ccna course 1
Download as ppt, pdf0 likes359 views
Cloud computing provides on-demand access to shared computing resources like servers, storage, databases, networking, software and analytics over the internet. It offers benefits like fast application deployment, reduced maintenance costs, better utilization of resources and scalability. Cloud services include infrastructure, platforms and software delivered on a pay-per-use model. Network access and security are important considerations for cloud computing given its reliance on internet connectivity and shared infrastructure.
1 of 7
Download to read offline





Ad
Recommended
Cloud-Trust - a Security Assessment Model for Infrastructure as a Service (Ia...
Cloud-Trust - a Security Assessment Model for Infrastructure as a Service (Ia...I3E Technologies
╠²
Cloud-Trust is a security assessment model for Infrastructure as a Service (IaaS) clouds that estimates high-level security metrics to quantify confidentiality and integrity. It assesses the security of four multi-tenant IaaS cloud architectures with different security controls. The probability of penetrating a cloud system (compromising high-value data) is high with minimal security controls, but drops substantially with a defense-in-depth architecture protecting VM images, strengthening access controls for administrators, and employing network security controls.Top Cited Papers - International Journal of Network Security & Its Applicatio...
Top Cited Papers - International Journal of Network Security & Its Applicatio...IJNSA Journal
╠²
The document discusses various aspects of security in computer networks, highlighting the importance of intrusion detection systems and the challenges posed by security in cloud computing and big data. It reviews several techniques for improving intrusion detection, including evolutionary algorithms and data mining methods, and addresses security risks associated with deploying cloud technologies. The text also emphasizes the need for proper planning and analysis of security threats before integrating cloud solutions in enterprises.Presentation On Effectively And Securely Using The Cloud Computing Paradigm V26
Presentation On Effectively And Securely Using The Cloud Computing Paradigm V26TT L
╠²
This document discusses effective and secure use of cloud computing. It begins with defining cloud computing and its essential characteristics, service models, and deployment models. It then discusses some general security advantages and challenges of cloud computing. Specific security considerations related to cloud provisioning services, data storage, processing infrastructure, and other components are also outlined. The document provides an overview of secure migration paths for adopting cloud computing and discusses NIST's role in developing standards to help ensure security.Effectively and Securely Using the Cloud Computing Paradigm
Effectively and Securely Using the Cloud Computing Paradigmfanc1985
╠²
This document provides an overview of cloud computing concepts including definitions, service models, deployment models, security considerations, standards, and economic factors. It discusses effective and secure use of cloud computing including understanding the cloud paradigm, cloud security issues and advantages, secure migration paths, and relevant publications. Case studies and foundational elements of cloud computing such as virtualization and web services are also covered.Asynchronous Power Management Using Grid Deployment Method for Wireless Senso...
Asynchronous Power Management Using Grid Deployment Method for Wireless Senso...Association of Scientists, Developers and Faculties
╠²
The document presents proceedings from the International Conference on Advances & Challenges in Interdisciplinary Engineering and Management 2017, featuring two papers addressing critical issues in wireless sensor networks and cloud computing security. The first paper discusses an asynchronous power management method for optimizing wireless sensor networks through a grid deployment strategy, while the second paper focuses on user and data security in cloud computing using attribute-based encryption and automatic password generation. The conference proceedings are published by ASDF International and include permissions for reproduction under certain conditions.Top Cited Paper - The International Journal of Network Security & Its Applica...
Top Cited Paper - The International Journal of Network Security & Its Applica...IJNSA Journal
╠²
The document discusses various aspects of intrusion detection systems (IDS) and security risks associated with cloud computing, proposing methods to improve detection rates and reduce false positives using algorithms like genetic algorithms, naive Bayesian classifiers, decision trees, and rough set theory. Additionally, it highlights the importance of analyzing log files for understanding user behavior and the security challenges in vehicular ad hoc networks (VANETs). Overall, the document emphasizes the ongoing need for advancements in IDS to address complex and evolving security threats.Data security in cloud environment
Data security in cloud environmentShivam Singh
╠²
The document discusses data security in cloud environments. It covers cloud computing models including infrastructure as a service, platform as a service and software as a service. It also discusses common attacks on clouds like denial of service and phishing attacks. The document outlines cloud security controls that are deterrent, preventive, detective and corrective. It discusses security models for data integrity, privacy and confidentiality in clouds.Why Everyone Needs a Cloud-First Security Program - SASEfaction Guaranteed!
