Vault Associate Certification Internals
1 like442 views
Vault Associate Certification Part 1 Internals Notes. This will be series of documents which will go through all components to achieve the certification.
1 of 18
Downloaded 13 times
















Recommended
Hashicorp Vault Associate Certification Configuration Part 3



Hashicorp Vault Associate Certification Configuration Part 3Adnan Rashid
?
Vault Associate Certification Part 3 Configuration Notes. This will be series of documents which will go through all components to achieve the certification.Hashicorp Vault Associate Certification Concepts Part 2 



Hashicorp Vault Associate Certification Concepts Part 2 Adnan Rashid
?
Vault Associate Certification Part 2 Concepts Notes. This will be series of documents which will go through all components to achieve the certification.CKA Certified Kubernetes Administrator Notes 



CKA Certified Kubernetes Administrator Notes Adnan Rashid
?
Unique course notes for the Certified Kubernetes Administrator (CKA) for each section of the exam. Designed to be engaging and used as a reference in the future for kubernetes concepts.Introduction to Memory Exploitation (CppEurope 2021)



Introduction to Memory Exploitation (CppEurope 2021)Patricia Aas
?
Stack based exploitation has gotten all the fame, but many platform and compiler mitigations have made it very hard to exploit stack vulnerabilities. Heap based exploits are still very relevant, and since this is black magic for most developers I will here give an introduction to the field.introduction to jsrsasign



introduction to jsrsasignKenji Urushima
?
jsrsasign is a opensource free pure JavaScript cryptographic library. This slide shows its features such like RSA/ECDSA signing, PKCS#1/8 private/public key, ASN.1, certificate, JWT/JWS/JWK for introduction.Beyond Mirai: The new age of MDDoS attacks



Beyond Mirai: The new age of MDDoS attacksAPNIC
?
This document discusses the growing threat of DDoS attacks launched from insecure IoT devices. It provides an overview of the Mirai botnet and how it has evolved to utilize different protocols like UDP, TCP, DNS, and HTTP floods. The document also examines how botnets are monetized through DDoS-for-hire services and how future IoT botnets may become more sophisticated through techniques like DGA, P2P networking, and targeting other vulnerabilities beyond default credentials. It concludes by questioning if the cybersecurity community is doomed given the prevalence of unsecured IoT devices and need for vendors, providers, and users to take proactive steps to address this threat.Building Cloud Applications Based On Zero Trust



Building Cloud Applications Based On Zero TrustMahesh Patil
?
These days code is driving things we can't even imagine, but there is also an inherent problem with code. A Kubernetes audit recently revealed 34 vulnerabilities, and data from various organisations has been stolen multiple times. This raises the question of whom to trust. This presentation makes a case and provides a framework for zero trust in the cloud.Hacking the Web



Hacking the WebMike Crabb
?
The document discusses various web application attacks like cross-site scripting, SQL injection, cross-site request forgery, sensitive data exposure, and cookie editing. For each attack, it provides information on threat agents, attack vectors, security weaknesses, impacts, prevalence, detectability, example exploits, and steps to prevent the attack. The overall document serves as an educational guide on common web hacking techniques and how to avoid falling victim to them.Hardening Your Config Management - Security and Attack Vectors in Config Mana...



Hardening Your Config Management - Security and Attack Vectors in Config Mana...Peter Souter
?
Configuration management is a great tool for helping with hardening and securing servers. But with any addition of new technology comes a new attack vector: Who watches the watchers?
Security is painful. Luckily the invention of configuration management tools has made this process easier, by allowing repeatable configuration for common hardening. However there comes a catch-22: How do we harden the configuration management itself?
When you have a tool that enables you to change systems at a fundamental level, it's a fairly tempting target for malicious agents, and one that would cause a lot of problems if compromised.
We'll be discussing some general patterns we can use to mitigate these problems: - Whitelisting "master" API's - Encrypting sensitive data - Adding a security element to code review
And we'll talk about some application specific options for some of most popular tools out there, such as Puppet, Chef, Ansible, cfengine and Salt.Tokenization vs encryption vs masking



Tokenization vs encryption vs maskingUlf Mattsson
?
Compare Vaultless tokenization to other tokenization approaches
No data replication/collision issues ¨C guaranties data integrity, no data corruption, allows parallel computing across many servers and location
High scalability and performance
Cryptographysecurity 1222867498937700-9



Cryptographysecurity 1222867498937700-9muthulx
?
This document provides an overview of cryptography, including its history, applications, challenges, and references. It discusses cryptography concepts like ciphertext, plaintext, keys, symmetric and asymmetric algorithms. It covers security requirements like confidentiality, integrity, and authentication. Applications mentioned include protecting ATM transactions, smart cards, cryptography application blocks, and watermarking. Challenges discussed include potential loss of privacy as networks become more digital. Cryptography plays an important role in security for business, e-commerce, banking, the military, and more.CLASS 2022 - Felipe Jord?o (Palo Alto Networks) - Boas pr¨˘ticas de opera??es ...



CLASS 2022 - Felipe Jord?o (Palo Alto Networks) - Boas pr¨˘ticas de opera??es ...TI Safe
?
This document discusses best practices for operational technology (OT) security in a hyperconnected world. It outlines the current cybersecurity challenges faced by industries due to expanding attack surfaces and evolving threats. It recommends establishing pillars like segmentation, zero trust, and access control policies based on users to protect OT environments. The document also describes implementing a next-generation firewall, multi-factor authentication, endpoint security, event correlation and response workflows to enhance industrial cybersecurity.Resilient IoT Security: The end of flat security models



Resilient IoT Security: The end of flat security modelsMilosch Meriac
?
Compartmentalizing code and data on low-end MMU-less microcontrollers using the ARM memory protection unit as available on present ARM Cortex-M3 and ARM Cortex-M4 devices.
More information and source code is available at https://github.com/ARMmbed/uvisor . This slideset was presented in November at ARM TechCon 2015.ϵ˝y02_ęPćIµÄˇ¸ĚŘ™ŕ+ŮYÁĎ°˛Č«ˇą×îááŇ»Á¨·Ŕľ€ ˝âÖŇş˛



