Dc 11 Brucepotter
Download as ppt, pdf1 like508 views
- Bluesniff is a tool that allows Bluetooth devices to be discovered through wardriving even if they are not set to be discoverable. It brute forces the discovery process by cycling through all possible MAC addresses. - Previous tools like Redfang also attempted this discovery of non-discoverable Bluetooth devices but required manually entering each MAC address. Bluesniff streamlines the process and integrates it with existing WiFi wardriving tools. - The goal of Bluesniff is to raise awareness of Bluetooth security issues by making it easier for people to discover Bluetooth devices and track locations through Bluetooth, even if the user thinks the device is not discoverable.
1 of 22
Download to read offline

















Ad
Recommended
Side channel attacks
Side channel attacksStefan Fodor
╠²
Side-channel attacks exploit physical implementations of cryptosystems to gain information without using brute force or known vulnerabilities. Common side-channel attacks include timing attacks, power analysis, electromagnetic analysis, acoustic analysis, and fault injection. Examples include using timing information to deduce private keys from OpenSSL and Apache servers, recovering passwords from keyboard sounds, and extracting encryption keys from electromagnetic emissions or by freezing RAM. Defenses depend on the system and attack but imagination limits hackers' techniques.Spread Spectrum
Spread SpectrumNimrah Shahbaz
╠²
Spread spectrum is a technique used in wireless communication to spread data over a wider bandwidth through encoding. There are two main types: frequency hopping (FHSS) and direct sequence (DSSS). FHSS transmits data by rapidly switching frequencies in a random, synchronized pattern between transmitter and receiver. DSSS represents each bit as a sequence of bits through spreading codes, effectively spreading the signal across a wider bandwidth. Both techniques make signal detection and jamming more difficult. Pseudorandom number generators are used to generate the deterministic spreading codes needed to encode and decode signals.AirHopper: Bridging the Air-Gap between Isolated Networks and Mobile Phones u...
AirHopper: Bridging the Air-Gap between Isolated Networks and Mobile Phones u...mordechaiguri
╠²
The document discusses 'Airhopper', a bifurcated malware designed to exfiltrate data from air-gapped networks to mobile phones using FM signals. By exploiting the radio emissions from a compromised computer's video display unit, the malware can transfer sensitive information to nearby mobile devices within 1-7 meters at a bandwidth of 13-60 bytes per second. The paper outlines the attack model, implementation, and modulation methods while emphasizing the feasibility of this method for skilled attackers.Chap9
Chap9Object-Frontier Software Pvt. Ltd
╠²
The document discusses various terms and concepts related to satellite communications. It describes different types of satellites based on coverage area, service provided, and orbit. It also defines terms like earth stations, uplinks, downlinks, transponders, elevation angles, and coverage angles. Finally, it discusses concepts like frequency division multiple access (FDMA), time division multiple access (TDMA), different satellite orbits like GEO, LEO and MEO, and considerations that impact satellite link performance.Wsh96 Wilkinson
Wsh96 WilkinsonObject-Frontier Software Pvt. Ltd
╠²
HIPERLAN is a European standard for wireless local area networks (WLANs) developed by ETSI to provide high performance networking comparable to wired Ethernet networks. HIPERLAN 1 operates in the 5GHz band and uses a frequency hopping spread spectrum technique along with advanced MAC and PHY layer protocols to provide data rates up to 23Mbps and support both asynchronous and isochronous traffic. HIPERLAN 2 is under development and aims to be compatible with asynchronous transfer mode networking to provide quality of service guarantees over wireless links.Presentation
PresentationObject-Frontier Software Pvt. Ltd
╠²
HIPERLAN was a wireless network standard developed in Europe as an alternative to IEEE 802.11. It aimed to provide higher data rates and quality of service compared to early 802.11 standards. HIPERLAN Type 1 achieved data rates up to 2Mbps in the 1990s. HIPERLAN Type 2 was developed later to support connection-oriented networking at up to 54Mbps, with quality of service, security, and flexibility to connect to different wired networks. While prototypes existed, commercial products were still in development in the early 2000s as the standard competed with improving 802.11 variants.Rmi
