ARE YOU READY FOR A CYBER EVENT - ASK YOURSELF THESE QUESTIONS.pptx
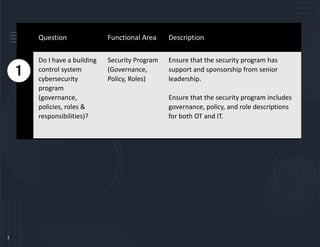
- 1. 1 Question Functional Area Description Do I have a building control system cybersecurity program (governance, policies, roles & responsibilities)? Security Program (Governance, Policy, Roles) Ensure that the security program has support and sponsorship from senior leadership. Ensure that the security program includes governance, policy, and role descriptions for both OT and IT.
- 2. 2 Question Functional Area Description Are all the devices and software that run my building(s) accounted for in an up-to-date asset inventory program? System Asset Inventory (Hardware and Software) A system asset inventory must be actively managed to keep information up to date. This applies to both hardware and software for all components in the system. The information included should be at a minimum of the following: ď‚· Manufacturer ď‚· Model name ď‚· Model number ď‚· Manufacturer support status (End of Life) ď‚· Operating system (OS)/firmware manufacturer/version ď‚· List of applications manufacturer/version ď‚· Location (building, floor, room number) ď‚· Network Address (e.g. IP)
- 3. 3 Question Functional Area Description Have I identified critical building systems and performed risk assessments? Risk Assessment with Identification of Essential Functions Documentation that shows how, when, and what was assessed. The risk assessment results must also include a risk rating that identifies critical systems and/or devices that would affect the operations of the building.
- 4. 4 Question Functional Area Description Do I have a complete, up-to-date list of each service provider that supports the systems within my buildings? Service Provider Management Provide a list of service providers. With the following information:  Service provider name  Service provider security contact  Service scope  Service provider’s responsibilities  Service provider agreements  List of authorized service provider personnel
- 5. 5 Question Functional Area Description Who controls access to my building control networks locally and remotely? System/Network Access Control (remote and local) Documents that outline how, who, and when anyone connects to the BACS system and/or network. ď‚· Account names ď‚· Account policies ď‚· Roles ď‚· Permissions ď‚· Access methods (local/remote)
- 6. 6 Question Functional Area Description Are all building control networks documented? Physical and Logical Network Architecture Drawing Actively managed drawings that include: ď‚· How the networks are interconnected ď‚· Description of systems and services on the network ď‚· Description of systems and services that connect to the network ď‚· Network management (devices, software, and services)
- 7. 7 Question Functional Area Description Are all building control systems, including the devices throughout the building, accurately and consistently backed up? System Backup/Restore BACS backup documentation identifies: ď‚· Scope (what is being backed up) ď‚· Frequency ď‚· Method ď‚· Storage (online/offline) ď‚· Location (onsite/offsite)
- 8. 8 Question Functional Area Description Do I control physical access to building systems in my facility? Physical Access Control Documented physical access control establishes guidelines for asset owner- employees and service providers. At a minimum, these guidelines identify: ď‚· Who has access to what location/area ď‚· Access methods (key checkout, card, biometric, etc.) ď‚· Enrollment Process ď‚· Restrictions
- 9. 9 Question Functional Area Description Do I control access to accounts used to login to building systems in my facility? System Account Management Processes for identifying users, adding and removing accounts, assigning permissions, and periodic review of accounts and permissions. Include any additional policies and procedures for privileged accounts (e.g., administrator accounts)
- 10. 10 Question Functional Area Description Do you know how all building systems networks are connected to each other? Network Infrastructure Management Documented network infrastructure management deals with the oversight of key OT infrastructure elements that are required to deliver building control and monitoring. These can include networking components, but the primary focus of network infrastructure management also includes physical components such as networking.
- 11. 11 Question Functional Area Description Do you have change management for building systems with the appropriate level of approval? Change Management Documentation that describes the practices designed to ensure successful prioritizing, approval, scheduling, and execution of changes to a BACS. 11
- 12. 12 Question Functional Area Description Is your As-built documentation for your building systems kept up to date? Updated As-builts System Documentation As-built system documentation must reflect the system as it is configured currently. 12
- 13. 13 Question Functional Area Description Do you periodically verify that your security measures are configured correctly and operational? System Security Verification This documentation shows that the systems have been commissioned/reviewed to ensure that cybersecurity measures have been implemented. This documentation must also show ongoing reviews to ensure that the implemented cybersecurity measures have not been altered or removed. 13
- 14. 14 Question Functional Area Description Do you have an incident response and recovery plan for your building systems that include cybersecurity incidents, and do you periodically test it? Incident Response and Recovery Incident response or what happens when an event occurs documentation must include: ď‚· Roles & responsibilities ď‚· Communication plan ď‚· Incident prevention ď‚· Monitoring ď‚· Containment of an event ď‚· Remediation processes ď‚· Recovery & restoration processes ď‚· Post-event analysis & forensics processes 14
- 15. 15 Question Functional Area Description Do you have building system security awareness and training programs that are appropriate for each role? Security Awareness and Skills Training Security awareness and training documentation must show: ď‚· Areas of focus ď‚· Expectations ď‚· Frequency ď‚· Active management to stay current on cybersecurity trends 15
- 16. 16 Question Functional Area Description Do you have a comprehensive approach to protecting data at rest or in motion? Data Protection Data protection policy and procedure documentation that includes: ď‚· Data classification ď‚· Data protection (at rest or in motion) ď‚· Data retention ď‚· Data purging 16