PHP7.2мҷҖ лӘЁлҚҳ м•”нҳён•ҷ
2 likes1,771 views
This document discusses PHP 7.2's inclusion of the cryptography library Libsodium and the password hashing algorithm Argon2. It provides an overview of Libsodium, describing it as a high-speed cryptography library that implements modern cryptographic standards, including authenticated encryption and public-key cryptography. It then demonstrates how to use Libsodium and Argon2 in PHP 7.2 for password hashing, generic hashing, secret-key encryption, and public-key encryption.
1 of 20
Download to read offline

















Ad
Recommended
Python Cryptography & Security
Python Cryptography & SecurityJose Manuel Ortega Candel
Мэ
This document provides an overview of Python cryptography and security topics including cryptography concepts like hashing, symmetric and asymmetric encryption, digital signatures, and Python libraries for working with cryptography like PyCrypto and Cryptography. It also discusses Django security best practices like using HTTPS, securing cookies and passwords, and access control.FIPS 140-2 Validations in a Secure Enclave
FIPS 140-2 Validations in a Secure EnclavewolfSSL
Мэ
The document discusses FIPS 140-2 validations in secure enclaves, particularly focusing on the wolfSSL and wolfCrypt products within Intel SGX technology. It highlights the advantages of enclave-based validations, such as enhanced security against privileged users and confidentiality of cryptographic processes, while also addressing the challenges in implementing these validations. Additionally, it outlines the validation process and provides insights into the current state and future possibilities of these technologies.Marco Balduzzi - Cyber-crime and attacks in the dark side of the web - Codemo...
Marco Balduzzi - Cyber-crime and attacks in the dark side of the web - Codemo...Codemotion
Мэ
The document discusses the intricacies of cybercrime occurring within dark web ecosystems, specifically utilizing platforms like Tor and I2P for illegal activities. It outlines various tools and methods used by cybercriminals, including ransomware, identity theft, and affected organizations, alongside a detailed exploration of dark web traffic and its detection challenges. The research also includes insights from a simulated cybercrime operation conducted over seven months, analyzing attack strategies and the resilience of malware in these environments." Breaking Extreme Networks WingOS: How to own millions of devices running on...
" Breaking Extreme Networks WingOS: How to own millions of devices running on...PROIDEA
Мэ
The document presents an analysis of vulnerabilities in the Wingos embedded Linux OS developed by Motorola and currently owned by Extreme Networks, highlighting its use in various applications including aircraft, healthcare, and smart buildings. It discusses remote pre-authentication vulnerabilities, the presence of a hidden root shell backdoor, and the potential impact of these flaws, alongside specifics on exploit techniques. The conclusions suggest that while patches have been provided, further improvements are needed to address the numerous acknowledged issues within Wingos.My Bro The ELK
My Bro The ELKTripwire
Мэ
The document discusses using the ELK stack (Elasticsearch, Logstash, Kibana) to analyze security logs and events. It describes how to ingest logs into Logstash, normalize the data through filtering and parsing, enrich it with threat intelligence and geolocation data, and visualize the results in Kibana. The TARDIS framework is introduced as a way to perform threat analysis, detection, and data intelligence on historical security logs processed through the ELK stack.wolfSSL and TLS 1.3
wolfSSL and TLS 1.3wolfSSL
Мэ
This document summarizes a talk given by Chris Conlon from wolfSSL on September 15, 2017 in Tokyo, Japan about TLS 1.3. It provides background on Chris Conlon and his role at wolfSSL, an overview of wolfSSL's products and services including their lightweight SSL/TLS library. It also discusses the history and components of the SSL/TLS protocol, common vulnerabilities, and the goals of the new TLS 1.3 specification.Workshop on Wireless Security
Workshop on Wireless Securityamiable_indian
Мэ
The document summarizes a presentation on wireless security. It discusses wireless standards like 802.11b, 802.11a, and 802.11g and security standards like WEP, WPA, and WPA2. It describes vulnerabilities in WEP like weak IVs and keys. It also explains attacks like identity theft through MAC spoofing and defenses like strong encryption, authentication, and regular key changes. InfoSec World 2016 вҖ“ RFIDiggity вҖ“ Pentester Guide to Hacking HF/NFC and UHF...
InfoSec World 2016 вҖ“ RFIDiggity вҖ“ Pentester Guide to Hacking HF/NFC and UHF...Bishop Fox
Мэ
The document is a comprehensive guide on hacking high-frequency (HF) and ultra-high-frequency (UHF) RFID systems, presented at InfoSec World 2016 by Francis Brown of Bishop Fox. It details methodologies for badge attacks, including reading and cloning RFID badges, exploiting controllers, and maintaining unauthorized access via devices like Raspberry Pi. Additionally, it discusses various RFID hacking tools and techniques, emphasizing the importance of badge information theft and backdoor implantations.2016 TTL Security Gap Analysis with Kali Linux
2016 TTL Security Gap Analysis with Kali LinuxJason Murray
Мэ
The document outlines a gap analysis and security evaluation framework focusing on awareness, information gathering, and phases of exploitation through the lens of cybersecurity. It details steps for conducting a security gap analysis, including policy and audit processes, technical reviews, and tools such as Kali Linux for vulnerability assessment. Key considerations include management of access privileges, organization of findings, and updating risk management strategies.osint + python: extracting information from tor network and darkweb
osint + python: extracting information from tor network and darkweb Jose Manuel Ortega Candel
Мэ
The document presents an overview of using Python for Open Source Intelligence (OSINT) in conjunction with the Tor network and dark web. It covers Tor's architecture, tools, and libraries for connecting and crawling hidden services, as well as various search engines and resources for discovering dark web content. Additionally, it discusses practical applications such as IP rotation, analyzing hidden services, and automating queries through APIs.Introduction to Dynamic Malware Analysis ...Or am I "Cuckoo for Malware?"
