1 of 16
Downloaded 14 times



![// SIMULATION OF LINKER
#include<iostream.h>
#include<conio.h>
#include<stdio.h>
#include<string.h>
#include<math.h>
#include<stdlib.h>
struct x
{
char f[10];
}s[20],t[20],r[10];](https://image.slidesharecdn.com/linker-141012125008-conversion-gate02/85/Linker-5-320.jpg)
![void main()
{
clrscr();
x o[2]={"int","float"};
x z[20],v[20];
char c,*a,*b;
int i=0, j=0, k=0, l=0, flag=0, flag1=0, h=0, y=0, u=0;
int m;
FILE *p1,*p2;
p1=fopen("p1.txt","r");
p2=fopen("p2.txt","r");](https://image.slidesharecdn.com/linker-141012125008-conversion-gate02/85/Linker-6-320.jpg)
![do
{
c=fgetc(p1);
if(c!=' '&&c!='n'&&c!=',')
{
a[i]=c;
i++;
}
else
{
a[i]='0';
strcpy(s[j].f,a);
j++;
i=0;
k++; }
}while(c!=EOF);](https://image.slidesharecdn.com/linker-141012125008-conversion-gate02/85/Linker-7-320.jpg)
![i=0;
j=0;
do
{
c=fgetc(p2);
if(c!=' '&& c!='n')
{
if((abs(c)>=65&&abs(c)<=90)||(abs(c)>=97&&abs(c)
<=122))
{
a[i]=c; //insert characters e.g.int x
i++;
flag=1;
}](https://image.slidesharecdn.com/linker-141012125008-conversion-gate02/85/Linker-8-320.jpg)
![else
{
b[h]=c; //insert digits e.g. 200
h++;
flag1=1;
}
}
else
{
if(flag==1) //For characters
{
a[i]='0';
strcpy(t[j].f,a);
j++;
i=0; l++; //counter](https://image.slidesharecdn.com/linker-141012125008-conversion-gate02/85/Linker-9-320.jpg)
![}
if(flag1==1) // For Digits
{
b[h]='0';
strcpy(r[y].f,b);
y++;
h=0;
u++; //counter
}
}
}while(c!=EOF);
h=0;](https://image.slidesharecdn.com/linker-141012125008-conversion-gate02/85/Linker-10-320.jpg)
![for(i=0;i<l;i++)
{
flag=0;
for(j=0;j<2;j++) //for characters
{
if(strcmp(t[i].f,o[j].f)==0||strcmp(t[i].f,"")==0)
{
flag=1;
}
}
if(flag==0)
{
strcpy(v[h].f,t[i].f );
h++;
} }](https://image.slidesharecdn.com/linker-141012125008-conversion-gate02/85/Linker-11-320.jpg)
![l=0;
for(i=0;i<u;i++) //for digits
{
if(strcmp(r[i].f,"")!=0)
{
strcpy(z[l].f,r[i].f );
l++;
}
}
cout<<"n***After Linking****n";
flag=0;
l=0;](https://image.slidesharecdn.com/linker-141012125008-conversion-gate02/85/Linker-12-320.jpg)
![for(i=0;i<k;i++)
{
flag=0;
for(j=0;j<h;j++)
{
if(strcmp(s[i].f,v[j].f)==0)
flag=1;
}
if(flag==1)
{
m=atoi(z[l].f)+400;
cout<<s[i].f<<" "<<"p1"<<" "<<m<<"n";
l++;
}](https://image.slidesharecdn.com/linker-141012125008-conversion-gate02/85/Linker-13-320.jpg)


Ad
Recommended
Bcsl 033 data and file structures lab s1-2
Bcsl 033 data and file structures lab s1-2Dr. Loganathan R
╠²
BCSL-033 Data and File Structures Lab ProgramsBcsl 033 data and file structures lab s4-3
Bcsl 033 data and file structures lab s4-3Dr. Loganathan R
╠²
BCSL-033 Data and File Structures Lab Programcontoh Program C++ tentang fungsi for
contoh Program C++ tentang fungsi forM Fahmi Ansori
╠²
berisi contoh-contoh fungsi for dalam bahasa C++Tablas hash (Rub├®n Ndong Obiang)
Tablas hash (Rub├®n Ndong Obiang)edi.euitio
╠²
Discusion sobre las tablas hah para ver si empleamos Object y la funci├│n de dispersi├│nInfix prefix postfix expression -conversion
Infix prefix postfix expression -conversionSyed Mustafa
╠²
Data Structure-Infix to Prefix and Postfix conversionNested micro
Nested microSatyamevjayte Haxor
╠²
This document discusses macro nesting in C programming. It defines several macros, including nested macros where a macro name is used within the definition of another macro. It then shows an example program that defines macros, reads a text file containing additional macro definitions, builds a linked list of the macros, replaces nested macro names within values, and prints the final macro table.Lessons from life_2
Lessons from life_2Mir Majid
╠²
The document shares lessons learned from life experiences. It discusses lessons such as heroes doing what needs to be done regardless of consequences, backgrounds influencing who people are, personal growth taking a long time, the world not stopping for grief, different types of love, maturity coming from experiences rather than years lived, pushing past what is thought possible, different perspectives of the same thing, being responsible for actions, leaving loved ones with kind words, having the right to anger but not cruelty, determining the line between kindness and beliefs, and finding strength to help friends in need. The document encourages remembering life's wisdom and keeping one's face towards the sunshine.ash
ashSeongJae Park
╠²
This document introduces "ash", a shell that allows controlling multiple devices with a single interface. Ash uses a text-based command language to send commands over a network to remotely control devices installed with the ash application. The architecture includes an evaluator that parses commands, a user interface, and device controllers. Commands can register functions and callbacks. The code is structured as lists, and ash supports interfaces from Android, Ubuntu, OSX, and Windows.Let the contribution begin (EST futures)
