Hacking
- 3. ’é× Hacking generally refers to act of a person abusing computer access, breaking into computers, or using computers without authorization. ’é× An intruder or attacker is a person who carries out an attack.
- 4. ’é× There are in essence two types of hackers, often referred to as 1.White-hat hackers. 2.Black-hat hackers. ’é× White hat hackers enjoy learning and working with computer systems, and consequently gains a deeper understanding of the subject. ’é× Black-hat hackers often called as ŌĆśCrackersŌĆÖ called by White-hat hackers.
- 5. ’é× Curiosity. ’é× Money. ’é× Spying. ’é× Prestige Intellectual Challenge. ’é× Anarchy.
- 6. ’é× Steal credit card numbers. ’é× Steal passwords to other systems. ’é× To steal programs or files. ’é× Read othersŌĆÖ mails.
- 7. ’é× Files disappear or are modified unexpectedly. ’é× Strange files appear or grow in size unexpectedly. ’é× Programs stop working as expected. ’é× Your internet connection slows dramatically for an extended period. ’é× The computer starts crashing frequently.
- 8. ’é× Gathering information. 1.port scanning. 2.packet sniffing. ’é× Launching attack 1.Denial of Service(DOS). 2.Password cracking. 3.Packet Sequence attacks. 4.Operating System exploits. 5.FTP(File Transfer Protocol). 6.Fore Core Dumping.
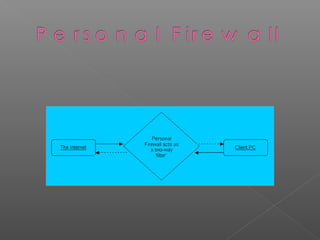
- 9. ’é× Server-side security. It is a very large and complex area. ’é× Client-side security:-This contains 3 areas 1.Anti-virus security. 2.Personal Firewall. 3.Encryption.
- 12. ’é× Encryption programs basically ŌĆśscrambleŌĆÖ the original file so that it is unreadable to anyone without the correct password to de-scramble the file. ’é× The key to data encryption is to choose your passwords carefully, and change your passwords frequently.
- 13. ’é× The main appeal to me is to ability to communicate complex ideas in a fast, cheap and creative way. ’é× A level-headed approach should be taken by all internet users to protect their privacy and security online. ’é× When the true meaning of hacking is realized people will be able to publicly declare themselves as hackers.