Introduction to Dynamic Malware Analysis ...Or am I "Cuckoo for Malware?"Lane Huff
Мэ
The document presents a detailed overview of dynamic malware analysis using Cuckoo Sandbox, including its architecture, various types of analysis (dynamic and static), and countermeasures against detection. It covers the challenges in analyzing malware, such as evasion techniques used by malware authors, and provides practical insights on how to set up a malware analysis environment. Additionally, it introduces tools like vmcloak and pafish to enhance the effectiveness of malware analysis.Rafa SГЎnchez & Fran Gomez - IoCker - When IPv6 met malware [rooted2019]
Rafa SГЎnchez & Fran Gomez - IoCker - When IPv6 met malware [rooted2019]RootedCON
Мэ
This document discusses dual stack IPv4 and IPv6 threat analysis. It notes that firewalls and intrusion detection systems may not recognize IPv6 traffic and could be bypassed. It also lists security considerations like vulnerabilities in IPv6, lack of vendor support, and lack of knowledge by security teams. Unauthorized deployment of IPv6 is highlighted as a risk since most current operating systems support IPv6 by default. The document provides information on analyzing IPv6 prefixes and addresses to identify threats and indicates various categories of malware, fraud, and anonymization threats that could be investigated.Fileextraction with suricata
Fileextraction with suricataMrArora Arjuna
Мэ
This document summarizes steps for installing and configuring Suricata on Kali Linux for intrusion detection and prevention. It describes setting up Suricata with NFQUEUE to inspect network traffic, configuring rules for file extraction and storage, and various ways of writing rules to detect files based on properties like file extensions, magic bytes, and pixel dimensions. It also provides examples of rules for common file types and quizzes for writing rules to detect specific file attributes.Hacking the Gateways
Hacking the GatewaysOnur Alanbel
Мэ
This document outlines a plan to hack routers by exploiting vulnerabilities. The plan involves deciding targets, finding vulnerabilities in routers like the AirTies RT series, writing exploits in MIPS assembly to achieve remote code execution, writing scripts for mass exploitation, running attacks on targets in Turkey, and analyzing results. Routers are attractive targets because they are directly internet accessible, can control all traffic once compromised, have limited logging capabilities, and rarely receive security updates.Proofpoint Emerging Threats Suricata 5.0 Webinar
Proofpoint Emerging Threats Suricata 5.0 WebinarJason Williams
Мэ
The document outlines the evolution and current focus of Proofpoint's Emerging Threats (ET) team post-acquisition, detailing their experiences in adapting to shifting cybersecurity threats over the past four years. Key updates include the launch of the Suricata 5.0 ruleset, which features new categories and improved classifications to better address modern malware. The team highlights the importance of community feedback and encourages users to upgrade to newer Suricata versions for continued support and access to updated rules.Dario Durando - IoT: Battle of Bots [rooted2018]
Dario Durando - IoT: Battle of Bots [rooted2018]RootedCON
Мэ
The document discusses the Mirai botnet, detailing its origins, functionality, and evolving variants such as Satori/Okiru and Masuta. It also outlines the objectives and outcomes of the Kaib project which aims to identify and analyze Mirai variants while logging and blacklisting related C2 servers. The conclusions highlight the adaptability of Mirai malware and its potential for continued dominance in IoT botnets due to its modular design and effective propagation methods.Kasza smashing the_jars
Kasza smashing the_jarsPacSecJP
Мэ
The document discusses various Java-based remote access trojans (RATs) and their evolution over time. It begins with an overview of Java basics and how RATs are packaged in JAR files. It then analyzes the lineage of several RAT families like Frutas, Adwind, Unrecom, AlienSpy, jSocket, and others; how they emerged and were developed over time, sharing codebases and techniques. Common behaviors of Java RATs are also outlined, such as obfuscation, anti-analysis tricks, and persistence mechanisms. The document concludes with recommendations for analyzing and detecting Java threats.DEF CON 27 - ROGER DINGLEDINE -tor censorship arms race
DEF CON 27 - ROGER DINGLEDINE -tor censorship arms raceFelipe Prado
Мэ
- Tor is an anonymity network used by millions daily that allows censorship resistance but faces active censorship attempts from governments like China and Iran (paragraphs 1-3, 17-18)
- Tor's safety depends on diversity of relays and users, and transparency of its open source design, but governments have blocked relays, bridges, and discovery methods over time (paragraphs 14-16, 21-23, 25-34)
- Tor has developed new techniques like pluggable transports and Snowflake to evade censorship, but censors also escalate with techniques like active probing, and an ongoing arms race continues (paragraphs 35-37, 43-45, 59-60)[CB19] CIRCO: Cisco Implant Raspberry Controlled Operations by Emilio Couto
[CB19] CIRCO: Cisco Implant Raspberry Controlled Operations by Emilio CoutoCODE BLUE
Мэ
The document outlines the capabilities and features of a hacking tool called Circo, which includes various methods for exfiltrating data from networks using techniques like packet manipulation, honeypots, and credential integration. It highlights the tool's ability to mimic Cisco devices, bypass network access controls, and provides multiple exfiltration formats and flows for different protocols. The creator, Emilio, shares the tool's development progress and functionality aimed at security professionals and hackers.BalCCon2k18 - Towards the perfect cryptocurrency wallet
BalCCon2k18 - Towards the perfect cryptocurrency walletNemanja NikodijeviДҮ
Мэ
The document discusses the ideal characteristics and vulnerabilities of cryptocurrency wallets, distinguishing between full node, cold storage, and software wallets. It highlights security risks associated with various wallet types, including key extraction and hacking incidents, while advocating for hardware wallets with secure elements. The author emphasizes the necessity for improved security practices in hardware wallet design and calls for open-source projects to address these issues.DDoS Challenges in IPv6 environment
DDoS Challenges in IPv6 environmentPavel Odintsov
Мэ
This document discusses challenges and solutions related to detecting and mitigating DDoS attacks in IPv6 environments. It provides an overview of common attack vectors in IPv6, such as protocol floods, fragmentation attacks, and spoofing. It also addresses issues with using existing monitoring tools in IPv6 networks and proposes protocols like Netflow v9, IPFIX, and sFlow v5 for exporting IPv6 traffic metadata. Specific challenges involving BGP, blackholing, traffic engineering and fastnetmon tool support for IPv6 are examined along with potential solutions.RFID Hacking: Live Free or RFID Hard