RmiObject-Frontier Software Pvt. Ltd
╠²
This document provides an overview of Remote Method Invocation (RMI) in Java. It describes how RMI allows objects to be distributed across machines and invoked remotely. The key steps to building an RMI application are discussed, including defining a remote interface, implementing remote objects, running the RMI registry, and compiling/running client and server code. An example is presented to demonstrate the required classes for a simple RMI application that retrieves a string remotely.CORBA
CORBAObject-Frontier Software Pvt. Ltd
╠²
The document discusses the goal of going more in depth on the core architecture of CORBA, including less breadth and focusing on reading suggested sections from referenced books, with an outlined lecture covering CORBA's general overview, interface definition language, ORB components, and conclusions.Hack.lu 2006 - All your Bluetooth is belong to us
Hack.lu 2006 - All your Bluetooth is belong to usThierry Zoller
╠²
The document discusses various vulnerabilities and security risks associated with Bluetooth technology, highlighting insights from security experts Kevin Finisterre and Thierry Zoller. It covers the historical context of Bluetooth, different modes and protocols, and details on potential attack vectors such as bluebugging and bluesnarfing. The presentation aims to raise awareness about Bluetooth security issues and encourages proactive measures to mitigate risks.All your Bluetooth is belong to us - the rest too.
All your Bluetooth is belong to us - the rest too.Thierry Zoller
╠²
This document summarizes a talk about Bluetooth security. The talk covers extending the range of Bluetooth devices, wardriving to discover Bluetooth devices, and various attacks against Bluetooth including Bluebug, Bluesnarf, attacking cars and headsets, and cracking Bluetooth pins and link keys. It also discusses vulnerabilities in Bluetooth implementations on Apple and Windows devices that can allow compromising internal networks. Throughout it emphasizes the risks of Bluetooth and gives recommendations to improve security like disabling Bluetooth when not in use and pairing devices securely.Bluetooth Vulnerabilities
Bluetooth VulnerabilitiesVictorYee
╠²
This document summarizes vulnerabilities in Bluetooth technology, including eavesdropping, impersonation, and cipher vulnerabilities. It describes "bluejacking", "bluesnarfing", and other attacks that exploit flaws in Bluetooth functionality and permissions. The document recommends turning off Bluetooth when not in use, setting devices to non-discoverable, using random PINs, and avoiding transmitting sensitive data over Bluetooth to help protect against these vulnerabilities and attacks.Bluetooth
BluetoothAvishek Pratap Singh
╠²
Bluetooth is a short-range wireless technology that allows electronic devices to connect and exchange information over short distances without wires. It was developed as an open standard for affordable, low-power connections between devices like mobile phones, laptops, PCs, printers, digital cameras and video game consoles. Bluetooth has advantages like wireless connectivity, easy setup, low power usage, and industry support. However, it also has disadvantages like a short range of around 30 feet, lower data rates compared to other wireless technologies, and higher costs. Bluetooth works by using small, low-cost radio frequency transceivers called chips that are embedded in devices and allow them to communicate over the 2.4GHz spectrum in a piconet configuration.Bluetooth presentation
Bluetooth presentationDhairYash Kotwani
╠²
Bluetooth is a wireless technology standard that allows short-range wireless transmissions between devices like mobile phones, headphones, laptops and more. It uses short-wavelength UHF radio waves in the industrial, scientific and medical radio bands to transmit data over short distances of about 10 meters. Bluetooth specifications include frequency hopping, packet structure and encryption for security.Bluetooth
BluetoothFahim Faysal
╠²
Bluetooth is an open wireless technology standard for exchanging data over short distances between devices like mobile phones, headphones, cars and computers. It allows for personal area networks and has high levels of security. The document provides an overview of Bluetooth including its history, specifications, operation, applications and limitations.Bluetooth versus wi
