Tbhf
- 1. ŌĆ£THRESHOLD BASED KERNEL LEVEL HTTP FILTER (TBHF)ŌĆØ for DDoS Mitigation by MOHAMED IBRAHIM AK 82008132041 LIJO GEORGE 82008132515 Dept. of CSE TEC, Trichy INTERNEL GUIDE EXTERNAL GUIDE Mr. A. NARENTHIRA KUMAR Dr. S. SELVAKUMAR Asst. Professor Professor Dept. of CSE Dept. of CSE TEC, Trichy NIT, Trichy
- 2. OUTLINE ’éŚ Abstract ’éŚ Insight into DDoS attack ’éŚ Existing and Proposed system ’éŚ Algorithm ’éŚ Modules ’éŚ TBHF Driver ’éŚ Technology ’éŚ Conclusion ’éŚ References ║▌║▌▀Ż 2 Dept. of CSE, TEC. 3 April 2012
- 3. Abstract ’éŚ Application layer attack ’éŚ Client Side Scripting ’éŚ High rate flooding attack ’éŚ No manifestation ’éŚ Data on the flow analysis ’éŚ Threshold based Decision Support System ’éŚ Vulnerability Status: Effective ŌĆō Real time ║▌║▌▀Ż 3 Dept. of CSE, TEC. 3 April 2012
- 4. OUTLINE ’éŚ Abstract ’éŚ Insight into DDoS attack ’éŚ Existing and Proposed system ’éŚ Algorithm ’éŚ Modules ’éŚ TBHF Driver ’éŚ Technology ’éŚ Conclusion ’éŚ References Dept. of CSE, TEC. 3 April 2012
- 5. DDoS attack - Actors ’éŚ Individuals ’āś Julian Assange - Wikileaks ’éŚ Blackhat underground community ’āś ŌĆśAnonymousŌĆÖ, ŌĆśLords of DharmarajaŌĆÖ ’éŚ Government sponsored ’āś China - GhostNet ’āś Israel - Stuxnet ║▌║▌▀Ż 4 Dept. of CSE, TEC. 3 April 2012
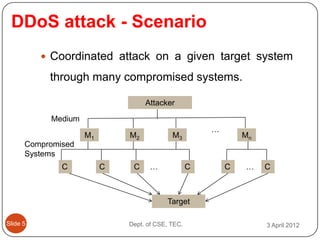
- 6. DDoS attack - Scenario ’éŚ Coordinated attack on a given target system through many compromised systems. Attacker Medium ŌĆ” M1 M2 M3 Mn Compromised Systems C C C ŌĆ” C C ŌĆ” C Target ║▌║▌▀Ż 5 Dept. of CSE, TEC. 3 April 2012
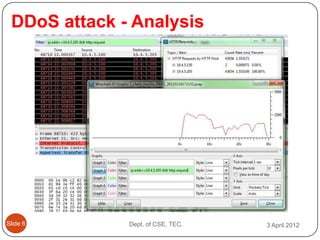
- 7. DDoS attack - Analysis ║▌║▌▀Ż 6 Dept. of CSE, TEC. 3 April 2012
- 8. DDoS attack - Timeline ’éŚ July 2011 ’āś Live Journal Hit by Massive Cyber Attack ’éŚ March 2011 (Korean Websites) ’āś 40 websites under DDoS attack ’éŚ February 2011 (Total Choice Hosting Network) ’āś 7,00,000 packets per second ’āś 600 Mbps ’éŚ January 2011 ’āś FBI executed 40 search warrants for DDoS attacks ’é¦ Low Orbit Ion Cannon tool ║▌║▌▀Ż 7 Dept. of CSE, TEC. 3 April 2012
- 9. OUTLINE ’éŚ Abstract ’éŚ Insight into DDoS attack ’éŚ Existing and Proposed system ’éŚ Algorithm ’éŚ Modules ’éŚ TBHF Driver ’éŚ Technology ’éŚ Conclusion ’éŚ References Dept. of CSE, TEC. 3 April 2012
- 10. Existing System ’éŚ Predominately in Server side ’éŚ Page access behaviour ’éŚ Captcha ’éŚ Black list ’éŚ Signature based detection ║▌║▌▀Ż 8 Dept. of CSE, TEC. 3 April 2012
- 11. Proposed System ’éŚ Client side ’éŚ Threshold based ’éŚ Real time ’āś Monitoring ’āś Detection ’āś Prevention ’éŚ Detects zero-day vulnerability ║▌║▌▀Ż 9 Dept. of CSE, TEC. 3 April 2012
