Web application security
Download as PPSX, PDF1 like822 views
This document discusses various security threats to web applications such as cross-site scripting, SQL injection, denial-of-service attacks, and brute force attacks. It provides details on each threat, including how they occur and methods of prevention. Defense tactics covered include input validation, account lockouts, CAPTCHAs, encryption, access restrictions, and server hardening techniques.
1 of 30
Downloaded 29 times



























Recommended
Web Application Penetration Testing 



Web Application Penetration Testing Priyanka Aash
Ėý
Introduction of Ethical Hacking, Life cycle of Hacking, Introduction of Penetration testing, Steps in Penetration Testing, Foot printing Module, Scanning Module, Live Demos on Finding Vulnerabilities a) Bypass Authentication b) Sql Injection c) Cross site Scripting d) File upload Vulnerability (Web Server Hacking) Countermeasures of Securing Web applicationsApplication Security - Your Success Depends on it



Application Security - Your Success Depends on itWSO2
Ėý
Traditional information security mainly revolves around network and operating system (OS) level protection. Regardless of the level of security guarding those aspects, the system can be penetrated and the entire deployment can be brought down if your application's security isn't taken into serious consideration. Information security should ideally start at the application level, before network and OS level security is ensured. To achieve this, security needs to be integrated into the application at the software development phase.
In this session, Dulanja will discuss the following:
The importance of application security - why network and OS security is insufficient.
Challenges in securing your application.
Making security part of the development lifecycle.Application Security



Application Securityflorinc
Ėý
The document summarizes application security best practices. It discusses who is responsible for application security and design considerations like authentication, authorization, privacy and data integrity. It then covers security principles like designing for security by default and in deployment. Top application vulnerabilities like SQL injection, cross-site scripting and access control issues are explained along with remedies. Finally, it provides checklists for designers, developers and testers to follow for application security.Cybersecurity Attack Vectors: How to Protect Your Organization



Cybersecurity Attack Vectors: How to Protect Your OrganizationTriCorps Technologies
Ėý
The document discusses various cybersecurity attack vectors and how organizations can protect themselves. It outlines common attack methods like ransomware, malicious code delivery, social engineering, and phishing. It then recommends that organizations conduct regular security audits, establish governance policies, create an incident response plan, and provide cybersecurity education to employees. The document promotes cybersecurity services from Future Point of View including vulnerability testing, forensics, and training to help organizations enhance their protections.Web Application Security 101



Web Application Security 101Jannis Kirschner
Ėý
Web Application Security Basics.
- What's (Web) Application Security About
- Practical Example covering OWASP Top 10
- Mitigation StrategiesApplication Security



Application SecurityReggie Niccolo Santos
Ėý
* Brief timeline on cyber attack history
* Definition
* Foundations of Security
* Definition of Terms
* Threat Modeling
* Application Vulnerability Categories
* Core Security Principles
* Web Application Security
* Risks and Risk Mitigation/Control MeasuresVAPT PRESENTATION full.pptx



VAPT PRESENTATION full.pptxDARSHANBHAVSAR14
Ėý
The document provides information on vulnerability assessment and penetration testing. It defines vulnerability assessment as a systematic approach to finding security issues in a network or system through manual and automated scanning. Penetration testing involves exploring and exploiting any vulnerabilities that are found to confirm their existence and potential damage. The document outlines the types of testing as blackbox, graybox, and whitebox. It also lists some common tools used for testing like Nmap, ZAP, Nikto, WPScan, and HostedScan. Finally, it provides examples of specific vulnerabilities found and their solutions, such as outdated themes/plugins, backup files being accessible, and SQL injection issues.Application Security | Application Security Tutorial | Cyber Security Certifi...



Application Security | Application Security Tutorial | Cyber Security Certifi...Edureka!
Ėý
This Edureka PPT on "Application Security" will help you understand what application security is and measures taken to improve the security of an application often by finding, fixing and preventing security vulnerabilities.
Following are the topics covered in this PPT:
Introduction to Cybersecurity
What is Application Security?
What is an SQL Injection attack
Demo on SQL Injection
Follow us to never miss an update in the future.
Instagram: https://www.instagram.com/edureka_learning/
Facebook: https://www.facebook.com/edurekaIN/
Twitter: https://twitter.com/edurekain
LinkedIn: https://www.linkedin.com/company/edurekaSecure coding practices



Secure coding practicesMohammed Danish Amber
Ėý
Secure Coding Practices - PHP.
How to safe gaurd your application from CSRF, Session Hijacking, SQLiVulnerabilities in modern web applications



Vulnerabilities in modern web applicationsNiyas Nazar
Ėý
Microsoft powerpoint presentation for BTech academic seminar.This seminar discuses about penetration testing, penetration testing tools, web application vulnerabilities, impact of vulnerabilities and security recommendations.Fundamentals of Network security



Fundamentals of Network securityAPNIC
Ėý
Presented by Paul Wilson, Director General of APNIC and Chair of APrIGF Multistakeholder Steering Group at the Asia Pacific Internet Leadership Program as part of 2016 APrIGF TaipeiEthical Hacking & Penetration Testing



Ethical Hacking & Penetration Testingecmee
Ėý
This document summarizes a presentation on ethical hacking and penetration testing. It includes:
1. An overview of what ethical hacking and penetration testing are, which involves improving security by finding vulnerabilities before hackers do.
2. The issues organizations face from internal and external risks like employees' lack of security awareness or external hackers exploiting weaknesses.
3. The tools and techniques used in penetration testing, including automated vs manual methods, external vs internal testing, and examples like denial of service, social engineering, and Google hacking.
4. Both the benefits of strengthening security and limitations, like testing not being guaranteed to find all vulnerabilities or account for changing technologies.Penetration testing reporting and methodology



