IT Breakafst for FIN 28 sierpnia 2014, Warszawa, Pałac Sobańskich
1 like308 views
The document discusses a modern architecture solution for data management focused on secure, efficient file sharing and synchronization across mobile and public devices while minimizing risks associated with data sprawl and security breaches. It emphasizes the importance of maintaining control and protection of corporate data within a private cloud environment to support innovation and user mobility. Key features include automatic protection of data, version recovery, and the ability to easily share files and folders, all while integrating with existing IT infrastructures.
1 of 14
Download to read offline







Ad
Recommended
GWAVACon - Files Matters (English)
GWAVACon - Files Matters (English)GWAVA
Ěý
This document summarizes Novell's file management solution and products. It discusses how Novell products like File Reporter and Storage Manager provide storage intelligence, automation of file management and access governance. These solutions help with issues like understanding file usage, optimizing storage, managing user access and automating file operations. The document also advertises an upcoming product manager meeting to discuss specific Novell collaboration and file management products.The Enterprise File Fabric for Google Cloud Platform
The Enterprise File Fabric for Google Cloud PlatformHybrid Cloud
Ěý
The document outlines the capabilities of the Enterprise File Fabric platform from Storage Made Easy, designed for efficient data transfer and management between on-premises and cloud storage, particularly Google Cloud Platform. It emphasizes cost reduction, quick asset movement, comprehensive security, and governance policies, all while avoiding vendor lock-in and the need for expensive hardware. The solution offers fast upload/download speeds, a unified virtual file system, and enhanced data transfer acceleration, making it suitable for enterprises aiming to manage their cloud data sprawl effectively.Q90 saving projectfiles
Q90 saving projectfilesErik Rusek - Cybersecurity Strategie und Awareness
Ěý
While working on customer projects, sensitive data like plans, specifications, financial data and project results will be accessed. Saving this data only on notebooks poses risks like unauthorized access if the notebook is lost or stolen, the notebook becoming unusable if infected with malware, and data being inaccessible to colleagues if only stored locally. To mitigate these risks, project files should be saved to the company's network share as soon as possible to be included in regular backups, or saved locally if no network connection but copied to the share when a connection is available. Proper handling of sensitive customer and project data is important.Firewall
FirewallNaga Dinesh
Ěý
This document discusses firewalls, including their definition, history, types, and purposes. A firewall is a program or hardware device that filters network traffic between the internet and an internal network based on a set of security rules. There are different types of firewalls, including packet filtering routers, application-level gateways, and circuit-level gateways. Firewalls aim to restrict network access and protect internal systems by only allowing authorized traffic according to a security policy.Are You Leveraging the Cloud? Or is it Leveraging You?
Are You Leveraging the Cloud? Or is it Leveraging You?Tom Mumford
Ěý
The document discusses the complexities of utilizing cloud technologies in organizations, highlighting the risks of 'shadow IT' where employees use unapproved tools that can jeopardize data security. It emphasizes the importance of leveraging a comprehensive solution like CTERA to enhance secure collaboration and file sharing, mitigate cyber risks, and maintain control over sensitive data. Additionally, CTERA offers a scalable service (CTaaS) to provide security and functionality for various organizations, ensuring compliance and resilience while improving business continuity.Big data in term of security measure
Big data in term of security measureYaakub Idris
Ěý
This document discusses security measures for Hadoop environments. It outlines existing issues with Hadoop's architecture like distributed nodes and lack of security. It proposes solutions like using Kerberos and encryption. It also discusses how some corporate security solutions like IBM and Solera Networks use big data analytics to detect abnormalities and insider threats in real-time. The conclusion states that traditional security solutions are insufficient for big data and real-time analytics is needed to derive actionable security intelligence from data streams.DirectShare by Cloudtenna
DirectShare by CloudtennaChristian Petrou
Ěý
Cloudtenna's DirectShare software allows users to securely collaborate and share large files without uploading to the cloud, improving productivity and speed. It integrates seamlessly with existing network storage, maintaining control over files while providing external sharing capabilities with robust security measures. This solution helps enterprises manage file sharing demands from employees while preventing unauthorized third-party applications.Using Tags to adress big data and mobile challanges
Using Tags to adress big data and mobile challangesLars Jeppesen
Ěý
The document outlines the learning objectives of a session on using tags to manage records in the face of big data and mobile challenges. It introduces the tag cloud concept as a tool for simplifying information retrieval and encourages data exploration while supporting mobile access. Additionally, it highlights the evolving role of tags from search functionalities to facilitating actionable tasks.EMC Storage Redefine FILE
EMC Storage Redefine FILEsolarisyougood
Ěý
This document discusses the challenges of unstructured data growth and how EMC is addressing them through solutions that consolidate, protect, discover, and enable mobile access to unstructured data. Key points include:
- Unstructured data such as documents, presentations, and spreadsheets is growing rapidly and becoming more difficult for organizations to manage.
- EMC offers solutions like Isilon for consolidation, Data Domain for protection, and Syncplicity for mobile access to help customers better manage their unstructured data.