RFID Hacking: Live Free or RFID HardBishop Fox
Мэ
The document is a presentation on RFID hacking, discussing the basics of RFID badges, existing hacking tools, and methods to exploit RFID systems. It includes various attack approaches, defenses against such attacks, and recommendations for improving RFID security. It emphasizes the vulnerabilities of commonly used RFID technologies and suggests implementing stronger, encrypted systems for better protection.The day I ruled the world (RootedCON 2020)
The day I ruled the world (RootedCON 2020)Javier Junquera
Мэ
The document discusses vulnerabilities in software libraries due to homograph attacks, focusing on how developers can unintentionally expose their projects to security threats via package managers like PyPI and npm. It outlines the process of uploading libraries and the potential for malicious dependencies being introduced through similar character names. The authors emphasize the lack of awareness among developers regarding these security risks and recommend measures to mitigate them, such as disabling code execution and implementing stricter upload controls.proxy2: HTTPS pins and needles
proxy2: HTTPS pins and needlesinaz2
Мэ
This document discusses techniques for intercepting and analyzing HTTPS traffic, including using a custom HTTPS proxy called Proxy2. Key points:
- Proxy2 is a Python HTTPS proxy that can trace, modify, and save HTTPS payloads without user interaction. It works by installing a private CA certificate, decrypting traffic.
- The proxy prints colored headers and POST data by default. It can change user-agents and rewrite request paths.
- While useful for developers and security, installing private CAs opens risks if they become compromised, as with preinstalled CAs like Superfish. End-to-end encryption provides better security.
- Other tools like Fiddler require user interaction, while Proxy2 allowsFastNetMon Advanced DDoS detection tool
FastNetMon Advanced DDoS detection toolPavel Odintsov
Мэ
The document outlines the history and features of the FastNetMon project, which was founded in 2013 and supports various types of volumetric attacks with quick detection capabilities. Key features include automation, integration with various traffic capture engines, and a user-friendly interface, aimed at reducing costs and downtime for businesses. FastNetMon offers unlimited scalability and compatibility with different DDoS filtering hardware and clouds, making it an effective solution for network security.Penetration Testing Boot CAMP
Penetration Testing Boot CAMPShaikh Jamal Uddin l CISM, QRadar, Hack Card Recovery Expert
Мэ
The document provides instructions on how to configure an SSH server on Linux, perform footprinting and reconnaissance, scanning tools and techniques, enumeration tools and techniques, password cracking techniques and tools, privilege escalation methods, and keylogging and hidden file techniques. It discusses active and passive footprinting, Nmap port scanning, NetBIOS and SNMP enumeration, Windows password hashes, the sticky keys method for privilege escalation, ActualSpy keylogging software, and hiding files using NTFS alternate data streams. Countermeasures for many of these techniques are also outlined.Pyongyang Fortress
Pyongyang FortressMayank Dhiman
Мэ
The document summarizes research into the Red Star OS operating system used in North Korea. Key findings include:
1) Red Star OS is based on Linux and resembles Windows XP or Mac OS X. It includes custom firewall software called Pyongyang Fortress which is derived from the open-source Snort network intrusion detection system.
2) Analysis of Pyongyang Fortress found it to be security theater with binaries that were much smaller than their open source counterparts and lacked full functionality.
3) Tests of censorship detection found that internet requests were not modified or blocked from within Red Star OS, suggesting censorship occurs at the intranet level before internet access.Kali Linux - Falconer
Kali Linux - FalconerTony Godfrey
Мэ
Tony Godfrey gave a presentation on Kali Linux at the Ohio HTCIA 2014 Spring Conference. Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It contains many security tools for information gathering, vulnerability analysis, password attacks, wireless attacks, exploitation tools, and more. The presentation demonstrated how to use various command line tools in Kali Linux like nmap, nmap, rlogin, and showed how to use Metasploit within msfconsole.The Sodium crypto library of PHP 7.2 (PHP Day 2018)
The Sodium crypto library of PHP 7.2 (PHP Day 2018)Zend by Rogue Wave Software
Мэ
The document provides an overview of the Sodium crypto library introduced in PHP 7.2, covering its features such as encryption, authentication, digital signatures, and secure password storage. It discusses cryptographic principles, potential vulnerabilities like side-channel attacks, and includes various code examples demonstrating how to implement these features in PHP. Additionally, it highlights the library's compatibility with functions and algorithms that enhance secure data handling in applications.Cryptography in PHP: Some Use Cases
Cryptography in PHP: Some Use CasesZend by Rogue Wave Software
Мэ
Enrico Zimuel's presentation covers the use of cryptography in PHP, highlighting secure password storage, pseudo-random number generation, and data encryption/decryption techniques. It emphasizes the importance of using strong algorithms like bcrypt for passwords and AES for data protection, while also mentioning the role of HMAC for authentication. The presentation concludes with recommendations for implementing cryptographic practices effectively, including the necessity of HTTPS for secure client-server communication.More Related Content
What's hot (20)
2016 TTL Security Gap Analysis with Kali Linux
2016 TTL Security Gap Analysis with Kali LinuxJason Murray
Мэ
The document outlines a gap analysis and security evaluation framework focusing on awareness, information gathering, and phases of exploitation through the lens of cybersecurity. It details steps for conducting a security gap analysis, including policy and audit processes, technical reviews, and tools such as Kali Linux for vulnerability assessment. Key considerations include management of access privileges, organization of findings, and updating risk management strategies.osint + python: extracting information from tor network and darkweb
osint + python: extracting information from tor network and darkweb Jose Manuel Ortega Candel
Мэ
The document presents an overview of using Python for Open Source Intelligence (OSINT) in conjunction with the Tor network and dark web. It covers Tor's architecture, tools, and libraries for connecting and crawling hidden services, as well as various search engines and resources for discovering dark web content. Additionally, it discusses practical applications such as IP rotation, analyzing hidden services, and automating queries through APIs.Introduction to Dynamic Malware Analysis ...Or am I "Cuckoo for Malware?"