Penetration testing reporting and methodologyRashad Aliyev
Ėý
This paper covering information about Penetration testing methodology, standards reporting formats and comparing reports. Explained problem of Cyber Security experts when they making penetration tests. How they doing current presentations.
We will focus our work in penetration testing methodology reporting form and detailed information how to compare result and related work information.
Web application security



Web application securityKapil Sharma
Ėý
The document discusses web application security and provides an overview of common vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). It summarizes the OWASP Top 10 list of most critical web app security risks, including injection flaws, broken authentication, sensitive data exposure, and more. The document also offers best practices for developing more securely, like using prepared statements, validating and sanitizing input, and implementing authentication and session management properly.OWASP Top 10 2021 Presentation (Jul 2022)



OWASP Top 10 2021 Presentation (Jul 2022)TzahiArabov
Ėý
The document provides information about the OWASP Top 10 2021 list of web application security risks. It describes the top risk, A01: Broken Access Control, giving its definition, examples of vulnerabilities it can enable, prevention methods, and examples. It also summarizes the second and third top risks, A02: Cryptographic Failures and A03: Injection, in a similar manner.Security Vulnerabilities



Security VulnerabilitiesMarius Vorster
Ėý
The document discusses common security threats such as URL spoofing, man-in-the-middle attacks, cross-frame scripting, SQL injection, rainbow table matching, denial of service attacks, cross-site scripting, cross-site request forgery, brute force attacks, and dictionary attacks. For each threat, it describes variations, prevention methods such as input validation, access control, and encryption, and detection techniques like monitoring for anomalous behavior.Introduction to Web Application Penetration Testing



Introduction to Web Application Penetration TestingAnurag Srivastava
Ėý
Web Application Pentesting
* Process to check and penetrate the security of a web application or a website
* process involves an active analysis of the application for any weaknesses, technical flaws, or vulnerabilities
* Any security issues that are found will be presented to the system owner, together with an assessment of the impact, a proposal for mitigation or a technical solution.Threat Modelling



Threat Modellingn|u - The Open Security Community
Ėý
This document discusses threat modeling for software applications. It covers the key stages of threat modeling including decomposing the application, determining and ranking threats using STRIDE, and determining countermeasures. Specific topics covered include threat modeling approaches, data flow diagrams, trust levels, the STRIDE framework for analyzing spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privilege threats. It also discusses mobile threat modeling and provides an example threat analysis of a student results portal application.OWASP Top 10 Web Application Vulnerabilities



OWASP Top 10 Web Application VulnerabilitiesSoftware Guru
Ėý
This document provides an overview of the OWASP Top 10 Risk Rating Methodology. It explains how risks are rated based on four factors: threat agent, attack vector, technical impact, and business impact. Each factor is given a rating of 1-3 (easy to difficult) and these ratings are multiplied together to calculate an overall weighted risk rating. An example of how this methodology would be applied to an SQL injection vulnerability is also provided.OWASP Top 10 Vulnerabilities - A5-Broken Access Control; A6-Security Misconfi...



OWASP Top 10 Vulnerabilities - A5-Broken Access Control; A6-Security Misconfi...Lenur Dzhemiliev
Ėý
This document discusses security issues related to broken access control and security misconfiguration. It provides examples of broken access control including modifying URL parameters to access restricted resources, restricting folder access, and using malicious URLs as parameters. Recommendations are given to implement access controls consistently, limit account data changes to account holders, and log access control failures. Examples of security misconfiguration include using default credentials and configurations, having an overly informative error handling, and leaving unnecessary features enabled. Recommendations include removing unused features, sending secure headers, not using default configurations, and properly configuring robots.txt files. Links to additional resources on these topics are also provided.Web application attacks



Web application attackshruth
Ėý
Web application attacks can take many forms, including cross-site scripting (XSS), SQL injection, parameter tampering, command injection, session management issues, cookie poisoning, directory traversal, cross-site request forgery, and buffer overflows. XSS is a vulnerability that allows malicious JavaScript code to be injected and run in a user's browser, potentially accessing data. SQL injection involves inserting SQL commands into a database query to gain unauthorized access. Parameter tampering modifies URL parameters to change expected behavior.Whitman_Ch02.pptx



Whitman_Ch02.pptxSiphamandla9
Ėý
This document summarizes key points from Chapter 2 of the textbook "Principles of Information Security". The chapter discusses the need for information security in organizations. It states that information security programs aim to keep information assets safe and useful by addressing threats from attacks. The responsibilities of information security are discussed, including protecting business functions, data, applications, and technology assets. Common threats like malware, phishing attacks, and data breaches are outlined. Internal and external threats are rated based on a survey of organizations. The chapter objectives are to understand the need for security programs and the threats faced.MITRE ATT&CK Framework



MITRE ATT&CK Frameworkn|u - The Open Security Community
Ėý
The document discusses the MITRE ATT&CK framework, which is a knowledge base of adversary behaviors and tactics collected from real-world observations. It describes how the framework categorizes behaviors using tactics, techniques, and procedures. The framework can be used for threat intelligence, detection and analytics, adversary emulation, and assessment and engineering. The document provides examples of how organizations can map their detection capabilities and data sources to techniques in the framework to improve visibility of attacks. It cautions against misusing the framework as a checklist rather than taking a threat-informed approach.Client-Side Penetration Testing Presentation



Client-Side Penetration Testing PresentationChris Gates
Ėý
Full Scope Security
Client-Side Penetration Testing presentation from SOURCE Boston/NotACon/ChicagoConSupply Chain Attacks



Supply Chain AttacksLionel Faleiro
Ėý
This document discusses supply chain attacks and provides examples of recent attacks. It defines supply chain attacks as compromising enterprise networks via third party applications or entities. The document then summarizes the anatomy and timeline of the Kaseya and 3CX ransomware attacks. In the Kaseya attack, a malicious task was deployed to VSA servers which then pushed ransomware downstream. The 3CX attack involved a trojanized software update that bundled a malicious DLL leading to data theft. Finally, the document outlines defenses such as software inventory, access controls, and secure development practices to help prevent supply chain attacks.Ethical Hacking n VAPT presentation by Suvrat jain



