ZRT - Pentest Project Management & Report Automation Tool
Download as pptx, pdf0 likes572 views
ZinnoX Reporting Tool (ZRT) is an automated penetration testing report generation tool that allows security professionals to quickly and easily create comprehensive reports. Key features of ZRT include managing project details and findings databases, one-click uploads and report generation, customization options, backup and restore functionality, and integration of the OWASP vulnerability mapping and DREAD risk assessment models to prioritize issues. ZRT aims to revolutionize the penetration testing reporting process by providing a simple user interface and streamlining the entire reporting workflow into just a few clicks to produce high-quality reports in a matter of minutes.
1 of 15
Download to read offline












Ad
Recommended
The uncool-security-hygiene
The uncool-security-hygieneThiagu Haldurai
╠²
1. The document discusses challenges with endpoint security including lack of visibility, isolated solutions, excessive resource usage, and heterogeneous environments. It argues for continuous vulnerability assessment, automated patching, and compliance enforcement through a single solution.
2. Key recommendations include maintaining continuous asset visibility, performing ongoing risk assessment, quickly addressing high-profile vulnerabilities, consolidating patching, applying critical patches immediately, and automating compliance.
3. The SecPod SanerNow platform is presented as providing a single dashboard and agent to address these needs through tools for asset management, vulnerability scanning, patching, compliance, and threat management.Application of Data Mining Techniques for Improving Continuous Integration
Application of Data Mining Techniques for Improving Continuous IntegrationDr. Amarjeet Singh
╠²
This document discusses how data mining techniques can be applied to data from continuous integration (CI) processes to extract useful knowledge and solve problems. CI involves frequent integration of code changes to detect errors early. It generates vast amounts of log and monitoring data that is often ignored. The document proposes applying clustering, classification, text mining and other techniques to this CI data to group similar logs, predict failures, find frequent issues, and understand team productivity and code changes. This could help with maintenance and further development by gaining insights from the abundant CI data typically not utilized.Secure Software Development Life Cycle
Secure Software Development Life CycleMaurice Dawson
╠²
The document discusses the importance of secure software development life cycles (SDLC) as defense contractors develop systems for the Department of Defense (DoD), emphasizing the need for software assurance due to vulnerabilities often found at the application layer. It outlines the integration of security controls throughout the development process to maintain the integrity, availability, and confidentiality of software while adhering to DoD standards. Additionally, it highlights the need for a knowledgeable staff and secure software policies to effectively mitigate exploitable vulnerabilities.The impact of consumerization
The impact of consumerizationMichel de Goede
╠²
The document discusses the impact of consumerization on IT and the evolving role of employees who are now more computer literate and creatively managing their work. It highlights the challenges and risks related to back-end integration, data formats, and security while suggesting countermeasures such as reducing complexity, educating staff, and fostering resiliency. Ultimately, it emphasizes the need for IT to adapt to a user-led approach and share responsibilities.8 Patterns For Continuous Code Security by Veracode CTO Chris Wysopal
8 Patterns For Continuous Code Security by Veracode CTO Chris WysopalThreat Stack
╠²
The document outlines eight patterns for integrating continuous code security within agile development processes, emphasizing the necessity of addressing security vulnerabilities early in the software development lifecycle. It advocates for collaboration between security assessments and development tools to help automate code analysis, streamline vulnerability management, and enhance overall security without compromising efficiency. Implementing these practices allows organizations to reduce risks associated with web applications, ultimately leading to more secure and efficient code deployment.Veracode - Overview
Veracode - OverviewStephen Durrant
╠²
The document summarizes Veracode's application security platform. It continuously learns from scans to address evolving threats. It uses a cloud-based platform that is massively scalable and allows organizations to start immediately without hiring consultants or installing servers. It also provides program managers to help implement a centralized, policy-based approach to managing application security across an enterprise.Why Patch Management is Still the Best First Line of Defense
Why Patch Management is Still the Best First Line of DefenseLumension
╠²
The document discusses the increasing vulnerabilities in applications beyond Microsoft, emphasizing that 90% of exploits used in breaches had patches available for over six months. It highlights the challenges of patch management, including lack of resources and visibility, which hinder effective endpoint operations and security. The presentation concludes that focusing on patching client-side applications is crucial for mitigating cybersecurity risks, with the Lumension Endpoint Management and Security Suite positioned as a comprehensive solution for managing vulnerabilities.IBM Rational AppScan Product Overview
IBM Rational AppScan Product OverviewAshish Patel
╠²
The document discusses the importance of application security and the need for integrating security testing into the application development lifecycle. It highlights the challenges faced by organizations in implementing security measures and how IBM's Rational AppScan solutions can empower developers to proactively address security vulnerabilities without requiring extensive security expertise. Additionally, it emphasizes the benefits of early security checks, automated testing processes, and comprehensive analysis techniques designed for non-security professionals.IBM AppScan Standard
- The Web Application Security Solution
IBM AppScan Standard
- The Web Application Security Solutionhearme limited company
╠²
IBM AppScan Standard is a web application security testing tool that identifies vulnerabilities and risks associated with web applications. Key features include dynamic, static, and interactive analysis to assess and improve application security against threats like cross-site scripting and injection flaws. The solution integrates with various management tools and has been implemented successfully for clients in Vietnam.IBM AppScan Enterprise
- The total software security solution
IBM AppScan Enterprise
- The total software security solutionhearme limited company
╠²
The document provides an overview of IBM AppScan Enterprise, its key features, workflows, and benefits for application security. It discusses various web application vulnerabilities, the importance of security in the software development lifecycle, and how AppScan addresses these issues through centralized control and reporting capabilities. Additionally, it highlights IBM's recognition as a leader in application security testing by Gartner.IBM AppScan - the total software security solution
IBM AppScan - the total software security solutionhearme limited company
╠²
The document discusses the IBM AppScan security solution, emphasizing application security best practices and vulnerabilities such as cross-site scripting and SQL injection. It outlines different types of analysis methods, including static and dynamic analysis, and describes the AppScan products used for security testing throughout the software development lifecycle. Additionally, it includes trends in web application vulnerabilities and highlights the importance of integrating security testing into the development process.What Good is this Tool? A Guide to Choosing the Right Application Security Te...