Why Everyone Needs a Cloud-First Security Program - SASEfaction Guaranteed!Netskope
╠²
The document discusses the transformation of network security due to the increasing use of cloud services and the shift towards a cloud-first security approach. It highlights that 85% of enterprise web traffic is now cloud-based, leading to rising concerns around phishing and security misconfigurations. The recommended solution is the adoption of Secure Access Service Edge (SASE) architecture to better secure cloud and mobile environments.Cloud computing
Cloud computingShivam Singh
╠²
Cloud computing allows users to access applications and store data over the internet through cloud services instead of locally. It offers various models including public, private, hybrid and community clouds as well as infrastructure, platform and software services. The key benefits are efficiency, cost effectiveness and access to resources online or on demand without needing to install software locally. However, security, privacy and vendor lock-in pose risks to cloud computing that need to be addressed.Ea33762765
Ea33762765IJERA Editor
╠²
The document discusses the security threats posed by cloud computing, highlighting vulnerabilities that attract cyber criminals as services migrate to cloud architectures. It reviews existing malware detection systems, emphasizing the need for enhanced detection methodologies, particularly at the hypervisor level, to combat unique risks associated with virtualization. Ultimately, it argues for a coordinated approach to malware detection across cloud environments to effectively manage these emerging security challenges.Security in cloud computing kashyap kunal
Security in cloud computing kashyap kunalKashyap Kunal
╠²
This document discusses data security in cloud computing. It defines cloud computing and describes the types including SaaS, PaaS, and IaaS. It also covers deployment types such as private, public, and hybrid clouds. While cloud computing provides security advantages through data centralization and logging, it also poses security disadvantages regarding data location and regulatory compliance. Major security threats in the cloud include abuse of cloud services, insecure APIs, and data loss. Risk analysis approaches are needed to estimate security risks and ensure customer data protection in the cloud.Cloud Security for U.S. Military Agencies
Cloud Security for U.S. Military AgenciesNJVC, LLC
╠²
NJVC is an IT contractor that specializes in providing secure IT solutions, including designing, implementing, and maintaining secure cloud architectures for government agencies. NJVC has over a decade of experience hosting hundreds of mission systems and migrating systems between data center environments. Securing systems in the cloud presents unique challenges compared to traditional IT environments due to the shared nature of cloud resources. NJVC outlines a strategic framework for assessing, planning, transitioning, and sustaining secure cloud operations. This includes understanding security responsibilities, implementing necessary security services, properly transitioning systems to the cloud according to best practices, and establishing agreements and continuing authorization to maintain security.Cloud Encounters: Measuring the computing cloud
Cloud Encounters: Measuring the computing cloudPeter HJ van Eijk
╠²
The document summarizes measurements and analysis of various cloud computing platforms. It finds that cloud uptime is generally good and improving. Location and proximity matter - response times increase with distance from data centers. Over time, some cloud providers like Google have expanded their global coverage and reduced response times. Routing of requests can be location-dependent. Large cloud providers like Amazon and Google have demonstrated the ability to scale infrastructure globally on demand.PRISMACLOUD Cloud Security and Privacy by Design
PRISMACLOUD Cloud Security and Privacy by DesignPRISMACLOUD Project
╠²
The document presents an overview of the Horizon 2020 project Prismacloud, aimed at enhancing security and privacy in cloud computing from February 2015 to July 2018. It discusses the characteristics of cloud computing, the risks involved, and introduces cryptographic solutions to empower end users with better governance over their data. The project involves 16 partners and focuses on developing services such as secure cloud storage and user privacy protection through various cryptographic functions.CSA v4 Topology
CSA v4 TopologyJason Rusch - CISSP CGEIT CISM CISA GNSA
╠²
The document discusses 14 domains related to security guidance for critical areas of focus in cloud computing. The domains include legal issues, contracts, electronic discovery, governance, risk management, infrastructure security, incident response, management and business continuity, information governance, cloud concepts and architectures, virtualization and containers, application security, data security and encryption, identity and access management, security as a service, and related technologies. The document also notes that the CSA uses the NIST 800-145 model for defining cloud computing and endorses the more in-depth ISO/IEC 17788 reference model.Ariel Litvin - CCSK