Ethical Hacking n VAPT presentation by Suvrat jainSuvrat Jain
Ėý
a perfect example of your 6 weeks summer training ppt. Course-Ethical Hacking , its info and VAPT- Vulnerability Assessment n Penetration testing. about how vulnerability scanning , tools used , cracking password , etc.OWASP Top Ten 2017



OWASP Top Ten 2017Michael Furman
Ėý
The document discusses the OWASP Top Ten project, which identifies the 10 most critical web application security risks. It provides an overview of OWASP, describes the Top 10 risks from 2013 and 2017, and explains changes between the two versions. For each risk, it gives a brief example and recommendations for prevention. The key topics covered are injection, broken authentication, sensitive data exposure, XML external entities, broken access control, security misconfiguration, cross-site scripting, insecure deserialization, use of vulnerable components, and insufficient logging/monitoring.Ethical hacking/ Penetration Testing



Ethical hacking/ Penetration TestingANURAG CHAKRABORTY
Ėý
This document summarizes an ethical hacking seminar that was presented. It discusses the following key points:
- Ethical hacking involves using the same tools and techniques as hackers but in a legal manner to test security vulnerabilities.
- The hacking process involves footprinting, scanning, gaining access, and maintaining access. Footprinting gathers information, scanning finds open ports and services, and gaining access exploits vulnerabilities.
- Ethical hackers are independent security professionals who evaluate systems without damaging them or stealing data. They find vulnerabilities and report them to owners.
- Skills needed for ethical hacking include knowledge of operating systems, firewalls, networking protocols, and project management. Understanding how hackers think is important to catch securitySecure Coding BSSN Semarang Material.pdf



Secure Coding BSSN Semarang Material.pdfnanangAris1
Ėý
This document provides an introduction to application security. It discusses why security is important and how applications can become vulnerable. It outlines common application security attacks like SQL injection, cross-site scripting, and denial-of-service attacks. It also discusses software security standards, models and frameworks like OWASP that can help make applications more secure. The document emphasizes the importance of secure coding practices and security testing to prevent vulnerabilities.WEB APPLICATION SECURITY



WEB APPLICATION SECURITYyashwanthlavu
Ėý
Cross-site scripting (XSS) is the most prevalent web application security vulnerability. XSS allows attackers to inject client-side scripts to compromise user data or bypass access controls. Contextual output encoding, input validation, and emerging defensive technologies like content security policy promise to reduce XSS occurrences. SQL injection is another common threat that exploits code injection to access databases. Memory corruption from buffer overflows or faulty memory management can enable arbitrary code execution attacks. Cross-site request forgery tricks users into unknowingly submitting malicious requests. Data breaches unintentionally release secure information, requiring notification laws.More Related Content
What's hot (20)
Secure coding practices



Secure coding practicesMohammed Danish Amber
Ėý
Secure Coding Practices - PHP.
How to safe gaurd your application from CSRF, Session Hijacking, SQLiVulnerabilities in modern web applications



Vulnerabilities in modern web applicationsNiyas Nazar
Ėý
Microsoft powerpoint presentation for BTech academic seminar.This seminar discuses about penetration testing, penetration testing tools, web application vulnerabilities, impact of vulnerabilities and security recommendations.Fundamentals of Network security



Fundamentals of Network securityAPNIC
Ėý
Presented by Paul Wilson, Director General of APNIC and Chair of APrIGF Multistakeholder Steering Group at the Asia Pacific Internet Leadership Program as part of 2016 APrIGF TaipeiEthical Hacking & Penetration Testing



Ethical Hacking & Penetration Testingecmee
Ėý
This document summarizes a presentation on ethical hacking and penetration testing. It includes:
1. An overview of what ethical hacking and penetration testing are, which involves improving security by finding vulnerabilities before hackers do.
2. The issues organizations face from internal and external risks like employees' lack of security awareness or external hackers exploiting weaknesses.
3. The tools and techniques used in penetration testing, including automated vs manual methods, external vs internal testing, and examples like denial of service, social engineering, and Google hacking.
4. Both the benefits of strengthening security and limitations, like testing not being guaranteed to find all vulnerabilities or account for changing technologies.Penetration testing reporting and methodology



Penetration testing reporting and methodologyRashad Aliyev
Ėý
This paper covering information about Penetration testing methodology, standards reporting formats and comparing reports. Explained problem of Cyber Security experts when they making penetration tests. How they doing current presentations.
We will focus our work in penetration testing methodology reporting form and detailed information how to compare result and related work information.
Web application security



Web application securityKapil Sharma
Ėý
The document discusses web application security and provides an overview of common vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). It summarizes the OWASP Top 10 list of most critical web app security risks, including injection flaws, broken authentication, sensitive data exposure, and more. The document also offers best practices for developing more securely, like using prepared statements, validating and sanitizing input, and implementing authentication and session management properly.OWASP Top 10 2021 Presentation (Jul 2022)



OWASP Top 10 2021 Presentation (Jul 2022)TzahiArabov
Ėý
The document provides information about the OWASP Top 10 2021 list of web application security risks. It describes the top risk, A01: Broken Access Control, giving its definition, examples of vulnerabilities it can enable, prevention methods, and examples. It also summarizes the second and third top risks, A02: Cryptographic Failures and A03: Injection, in a similar manner.Security Vulnerabilities



Security VulnerabilitiesMarius Vorster
Ėý
The document discusses common security threats such as URL spoofing, man-in-the-middle attacks, cross-frame scripting, SQL injection, rainbow table matching, denial of service attacks, cross-site scripting, cross-site request forgery, brute force attacks, and dictionary attacks. For each threat, it describes variations, prevention methods such as input validation, access control, and encryption, and detection techniques like monitoring for anomalous behavior.Introduction to Web Application Penetration Testing