What Good is this Tool? A Guide to Choosing the Right Application Security Te...Kevin Fealey
╠²
The document serves as a guide for choosing the right application security testing (AST) tools, outlining the differences between static (SAST), dynamic (DAST), and interactive application security testing (IAST). It discusses the importance of integration within the software development lifecycle (SDLC) and offers recommendations for effective security practices. Additionally, it highlights various popular AST vendors and tools, while emphasizing the need for consistent testing and minimizing false positives.A Bug Tracking System Is A Software Application
A Bug Tracking System Is A Software ApplicationAbhishek Pasricha
╠²
This document provides an overview of a bug tracking system called Bug Zero. It begins with definitions of what a bug is and an introduction to bug tracking systems and their purpose. It then describes some important facts that are typically recorded in a bug tracking system database. The document outlines the benefits of centralized bug tracking and different types of bug trackers. It provides details about Bug Zero, including its advantages, stages of use, and screenshots. It concludes with an estimate of the time required to install Bug Zero and references additional resources.WhatŌĆÖs making way for secure sdlc
WhatŌĆÖs making way for secure sdlcAvancercorp
╠²
Organizations are increasingly incorporating security practices into the software development lifecycle (SDLC) to improve security and reduce expensive post-release fixes. The SDLC stages now include considering security in requirements, defining security parameters in design, building with security controls, and conducting penetration testing. Implementing a secure SDLC brings security practices into software development from the beginning to prevent vulnerabilities and ensure compliance with standards.Veracode - Inglês
Veracode - Ingl├¬sDeServ - Tecnologia e Serv├¦os
╠²
Veracode is a well-established US-based provider of application security testing (AST) services including static application security testing (SAST), dynamic application security testing (DAST), mobile AST, and software composition analysis (SCA). Veracode offers a broad set of AST services to help organizations build and deploy applications faster while reducing business risk. The company pioneered binary code analysis and was an early innovator in mobile AST and SCA. Veracode aims to help customers reduce risk across their entire software development lifecycle through its unified cloud-based platform and services.SAST vs. DAST: WhatŌĆÖs the Best Method For Application Security Testing?
SAST vs. DAST: WhatŌĆÖs the Best Method For Application Security Testing?Cigital
╠²
Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) are two distinct methods for identifying security vulnerabilities in software, differing mainly in their approach and timing within the Software Development Life Cycle (SDLC). SAST analyzes source code or binaries without executing the application, while DAST tests a running application and can discover runtime vulnerabilities. Both methods complement each other and should be used together for comprehensive security testing.What's New in Innoslate 4.3
What's New in Innoslate 4.3Elizabeth Steiner
╠²
The document outlines new features in Innoslate 4.3, including interface control diagrams, risk burndown charts, and OAuth/SAML support. It highlights Innoslate's capabilities in requirements management and systems engineering for defense and aerospace sectors. Additionally, the document provides information about online training courses and support options for users.24may 1200 valday eric anklesaria 'secure sdlc ŌĆō core banking'
24may 1200 valday eric anklesaria 'secure sdlc ŌĆō core banking'Positive Hack Days
╠²
Secure SDLC aims to integrate security practices into the entire software development lifecycle for core banking applications. It addresses shortcomings like lack of security requirements documentation, threat modeling, secure design practices, developer security training, and security testing. Implementing a Secure SDLC helps ensure core banking applications are developed securely through practices like threat modeling, secure coding guidelines, security testing, and ongoing security reviews of applications and infrastructure. This helps protect critical banking data and systems from threats while maintaining regulatory compliance.Zed Attack Proxy (ZAP)
Zed Attack Proxy (ZAP)JAINAM KAPADIYA
╠²
The document provides an overview of the OWASP Zed Attack Proxy (ZAP), an open-source web application security scanner. It discusses how ZAP can be used to automatically find vulnerabilities during development and testing. The document covers how to install ZAP and use its features like passive scanning, spidering, active scanning, fuzzing and brute forcing to analyze vulnerabilities. It also discusses ZAP's advantages in identifying issues and providing solutions, and potential disadvantages like lack of authentication.Owasp zap
Owasp zappenetration Tester
╠²
The document provides information on OWASP ZAP, a free and open source web application security testing tool. It discusses what ZAP is, why it is a good choice for security testing, its key features which include an intercepting proxy, scanners, spiders, and fuzzing. It then describes how to launch and use ZAP, covering its graphical user interface, attacking websites by spidering, scanning and reviewing alerts. Key terms like session and context are also explained. Steps to run a scan are outlined, including crawling the site, creating a session and context, attacking with spider and active scans, and reviewing scan results. Finally, the difference between active and passive scans is summarized.ZAP @FOSSASIA2015
ZAP @FOSSASIA2015Sumanth Damarla
╠²
ZAP is an easy to use and completely free and open source web application penetration testing tool. It is ideal for beginners and professionals alike due to its user-friendly interface and powerful features. As an OWASP flagship project, ZAP has an active development community, is translated into many languages, and is improving rapidly to detect more vulnerabilities and integrate better with other tools and APIs.Practical Security Testing for Developers using OWASP ZAP at Dot Net Bangalor...