Ariel Litvin - CCSKCSAIsrael
╠²
This document provides information about the Certificate of Cloud Security Knowledge (CCSK) certification. The CCSK is a 50 question, multiple choice exam that tests knowledge of cloud security concepts. It takes 60 minutes to complete and requires getting 80% of questions correct to pass. The exam costs $295 USD. It covers 13 domains of cloud security knowledge that are based on the Cloud Security Alliance guidance document and the ENISA cloud computing risk assessment report. The CCSK certification demonstrates an individual's knowledge of best practices for securing data, applications, and infrastructure in the cloud.Cloud Computing Security
Cloud Computing Securityneicher
╠²
This document discusses cloud computing security. It provides an overview of cloud computing and outlines some of the key benefits it provides including minimized costs, scalability, and efficiency. However, it also notes there are security concerns to consider like data breaches, hijacking, and insider threats. The document examines some common threats and vulnerabilities cloud systems face and recommends various countermeasures that can be implemented, such as encryption, identity management, and service level agreements. It concludes with a summary of the main topics covered regarding cloud computing security.Cloud computing
Cloud computingVivekananda college
╠²
Cloud computing is the use of computing resources that are delivered as a service over the Internet. It allows users to access data, software and computing power remotely. There are several types of cloud platforms including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). While cloud computing can improve security through centralization, users lose some control over sensitive data and security is complex with data distributed across multiple devices. Performance is monitored in cloud applications which are easier to maintain since they do not need to be installed locally on each user's computer.Demystifying Top 5 Cloud Migration Myths
Demystifying Top 5 Cloud Migration MythsVivek Mishra
╠²
The document discusses the shift from on-premise IT infrastructure to cloud environments, highlighting that cloud security is more holistic and adaptable despite common misconceptions about on-premise security being superior. It outlines the benefits of cloud migration, including improved data storage, flexibility, and collaboration, while acknowledging the challenges of migration such as downtime and potential vendor lock-in. The document emphasizes careful planning and understanding vendor capabilities as key to successful cloud adoption.Cloud with Cyber Security
Cloud with Cyber SecurityNiki Upadhyay
╠²
This document proposes a cyber security model for cloud computing environments. It discusses key cloud concepts like service and deployment models. It then covers cyber security threats in cloud computing, including those originating from the host, between the customer and datacenter, and from virtual machines. The document also presents a mean failure cost approach to measure security and quantify risks through stakeholder, dependency, and impact matrices. Finally, it argues the model can support cloud business decisions by pricing security upgrades and assessing enhancement cost effectiveness.Comprehensive Cloud Security Requires an Automated Approach
Comprehensive Cloud Security Requires an Automated ApproachCloudPassage
╠²
The document discusses the importance of cloud security and the need for an automated approach to address its challenges, including data protection and inconsistent control. It emphasizes that while cloud services offer significant benefits, they also complicate security responsibilities and necessitate a comprehensive security strategy. Recommendations include centralizing security policy management, automating security measures, and engaging with cloud service providers for clear security delineations.wap-IoT
wap-IoTS Sridhar
╠²
The document discusses how wireless application protocol (WAP) enables internet access and advanced services on mobile devices. It provides examples of using WAP for mobile stock trading, banking, and broking by accessing real-time information and placing orders from a mobile phone. It also describes the software architecture used for mobility applications and how WAP has been implemented in systems at Sharjah International Airport, including flight information, passenger information, visa/passport management, cargo tracking, and more.ccna course 2
ccna course 2S Sridhar
╠²
This document discusses cloud computing and network traffic. It covers several topics:
1. Web-scale problems that are data-intensive and require large data centers to solve. Examples include searching the web and scientific research data.
2. Large data centers have become necessary to handle web-scale problems by centralizing computing resources. Issues include redundancy, efficiency, and management.
3. Different cloud computing models have emerged like utility computing, platform as a service, and software as a service.