Introduction to Web Application Penetration TestingAnurag Srivastava
Ėý
Web Application Pentesting
* Process to check and penetrate the security of a web application or a website
* process involves an active analysis of the application for any weaknesses, technical flaws, or vulnerabilities
* Any security issues that are found will be presented to the system owner, together with an assessment of the impact, a proposal for mitigation or a technical solution.Threat Modelling



Threat Modellingn|u - The Open Security Community
Ėý
This document discusses threat modeling for software applications. It covers the key stages of threat modeling including decomposing the application, determining and ranking threats using STRIDE, and determining countermeasures. Specific topics covered include threat modeling approaches, data flow diagrams, trust levels, the STRIDE framework for analyzing spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privilege threats. It also discusses mobile threat modeling and provides an example threat analysis of a student results portal application.OWASP Top 10 Web Application Vulnerabilities



OWASP Top 10 Web Application VulnerabilitiesSoftware Guru
Ėý
This document provides an overview of the OWASP Top 10 Risk Rating Methodology. It explains how risks are rated based on four factors: threat agent, attack vector, technical impact, and business impact. Each factor is given a rating of 1-3 (easy to difficult) and these ratings are multiplied together to calculate an overall weighted risk rating. An example of how this methodology would be applied to an SQL injection vulnerability is also provided.OWASP Top 10 Vulnerabilities - A5-Broken Access Control; A6-Security Misconfi...



OWASP Top 10 Vulnerabilities - A5-Broken Access Control; A6-Security Misconfi...Lenur Dzhemiliev
Ėý
This document discusses security issues related to broken access control and security misconfiguration. It provides examples of broken access control including modifying URL parameters to access restricted resources, restricting folder access, and using malicious URLs as parameters. Recommendations are given to implement access controls consistently, limit account data changes to account holders, and log access control failures. Examples of security misconfiguration include using default credentials and configurations, having an overly informative error handling, and leaving unnecessary features enabled. Recommendations include removing unused features, sending secure headers, not using default configurations, and properly configuring robots.txt files. Links to additional resources on these topics are also provided.Web application attacks



Web application attackshruth
Ėý
Web application attacks can take many forms, including cross-site scripting (XSS), SQL injection, parameter tampering, command injection, session management issues, cookie poisoning, directory traversal, cross-site request forgery, and buffer overflows. XSS is a vulnerability that allows malicious JavaScript code to be injected and run in a user's browser, potentially accessing data. SQL injection involves inserting SQL commands into a database query to gain unauthorized access. Parameter tampering modifies URL parameters to change expected behavior.Whitman_Ch02.pptx



Whitman_Ch02.pptxSiphamandla9
Ėý
This document summarizes key points from Chapter 2 of the textbook "Principles of Information Security". The chapter discusses the need for information security in organizations. It states that information security programs aim to keep information assets safe and useful by addressing threats from attacks. The responsibilities of information security are discussed, including protecting business functions, data, applications, and technology assets. Common threats like malware, phishing attacks, and data breaches are outlined. Internal and external threats are rated based on a survey of organizations. The chapter objectives are to understand the need for security programs and the threats faced.MITRE ATT&CK Framework



MITRE ATT&CK Frameworkn|u - The Open Security Community
Ėý
The document discusses the MITRE ATT&CK framework, which is a knowledge base of adversary behaviors and tactics collected from real-world observations. It describes how the framework categorizes behaviors using tactics, techniques, and procedures. The framework can be used for threat intelligence, detection and analytics, adversary emulation, and assessment and engineering. The document provides examples of how organizations can map their detection capabilities and data sources to techniques in the framework to improve visibility of attacks. It cautions against misusing the framework as a checklist rather than taking a threat-informed approach.Client-Side Penetration Testing Presentation



Client-Side Penetration Testing PresentationChris Gates
Ėý
Full Scope Security
Client-Side Penetration Testing presentation from SOURCE Boston/NotACon/ChicagoConSupply Chain Attacks



Supply Chain AttacksLionel Faleiro
Ėý
This document discusses supply chain attacks and provides examples of recent attacks. It defines supply chain attacks as compromising enterprise networks via third party applications or entities. The document then summarizes the anatomy and timeline of the Kaseya and 3CX ransomware attacks. In the Kaseya attack, a malicious task was deployed to VSA servers which then pushed ransomware downstream. The 3CX attack involved a trojanized software update that bundled a malicious DLL leading to data theft. Finally, the document outlines defenses such as software inventory, access controls, and secure development practices to help prevent supply chain attacks.Ethical Hacking n VAPT presentation by Suvrat jain



Ethical Hacking n VAPT presentation by Suvrat jainSuvrat Jain
Ėý
a perfect example of your 6 weeks summer training ppt. Course-Ethical Hacking , its info and VAPT- Vulnerability Assessment n Penetration testing. about how vulnerability scanning , tools used , cracking password , etc.OWASP Top Ten 2017



OWASP Top Ten 2017Michael Furman
Ėý
The document discusses the OWASP Top Ten project, which identifies the 10 most critical web application security risks. It provides an overview of OWASP, describes the Top 10 risks from 2013 and 2017, and explains changes between the two versions. For each risk, it gives a brief example and recommendations for prevention. The key topics covered are injection, broken authentication, sensitive data exposure, XML external entities, broken access control, security misconfiguration, cross-site scripting, insecure deserialization, use of vulnerable components, and insufficient logging/monitoring.Ethical hacking/ Penetration Testing



