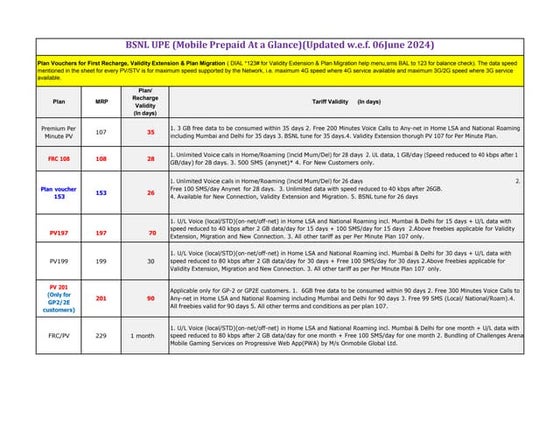
EVHEN. Asymmetric SPN-cipher (RusCrypto-2017)
- 1. CREATING ASYMMETRIC SPN-CIPHER WITH WHITE-BOX CRYPTOGRAPHY AND CHAOTIC MAPS PhD, Dmitry Schelkunov Bauman Moscow State Technical University, Kaluga branch RusCrypto-2017
- 2. White-box cryptography Ō£ōAllows to transform a symmetric block cipher to the asymmetric one by hiding a symmetric key in the obfuscated implementation (white-box implementation) of the encryption algorithm Ō£ōAims to create fast asymmetric ciphers that allow both encryption and signing Ō£ōWould make a communication much lighter, faster and secure (there would be no need for Diffie-Hellman key exchange algorithm) Ō£ōOne would communicate simultaneously with 2 and more others encryptingdecrypting a content "on-the-fly" without fear of the sender spoofing
- 3. Related work Ō£ōChow S., Eisen P., Johnson H., Van Oorschot P.C. (2003), White-Box Cryptography and an AES Implementation. In: Nyberg K., Heys H. (eds) Selected Areas in Cryptography. SAC 2002. Lecture Notes in Computer Science, vol 2595. Springer, Berlin, Heidelberg Ō£ōOlivier Billet and Henri Gilbert. A Traceable Block Cipher. In Advances in Cryptology - ASIACRYPT 2003, volume 2894 of Lecture Notes in Computer Science, pages 331-346. Springer-Verlag, 2003 Ō£ōOlivier Billet, Henri Gilbert, and Charaf Ech-Chatbi. Cryptanalysis of a White-Box AES Implementation. In Proceedings of the 11th International Workshop on Selected Areas in Cryptography (SAC 2004), volume 3357 of Lecture Notes in Computer Science, pages 227ŌĆō240. Springer-Verlag, 2004. Ō£ōBrecht Wyseur, White-box cryptography, PhD thesis, March 2009 Ō£ōDmitry Schelkunov, White-Box Cryptography and SPN ciphers. LRC method, Cryptology ePrint Archive: Report 2010/419 Ō£ōBrecht Wyseur, White-box cryptography: hiding keys in software, MISC magazine, April 2012 Ō£ōJoppe W. Bos and Charles Hubain and Wil Michiels and Philippe Teuwen, Differential Computation Analysis: Hiding your White-Box Designs is Not Enough, Cryptology ePrint Archive: Report 2015/753
- 4. Attacks on white-box implementations Almost all attacks are based on separation of known linear and non- linear parts of the source symmetric cipher and added white-box transformations Ō£ōDifferential cryptanalysis (including fault injection) Ō£ōAlgebraic cryptanalysis Ō£ōExtraction of the non-linear part (Olivier Billet, Henri Gilbert, and Charaf Ech-Chatbi. Cryptanalysis of a White-Box AES Implementation)
- 5. Method of concealing of a linear relationship n,xa,b,c,d,x npp ppcbax pcpbax thanlessdegreeswithspolinomial degreewithspolynomialeirreducibl, (1) )))(mod)(mod(( ))(mod))(mod(( 21 21 122 211 ’ĆŁ ’ĆŁ ’ā« ’āŁ ’ā¼ ’āŚ’āŚ’ĆĮ ’āŚ’āŚ’ĆĮ 21 xx ’é╣