- EMC services can also help customers discover and classify their unstructured data to build effective information management strategies.The Enterprise File Fabric for Media & Entertainment Industry | Solution Brief
The Enterprise File Fabric for Media & Entertainment Industry | Solution BriefHybrid Cloud
Ěý
The document summarizes a solution brief for the Enterprise File Fabric from Storage Made Easy. The File Fabric provides media companies with secure access and collaboration across distributed data stores. It offers a single interface, high-speed file transfers, integrated workflows and approvals, encryption and access controls to streamline secure collaboration throughout content production and distribution.Third Party Access Control
Third Party Access Controlfrancisdinha
Ěý
This document discusses third party access control and how OpenVPN Access Server can provide logical access control. It explains that Access Server uses LDAP to authenticate users via Active Directory, allowing different levels of access for employees and third parties like contractors. It provides an example of a home security company that used Access Server and Active Directory to give contractors access only to email and workforce management servers, while employees received greater network access.Secure Enterprise Content Management and File Management for the Legal Sector...
Secure Enterprise Content Management and File Management for the Legal Sector...Hybrid Cloud
Ěý
The document outlines the Enterprise File Fabric solution designed for the legal sector, focusing on secure content management, file sharing, and collaboration features tailored to meet compliance and governance standards. Key benefits include integration with existing repositories, secure client communications, data loss protection, and ransomware protection. The solution aims to unify on-premises and cloud data management, enhancing productivity and security for law firms.Data security in the cloud
Data security in the cloud IBM Security
Ěý
The document discusses cloud data security challenges and emphasizes the need for comprehensive protection strategies due to increasing security incidents and data breaches. It outlines solutions provided by IBM's Infosphere Guardium, including continuous monitoring, vulnerability assessments, and compliance automation to safeguard sensitive data in cloud and virtual environments. Additionally, it highlights the philosophy of understanding data value and risk to enhance overall security measures and compliance with regulations.Cloud Managed Services: Cloud Infrastructure
Cloud Managed Services: Cloud InfrastructureThe TNS Group
Ěý
The TNS Group offers collaborative design and management of cloud infrastructure to enhance business efficiency and cost management. Their services include security features like encryption and multi-factor authentication, mobile access to resources, scalability for fluctuating demands, and reduced operational costs. Partnering with TNS ensures businesses maintain a competitive edge through 24/7 support and access to advanced technology.True IDC Share
True IDC ShareKornthawat Phichitoakkhanit
Ěý
True IDC Share Services provides cloud storage capabilities tailored for small and medium enterprises (SMEs). It offers simple, fast sharing of files anytime, anywhere. Users can improve productivity through collaboration enabled by fast access to shared files. The service also provides reliable backup and archiving in the cloud for business continuity.Cloudciti Enterprise File Share Services
Cloudciti Enterprise File Share ServicesPT Datacomm Diangraha
Ěý
This document provides an overview of Cloudciti Enterprise File Share (CEFS), a content collaboration platform that allows secure file sharing across devices. It defines digital workspaces and the challenges they aim to address. CEFS increases workforce productivity by enabling syncing and mobile access offline. It facilitates collaboration across boundaries through features like file sharing, requests, and notifications. CEFS integrates with Active Directory and APIs. It protects data through encryption at rest and in transit, remote wiping, and auditing. The document compares CEFS features to competitors and provides use case examples for industries like accounting, insurance, and healthcare.Enadoc how does it work
Enadoc how does it workLars Jeppesen
Ěý
Enadoc is a cloud-based document imaging and e-archiving solution accessible on various platforms without the need for software installation. It enables users to capture, upload, and tag documents using advanced OCR and machine learning for efficient organization and retrieval. Enadoc also offers scalability, advanced security features, and the flexibility to store data in multiple environments.CloudControl - Enterprise backup, access and collaboartion solution from Soft...
CloudControl - Enterprise backup, access and collaboartion solution from Soft...ILYA ROITMAN
Ěý
CloudControl provides a secure on-premise solution for file sharing and collaboration that gives IT control back from consumer cloud services. It hosts files and syncs data between devices and a server located on the customer's network. This minimizes security risks and data leaks while providing flexibility and ease of use similar to popular cloud services. Customizable features include file sharing, backup, syncing, and integration with existing user directories and storage. SoftControl offers support and customization services to help customers implement CloudControl.The Enterprise File Fabric for Healthcare and Genomics | SME Solution Brief
The Enterprise File Fabric for Healthcare and Genomics | SME Solution BriefHybrid Cloud
Ěý
The document outlines the Enterprise File Fabric solution that facilitates the management of genomic data within the life science community, ensuring secure and efficient data access for researchers, developers, and health organizations. It highlights features such as integration with scalable storage, secure access, a web-based genomics viewer, and compliance with regulatory requirements. Additionally, it emphasizes the importance of unified data management to ensure governance, security, and compliance with data protection regulations.Webinar: Endpoint Backup is not Enough - You Need an End-user Data Strategy
Webinar: Endpoint Backup is not Enough - You Need an End-user Data StrategyStorage Switzerland
Ěý
The document outlines the importance of developing a comprehensive end-user data strategy, which goes beyond mere endpoint backup to encompass data protection, sharing, and management. It identifies three key pillars: protection of laptops and SaaS applications, management of data regulation and compliance, and sharing capabilities to mitigate risks associated with shadow IT and data leakage. With increasing data risks, compliance demands, and ransomware threats, organizations are urged to adopt holistic data governance and protection strategies to safeguard sensitive information.BlackBerry Workspaces: Solutions for Technology & Manufacturing
BlackBerry Workspaces: Solutions for Technology & ManufacturingBlackBerry
Ěý
BlackBerry Workspaces enhances mobile collaboration while ensuring document security for enterprises with its unique data-centric architecture. It allows control and tracking of shared files across devices, maintains high-level data encryption, and supports easy-to-use digital rights management features. This solution addresses risks associated with traditional document-sharing methods, especially in technology and manufacturing sectors, by providing a seamless user experience for managing sensitive files securely.Look Up
Look UpRobert Crane
Ěý
The document discusses the transformative impact of cloud computing on technology and business models, emphasizing its ability to streamline operations and reduce costs through a utility payment model. It highlights the transition from traditional in-house services, like email servers, to cloud solutions, which offer increased accessibility and reduced maintenance burdens. The narrative also addresses challenges such as security and bandwidth, while encouraging stakeholders to embrace cloud computing to remain competitive in an evolving landscape.Enterprise File Management Systems
Enterprise File Management SystemsSwiftTech Solutions, Inc.