Ethical hacking/ Penetration TestingANURAG CHAKRABORTY
Ėý
This document summarizes an ethical hacking seminar that was presented. It discusses the following key points:
- Ethical hacking involves using the same tools and techniques as hackers but in a legal manner to test security vulnerabilities.
- The hacking process involves footprinting, scanning, gaining access, and maintaining access. Footprinting gathers information, scanning finds open ports and services, and gaining access exploits vulnerabilities.
- Ethical hackers are independent security professionals who evaluate systems without damaging them or stealing data. They find vulnerabilities and report them to owners.
- Skills needed for ethical hacking include knowledge of operating systems, firewalls, networking protocols, and project management. Understanding how hackers think is important to catch securitySimilar to Web application security (20)
Secure Coding BSSN Semarang Material.pdf



Secure Coding BSSN Semarang Material.pdfnanangAris1
Ėý
This document provides an introduction to application security. It discusses why security is important and how applications can become vulnerable. It outlines common application security attacks like SQL injection, cross-site scripting, and denial-of-service attacks. It also discusses software security standards, models and frameworks like OWASP that can help make applications more secure. The document emphasizes the importance of secure coding practices and security testing to prevent vulnerabilities.WEB APPLICATION SECURITY



WEB APPLICATION SECURITYyashwanthlavu
Ėý
Cross-site scripting (XSS) is the most prevalent web application security vulnerability. XSS allows attackers to inject client-side scripts to compromise user data or bypass access controls. Contextual output encoding, input validation, and emerging defensive technologies like content security policy promise to reduce XSS occurrences. SQL injection is another common threat that exploits code injection to access databases. Memory corruption from buffer overflows or faulty memory management can enable arbitrary code execution attacks. Cross-site request forgery tricks users into unknowingly submitting malicious requests. Data breaches unintentionally release secure information, requiring notification laws.Types of attack



Types of attackRajuPrasad33
Ėý
The document describes several types of cyber attacks:
Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks aim to overwhelm systems' resources to prevent legitimate access. TCP SYN flood attacks exploit buffer space during connection setup to crash systems. Botnets are networks of infected systems controlled remotely to carry out large-scale DDoS attacks. SQL injection attacks insert malicious code into database queries to compromise websites. Cross-site scripting (XSS) attacks use third-party scripts to run code on users' browsers. Eavesdropping attacks intercept network traffic to steal passwords and other sensitive data, either passively or actively. Encryption is the primary defense against eavesdroWEB APPLICATION SECURITY



WEB APPLICATION SECURITYyashwanthlavu
Ėý
Cross-site scripting (XSS) is the most prevalent web application security vulnerability. XSS allows attackers to inject client-side scripts and compromise user data. Prevention methods include output encoding, input validation, and emerging defensive technologies. SQL injection is another common threat that allows attackers to execute malicious SQL statements and access sensitive data. Memory corruption vulnerabilities can also allow arbitrary code execution on a system. Cross-site request forgery and data breaches are additional security risks for web applications. Proper authentication, authorization, input validation, output encoding and other defenses are needed to help mitigate these threats.Vulnerabilities in Web Applications



Vulnerabilities in Web ApplicationsVenkat Ramana Reddy Parine
Ėý
This document discusses three common web application vulnerabilities: SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). SQL injection occurs when user input is not sanitized before being used in SQL queries, allowing attackers to alter queries. XSS happens when user input containing script code is rendered without sanitization, allowing attackers to run script on users' browsers. CSRF tricks the user's browser into executing unwanted actions by forging requests from a user who is currently authenticated. The document provides examples and techniques for exploiting each vulnerability as well as recommendations for prevention.Computer Network Case Study - bajju.pptx



Computer Network Case Study - bajju.pptxShivamBajaj36
Ėý
This document discusses various computer network attacks and vulnerabilities. It covers topics like ransomware, IoT attacks, social engineering, man-in-the-middle attacks, denial of service attacks, distributed denial of service attacks, SQL injection, SSL stripping, URL misinterpretation, directory browsing, input validation vulnerabilities, and vulnerabilities in each layer of the OSI model. The goal is to provide an overview of common network attacks and how they can be carried out.Internet Security



Internet SecurityMitesh Gupta
Ėý
This document discusses various internet security threats such as hijacked web servers, denial-of-service attacks, cross-site scripting, email spoofing, and trap doors. It provides details on how these threats are carried out and potential defensive measures. The key threats are hijacking web servers to plant hostile code, denial-of-service attacks which try to interrupt services, cross-site scripting which injects scripts to steal cookies or phish users, email spoofing which forges sender addresses in spam/phishing, and trap doors which bypass authentication. Internet security aims to establish rules against such attacks over the insecure internet.cyber security and threats.pptx



cyber security and threats.pptxVSAM Technologies India Private Limited
Ėý
Cybersecurity involves protecting internet-connected systems, hardware, software, and data from cyber attacks. It is based on the CIA triad of confidentiality, integrity, and availability. Cyber threats come from various sources and take many forms, including phishing attacks, SQL injection, man-in-the-middle attacks, malware, zero-day exploits, cross-site scripting, and password attacks. Organizations must implement appropriate defenses such as encryption, firewalls, anti-virus software, and user education to prevent and mitigate these threats.3-types of attacks_Types of attacks.pptx



3-types of attacks_Types of attacks.pptxAmandeepSohal4
Ėý
Types of attacks Types of attacks Types of attacks Types of attacks Types of attacks Types of attacks Types of attacks
Types of attacks
Types of attacksTypes of attacksTypes of attacksTypes of attacksTypes of attacksEntrepreneurship & Commerce in IT - 11 - Security & Encryption



Entrepreneurship & Commerce in IT - 11 - Security & EncryptionSachintha Gunasena
Ėý
This series in about the Entrepreneurial and E-Commerce opportunities and how to harness the power of Information Technology to improve or revolutionize business.
This session discusses about:
the types of threats that could occur to an e-commerce business, and what are the prevention methods and technologies available for such threats.Web and Mobile Application Security