Bluetooth versus wisher1242
╠²
This document provides an overview and comparison of Bluetooth and Wi-Fi (802.11b) wireless technologies. It discusses their histories, technical specifications including their radio frequencies and data transmission rates. The document also examines the security features and risks of each, such as Bluetooth's encryption and Wi-Fi's vulnerable Wired Equivalent Privacy (WEP) protocol. Mitigation strategies are suggested to help secure communications when using these wireless technologies.Bluetooth1
Bluetooth1Vikas Bansal
╠²
This document discusses Bluetooth security issues, threats, and consequences. It provides an introduction to Bluetooth technology and describes how Bluetooth networks are formed. It then outlines several security issues with Bluetooth, including that many devices operate in insecure modes by default. It describes specific attacks like Bluesnarfing, Helomoto, and Bluebugging that take advantage of these issues to access devices without authorization. These attacks can steal information from both individuals and corporations. The document concludes by noting a large number of popular devices are potentially vulnerable and references are provided.Bluetooth
BluetoothSarah Saqib
╠²
Bluetooth is a short-range, low power wireless technology for creating personal area networks and operates at 2.4 GHz. It facilitates data exchange among various devices but has limitations including short range and security concerns. The future of Bluetooth looks promising with ongoing improvements in speed, security, and the potential for larger networks.Bluetooth
Bluetoothstooty s
╠²
Bluetooth is a short-range wireless technology that was originally intended to replace cables connecting portable electronic devices. It allows for the creation of personal area networks within a range of about 10 meters. Bluetooth devices can connect and communicate with each other through a wireless protocol that uses frequency hopping to avoid interference. Popular applications of Bluetooth include wireless headphones, wireless speakers, and connecting mobile devices to keyboards and mice.Bluetooth Presentation
Bluetooth Presentationankit680
╠²
Bluetooth is a wireless communication standard invented by Ericsson in 1996, designed for low power consumption and short-range communication. It allows devices to connect and share data, can support multiple connections, and is governed by profiles that dictate how devices communicate. The term 'Bluetooth' is derived from the 10th-century Danish king Harald Bluetooth, who united tribes, symbolizing the unification of devices through this technology.R K 2 Bluetooth Technologies
R K 2 Bluetooth TechnologiesSaurav Kumar
╠²
Bluetooth is a wireless technology standard for exchanging data over short distances. It was created in 1994 initially to replace cables connecting devices like mobile phones, laptops, and peripherals. Bluetooth specifications allow for ad-hoc connections between up to eight devices within a range of around 30 feet. Devices are organized into piconets, with one device acting as the master to synchronize connections. Bluetooth aims to be a low-cost, low-power solution for connecting various consumer electronic devices and building personal area networks.Bluetooth
Bluetoothkannabhargav
╠²
Bluetooth is a wireless technology that allows devices such as computers, phones, and other electronics to connect and exchange information within short ranges of up to 10-100 meters. It uses radio transmissions in the ISM band between 2400-2483.5 MHz to form ad-hoc networks between devices. Bluetooth devices can operate at different power classes and data rates to support both voice calls and asynchronous data transfer between connected devices like transferring contacts between a phone and laptop. The Bluetooth Special Interest Group develops specifications to ensure interoperability between devices from different manufacturers.Seminar
Seminarguest355eea5d
╠²
Bluetooth is a wireless technology standard for exchanging data over short distances. It allows devices such as phones, laptops, headphones, etc. to connect and communicate with each other without wires. Bluetooth operates using radio waves to connect devices within a range of about 30 feet, using less power than WiFi. It was developed in 1994 by Ericsson and adopted as an official standard in 1998. Future versions aim to improve security, usability, and support higher data rates and more devices per connection.Unit 2 bluetooth-iot_complete notes