Let the contribution begin (EST futures)SeongJae Park
╠²
The document discusses contributing to open source software as a newcomer. It recommends getting the source code, making small, targeted changes like fixing coding style issues, and submitting patches for review. The Linux kernel is presented as a popular project to start contributing to. Topic branches in version control are introduced as a way to develop changes separately before submitting them for merging.More Related Content
What's hot (18)
Tablas hash (Rub├®n Ndong Obiang)
Tablas hash (Rub├®n Ndong Obiang)edi.euitio
╠²
Discusion sobre las tablas hah para ver si empleamos Object y la funci├│n de dispersi├│nInfix prefix postfix expression -conversion
Infix prefix postfix expression -conversionSyed Mustafa
╠²
Data Structure-Infix to Prefix and Postfix conversionViewers also liked (20)
Nested micro
Nested microSatyamevjayte Haxor
╠²
This document discusses macro nesting in C programming. It defines several macros, including nested macros where a macro name is used within the definition of another macro. It then shows an example program that defines macros, reads a text file containing additional macro definitions, builds a linked list of the macros, replaces nested macro names within values, and prints the final macro table.Lessons from life_2
Lessons from life_2Mir Majid
╠²
The document shares lessons learned from life experiences. It discusses lessons such as heroes doing what needs to be done regardless of consequences, backgrounds influencing who people are, personal growth taking a long time, the world not stopping for grief, different types of love, maturity coming from experiences rather than years lived, pushing past what is thought possible, different perspectives of the same thing, being responsible for actions, leaving loved ones with kind words, having the right to anger but not cruelty, determining the line between kindness and beliefs, and finding strength to help friends in need. The document encourages remembering life's wisdom and keeping one's face towards the sunshine.ash
ashSeongJae Park
╠²
This document introduces "ash", a shell that allows controlling multiple devices with a single interface. Ash uses a text-based command language to send commands over a network to remotely control devices installed with the ash application. The architecture includes an evaluator that parses commands, a user interface, and device controllers. Commands can register functions and callbacks. The code is structured as lists, and ash supports interfaces from Android, Ubuntu, OSX, and Windows.Let the contribution begin (EST futures)
Let the contribution begin (EST futures)SeongJae Park
╠²
The document discusses contributing to open source software as a newcomer. It recommends getting the source code, making small, targeted changes like fixing coding style issues, and submitting patches for review. The Linux kernel is presented as a popular project to start contributing to. Topic branches in version control are introduced as a way to develop changes separately before submitting them for merging.AOSPņŚÉ ņ╗©ĒŖĖļ”¼ļĘ░ņģś ĒĢśĻĖ░ dev festx korea 2012 presentation
AOSPņŚÉ ņ╗©ĒŖĖļ”¼ļĘ░ņģś ĒĢśĻĖ░ dev festx korea 2012 presentationSeongJae Park
╠²
dev festx korea 2012 Ē¢ēņé¼ ļĢī ļ░£Ēæ£Ē¢łļŹś, AOSPņŚÉ ņ╗©ĒŖĖļ”¼ļĘ░ņģś ĒĢśļŖö ļ░®ļ▓ĢņØä ļŗżļŻ¼ ļ░£Ēæ£ņ×ÉļŻīņ×ģļŗłļŗż.Porting golang development environment developed with golang
Porting golang development environment developed with golangSeongJae Park
╠²
Seongjae Park developed an Android application called ADE, which serves as a Go language development environment, allowing users to code and run Go programs directly on their Android devices. The project is open source and was presented at the GDG KR meetup in February 2016. Park emphasizes that developing Android applications using Go was a positive experience.Assembler
AssemblerVaibhav Bajaj
╠²
The document provides an overview of assembler languages and machine code. It discusses 3 levels of language - high level languages, assembler languages, and machine code. Assembler languages translate symbolic commands and addresses into machine code instructions. Machine code instructions are binary words that directly trigger elementary CPU operations. The document also describes assembler language structure, common instruction types, registers like the flag and general purpose registers, and jump operations.Unit 3 assembler and processor
Unit 3 assembler and processorAbha Damani
╠²