Ěý
The document discusses the advantages and drawbacks of consumer file sharing services compared to enterprise file management systems, emphasizing the importance of security and regulatory compliance. It highlights enterprise features such as data encryption, mobile access, and activity tracking, which make them more secure. Additionally, it mentions various application options for enterprise file management and offers consultation services from Swifttech Solutions.Trusted Edge Ice For Owa 2009
Trusted Edge Ice For Owa 2009Alexis Brown
Ěý
1) Trusted Edge ICE allows corporations to define and implement document retention and filing policies for Microsoft Outlook Web Access emails.
2) It classifies emails at creation according to corporate policy and ensures all copies are retained or disposed of appropriately.
3) Centrally managed policies allow emails accessed on OWA to be classified and managed remotely according to the organization's retention schedule, even when users are offline.Don't manage strategic data in email
Don't manage strategic data in emailFelix Puetsch
Ěý
rogr.io is a secure platform designed for asynchronous data exchange and collaboration, mitigating the risks associated with traditional email and manual data handling. It facilitates the management of strategic data with features such as data requests, tracking, and secure publishing, ensuring data security and process control. The platform is B2B-centric, cloud-based, and integrates with existing tools, aiming to enhance efficiency in various data handling processes.Cloud infrastructure solutions
Cloud infrastructure solutions jbsmidis
Ěý
JBS offers cloud infrastructure solutions designed to create responsive and user-friendly IT systems, addressing various business challenges. Partnering with IBM, they focus on enhancing cybersecurity, data integrity, and risk reduction while helping clients leverage machine learning and next-gen manufacturing processes. JBS aims to transform existing systems into agile and flexible platforms while minimizing the risk of hardware or software failures through managed services.The connection forweb p12
The connection forweb p12Bloombase
Ěý
The document discusses the challenges companies face with data encryption and security in existing computing infrastructures, especially regarding legacy systems. It highlights the risks of unencrypted sensitive data and proposes the HPE Enterprise Secure Key Manager and Bloombase StoreSafe solution as an effective means to enhance data security without major system overhauls. The solution offers operational efficiency, vendor agnosticism, and compliance with regulatory standards while ensuring seamless integration into current systems.Managing storage on Prem and in Cloud
Managing storage on Prem and in CloudHoward Marks
Ěý
This document discusses managing storage across public and private resources. It covers the evolution of on-site storage management, storage options in the public cloud, and challenges of managing hybrid cloud storage. Key topics include the transition from siloed storage to software-defined storage, various cloud storage services like object storage and block storage, challenges of public cloud limitations, and solutions for connecting on-site and cloud storage like gateways, file systems, and caching appliances.Datanow datasheet
Datanow datasheetNuno Alves
Ěý
The Appsense DataNow product provides anywhere data access with enterprise-class governance, addressing the gap in IT infrastructure for mobile productivity. It allows seamless offline access to corporate data while maintaining visibility and control for IT teams and offers a flexible policy creation interface for data governance. With options for integrating with existing storage or transitioning to cloud solutions, DataNow caters to evolving business needs without compromising security.Transforming your Information Infrastructure with IBM’s Storage Cloud Solution
Transforming your Information Infrastructure with IBM’s Storage Cloud SolutionIBM India Smarter Computing
Ěý
This document discusses IBM's cloud storage solution for transforming information infrastructure. It provides three examples of how cloud storage could help organizations by allowing dynamic storage management: 1) A company running out of disk space on a Friday could non-disruptively add storage in the cloud. 2) Old storage systems can be replaced by migrating data to the cloud without downtime. 3) Cloud storage provides disaster recovery by replicating and accessing data in the cloud when primary storage fails.More Related Content
What's hot (19)
EMC Storage Redefine FILE
EMC Storage Redefine FILEsolarisyougood
Ěý
This document discusses the challenges of unstructured data growth and how EMC is addressing them through solutions that consolidate, protect, discover, and enable mobile access to unstructured data. Key points include:
- Unstructured data such as documents, presentations, and spreadsheets is growing rapidly and becoming more difficult for organizations to manage.
- EMC offers solutions like Isilon for consolidation, Data Domain for protection, and Syncplicity for mobile access to help customers better manage their unstructured data.
- EMC services can also help customers discover and classify their unstructured data to build effective information management strategies.The Enterprise File Fabric for Media & Entertainment Industry | Solution Brief
The Enterprise File Fabric for Media & Entertainment Industry | Solution BriefHybrid Cloud
Ěý
The document summarizes a solution brief for the Enterprise File Fabric from Storage Made Easy. The File Fabric provides media companies with secure access and collaboration across distributed data stores. It offers a single interface, high-speed file transfers, integrated workflows and approvals, encryption and access controls to streamline secure collaboration throughout content production and distribution.Third Party Access Control
Third Party Access Controlfrancisdinha
Ěý
This document discusses third party access control and how OpenVPN Access Server can provide logical access control. It explains that Access Server uses LDAP to authenticate users via Active Directory, allowing different levels of access for employees and third parties like contractors. It provides an example of a home security company that used Access Server and Active Directory to give contractors access only to email and workforce management servers, while employees received greater network access.Secure Enterprise Content Management and File Management for the Legal Sector...