Unit 2 bluetooth-iot_complete notestathagatanaha3
╠²
Short-range wireless technologies like Bluetooth focus on low-cost and low-energy usage to provide long battery life. Bluetooth standards were developed by the IEEE 802.15 working group. Bluetooth enables two types of wireless services - personal area networks within a person's workspace, and device-to-device communication in Internet of Things applications like health monitors and sensors in vehicles, homes, and industrial equipment. Bluetooth uses radio waves in the 2.4 GHz band to connect devices within about 10 meters of each other to share data and audio wirelessly.Bluetooth and profiles on WEC7
Bluetooth and profiles on WEC7gnkeshava
╠²
Bluetooth and Profiles
The document discusses Bluetooth technology and Bluetooth profiles. It provides an overview of Bluetooth including its history and development of different Bluetooth versions. It describes Bluetooth architecture and core system components. It also explains various Bluetooth profiles such as Generic Access Profile, Object Exchange Profile, Serial Port Profile, and File Transfer Profile which define how Bluetooth devices communicate and establish connections.Bluetooth
BluetoothSamraiz Tejani
╠²
Bluetooth is a short-range wireless technology that allows data exchange between fixed and mobile devices over short distances. It operates in the unlicensed 2.4GHz band and has an effective range of about 10 meters. Bluetooth was originally developed in 1994 by Ericsson to eliminate data cables between devices. It has since evolved through several versions with higher data rates and improved functionality. Bluetooth technology allows multiple devices to connect and exchange information in personal area networks. bluetooth technology
bluetooth technologydeepak kumar
╠²
This document provides an overview of Bluetooth technology. It discusses what Bluetooth is, its history and development by the Bluetooth Special Interest Group. The key technical features of Bluetooth like its operating spectrum, data rates, encryption standards and classifications are explained. The document also outlines the Bluetooth protocol stack including the baseband, link manager and middleware layers. Common Bluetooth profiles and potential applications are reviewed. Finally, the security measures used by Bluetooth and its advantages compared to alternatives like infrared are summarized.Bluetooth
BluetoothHassan Razzaq
╠²
Bluetooth is a short-range wireless technology that was originally developed as a cable replacement. It operates in the 2.4 GHz band and can connect various devices like phones, headphones, keyboards within a 10 meter range. The technology uses frequency hopping spread spectrum and supports data rates up to 2 Mbps. Popular applications include wireless headsets, file transfers between devices, and input/output device connectivity like mice and keyboards.Understanding bluetooth
Understanding bluetoothmadhu428
╠²
This document provides an overview of Bluetooth wireless technology, including how it works and potential usage models. Bluetooth allows devices to automatically connect within short ranges, forming small networks. It was originally intended to replace cables for connecting devices like printers and keyboards, but has evolved to enable wireless headsets, file sharing, internet access, and more. While offering convenience, Bluetooth also presents engineering challenges in ensuring ease of use, low power consumption, and small device size. The Bluetooth SIG develops standards to ensure interoperability between certified products.OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC
╠²
The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.More Related Content
Similar to Dc 11 Brucepotter (20)
Hack.lu 2006 - All your Bluetooth is belong to us
Hack.lu 2006 - All your Bluetooth is belong to usThierry Zoller
╠²
The document discusses various vulnerabilities and security risks associated with Bluetooth technology, highlighting insights from security experts Kevin Finisterre and Thierry Zoller. It covers the historical context of Bluetooth, different modes and protocols, and details on potential attack vectors such as bluebugging and bluesnarfing. The presentation aims to raise awareness about Bluetooth security issues and encourages proactive measures to mitigate risks.All your Bluetooth is belong to us - the rest too.