Assembly language is a low-level programming language that is one step away from machine language, with each statement translating to a single machine instruction, requiring programmers to understand the underlying computer architecture, and one-pass assemblers generate object code by resolving forward references on later passes or generating modification records for the loader.Use case diagrams
Use case diagramsMir Majid
╠²
A use case diagram describes interactions between users and a system. It displays relationships between actors and use cases. Actors represent users or other systems interacting with the system being modeled. Use cases represent actions a user performs to complete a task. Use case diagrams are helpful early in projects to expose requirements and plan projects, and more use cases may be identified as projects continue.sCode optimization
sCode optimizationSatyamevjayte Haxor
╠²
The document discusses code optimization techniques including constant folding, copy propagation, and common subexpression elimination. It provides examples of code before and after applying these optimizations. Constant folding replaces expressions with known constant values. Copy propagation replaces variable uses with the variable's assignment. Common subexpression elimination computes shared subexpressions only once. Together these optimizations can improve code efficiency.Let the contribution begin
Let the contribution beginSeongJae Park
╠²
This document is a presentation aimed at newbie hackers discussing contributions to free/open source software (FOSS). It outlines the types of software, the contribution process, best practices for coding, and specifics on contributing to both the Linux kernel and the Android Open Source Project (AOSP). Key steps include getting the source code, setting goals, making patches, and getting reviews, emphasizing a supportive environment for newcomers in the open-source community.Patterns
PatternsSatyamevjayte Haxor
╠²
This document discusses different types of patterns used in object-oriented software development, including anti-patterns, requirements patterns, analysis patterns, architecture patterns, and design patterns. It defines patterns as abstractions that describe solutions to recurring problems in software development. Each type of pattern addresses a different phase of development, like analysis patterns supporting the creation of conceptual models or architecture patterns describing principles for software structure. The document also defines some key terminology related to patterns, such as pattern languages and pattern instantiation.Keyword Presentation
Keyword PresentationSatyamevjayte Haxor
╠²
The document discusses keywords, identifiers, constants, and operators in the C programming language, providing examples of each and noting that keywords have fixed meanings while identifiers are user-defined names; it then presents code to count the number of times various keywords are used in an input C file and output the results.Deep dark side of git - prologue
Deep dark side of git - prologueSeongJae Park
╠²
This document discusses Git and provides an introduction to its basic concepts and functionality. It begins by introducing Git as a distributed version control system created by Linus Torvalds to manage Linux code. It then notes that many projects use Git because it is powerful. Finally, it summarizes that at its core, Git is a content-addressable file system based around blobs, trees, commits and references.gcma: guaranteed contiguous memory allocator
gcma: guaranteed contiguous memory allocatorSeongJae Park
╠²
This document presents GCMA, a Guaranteed Contiguous Memory Allocator that improves upon the current Contiguous Memory Allocator (CMA) solution in Linux. CMA can have unpredictable latency and even fail when allocating contiguous memory, especially under memory pressure or with background workloads. GCMA guarantees fast latency for contiguous memory allocation, success of allocation, and reasonable memory utilization by using discardable memory as its secondary client instead of movable pages. Experimental results on a Raspberry Pi 2 show that GCMA has significantly faster allocation latency than CMA, keeps camera latency fast even with background workloads, and can improve overall system performance compared to CMA.(Live) build and run golang web server on android.avi
(Live) build and run golang web server on android.aviSeongJae Park
╠²
The document details a live coding session where a Golang web server is developed for Android. It discusses the Golang programming language's support for Android since version 1.4, outlining the complex build process involved in creating .so or .apk files as well as binary executables. Additionally, it covers issues encountered when running Golang on Android and provides links to source code and resources related to the project.DO YOU WANT TO USE A VCS
DO YOU WANT TO USE A VCSSeongJae Park
╠²