Secure Enterprise Content Management and File Management for the Legal Sector...Hybrid Cloud
Ěý
The document outlines the Enterprise File Fabric solution designed for the legal sector, focusing on secure content management, file sharing, and collaboration features tailored to meet compliance and governance standards. Key benefits include integration with existing repositories, secure client communications, data loss protection, and ransomware protection. The solution aims to unify on-premises and cloud data management, enhancing productivity and security for law firms.Data security in the cloud
Data security in the cloud IBM Security
Ěý
The document discusses cloud data security challenges and emphasizes the need for comprehensive protection strategies due to increasing security incidents and data breaches. It outlines solutions provided by IBM's Infosphere Guardium, including continuous monitoring, vulnerability assessments, and compliance automation to safeguard sensitive data in cloud and virtual environments. Additionally, it highlights the philosophy of understanding data value and risk to enhance overall security measures and compliance with regulations.Cloud Managed Services: Cloud Infrastructure
Cloud Managed Services: Cloud InfrastructureThe TNS Group
Ěý
The TNS Group offers collaborative design and management of cloud infrastructure to enhance business efficiency and cost management. Their services include security features like encryption and multi-factor authentication, mobile access to resources, scalability for fluctuating demands, and reduced operational costs. Partnering with TNS ensures businesses maintain a competitive edge through 24/7 support and access to advanced technology.True IDC Share
True IDC ShareKornthawat Phichitoakkhanit
Ěý
True IDC Share Services provides cloud storage capabilities tailored for small and medium enterprises (SMEs). It offers simple, fast sharing of files anytime, anywhere. Users can improve productivity through collaboration enabled by fast access to shared files. The service also provides reliable backup and archiving in the cloud for business continuity.Cloudciti Enterprise File Share Services
Cloudciti Enterprise File Share ServicesPT Datacomm Diangraha
Ěý
This document provides an overview of Cloudciti Enterprise File Share (CEFS), a content collaboration platform that allows secure file sharing across devices. It defines digital workspaces and the challenges they aim to address. CEFS increases workforce productivity by enabling syncing and mobile access offline. It facilitates collaboration across boundaries through features like file sharing, requests, and notifications. CEFS integrates with Active Directory and APIs. It protects data through encryption at rest and in transit, remote wiping, and auditing. The document compares CEFS features to competitors and provides use case examples for industries like accounting, insurance, and healthcare.Enadoc how does it work
Enadoc how does it workLars Jeppesen
Ěý
Enadoc is a cloud-based document imaging and e-archiving solution accessible on various platforms without the need for software installation. It enables users to capture, upload, and tag documents using advanced OCR and machine learning for efficient organization and retrieval. Enadoc also offers scalability, advanced security features, and the flexibility to store data in multiple environments.CloudControl - Enterprise backup, access and collaboartion solution from Soft...
CloudControl - Enterprise backup, access and collaboartion solution from Soft...ILYA ROITMAN
Ěý
CloudControl provides a secure on-premise solution for file sharing and collaboration that gives IT control back from consumer cloud services. It hosts files and syncs data between devices and a server located on the customer's network. This minimizes security risks and data leaks while providing flexibility and ease of use similar to popular cloud services. Customizable features include file sharing, backup, syncing, and integration with existing user directories and storage. SoftControl offers support and customization services to help customers implement CloudControl.The Enterprise File Fabric for Healthcare and Genomics | SME Solution Brief
The Enterprise File Fabric for Healthcare and Genomics | SME Solution BriefHybrid Cloud
Ěý
The document outlines the Enterprise File Fabric solution that facilitates the management of genomic data within the life science community, ensuring secure and efficient data access for researchers, developers, and health organizations. It highlights features such as integration with scalable storage, secure access, a web-based genomics viewer, and compliance with regulatory requirements. Additionally, it emphasizes the importance of unified data management to ensure governance, security, and compliance with data protection regulations.Webinar: Endpoint Backup is not Enough - You Need an End-user Data Strategy
Webinar: Endpoint Backup is not Enough - You Need an End-user Data StrategyStorage Switzerland
Ěý
The document outlines the importance of developing a comprehensive end-user data strategy, which goes beyond mere endpoint backup to encompass data protection, sharing, and management. It identifies three key pillars: protection of laptops and SaaS applications, management of data regulation and compliance, and sharing capabilities to mitigate risks associated with shadow IT and data leakage. With increasing data risks, compliance demands, and ransomware threats, organizations are urged to adopt holistic data governance and protection strategies to safeguard sensitive information.BlackBerry Workspaces: Solutions for Technology & Manufacturing
BlackBerry Workspaces: Solutions for Technology & ManufacturingBlackBerry
Ěý
BlackBerry Workspaces enhances mobile collaboration while ensuring document security for enterprises with its unique data-centric architecture. It allows control and tracking of shared files across devices, maintains high-level data encryption, and supports easy-to-use digital rights management features. This solution addresses risks associated with traditional document-sharing methods, especially in technology and manufacturing sectors, by providing a seamless user experience for managing sensitive files securely.Look Up
Look UpRobert Crane
Ěý
The document discusses the transformative impact of cloud computing on technology and business models, emphasizing its ability to streamline operations and reduce costs through a utility payment model. It highlights the transition from traditional in-house services, like email servers, to cloud solutions, which offer increased accessibility and reduced maintenance burdens. The narrative also addresses challenges such as security and bandwidth, while encouraging stakeholders to embrace cloud computing to remain competitive in an evolving landscape.Enterprise File Management Systems
Enterprise File Management SystemsSwiftTech Solutions, Inc.