Web and Mobile Application SecurityPrateek Jain
Ėý
OWASP security vulnerabilities, their technical and business impact and mitigating strategies for web and mobile applications with examples.Cyber attack



Cyber attackManjushree Mashal
Ėý
CYBER ATTACK INTRODUCTION,TYPES OF CYBER ATTACK,DOS ATTACK,MAJOR CYBER ATTACK IN INDIA,PREVENTION TIPSNetwork security and firewalls



Network security and firewallsMurali Mohan
Ėý
Network security and firewalls are important tools for protecting client-server networks. Firewalls act as a barrier between private networks and the public internet, controlling incoming and outgoing network traffic based on set rules. Common security threats to client-server networks include malicious software, phishing, hacking, and denial of service attacks. Encryption techniques like public key cryptography and digital signatures are important for ensuring data security and authenticity in electronic communications. Firewall types include packet filtering routers, application proxies, and hardened firewall hosts.Codeinjection



CodeinjectionNitish Kumar
Ėý
Code injection is the exploitation of a computer bug that allows an attacker to introduce malicious code into a computer program and alter its execution. There are several types of code injection including SQL injection, which modifies database values; OS command injection, which installs malware by exploiting vulnerabilities in browsers/plugins; and cross-site scripting (XSS), where malicious scripts are introduced into trusted websites. XSS can be stored, reflected, or DOM-based. Code injection attacks can have disastrous consequences, including compromising sensitive data, installing malware, and escalating privileges.Software security 



Software security Akshay Jaryal
Ėý
The document discusses various software security issues including insecure interaction between components like SQL injection and cross-site scripting (XSS). It also discusses risky resource management issues like buffer overflows. Additionally, it discusses porous defenses like missing authentication. The document emphasizes the importance of filtering all untrusted inputs and outputs to prevent attacks like XSS that could allow altering of user data or behavior. It provides recommendations for secure coding practices like prepared statements and output encoding to prevent attacks on programs that display external data.Unit 5 - Designing Internet Systems and Servers - IT



Unit 5 - Designing Internet Systems and Servers - ITDeepraj Bhujel
Ėý
This document discusses various concepts related to designing internet systems and servers. It covers network architecture principles, components of internet architecture like routers and clients, and building blocks like addressing and routing. It also discusses server concepts like web, mail, proxy and RADIUS servers. It provides details on load balancing and the use of proxy server arrays for load balancing.A general security rule is that if an individual can physically touch a devic...



A general security rule is that if an individual can physically touch a devic...Chandravathi Dittakavi
Ėý
To stay current with virus and spyware threats, most antivirus solutions perform constant updates to their virus signature dictionary/database.
the antivirus software, as shown inĖýFIGURE, pulls in the threat signatures from across the cloud.
i.e Antivirus systems
retrieve cloud-based
Updates regarding
new threats in near real time.Website hacking and prevention (All Tools,Topics & Technique )



Website hacking and prevention (All Tools,Topics & Technique )Jay Nagar
Ėý
This document discusses the Heartbleed vulnerability in OpenSSL and its potential impacts. Heartbleed is a bug in the OpenSSL cryptography library that exposes the contents of the server's memory, including private keys and user session cookies. An attacker can exploit Heartbleed to steal sensitive data from vulnerable servers or impersonate services. The vulnerability had widespread implications because OpenSSL is used to secure a majority of websites. While patching servers and changing passwords addressed direct theft of information, Heartbleed also weakened the security of encrypted communications and online identities.UNIT 5 (2).pptx



UNIT 5 (2).pptxjanani603976
Ėý
The document provides an overview of various ethical hacking techniques including social engineering, denial of service attacks, session hijacking, hacking web servers, hacking web applications, SQL injection, hacking wireless networks, and hacking mobile platforms. It describes key aspects of each technique such as how they work, common tools used, and countermeasures to prevent attacks. For social engineering it outlines common human-based and computer-based methods. For denial of service it explains how distributed denial of service attacks work using botnets. For session hijacking it provides the three step process. For hacking web servers it lists common vulnerabilities exploited. And for mobile platforms it discusses threats from malware, app stores, and sandboxing issues.A general security rule is that if an individual can physically touch a devic...



A general security rule is that if an individual can physically touch a devic...Chandravathi Dittakavi
Ėý
Recently uploaded (18)
Hygiene-and-Sanitation with healthcare and the most important hygiene to be



Hygiene-and-Sanitation with healthcare and the most important hygiene to beLoveJade1
Ėý
Hygiene and sanitation A Teaching Guide for Those interested in teaching monkey beach



A Teaching Guide for Those interested in teaching monkey beachsethiserena
Ėý
A Teaching Guide for Those interested in teaching monkey beachHITRUST Overview and AI Assessments Webinar.pptx



HITRUST Overview and AI Assessments Webinar.pptxAmyPoblete3
Ėý
This webinar provides an overview of HITRUST, a widely recognized cybersecurity framework, and its application in AI assessments for risk management and compliance. It explores different HITRUST assessment options, including AI-specific frameworks, and highlights how organizations can streamline certification processes to enhance security and regulatory adherence.Elliptic Curve Cryptography Algorithm with Recurrent Neural Networks for Atta...