The document discusses version control systems (VCS), particularly focusing on Git, emphasizing its ability to manage software changes and maintain file histories. It covers Git commands such as initialization, adding files, committing changes, managing branches, and collaborating through remote repositories. Additionally, it mentions best practices for committing and reverting changes in Git.Git inter-snapshot public
Git inter-snapshot publicSeongJae Park
╠²
This document summarizes key concepts of Git including snapshots, histories as sequences of snapshots, parallel universes/histories, and basic Git commands like init, add, commit, branch, checkout, merge, rebase, remote repositories, and free hosting services. The document uses diagrams and examples to explain how Git conceptually implements versions as snapshots and allows managing parallel software histories through branches.Class Outlier Mining
Class Outlier MiningMotaz Saad
╠²
This document summarizes a research paper on class outlier mining, which aims to identify rare or unusual cases within individual classes of labeled data rather than across an entire dataset. It presents an approach to class outlier mining based on calculating distances between data points to find exceptions within each class. The abstract also outlines that the paper will provide an overview of the concept of class outliers and the distance-based approach presented in the full paper.Experimental android hacking using reflection
Experimental android hacking using reflectionSeongJae Park
╠²
This document discusses using reflection in Android to access hidden and restricted features. It describes how Android separates interfaces for third-party and built-in apps. It then explains how reflection can be used to change the interface and allow third-party apps to access features usually only available to built-in apps, with examples of how to end a call via reflection. However, it notes reflection has limitations like performance overhead and may not work on all devices.Ad
More from Satyamevjayte Haxor (14)
Processes and threads
Processes and threadsSatyamevjayte Haxor
╠²
Processes are heavyweight flows of execution that run concurrently in separate address spaces, while threads are lightweight flows that run concurrently within the same process address space. Active classes represent concurrent flows of control and can be stereotyped as <<process>> or <<thread>>. There are four types of communication between active and passive objects: active to active, active to passive, passive to active, and passive to passive. Synchronization coordinates concurrent flows using sequential, guarded, or concurrent approaches.Uml class Diagram
Uml class DiagramSatyamevjayte Haxor
╠²
A class diagram describes the structure of a system by showing classes, attributes, operations, and relationships. A class represents a set of objects with common properties. Attributes and operations are included within classes. Relationships between classes such as associations, generalizations, and dependencies are also shown graphically. The class diagram provides an overview of the system design and structure.Uml Common Mechanism
Uml Common MechanismSatyamevjayte Haxor
╠²
The document discusses four common mechanisms in the Unified Modeling Language (UML): (i) specifications which provide textual definitions for graphical notations, (ii) adornments like notes that attach constraints to elements, (iii) common divisions between classes and objects, and (iv) extensibility mechanisms that allow customizing UML through stereotypes, tagged values, and constraints.Types and roles
Types and rolesSatyamevjayte Haxor
╠²
The document discusses types and roles in UML. Types are conceptual classes used during analysis to identify possible object types in a system. They do not have methods or instances. Roles represent the behaviors of entities in particular contexts. An object can play different roles depending on the context, presenting different properties based on its role. Types and roles are modeling concepts in UML used to describe the abstraction of classes and behaviors before implementation.States machine
States machineSatyamevjayte Haxor
╠²
State machines model the different states an object can be in and the transitions between those states. A state represents a condition or situation during an object's lifetime. Transitions between states are triggered by events and may include actions. States can have substates that run either sequentially or concurrently. Sequential substates represent stages in a process, while concurrent substates run in parallel. Advanced state machine features like entry/exit actions, internal transitions, and history states help simplify complex models.What is symbol table?