Practical Security Testing for Developers using OWASP ZAP at Dot Net Bangalor...gmaran23
╠²
The document introduces OWASP ZAP, an open-source web application security testing tool designed for developers, emphasizing its ease of use and the importance of integrating security throughout the development lifecycle. It discusses the common security challenges faced by developers and highlights the benefits of using ZAP for proactive security testing and vulnerability management. The conclusion encourages developers to incorporate security tools, such as ZAP, into their workflows for better application security.Zed attack proxy [ What is ZAP(Zed Attack Proxy)? ]
Zed attack proxy [ What is ZAP(Zed Attack Proxy)? ]raj upadhyay
╠²
Zed Attack Proxy (ZAP) is a free and open source web application security tool that can be used to test for vulnerabilities during the development and testing phases. It includes features like an intercepting proxy, spidering to discover hidden links, both active and passive scanning to detect vulnerabilities, and reporting of results. ZAP allows users to intercept web traffic, modify requests and responses, scan sites for issues like XSS and SQLi, analyze results, and generate detailed vulnerability reports.JoinSEC 2013 London - ZAP Intro
JoinSEC 2013 London - ZAP IntroSimon Bennetts
╠²
ZAP (Zed Attack Proxy) is a free and open-source web application penetration testing tool developed by the OWASP Foundation to help find vulnerabilities in web applications. It includes features like an intercepting proxy, scanners, a spider, fuzzing tools and a macro language to aid in testing applications. The tool is actively developed by a community of contributors and used by both professionals and beginners for tasks like security testing, debugging and regression testing of applications.JavaOne 2014 Security Testing for Developers using OWASP ZAP
JavaOne 2014 Security Testing for Developers using OWASP ZAPSimon Bennetts
╠²
This document summarizes a presentation about using the OWASP Zed Attack Proxy (ZAP) for security testing during the development process. ZAP is an open source web application security scanner that can be used by developers to automate security testing. The presentation covers how to configure and use ZAP to explore applications, perform passive and active scans, and integrate ZAP into the development workflow through its API and scripting capabilities. It emphasizes that considering security early in development helps build more secure applications.OWASP ZAP API Automation
OWASP ZAP API AutomationThivya Lakshmi
╠²
This document provides an agenda for an OWASP ZAP API automation workshop. It will include an introduction to ZAP, familiarizing with the UI, using ZAP with Selenium for hands-on exercises, exploring key ZAP features like intercepting proxy, spider, passive/active scanners, fuzzing, and report generation using the ZAP API. It will also demonstrate integrating ZAP with CI/CD pipelines for security testing. The document provides details on active scanning, report generation, fuzzing, and accessing ZAP rules and a GitHub repo for hands-on exercises. It concludes with mentioning additional ZAP features like authentication, anti-CSRF, port scanning, and the ZAP marketplace.Security testing using zap
Security testing using zapConfiz Limited
╠²
The document presents an overview of the OWASP Zed Attack Proxy (ZAP), a tool for web penetration testing designed to identify vulnerabilities in web applications. It covers the features, advantages, installation process, and provides a demonstration of ZAP's capabilities, such as active and passive scanning. Additionally, it emphasizes ZAP's ease of use, open-source nature, and supportive community, along with future areas for potential exploration.2014 ZAP Workshop 1: Getting Started
2014 ZAP Workshop 1: Getting StartedSimon Bennetts
╠²
This document discusses an introduction to using OWASP ZAP, an open source web application security scanning tool. It provides an overview of ZAP's capabilities and principles, including that it is free, open source, and designed to be easy to use for both beginners and professionals. The document then demonstrates several features of ZAP through practical examples, such as using the quick start feature to scan a target site, configuring the browser as a proxy, and intercepting requests and responses. It concludes with potential topics to cover in future sessions, and invites questions from the audience.OWASP Zed Attack Proxy
OWASP Zed Attack ProxyFadi Abdulwahab
╠²
The OWASP Zed Attack Proxy (ZAP) is a free, open-source pen testing tool for web applications that is user-friendly for both beginners and professionals. It features capabilities such as active/passive scanning, spidering, brute force tools, and session management while being cross-platform and well-documented. ZAP emphasizes the importance of integrating security testing throughout the development and QA phases of the project lifecycle.OWSAP Zap Tool Execution - API Security Scan
OWSAP Zap Tool Execution - API Security ScanPalani Kumar
╠²
OWASP ZAP (Zed Attack Proxy) is an open-source tool designed for web application security testing, helping users identify vulnerabilities and security issues. Key features include proxy functionality, active and passive scanning, spidering, and session management testing. Users can easily conduct automated scans to detect various issues such as SQL injection, cross-site scripting, and sensitive data exposure.More Related Content
What's hot (10)
IBM AppScan Standard
- The Web Application Security Solution
IBM AppScan Standard
- The Web Application Security Solutionhearme limited company
╠²
IBM AppScan Standard is a web application security testing tool that identifies vulnerabilities and risks associated with web applications. Key features include dynamic, static, and interactive analysis to assess and improve application security against threats like cross-site scripting and injection flaws. The solution integrates with various management tools and has been implemented successfully for clients in Vietnam.IBM AppScan Enterprise
- The total software security solution
IBM AppScan Enterprise
- The total software security solutionhearme limited company
╠²
The document provides an overview of IBM AppScan Enterprise, its key features, workflows, and benefits for application security. It discusses various web application vulnerabilities, the importance of security in the software development lifecycle, and how AppScan addresses these issues through centralized control and reporting capabilities. Additionally, it highlights IBM's recognition as a leader in application security testing by Gartner.IBM AppScan - the total software security solution
IBM AppScan - the total software security solutionhearme limited company
╠²
The document discusses the IBM AppScan security solution, emphasizing application security best practices and vulnerabilities such as cross-site scripting and SQL injection. It outlines different types of analysis methods, including static and dynamic analysis, and describes the AppScan products used for security testing throughout the software development lifecycle. Additionally, it includes trends in web application vulnerabilities and highlights the importance of integrating security testing into the development process.What Good is this Tool? A Guide to Choosing the Right Application Security Te...