All your Bluetooth is belong to us - the rest too.Thierry Zoller
╠²
This document summarizes a talk about Bluetooth security. The talk covers extending the range of Bluetooth devices, wardriving to discover Bluetooth devices, and various attacks against Bluetooth including Bluebug, Bluesnarf, attacking cars and headsets, and cracking Bluetooth pins and link keys. It also discusses vulnerabilities in Bluetooth implementations on Apple and Windows devices that can allow compromising internal networks. Throughout it emphasizes the risks of Bluetooth and gives recommendations to improve security like disabling Bluetooth when not in use and pairing devices securely.Bluetooth Vulnerabilities
Bluetooth VulnerabilitiesVictorYee
╠²
This document summarizes vulnerabilities in Bluetooth technology, including eavesdropping, impersonation, and cipher vulnerabilities. It describes "bluejacking", "bluesnarfing", and other attacks that exploit flaws in Bluetooth functionality and permissions. The document recommends turning off Bluetooth when not in use, setting devices to non-discoverable, using random PINs, and avoiding transmitting sensitive data over Bluetooth to help protect against these vulnerabilities and attacks.Bluetooth
BluetoothAvishek Pratap Singh
╠²
Bluetooth is a short-range wireless technology that allows electronic devices to connect and exchange information over short distances without wires. It was developed as an open standard for affordable, low-power connections between devices like mobile phones, laptops, PCs, printers, digital cameras and video game consoles. Bluetooth has advantages like wireless connectivity, easy setup, low power usage, and industry support. However, it also has disadvantages like a short range of around 30 feet, lower data rates compared to other wireless technologies, and higher costs. Bluetooth works by using small, low-cost radio frequency transceivers called chips that are embedded in devices and allow them to communicate over the 2.4GHz spectrum in a piconet configuration.Bluetooth presentation
Bluetooth presentationDhairYash Kotwani
╠²
Bluetooth is a wireless technology standard that allows short-range wireless transmissions between devices like mobile phones, headphones, laptops and more. It uses short-wavelength UHF radio waves in the industrial, scientific and medical radio bands to transmit data over short distances of about 10 meters. Bluetooth specifications include frequency hopping, packet structure and encryption for security.Bluetooth
BluetoothFahim Faysal
╠²
Bluetooth is an open wireless technology standard for exchanging data over short distances between devices like mobile phones, headphones, cars and computers. It allows for personal area networks and has high levels of security. The document provides an overview of Bluetooth including its history, specifications, operation, applications and limitations.Bluetooth versus wi
Bluetooth versus wisher1242
╠²
This document provides an overview and comparison of Bluetooth and Wi-Fi (802.11b) wireless technologies. It discusses their histories, technical specifications including their radio frequencies and data transmission rates. The document also examines the security features and risks of each, such as Bluetooth's encryption and Wi-Fi's vulnerable Wired Equivalent Privacy (WEP) protocol. Mitigation strategies are suggested to help secure communications when using these wireless technologies.Bluetooth1
Bluetooth1Vikas Bansal
╠²
This document discusses Bluetooth security issues, threats, and consequences. It provides an introduction to Bluetooth technology and describes how Bluetooth networks are formed. It then outlines several security issues with Bluetooth, including that many devices operate in insecure modes by default. It describes specific attacks like Bluesnarfing, Helomoto, and Bluebugging that take advantage of these issues to access devices without authorization. These attacks can steal information from both individuals and corporations. The document concludes by noting a large number of popular devices are potentially vulnerable and references are provided.Bluetooth
BluetoothSarah Saqib
╠²
Bluetooth is a short-range, low power wireless technology for creating personal area networks and operates at 2.4 GHz. It facilitates data exchange among various devices but has limitations including short range and security concerns. The future of Bluetooth looks promising with ongoing improvements in speed, security, and the potential for larger networks.Bluetooth
Bluetoothstooty s
╠²