What is symbol table?Satyamevjayte Haxor
╠²
The document summarizes a seminar presentation on symbol table generation. It defines what a symbol table is, explaining that it collects information about identifiers in a source program like their storage allocation, type, and scope. This information includes the type of arguments for procedures, how arguments are passed, and the return type. A symbol table is necessary because declarations appear once but uses may be in many places, and it is used by compiler phases for type checking, verifying definitions are used correctly, and generating code.Lexical
LexicalSatyamevjayte Haxor
╠²
This document summarizes a seminar presentation on lexical programs and parsers. It provides an overview of Lex, a program generator for lexical analysis of character streams, and how it works with Yacc, a parser generator. It then describes the components and structure of Lex source code including definitions, rules, and user subroutines. Finally, it includes an example Lex program that identifies keywords and operators in C code.Single Pass Assembler
Single Pass AssemblerSatyamevjayte Haxor
╠²
The document provides an overview of single pass assemblers, which translate assembly language into machine code in a single scan of the source program. It details the assembler's functions, the challenges of forward references, and solutions to address them, including methods for eliminating forward references and generating object code in memory. Additionally, a sample C program is included that demonstrates how to implement a single pass assembler to process assembly instructions.Multiplier control unit
Multiplier control unitSatyamevjayte Haxor
╠²
Computer Organization & Architecture Multiplier Control UnitControl unit design
Control unit designSatyamevjayte Haxor
╠²
The document discusses the organization and design of a computer's control unit. It describes control units as being implemented as combinational logic circuits using gates, flip-flops, and decoders. The control unit uses the opcode of the instruction in the instruction register along with the clock and flags to determine the required control signals. A decoder is used to trigger a unique output line for each opcode input pattern. The control unit issues clock pulses to control the micro-operations and its behavior can be designed as a state table.Direct linking loaders
Direct linking loadersSatyamevjayte Haxor
╠²
The document summarizes the key aspects of direct linking loaders. A direct linking loader allows for multiple procedure and data segments and flexible intersegment referencing. It provides assembler output with the length and symbol tables (USE and DEFINITION) to the loader. The loader performs two passes, building a Global External Symbol Table in Pass 1 and performing relocation and linking in Pass 2 using the object decks with External Symbol Dictionary, instructions/data, and relocation/linkage sections. This allows combining and executing object code from separate object programs.Two pass Assembler
Two pass AssemblerSatyamevjayte Haxor
╠²
The document discusses a seminar on two-pass assemblers at the Walchand Institute of Technology, Solapur, detailing the two processing passes of a source program. It outlines the algorithms for both passes, including the management of symbol tables and opcode translation, and discusses data structures like operation code tables and symbol tables. A sample program is also included to illustrate how the assembly process works, including location counting and symbol resolution.Compilers
