DevSecOps 實踐與 GitHub 進階安全: 建立安全的開發流程
- 1. DevSecOps 實踐與 GitHub 進階安 全:建立安全的開發流程 George Chen / 微軟雲端安全架構師 Duran Hsieh / 微軟最有價值專家
- 2. Agenda Announcing GitHub Advanced Security for Azure DevOps (GHAzDO)—available now! ? Why GHAzDO? ? Demo of GitHub Advanced Security ? Demo of Azure DevOps Advanced Security ? GHAzDO billing and signup info DevSecOps and best practices ? What is DevSecOps? ? Cloud Native Security ? DevSecOps Best Practices
- 3. What is DevSecOps ? Security Challenges with DevOps Practices ? Emphasis on delivery, not security ? General DevOps practices do not inherently support application security concepts ? Traditional automated testing does not focus on Security Testing ? DevOps teams may lack security knowledge ? Prevalent use of Open Source libraries without the use of Software Composition Analysis tools
- 4. What is DevSecOps ? DevSecOps applies security checks and controls into the DevOps pipeline automatically and transparently, without slowing the development & release process ? Relies on continuous learning instead of security gates ? “Shift-left” strategy where security issues are discovered and dealt with earlier in the build and release cycles
- 5. Security in DevOps workflow cspkg DEV 1 3 5 6 7 8 4 version controlled source code version controlled security config 2 write secure code security acceptance tests validate infra compliance config deployment security/compliance assessment continuously monitor for external threats to application/infra developer scenario InfoSec scenario config deployment 5 static analysis of code OSS library scanning threat/vulnerability scanning
- 6. Cloud Native Security ? Code ? Application code is one of the primary attack surfaces over which you have the most control ? Container ? Container Vulnerability Scanning and OS Dependency Security ? Image Signing and Enforcement ? Cluster ? Securing the cluster components that are configurable ? Securing the applications which run in the cluster ? Cloud ? Cloud provider security ? Infrastructure security Source: https://kubernetes.io/docs/concepts/security/overview/
- 7. DevSecOps Best Practices ? Shift Left ? Security testing should be integrated as early as possible into the software development process, rather than tacked on at the end. ? Why Shift Left ? Deployment is the most expensive during in the software development process ? If the team only performs security checks and controls during the delivery phase ? Increase cost ? Undeliverable ? Delivery of unstable software ? Shift Left Implementation ? Development Phrase - Find and solve information security problems via IDE ? Scan in build phrase - Spot a threat and fix it before the code leaves the engineer
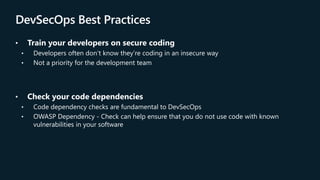
- 8. DevSecOps Best Practices ? Train your developers on secure coding ? Developers often don’t know they’re coding in an insecure way ? Not a priority for the development team ? Check your code dependencies ? Code dependency checks are fundamental to DevSecOps ? OWASP Dependency - Check can help ensure that you do not use code with known vulnerabilities in your software
- 9. DevSecOps Best Practices ? Encrypt Data in Motion ? Data should be encrypted when being transferred between different systems ? Protect the data from being intercepted and read by unauthorized people ? Use secrets management tools ? Secrets management is the process of securely storing and managing secrets. ? There are a number of secrets management tools available, such as Hashicorp’s Vault and Azure Key Vault ? Manage secrets and provide access control and auditing capabilities.
- 10. DevSecOps Best Practices ? Use role-based access control (RBAC) ? Organizations need to trust that the right people have access to the right information at the right time. ? Control who has access to what resources in an organization. ? Control what actions users can take with those resources. ? Prevent unauthorized access to sensitive data and systems. ? Ensure that only authorized users can make changes to systems and data.
- 11. DevSecOps Best Practices ? Use role-based access control (RBAC) ? Organizations need to trust that the right people have access to the right information at the right time. ? Control who has access to what resources in an organization. ? Control what actions users can take with those resources. ? Prevent unauthorized access to sensitive data and systems. ? Ensure that only authorized users can make changes to systems and data.
- 12. Cloud resource monitoring Code Operate & monitor Continuous integration (CI) Continuous deployment (CD) Secret scanning & push protection Code & dependency scanning Signature & policy enforcement
- 13. Native functionality built directly into Azure DevOps to protect Azure Repos and Pipelines Code scanning Static Application Security Testing (SAST) using CodeQL C#, C/C++, Java, Python, Go, JavaScript/TypeScript and more Dependency scanning Software Composition Analysis (SCA) to identify open-source supply chain vulnerabilities Direct and transitive dependencies Secret scanning Find and fix secrets already exposed in your Azure Repos Block new pushes that would expose new secrets
- 14. Demo內容示意圖 – Enable GitHub Advanced Security (Secret Scan)
- 15. Demo內容示意圖 – GitHub Advanced Security (Secret Scan)
- 16. DEMO 內容示意圖 (Push Protection with VSCode)
- 17. DEMO 內容示意圖 (Push Protection with VSCode)
- 18. DEMO 內容示意圖 (Dependency Scan)
- 19. DEMO 內容示意圖 (Code Scan)
- 20. Demo – Enable Azure DevOps Advanced Security
- 22. Demo - Azure DevOps Advanced Security
- 23. Demo – Secret Scan of Advanced Security
- 27. Demo – Depenency Scan of Advanced Security
- 32. Demo – CodeQL Scan of Advanced Security
- 37. GHAzDO Public Preview available now! Sign up here: https://aka.ms/advancedsecurity-signup ? Billed at $49 per active committer (full price) starting June 1 ? Billed directly to your Azure subscription based on consumed usage ? No commitment necessary, scale up or down or off at any time by turning GHAzDO on/off for more repos ? Users are counted at the Azure subscription level We’ll be setting up enablement sessions with teams who sign up
- 38. Summary ? DevSecOps applies security checks and controls into the DevOps pipeline automatically and transparently, without slowing the development & release process. ? Deployment is the most expensive during in the software development process. ? Security testing should be integrated as early as possible into the software development process.
- 39. ? Copyright Microsoft Corporation. All rights reserved. Thank you!