ϵ˝y02_ęPćIµÄˇ¸ĚŘ™ŕ+ŮYÁĎ°˛Č«ˇą×îááŇ»Á¨·Ŕľ€ ˝âÖŇş˛Galaxy Software Services
?
This document discusses several topics related to privileged account management and file transfer security. It notes that organizations typically have 3-4x more privileged accounts than employees. It also provides guidance on properly securing and managing cryptographic keys according to PCI compliance standards. Finally, it outlines recommendations for strengthening file transfer processes, such as establishing a centralized file transfer management platform, improving file access controls, integrating user authentication with AD, and controlling privileged account passwords.Cryptography&Security



Cryptography&SecuritySanjeev Kumar Jaiswal
?
The document discusses cryptography and its applications in security. It covers topics like encryption, decryption, digital signatures, hash algorithms, and their roles in providing confidentiality, integrity and authentication. It also discusses challenges like protecting ATM transactions and discusses the role of cryptography in applications like smart cards, secure cryptoprocessors and watermarking. In the end, it emphasizes the growing importance of cryptography in ensuring privacy and security in the digital world.MITRE-Module 4 şÝşÝߣs.pdf



MITRE-Module 4 şÝşÝߣs.pdfReZa AdineH
?
The document discusses various ways that threat intelligence data mapped to the MITRE ATT&CK framework can be stored and analyzed. It provides examples of how ATT&CK techniques have been included in security reports and notes that the community is still exploring the best methods and formats for capturing and linking ATT&CK data to other information like indicators. The goal is to be able to make defensive recommendations by analyzing stored ATT&CK-mapped intelligence.Security as a top of mind issue for mobile application development



Security as a top of mind issue for mobile application development?tefan Popa
?
Mobile technologies bring to life new capabilities and opportunities for consumers all around the world. However, the advent of mobile has also resulted in new points of attack for hackers. This presentation it's about how to assess security vulnerabilities in the development process, and how to deliver high-performing applications that provide functionality with security in mind.Designing Secure APIs



Designing Secure APIsSteven Chen
?
APIs are the building blocks of interoperability on the web and are a key component of scalable and successful technology companies. As externally-consumable APIs expose more information and functionality, ensuring privacy and security of customer data is an increasingly risky proposition. In this session, weˇŻll talk about some of SlackˇŻs learnings around building Developer APIs and best practices for keeping your APIs safe.
şÝşÝߣs originally for a presentation at the Rocky Mountain Technology Summit. Slightly reduced content.
Qark DefCon 23



Qark DefCon 23?Tony Trummer?
?
QARK is a tool created by LinkedIn penetration testers Tony Trummer and Tushar Dalvi to audit Android apps for security issues. It uses multiple decompilers and techniques to analyze app structure, find data flows between sources and sinks, and check for vulnerabilities related to permissions, webviews, intents, and cryptography. The goal is to help developers identify and address bugs before release by automating some security checks and providing exploit code. Future plans include dynamic analysis, Smali inspection, and other improvements to make the tool more extensive and extensible.Architecture vulnerabilities in?SAP?platforms



Architecture vulnerabilities in?SAP?platformsERPScan
?
SAP security becomes a hot theme nowadays. Attacks on SAP can put a business at risk of Espionage, Sabotage and Fraud.
The presentation covers the following architecture and unusual issues:
Authentication Bypass
1. Verb tampering
2. Invoker servlet
Encryption
3. Storage ¨C SAPGUI
4. Authentication ¨C P4
5. Transfer ¨C RFC, Diag
SSRF
6. Port Scan
7. Command execution
8. Security bypass
Also, the presentation gives advice for developers and describes future trends in SAP Security area.PPT 1.pptx



PPT 1.pptxIvar35
?
This document outlines the phases of developing a healthcare network system, including:
1) Conducting a feasibility study to assess the technical, economic, legal, and operational feasibility.
2) Gathering requirements and analyzing them to design the network infrastructure to securely transmit data and efficiently manage patient records with emergency response and telemedicine capabilities.
3) Implementing the design through coding, testing, deploying, and maintaining the system according to the software development life cycle (SDLC).PCI DSS v 3.0 and Oracle Security Mapping



PCI DSS v 3.0 and Oracle Security MappingTroy Kitch
?
This document discusses helping customers comply with PCI DSS v3.0 requirements for payment card security. It provides an overview of the history of payments, reasons for PCI standards due to losses from security breaches, details of PCI requirements and levels based on transaction volume, and capabilities of Oracle products to address key requirements such as encrypting stored data and restricting access. Real-world examples of Oracle customers SquareTwo Financial and TransUnion are also presented that secured cardholder data and addressed compliance needs using Oracle technologies.Using hypervisor and container technology to increase datacenter security pos...



Using hypervisor and container technology to increase datacenter security pos...Tim Mackey
?
As presented at LinuxCon/ContainerCon 2016:
Cyber threats consistently rank as a high priority for data center operators and their reliability teams. As increasingly sophisticated attacks mount, the risk associated with a zero-day attack is significant. Traditional responses include perimeter monitoring and anti-malware agents. Unfortunately, those techniques introduce performance and management challenges when used at large VM densities, and may not work well with containerized applications.
Fortunately, the Xen Project community has collaborated to create a solution which reduces the potential of success associated with rootkit attack vectors. When combined with recent advancements in processor capabilities, and secure development models for container deployment, itˇŻs possible to both protect against and be proactively alerted to potential zero-day attacks. In this session, weˇŻll cover models to limit the scope of compromise should an attack be mounted against your infrastructure. Two attack vectors will be illustrated, and weˇŻll see how itˇŻs possible to be proactively alerted to potential zero-day actions without requiring significant reconfiguration of your datacenter environment.
Technology elements explored include those from Black Duck, Bitdefender, Citrix, Intel and Guardicore. Using hypervisor and container technology to increase datacenter security pos...