For all the network traffic generated, smart network access control, traffic management, and effective security techniques are needed, and there is ongoing research in these areas.engg pedagogy30 june 2015
engg pedagogy30 june 2015S Sridhar
╠²
The document discusses engineering pedagogy and human factors in design. It covers goals of engineering including proper functionality and reliability. It also discusses motivations for incorporating human factors in design such as life critical systems and industrial uses. Additionally, it examines accommodating human diversity considering physical, cognitive, and personality differences. The document provides examples of practices from organizations like ONGC and Sharjah International Airport.foss-30oct-2012
foss-30oct-2012S Sridhar
╠²
The document discusses FOSS (Free Open Source Software) for web designing. It defines FOSS and lists 10 criteria that the distribution terms of open-source software must comply with, such as allowing free redistribution, distribution of source code, allowing derivatives, and not restricting use based on field of endeavor or type of software. It then briefly mentions examining Tripod.com as an example of a FOSS for web site designing.leadership
leadershipS Sridhar
╠²
This document discusses different aspects of effective leadership. It states that to be a good leader, people must want to follow you. It also discusses visionary leadership, transformational leaders, and the differences between leadership and management. Effective leaders challenge processes, inspire action, empower teams, and celebrate achievements. Building trust among followers is also key to leadership, which requires consistency, clear communication, and understanding issues. The document advocates for creativity and constructive action over criticism in driving progress. It provides guidance on leading change and getting the most out of leadership development programs.Talk on Ramanujan
Talk on RamanujanS Sridhar
╠²
1) Srinivasa Ramanujan was a renowned Indian mathematician who made extraordinary contributions to mathematical analysis, number theory, infinite series, and continued fractions.
2) He was mostly self-taught and discovered his talent for mathematics at a young age without access to formal education.
3) In 1913, he wrote a letter to G.H. Hardy including theorems and results that Hardy found extraordinary and helped arrange for Ramanujan to travel to Cambridge University where they collaborated until Ramanujan's death in 1920.More Related Content
What's hot (13)
Cloud computing
Cloud computingShivam Singh
╠²
Cloud computing allows users to access applications and store data over the internet through cloud services instead of locally. It offers various models including public, private, hybrid and community clouds as well as infrastructure, platform and software services. The key benefits are efficiency, cost effectiveness and access to resources online or on demand without needing to install software locally. However, security, privacy and vendor lock-in pose risks to cloud computing that need to be addressed.Ea33762765
Ea33762765IJERA Editor
╠²
The document discusses the security threats posed by cloud computing, highlighting vulnerabilities that attract cyber criminals as services migrate to cloud architectures. It reviews existing malware detection systems, emphasizing the need for enhanced detection methodologies, particularly at the hypervisor level, to combat unique risks associated with virtualization. Ultimately, it argues for a coordinated approach to malware detection across cloud environments to effectively manage these emerging security challenges.Security in cloud computing kashyap kunal
Security in cloud computing kashyap kunalKashyap Kunal
╠²
This document discusses data security in cloud computing. It defines cloud computing and describes the types including SaaS, PaaS, and IaaS. It also covers deployment types such as private, public, and hybrid clouds. While cloud computing provides security advantages through data centralization and logging, it also poses security disadvantages regarding data location and regulatory compliance. Major security threats in the cloud include abuse of cloud services, insecure APIs, and data loss. Risk analysis approaches are needed to estimate security risks and ensure customer data protection in the cloud.Cloud Security for U.S. Military Agencies
Cloud Security for U.S. Military AgenciesNJVC, LLC
╠²
NJVC is an IT contractor that specializes in providing secure IT solutions, including designing, implementing, and maintaining secure cloud architectures for government agencies. NJVC has over a decade of experience hosting hundreds of mission systems and migrating systems between data center environments. Securing systems in the cloud presents unique challenges compared to traditional IT environments due to the shared nature of cloud resources. NJVC outlines a strategic framework for assessing, planning, transitioning, and sustaining secure cloud operations. This includes understanding security responsibilities, implementing necessary security services, properly transitioning systems to the cloud according to best practices, and establishing agreements and continuing authorization to maintain security.Cloud Encounters: Measuring the computing cloud
Cloud Encounters: Measuring the computing cloudPeter HJ van Eijk
╠²
The document summarizes measurements and analysis of various cloud computing platforms. It finds that cloud uptime is generally good and improving. Location and proximity matter - response times increase with distance from data centers. Over time, some cloud providers like Google have expanded their global coverage and reduced response times. Routing of requests can be location-dependent. Large cloud providers like Amazon and Google have demonstrated the ability to scale infrastructure globally on demand.PRISMACLOUD Cloud Security and Privacy by Design
PRISMACLOUD Cloud Security and Privacy by DesignPRISMACLOUD Project
╠²