Bluetooth is a short-range wireless technology that was originally intended to replace cables connecting portable electronic devices. It allows for the creation of personal area networks within a range of about 10 meters. Bluetooth devices can connect and communicate with each other through a wireless protocol that uses frequency hopping to avoid interference. Popular applications of Bluetooth include wireless headphones, wireless speakers, and connecting mobile devices to keyboards and mice.Bluetooth Presentation
Bluetooth Presentationankit680
╠²
Bluetooth is a wireless communication standard invented by Ericsson in 1996, designed for low power consumption and short-range communication. It allows devices to connect and share data, can support multiple connections, and is governed by profiles that dictate how devices communicate. The term 'Bluetooth' is derived from the 10th-century Danish king Harald Bluetooth, who united tribes, symbolizing the unification of devices through this technology.R K 2 Bluetooth Technologies
R K 2 Bluetooth TechnologiesSaurav Kumar
╠²
Bluetooth is a wireless technology standard for exchanging data over short distances. It was created in 1994 initially to replace cables connecting devices like mobile phones, laptops, and peripherals. Bluetooth specifications allow for ad-hoc connections between up to eight devices within a range of around 30 feet. Devices are organized into piconets, with one device acting as the master to synchronize connections. Bluetooth aims to be a low-cost, low-power solution for connecting various consumer electronic devices and building personal area networks.Bluetooth
Bluetoothkannabhargav
╠²
Bluetooth is a wireless technology that allows devices such as computers, phones, and other electronics to connect and exchange information within short ranges of up to 10-100 meters. It uses radio transmissions in the ISM band between 2400-2483.5 MHz to form ad-hoc networks between devices. Bluetooth devices can operate at different power classes and data rates to support both voice calls and asynchronous data transfer between connected devices like transferring contacts between a phone and laptop. The Bluetooth Special Interest Group develops specifications to ensure interoperability between devices from different manufacturers.Seminar
Seminarguest355eea5d
╠²
Bluetooth is a wireless technology standard for exchanging data over short distances. It allows devices such as phones, laptops, headphones, etc. to connect and communicate with each other without wires. Bluetooth operates using radio waves to connect devices within a range of about 30 feet, using less power than WiFi. It was developed in 1994 by Ericsson and adopted as an official standard in 1998. Future versions aim to improve security, usability, and support higher data rates and more devices per connection.Unit 2 bluetooth-iot_complete notes
Unit 2 bluetooth-iot_complete notestathagatanaha3
╠²
Short-range wireless technologies like Bluetooth focus on low-cost and low-energy usage to provide long battery life. Bluetooth standards were developed by the IEEE 802.15 working group. Bluetooth enables two types of wireless services - personal area networks within a person's workspace, and device-to-device communication in Internet of Things applications like health monitors and sensors in vehicles, homes, and industrial equipment. Bluetooth uses radio waves in the 2.4 GHz band to connect devices within about 10 meters of each other to share data and audio wirelessly.Bluetooth and profiles on WEC7
Bluetooth and profiles on WEC7gnkeshava
╠²
Bluetooth and Profiles
The document discusses Bluetooth technology and Bluetooth profiles. It provides an overview of Bluetooth including its history and development of different Bluetooth versions. It describes Bluetooth architecture and core system components. It also explains various Bluetooth profiles such as Generic Access Profile, Object Exchange Profile, Serial Port Profile, and File Transfer Profile which define how Bluetooth devices communicate and establish connections.Bluetooth
BluetoothSamraiz Tejani
╠²
Bluetooth is a short-range wireless technology that allows data exchange between fixed and mobile devices over short distances. It operates in the unlicensed 2.4GHz band and has an effective range of about 10 meters. Bluetooth was originally developed in 1994 by Ericsson to eliminate data cables between devices. It has since evolved through several versions with higher data rates and improved functionality. Bluetooth technology allows multiple devices to connect and exchange information in personal area networks. bluetooth technology
