing vulnerabilities in real-time, and ensuring compliance. This increases client revenue through expanded services and introduces new services while also increasing profit margins by maximizing client value and minimizing technical resource costs. The document then introduces a new proactive approach to endpoint security using Saner, which provides real-time endpoint visibility, automatically fixes vulnerabilities and misconfigurations, and detects and responds to threats in seconds through prevention-first capabilities.Saner 2.0



Saner 2.0SecPod Technologies
?
Saner is an endpoint security solution that provides continuous visibility and control of endpoints. It takes a proactive approach to security by detecting threats and responding before exploits can occur. Saner collects security posture data from endpoints and correlates it with threat intelligence to detect risks and indicators of compromise in real-time. It then automatically fixes vulnerabilities, misconfigurations, and responds to incidents. The solution aims to simplify and automate endpoint security management while reducing costs and ensuring compliance.Saner 2.0 product sheet



Saner 2.0 product sheetSecPod Technologies
?
SecPod Saner provides continuous visibility and control for all endpoints. It proactively remediates risks and detects and responds to threats. Saner combines endpoint vulnerability, patch and compliance management with endpoint threat detection and response into one easy to manage solution.Ransomware - A look back



Ransomware - A look backSecPod Technologies
?
Ransomware has evolved since its origins in 1989 when the first known "AIDS" trojan spread via floppy disks. There are two main types - locker ransomware that denies access to devices, and crypto ransomware that encrypts files until ransom is paid. Notable examples like Cryptolocker and CryptoLocker have targeted home users, businesses, and public agencies on computers, servers, and mobile devices. Ransomware infects through malicious advertisements, spam emails, downloaders, botnets, and social engineering. Profits from ransomware have grown substantially, reaching over $18 million in 2015. Ransomware impacts many countries worldwide, with payments typically demanded through vouchers or bitcoins.Worst security data breaches till 2015 - SecPod



Worst security data breaches till 2015 - SecPodSecPod Technologies
?
The document summarizes major data security breaches from 2006 to 2015. It provides details on the impact and source of each breach. Some key breaches included:
- 2006: Personal information of 26.5 million veterans stolen from a Department of Veterans Affairs database stored on a stolen laptop and hard drive.
- 2007: A Fidelity National Information Services employee stole customer records of 3.2 million people.
- 2013: Hackers gained access to payment card information for up to 110 million Target customers through compromised third-party vendors.Our talk in Black Hat Asia 2015 Briefing 



Our talk in Black Hat Asia 2015 Briefing SecPod Technologies
?
In this whitepaper, presented at Black Hat Asia 2015 Briefing session, we highlight how even if the Security Content Automation Protocol (SCAP) federates a number of open standards that are used to enumerate software
flaws and configuration issues related to security, there is a need for having a unique common metadata schema to represent important aspects relevant for designing efficient search enginesChanging L andscape Of Cyber Attacks



Changing L andscape Of Cyber AttacksSecPod Technologies
?
Infographic on how landscape of cyber attacks have changed to become more effective and precise.Cost Of Cyber Crime



Cost Of Cyber CrimeSecPod Technologies
?
Infographic on the increasing cost of cyber crime and how it affects an organisation.Perception vs reality of cyber security



Perception vs reality of cyber securitySecPod Technologies
?
Infographic on how CISOs and IT Managers perceive their organization°Øs security and how different it is from reality.Vulnerabilities By Numbers



Vulnerabilities By NumbersSecPod Technologies
?
Infographic on the increasing number of vulnerabilities,where they reside, OS and the applications they affectVulnerabilities: Cause And Effect



Vulnerabilities: Cause And EffectSecPod Technologies
?
Take a look at the main cause for vulnerabilities to exploit endpoints, top industries it affects and how breached occur.Managing Compliance



Managing ComplianceSecPod Technologies
?
For an organization to function efficiently it is important to have security controls to ensure the protection of confidentiality, integrity and availability of information and systems. Compliance is the process of ensuring all systems in an organization met a set of predefined specific rules.
In this article we will address the need for compliance automation and how SecPod°Øs Saner provides enterprises the ability to automate compliance while minimizing time spent on non-compliant state.Recently uploaded (20)
DevNexus - Building 10x Development Organizations.pdf



DevNexus - Building 10x Development Organizations.pdfJustin Reock
?
Developer Experience is Dead! Long Live Developer Experience!
In this keynote-style session, we°Øll take a detailed, granular look at the barriers to productivity developers face today and modern approaches for removing them. 10x developers may be a myth, but 10x organizations are very real, as proven by the influential study performed in the 1980s, °ÆThe Coding War Games.°Ø
Right now, here in early 2025, we seem to be experiencing YAPP (Yet Another Productivity Philosophy), and that philosophy is converging on developer experience. It seems that with every new method, we invent to deliver products, whether physical or virtual, we reinvent productivity philosophies to go alongside them.
But which of these approaches works? DORA? SPACE? DevEx? What should we invest in and create urgency behind today so we don°Øt have the same discussion again in a decade?SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOT



SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOTTanmaiArni
?
SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOTThe Future of Repair: Transparent and Incremental by Botond De?nes



The Future of Repair: Transparent and Incremental by Botond De?nesScyllaDB
?
Regularly run repairs are essential to keep clusters healthy, yet having a good repair schedule is more challenging than it should be. Repairs often take a long time, preventing running them often. This has an impact on data consistency and also limits the usefulness of the new repair based tombstone garbage collection. We want to address these challenges by making repairs incremental and allowing for automatic repair scheduling, without relying on external tools.Early Adopter's Guide to AI Moderation (Preview)



Early Adopter's Guide to AI Moderation (Preview)nick896721
?
Early Adopter's Guide to AI Moderation preview by User Interviews.Field Device Management Market Report 2030 - TechSci Research



Field Device Management Market Report 2030 - TechSci ResearchVipin Mishra
?
The Global Field Device Management (FDM) Market is expected to experience significant growth in the forecast period from 2026 to 2030, driven by the integration of advanced technologies aimed at improving industrial operations.
? According to TechSci Research, the Global Field Device Management Market was valued at USD 1,506.34 million in 2023 and is anticipated to grow at a CAGR of 6.72% through 2030. FDM plays a vital role in the centralized oversight and optimization of industrial field devices, including sensors, actuators, and controllers.
Key tasks managed under FDM include:
Configuration
Monitoring
Diagnostics
Maintenance
Performance optimization
FDM solutions offer a comprehensive platform for real-time data collection, analysis, and decision-making, enabling:
Proactive maintenance
Predictive analytics
Remote monitoring
By streamlining operations and ensuring compliance, FDM enhances operational efficiency, reduces downtime, and improves asset reliability, ultimately leading to greater performance in industrial processes. FDM°Øs emphasis on predictive maintenance is particularly important in ensuring the long-term sustainability and success of industrial operations.
For more information, explore the full report: https://shorturl.at/EJnzR
Major companies operating in Global?Field Device Management Market are:
General Electric Co
Siemens AG
ABB Ltd
Emerson Electric Co
Aveva Group Ltd
Schneider Electric SE
STMicroelectronics Inc
Techno Systems Inc
Semiconductor Components Industries LLC
International Business Machines Corporation (IBM)
#FieldDeviceManagement #IndustrialAutomation #PredictiveMaintenance #TechInnovation #IndustrialEfficiency #RemoteMonitoring #TechAdvancements #MarketGrowth #OperationalExcellence #SensorsAndActuatorsBackstage Software Templates for Java Developers



Backstage Software Templates for Java DevelopersMarkus Eisele
?
As a Java developer you might have a hard time accepting the limitations that you feel being introduced into your development cycles. Let's look at the positives and learn everything important to know to turn Backstag's software templates into a helpful tool you can use to elevate the platform experience for all developers.THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIA



THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIASrivaanchi Nathan
?
This business intelligence report, "The Big Ten Biopharmaceutical MNCs: Global Capability Centers in India", provides an in-depth analysis of the operations and contributions of the Global Capability Centers (GCCs) of ten leading biopharmaceutical multinational corporations in India. The report covers AstraZeneca, Bayer, Bristol Myers Squibb, GlaxoSmithKline (GSK), Novartis, Sanofi, Roche, Pfizer, Novo Nordisk, and Eli Lilly. In this report each company's GCC is profiled with details on location, workforce size, investment, and the strategic roles these centers play in global business operations, research and development, and information technology and digital innovation.UiPath Document Understanding - Generative AI and Active learning capabilities



UiPath Document Understanding - Generative AI and Active learning capabilitiesDianaGray10
?
This session focus on Generative AI features and Active learning modern experience with Document understanding.
Topics Covered:
Overview of Document Understanding
How Generative Annotation works?
What is Generative Classification?
How to use Generative Extraction activities?
What is Generative Validation?
How Active learning modern experience accelerate model training?
Q/A
? If you have any questions or feedback, please refer to the "Women in Automation 2025" dedicated Forum thread. You can find there extra details and updates. Replacing RocksDB with ScyllaDB in Kafka Streams by Almog Gavra



Replacing RocksDB with ScyllaDB in Kafka Streams by Almog GavraScyllaDB
?
Learn how Responsive replaced embedded RocksDB with ScyllaDB in Kafka Streams, simplifying the architecture and unlocking massive availability and scale. The talk covers unbundling stream processors, key ScyllaDB features tested, and lessons learned from the transition.UiPath Automation Developer Associate Training Series 2025 - Session 2



UiPath Automation Developer Associate Training Series 2025 - Session 2DianaGray10
?
In session 2, we will introduce you to Data manipulation in UiPath Studio.
Topics covered:
Data Manipulation
What is Data Manipulation
Strings
Lists
Dictionaries
RegEx Builder
Date and Time
Required Self-Paced Learning for this session:
Data Manipulation with Strings in UiPath Studio (v2022.10) 2 modules - 1h 30m - https://academy.uipath.com/courses/data-manipulation-with-strings-in-studio
Data Manipulation with Lists and Dictionaries in UiPath Studio (v2022.10) 2 modules - 1h - https:/academy.uipath.com/courses/data-manipulation-with-lists-and-dictionaries-in-studio
Data Manipulation with Data Tables in UiPath Studio (v2022.10) 2 modules - 1h 30m - https:/academy.uipath.com/courses/data-manipulation-with-data-tables-in-studio
?? For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (∆Ω…Ω“„)



DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (∆Ω…Ω“„)Tsuyoshi Hirayama
?
DAO UTokyo 2025
ñ|æ©¥Û—ß«ÈàÛ—ß≠h •÷•Ì•√•Ø•¡•ß©`•Û—–æø•§•À•∑•¢•∆•£•÷
https://utbciii.com/2024/12/12/announcing-dao-utokyo-2025-conference/
Session 1 :DLT mass adoption
IBM Tsuyoshi Hirayama (∆Ω…Ω“„)[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
[Webinar] Scaling Made Simple: Getting Started with No-Code Web AppsSafe Software
?
Ready to simplify workflow sharing across your organization without diving into complex coding? With FME Flow Apps, you can build no-code web apps that make your data work harder for you °™ fast.
In this webinar, we°Øll show you how to:
Build and deploy Workspace Apps to create an intuitive user interface for self-serve data processing and validation.
Automate processes using Automation Apps. Learn to create a no-code web app to kick off workflows tailored to your needs, trigger multiple workspaces and external actions, and use conditional filtering within automations to control your workflows.
Create a centralized portal with Gallery Apps to share a collection of no-code web apps across your organization.
Through real-world examples and practical demos, you°Øll learn how to transform your workflows into intuitive, self-serve solutions that empower your team and save you time. We can°Øt wait to show you what°Øs possible!MIND Revenue Release Quarter 4 2024 - Finacial Presentation



MIND Revenue Release Quarter 4 2024 - Finacial PresentationMIND CTI
?
MIND Revenue Release Quarter 4 2024 - Finacial PresentationUiPath Automation Developer Associate Training Series 2025 - Session 1



UiPath Automation Developer Associate Training Series 2025 - Session 1DianaGray10
?
Welcome to UiPath Automation Developer Associate Training Series 2025 - Session 1.
In this session, we will cover the following topics:
Introduction to RPA & UiPath Studio
Overview of RPA and its applications
Introduction to UiPath Studio
Variables & Data Types
Control Flows
You are requested to finish the following self-paced training for this session:
Variables, Constants and Arguments in Studio 2 modules - 1h 30m - https://academy.uipath.com/courses/variables-constants-and-arguments-in-studio
Control Flow in Studio 2 modules - 2h 15m - https:/academy.uipath.com/courses/control-flow-in-studio
?? For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. Gojek Clone Multi-Service Super App.pptx



Gojek Clone Multi-Service Super App.pptxV3cube
?
Gojek Clone is a versatile multi-service super app that offers ride-hailing, food delivery, payment services, and more, providing a seamless experience for users and businesses alike on a single platform.EaseUS Partition Master Crack 2025 + Serial Key



EaseUS Partition Master Crack 2025 + Serial Keykherorpacca127
?
https://ncracked.com/7961-2/
Note: >> Please copy the link and paste it into Google New Tab now Download link
EASEUS Partition Master Crack is a professional hard disk partition management tool and system partition optimization software. It is an all-in-one PC and server disk management toolkit for IT professionals, system administrators, technicians, and consultants to provide technical services to customers with unlimited use.
EASEUS Partition Master 18.0 Technician Edition Crack interface is clean and tidy, so all options are at your fingertips. Whether you want to resize, move, copy, merge, browse, check, convert partitions, or change their labels, you can do everything with a few clicks. The defragmentation tool is also designed to merge fragmented files and folders and store them in contiguous locations on the hard drive.
Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]Jonathan Bowen
?
Alan Turing arguably wrote the first paper on formal methods 75 years ago. Since then, there have been claims and counterclaims about formal methods. Tool development has been slow but aided by Moore°Øs Law with the increasing power of computers. Although formal methods are not widespread in practical usage at a heavyweight level, their influence as crept into software engineering practice to the extent that they are no longer necessarily called formal methods in their use. In addition, in areas where safety and security are important, with the increasing use of computers in such applications, formal methods are a viable way to improve the reliability of such software-based systems. Their use in hardware where a mistake can be very costly is also important. This talk explores the journey of formal methods to the present day and speculates on future directions.
Brave Browser Crack 1.45.133 Activated 2025



Brave Browser Crack 1.45.133 Activated 2025kherorpacca00126
?
https://ncracked.com/7961-2/
Note: >> Please copy the link and paste it into Google New Tab now Download link
Brave is a free Chromium browser developed for Win Downloads, macOS and Linux systems that allows users to browse the internet in a safer, faster and more secure way than its competition. Designed with security in mind, Brave automatically blocks ads and trackers which also makes it faster,
As Brave naturally blocks unwanted content from appearing in your browser, it prevents these trackers and pop-ups from slowing Download your user experience. It's also designed in a way that strips Downloaden which data is being loaded each time you use it. Without these components