Using hypervisor and container technology to increase datacenter security pos...Black Duck by Synopsys
?
As presented by Tim Mackey, Senior Technical Evangelist - Black Duck Software, at LinuxCon/ContainerCon 2016:
Cyber threats consistently rank as a high priority for data center operators and their reliability teams. As increasingly sophisticated attacks mount, the risk associated with a zero-day attack is significant. Traditional responses include perimeter monitoring and anti-malware agents. Unfortunately, those techniques introduce performance and management challenges when used at large VM densities, and may not work well with containerized applications.
Fortunately, the Xen Project community has collaborated to create a solution which reduces the potential of success associated with rootkit attack vectors. When combined with recent advancements in processor capabilities, and secure development models for container deployment, itˇŻs possible to both protect against and be proactively alerted to potential zero-day attacks. In this session, weˇŻll cover models to limit the scope of compromise should an attack be mounted against your infrastructure. Two attack vectors will be illustrated, and weˇŻll see how itˇŻs possible to be proactively alerted to potential zero-day actions without requiring significant reconfiguration of your datacenter environment.
Technology elements explored include those from Black Duck, Bitdefender, Citrix, Intel and Guardicore. 2019_USA RSAConference_stir-shake-n-sip-to-stop-robocalling.pdf



2019_USA RSAConference_stir-shake-n-sip-to-stop-robocalling.pdfLilminow
?
Cybercriminals are eroding trust in voice services with 5.1 billion robocalls a month duping consumers with phone scams. The robocall strike-force has socialized the STIR/Shaken (Secure Telephony Identity Revisited/Signature-based handling of Asserted Information using tokens) framework to combat robocalling. Learn about the framework, limitations and security architectures for robust implementation.
Learning Objectives:
1: Become part of the cybersecurity community that is aware of voice crime specifically robocalling.
2: Review the framework that many service providers are working on to thwart.
3: Support your voice professional counterparts in implementing secure architectures.Big Data security: Facing the challenge by Carlos G¨®mez at Big Data Spain 2017



Big Data security: Facing the challenge by Carlos G¨®mez at Big Data Spain 2017Big Data Spain
?
This talk gives a technical and innovative overview of how companies can face the challenge of protecting the data and services that are in their data-centric platform, focusing on three main aspects: implementing network segmentation, managing AAA and securing data processing.
https://www.bigdataspain.org/2017/talk/big-data-security-facing-the-challenge
Big Data Spain 2017
16th - 17th November Kin¨¦polis MadridData Encryption at Rest



Data Encryption at RestAll Things Open
?
Valerie Parham-Thompson
Lead Database Consultant with Pythian
Find more by Valerie Parham-Thompson: https://speakerdeck.com/dataindataout
All Things Open
October 26-27, 2016
Raleigh, North CarolinaAnalysis of Security and Compliance using Oracle SPARC T-Series Servers: Emph...



Analysis of Security and Compliance using Oracle SPARC T-Series Servers: Emph...Ramesh Nagappan
?
This document discusses security and compliance using Oracle SPARC T-Series servers. It provides an overview of the security technologies including on-chip cryptographic accelerators. It explores how the accelerators enable encryption and the role of the Solaris crypto framework. Examples of applying encryption to Oracle database and middleware are discussed. The performance benefits of using the accelerators are shown. Finally, how the servers can help achieve compliance goals like HIPAA and PCI-DSS is described.The nature of technolog and Computer networks.pptx



The nature of technolog and Computer networks.pptxvallidevi6
?
Usefu for Grade 5 Cambridge Computing studentsCSUN 2025 - Interactive Charts for Everyone.pptx



CSUN 2025 - Interactive Charts for Everyone.pptx?ystein Moseng
?
şÝşÝߣs from our presentation on accessible, interactive charts, at CSUN 2025.More Related Content
Similar to Vault Associate Certification Internals (20)
Hardening Your Config Management - Security and Attack Vectors in Config Mana...



Hardening Your Config Management - Security and Attack Vectors in Config Mana...Peter Souter
?
Configuration management is a great tool for helping with hardening and securing servers. But with any addition of new technology comes a new attack vector: Who watches the watchers?
Security is painful. Luckily the invention of configuration management tools has made this process easier, by allowing repeatable configuration for common hardening. However there comes a catch-22: How do we harden the configuration management itself?
When you have a tool that enables you to change systems at a fundamental level, it's a fairly tempting target for malicious agents, and one that would cause a lot of problems if compromised.
We'll be discussing some general patterns we can use to mitigate these problems: - Whitelisting "master" API's - Encrypting sensitive data - Adding a security element to code review
And we'll talk about some application specific options for some of most popular tools out there, such as Puppet, Chef, Ansible, cfengine and Salt.Tokenization vs encryption vs masking



Tokenization vs encryption vs maskingUlf Mattsson
?
Compare Vaultless tokenization to other tokenization approaches
No data replication/collision issues ¨C guaranties data integrity, no data corruption, allows parallel computing across many servers and location
High scalability and performance
Cryptographysecurity 1222867498937700-9



Cryptographysecurity 1222867498937700-9muthulx
?
This document provides an overview of cryptography, including its history, applications, challenges, and references. It discusses cryptography concepts like ciphertext, plaintext, keys, symmetric and asymmetric algorithms. It covers security requirements like confidentiality, integrity, and authentication. Applications mentioned include protecting ATM transactions, smart cards, cryptography application blocks, and watermarking. Challenges discussed include potential loss of privacy as networks become more digital. Cryptography plays an important role in security for business, e-commerce, banking, the military, and more.CLASS 2022 - Felipe Jord?o (Palo Alto Networks) - Boas pr¨˘ticas de opera??es ...



CLASS 2022 - Felipe Jord?o (Palo Alto Networks) - Boas pr¨˘ticas de opera??es ...TI Safe
?
This document discusses best practices for operational technology (OT) security in a hyperconnected world. It outlines the current cybersecurity challenges faced by industries due to expanding attack surfaces and evolving threats. It recommends establishing pillars like segmentation, zero trust, and access control policies based on users to protect OT environments. The document also describes implementing a next-generation firewall, multi-factor authentication, endpoint security, event correlation and response workflows to enhance industrial cybersecurity.Resilient IoT Security: The end of flat security models



Resilient IoT Security: The end of flat security modelsMilosch Meriac
?
Compartmentalizing code and data on low-end MMU-less microcontrollers using the ARM memory protection unit as available on present ARM Cortex-M3 and ARM Cortex-M4 devices.
More information and source code is available at https://github.com/ARMmbed/uvisor . This slideset was presented in November at ARM TechCon 2015.ϵ˝y02_ęPćIµÄˇ¸ĚŘ™ŕ+ŮYÁĎ°˛Č«ˇą×îááŇ»Á¨·Ŕľ€ ˝âÖŇş˛