What Good is this Tool? A Guide to Choosing the Right Application Security Te...Kevin Fealey
╠²
The document serves as a guide for choosing the right application security testing (AST) tools, outlining the differences between static (SAST), dynamic (DAST), and interactive application security testing (IAST). It discusses the importance of integration within the software development lifecycle (SDLC) and offers recommendations for effective security practices. Additionally, it highlights various popular AST vendors and tools, while emphasizing the need for consistent testing and minimizing false positives.A Bug Tracking System Is A Software Application
A Bug Tracking System Is A Software ApplicationAbhishek Pasricha
╠²
This document provides an overview of a bug tracking system called Bug Zero. It begins with definitions of what a bug is and an introduction to bug tracking systems and their purpose. It then describes some important facts that are typically recorded in a bug tracking system database. The document outlines the benefits of centralized bug tracking and different types of bug trackers. It provides details about Bug Zero, including its advantages, stages of use, and screenshots. It concludes with an estimate of the time required to install Bug Zero and references additional resources.WhatŌĆÖs making way for secure sdlc
WhatŌĆÖs making way for secure sdlcAvancercorp
╠²
Organizations are increasingly incorporating security practices into the software development lifecycle (SDLC) to improve security and reduce expensive post-release fixes. The SDLC stages now include considering security in requirements, defining security parameters in design, building with security controls, and conducting penetration testing. Implementing a secure SDLC brings security practices into software development from the beginning to prevent vulnerabilities and ensure compliance with standards.Veracode - Inglês
Veracode - Ingl├¬sDeServ - Tecnologia e Serv├¦os
╠²
Veracode is a well-established US-based provider of application security testing (AST) services including static application security testing (SAST), dynamic application security testing (DAST), mobile AST, and software composition analysis (SCA). Veracode offers a broad set of AST services to help organizations build and deploy applications faster while reducing business risk. The company pioneered binary code analysis and was an early innovator in mobile AST and SCA. Veracode aims to help customers reduce risk across their entire software development lifecycle through its unified cloud-based platform and services.SAST vs. DAST: WhatŌĆÖs the Best Method For Application Security Testing?
SAST vs. DAST: WhatŌĆÖs the Best Method For Application Security Testing?Cigital
╠²
Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) are two distinct methods for identifying security vulnerabilities in software, differing mainly in their approach and timing within the Software Development Life Cycle (SDLC). SAST analyzes source code or binaries without executing the application, while DAST tests a running application and can discover runtime vulnerabilities. Both methods complement each other and should be used together for comprehensive security testing.What's New in Innoslate 4.3
What's New in Innoslate 4.3Elizabeth Steiner
╠²
The document outlines new features in Innoslate 4.3, including interface control diagrams, risk burndown charts, and OAuth/SAML support. It highlights Innoslate's capabilities in requirements management and systems engineering for defense and aerospace sectors. Additionally, the document provides information about online training courses and support options for users.24may 1200 valday eric anklesaria 'secure sdlc ŌĆō core banking'
24may 1200 valday eric anklesaria 'secure sdlc ŌĆō core banking'Positive Hack Days
╠²
Secure SDLC aims to integrate security practices into the entire software development lifecycle for core banking applications. It addresses shortcomings like lack of security requirements documentation, threat modeling, secure design practices, developer security training, and security testing. Implementing a Secure SDLC helps ensure core banking applications are developed securely through practices like threat modeling, secure coding guidelines, security testing, and ongoing security reviews of applications and infrastructure. This helps protect critical banking data and systems from threats while maintaining regulatory compliance.Similar to ZRT - Pentest Project Management & Report Automation Tool (20)
Zed Attack Proxy (ZAP)
Zed Attack Proxy (ZAP)JAINAM KAPADIYA
╠²
The document provides an overview of the OWASP Zed Attack Proxy (ZAP), an open-source web application security scanner. It discusses how ZAP can be used to automatically find vulnerabilities during development and testing. The document covers how to install ZAP and use its features like passive scanning, spidering, active scanning, fuzzing and brute forcing to analyze vulnerabilities. It also discusses ZAP's advantages in identifying issues and providing solutions, and potential disadvantages like lack of authentication.Owasp zap
Owasp zappenetration Tester
╠²
The document provides information on OWASP ZAP, a free and open source web application security testing tool. It discusses what ZAP is, why it is a good choice for security testing, its key features which include an intercepting proxy, scanners, spiders, and fuzzing. It then describes how to launch and use ZAP, covering its graphical user interface, attacking websites by spidering, scanning and reviewing alerts. Key terms like session and context are also explained. Steps to run a scan are outlined, including crawling the site, creating a session and context, attacking with spider and active scans, and reviewing scan results. Finally, the difference between active and passive scans is summarized.ZAP @FOSSASIA2015
ZAP @FOSSASIA2015Sumanth Damarla
╠²
ZAP is an easy to use and completely free and open source web application penetration testing tool. It is ideal for beginners and professionals alike due to its user-friendly interface and powerful features. As an OWASP flagship project, ZAP has an active development community, is translated into many languages, and is improving rapidly to detect more vulnerabilities and integrate better with other tools and APIs.Practical Security Testing for Developers using OWASP ZAP at Dot Net Bangalor...