- 12. OUTLINE ’éŚ Abstract ’éŚ Insight into DDoS attack ’éŚ Existing and Proposed system ’éŚ Algorithm ’éŚ Modules ’éŚ TBHF Driver ’éŚ Technology ’éŚ Conclusion ’éŚ References Dept. of CSE, TEC. 3 April 2012
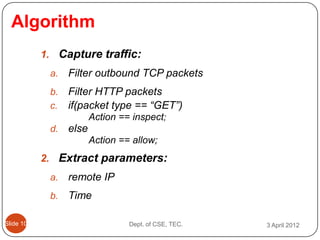
- 13. Algorithm 1. Capture traffic: a. Filter outbound TCP packets b. Filter HTTP packets c. if(packet type == ŌĆ£GETŌĆØ) Action == inspect; d. else Action == allow; 2. Extract parameters: a. remote IP b. Time ║▌║▌▀Ż 10 Dept. of CSE, TEC. 3 April 2012
- 14. Algorithm ContdŌĆ” //r.addr1, r.addr2, ŌĆ”, r.addri -> remote IP //T1, T2, ŌĆ”, Ti -> packet time // Ōłåt -> Time stamp 3. Inspect: a. If(r. addri not in array) addr[i] = r.addri; t[i] = Ti; b. else if (r. addri in array && (T(i+1) ŌĆō Ti)<=Ōłåt) r.count[i]++; c. Else Reset r.count[]; ║▌║▌▀Ż 11 Dept. of CSE, TEC. 3 April 2012
- 15. Algorithm ContdŌĆ” //N -> Threshold value 4. Decision Making: a. If(r.count[i] >= N) Action = allow packet; b. else Action = drop packet; ║▌║▌▀Ż 12 Dept. of CSE, TEC. 3 April 2012
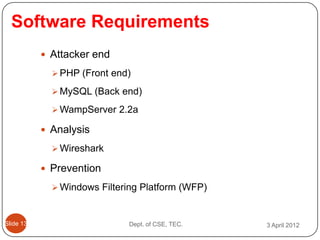
- 16. Software Requirements ’éŚ Attacker end ’āś PHP (Front end) ’āś MySQL (Back end) ’āś WampServer 2.2a ’éŚ Analysis ’āś Wireshark ’éŚ Prevention ’āś Windows Filtering Platform (WFP) ║▌║▌▀Ż 13 Dept. of CSE, TEC. 3 April 2012
- 17. OUTLINE ’éŚ Abstract ’éŚ Insight into DDoS attack ’éŚ Existing and Proposed system ’éŚ Algorithm ’éŚ Modules ’éŚ TBHF Driver ’éŚ Technology ’éŚ Conclusion ’éŚ References Dept. of CSE, TEC. 3 April 2012
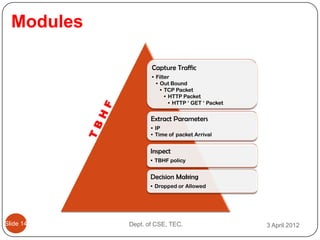
- 18. Modules Capture Traffic ŌĆó Filter ŌĆó Out Bound ŌĆó TCP Packet ŌĆó HTTP Packet ŌĆó HTTP ŌĆś GET ŌĆś Packet Extract Parameters ŌĆó IP ŌĆó Time of packet Arrival Inspect ŌĆó TBHF policy Decision Making ŌĆó Dropped or Allowed ║▌║▌▀Ż 14 Dept. of CSE, TEC. 3 April 2012
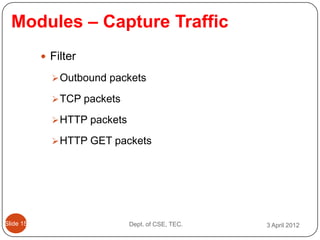
- 19. Modules ŌĆō Capture Traffic ’éŚ Filter ’āś Outbound packets ’āś TCP packets ’āś HTTP packets ’āś HTTP GET packets ║▌║▌▀Ż 15 Dept. of CSE, TEC. 3 April 2012
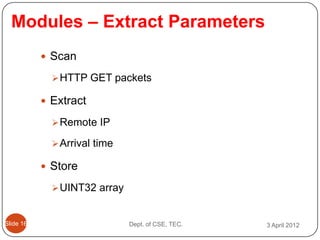
- 20. Modules ŌĆō Extract Parameters ’éŚ Scan ’āś HTTP GET packets ’éŚ Extract ’āś Remote IP ’āś Arrival time ’éŚ Store ’āś UINT32 array ║▌║▌▀Ż 16 Dept. of CSE, TEC. 3 April 2012
- 21. Modules ŌĆō Inspect, Decision Making ’éŚ Inspect ’āś Time stamp ’āś Remote IP ’āś IP count ’éŚ Decision Making ’āś Threshold ║▌║▌▀Ż 17 Dept. of CSE, TEC. 3 April 2012
- 22. OUTLINE ’éŚ Abstract ’éŚ Insight into DDoS attack ’éŚ Existing and Proposed system ’éŚ Algorithm ’éŚ Modules ’éŚ TBHF Driver ’éŚ Technology ’éŚ Conclusion ’éŚ References Dept. of CSE, TEC. 3 April 2012