Ěý
The document discusses the advantages and drawbacks of consumer file sharing services compared to enterprise file management systems, emphasizing the importance of security and regulatory compliance. It highlights enterprise features such as data encryption, mobile access, and activity tracking, which make them more secure. Additionally, it mentions various application options for enterprise file management and offers consultation services from Swifttech Solutions.Trusted Edge Ice For Owa 2009
Trusted Edge Ice For Owa 2009Alexis Brown
Ěý
1) Trusted Edge ICE allows corporations to define and implement document retention and filing policies for Microsoft Outlook Web Access emails.
2) It classifies emails at creation according to corporate policy and ensures all copies are retained or disposed of appropriately.
3) Centrally managed policies allow emails accessed on OWA to be classified and managed remotely according to the organization's retention schedule, even when users are offline.Don't manage strategic data in email
Don't manage strategic data in emailFelix Puetsch
Ěý
rogr.io is a secure platform designed for asynchronous data exchange and collaboration, mitigating the risks associated with traditional email and manual data handling. It facilitates the management of strategic data with features such as data requests, tracking, and secure publishing, ensuring data security and process control. The platform is B2B-centric, cloud-based, and integrates with existing tools, aiming to enhance efficiency in various data handling processes.Cloud infrastructure solutions
Cloud infrastructure solutions jbsmidis
Ěý
JBS offers cloud infrastructure solutions designed to create responsive and user-friendly IT systems, addressing various business challenges. Partnering with IBM, they focus on enhancing cybersecurity, data integrity, and risk reduction while helping clients leverage machine learning and next-gen manufacturing processes. JBS aims to transform existing systems into agile and flexible platforms while minimizing the risk of hardware or software failures through managed services.The connection forweb p12
The connection forweb p12Bloombase
Ěý
The document discusses the challenges companies face with data encryption and security in existing computing infrastructures, especially regarding legacy systems. It highlights the risks of unencrypted sensitive data and proposes the HPE Enterprise Secure Key Manager and Bloombase StoreSafe solution as an effective means to enhance data security without major system overhauls. The solution offers operational efficiency, vendor agnosticism, and compliance with regulatory standards while ensuring seamless integration into current systems.Similar to IT Breakafst for FIN 28 sierpnia 2014, Warszawa, Pałac Sobańskich (20)
Managing storage on Prem and in Cloud
Managing storage on Prem and in CloudHoward Marks
Ěý
This document discusses managing storage across public and private resources. It covers the evolution of on-site storage management, storage options in the public cloud, and challenges of managing hybrid cloud storage. Key topics include the transition from siloed storage to software-defined storage, various cloud storage services like object storage and block storage, challenges of public cloud limitations, and solutions for connecting on-site and cloud storage like gateways, file systems, and caching appliances.Datanow datasheet
Datanow datasheetNuno Alves
Ěý
The Appsense DataNow product provides anywhere data access with enterprise-class governance, addressing the gap in IT infrastructure for mobile productivity. It allows seamless offline access to corporate data while maintaining visibility and control for IT teams and offers a flexible policy creation interface for data governance. With options for integrating with existing storage or transitioning to cloud solutions, DataNow caters to evolving business needs without compromising security.Transforming your Information Infrastructure with IBM’s Storage Cloud Solution
Transforming your Information Infrastructure with IBM’s Storage Cloud SolutionIBM India Smarter Computing
Ěý
This document discusses IBM's cloud storage solution for transforming information infrastructure. It provides three examples of how cloud storage could help organizations by allowing dynamic storage management: 1) A company running out of disk space on a Friday could non-disruptively add storage in the cloud. 2) Old storage systems can be replaced by migrating data to the cloud without downtime. 3) Cloud storage provides disaster recovery by replicating and accessing data in the cloud when primary storage fails.Transforming your Information Infrastructure with IBM's Storage Cloud Solutio...