Practical Security Testing for Developers using OWASP ZAP at Dot Net Bangalor...gmaran23
╠²
The document introduces OWASP ZAP, an open-source web application security testing tool designed for developers, emphasizing its ease of use and the importance of integrating security throughout the development lifecycle. It discusses the common security challenges faced by developers and highlights the benefits of using ZAP for proactive security testing and vulnerability management. The conclusion encourages developers to incorporate security tools, such as ZAP, into their workflows for better application security.Zed attack proxy [ What is ZAP(Zed Attack Proxy)? ]
Zed attack proxy [ What is ZAP(Zed Attack Proxy)? ]raj upadhyay
╠²
Zed Attack Proxy (ZAP) is a free and open source web application security tool that can be used to test for vulnerabilities during the development and testing phases. It includes features like an intercepting proxy, spidering to discover hidden links, both active and passive scanning to detect vulnerabilities, and reporting of results. ZAP allows users to intercept web traffic, modify requests and responses, scan sites for issues like XSS and SQLi, analyze results, and generate detailed vulnerability reports.JoinSEC 2013 London - ZAP Intro
JoinSEC 2013 London - ZAP IntroSimon Bennetts
╠²
ZAP (Zed Attack Proxy) is a free and open-source web application penetration testing tool developed by the OWASP Foundation to help find vulnerabilities in web applications. It includes features like an intercepting proxy, scanners, a spider, fuzzing tools and a macro language to aid in testing applications. The tool is actively developed by a community of contributors and used by both professionals and beginners for tasks like security testing, debugging and regression testing of applications.JavaOne 2014 Security Testing for Developers using OWASP ZAP
JavaOne 2014 Security Testing for Developers using OWASP ZAPSimon Bennetts
╠²
This document summarizes a presentation about using the OWASP Zed Attack Proxy (ZAP) for security testing during the development process. ZAP is an open source web application security scanner that can be used by developers to automate security testing. The presentation covers how to configure and use ZAP to explore applications, perform passive and active scans, and integrate ZAP into the development workflow through its API and scripting capabilities. It emphasizes that considering security early in development helps build more secure applications.OWASP ZAP API Automation
OWASP ZAP API AutomationThivya Lakshmi
╠²
This document provides an agenda for an OWASP ZAP API automation workshop. It will include an introduction to ZAP, familiarizing with the UI, using ZAP with Selenium for hands-on exercises, exploring key ZAP features like intercepting proxy, spider, passive/active scanners, fuzzing, and report generation using the ZAP API. It will also demonstrate integrating ZAP with CI/CD pipelines for security testing. The document provides details on active scanning, report generation, fuzzing, and accessing ZAP rules and a GitHub repo for hands-on exercises. It concludes with mentioning additional ZAP features like authentication, anti-CSRF, port scanning, and the ZAP marketplace.Security testing using zap
Security testing using zapConfiz Limited
╠²
The document presents an overview of the OWASP Zed Attack Proxy (ZAP), a tool for web penetration testing designed to identify vulnerabilities in web applications. It covers the features, advantages, installation process, and provides a demonstration of ZAP's capabilities, such as active and passive scanning. Additionally, it emphasizes ZAP's ease of use, open-source nature, and supportive community, along with future areas for potential exploration.2014 ZAP Workshop 1: Getting Started
2014 ZAP Workshop 1: Getting StartedSimon Bennetts
╠²
This document discusses an introduction to using OWASP ZAP, an open source web application security scanning tool. It provides an overview of ZAP's capabilities and principles, including that it is free, open source, and designed to be easy to use for both beginners and professionals. The document then demonstrates several features of ZAP through practical examples, such as using the quick start feature to scan a target site, configuring the browser as a proxy, and intercepting requests and responses. It concludes with potential topics to cover in future sessions, and invites questions from the audience.OWASP Zed Attack Proxy
OWASP Zed Attack ProxyFadi Abdulwahab
╠²
The OWASP Zed Attack Proxy (ZAP) is a free, open-source pen testing tool for web applications that is user-friendly for both beginners and professionals. It features capabilities such as active/passive scanning, spidering, brute force tools, and session management while being cross-platform and well-documented. ZAP emphasizes the importance of integrating security testing throughout the development and QA phases of the project lifecycle.OWSAP Zap Tool Execution - API Security Scan
OWSAP Zap Tool Execution - API Security ScanPalani Kumar
╠²
OWASP ZAP (Zed Attack Proxy) is an open-source tool designed for web application security testing, helping users identify vulnerabilities and security issues. Key features include proxy functionality, active and passive scanning, spidering, and session management testing. Users can easily conduct automated scans to detect various issues such as SQL injection, cross-site scripting, and sensitive data exposure.OWASP 2013 EU Tour Amsterdam ZAP Intro
OWASP 2013 EU Tour Amsterdam ZAP IntroSimon Bennetts
╠²
The OWASP Zed Attack Proxy (ZAP) is a free, open-source web application penetration testing tool ideal for both beginners and professionals, offering features like an intercepting proxy, scanners, and add-ons marketplace. Launched in 2010, ZAP has become a flagship project of OWASP, with a user-friendly interface and extensive documentation. Its capabilities support manual and automated security testing for developers and pentesters alike.Owasp zap
Owasp zapColdFusionConference
