Fun With Http Handlers - Miguel A. Castro
- 1. FUN WITH HTTP HANDLERS Miguel A. Castro [email_address]
- 2. .NET Architect, Developer, & Trainer Microsoft MVP ASP Insider Member of the INETA Speakers Bureau Conference Speaker Creator of CodeBreeze In IT business since 1986 ineta
- 3. Agenda Identifying the Problem Methods of securing Setting up a Bulletproof Technique More about Handlers Summary
- 4. Identifying The Problem Reasons: User has not purchased your product You want to track downloads (even on freeware) You want to hide file locations on your site Require the ability to prevent unauthorized downloading of files from your web site.
- 5. Common Protection Zip-file Password Protection Zip file can be spread but cannot be unlocked If password gets out, youˇŻre SOL Emails Sending user file link in an email Provide download for limited time Insufficient for client account with download list Usually accompanied by a temporary file name
- 6. Common Protection Temporary / Cryptic File Names Usually GUID-based Sometimes cryptic URLs are used, then rewritten Usually accompanied by a download time limitation
- 7. All of these are Crackable or Abusable
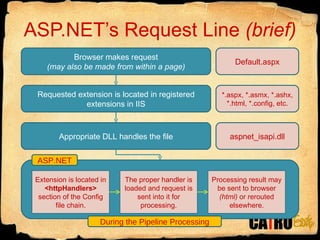
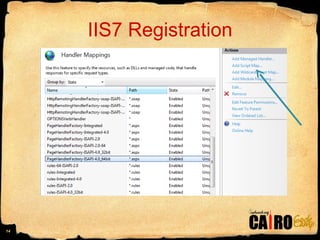
- 8. ASP.NETˇŻs Request Line (brief) Browser makes request (may also be made from within a page) Requested extension is located in registered extensions in IIS Appropriate DLL handles the file Default.aspx *.aspx, *.asmx, *.ashx, *.html, *.config, etc. aspnet_isapi.dll ASP.NET Extension is located in <httpHandlers> section of the Config file chain. The proper handler is loaded and request is sent into it for processing. Processing result may be sent to browser (html) or rerouted elsewhere. During the Pipeline Processing
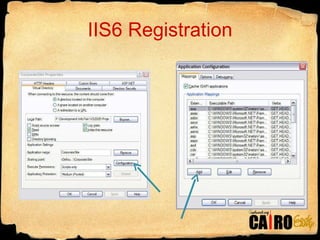
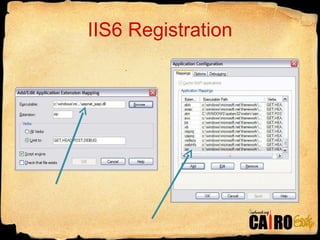
- 9. Show IIS Configuration and machine.config HTTP Handlers
- 10. Bulletproof Technique (step 1) Add ˇ°zipˇ± extension to IIS for specified application. Will cause all ˇ°zipˇ± files to be routed through standard ASP.NET channels where they can be dealt with under controlled environment.
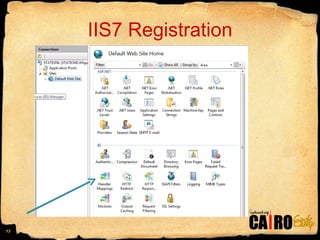
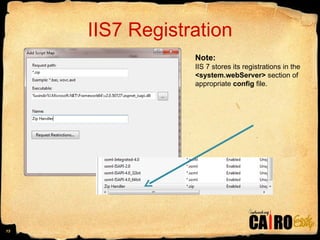
- 15. IIS7 Registration Note: IIS 7 stores its registrations in the <system.webServer> section of appropriate config file.
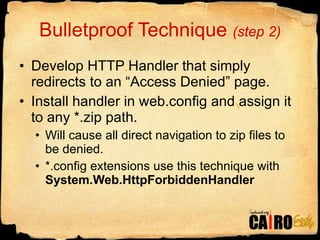
- 16. Bulletproof Technique (step 2) Develop HTTP Handler that simply redirects to an ˇ°Access Deniedˇ± page. Install handler in web.config and assign it to any *.zip path. Will cause all direct navigation to zip files to be denied. *.config extensions use this technique with System.Web.HttpForbiddenHandler
- 17. ASHX Files Navigating to an ASPX file causes the PageHandlerFactory class to invoke a ˇ°Pageˇ± handler and start the events in the page lifecycle. ASHX files are HTTP Handlers exposed as direct ASP.NET navigation points. They are intercepted by the SimpleHandlerFactory class.
- 18. Bulletproof Technique (step 3) Develop ASHX handler to be used to download files. Receive product ID in query string variable. Confirm authenticated user. Check user products for product requested. Download product by streaming the file. Cannot redirect to it because of previous security.
- 19. Other Uses For Handlers URL Rewriting A must for good search engine incorporation ASP.NET 4.0 includes routing engine Image Watermarking Intercepting all images and embedding watermark RSS Syndication ASHX useful in image paths for resource extraction
- 20. More About Handlers Handler Factories IHttpHandlerFactory interface Can serve different handlers based on conditioning. Installs in config EXACTLY the same as a handler. Asynchronous Handlers IHttpAsyncHandler interface Uses familiar Begin/End pattern for asynchronous processing.
- 21. Summary Secure technique against unauthorized file downloading. Can be combined with additional techniques. Lets you track downloads, even if theyˇŻre free. Handlers are a great tool for intercepting requests for advanced manipulation. IIS7ˇŻs a pain-in-the-butt.
- 22. Programming Microsoft ASP.NET {and} Advanced Topics Dino Esposito ¨C Microsoft Press Essential ASP.NET 2.0 Fritz Onion ¨C Addison-Wesley ASP.NET Architecture http://www.code-magazine.com/Article.aspx?quickid=0511061 Rick Strahl, et.al. ¨C CoDe Magazine
Editor's Notes
- MGB 2003 ? 2003 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary.
![FUN WITH HTTP HANDLERS Miguel A. Castro [email_address]](https://image.slidesharecdn.com/funwithhttphandlers-100323035034-phpapp02/85/Fun-With-Http-Handlers-Miguel-A-Castro-1-320.jpg)