IDS.pptx
- 2. ’é¦ What is Intrusion Detection System ’é¦ Attack Types ’é¦ Problem Definition ’é¦ KDDcup99 ’é¦ Reference Paper
- 5. ’é¦ Objective ’é¦ Build a machine learning model/Deep learning model (classifiers) to detect the potential attack type based on features in connections provided in the datasets. ’é¦ Datasets: KDD cup 1999 https://www.kdd.org/kdd-cup/view/kdd-cup-1999/Data
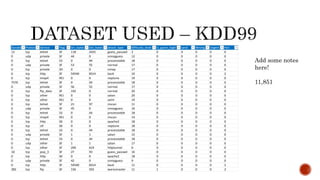
- 6. Duration Protocol_type Service Flag Src_bytes Dst_bytes attack_type difficulty_level Is_guest_login Land Wrong_fragment Urgent Hot 13 tcp telnet SF 118 2425 guess_passwd 2 0 0 0 0 0 0 udp private SF 44 0 snmpguess 12 0 0 0 0 0 0 tcp telnet S3 0 44 processtable 18 0 0 0 0 0 0 udp private SF 53 55 normal 17 0 0 0 0 0 0 tcp private SH 0 0 nmap 17 0 0 0 0 0 0 tcp http SF 54540 8314 back 10 0 0 0 0 2 0 tcp imap4 REJ 0 0 neptune 19 0 0 0 0 0 7570 tcp telnet SF 0 44 processtable 18 0 0 0 0 0 0 udp private SF 56 52 normal 17 0 0 0 0 0 0 tcp ftp_data SF 192 0 normal 20 0 0 0 0 0 0 tcp other REJ 0 0 satan 20 0 0 0 0 0 0 tcp other REJ 0 0 saint 19 0 0 0 0 0 0 tcp telnet SF 21 97 mscan 11 0 0 0 0 0 0 udp private SF 45 0 snmpguess 16 0 0 0 0 0 0 tcp telnet S3 0 44 processtable 18 0 0 0 0 0 0 tcp imap4 REJ 0 0 mscan 14 0 0 0 0 0 0 tcp http S0 0 0 apache2 18 0 0 0 0 0 0 tcp ctf S0 0 0 neptune 18 0 0 0 0 0 0 tcp telnet S3 0 44 processtable 18 0 0 0 0 0 0 udp private SF 1 1 satan 15 0 0 0 0 0 0 tcp telnet S3 0 44 processtable 18 0 0 0 0 0 0 udp other SF 1 1 satan 17 0 0 0 0 0 0 tcp other SF 240 619 httptunnel 6 0 0 0 0 0 10 tcp pop_3 SF 27 93 guess_passwd 16 0 0 0 0 0 0 tcp http S0 0 0 apache2 18 0 0 0 0 0 0 udp private SF 42 0 snmpguess 9 0 0 0 0 0 0 tcp http SF 54540 8314 back 11 0 0 0 0 2 282 tcp ftp SF 156 593 warezmaster 11 1 0 0 0 2 Add some notes here! 11,851
- 7. ’é¦ Normal and Attack diagram ’é¦ see kdd video
- 8. Through this paper, the author compares various data pre- processing methods categorized as: 1- Feature selection, ŌĆó Chi-Squared Test (CST) ŌĆó Random forest classifier (RFC) ŌĆó Extra tree classifier (ETC) 2- Feature encoding, ŌĆó One hot encoder (OHT) ŌĆó Binary encoder (BE) ŌĆó Frequency encoder (FE) ŌĆó Label encoder (LE) 3- and Feature scaling. ŌĆó Min-Max (MM) ŌĆó Standardization (Std) ŌĆó Binarizing(Bin) ŌĆó Normalizing(Norm) The pre-processed data and an Autoencoder are used for further processing to get the best features and use them with a deep neural network for classification.