ϵ˝y02_ęPćIµÄˇ¸ĚŘ™ŕ+ŮYÁĎ°˛Č«ˇą×îááŇ»Á¨·Ŕľ€ ˝âÖŇş˛Galaxy Software Services
?
This document discusses several topics related to privileged account management and file transfer security. It notes that organizations typically have 3-4x more privileged accounts than employees. It also provides guidance on properly securing and managing cryptographic keys according to PCI compliance standards. Finally, it outlines recommendations for strengthening file transfer processes, such as establishing a centralized file transfer management platform, improving file access controls, integrating user authentication with AD, and controlling privileged account passwords.Cryptography&Security



Cryptography&SecuritySanjeev Kumar Jaiswal
?
The document discusses cryptography and its applications in security. It covers topics like encryption, decryption, digital signatures, hash algorithms, and their roles in providing confidentiality, integrity and authentication. It also discusses challenges like protecting ATM transactions and discusses the role of cryptography in applications like smart cards, secure cryptoprocessors and watermarking. In the end, it emphasizes the growing importance of cryptography in ensuring privacy and security in the digital world.MITRE-Module 4 şÝşÝߣs.pdf



MITRE-Module 4 şÝşÝߣs.pdfReZa AdineH
?
The document discusses various ways that threat intelligence data mapped to the MITRE ATT&CK framework can be stored and analyzed. It provides examples of how ATT&CK techniques have been included in security reports and notes that the community is still exploring the best methods and formats for capturing and linking ATT&CK data to other information like indicators. The goal is to be able to make defensive recommendations by analyzing stored ATT&CK-mapped intelligence.Security as a top of mind issue for mobile application development



Security as a top of mind issue for mobile application development?tefan Popa
?
Mobile technologies bring to life new capabilities and opportunities for consumers all around the world. However, the advent of mobile has also resulted in new points of attack for hackers. This presentation it's about how to assess security vulnerabilities in the development process, and how to deliver high-performing applications that provide functionality with security in mind.Designing Secure APIs



Designing Secure APIsSteven Chen
?
APIs are the building blocks of interoperability on the web and are a key component of scalable and successful technology companies. As externally-consumable APIs expose more information and functionality, ensuring privacy and security of customer data is an increasingly risky proposition. In this session, weˇŻll talk about some of SlackˇŻs learnings around building Developer APIs and best practices for keeping your APIs safe.
şÝşÝߣs originally for a presentation at the Rocky Mountain Technology Summit. Slightly reduced content.
Qark DefCon 23



Qark DefCon 23?Tony Trummer?
?
QARK is a tool created by LinkedIn penetration testers Tony Trummer and Tushar Dalvi to audit Android apps for security issues. It uses multiple decompilers and techniques to analyze app structure, find data flows between sources and sinks, and check for vulnerabilities related to permissions, webviews, intents, and cryptography. The goal is to help developers identify and address bugs before release by automating some security checks and providing exploit code. Future plans include dynamic analysis, Smali inspection, and other improvements to make the tool more extensive and extensible.Architecture vulnerabilities in?SAP?platforms



Architecture vulnerabilities in?SAP?platformsERPScan
?
SAP security becomes a hot theme nowadays. Attacks on SAP can put a business at risk of Espionage, Sabotage and Fraud.
The presentation covers the following architecture and unusual issues:
Authentication Bypass
1. Verb tampering
2. Invoker servlet
Encryption
3. Storage ¨C SAPGUI
4. Authentication ¨C P4
5. Transfer ¨C RFC, Diag
SSRF
6. Port Scan
7. Command execution
8. Security bypass
Also, the presentation gives advice for developers and describes future trends in SAP Security area.PPT 1.pptx



PPT 1.pptxIvar35
?
This document outlines the phases of developing a healthcare network system, including:
1) Conducting a feasibility study to assess the technical, economic, legal, and operational feasibility.
2) Gathering requirements and analyzing them to design the network infrastructure to securely transmit data and efficiently manage patient records with emergency response and telemedicine capabilities.
3) Implementing the design through coding, testing, deploying, and maintaining the system according to the software development life cycle (SDLC).PCI DSS v 3.0 and Oracle Security Mapping



PCI DSS v 3.0 and Oracle Security MappingTroy Kitch
?
This document discusses helping customers comply with PCI DSS v3.0 requirements for payment card security. It provides an overview of the history of payments, reasons for PCI standards due to losses from security breaches, details of PCI requirements and levels based on transaction volume, and capabilities of Oracle products to address key requirements such as encrypting stored data and restricting access. Real-world examples of Oracle customers SquareTwo Financial and TransUnion are also presented that secured cardholder data and addressed compliance needs using Oracle technologies.Using hypervisor and container technology to increase datacenter security pos...



Using hypervisor and container technology to increase datacenter security pos...Tim Mackey
?
As presented at LinuxCon/ContainerCon 2016:
Cyber threats consistently rank as a high priority for data center operators and their reliability teams. As increasingly sophisticated attacks mount, the risk associated with a zero-day attack is significant. Traditional responses include perimeter monitoring and anti-malware agents. Unfortunately, those techniques introduce performance and management challenges when used at large VM densities, and may not work well with containerized applications.
Fortunately, the Xen Project community has collaborated to create a solution which reduces the potential of success associated with rootkit attack vectors. When combined with recent advancements in processor capabilities, and secure development models for container deployment, itˇŻs possible to both protect against and be proactively alerted to potential zero-day attacks. In this session, weˇŻll cover models to limit the scope of compromise should an attack be mounted against your infrastructure. Two attack vectors will be illustrated, and weˇŻll see how itˇŻs possible to be proactively alerted to potential zero-day actions without requiring significant reconfiguration of your datacenter environment.
Technology elements explored include those from Black Duck, Bitdefender, Citrix, Intel and Guardicore. Using hypervisor and container technology to increase datacenter security pos...



