NoSQL - No Security? - The BSides Edition
- 1. NoSQL ©C No Security? A way to lose even more stuff Gavin Holt (@GavinHolt)
- 2. What we will cover today What is Big Data? What is NoSQL? Why NoSQL Security is an issue NoSQL Vulnerabilities Securing NoSQL Installations
- 3. What is Big Data? Datasets that are so large or complex that they are difficult to process using traditional database processing applications
- 4. 2.5 quintillion bytes (1followed by 18 zeros) Data being generated every day (IBM)
- 5. 2.5 Petabytes (1048576Gigabytes) The total size of Walmarts transaction database (The Economist)
- 6. 40 Terabytes per second Data generated by experiments on the LHC at CERN (The Economist)
- 7. 72 Hours per Minute Video uploaded to YouTube (Google Inc.)
- 8. That is a lot of data! Try running any of them in MS Access
- 9. What is NoSQL? Ī░Not Only SQLĪ▒
- 10. Umbrella Term Type of System ©C Not a Product
- 11. Not the Traditional Relational Model
- 12. Generally donĪ»t use tables
- 13. Optimised for appends and retrieves Do very little other than record storage
- 14. Highly Scalable & Very Quick This is all about speed and size
- 15. Why use NoSQL? Why the Big Data/NoSQL Hype?
- 16. Eventual Consistency Delays in writing across nodes slow down your application
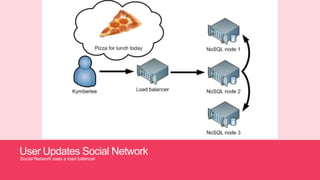
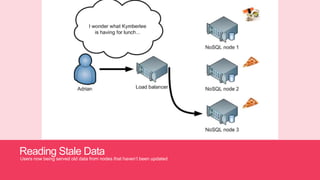
- 17. User Updates Social Network Social Network uses a load balancer
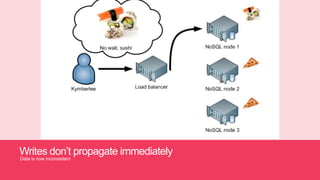
- 18. Writes donĪ»t propagate immediately Data is now inconsistent
- 19. Reading Stale Data Users now being served old data from nodes that havenĪ»t been updated
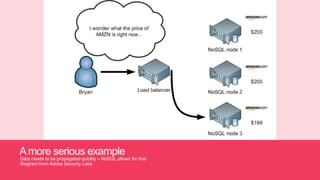
- 20. Amore serious example Data needs to be propagated quickly ©C NoSQL allows for that Diagram from Adobe Security Labs
- 21. NoSQL Vulnerabilities How do these compare to traditional databases?
- 22. The Developer By Laziness or Ignorance
- 23. Little to no Authentication Ī░Trusted EnvironmentsĪ▒
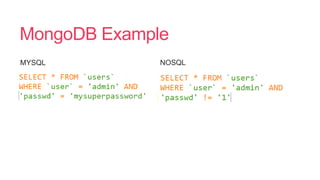
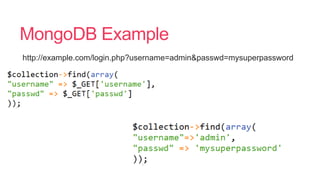
- 24. NoSQL Injection
- 25. Helpful isnĪ»t always useful Flattening associative arrays
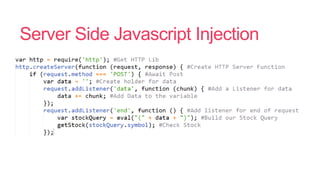
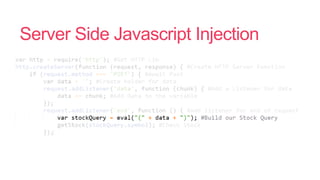
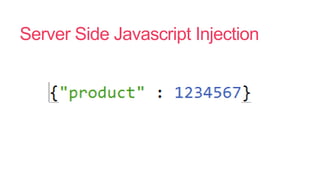
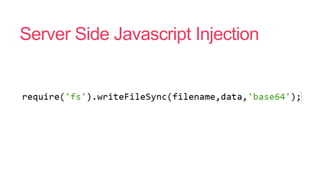
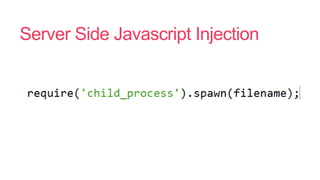
- 31. Server Side Javascript Injection
- 32. Server Side Javascript Injection
- 33. Server Side Javascript Injection
- 34. Server Side Javascript Injection
- 35. Server Side Javascript Injection
- 36. Server Side Javascript Injection
- 37. Example of an Attack
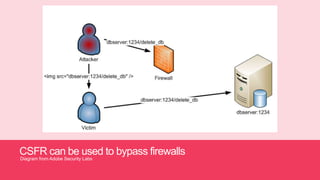
- 38. CSFR can be used to bypass firewalls Diagram from Adobe Security Labs
- 39. POST is all an Attacker needs Inserting Data Inserting Script Data Execute any REST command from inside the firewall
- 40. Securing NoSQL One does not simply secure NoSQL </meme>
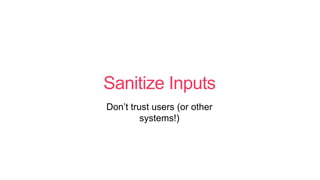
- 41. Sanitize Inputs DonĪ»t trust users (or other systems!)
- 42. Be in control of your query building DonĪ»t simply concatenate user input
- 43. Check how your solution works Read the manual
- 44. All other SQL Best Practice These arenĪ»t different attack vectors ©C just new
- 45. Questions? Twitter: @GavinHolt LinkedIn: http://uk.linkedin.com/in/gavinholt/ Email: gavin@gavin-holt.com Around all day ©C Grab me for a chat.
- 46. NoSQL ©C No Security? A way to lose even more stuff Gavin Holt (@GavinHolt)
Editor's Notes
- What is Big Data and why it is distinct from average sized DataWhat NoSQL Actually isWhy the issue of NoSQL Security should be important to DevelopersNoSQL Attack VectorsHow to secure NoSQL Deployments
- Buzzword
- Traditional Relational solutions not appropriate for this magnitude of Data
- Attacker compromised a user of the application using a CSFR, They execute the command on the DB on the Attackers behalf
- Post crap data into the databasePost Script data into the database ©C give yourself access to moreFull control, bypassing the firewall as you are using a trusted client



















![MongoDB Example
http://example.com/login.php?username=admin&passwd[$ne]=1](https://image.slidesharecdn.com/nosqlnosecurity-130427064821-phpapp02/85/NoSQL-No-Security-The-BSides-Edition-27-320.jpg)
![MongoDB Example
http://example.com/login.php?username=admin&passwd[$ne]=1](https://image.slidesharecdn.com/nosqlnosecurity-130427064821-phpapp02/85/NoSQL-No-Security-The-BSides-Edition-28-320.jpg)