The document presents an overview of the Horizon 2020 project Prismacloud, aimed at enhancing security and privacy in cloud computing from February 2015 to July 2018. It discusses the characteristics of cloud computing, the risks involved, and introduces cryptographic solutions to empower end users with better governance over their data. The project involves 16 partners and focuses on developing services such as secure cloud storage and user privacy protection through various cryptographic functions.CSA v4 Topology
CSA v4 TopologyJason Rusch - CISSP CGEIT CISM CISA GNSA
╠²
The document discusses 14 domains related to security guidance for critical areas of focus in cloud computing. The domains include legal issues, contracts, electronic discovery, governance, risk management, infrastructure security, incident response, management and business continuity, information governance, cloud concepts and architectures, virtualization and containers, application security, data security and encryption, identity and access management, security as a service, and related technologies. The document also notes that the CSA uses the NIST 800-145 model for defining cloud computing and endorses the more in-depth ISO/IEC 17788 reference model.Ariel Litvin - CCSK
Ariel Litvin - CCSKCSAIsrael
╠²
This document provides information about the Certificate of Cloud Security Knowledge (CCSK) certification. The CCSK is a 50 question, multiple choice exam that tests knowledge of cloud security concepts. It takes 60 minutes to complete and requires getting 80% of questions correct to pass. The exam costs $295 USD. It covers 13 domains of cloud security knowledge that are based on the Cloud Security Alliance guidance document and the ENISA cloud computing risk assessment report. The CCSK certification demonstrates an individual's knowledge of best practices for securing data, applications, and infrastructure in the cloud.Cloud Computing Security
Cloud Computing Securityneicher
╠²
This document discusses cloud computing security. It provides an overview of cloud computing and outlines some of the key benefits it provides including minimized costs, scalability, and efficiency. However, it also notes there are security concerns to consider like data breaches, hijacking, and insider threats. The document examines some common threats and vulnerabilities cloud systems face and recommends various countermeasures that can be implemented, such as encryption, identity management, and service level agreements. It concludes with a summary of the main topics covered regarding cloud computing security.Cloud computing
Cloud computingVivekananda college
╠²
Cloud computing is the use of computing resources that are delivered as a service over the Internet. It allows users to access data, software and computing power remotely. There are several types of cloud platforms including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). While cloud computing can improve security through centralization, users lose some control over sensitive data and security is complex with data distributed across multiple devices. Performance is monitored in cloud applications which are easier to maintain since they do not need to be installed locally on each user's computer.Demystifying Top 5 Cloud Migration Myths
Demystifying Top 5 Cloud Migration MythsVivek Mishra
╠²
The document discusses the shift from on-premise IT infrastructure to cloud environments, highlighting that cloud security is more holistic and adaptable despite common misconceptions about on-premise security being superior. It outlines the benefits of cloud migration, including improved data storage, flexibility, and collaboration, while acknowledging the challenges of migration such as downtime and potential vendor lock-in. The document emphasizes careful planning and understanding vendor capabilities as key to successful cloud adoption.Cloud with Cyber Security
Cloud with Cyber SecurityNiki Upadhyay
╠²
This document proposes a cyber security model for cloud computing environments. It discusses key cloud concepts like service and deployment models. It then covers cyber security threats in cloud computing, including those originating from the host, between the customer and datacenter, and from virtual machines. The document also presents a mean failure cost approach to measure security and quantify risks through stakeholder, dependency, and impact matrices. Finally, it argues the model can support cloud business decisions by pricing security upgrades and assessing enhancement cost effectiveness.Comprehensive Cloud Security Requires an Automated Approach
Comprehensive Cloud Security Requires an Automated ApproachCloudPassage
╠²
The document discusses the importance of cloud security and the need for an automated approach to address its challenges, including data protection and inconsistent control. It emphasizes that while cloud services offer significant benefits, they also complicate security responsibilities and necessitate a comprehensive security strategy. Recommendations include centralizing security policy management, automating security measures, and engaging with cloud service providers for clear security delineations.More from S Sridhar (6)
wap-IoT
wap-IoTS Sridhar
╠²
The document discusses how wireless application protocol (WAP) enables internet access and advanced services on mobile devices. It provides examples of using WAP for mobile stock trading, banking, and broking by accessing real-time information and placing orders from a mobile phone. It also describes the software architecture used for mobility applications and how WAP has been implemented in systems at Sharjah International Airport, including flight information, passenger information, visa/passport management, cargo tracking, and more.ccna course 2
ccna course 2S Sridhar
╠²
This document discusses cloud computing and network traffic. It covers several topics:
1. Web-scale problems that are data-intensive and require large data centers to solve. Examples include searching the web and scientific research data.