- 6. Method of concealing of a linear relationship tableslookupassetare)(),( unknownare,,,,,,, thanlessdegreeswith)(overspolynomialarbitrary,,,, degreewith)( overspolynomialeirreduciblunequalpairwice,, )2( )(mod))(mod)(()( )(mod))(mod)(()( 21 321 321 312 211 xyxy dcbaxppp nGFdcbax nGF ppp pdpcxsxy pbpaxsxy ’üĪ ’üĪ ’ĆŁ ’ĆŁ ’ā« ’āŁ ’ā¼ ’āŚ’āŚ’ĆĮ ’āŚ’āŚ’ĆĮ
- 7. Method of concealing of a linear relationship )(mod)(and)(mod)( betweeniprelationshlinearafind:PROBLEM )2( )(mod))(mod)(()( )(mod))(mod)(()( 11 312 211 pcxspaxs pdpcxsxy pbpaxsxy ’āŚ’āŚ ’ā« ’āŁ ’ā¼ ’āŚ’āŚ’ĆĮ ’āŚ’āŚ’ĆĮ
- 8. Method of concealing of a linear relationship caxyxy p dqpdcxs q p bqpbaxs q p cxs q p axs q qpdqpdcxsxy qpbqpbaxsxy pdqpcxsxy pbqpaxsxy andFindtables).(lookupknownare)(,)(:PROBLEM ')( ; )( ; )( '; )( )4( ')()( )()( )3( )(mod)')(()( )(mod))(()( 21 3 11 3 2 11 2 1 1 1 1 33112 22111 3112 2111 ’ā║ ’ā╗ ’ā║ ’ā¬ ’ā½ ’ā¬ ’āŚ’āŚ’ĆŁ’āŚ’āŚ ’ĆĮ’ā║ ’ā╗ ’ā║ ’ā¬ ’ā½ ’ā¬ ’āŚ’āŚ’ĆŁ’āŚ’āŚ ’ĆĮ’ā║ ’ā╗ ’ā║ ’ā¬ ’ā½ ’ā¬ ’āŚ ’ĆĮ’ā║ ’ā╗ ’ā║ ’ā¬ ’ā½ ’ā¬ ’āŚ ’ĆĮ ’ā« ’āŁ ’ā¼ ’āŚ’ĆŁ’āŚ’āŚ’ĆŁ’āŚ’āŚ’ĆĮ ’āŚ’ĆŁ’āŚ’āŚ’ĆŁ’āŚ’āŚ’ĆĮ ’ā« ’āŁ ’ā¼ ’āŚ’āŚ’ĆŁ’āŚ’ĆĮ ’āŚ’āŚ’ĆŁ’āŚ’ĆĮ RLWE?
- 9. Method of concealing of a linear relationship Make (2) harder (5) )(mod)...)(mod))(mod)((...()( )(mod)...)(mod))(mod)((...()( )()()0( 3 )0( 12 )()()0( 2 )0( 11 ’ā« ’āŁ ’ā¼ ’āŚ’āŚ’āŚ’ĆĮ ’āŚ’āŚ’āŚ’ĆĮ k v k k u k pdpdpcxsxy pbpbpaxsxy )()( ’üĪ’üĪ jppi ’é╣ ’Ć© ’Ć® )!2,2min(:Hardness 2)1(2 nkn ’Ć½
- 10. Chaos theory in cryptography Ō£ōGoce Jakimoski and Ljup╦ćco Kocarev, Chaos and Cryptography: Block Encryption Ciphers Based on Chaotic Maps. IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMSŌĆöI: FUNDAMENTAL THEORY AND APPLICATIONS, VOL. 48, NO. 2, FEBRUARY 2001 Ō£ōAsim, M., Jeoti, V.: Efficient and simple method for designing chaotic S-boxes. ETRI Journal 30(1), 170ŌĆō172 (2008) Ō£ōMona Dara and Kooroush Manochehri, A Novel Method for Designing S-Boxes Based on Chaotic Logistic Maps Using Cipher Key. World Applied Sciences Journal 28 (12): 2003-2009, 2013 Ō£ōChristopher A. Wood, Chaos-Based Symmetric Key Cryptosystems Ō£ōDragan Lambi─ć and Miodrag ┼Įivkovi─ć, COMPARISON OF RANDOM S-BOX GENERATION METHODS. PUBLICATIONS DE LŌĆÖINSTITUT MATH├ēMATIQUE Nouvelle s├®rie, tome 93 (107) (2013)
- 11. Designing S-boxes with chaotic maps Ō£ōGood cryptographic properties Ō£ōSimple algorithms Ō£ōRandom S-boxes with good cryptographic properties allow to increase a security of a white-box implementation