Elliptic Curve Cryptography Algorithm with Recurrent Neural Networks for Atta...IJCNCJournal
Ėý
The increasing use of Industrial Internet of Things (IIoT) devices has brought about new security vulnerabilities, emphasizing the need to create strong and effective security solutions. This research proposes a two-layered approach to enhance security in IIoT networks by combining lightweight encryption and RNN-based attack detection. The first layer utilizes Improved Elliptic Curve Cryptography (IECC), a novel encryption scheme tailored for IIoT devices with limited computational resources. IECC employs a Modified Windowed Method (MWM) to optimize key generation, reducing computational overhead and enabling efficient secure data transmission between IIoT sensors and gateways. The second layer employs a Recurrent Neural Network (RNN) for real-time attack detection. The RNN model is trained on a comprehensive dataset of IIoT network traffic, including instances of Distributed Denial of Service (DDoS), Man-in-the-Middle (MitM), ransomware attacks, and normal communications. The RNN effectively extracts contextual features from IIoT nodes and accurately predicts and classifies potential attacks. The effectiveness of the proposed two-layered approach is evaluated using three phases. The first phase compares the computational efficiency of IECC to established cryptographic algorithms including RSA, AES, DSA, Diffie-Hellman, SHA-256 and ECDSA. IECC outperforms all competitors in key eneration speed, encryption and decryption time, throughput, memory usage, information loss, and overall processing time. The second phase evaluates the prediction accuracy of the RNN model compared to other AI-based models DNNs, DBNs, RBFNs, and LSTM networks. The proposed RNN achieves the highest overall accuracy of 96.4%, specificity of 96.5%, precision of 95.2%, and recall of 96.8%, and the lowest false positive of 3.2% and false negative rates of 3.1%.
IPv6 - Global and Malaysia's Perspectives



IPv6 - Global and Malaysia's PerspectivesAPNIC
Ėý
APNIC's Senior Regional Advisor, Membership and Policy, Sunny Chendi presented on IPv6 at MyAPIGA 2025 held in Putrajaya from 16 to 18 February 2025. Introduction on how unique identifier systems are managed and coordinated - R...



Introduction on how unique identifier systems are managed and coordinated - R...APNIC
Ėý
Sunny Chendi, Senior Regional Advisor, Membership and Policy at APNIC, presented an 'Introduction on how unique identifier systems are managed and coordinated - RIRs (APNIC for APAC), ICANN, IETF and policy development' at MyAPIGA 2025 held in Putrajaya from 16 to 18 February 2025.IDM Crack 2025 Internet Download Manger Patch



IDM Crack 2025 Internet Download Manger Patchwistrendugftr
Ėý
copy & paste ð ð âĪâĪðĄ https://filedownloadx.com/download-link/
This project provides a cracked version of IDM, enabling users to use the premium features without purchasing a license. This project is for educational purposes only. Using cracked software is illegal and unethical. We strongly recommend purchasing a legitimate license from the official IDM website to support the developers and respect copyright laws.Custom Development vs Off-the-Shelf Solutions for Shopify Plus ERP Integratio...



Custom Development vs Off-the-Shelf Solutions for Shopify Plus ERP Integratio...CartCoders
Ėý
Choosing between custom development and off-the-shelf solutions for Shopify Plus ERP integration? Our latest blog explores the pros and cons to help you decide the best approach for optimizing your eCommerce operations.cyber hacking and cyber fraud by internet online money



cyber hacking and cyber fraud by internet online moneyVEENAKSHI PATHAK
Ėý
Cyber fraud is a blanket term to describe crimes committed by cyberattacks via the internet. These crimes are committed with the intent to illegally acquire and leverage an individual's or businessâs sensitive information for monetary gainShopify API Integration for Custom Analytics_ Advanced Metrics & Reporting Gu...



Shopify API Integration for Custom Analytics_ Advanced Metrics & Reporting Gu...CartCoders
Ėý
CartCoders offers specialized Shopify integration services to enhance your eCommerce store's functionality and user experience. Connect your Shopify store seamlessly with essential software and applications. Perfect for businesses aiming to streamline operations and boost efficiency.KeepItOn-2024-Internet-Shutdowns-Annual-Report.pdf



KeepItOn-2024-Internet-Shutdowns-Annual-Report.pdfsabranghindi
Ėý
Indiaâs figure of 84 shutdowns in 2024 is surpassed only by Myanmar, which endured 85 shutdowns under the military juntaâs rule. JACKPOT TANGKI4D BERMAIN MENGGUNAKAN ID PRO 2025 TEPERCAYA LISENSI STAR GAMIN...



