Workshop: Advanced Federation Use-Cases with PingFederate
- 1. Workshop: Advanced Federation Use-Cases with PingFederate Craig Wu - Director, Product Development Peter Motykowski - Senior Engineer/Developer
- 2. Agenda • Introductions • New Features Overview – OAuth – Adaptive Federation – PingFederate 6.7 and beyond 2 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 3. Agenda • Demos – OAuth Authorization Code Flow – Adaptive Federation Use Cases • Adapter Selectors • Composite Adapter • Multiple IdP data stores 3 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 4. Agenda • Extending PingFederate – Developing Plugins • PingFederate SDK – Building a custom adapter selector 4 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 5. Who are these guys? INTRODUCTIONS 5 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 6. Craig Wu • Director, Product Development • Been with Ping Identity since Feb 2007 • Started with Integration Kits • PF STS integration • PingFederate Fall 2009 – PF 6.2 6 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 7. Peter Motykowski • Senior Engineer/Developer • Been with Ping Identity since May 2007 • Started with PingLabs • PF STS Integration, Adapter Selectors, OAuth 7 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 8. PingFederate Engineering Team Denver, CO - Vancouver, BC - Moscow, Russia - Dublin, Ireland 8 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 9. PingFederate 6.5 OAUTH 9 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
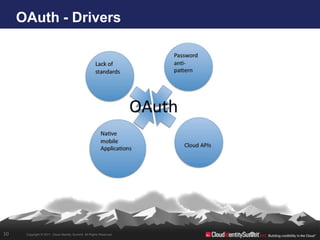
- 10. OAuth - Drivers 10 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 11. OAuth - Securing APIs • Simple and Standard – exchange user credentials for tokens – Present token for access • Scopes to limit access • Easily revoke access • Browser, mobile and desktop clients • PingFederate Authorization Server – User authenticates with AS – Leverage existing PF authentication 11 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
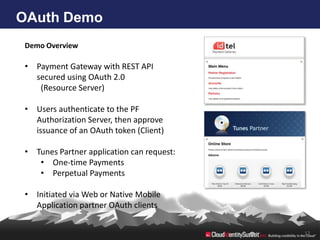
- 12. OAuth Demo Demo Overview • Payment Gateway with REST API secured using OAuth 2.0 (Resource Server) • Users authenticate to the PF Authorization Server, then approve issuance of an OAuth token (Client) • Tunes Partner application can request: • One-time Payments • Perpetual Payments • Initiated via Web or Native Mobile Application partner OAuth clients 12
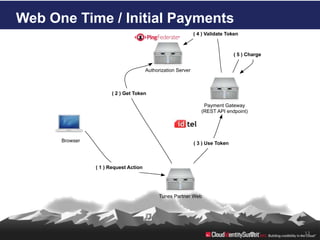
- 13. Web One Time / Initial Payments ( 4 ) Validate Token ( 5 ) Charge Authorization Server ( 2 ) Get Token Payment Gateway (REST API endpoint) Browser ( 3 ) Use Token ( 1 ) Request Action Tunes Partner Web 13
- 14. PingFederate 6.6 ADAPTIVE FEDERATION 14 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
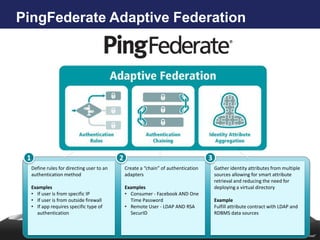
- 15. PingFederate Adaptive Federation 1 2 3 Define rules for directing user to an Create a “chain” of authentication SAML Gather identity attributes from multiple authentication method adapters sources allowing for smart attribute retrieval and reducing the need for Examples Examples deploying a virtual directory • If user is from specific IP • Consumer - Facebook AND One • If user is from outside firewall Time Password Example • If app requires specific type of • Remote User - LDAP AND RSA Fulfill attribute contract with LDAP and authentication SecurID RDBMS data sources