- 12. MDS codes and MDS matrix MDS matrix (Maximal Distance Separable matrix) is a generating matrix of an MDS code ŌŚ” Maximal diffusion by design ŌŚ” Is used in SPN-ciphers in diffusion layers ŌŚ” Interesting types of matrices: ŌŚ” Vandermonde matrix ŌŚ” Involutory matrix (the same MDS matrix for encryption and decryption) ŌŚ” Cauchy matrix ŌŚ” Circulant matrix (like in Rijndael)
- 13. Cauchy matrix Ō£ōMDS matrix by design Ō£ōSimple algorithm of generation regardless of dimension Ō£ōThe property of circularity is not principal for the white-box implementation Ō£ōThe property of involutivity is harmful for the white-box implementation Ō£ōSo, choose a Cauchy matrix ’Ć© ’Ć® ’Ć© ’Ć®k ijjijijiij GFayxnjmiyxyxa 2,,;0;0;0; 1 ’āÄ’Ć╝’鯒Ć╝’鯒é╣’Ć½’Ć½’ĆĮ ’ĆŁ
- 14. A round of SPN-cipher Nonlinear part (S-boxes) Add round key Diffusion layer (MDS matrix + shifts)
- 15. A round of SPN cipher and T-boxes (Rijndael)
- 16. Chaotic asymmetric white-box SPN cipher Ō£ōS-boxes (8x8 bits) are generated randomly (using chaotic maps) for the every of the input bytes of the every of the rounds Ō£ōMDS matrix (16x16 bytes) is generated randomly (Cauchy matrix) for the every of the rounds Ō£ōA white-box implementation is based on obfuscation of the T-boxes Ō£ōA linear relationship between elements of the T-box is obfuscated with method of concealing of a linear relationship Ō£ōA set of the obfuscated T-boxes is a public key
- 17. A round of the chaotic asymmetric white-box SPN cipher iprelationshlinearaofconcealingofmethodusingnobfuscatio 2overmatrixMDStheofelementeappropriaton thetionmultiplica box-Sunique )0ifbyteinputan(orroundprevioustheofbyteoutput )6( ))((( ... ))((( ))((( ... ))((( ... ))((( ))((( ))((( ... ))((( ))((( ... )15( 8),( )( )0( 1 )15( 1 )15()15,315()15( )15( 1 )15()15,1()1( )15( 1 )15()15,0()0( )1( 1 )1()1,15()15( )1( 1 )1()1,1()1( )1( 1 )1()1,0()0( )0( 1 )0()0,15()15( )0( 1 )0()0,1()1( )0( 1 )0()0,0()0( )15( )1( )0( ’ĆŁ ’ĆŁ ’ĆŁ ’ĆĮ’ĆŁ ’ā║ ’ā║ ’ā║ ’ā║ ’ā║ ’ā╗ ’ā╣ ’ā¬ ’ā¬ ’ā¬ ’ā¬ ’ā¬ ’ā½ ’ā® ’āģ’āģ ’ā║ ’ā║ ’ā║ ’ā║ ’ā║ ’ā╗ ’ā╣ ’ā¬ ’ā¬ ’ā¬ ’ā¬ ’ā¬ ’ā½ ’ā® ’āģ ’ā║ ’ā║ ’ā║ ’ā║ ’ā║ ’ā╗ ’ā╣ ’ā¬ ’ā¬ ’ā¬ ’ā¬ ’ā¬ ’ā½ ’ā® ’ĆĮ ’ā║ ’ā║ ’ā║ ’ā║ ’ā║ ’ā╗ ’ā╣ ’ā¬ ’ā¬ ’ā¬ ’ā¬ ’ā¬ ’ā½ ’ā® ’ĆĮ ’ĆŁ ’ĆŁ ’ĆŁ ’ĆŁ ’ĆŁ ’ĆŁ ’ĆŁ ’ĆŁ ’ĆŁ ’ĆŁ j kl j k j j jjjj jjjj jjjj jjjj jjjj jjjj jjjj jjjj jjjj j j j j mix )GF(t s jy ystmix ystmix ystmix ystmix ystmix ystmix ystmix ystmix ystmix y y y Y