Transforming your Information Infrastructure with IBM's Storage Cloud Solutio...IBM India Smarter Computing
Ěý
IBM's cloud storage solution allows organizations to transform their information infrastructure by providing dynamic storage management, scalable capacity and performance, and centralized management. It implements a storage cloud using proven IBM technologies like GPFS and Tivoli Storage Manager. Administrators can dynamically allocate storage space, migrate data between storage tiers automatically using policies, and manage billions of files across multiple petabytes of storage from a single interface.Disruptive Tech - Cloud Computing
Disruptive Tech - Cloud ComputingErin Tilley
Ěý
Cloud computing changed the computing landscape by introducing a layer of abstraction between users and dedicated hardware resources. This allowed for increased utilization of resources through automated data storage and on-demand access to applications and files from any device. It lowered barriers to entry for small businesses and entrepreneurs by reducing costs and IT overhead. Individuals also benefit from greater mobility, convenience, and less concern over personal storage limits due to cheaper cloud storage options.NetApp Industry Keynote - Flash Memory Summit - Aug2015
NetApp Industry Keynote - Flash Memory Summit - Aug2015Val Bercovici
Ěý
This document discusses the evolution of data center architectures, including hyperscale vs enterprise architectures. It notes that hyperscale architectures focus on scale-out designs using commodity hardware, while enterprise focuses more on scale-up. Emerging technologies like non-volatile memory and software-defined infrastructure are converging these approaches. The document also covers how these trends impact storage strategies and the economics of hybrid cloud computing.Development Model for The Cloud
Development Model for The Cloudumityalcinalp
Ěý
This document discusses the development model for cloud computing platforms. It provides an overview of computing history from Turing machines to modern application platforms and servers. It then discusses how cloud computing aims to further reduce complexity by providing hosted services, software, and platforms. The document compares traditional on-premise application development with challenges to the cloud development approach using services like Amazon Web Services, Microsoft Azure, Google App Engine, and Salesforce Force.com platform. It analyzes commonalities and differences between these platforms in terms of abstraction levels, application capabilities, and developer experience.Move your Data Center to the Cloud
Move your Data Center to the CloudRedZone Technologies
Ěý
The document discusses moving a data center to the cloud. It outlines an agenda for analyzing such a transition, including considering cloud security, understanding the current environment, and comparing costs and contracts. The analysis section lists many line items to compare between the current data center and cloud providers, such as infrastructure, licensing costs, disaster recovery, and support. Conducting a thorough analysis of needs, strengths, and weaknesses is important to understand if cloud computing is suitable.OSS Presentation Keynote by Per Sedihn
OSS Presentation Keynote by Per SedihnOpenStorageSummit
Ěý
The document discusses the need for IT organizations to adapt to business demands for faster delivery of services and information. It summarizes the background and services of Proact IT Group, a large European IT services company. The rest of the document outlines challenges facing IT, including the rise of public cloud usage outside of IT policies, and explores how technologies like virtualization, storage tiering, and data classification can help IT deliver services in a more automated, flexible and cost effective manner aligned with business needs.Windows Azure overview webinar by Sentri
Windows Azure overview webinar by SentriSentri
Ěý
The document discusses Microsoft's Windows Azure cloud platform. It describes Azure as an open and flexible platform that allows users to focus on their projects instead of infrastructure. Azure provides agility through services like virtual machines, databases, storage and networking that can be accessed on demand over the internet.How to Succeed in the Cloud (Financially)
How to Succeed in the Cloud (Financially)Rand Group
Ěý
The document discusses cloud computing, outlining its compelling aspects, business demands, and the necessary finance-level actions for 2013. It highlights the benefits of cloud services, including cost reduction, flexibility, and scalability, and forecasts significant growth in the market for cloud-based applications. Key issues such as security, compliance, control, and disaster recovery are also addressed, emphasizing the advantages of transitioning to cloud solutions.Three Steps to Modern Media Asset Management with Active Archive
Three Steps to Modern Media Asset Management with Active ArchiveAvere Systems
Ěý
This document discusses a three step approach to modern media asset management with an active archive:
1) Using object storage like Cleversafe for scalable, low-cost archive storage that is geo-dispersed for resilience.
2) Making the archive easily accessible using tools like Avere to provide NAS simplicity and performance.
3) Managing large quantities of media assets using asset management tools like CatDV for ingest, metadata, search, collaboration and workflows.Houd controle over uw data
Houd controle over uw dataICT-Partners
Ěý
The document discusses the evolving landscape of data management, emphasizing the shift towards treating data as a strategic asset amidst increasing data volumes, cloud integration, and legacy system modernization. It highlights the need for effective management, governance, and universal access to data, along with the benefits of a unified repository, analytics, and disaster recovery strategies. The importance of flexibility, security, and compliance within a cloud-agnostic and vendor-independent framework is also underscored.Chip ICT | Hgst storage brochure
Chip ICT | Hgst storage brochureMarco van der Hart
Ěý
The document discusses several data storage solutions from HGST, including:
- The Ultrastar Data102 and Data60 hybrid storage platforms, which can store up to 1.2PB and 720TB respectively in a 4U form factor, and feature vibration isolation and efficient cooling technologies.
- The ActiveScale X100 and P100 object storage systems, which provide scalable, durable storage for applications such as analytics, media and entertainment, and backup.
- The IntelliFlash all-flash and hybrid storage arrays, which combine flash performance with data management capabilities to accelerate a wide variety of workloads while maintaining high density and compelling economics.E newsletter promise_&_challenges_of_cloud storage-2
E newsletter promise_&_challenges_of_cloud storage-2Anil Vasudeva
Ěý
The document discusses the promise and challenges of cloud storage. The promise includes reduced costs, scalability, and accessibility. However, challenges include performance issues due to latency, security concerns about data in third-party control, and interoperability with existing systems and protocols. The document also outlines types of cloud storage solutions and how to optimize cloud storage using tiered data sets placed in different storage mediums and locations according to characteristics and needs.Fujitsu - 27mai2011
Fujitsu - 27mai2011Agora Group
Ěý
This document discusses increasing datacenter efficiency with Fujitsu and NetApp technologies. It provides an overview of Fujitsu's PRIMERGY servers and storage solutions, such as the PRIMERGY BX400 data center in a box. It also summarizes NetApp's storage portfolio including FAS storage systems, V-Series controllers, and data efficiency technologies like deduplication, thin provisioning, snapshots, and thin replication. Case studies on BT show how NetApp helped consolidate servers, improve utilization, reduce power consumption, and improve backup times.Innovating for Growth
Innovating for Growth NetApp
Ěý
The document discusses NetApp's strategy for managing and storing data at scale. It highlights NetApp's Data ONTAP operating system and unified storage architecture as the foundation. It also outlines NetApp's 10-year vision, which includes managing large-scale infrastructure simply through automation and orchestration. NetApp is well-positioned for data center transformation and the growth of big data through its portfolio that combines Data ONTAP, E-Series, StorageGRID, and partnerships with Hadoop and analytics vendors.Technology Overview
Technology OverviewLiran Zelkha
Ěý
The document discusses several technology topics including:
1. SOA and its benefits such as facilitating interoperability and promoting technology reuse.
2. Cloud computing and common questions around it such as what cloud computing is, how many clouds there will be, and what's new in cloud computing.