╠²
This document discusses using the OWASP Zed Attack Proxy (ZAP) tool to find vulnerabilities in web applications. ZAP is a free and open-source web application penetration testing tool that can be used to conduct both automated and manual testing of applications. The document provides an overview of ZAP's features, how to install and configure it, how to test applications for vulnerabilities using both automated and direct methods, and how to integrate ZAP with other tools.OWASP 2013 AppSec EU Hamburg - ZAP Innovations
OWASP 2013 AppSec EU Hamburg - ZAP InnovationsSimon Bennetts
╠²
The document details the OWASP Zed Attack Proxy (ZAP), a free and open-source web application penetration testing tool ideal for both beginners and professionals. It outlines ZAP's principles, main features, and recent innovations, such as enhanced session handling and advanced reporting capabilities. The document encourages community involvement and feedback to further improve the tool.N Different Strategies to Automate OWASP ZAP - Cybersecurity WithTheBest - Oc...
N Different Strategies to Automate OWASP ZAP - Cybersecurity WithTheBest - Oc...gmaran23
╠²
The document discusses automating application security using the OWASP Zed Attack Proxy (ZAP), highlighting common security challenges faced by developers and the importance of integrating security tools in the development lifecycle. It provides an overview of the ZAP API, various strategies for automating security testing, and practical demonstrations of baseline and authenticated scans. Key tips for CI/CD integration and scripting for additional automation are also included, emphasizing the need for continuous security consideration in software development.OWASP Zed Attack Proxy Demonstration - OWASP Bangalore Nov 22 2014
OWASP Zed Attack Proxy Demonstration - OWASP Bangalore Nov 22 2014gmaran23
╠²
The document summarizes a presentation on the OWASP Zed Attack Proxy (ZAP), an open source web application security scanner. It provides an overview of ZAP's history and core features, including its use as an intercepting proxy, passive and active scanner, spider, and fuzzer. Advanced features such as auto-tagging and the add-ons marketplace are also highlighted. The presentation concludes with a demonstration of ZAP's scanning and testing capabilities.Simon Bennetts - Automating ZAP
Simon Bennetts - Automating ZAP DevSecCon
╠²
The document provides information about automating scans using the OWASP ZAP security tool. It discusses getting started with the baseline scan, options for full scans including the command line, Jenkins plugin, and API. It also covers exploring targets using the spider, performing passive and active scans, generating reports, and authenticating. The workshop aims to demonstrate how to integrate ZAP into development pipelines to find security issues early.Automating OWASP ZAP - DevCSecCon talk
Automating OWASP ZAP - DevCSecCon talk Simon Bennetts
╠²
This document provides information about automating scans with the OWASP Zap security tool, including:
- An introduction to the baseline scan, which runs quickly and can be easily integrated into continuous integration pipelines.
- Options for more thorough scanning using the Zap command line interface, Jenkins plugin, or driving the Zap API directly from scripts.
- Tips for customizing Zap scans, such as configuring authentication, tuning speed and accuracy, and getting help with the documentation and user community.
- A demonstration of exploring targets using the Zap API, running passive and active scans, and generating reports programmatically.AppSec EU 2011 - An Introduction to ZAP by Simon Bennetts
AppSec EU 2011 - An Introduction to ZAP by Simon BennettsMagno Logan
╠²
ZAP (Zed Attack Proxy) is an open source web application penetration testing tool that is easy to use, cross-platform, and has been downloaded over 6,300 times. It includes features like an intercepting proxy, active and passive scanners, a spider, and report generation that allow it to test web applications for vulnerabilities. ZAP has an active international development community, is improving rapidly with new releases, and has the potential to introduce more people to application security best practices.Ad
Recently uploaded (11)
Where to Safely Buy a Verified Cash App Account Online in 2025
Where to Safely Buy a Verified Cash App Account Online in 2025SEOVCC
╠²
Purchasing verified Cash App accounts can simplify your transactions. These accounts offer security and efficiency. They help you avoid the hassle of account verification. Always choose reliable sources for buying these accounts. This ensures your safety and peace of mind.Kitchen Renovation: Creating Your Dream Cooking Space
Kitchen Renovation: Creating Your Dream Cooking Spaceyagnapathi049
╠²
Kitchen Renovation refers to the process of updating, remodeling, or completely redesigning a kitchen space to improve its functionality, aesthetics, and overall value. This can involve a wide range of changes, from installing new cabinets, countertops, and flooring to upgrading appliances, lighting, and plumbing fixtures. Kitchen renovations often aim to create a more efficient layout, enhance storage options, and modernize the look to suit the homeownerŌĆÖs style and needs. Whether itŌĆÖs a minor refresh or a full-scale overhaul, a kitchen renovation transforms the heart of the home into a more enjoyable, practical, and attractive space.Book of Clarity on Wingify's success - Paras Chopra
Book of Clarity on Wingify's success - Paras ChopraRazin Mustafiz
╠²
Source: https://docs.google.com/presentation/d/16woYvXbvgvjoMqAXQ9jE9lJGdicEDReF12JO9moTbmg/edit?usp=sharingThe Ultimate Guide to Local SEO Automation.pdf
The Ultimate Guide to Local SEO Automation.pdfKHM Anwar
╠²
Are you exhausted by your rivalsŌĆÖ success in local search results? Local SEO Automation is changing digital marketingŌĆÖs rules. Discover ten smart tools to dominate local SEO by 2025. These tools will simplify your processes and make it easy for customers to find you.