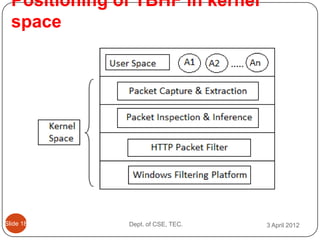
- 23. Positioning of TBHF in kernel space ║▌║▌▀Ż 18 Dept. of CSE, TEC. 3 April 2012
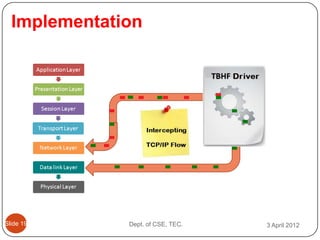
- 24. Implementation ║▌║▌▀Ż 19 Dept. of CSE, TEC. 3 April 2012
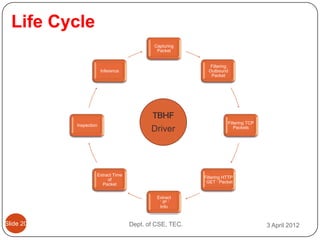
- 25. Life Cycle Capturing Packet Filtering Inference Outbound Packet TBHF Filtering TCP Inspection Driver Packets Extract Time Filtering HTTP of ŌĆś GET ŌĆś Packet Packet Extract ŌĆś IP ŌĆś Info ║▌║▌▀Ż 20 Dept. of CSE, TEC. 3 April 2012
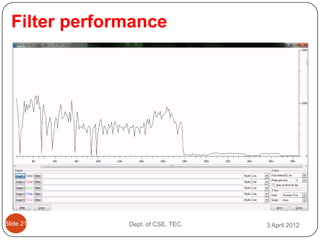
- 26. Filter performance ║▌║▌▀Ż 21 Dept. of CSE, TEC. 3 April 2012
- 27. OUTLINE ’éŚ Abstract ’éŚ Insight into DDoS attack ’éŚ Existing and Proposed system ’éŚ Algorithm ’éŚ Modules ’éŚ TBHF Driver ’éŚ Technology ’éŚ Conclusion ’éŚ References Dept. of CSE, TEC. 3 April 2012
- 28. Technology ’éŚ Windows Filtering Platform (WFP) ’āś Supports from Longhorn ’āś Manipulate packet at OSI layers ║▌║▌▀Ż 22 Dept. of CSE, TEC. 3 April 2012
- 29. Conclusion ’éŚ Deployed in kernel level ’éŚ Priority to overwrite packets ’éŚ Real time prevention ’éŚ DDoS participation is prevented ’éŚ Future Enhancement ’āś Mobile platforms ║▌║▌▀Ż 23 Dept. of CSE, TEC. 3 April 2012
- 30. References ’éŚ Ying Xuan, Incheol Shin, My T. Thai, and Taieb Znati, ŌĆ£Detecting Application Denial-of-Service Attacks: A Group-Testing-Based ApproachŌĆØ IEEE Transactions on Parallel and Distributed Systems, Vol. 21, No. 8, pp. 1203-1216, August 2010. ’éŚ Takeshi Yatagai, Takamasa Isohara, and Iwao Sasase, ŌĆ£Detection of HTTP-GET flood Attack Based on Analysis of Page Access BehaviourŌĆØ, IEEE Conference on Communications, Computers and Signal Processing, August 2007 ’éŚ http://msdn.microsoft.com/en- us/library/windows/desktop/aa366510%28v=vs.85 %29.aspx ║▌║▌▀Ż 24 Dept. of CSE, TEC. 3 April 2012
- 31. Thank You!!! Dept. of CSE, TEC. 3 April 2012








![Algorithm ContdŌĆ”
//r.addr1, r.addr2, ŌĆ”, r.addri -> remote IP
//T1, T2, ŌĆ”, Ti -> packet time
// Ōłåt -> Time stamp
3. Inspect:
a. If(r. addri not in array)
addr[i] = r.addri;
t[i] = Ti;
b. else if (r. addri in array && (T(i+1) ŌĆō Ti)<=Ōłåt)
r.count[i]++;
c. Else
Reset r.count[];
║▌║▌▀Ż 11 Dept. of CSE, TEC. 3 April 2012](https://image.slidesharecdn.com/tbhf-13398513794974-phpapp01-120616075913-phpapp01/85/Tbhf-14-320.jpg)
![Algorithm ContdŌĆ”
//N -> Threshold value
4. Decision Making:
a. If(r.count[i] >= N)
Action = allow packet;
b. else
Action = drop packet;
║▌║▌▀Ż 12 Dept. of CSE, TEC. 3 April 2012](https://image.slidesharecdn.com/tbhf-13398513794974-phpapp01-120616075913-phpapp01/85/Tbhf-15-320.jpg)