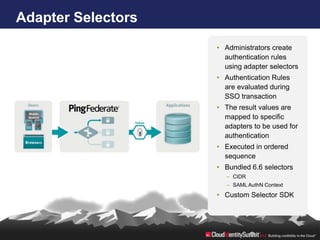
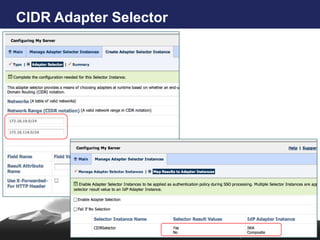
- 16. Adapter Selectors • Administrators create authentication rules using adapter selectors • Authentication Rules are evaluated during SSO transaction • The result values are mapped to specific adapters to be used for authentication • Executed in ordered sequence • Bundled 6.6 selectors – CIDR – SAML AuthN Context • Custom Selector SDK
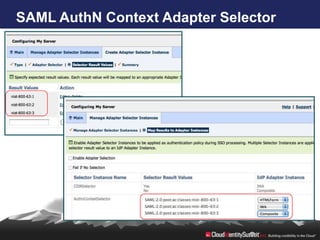
- 18. SAML AuthN Context Adapter Selector
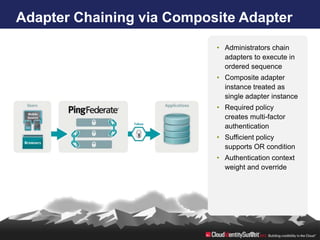
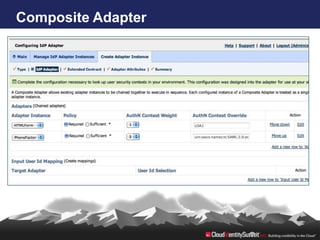
- 19. Adapter Chaining via Composite Adapter • Administrators chain adapters to execute in ordered sequence • Composite adapter instance treated as single adapter instance • Required policy creates multi-factor authentication • Sufficient policy supports OR condition • Authentication context weight and override
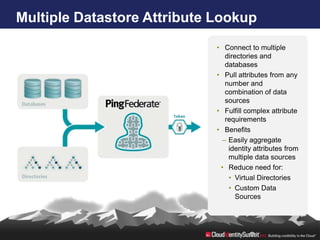
- 21. Multiple Datastore Attribute Lookup • Connect to multiple directories and databases • Pull attributes from any number and combination of data sources • Fulfill complex attribute requirements • Benefits – Easily aggregate identity attributes from multiple data sources • Reduce need for: • Virtual Directories • Custom Data Sources
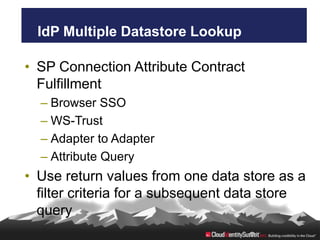
- 22. IdP Multiple Datastore Lookup • SP Connection Attribute Contract Fulfillment – Browser SSO – WS-Trust – Adapter to Adapter – Attribute Query • Use return values from one data store as a filter criteria for a subsequent data store query
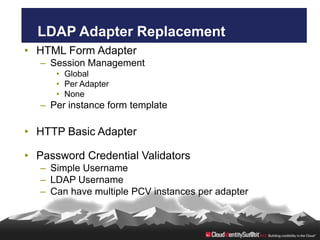
- 23. LDAP Adapter Replacement • HTML Form Adapter – Session Management • Global • Per Adapter • None – Per instance form template • HTTP Basic Adapter • Password Credential Validators – Simple Username – LDAP Username – Can have multiple PCV instances per adapter
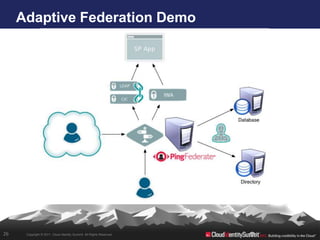
- 26. Adaptive Federation Demo 26 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
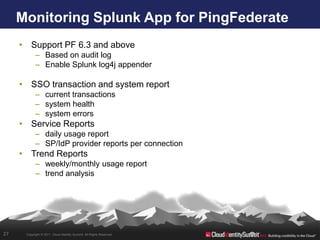
- 27. Monitoring Splunk App for PingFederate • Support PF 6.3 and above – Based on audit log – Enable Splunk log4j appender • SSO transaction and system report – current transactions – system health – system errors • Service Reports – daily usage report – SP/IdP provider reports per connection • Trend Reports – weekly/monthly usage report – trend analysis 27 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
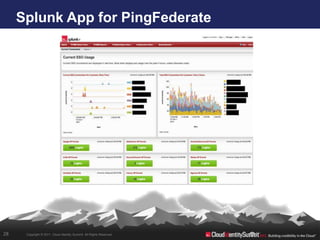
- 28. Splunk App for PingFederate 28 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 29. Free on SplunkBase http://splunk-base.splunk.com/apps/Splunk+App+for+PingFederate 29 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 30. PingFederate 6.7 and beyond PINGFEDERATE FUTURES 30 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 31. PingFederate 2012 Releases • Two month releases – RTM Release to Marketing – Fully qualified and documented – Upgrade Utility • Marketing determines GA 31 