Introduction to Dynamic Malware Analysis ...Or am I "Cuckoo for Malware?"Lane Huff
Мэ
The document presents a detailed overview of dynamic malware analysis using Cuckoo Sandbox, including its architecture, various types of analysis (dynamic and static), and countermeasures against detection. It covers the challenges in analyzing malware, such as evasion techniques used by malware authors, and provides practical insights on how to set up a malware analysis environment. Additionally, it introduces tools like vmcloak and pafish to enhance the effectiveness of malware analysis.Rafa SГЎnchez & Fran Gomez - IoCker - When IPv6 met malware [rooted2019]
Rafa SГЎnchez & Fran Gomez - IoCker - When IPv6 met malware [rooted2019]RootedCON
Мэ
This document discusses dual stack IPv4 and IPv6 threat analysis. It notes that firewalls and intrusion detection systems may not recognize IPv6 traffic and could be bypassed. It also lists security considerations like vulnerabilities in IPv6, lack of vendor support, and lack of knowledge by security teams. Unauthorized deployment of IPv6 is highlighted as a risk since most current operating systems support IPv6 by default. The document provides information on analyzing IPv6 prefixes and addresses to identify threats and indicates various categories of malware, fraud, and anonymization threats that could be investigated.Fileextraction with suricata
Fileextraction with suricataMrArora Arjuna
Мэ
This document summarizes steps for installing and configuring Suricata on Kali Linux for intrusion detection and prevention. It describes setting up Suricata with NFQUEUE to inspect network traffic, configuring rules for file extraction and storage, and various ways of writing rules to detect files based on properties like file extensions, magic bytes, and pixel dimensions. It also provides examples of rules for common file types and quizzes for writing rules to detect specific file attributes.Hacking the Gateways
Hacking the GatewaysOnur Alanbel
Мэ
This document outlines a plan to hack routers by exploiting vulnerabilities. The plan involves deciding targets, finding vulnerabilities in routers like the AirTies RT series, writing exploits in MIPS assembly to achieve remote code execution, writing scripts for mass exploitation, running attacks on targets in Turkey, and analyzing results. Routers are attractive targets because they are directly internet accessible, can control all traffic once compromised, have limited logging capabilities, and rarely receive security updates.Proofpoint Emerging Threats Suricata 5.0 Webinar
Proofpoint Emerging Threats Suricata 5.0 WebinarJason Williams
Мэ
The document outlines the evolution and current focus of Proofpoint's Emerging Threats (ET) team post-acquisition, detailing their experiences in adapting to shifting cybersecurity threats over the past four years. Key updates include the launch of the Suricata 5.0 ruleset, which features new categories and improved classifications to better address modern malware. The team highlights the importance of community feedback and encourages users to upgrade to newer Suricata versions for continued support and access to updated rules.Dario Durando - IoT: Battle of Bots [rooted2018]
Dario Durando - IoT: Battle of Bots [rooted2018]RootedCON
Мэ
The document discusses the Mirai botnet, detailing its origins, functionality, and evolving variants such as Satori/Okiru and Masuta. It also outlines the objectives and outcomes of the Kaib project which aims to identify and analyze Mirai variants while logging and blacklisting related C2 servers. The conclusions highlight the adaptability of Mirai malware and its potential for continued dominance in IoT botnets due to its modular design and effective propagation methods.Kasza smashing the_jars
Kasza smashing the_jarsPacSecJP
Мэ
The document discusses various Java-based remote access trojans (RATs) and their evolution over time. It begins with an overview of Java basics and how RATs are packaged in JAR files. It then analyzes the lineage of several RAT families like Frutas, Adwind, Unrecom, AlienSpy, jSocket, and others; how they emerged and were developed over time, sharing codebases and techniques. Common behaviors of Java RATs are also outlined, such as obfuscation, anti-analysis tricks, and persistence mechanisms. The document concludes with recommendations for analyzing and detecting Java threats.DEF CON 27 - ROGER DINGLEDINE -tor censorship arms race
DEF CON 27 - ROGER DINGLEDINE -tor censorship arms raceFelipe Prado
Мэ
- Tor is an anonymity network used by millions daily that allows censorship resistance but faces active censorship attempts from governments like China and Iran (paragraphs 1-3, 17-18)
- Tor's safety depends on diversity of relays and users, and transparency of its open source design, but governments have blocked relays, bridges, and discovery methods over time (paragraphs 14-16, 21-23, 25-34)
- Tor has developed new techniques like pluggable transports and Snowflake to evade censorship, but censors also escalate with techniques like active probing, and an ongoing arms race continues (paragraphs 35-37, 43-45, 59-60)[CB19] CIRCO: Cisco Implant Raspberry Controlled Operations by Emilio Couto
[CB19] CIRCO: Cisco Implant Raspberry Controlled Operations by Emilio CoutoCODE BLUE
Мэ