Using hypervisor and container technology to increase datacenter security pos...Black Duck by Synopsys
?
As presented by Tim Mackey, Senior Technical Evangelist - Black Duck Software, at LinuxCon/ContainerCon 2016:
Cyber threats consistently rank as a high priority for data center operators and their reliability teams. As increasingly sophisticated attacks mount, the risk associated with a zero-day attack is significant. Traditional responses include perimeter monitoring and anti-malware agents. Unfortunately, those techniques introduce performance and management challenges when used at large VM densities, and may not work well with containerized applications.
Fortunately, the Xen Project community has collaborated to create a solution which reduces the potential of success associated with rootkit attack vectors. When combined with recent advancements in processor capabilities, and secure development models for container deployment, itˇŻs possible to both protect against and be proactively alerted to potential zero-day attacks. In this session, weˇŻll cover models to limit the scope of compromise should an attack be mounted against your infrastructure. Two attack vectors will be illustrated, and weˇŻll see how itˇŻs possible to be proactively alerted to potential zero-day actions without requiring significant reconfiguration of your datacenter environment.
Technology elements explored include those from Black Duck, Bitdefender, Citrix, Intel and Guardicore. 2019_USA RSAConference_stir-shake-n-sip-to-stop-robocalling.pdf



2019_USA RSAConference_stir-shake-n-sip-to-stop-robocalling.pdfLilminow
?
Cybercriminals are eroding trust in voice services with 5.1 billion robocalls a month duping consumers with phone scams. The robocall strike-force has socialized the STIR/Shaken (Secure Telephony Identity Revisited/Signature-based handling of Asserted Information using tokens) framework to combat robocalling. Learn about the framework, limitations and security architectures for robust implementation.
Learning Objectives:
1: Become part of the cybersecurity community that is aware of voice crime specifically robocalling.
2: Review the framework that many service providers are working on to thwart.
3: Support your voice professional counterparts in implementing secure architectures.Big Data security: Facing the challenge by Carlos G¨®mez at Big Data Spain 2017



Big Data security: Facing the challenge by Carlos G¨®mez at Big Data Spain 2017Big Data Spain
?
This talk gives a technical and innovative overview of how companies can face the challenge of protecting the data and services that are in their data-centric platform, focusing on three main aspects: implementing network segmentation, managing AAA and securing data processing.
https://www.bigdataspain.org/2017/talk/big-data-security-facing-the-challenge
Big Data Spain 2017
16th - 17th November Kin¨¦polis MadridData Encryption at Rest



Data Encryption at RestAll Things Open
?
Valerie Parham-Thompson
Lead Database Consultant with Pythian
Find more by Valerie Parham-Thompson: https://speakerdeck.com/dataindataout
All Things Open
October 26-27, 2016
Raleigh, North CarolinaAnalysis of Security and Compliance using Oracle SPARC T-Series Servers: Emph...



Analysis of Security and Compliance using Oracle SPARC T-Series Servers: Emph...Ramesh Nagappan
?
This document discusses security and compliance using Oracle SPARC T-Series servers. It provides an overview of the security technologies including on-chip cryptographic accelerators. It explores how the accelerators enable encryption and the role of the Solaris crypto framework. Examples of applying encryption to Oracle database and middleware are discussed. The performance benefits of using the accelerators are shown. Finally, how the servers can help achieve compliance goals like HIPAA and PCI-DSS is described.Using hypervisor and container technology to increase datacenter security pos...



Using hypervisor and container technology to increase datacenter security pos...Black Duck by Synopsys
?
Recently uploaded (20)
The nature of technolog and Computer networks.pptx



The nature of technolog and Computer networks.pptxvallidevi6
?
Usefu for Grade 5 Cambridge Computing studentsCSUN 2025 - Interactive Charts for Everyone.pptx



CSUN 2025 - Interactive Charts for Everyone.pptx?ystein Moseng
?
şÝşÝߣs from our presentation on accessible, interactive charts, at CSUN 2025.Software-Engineering-and-Best-Practices.



Software-Engineering-and-Best-Practices.oziasrondonc
?
Software engineering is more than just writing codeˇŞitˇŻs about building scalable, maintainable, and efficient applications. This presentation explores the best practices in software engineering, including coding standards, version control, testing strategies, agile methodologies, and DevOps integration. Learn how to enhance code quality, improve team collaboration, and optimize the software development lifecycle for long-term success."Constructive Interaction During Emotional Burnout: With Local and Internatio...



"Constructive Interaction During Emotional Burnout: With Local and Internatio...Fwdays
?
One of the biggest challenges in workplace communication is expressing dissatisfaction and providing feedback. Over 50% of misunderstandings arise in these situations, regardless of the project. Add emotional burnout and cultural differences, and the consequences can become serious.
In his speech, Alexey will tell share feedback tools that work effectively for IT professionals. He will explore why many cultures struggle with giving and receiving constructive criticism and how fundamental argumentation principles, combined with simple empathy-based techniques, can help prevent more than half of potential conflicts.UiPath Automation Developer Associate Training Series 2025 - Session 6



UiPath Automation Developer Associate Training Series 2025 - Session 6DianaGray10
?
Welcome to session 6 where we will cover Error and Exceptional handling, along with Debugging Studio and an Introduction to Logging in Studio.
The required self-paced lessons that you need to complete are here:
Error and Exception Handling in Studio, Debugging in Studio, Introduction to Logging in Studio - 2 modules - 1h 15m - https:/academy.uipath.com/courses/error-and-exception-handling-in-studio
Debugging in Studio - 2 modules - 2h - https:/academy.uipath.com/courses/debugging-in-studio
Introduction to Logging in Studio - 2 modules - 1h 15m - https:/academy.uipath.com/courses/introduction-to-logging-in-studioBlending AI in Enterprise Architecture.pdf



Blending AI in Enterprise Architecture.pdfCalvin Hendryx-Parker
?
C-level executives, directors, and product managers face the complex task of integrating AI into existing systems while addressing challenges related to data quality, scalability, interoperability, ethics, skill gaps, and security compliance.
Join Calvin Hendryx-Parker ˇŞ AWS Hero and CTO of Six Feet Up, the premier AI and Python agency in the U.S. ˇŞ for this interactive talk exploring generative AI technologies. YouˇŻll gain ready-to-use resources and a clear understanding of how to roll out AI in your organization.
What YouˇŻll Learn:
AI Implementation Strategies: Get practical tips on evaluating and integrating open source and closed AI models, addressing governance, compliance, and scalability.
Real-Case Demo: Explore what it takes to leverage generative AI technology using RAG.
Team Enablement: Discover how other companies are fostering innovation internally.
Walk away with the tools and insights you need to confidently lead your organizationˇŻs AI journey.Salesforce Welly March 2025User Group Meeting