JACKPOT TANGKI4D BERMAIN MENGGUNAKAN ID PRO 2025 TEPERCAYA LISENSI STAR GAMIN...TANGKI4D
Ėý
MODAL 50RIBU JACKPOT 10JUTA
BERMAIN DI STARLIGHT PRINCESS
TUNGGU APA LAGI MAIN KAN SEKARANG
GUNAKAN POLA BERMAIN REKOMENDASI KAMI
3x MANUAL SPIN âââ
DC ON-OFF
10x TURBO Spin â
â â
DC OFF
2x MANUAL Spin â
ââ
DC ON-OFF
20x CEPAT Spin ââ
â
DC OFF
COMBO DENGAN BUY FITURE SPIN
#Tangki4dexclusive #tangki4dlink #tangki4dvip #bandarsbobet #idpro2025 #stargamingasia #situsjitu #jppragmaticplayWeb application security
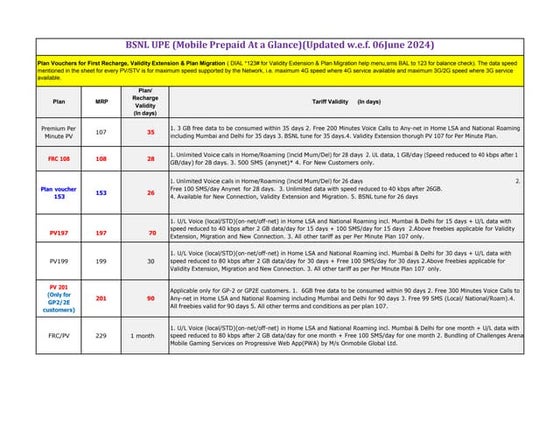
- 3. Security Threats âĒ Cross-site scripting âĒ SQL injection âĒ Denial-of-service attack âĒ Brute Force attack âĒ Remote file inclusion âĒ Man in Middle Attack âĒ Other Server side Threats.
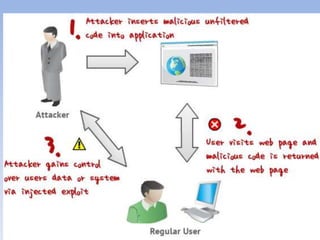
- 5. Cross-site scripting(XSS) âĒ Allows attackers to inject their own malicious scripts onto web pages and have it executed by the userâs browser âĒ Vulnerability commonly seen in : â Search results that display back the text that was entered â Error messages that display the text that caused the error â Forms which are filled out whose values are later displayed to the user â Web message boards where users can post messages
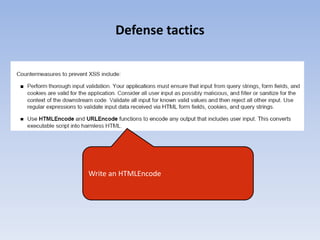
- 8. Defense tactics Write an HTMLEncode
- 9. SQL Injection âĒ The process of attacker adding his own SQL Statements in user input âĒ Used by attackers to â Gain confidential information (Credit Card numbers, Account details etc.) â Bypass authorization â Perform unauthorized updates âĒ Injection occurs through : â Input fields (e.g. UserID and Password entry) â Query string (values added to websiteâs URL) â Manipulated values in HTML
- 10. 10 UserID: Test Password : 123 Select * from Users where UserID = âTestâ and Password = â123â; Web Applications take user input and build an SQL statement which they send to the database Drop example
- 11. 11 UserID: Test; drop table users; -- Password : 123 Select * from Users where UserID = âTestâ; drop table users; -- and Password = â123â; Web Applications take user input and build an SQL statement which they send to the database
- 12. SQL Injection Defense âĒ It is quite simple: input validation âĒ Check all input âĒ Web Applications should not directly build SQL statements based on user input
- 13. Brute Force Attack âĒ A brute force attack is a trial-and-error method used to obtain information such as a user password or personal identification number (PIN). âĒ In a brute force attack, automated software is used to generate a large number of consecutive guesses as to the value of the desired data. Brute force attacks may be used by criminals to crack encrypted data, or by security analysts to test an organization's network security. A brute force attack may also be referred to as brute force cracking.
- 14. Preventing Brute Force Attack âĒ Implement an account lockout policy âĒ Another technique is to use a challenge- response test to prevent automated submissions of the login page. Tools such as the free reCAPTCHA âĒ Web application should enforce the use of strong passwords
- 15. Dos and DDOS âĒ Attempt to make a machine or network resource unavailable to its intended users. âĒ One common method of attack involves saturating the target machine with external communications requests âĒ attacks usually lead to a server overload
- 17. Effects of DDOS âĒ Consumption of computational resources, such as bandwidth, memory, disk space, or processor time. âĒ Disruption of configuration information, such as routing information. âĒ Disruption of state information, such as unsolicited resetting of TCP sessions. âĒ Disruption of physical network components. âĒ Obstructing the communication media between the intended users and the victim so that they can no longer communicate adequately.
- 18. DDOS Prevention âĒ An effective defense against an HTTP flood can be the deployment of a reverse proxy âĒ increase the capability of the system. âĒ Load-balancing tools can distribute requests among many servers scattered across a wide geographical area
- 19. Remote file inclusion âĒ It allows an attacker to include a file, usually through a script on the web server. âĒ vulnerability occurs due to the use of user- supplied input without proper validation
- 20. This can lead to âĒ Code execution on the web server âĒ Code execution on the client-side such as JavaScript which can lead to other attacks such as cross site scripting (XSS) âĒ Denial of service (DoS) âĒ Data theft/manipulation
- 21. Prevention âĒ This type of attack can be defended against at the .htaccess level and by filtering the inputs. âĒ Make sure you keep the Global Registers OFF. This is a biggie that will prevent much evil! âĒ Hardening the Server
- 22. Man in Middle Attack âĒ A man-in-the-middle attack is a type of cyberattack where a malicious actor inserts him/herself into a conversation between two parties, âĒ A MITM attack exploits the real-time processing of transactions, conversations or transfer of other data.
- 24. Prevention âĒ use a strong encryption between the client and the server âĒ you can use a browser plug-in such as HTTPS Everywhere or ForceTLS.
- 25. Server Hardening âĒ Shut down unused Services âĒ Hide Services with Port Knocking â Example: âĒ Web Server Service is public âĒ hide SFTP-, SSH- Services âĒ Use Onetime Passwords by generating them with Password generators 25
- 26. Restrict Resources to avoid DoS-Attacks âĒ Change Default TimeOut âĒ Restrict HTTP-Requests Restrict access to Web Resources âĒ Often resources are not to be accessible for everyone âĒ htaccess is a simple mechanism for access Protection âĒ htaccess is activated by a file .htaccess to protected directory (or above in one) 26 Source: http://www.howtomonster.com/2007/08/12/how-to-restrict-access-to-a-web-site-folder/
- 28. Linux Systems Monitoring Cycle 28
- 29. OWASP âĒ The Open Web Application Security Project is an online community dedicated to web application security. The OWASP community includes corporations, educational organizations, and individuals from around the world âĒ https://www.owasp.org/
Editor's Notes
- #13: Input validation is the most important part of defending against SQL injection. You should enforce input validation in all new applications through strong design. Any you should audit all your existing code and websites. You should additionally always harden your servers as well.
- #26: ·ĄūąēÔģūēđąô-ąĘēđēõēõ·ÉÃķ°ųģŲąð°ų
- #27: LimitRequestBody can be unlimited (practically up 2 GB to go!)




![phase_4_presentation[1] - Read-Only.pptx Iot](https://cdn.slidesharecdn.com/ss_thumbnails/phase4presentation1-read-only-250301195122-ec11f187-thumbnail.jpg?width=560&fit=bounds)