The game-changing applications worthy of being in your toolkit include Local SEO automation tools that simplify tasks such as optimizing Google Business Profiles, gathering customer reviews, and establishing consistent citations across the Internet.Why Cloud Monitoring Tools Break Down When You Need Them Most.pdf
Why Cloud Monitoring Tools Break Down When You Need Them Most.pdfSudeep Khire
╠²
Cloudshot is a comprehensive cloud management platform designed to simplify and optimize multi-cloud operations. It offers real-time visualization, monitoring, and deployment capabilities across leading cloud providers such as AWS, Azure, and GCP. With features like AI-powered cost optimization, zero-trust security, and intelligent automation, Cloudshot enables businesses to reduce expenses by up to 40% and accelerate deployment speeds by three times. Its patented integration technology ensures seamless and secure management of complex cloud infrastructures. Local SEO Guide 2025-12 Strategies Explained.pdf
Local SEO Guide 2025-12 Strategies Explained.pdfKHM Anwar
╠²
Local SEO Guide: Why do some shops appear on Google Maps while others do not? This article will help you get your coffee shop at the top of local searches. Search engines reveal their new methods every few months. For instance, today, 55% of users search for information about people and places in their vicinity.
Simply having an online presence is no longer enough. You have to specialize in your area. If you deliver pizza or fix roofs next door, make your presence felt locally.
These Local SEO Guide-twelve tips will help create your local authority on search results pages in 2025. They are responsive to modern-day algorithms and build on what others say about you. You may now get noticed by those who live close by. Let us get started.Why DevOps Alert Fatigue Is Undermining Cloud Reliability.pdf
Why DevOps Alert Fatigue Is Undermining Cloud Reliability.pdfSudeep Khire
╠²
Cloudshot is a comprehensive cloud management platform designed to simplify and optimize multi-cloud operations. It offers real-time visualization, monitoring, and deployment capabilities across leading cloud providers such as AWS, Azure, and GCP. With features like AI-powered cost optimization, zero-trust security, and intelligent automation, Cloudshot enables businesses to reduce expenses by up to 40% and accelerate deployment speeds by three times. Its patented integration technology ensures seamless and secure management of complex cloud infrastructures. Chapter 1.pptx: Urban economics analysis
Chapter 1.pptx: Urban economics analysisAtoshe Elmi
╠²
This chapter is about analysis of urban economics Cut Incident Diagnosis Time by 60% With One Cloudshot Upgrade.pdf
Cut Incident Diagnosis Time by 60% With One Cloudshot Upgrade.pdfSudeep Khire
╠²
Cloudshot is a comprehensive cloud management platform designed to simplify and optimize multi-cloud operations. It offers real-time visualization, monitoring, and deployment capabilities across leading cloud providers such as AWS, Azure, and GCP. With features like AI-powered cost optimization, zero-trust security, and intelligent automation, Cloudshot enables businesses to reduce expenses by up to 40% and accelerate deployment speeds by three times. Its patented integration technology ensures seamless and secure management of complex cloud infrastructures. Building Financial Resilience_ Why ItŌĆÖs More Important Than Ever
Building Financial Resilience_ Why ItŌĆÖs More Important Than EverMatt Dixon
╠²
"Building Financial Resilience: Why ItŌĆÖs More Important Than Ever"** explores the critical need for individuals and families to strengthen their financial stability in an increasingly uncertain world. This piece highlights practical strategies for managing debt, saving effectively, and preparing for unexpected challengesŌĆöempowering readers to take control of their financial future with confidence.Ad
ZRT - Pentest Project Management & Report Automation Tool
- 1. ZinnoX Reporting Tool ZRT Pentest Project Management & Report Automation Tool
- 2. ZinnoX - Introduction ZinnoX is a Business and Technology Solutions company, headquartered in Bangalore, India Our solutions include services in IT Security. ZinnoX Presence ŌĆō Europe, US, Africa, India, Australia, New Zealand & Canada
- 3. About ZinnoX Security Testing ZinnoX Security Testing Services include Penetration Testing and Vulnerability Assessment Services - Web Application - Mobile Application - Network Combines advantages of traditional Testing Techniques - Hybrid testing (Automated Scanners + Manual Testing) Ensures convenience, speed, cost-saving and increased efficiency
- 4. PenTesting Reports & ZRT The Report Creation stage typically takes a minimum of one day or more depending on the project scope. ZinnoX intends to help companies address the specific challenge of speeding up the report creation process. ZinnoXŌĆÖs Reporting Tool (ZRT) aims at making the Pen Testing Report Creation a completely automated process ZRT is an extremely simple, user friendly and efficient application that one can use to create concise, crisp and comprehensive reports by following just a few simple steps
