I psec vpn with forti client
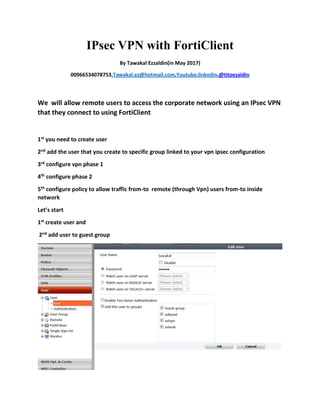
- 1. IPsec VPN with FortiClient By Tawakal Ezzaldin(in May 2017) 00966534078753,Tawakal.ez@hotmail.com,Youtube,linkedin,@titoezaldin We will allow remote users to access the corporate network using an IPsec VPN that they connect to using FortiClient 1st you need to create user 2nd add the user that you create to specific group linked to your vpn ipsec configuration 3rd configure vpn phase 1 4th configure phase 2 5th configure policy to allow traffic from-to remote (through Vpn) users from-to inside network Let’s start 1st create user and 2nd add user to guest group
- 2. 3rd configure vpn phase 1 GOTO VPN and then IPsec to create phase 1 Give the pahse1 name like (VPN) and choose remote Gateway Dialup Users and specify wan interface as local interface and enable ipsec interface and put the ip address connected to wan and then p1 proposal including encryption DES and authentication MD5 also DH group Group 5 also lifetime 28800 sec and enable Xauth for authentication remote users (guest roup ) and enable dead peer detection and enable NAT and keepalive 10 sec
- 3. 4th configure pahse 2 Name phase 2 (forticlent) and choose phase 1 and choose p2 proposal 5th configure policy to allow traffic from-to remote (through VPN) users from-to inside network You need to allow traffic from remote users (Guest Group) that using forticlient to inside lan network And also the traffic from inside to remote users Goto policy and add two policy One From VPN interface To Inside Another from inside to VPN interface