The document outlines the capabilities and features of a hacking tool called Circo, which includes various methods for exfiltrating data from networks using techniques like packet manipulation, honeypots, and credential integration. It highlights the tool's ability to mimic Cisco devices, bypass network access controls, and provides multiple exfiltration formats and flows for different protocols. The creator, Emilio, shares the tool's development progress and functionality aimed at security professionals and hackers.BalCCon2k18 - Towards the perfect cryptocurrency wallet
BalCCon2k18 - Towards the perfect cryptocurrency walletNemanja NikodijeviДҮ
Мэ
The document discusses the ideal characteristics and vulnerabilities of cryptocurrency wallets, distinguishing between full node, cold storage, and software wallets. It highlights security risks associated with various wallet types, including key extraction and hacking incidents, while advocating for hardware wallets with secure elements. The author emphasizes the necessity for improved security practices in hardware wallet design and calls for open-source projects to address these issues.DDoS Challenges in IPv6 environment
DDoS Challenges in IPv6 environmentPavel Odintsov
Мэ
This document discusses challenges and solutions related to detecting and mitigating DDoS attacks in IPv6 environments. It provides an overview of common attack vectors in IPv6, such as protocol floods, fragmentation attacks, and spoofing. It also addresses issues with using existing monitoring tools in IPv6 networks and proposes protocols like Netflow v9, IPFIX, and sFlow v5 for exporting IPv6 traffic metadata. Specific challenges involving BGP, blackholing, traffic engineering and fastnetmon tool support for IPv6 are examined along with potential solutions.RFID Hacking: Live Free or RFID Hard
RFID Hacking: Live Free or RFID HardBishop Fox
Мэ
The document is a presentation on RFID hacking, discussing the basics of RFID badges, existing hacking tools, and methods to exploit RFID systems. It includes various attack approaches, defenses against such attacks, and recommendations for improving RFID security. It emphasizes the vulnerabilities of commonly used RFID technologies and suggests implementing stronger, encrypted systems for better protection.The day I ruled the world (RootedCON 2020)
The day I ruled the world (RootedCON 2020)Javier Junquera
Мэ
The document discusses vulnerabilities in software libraries due to homograph attacks, focusing on how developers can unintentionally expose their projects to security threats via package managers like PyPI and npm. It outlines the process of uploading libraries and the potential for malicious dependencies being introduced through similar character names. The authors emphasize the lack of awareness among developers regarding these security risks and recommend measures to mitigate them, such as disabling code execution and implementing stricter upload controls.proxy2: HTTPS pins and needles
proxy2: HTTPS pins and needlesinaz2
Мэ
This document discusses techniques for intercepting and analyzing HTTPS traffic, including using a custom HTTPS proxy called Proxy2. Key points:
- Proxy2 is a Python HTTPS proxy that can trace, modify, and save HTTPS payloads without user interaction. It works by installing a private CA certificate, decrypting traffic.
- The proxy prints colored headers and POST data by default. It can change user-agents and rewrite request paths.
- While useful for developers and security, installing private CAs opens risks if they become compromised, as with preinstalled CAs like Superfish. End-to-end encryption provides better security.
- Other tools like Fiddler require user interaction, while Proxy2 allowsFastNetMon Advanced DDoS detection tool
FastNetMon Advanced DDoS detection toolPavel Odintsov
Мэ
The document outlines the history and features of the FastNetMon project, which was founded in 2013 and supports various types of volumetric attacks with quick detection capabilities. Key features include automation, integration with various traffic capture engines, and a user-friendly interface, aimed at reducing costs and downtime for businesses. FastNetMon offers unlimited scalability and compatibility with different DDoS filtering hardware and clouds, making it an effective solution for network security.Penetration Testing Boot CAMP
Penetration Testing Boot CAMPShaikh Jamal Uddin l CISM, QRadar, Hack Card Recovery Expert
Мэ
The document provides instructions on how to configure an SSH server on Linux, perform footprinting and reconnaissance, scanning tools and techniques, enumeration tools and techniques, password cracking techniques and tools, privilege escalation methods, and keylogging and hidden file techniques. It discusses active and passive footprinting, Nmap port scanning, NetBIOS and SNMP enumeration, Windows password hashes, the sticky keys method for privilege escalation, ActualSpy keylogging software, and hiding files using NTFS alternate data streams. Countermeasures for many of these techniques are also outlined.Pyongyang Fortress
Pyongyang FortressMayank Dhiman
Мэ
The document summarizes research into the Red Star OS operating system used in North Korea. Key findings include:
1) Red Star OS is based on Linux and resembles Windows XP or Mac OS X. It includes custom firewall software called Pyongyang Fortress which is derived from the open-source Snort network intrusion detection system.
2) Analysis of Pyongyang Fortress found it to be security theater with binaries that were much smaller than their open source counterparts and lacked full functionality.