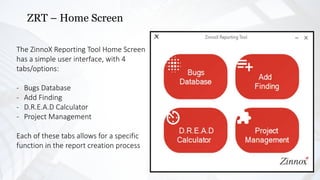
- 5. ZRT ŌĆō Home Screen The ZinnoX Reporting Tool Home Screen has a simple user interface, with 4 tabs/options: - Bugs Database - Add Finding - D.R.E.A.D Calculator - Project Management Each of these tabs allows for a specific function in the report creation process
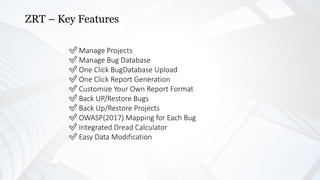
- 6. ZRT ŌĆō Key Features Ō£ģ Manage Projects Ō£ģ Manage Bug Database Ō£ģ One Click BugDatabase Upload Ō£ģ One Click Report Generation Ō£ģ Customize Your Own Report Format Ō£ģ Back UP/Restore Bugs Ō£ģ Back Up/Restore Projects Ō£ģ OWASP(2017) Mapping for Each Bug Ō£ģ Integrated Dread Calculator Ō£ģ Easy Data Modification
- 7. Manage Projects Each individual PenTest Project Reporting Process can be managed using the ŌĆ£Project ManagementŌĆØ tab. It allows for ŌĆ£CreationŌĆØ of new projects individually with details such as ŌĆ£Project OwnerŌĆØ, ŌĆ£Created forŌĆØ, Time Window, dates the Test was conducted etc. Each new project created gets populated in the ŌĆ£ProjectsŌĆØ section, and is available for easy access and modification, if required And create a report just by clicking on the ŌĆ£Generate reportŌĆØ button at the screen.
- 8. Manage Bug Database The ZRT Home screen includes two important sections/tabs that allow the effective management of a comprehensive Bug database. 1. Add Findings : To add new bug to the database 2. Bug Database : Every bug added will be found here for read & write purpose.
- 9. One-Click Options for Knowledge Base Upload and Report Generation The upload can be done in 2 ways 1. Feed all the data in the template given & upload in the tool. 2. Find the backup file from ZRT and restore it again. Note** : You will find the upload template in Zip file you have downloaded from ZinnoX website. Similarly, once each individual projects are created, with details of all findings being selected for each project, all it takes is the click of one button ŌĆ£GenerateŌĆØ to complete the Report Generation Process
- 10. Customize Your Own Report Format Although ZRT comes with a default template and a default format, the complete customization of the format is also possible If one chooses to have the Reports from ZRT to be created/generated in their own specific formats, it can be done by following a simple set of instructions and a bit of technical know-how (Complete step by step process for this will be shared upon request) Note**: You will find the ŌĆśUser ManualŌĆÖ in Zip file you have downloaded from ZinnoX website.
- 11. Back Up / Restore Bugs and Projects The ŌĆ£Bugs DatabaseŌĆØ section includes an option ŌĆ£Backup BugsŌĆØ & ŌĆ£Restore BugsŌĆØ which can be used to take a backup / restore of the entire database for future use. Similarly, the ŌĆ£Project managementŌĆØ section includes an option ŌĆ£Backup ProjectsŌĆØ and ŌĆ£Restore ProjectsŌĆØ. This feature is very useful in several instances. For example, if multiple systems are in use, a backup from one and restore to another system allows the seamless use of data on ZRT across systems
- 12. OWASP Mapping for Each Bug The Open Web Application Security Project (OWASP) is an online community which offers for free, articles, documentation, methodologies, technology and even tools in the Application Security field The OWASP Top 10 is a powerful document on awareness for Application Security and is a compilation of the broad consensus on most critical risks Adopting the OWASP Top 10 is considered widely as the most effective first step to producing secure code ZRT allows for OWASP Mapping using the ŌĆ£Vulnerability (OWASP)ŌĆØ dropdown in the ŌĆ£Add FindingsŌĆØ section. A helpful ŌĆ£More Info..ŌĆØ link redirects to the OWASP.org website for a clear understanding
- 13. D.R.E.A.D Calculator The DREAD is a mnemonic for a Risk Assessment Model to assess the criticality/impact/risk associated with the computer security threats/vulnerabilities/bugs. Damage - how bad would an attack be? Reproducibility - how easy is it to reproduce the attack? Exploitability - how much work is it to launch the attack? Affected users - how many people will be impacted? Discoverability - how easy is it to discover the threat? This rating allows us to prioritize on which vulnerability has to be attended to first, that is, Critical and High vulnerabilities will have to be looked into first because they have a higher impact on the application. (There is a handy ŌĆ£More Info..ŌĆØ link which redirects to the Wikipedia page on DREAD)
- 14. ZinnoX Reporting Tool ŌĆō Unique Proposition The ZRT is all set to revolutionize the report automation industry by bringing together the simplest user interface and experience, with the highest impacting value added features This makes the entire reporting process a quick, hassle-free experience The outcome is crisp, concise and comprehensive reports, all in a matter of minutes, with the push of a series of a few buttons
- 15. Thank You Bangalore | India www.zinnox.com