2. Large data centers have become necessary to handle web-scale problems by centralizing computing resources. Issues include redundancy, efficiency, and management.
3. Different cloud computing models have emerged like utility computing, platform as a service, and software as a service.
For all the network traffic generated, smart network access control, traffic management, and effective security techniques are needed, and there is ongoing research in these areas.engg pedagogy30 june 2015
engg pedagogy30 june 2015S Sridhar
╠²
The document discusses engineering pedagogy and human factors in design. It covers goals of engineering including proper functionality and reliability. It also discusses motivations for incorporating human factors in design such as life critical systems and industrial uses. Additionally, it examines accommodating human diversity considering physical, cognitive, and personality differences. The document provides examples of practices from organizations like ONGC and Sharjah International Airport.foss-30oct-2012
foss-30oct-2012S Sridhar
╠²
The document discusses FOSS (Free Open Source Software) for web designing. It defines FOSS and lists 10 criteria that the distribution terms of open-source software must comply with, such as allowing free redistribution, distribution of source code, allowing derivatives, and not restricting use based on field of endeavor or type of software. It then briefly mentions examining Tripod.com as an example of a FOSS for web site designing.leadership
leadershipS Sridhar
╠²
This document discusses different aspects of effective leadership. It states that to be a good leader, people must want to follow you. It also discusses visionary leadership, transformational leaders, and the differences between leadership and management. Effective leaders challenge processes, inspire action, empower teams, and celebrate achievements. Building trust among followers is also key to leadership, which requires consistency, clear communication, and understanding issues. The document advocates for creativity and constructive action over criticism in driving progress. It provides guidance on leading change and getting the most out of leadership development programs.Talk on Ramanujan
Talk on RamanujanS Sridhar
╠²
1) Srinivasa Ramanujan was a renowned Indian mathematician who made extraordinary contributions to mathematical analysis, number theory, infinite series, and continued fractions.
2) He was mostly self-taught and discovered his talent for mathematics at a young age without access to formal education.
3) In 1913, he wrote a letter to G.H. Hardy including theorems and results that Hardy found extraordinary and helped arrange for Ramanujan to travel to Cambridge University where they collaborated until Ramanujan's death in 1920.Ad
ccna course 1
- 1. Cloud computing , Network Access, Security By Dr.S.Sridhar, Ph.D.(JNUD), RACI(Paris, NICE), RMR(USA), RZFM(Germany) Dean ÔÇô Cognitive & Central Computing Facility R.V. COLLEGE OF ENGINEERING BANGALORE
- 2. Why Cloud- As basic Business Scenarios ´ü« Fast Application Deployment ´ü« Hassle Free Maintenance ´ü« Better Resources Utilization ´ü« Platform Independent, Security, Scalability
- 3. What is Cloud? ´ü« Infrastructure provided by the service provider to build internet application. ´ü« The service provided by cloud are categorize > Software As a Service > Infrastructure As a Service > Platform As a Service > Database As a Service > Software plus Service
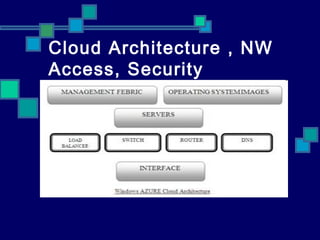
- 4. Cloud Architecture , NW Access, Security
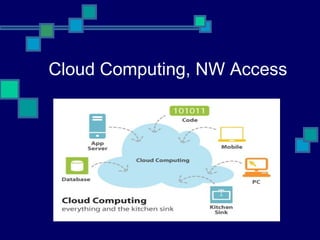
- 5. Cloud Computing, NW Access
- 6. Cloud Computing Cycle, NW access, Security
- 7. Cloud Computing, NW Access Growth Rate