3) Tests of censorship detection found that internet requests were not modified or blocked from within Red Star OS, suggesting censorship occurs at the intranet level before internet access.Kali Linux - Falconer
Kali Linux - FalconerTony Godfrey
Мэ
Tony Godfrey gave a presentation on Kali Linux at the Ohio HTCIA 2014 Spring Conference. Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It contains many security tools for information gathering, vulnerability analysis, password attacks, wireless attacks, exploitation tools, and more. The presentation demonstrated how to use various command line tools in Kali Linux like nmap, nmap, rlogin, and showed how to use Metasploit within msfconsole.Similar to PHP7.2мҷҖ лӘЁлҚҳ м•”нҳён•ҷ (9)
The Sodium crypto library of PHP 7.2 (PHP Day 2018)
The Sodium crypto library of PHP 7.2 (PHP Day 2018)Zend by Rogue Wave Software
Мэ
The document provides an overview of the Sodium crypto library introduced in PHP 7.2, covering its features such as encryption, authentication, digital signatures, and secure password storage. It discusses cryptographic principles, potential vulnerabilities like side-channel attacks, and includes various code examples demonstrating how to implement these features in PHP. Additionally, it highlights the library's compatibility with functions and algorithms that enhance secure data handling in applications.Cryptography in PHP: Some Use Cases
Cryptography in PHP: Some Use CasesZend by Rogue Wave Software
Мэ
Enrico Zimuel's presentation covers the use of cryptography in PHP, highlighting secure password storage, pseudo-random number generation, and data encryption/decryption techniques. It emphasizes the importance of using strong algorithms like bcrypt for passwords and AES for data protection, while also mentioning the role of HMAC for authentication. The presentation concludes with recommendations for implementing cryptographic practices effectively, including the necessity of HTTPS for secure client-server communication.Password Storage and Attacking in PHP
Password Storage and Attacking in PHPAnthony Ferrara
Мэ
The document discusses various methods of password storage and the vulnerabilities associated with each, highlighting the inadequacies of plain-text storage and MD5 hashing. It introduces enhanced techniques like salted MD5, iterated MD5, PBKDF2, and bcrypt, along with their respective resilience against brute-force attacks. It also touches on future advancements in password hashing strategies and the importance of ongoing community efforts in this field.Password Storage And Attacking In PHP - PHP Argentina
Password Storage And Attacking In PHP - PHP ArgentinaAnthony Ferrara
Мэ
The document discusses various methods and strategies for password storage and attack prevention in PHP, emphasizing the vulnerabilities of plain-text and hash storage systems. It highlights the use of salting and various hash functions like MD5, PBKDF2, and bcrypt to improve security, as well as the limitations and effectiveness of brute-force attacks against these methods. Additionally, it introduces advanced concepts such as scrypt and the importance of using strong, random passwords and password managers.Cryptography with Zend Framework
Cryptography with Zend FrameworkEnrico Zimuel
Мэ
Zend\Crypt is a new component in Zend Framework 2 that facilitates cryptography in PHP projects. It supports symmetric and asymmetric encryption, hashing, key derivation functions, and other cryptographic algorithms. Some features include AES encryption, RSA and Diffie-Hellman for public key cryptography, bcrypt for secure password hashing, and PBKDF2 for password-based key derivation. The component provides classes for different algorithms and use cases like encryption, signatures, and password storage.Strong cryptography in PHP
Strong cryptography in PHPEnrico Zimuel
Мэ
The document discusses strong cryptography in PHP, highlighting its importance in secure data handling and various algorithms such as AES and RSA. It emphasizes that strong cryptography involves more than encryption, including hashing and secure password storage practices. Additionally, it outlines best practices, key generation techniques, and the use of libraries like OpenSSL and mcrypt in PHP applications.Cryptography For The Average Developer
Cryptography For The Average DeveloperAnthony Ferrara
Мэ
This document provides an overview of cryptography concepts for PHP developers. It discusses keeping data secure from viewing, tampering and forgery through encryption but notes cryptography is not a silver bullet and vulnerabilities still exist. The document covers random number generation, symmetric and asymmetric encryption, hashing, common ciphers and modes, and securely storing passwords through hashing rather than encryption. It strongly recommends using existing libraries rather than implementing cryptography directly due to the complexity and risk of bugs.Cryptography For The Average Developer - Sunshine PHP
Cryptography For The Average Developer - Sunshine PHPAnthony Ferrara
Мэ
This document provides an overview of cryptography concepts for PHP developers. It discusses keeping data secure from viewing, tampering and forgery without cryptography being a "silver bullet" solution. The document covers random number generation, symmetric and asymmetric encryption, hashing, common ciphers and modes, authentication, and password storage best practices like hashing passwords instead of encrypting them. The key messages are that cryptography is very difficult to implement securely and developers should rely on expert libraries or hire an expert instead of rolling their own solutions.php[tek] 2108 - Cryptography Advances in PHP 7.2
php[tek] 2108 - Cryptography Advances in PHP 7.2Adam Englander
Мэ
The document summarizes advances in cryptography introduced in PHP 7.2, highlighting significant changes such as the deprecation of SSL in favor of TLS and the introduction of the sodium library for secure cryptographic operations. It discusses new features like strong authentication methods, modern encryption algorithms, and simple interfaces for implementing security practices. Additionally, it provides examples of key generation, encryption, and hashing functions using the sodium library.Ad
Recently uploaded (20)
Introduction to Python Programming Language
Introduction to Python Programming Languagemerlinjohnsy
Мэ
This PPT covers features, applications, variable, data types and statements in PythonAbraham Silberschatz-Operating System Concepts (9th,2012.12).pdf
Abraham Silberschatz-Operating System Concepts (9th,2012.12).pdfShabista Imam
Мэ
Complete book of operating system edition 9FUNDAMENTALS OF COMPUTER ORGANIZATION AND ARCHITECTURE
FUNDAMENTALS OF COMPUTER ORGANIZATION AND ARCHITECTUREShabista Imam
Мэ
FUNDAMENTALS OF COMPUTER ORGANIZATION AND ARCHITECTURE
By : Mostafa Abd-El-Barr & Hesham El-Rewini:: wiley
A complete guidance bookIntroduction to Natural Language Processing - Stages in NLP Pipeline, Challen...
Introduction to Natural Language Processing - Stages in NLP Pipeline, Challen...resming1
Мэ
Lecture delivered in 2021. This gives an introduction to Natural Language Processing. It describes the use cases of NLP in daily life. It discusses the stages in NLP Pipeline. It highlights the challenges involved covering the different levels of ambiguity that could arise. It also gives a brief note on the present scenario with the latest language models, tools and frameworks/libraries for NLP.Tesla-Stock-Analysis-and-Forecast.pptx (1).pptx
Tesla-Stock-Analysis-and-Forecast.pptx (1).pptxmoonsony54
Мэ
this is data science ppt for tesla stock (linear regression)Tally.ERP 9 at a Glance.book - Tally Solutions .pdf
Tally.ERP 9 at a Glance.book - Tally Solutions .pdfShabista Imam
Мэ
Tally.ERP 9 at a Glance.book, a fully completed guidance to learn tally erp 9.0Rapid Prototyping for XR: Lecture 1 Introduction to Prototyping
Rapid Prototyping for XR: Lecture 1 Introduction to PrototypingMark Billinghurst
Мэ
Lecture 1 of a course on Rapid Prototyping for XR taught by Mark Billinghurst at Oulu University on June 9th, 2025. This lecture presents an Introduction to Prototyping. Machine Learning - Classification Algorithms
Machine Learning - Classification Algorithmsresming1
Мэ
This covers traditional machine learning algorithms for classification. It includes Support vector machines, decision trees, Naive Bayes classifier , neural networks, etc.