Salesforce Welly March 2025User Group MeetingAnna Loughnan Colquhoun
?
This is the expanded slide deck from the Salesforce Wellington user group lunchtime meeting hosted by Forsyth Barr March 19, 2025.
Presentations were from Forsyth Barr, showing the Tempo app, as well as Katie Connors, Daneen Johnson and Anna Loughnan. Carl Thomas presented prizes for the Uppern Echeleon sponsored photo booth from our Xmas gathering[QUICK TALK] "Coaching 101: How to Identify and Develop Your Leadership Quali...![[QUICK TALK] "Coaching 101: How to Identify and Develop Your Leadership Quali...](https://cdn.slidesharecdn.com/ss_thumbnails/softskillsfwdays25ilonalesko-250317075721-cb56ed6c-thumbnail.jpg?width=560&fit=bounds)
![[QUICK TALK] "Coaching 101: How to Identify and Develop Your Leadership Quali...](https://cdn.slidesharecdn.com/ss_thumbnails/softskillsfwdays25ilonalesko-250317075721-cb56ed6c-thumbnail.jpg?width=560&fit=bounds)
![[QUICK TALK] "Coaching 101: How to Identify and Develop Your Leadership Quali...](https://cdn.slidesharecdn.com/ss_thumbnails/softskillsfwdays25ilonalesko-250317075721-cb56ed6c-thumbnail.jpg?width=560&fit=bounds)
![[QUICK TALK] "Coaching 101: How to Identify and Develop Your Leadership Quali...](https://cdn.slidesharecdn.com/ss_thumbnails/softskillsfwdays25ilonalesko-250317075721-cb56ed6c-thumbnail.jpg?width=560&fit=bounds)
[QUICK TALK] "Coaching 101: How to Identify and Develop Your Leadership Quali...Fwdays
?
What does it mean to be a leader, and what qualities should you develop in yourself? And how do you know if you even have these skills? This isnˇŻt just a questionˇŞitˇŻs the key to understanding where to start and how to move forward in unlocking your potential.
LetˇŻs break down leadership and coaching as a tool for unleashing your leadership potential. WeˇŻll explore how coaching differs from mentoring, psychotherapy, and trainingˇŞand why theyˇŻre not all the same. Special focus will be on self-coaching: learning to engage in an internal dialogue so you can keep moving forward even when external support is lacking.
IˇŻll share a few practical life hacks and real-world examples that will help you create a plan and start taking action as soon as tomorrow.WSO2Con 2025 - Architecting Cloud-Native Applications



WSO2Con 2025 - Architecting Cloud-Native ApplicationsWSO2
?
As enterprises modernise their technology stacks, designing platform-agnostic, scalable, and well-governed cloud-native architectures is essential for long-term success. This lab session will explore how to apply the platformless concept to build cloud-native applications that offer flexibility, portability, and resilience across diverse cloud environments.
Through guided discussions and real-world insights, we will examine key architectural patterns, including microservices, API gateways, and Kubernetes orchestration, while addressing critical aspects such as scalability, governance, and operational efficiency.
Join us to exchange ideas, refine best practices, and explore strategies for architecting cloud-native applications that are future-proof, scalable, and effectively governed.Columbia Weather Systems - Product Overview



Columbia Weather Systems - Product OverviewColumbia Weather Systems
?
Columbia Weather Systems offers professional weather stations in basically three configurations for industry and government agencies worldwide: Fixed-Base or Fixed-Mount Weather Stations, Portable Weather Stations, and Vehicle-Mounted Weather Stations.
Models include all-in-one sensor configurations as well as modular environmental monitoring systems. Real-time displays include hardware console, WeatherMaster? Software, and a Weather MicroServer? with industrial protocols, web and app monitoring options.
Innovative Weather Monitoring: Trusted by industry and government agencies worldwide. Professional, easy-to-use monitoring options. Customized sensor configurations. One-year warranty with personal technical support. Proven reliability, innovation, and brand recognition for over 45 years.Slack Social Meetup Connect, Collaborate & Grow!.pptx



Slack Social Meetup Connect, Collaborate & Grow!.pptxSanjeetMishra29
?
Slack Community - Patna - In-Person Event"Conflicts within a Team: Not an Enemy, But an Opportunity for Growth", Orest...



"Conflicts within a Team: Not an Enemy, But an Opportunity for Growth", Orest...Fwdays
?
Conflicts within a team are not always a bad sign. On the contrary, they can become a powerful tool for development. In this talk, Orest will share my experience and practical tools for resolving conflicts constructively, which help not only maintain harmony in the team but also improve its overall performance. You will learn how to turn conflicts into opportunities to strengthen team bonds, enhance communication skills, and achieve better results.Think Like and Architect Series: Session 1 of 9 Declarative Design



Think Like and Architect Series: Session 1 of 9 Declarative DesignWalter Spinrad
?
1st of 9 in a series sharing my thoughts on what it takes to be an architect in the Salesforce ecosystem. I will be sharing from experience as a Salesforce CTA in the ecosystem for 17 years. UiPath Automation Developer Associate Training Series 2025 - Session 5



UiPath Automation Developer Associate Training Series 2025 - Session 5DianaGray10
?
In this session, we will cover Excel automation and Email automation.
The self-paced lessons required for this session are:
Excel Automation with the Modern Experience in Studio - 2 modules - 1h 45m - https:/academy.uipath.com/courses/excel-automation-with-the-modern-experience-in-studio
Email Automation With Studio - 2 modules - 1h 45m - https:/academy.uipath.com/courses/email-automation-with-studio
Project Organization in Studio - 2 modules - 2h - https:/academy.uipath.com/courses/project-organization-in-studio
?? For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. WSO2Con 2025 - How an Internal Developer Platform Lets Developers Focus on Code



WSO2Con 2025 - How an Internal Developer Platform Lets Developers Focus on CodeWSO2
?
Cloud-native development often involves setting up infrastructure, managing security, and integrating servicesˇŞtasks that take time away from coding. An internal developer platform (IDP) streamlines these complexities, enabling developers to focus on building business logic.
This lab demonstrates how an IDP supports a hybrid development approach, where developers run some components locally while consuming cloud services seamlessly. Instead of manually configuring databases, authentication, or API gateways, they leverage platform capabilities for rapid iteration.
WeˇŻll walk through a real-world scenario where a developer:
Onboards quickly with an architect-defined application structure.
Develops in a hybrid environment, consuming cloud APIs, databases, and AI services while iterating locally.
Uses Choreo-managed authentication without dealing with OAuth2 intricacies.
Discovers and reuses microservices and APIs instead of rebuilding them.
Debugs efficiently without deploying all dependencies locally.
Ensures security and compliance automatically, catching vulnerabilities early.
By the end, youˇŻll see how an IDP accelerates onboarding, enhances security, and simplifies cloud-native developmentˇŞso developers can focus on building great applications instead of managing infrastructure."AI-Driven Automation for High-Performing Teams: Optimize Routine Tasks & Lea...