3. An example scenario of a company called FredsList gradually adopting more cloud capabilities for their listings website, from basic storage to search, photos, analytics and performance optimization.Successfully Implementing a private storage cloud to help reduce total cost o...
Successfully Implementing a private storage cloud to help reduce total cost o...IBM India Smarter Computing
Ěý
This document discusses implementing a private storage cloud to help reduce data storage costs. A private storage cloud allows sharing of storage resources across an organization on a dedicated private network. It provides flexibility, scalability and efficient management of rapidly growing data storage needs. The document outlines how a private storage cloud can help in situations like running out of storage space, upgrading old storage, and facilitating disaster recovery in the event of site failures. It also provides an overview of private storage cloud architecture.Käyttäjien omat laitteet ja ohjelmistot työpaikoilla - Esa Aho 31.5.2012
Käyttäjien omat laitteet ja ohjelmistot työpaikoilla - Esa Aho 31.5.2012Etelä-Pohjanmaan kauppakamari - South Ostrobothnia Chamber of Commerce
Ěý
The document discusses the rise of shadow IT and consumerization of IT. It notes that over the last 3 years, user-driven IT has added more to productivity than corporate IT. Reasons for the rise of shadow IT include rigid corporate IT policies, lack of choice and fun usability. The document outlines how IT is evolving to become more flexible and driven by end user needs, including accepting bring your own device (BYOD) and moving to cloud-based solutions. It argues that standardization will mean creating a more dynamic IT environment that removes technology constraints and allows self-service options.Transforming your Information Infrastructure with IBM’s Storage Cloud Solution
Transforming your Information Infrastructure with IBM’s Storage Cloud SolutionIBM India Smarter Computing
Ěý
Transforming your Information Infrastructure with IBM's Storage Cloud Solutio...
Transforming your Information Infrastructure with IBM's Storage Cloud Solutio...IBM India Smarter Computing
Ěý
Successfully Implementing a private storage cloud to help reduce total cost o...
Successfully Implementing a private storage cloud to help reduce total cost o...IBM India Smarter Computing
Ěý
Käyttäjien omat laitteet ja ohjelmistot työpaikoilla - Esa Aho 31.5.2012
Käyttäjien omat laitteet ja ohjelmistot työpaikoilla - Esa Aho 31.5.2012Etelä-Pohjanmaan kauppakamari - South Ostrobothnia Chamber of Commerce
Ěý
Ad
More from Foundation IT Leader Club Poland (6)
It breakfast fin_28.08.2014_knf
It breakfast fin_28.08.2014_knfFoundation IT Leader Club Poland
Ěý
Temat prelekcji: "Ocena sytuacji i kierunki zmian w IT oraz obszarze bezpieczeństwa i jakości danych bankowych okiem KNF i rynku"IT Breakafst for FIN 28 sierpnia 2014, Warszawa, Pałac Sobańskich
IT Breakafst for FIN 28 sierpnia 2014, Warszawa, Pałac SobańskichFoundation IT Leader Club Poland
Ěý
Temat prelekcji: "Ocena sytuacji i kierunki zmian w IT oraz obszarze bezpieczeństwa i jakości danych bankowych okiem KNF i rynku"IT Breakafst for FIN 28 sierpnia 2014, Warszawa, Pałac Sobańskich
IT Breakafst for FIN 28 sierpnia 2014, Warszawa, Pałac SobańskichFoundation IT Leader Club Poland
Ěý
Temat prelekcji: Ocena sytuacji i kierunki zmian w IT oraz obszarze bezpieczeństwa i jakości danych bankowych okiem KNF i rynkuPrezentacja - IT BREAKFAST - 30.05.2014 - Warszawa
Prezentacja - IT BREAKFAST - 30.05.2014 - WarszawaFoundation IT Leader Club Poland
Ěý
We współczesnym biznesie praktycznie każda istotna zmiana w firmie musi przejść przez dział IT, który pod nawałem żądań często się „zatyka”, stając się wąskim gardłem -- ku niezadowoleniu biznesu. Jednocześnie nie ma jednak środków na zwiększenie zasobów IT. Powstaje więc pytanie: czy można istotnie zwiększyć efektywność wykorzystania już istniejących zasobów, bez dokonywania istotnych inwestycji i rewolucyjnych zmian?
Tak, jeśli zdamy sobie sprawę, do jakiego stopnia jesteśmy ofiarą złej wielozadaniowości -- i jeśli zastosujemy proste, choć czasem nieintuicyjne reguły postępowania. Opóźnienia w wykonywaniu projektów najczęściej nie wynikają bowiem z braku zasobów, ale z ich marnowania wskutek wszechobecnej złej wielozadaniowości. Zła wielozadaniowość to sytuacja, w której żonglujemy zbyt wieloma zadaniami jednocześnie, co powoduje znaczne wydłużenie czasu realizacji wszystkich projektów, nadmierne zmęczenie i dużą liczbę błędów. Praktycznym sposobem rozładowania kolejki projektów czekających na realizację jest ograniczenie ilości pracy w toku wykorzystując kanban.