It also discusses about model evaluation and selection. It discusses ID3 and C4.5 algorithms. It also describes k-nearest neighbor classifer.Call For Papers - 17th International Conference on Wireless & Mobile Networks...
Call For Papers - 17th International Conference on Wireless & Mobile Networks...hosseinihamid192023
Мэ
17th International Conference on Wireless & Mobile Networks (WiMoNe 2025) will provide
an excellent international forum for sharing knowledge and results in theory, methodology and
applications of Wireless & Mobile computing Environment. Current information age is witnessing
a dramatic use of digital and electronic devices in the workplace and beyond. Wireless, Mobile
Networks & its applications had received a significant and sustained research interest in terms of
designing and deploying large scale and high performance computational applications in real life.
The aim of the conference is to provide a platform to the researchers and practitioners from both
academia as well as industry to meet and share cutting-edge development in the field.May 2025: Top 10 Read Articles in Data Mining & Knowledge Management Process
May 2025: Top 10 Read Articles in Data Mining & Knowledge Management ProcessIJDKP
Мэ
Data mining and knowledge discovery in databases have been attracting a significant amount of research, industry, and media attention of late. There is an urgent need for a new generation of computational theories and tools to assist researchers in extracting useful information from the rapidly growing volumes of digital data.
This Journal provides a forum for researchers who address this issue and to present their work in a peer-reviewed open access forum. Authors are solicited to contribute to the Journal by submitting articles that illustrate research results, projects, surveying works and industrial experiences that describe significant advances in the following areas, but are not limited to these topics only.Proposal for folders structure division in projects.pdf
Proposal for folders structure division in projects.pdfMohamed Ahmed
Мэ
Proposal for folders structure division in projectsGenerative AI & Scientific Research : Catalyst for Innovation, Ethics & Impact
Generative AI & Scientific Research : Catalyst for Innovation, Ethics & ImpactAlqualsaDIResearchGr
Мэ
Invited keynote at the Artificial Intelligence Symposium on AI-powered Research Innovation, taking place at ENSEM (L'Гүcole Nationale SupГ©rieure d'ГүlectricitГ© et de MГ©canique), Casablanca on June 21, 2025. IвҖҷll be giving a keynote titled: "Generative AI & Scientific Research: Catalyst for Innovation, Ethics & Impact". Looking forward to engaging with researchers and doctoral students on how Generative AI is reshaping the future of science, from discovery to governance вҖ” with both opportunities and responsibilities in focus.
#AI hashtag#GenerativeAI #ScientificResearch #Innovation #Ethics #Keynote #AIinScience #GAI #ResearchInnovation #Casablanca
1. Thinking, Creative Thinking, Innovation
2. Societies Evolution from 1.0 to 5.0
3. AI - 3P Approach, Use Cases & Innovation
4. GAI & Creativity
5. TrustWorthy AI
6. Guidelines on The Responsible use of GAI In ResearchStructured Programming with C++ :: Kjell Backman
Structured Programming with C++ :: Kjell BackmanShabista Imam
Мэ
Step into the world of high-performance programming with the Complete Guidance Book of C++ ProgrammingвҖ”a definitive resource for mastering one of the most powerful and versatile languages in computer science.
Whether you're a beginner looking to learn the fundamentals or an intermediate developer aiming to sharpen your skills, this book walks you through C++ from the ground up. You'll start with basics like variables, control structures, and functions, then progress to object-oriented programming (OOP), memory management, file handling, templates, and the Standard Template Library (STL).Deep Learning for Natural Language Processing_FDP on 16 June 2025 MITS.pptx
Deep Learning for Natural Language Processing_FDP on 16 June 2025 MITS.pptxresming1
Мэ
This gives an introduction to how NLP has evolved from the time of World War II till this date through the advances in approaches, architectures and word representations. From rule based approaches, it advanced to statistical approaches. from traditional machine learning algorithms it advanced to deep neural network architectures. Deep neural architectures include recurrent neural networks, long short term memory, gated recurrent units, seq2seq models, encoder decoder models, transformer architecture, upto large language models and vision language models which are multimodal in nature.Call For Papers - 17th International Conference on Wireless & Mobile Networks...
Call For Papers - 17th International Conference on Wireless & Mobile Networks...hosseinihamid192023
Мэ
Generative AI & Scientific Research : Catalyst for Innovation, Ethics & Impact
Generative AI & Scientific Research : Catalyst for Innovation, Ethics & ImpactAlqualsaDIResearchGr
Мэ
Ad
PHP7.2мҷҖ лӘЁлҚҳ м•”нҳён•ҷ
- 3. ? ?