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 32. PingFederate 6.7 - RTM Feb 24, 2012 • Admin Console Optimizations – Large number of connections – Large number of adapters • Splunk App for PingFederate 32 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 33. PingFederate 6.8 – RTM April 27, 2012 • Centralized configuration for AD Domains/Kerberos Realms – IWA 3.0 Adapter – Kerberos Token Translator 2.0 • OAuth Client Management API – REST API for CRUD operations 33 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
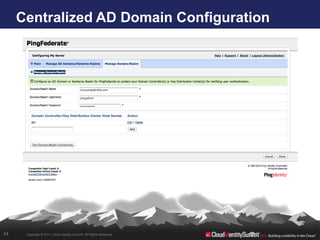
- 34. Centralized AD Domain Configuration 34 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
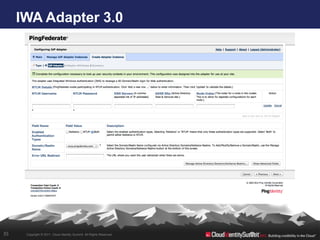
- 35. IWA Adapter 3.0 35 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 36. PingFederate 6.9 – RTM June 29, 2012 • Microsoft Office 365 Interoperability • Upgrade Jetty • Remove JBoss 36 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 37. PingFederate Software Development Kit (SDK) EXTENDING PINGFEDERATE 37 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 38. PingFederate Plugins • Adapters • Token Translators • Custom Data Sources • Adapter Selectors • Password Credential Validators 38 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
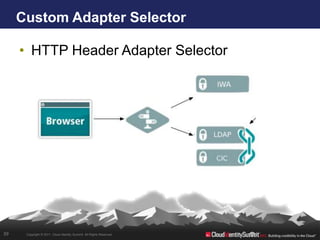
- 39. Custom Adapter Selector • HTTP Header Adapter Selector 39 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
- 40. Adapter Selector API Overview Methods needing to be implemented for the com.pingidentity.sdk.AdapterSelector interface: PluginDescriptor getPluginDescriptor(); void configure(Configuration configuration); AdapterSelectorContext selectContext(HttpServletRequest req, HttpServletResponse resp, Map<String, String> mappedAdapterIdsNames, Map<String, Object> extraParameters, String resumePath); void callback(HttpServletRequest req, HttpServletResponse resp, Map authnIdentifiers, String adapterInstanceId, AdapterSelectorContext adapterSelectorContext); 40 Copyright © 2011. Cloud Identity Summit. All Rights Reserved.
Editor's Notes
- #6: Insert funny pictures here
- #7: 5 to 40PF Web Services
- #8: 5 to 40PFWeb Services
- #11: Bad practice to give applications your passwords - Limit access – valet key to the web – only allow specific limited accessEasity revoke access – if you give out password you have to changePF – use IdP Adapters for authentication
- #12: Bad practice to give applications your passwords - Limit access – valet key to the web – only allow specific limited accessEasity revoke access – if you give out password you have to changePF – use IdP Adapters for authentication
- #13: Tunes Partner – client or appPayment Gateway – Resource ServerPF - AS
- #14: PFs responsibility is to authorize users and issue token to clients and validate tokens from RS
- #23: Available for all SP connection attribute contract fulfillment
- #28: Show link on spunkbase
- #29: Show link on spunkbase
- #30: Show link on spunkbase
- #32: 5 to 40PFWeb Services
- #33: 5 to 40PFWeb Services
- #34: 5 to 40PFWeb Services
- #35: 5 to 40PFWeb Services
- #36: 5 to 40PFWeb Services
- #37: 5 to 40PFWeb Services
- #39: 5 to 40PFWeb Services
- #40: 5 to 40PFWeb Services