Prezentacja - IT BREAKFAST - 30.05.2014 - Warszawa
Prezentacja - IT BREAKFAST - 30.05.2014 - Warszawa Foundation IT Leader Club Poland
Ěý
Cloud computing i Internet Rzeczy wkraczają mocniej do rzeczywistości przemysłowej. Pozwalają twórczo w zakresie wiedzy technicznej i atrakcyjnie społecznie rozwinąć ideę zwaną Product Lifecycle Management. Nowe podejście uzyskało w Niemczech nazwę Industry 4.0 i jest już programem rządowym, a ma też odzew rządu amerykańskiego. Warto tej idei kibicować, bowiem nawet jeśli jesteśmy jej odlegli biznesowo, to skorzystamy jako członkowie społeczeństwa. Prezentacja - IT BREAKFAST - 30.05.2014 - Warszawa
Prezentacja - IT BREAKFAST - 30.05.2014 - WarszawaFoundation IT Leader Club Poland
Ěý
The document outlines GTS's operations in five Central and Eastern European countries, serving 38,000 business customers with a range of services including voice, data transmission, and data center offerings. It highlights the importance of unified communication (UC) for improving collaboration, customer interactions, and employee satisfaction, along with a focus on productivity gains. Additionally, the document mentions the involvement of CIOs and IT managers in developing the UC vision and strategy.IT Breakafst for FIN 28 sierpnia 2014, Warszawa, Pałac Sobańskich
IT Breakafst for FIN 28 sierpnia 2014, Warszawa, Pałac SobańskichFoundation IT Leader Club Poland
Ěý
IT Breakafst for FIN 28 sierpnia 2014, Warszawa, Pałac Sobańskich
IT Breakafst for FIN 28 sierpnia 2014, Warszawa, Pałac SobańskichFoundation IT Leader Club Poland
Ěý
Ad
IT Breakafst for FIN 28 sierpnia 2014, Warszawa, Pałac Sobańskich
- 1. Przykład nowoczesnej architektury z centralnym magazynem danych dla wielu aplikacji. Współdzielenie i synchronizacja plików. Radosław Machnica 28.08.2014
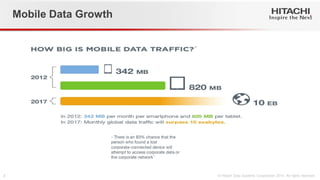
- 2. Mobile Access On-the-Go Public devices Inside our offices From our own devices
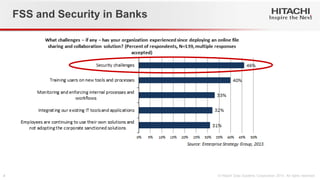
- 4. FSS and Security in Banks
- 5. Rogue IT in the consumer cloud What’s the risk ? Serious corporate data security and governance issues Risk of exposing intellectual property Violation of regulatory compliance for confidentiality and retention No control or audit of content flowing in and out of corporate network
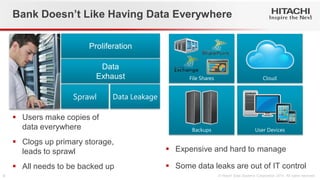
- 6. Users make copies of data everywhere Clogs up primary storage, leads to sprawl All needs to be backed up Bank Doesn’t Like Having Data Everywhere Expensive and hard to manage Some data leaks are out of IT control
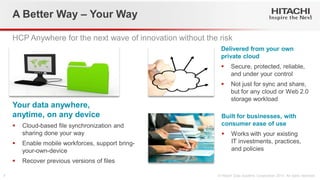
- 7. A Better Way – Your Way Delivered from your own private cloud Secure, protected, reliable, and under your control Not just for sync and share, but for any cloud or Web 2.0 storage workload HCP Anywhere for the next wave of innovation without the risk Built for businesses, with consumer ease of use Works with your existing IT investments, practices, and policies Your data anywhere, anytime, on any device Cloud-based file synchronization and sharing done your way Enable mobile workforces, support bring- your-own-device Recover previous versions of files
- 8. Freedom To Be an Innovation Center User work files available anywhere Shared links, not files Data is automatically protected Efficient, automatically managed storage Data is secure and under IT control
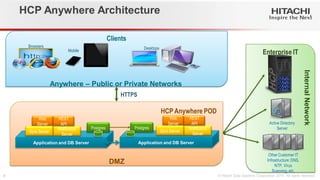
- 9. Clients Enterprise IT HCP Anywhere Architecture HCP Anywhere POD Desktops Mobile Browsers Active Directory Server HTTPS Other Customer IT Infrastructure: DNS, NTP, Virus Scanning, etc. Application and DB Server Notification Server Postgres Web Server REST API Sync Server Application and DB Server Postgres DMZ Internal Network Anywhere – Public or Private Networks Notification Server Web Server REST API Sync Server
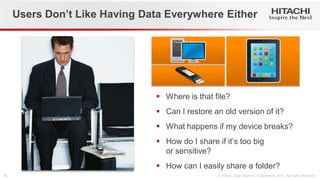
- 10. Users Don’t Like Having Data Everywhere Either Where is that file? Can I restore an old version of it? What happens if my device breaks? How do I share if it’s too big or sensitive? How can I easily share a folder?
- 11. More Freedom to Innovate Work files synchronized on all devices Data is automatically protected Old versions can be recovered Files are easily recovered to any device Files and folders are easily and safely shared with others
- 12. LET INSIGHT HAPPEN ANYWHERE Secure, Simple, Smart Hitachi Content Platform Anywhere
- 13. Quiz What’s Top 5 Information Sources Used By IT Pros ?
- 14. Thank You