- 4. Side Channel Attack вҖў , ( ) ? вҖў , , , , , , ? вҖў вҖЁ Meltdown, Spectre вҖў Large Prime Number
- 5. Elliptic Curve Cryptography вҖў вҖў RSA 3072bit = ECC 256bit вҖў key вҖў вҖў Side Channel Attack
- 6. Authenticated Encryption вҖў Message Authentication Code вҖў вҖў (nonce) вҖў
- 8. PHP 7.2 ? Libsodium & Argon2
- 9. Libsodium вҖў NaCl(salt) (2008-2010) вҖў Networking and cryptography library, high-speed software library for network communication, encryption, decryption, signature, etc. вҖў US EU Funding вҖў C(with inline assembler), C++, Python Wrapper вҖў Libsodium NaCl Cross-Platform (2013) вҖў вҖў 2017 PHP7.2
- 10. Argon2 вҖў Side Channel Attack Hash Algorithm вҖў 2015 вҖў password_hash Libsodium , Libsodium password_hash BCRYPT . ( 7.2 ) вҖў password_hash Libsodium вҖў Libsodium вҖў hash
- 11. Argon2 $password = 'secret password'; $hash = password_hash($password, PASSWORD_ARGON2I); echo $hash . PHP_EOL; if (password_verify($password, $hash)) { echo 'valid password' . PHP_EOL; if(password_needs_rehash($hash, PASSWORD_ARGON2I)) { echo 'save new password hash' . PHP_EOL; } } else { echo 'invalid password!' . PHP_EOL; } $argon2i$v=19$m=1024,t=2,p=2$RWRRb01PMnRETU8zMXNrag$/ BKnBpq0Yl82OsimPaNn/SlnAuaGsYWi3H95bfZKFSc valid password
- 12. Argon2 $password = 'secret password'; $hash = sodium_crypto_pwhash_str( $password, SODIUM_CRYPTO_PWHASH_OPSLIMIT_INTERACTIVE, SODIUM_CRYPTO_PWHASH_MEMLIMIT_INTERACTIVE ); echo $hash . PHP_EOL; if (sodium_crypto_pwhash_str_verify($hash, $password)) { sodium_memzero($password); echo 'valid password' . PHP_EOL; if (sodium_crypto_pwhash_str_needs_rehash($hash, SODIUM_CRYPTO_PWHASH_OPSLIMIT_INTERACTIVE, SODIUM_CRYPTO_PWHASH_MEMLIMIT_INTERACTIVE)) { echo 'save new password hash' . PHP_EOL; } } else { sodium_memzero($password); echo 'invalid password!' . PHP_EOL; } $argon2id$v=19$m=65536,t=2,p=1$zYnVgQGMf+YpTKZzTvqv2g$XHM3XJpOOgeQvibBX9fY4OB 6CA06aJVcsF+DmMFOMtc valid password
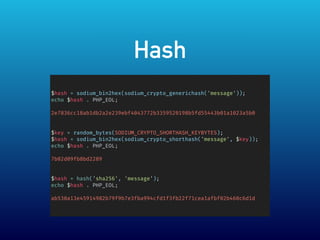
- 13. Hash вҖў Rainbow table , Collision Attack вҖў Libsodium generic hash BLAKE2b вҖў short hash SipHash-2-4 вҖў Libsodium вҖў PHP hash MD5 SHA-1 . SHA-256 SHA-512
- 14. Hash $hash = sodium_bin2hex(sodium_crypto_generichash('message')); echo $hash . PHP_EOL; 2e7836cc18ab1db2a2e239ebf4043772b3359520198b5fd55443b01a1023a5b0 $key = random_bytes(SODIUM_CRYPTO_SHORTHASH_KEYBYTES); $hash = sodium_bin2hex(sodium_crypto_shorthash('message', $key)); echo $hash . PHP_EOL; 7b02d09fb8bd2289 $hash = hash('sha256', 'message'); echo $hash . PHP_EOL; ab530a13e45914982b79f9b7e3fba994cfd1f3fb22f71cea1afbf02b460c6d1d
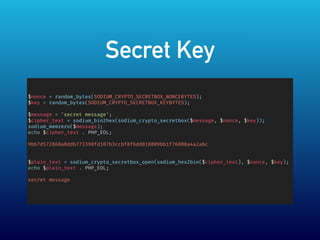
- 15. Secret Key вҖў XSalsa20 вҖў Poly1305 MAC вҖў nonce вҖў AEAD AEAD . ( ..)
- 16. Secret Key $nonce = random_bytes(SODIUM_CRYPTO_SECRETBOX_NONCEBYTES); $key = random_bytes(SODIUM_CRYPTO_SECRETBOX_KEYBYTES); $message = 'secret message'; $cipher_text = sodium_bin2hex(sodium_crypto_secretbox($message, $nonce, $key)); sodium_memzero($message); echo $cipher_text . PHP_EOL; 9bb7d572868a8ddb773398fd107b3ccbf8f6dd010809bb1f76008a4a2abc $plain_text = sodium_crypto_secretbox_open(sodium_hex2bin($cipher_text), $nonce, $key); echo $plain_text . PHP_EOL; secret message
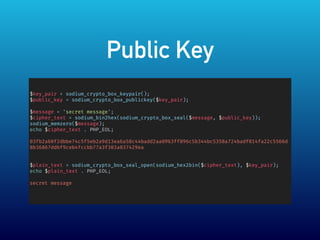
- 17. Public Key вҖў X25519 XSalsa20 вҖў Poly1305 MAC
- 18. Public Key $key_pair = sodium_crypto_box_keypair(); $public_key = sodium_crypto_box_publickey($key_pair); $message = 'secret message'; $cipher_text = sodium_bin2hex(sodium_crypto_box_seal($message, $public_key)); sodium_memzero($message); echo $cipher_text . PHP_EOL; 03fb2a60f2dbbe74c5f5eb2a9d13ea6a58c44badd2aa0963ff096c5b344bc5358a724badf814fa22c5566d 8b36867ddbf9ceb4fccbb77a3f303a037429ea $plain_text = sodium_crypto_box_seal_open(sodium_hex2bin($cipher_text), $key_pair); echo $plain_text . PHP_EOL; secret message
- 19. Libsodium 7.1
- 20. Reference вҖў Official siteвҖЁ https://www.gitbook.com/book/jedisct1/ libsodium/details вҖў Paragon IEвҖЁ https://paragonie.com/book/pecl- libsodium