- 18. Hiding a linear relationship between elements of the T-box )GF(hp )GF(b t valpbpbpbat valpbpbpbat valpbpbpbat valpbpbpbat valpbpbpbat aT uj i huj i n i n kn i kn i n i n i n i n i n i k i k iiiiii k i k iiiiii k i k iiiiii k i k iiiiii i nn 2overdegreewithpolinomialeirreduciblselectedrandomly 2inpolinomialselectedrandomly nobfuscatiobeforebox-Ttheofelement )7( )(mod)...)(mod))(mod)(((...( .......................................................................... )(mod)...)(mod))(mod)(((...( )(mod)...)(mod))(mod)(((...( )(mod)...)(mod))(mod)(((...( )(mod)...)(mod))(mod)(((...( ][' ),( ),( )( ),(),()1,()1,()0,()0,()( 3 ),3(),3()1,3()1,3()0,3()0,3()3( 2 ),2(),2()1,2()1,2()0,2()0,2()2( 1 ),1(),1()1,1()1,1()0,1()0,1()1( 0 ),0(),0()1,0()1,0()0,0()0,0()0( 33 22 11 00 ’ĆŁ ’ĆŁ ’ĆŁ ’ā║ ’ā║ ’ā║ ’ā║ ’ā║ ’ā║ ’ā║ ’ā║ ’ā╗ ’ā╣ ’ā¬ ’ā¬ ’ā¬ ’ā¬ ’ā¬ ’ā¬ ’ā¬ ’ā¬ ’ā½ ’ā® ’āģ’āŚ’āŚ’āŚ ’āģ’āŚ’āŚ’āŚ ’āģ’āŚ’āŚ’āŚ ’āģ’āŚ’āŚ’āŚ ’āģ’āŚ’āŚ’āŚ ’ĆĮ ),(),1(),0( ... vn i v i v i ppp ’é╣’é╣’é╣
- 19. EVHEN. A chaotic asymmetric white-box cipher Ō£ōIs named in honor of two greatest mathematicians: Evariste Galois and Jules Henri Poincare Ō£ōAllows both encryption and signing of messages with a speed of a classical block cipher Ō£ōA size of a public key: 640 Kbytes Ō£ōLight requirements: 16 xors of 16-byte values per round. Only 3 operations: memory read, xor and memory write
- 21. Links EVHEN source code: https://github.com/dmschelkunov/EVHEN AuthorŌĆÖs blog: http://dschelkunov.blogspot.com AuthorŌĆÖs e-mail: d.schelkunov@gmail.com


















![Hiding a linear relationship between
elements of the T-box
)GF(hp
)GF(b
t
valpbpbpbat
valpbpbpbat
valpbpbpbat
valpbpbpbat
valpbpbpbat
aT
uj
i
huj
i
n
i
n
kn
i
kn
i
n
i
n
i
n
i
n
i
n
i
k
i
k
iiiiii
k
i
k
iiiiii
k
i
k
iiiiii
k
i
k
iiiiii
i
nn
2overdegreewithpolinomialeirreduciblselectedrandomly
2inpolinomialselectedrandomly
nobfuscatiobeforebox-Ttheofelement
)7(
)(mod)...)(mod))(mod)(((...(
..........................................................................
)(mod)...)(mod))(mod)(((...(
)(mod)...)(mod))(mod)(((...(
)(mod)...)(mod))(mod)(((...(
)(mod)...)(mod))(mod)(((...(
]['
),(
),(
)(
),(),()1,()1,()0,()0,()(
3
),3(),3()1,3()1,3()0,3()0,3()3(
2
),2(),2()1,2()1,2()0,2()0,2()2(
1
),1(),1()1,1()1,1()0,1()0,1()1(
0
),0(),0()1,0()1,0()0,0()0,0()0(
33
22
11
00
’ĆŁ
’ĆŁ
’ĆŁ
’ā║
’ā║
’ā║
’ā║
’ā║
’ā║
’ā║
’ā║
’ā╗
’ā╣
’ā¬
’ā¬
’ā¬
’ā¬
’ā¬
’ā¬
’ā¬
’ā¬
’ā½
’ā®
’āģ’āŚ’āŚ’āŚ
’āģ’āŚ’āŚ’āŚ
’āģ’āŚ’āŚ’āŚ
’āģ’āŚ’āŚ’āŚ
’āģ’āŚ’āŚ’āŚ
’ĆĮ
),(),1(),0(
... vn
i
v
i
v
i ppp ’é╣’é╣’é╣](https://image.slidesharecdn.com/schelkunovruscrypto-2017-170412211823/85/EVHEN-Asymmetric-SPN-cipher-RusCrypto-2017-18-320.jpg)





















































![phase_4_presentation[1] - Read-Only.pptx Iot](https://cdn.slidesharecdn.com/ss_thumbnails/phase4presentation1-read-only-250301195122-ec11f187-thumbnail.jpg?width=560&fit=bounds)