"AI-Driven Automation for High-Performing Teams: Optimize Routine Tasks & Lea...Fwdays
?
Every day, managers and team leads face numerous routine tasks: creating and updating issues in Jira, running meetings, syncing the team, handling retrospectives, and managing documentation. Most of these processes take up valuable time that could be spent on strategic leadership and team development.
In this talk, I will show how AI can optimize team processes, automate routine tasks, and make workflows more efficient. You will learn how AI enhances Scrum processes and helps streamline team management.
I will also share my experience in automating workflows in Jira and Slack: how to reduce manual work with simple automation rules, set up automatic notifications for blockers, generate Confluence pages, track team productivity, and extract valuable insights. What will you gain from this talk??Redefining Efficiency in AI: The Impact of 1.58-bit LLMs on the Future of Com...



Redefining Efficiency in AI: The Impact of 1.58-bit LLMs on the Future of Com...Gregor Lyttek
?
This whitepaper examines how emerging 1.58-bit quantization approaches, exemplified by BitNet b1.58, address critical challenges in LLM deployment without compromising model performance. Our analysis demonstrates up to 65% reduction in energy consumption, 72% decrease in memory footprint, and inference speed improvements of 2.71x compared to traditional models. We present a comprehensive implementation framework for organizations seeking to balance computational efficiency with AI performance objectives.Vault Associate Certification Internals
- 4. OVERVIEW THESE NOTES FOLLOW HASHICORP SPECIFIC STRUCTURE FOUND HERE s HTTP www.VAVLTPROJECT.IO Docs INTERNALS SECURITY OVERVIEW ARCHITECTURE PROPERTIES FUNCTIONS WHAT IS VAULT eggs EffFE sAEEffffs TIGHTSECURITY CONTROLS AUDIT LOGS L v s API keys PASSWORDS CERTS
- 5. FEATURES SECURE 1 SECRET SECRET ENCRYPTION STORAGE STORAGE PROVIDETEMPACCESS to APP 2 DYNAMIC 4 SECRETS r 3 I I NEED v ACCESS GENERATE ENCRYPT ENCRYPT AND DATA ENCRYPTION i DATA DECRYPT WITHOUT DECRYPT STORINGINVAULT LEASING AND a REVOCATION SECRETRENEWAL ALLSECRETSHAVE Ability toRevokeLEASEASSOCIATED entiretree of secrets
- 6. ARCHITECTURE HTTPS IAPI TOKENSTORE POLICYSTORE AUDIT CORE ROLLBACKMGR EXPIRATIONMGR BROKER d AUDITw PATH ROUTING DEVICE A SYSTEM SECRET AUTH AUDIT BACKEND ENGINE METHOD DEVICE STORAGEBACKEND 0 HTTPS API EXTERNALFACING t BARRIER Vault Startsin Sealed state 1 MustUnseal Mustbe How Unsealed V Unsealkeys Alldata to Howsthrough SHAMIR'SSECRETSHARING Algorithm cryptographic barrier seal
- 7. SHAMIRS SECRET SHARING ALGORITHM ENCRYPTION MASTER KEY KEY SHARES s I 2 ABLETO DECRYPT DATA L ENTERUIVSEALED STORAGE STATE BACKEND UNSEALED Loads all audit devices Auth methods VAULT Secrets Engines ONCEUNSEALED REQUESTSCANBE Managethe flow of requestsPROCESSEDBYTHE CORE CORE Enforce ACLs Audit logging
- 8. I 1 Authentication O CORE MA f D 2 RETURN LIST OF POLICIES Named ACLS VAULT OPERATES EXCLUSIVELY IN WHITELIST MODE Access must be explicitly granted 2 O o or my TOKEN STORE HERE AREMY 1 CLIENTTOKENGENERATED f POLICIES j ATTACH LEASE 0 I f REQUEST SECRET CORE 2 SECRET ENGINE IIFiiiIIII N r CLIENT TOKEN I'MTelling 4 i.e Returning Secret EXPIRATION MANAGER 3 Attaching lease ID
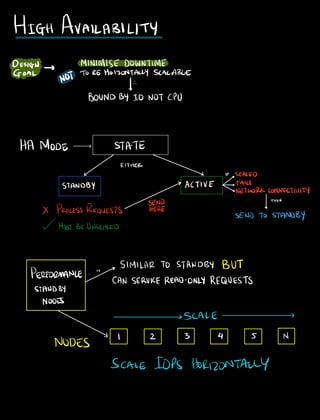
- 9. HIGH AVAILABILITY DESIGN MINIMISE DOWNTIME GOAL NOT TO BE140120NTALLY SCALABLE BOUND13410 NOT CPU HA MODE STATE EITHER L J IF aSEALED STANDBY 7 ACTIVE FAILS NETWORKCONNECTIVITY SEND THEN X PROCESSREQUESTS HERE v SEND TO STANDBY MUST BEUNSEALED PERFORMANCE is SIMILAR TO STANDBY BUT STANDBY CAN SERVICEREADONLY REQUESTS NODES SCALE NODES I 2 3 4 5 V SCALE IOPS HORIZONTALLY
- 10. INTEGRATED STORAGE VAULT INTEGRATED STORAGE t l t l t l v s 17A REPLICATION BACKUPAND RESTORE WORKFLOWS RAFT CONSENSUS PROTOCOL BASED ONPAXOS BUTSIMPLER CANSOMEONE EeiiEIIIIII VOTEFORME tfIfD Ok PEERNODE NODE START CANDIDATE STATE I WILLPROMOTE MYSELF te Np LEADERGREAT I CANACCEPT FOLLOWER IDEA STATE LOG ENTRIES STATE FROM A LEADER ICANACCEPTNEW GENTRIES AND I CAN VOTE REPLICATE TO ALLTHEOTHER FOLLOWERS NO ENTRIES FOR AWHILE
