4SO customer presentation
- 1. ID-SEC SOLUTIONS LTD Identity and Access Management Solutions
- 2. 4SO S mart, S imple, S ingle S ign- O n Solution for Lotus Notes
- 3. CURRENT SITUATION Lotus Notes is a highly secured messaging solution 10% â 20% of help-desk calls deals with password problems in Lotus Notes A user forgot his Notes password won ât be able to use his mailbox To reset password takes 4 hours in average and prevents the user to access his Notes account.
- 4. 4SO â THE PROBLEM IN HELPDESK When user forget his Notes password, The ID file must be replace. Same for losing ID file (when HD corrupted for example). ID file replacement is a process that takes ~4 hour
- 5. 4SO â SECURITY PROBLEMS By copying the ID file and knowing the password, user can take control of the other âs mailbox. Different password policy for Active Directory and Lotus Notes. When there are too many passwords to remember user tend to write the password on the screen, behind the keyboard or any insecure place.
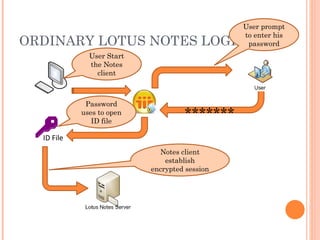
- 6. ORDINARY LOTUS NOTES LOGIN ID File ** User Start the Notes client User prompt to enter his password Password uses to open ID file Notes client establish encrypted session
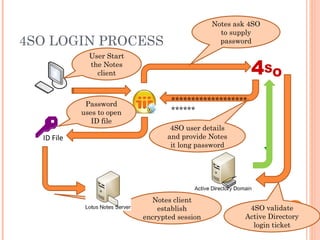
- 7. 4SO LOGIN PROCESS ID File 4 S O ï User Start the Notes client Notes ask 4SO to supply password 4SO user details and provide Notes it long password Password uses to open ID file Notes client establish encrypted session 4SO validate Active Directory login ticket
- 8. 4SO SOLUTION ADVANTAGES Reduce help desk calls on Notes forgotten password. Improve user experience along with improving Notes security. Quick and simple implementation, less than 30 Seconds installation process. Solution doesnâ t based on Active Directory password, but Active Directory authentication. Keeps the ID file password non human, 512 bit long.
- 9. TECHNOLOGY EDGE Notes login based on user âs Active Directory Kerberos ticket. Allow online and offline login to Notes. Offline login use when a portable computer don ât have connection to the Active Directory domain and the user login to the computer using cache login.
- 10. SUPPORT Lotus Notes client versions 6.x, 7.x, 8.x All Microsoft Windows versions Remote Desktop, Citrix Active Directory 2000, 2003, 2008 All Active Directory authentication methods include user/password , biometric , smart card etcâĶ
- 11. COMPOTITORS Lotus Notes Password sync and Shared Login Pistol Star Notes ID File Password Storage - The ID Vault General SSO solutions (TAM, imprivataâĶ)
- 12. NOTES SHARED LOGIN (NSL) You cannot use shared login if any of the following conditions is true: you use a computer that does not run Microsoft Windows you use a Smartcard to log in to Lotus Notes your User ID is protected by multiple passwords you are a roaming user that uses a roaming ID you run Notes on a USB drive you use a mandatory Windows profile you are running Notes in a Citrix environment 4SO support it all
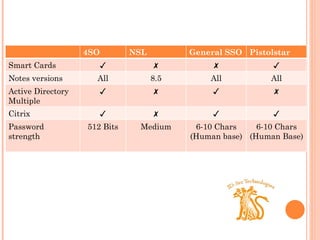
- 13. 4SO NSL General SSO Pistolstar Smart Cards â â â â Notes versions All 8.5 All All Active Directory Multiple passwords â â â â Citrix â â â â Password strength 512 Bits Medium 6-10 Chars (Human base) 6-10 Chars (Human Base)
- 14. PISTOLSTAR PistolStar Power Power is a full password synchronized between Notes and Active Directory. In order to synchronize password from Windows to Notes must replace GINA.DLL in every client. Keep a human based password â 4SO have a very long password
- 15. ID VAULT AND SSO SOLUTIONS Use Servers to store the passwords â Single point of failure. Keep a human based password â 4SO have a very long password
- 16. SUCCESS STORIES Major bank in Israel â 13,000 Users, works since 2008, not even one support call. Ministry of Finance â 2,000 users, works since 2009, not even one support call. Ministry of Interior â 2,000 users, works since 2009, not even one support call. Civil Services â 1,300 users, works since 2009, not even one support call. Governmental Organization â 3,500 users, works since 2009, not even one support call.