CompilersSatyamevjayte Haxor
╠²
A compiler is a program that translates a program written in one language (the source language) into an equivalent program in another language (the target language). Compilers perform several phases of analysis and translation: lexical analysis converts characters into tokens; syntax analysis groups tokens into a parse tree; semantic analysis checks for errors and collects type information; intermediate code generation produces an abstract representation; code optimization improves the intermediate code; and code generation outputs the target code. Compilers translate source code, detect errors, and produce optimized machine-readable code.Linking in MS-Dos System
Linking in MS-Dos SystemSatyamevjayte Haxor
╠²
This document discusses linking in the MS-DOS operating system. It describes how linking involves combining various pieces of code and data into a single file that can be loaded into memory and executed. The document outlines the role of linkers in automatically performing linking. It also provides details on the object module format and record types in MS-DOS, and describes how a linker would be designed for MS-DOS, including its invocation command format, linking and relocation processes, and use of data structures.Ad
Linker
- 2. What Is Linker ? ’āścombines two or more separate object programs and supplies the information needed to allow references between them
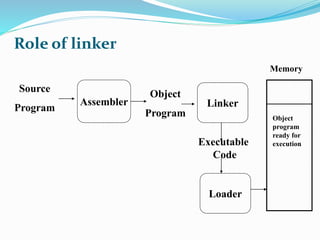
- 3. Role of linker Source Program Assembler Object Program Linker Executable Code Loader Memory Object program ready for execution
- 4. Program Input : 1. P1.txt extern x, y, z 2. P2.txt 200 int x 201 int y 202 int z
- 5. // SIMULATION OF LINKER #include<iostream.h> #include<conio.h> #include<stdio.h> #include<string.h> #include<math.h> #include<stdlib.h> struct x { char f[10]; }s[20],t[20],r[10];
- 6. void main() { clrscr(); x o[2]={"int","float"}; x z[20],v[20]; char c,*a,*b; int i=0, j=0, k=0, l=0, flag=0, flag1=0, h=0, y=0, u=0; int m; FILE *p1,*p2; p1=fopen("p1.txt","r"); p2=fopen("p2.txt","r");
- 7. do { c=fgetc(p1); if(c!=' '&&c!='n'&&c!=',') { a[i]=c; i++; } else { a[i]='0'; strcpy(s[j].f,a); j++; i=0; k++; } }while(c!=EOF);
- 8. i=0; j=0; do { c=fgetc(p2); if(c!=' '&& c!='n') { if((abs(c)>=65&&abs(c)<=90)||(abs(c)>=97&&abs(c) <=122)) { a[i]=c; //insert characters e.g.int x i++; flag=1; }
- 9. else { b[h]=c; //insert digits e.g. 200 h++; flag1=1; } } else { if(flag==1) //For characters { a[i]='0'; strcpy(t[j].f,a); j++; i=0; l++; //counter
- 10. } if(flag1==1) // For Digits { b[h]='0'; strcpy(r[y].f,b); y++; h=0; u++; //counter } } }while(c!=EOF); h=0;
- 11. for(i=0;i<l;i++) { flag=0; for(j=0;j<2;j++) //for characters { if(strcmp(t[i].f,o[j].f)==0||strcmp(t[i].f,"")==0) { flag=1; } } if(flag==0) { strcpy(v[h].f,t[i].f ); h++; } }
- 12. l=0; for(i=0;i<u;i++) //for digits { if(strcmp(r[i].f,"")!=0) { strcpy(z[l].f,r[i].f ); l++; } } cout<<"n***After Linking****n"; flag=0; l=0;
- 13. for(i=0;i<k;i++) { flag=0; for(j=0;j<h;j++) { if(strcmp(s[i].f,v[j].f)==0) flag=1; } if(flag==1) { m=atoi(z[l].f)+400; cout<<s[i].f<<" "<<"p1"<<" "<<m<<"n"; l++; }
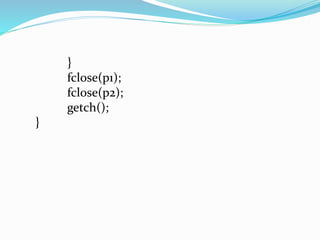
- 14. } fclose(p1); fclose(p2); getch(); }
- 15. P1.txt extern x, y, z; P2.txt 200 int x 201 int y 202 int z After Linking x p1 600 y p1 601 z p1 602