- 11. RAFT CONSENSUS PROTOCOL CONTINUED LEADER CLIENT REQUEST 1 APPEND A NEW LOG ENTRY 2 REPLICATE TO STORAGE FOLLOWERS 3QUORUM COMMITTED GO KEY VALUE Collection offinite STORE Stateswithtrasitions FINITE betweenthemAsnew STATE logsare appliedFSMis MACHINE allowedtotransitionbetween BOLTDB StatesApplicationoflogs Mustresultinthesamestate Deterministic This is the FSM AllowsVault whichmaintains snapshots to be cluster state very lightweight RECOMMENDED I 2 3 4 5 3 or 5 NODES DUE TOQUORUM
- 12. CONFIDENTIALITY SECURITY MODEL INTEGRITY AVAILABILITY ACCOUNTABILITY AUTHENTICATION EAVESDROPPING CONFIDENTIALITY OF STORED SECRETS 9 TAMPERING WITHDATA HREAT MODEL ACCESSTO DATA CONTROLS WITHOUT ACCOUNTABILITY ACCESSTODATA v WITHOUT AUTH AVAILABILITY OFDATA IN THE FACE OF FAILURE VAULTVALIDATES CLIENTTOKENAND a 2MAN RULEFOR NOTEXPIREDREVOKED UNSEALUSING INTERNAL SHAMIRSECRETSHARING DEFAULT a THREAT MUST BE ROOT FOR DENY SPECIFICTASKS EXTERNAL 256 BIT AES IN TL5t Gcm WITH 96 BIT TOKEN THREAT noncesFORALLDATA LEAVINGVAULT J CLIENT UNTRUSTED BY STORAGE DESIGN BACKEND ENCRYPTED
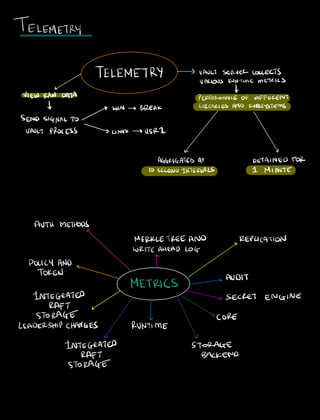
- 13. TELEMETRY TELEMETRY VAULT SERVERCOLLECTS VARIOUS RUNTIMEMETRICS I VIEW RAW DATA PERFORMANCE OF DIFFERENT 7 WIN BREAK LIBRARIESANDSUBSYSTEMS SENDSIGNALTO VAULT PROCESS LINUX 05121 v AGGREGATED AT RETAINED FOR 10SECONDINTERVALS 1 MINUTE AUTH METHODS r MERKLETREE AND REPLICATION WRITEAHEAD LOG POLICY AND TOKEN METRICS AUDIT INTEGRATED SECRET ENGINE RAFT in STORAGE CORE LEADERSHIPCHANGES RUNTIME I INTEGRATED STORAGE RAFT BACKEND STORAGE
- 14. TOKEN AUTHENTICATION TOKEN CORECLIENTAUTH AUTH 7 BUILT IN TOKEN ID Primary ID Randomly Generated Display Name Properties Meta data for auditlogging Immutable Number of Uses Optional Once Created ParentID Optional Parent created token Policies associated list of ACL policies SourcePath Path generated TOKENCREATED auth token create I Parent Toker TOKEN TREES Child tokens from subset of parent policies Tokenrevoked entire subtree revoked
- 15. KEY ROTATION START VAULT SEALED STATE UNSEAL 5 KEYS SHAMIR'SSECRET KEY ROTATION CHANGE UNSEAL KEYS MASTERKEY BACKENDENCRYPTION KEY OPERATION ROTATE CHANGE ENCRYPTION KEY 7 v u CANBEDONE NEW KEYGENERATEDAND REILEY c ONLINE ADDED TO KEYRING MEETTHRESHOLD GENERATE s OFCURRENTUNSEAL MASTERKEY KEYS
- 16. REPLICATION VAULT ENTERPRISE FOCUS ON HAFOR a REPLICATION PRIMARY SECONDARYG N GLOBALDEPLOYMENTS ASYNCHRONOUS REPLICATION SCALETHROUGHPUT USE CASES MULTI DCDEPLOYMENTS SINGLEVAULTCLUSTER IMPOSESHIGHLATENCY ENCRYPTIONASSERVICE v USERSMAYGENERATE Backup sites HIGHVOLUMEOFTRAFFIC BCPFORLOSSOFDC SIMPLE To DESIGN GOALS AVAILABILITY OPERATE TOLERATEREDUCED CONSISTENCY NEARREALTIME CONFLICT TRANSPARENTTO FREE CLIENTS 1 WRITECONFLICTS DO NOTTAKEPLACE
- 17. REPLICATION ARCHITECTURE BASED ONDESIGN GOALS TEBACKEND CONSUL y STORAC THATSUPPORTSTRANSACTIONAL UPDATES MULTIPLE KEYHALVEUPDATES ATOMICALLY WRITESAREVISIBLE REPLICATION I 4 CLUSTER MAINTAIN A LOGSHIPPING WRITE AHEAD LOG WAL L S OFALLUPDATES REPLICATE PRIMARY SECONDARY CHANGES f t AUTHORITATIVE READSECRETS PERFORM 1 SENDDATATHROUGH TRANSIT LOG WRITETOSTORAGE FORWARDWRITES TO PRIMARY SHIPPING 1 I 1 IF SECONDARY15 MODIFYPOLICY MODIFYSECRETS NEWORTOOFAR BEHINDprimary 1NOTENOUGHWALS BROKENCONNECTION SOURCE 1 PRIMARY X SECONDARY op VAULTMAINTAINS TRUTH MERKLEINDEX OFENCRYPTED WRITESCONTINUE FEETYED KEYS r STAYLOCAL NOREPLICATION TOKENSORLEASES PRIMARY COMPARETO SECONDARY VENTMUST WHICHKEYS UT AUTHIFSWITCH OFSYNC OSTERS PERFORMANCE I INDEXUPDATED IN COULD BEPOWER MEMORY Loss ? CONSISTENCY OF INDEX6000TOF INDEX UNDER T SYNC FAIL CONDITION ARIES ALGORITHM
- 18. PLUGIN SYSTEM COMMUNICATES OVER RPC COMPLETELY SEPERATE STANDALONE APPLICATIONS ALL AUTH AND SECRET PLUGINSBACKENDS DOES NOT SHARE SAME MEMORY SPACE TREATBUILTIN ANDEXTERNAL PLUGINLIKE PLUGIN CAN NOT CRASH VAULT ENTIRELYLEGO