bluetooth technologydeepak kumar
╠²
This document provides an overview of Bluetooth technology. It discusses what Bluetooth is, its history and development by the Bluetooth Special Interest Group. The key technical features of Bluetooth like its operating spectrum, data rates, encryption standards and classifications are explained. The document also outlines the Bluetooth protocol stack including the baseband, link manager and middleware layers. Common Bluetooth profiles and potential applications are reviewed. Finally, the security measures used by Bluetooth and its advantages compared to alternatives like infrared are summarized.Bluetooth
BluetoothHassan Razzaq
╠²
Bluetooth is a short-range wireless technology that was originally developed as a cable replacement. It operates in the 2.4 GHz band and can connect various devices like phones, headphones, keyboards within a 10 meter range. The technology uses frequency hopping spread spectrum and supports data rates up to 2 Mbps. Popular applications include wireless headsets, file transfers between devices, and input/output device connectivity like mice and keyboards.Understanding bluetooth
Understanding bluetoothmadhu428
╠²
This document provides an overview of Bluetooth wireless technology, including how it works and potential usage models. Bluetooth allows devices to automatically connect within short ranges, forming small networks. It was originally intended to replace cables for connecting devices like printers and keyboards, but has evolved to enable wireless headsets, file sharing, internet access, and more. While offering convenience, Bluetooth also presents engineering challenges in ensuring ease of use, low power consumption, and small device size. The Bluetooth SIG develops standards to ensure interoperability between certified products.Recently uploaded (20)
OpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC
╠²
The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.Coordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash
╠²
Coordinated Disclosure for ML - What's Different and What's the SameWebdriverIO & JavaScript: The Perfect Duo for Web Automation
WebdriverIO & JavaScript: The Perfect Duo for Web Automationdigitaljignect
╠²
In todayŌĆÖs dynamic digital landscape, ensuring the quality and dependability of web applications is essential. While Selenium has been a longstanding solution for automating browser tasks, the integration of WebdriverIO (WDIO) with Selenium and JavaScript marks a significant advancement in automation testing. WDIO enhances the testing process by offering a robust interface that improves test creation, execution, and management. This amalgamation capitalizes on the strengths of both tools, leveraging SeleniumŌĆÖs broad browser support and WDIOŌĆÖs modern, efficient approach to test automation. As automation testing becomes increasingly vital for faster development cycles and superior software releases, WDIO emerges as a versatile framework, particularly potent when paired with JavaScript, making it a preferred choice for contemporary testing teams.PyCon SG 25 - Firecracker Made Easy with Python.pdf
PyCon SG 25 - Firecracker Made Easy with Python.pdfMuhammad Yuga Nugraha
╠²
Explore the ease of managing Firecracker microVM with the firecracker-python. In this session, I will introduce the basics of Firecracker microVM and demonstrate how this custom SDK facilitates microVM operations easily. We will delve into the design and development process behind the SDK, providing a behind-the-scenes look at its creation and features. While traditional Firecracker SDKs were primarily available in Go, this module brings a simplicity of Python to the table.CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025pcprocore
╠²
¤æēØŚĪØŚ╝ØśüØŚ▓:ØŚ¢ØŚ╝ØŚĮØśå ØŚ╣ØŚČØŚ╗ØŚĖ & ØŚĮØŚ«ØśĆØśüØŚ▓ ØŚČØŚ╗ØśüØŚ╝ ØŚÜØŚ╝ØŚ╝ØŚ┤ØŚ╣ØŚ▓ ØŚ╗ØŚ▓Øśä ØśüØŚ«ØŚ»> https://pcprocore.com/ ¤æłŌŚĆ
CapCut Pro Crack is a powerful tool that has taken the digital world by storm, offering users a fully unlocked experience that unleashes their creativity. With its user-friendly interface and advanced features, itŌĆÖs no wonder why aspiring videographers are turning to this software for their projects.Wenn alles versagt - IBM Tape sch├╝tzt, was z├żhlt! Und besonders mit dem neust...
Wenn alles versagt - IBM Tape sch├╝tzt, was z├żhlt! Und besonders mit dem neust...Josef Weingand
╠²
IBM LTO10Cluster-Based Multi-Objective Metamorphic Test Case Pair Selection for Deep N...
Cluster-Based Multi-Objective Metamorphic Test Case Pair Selection for Deep N...janeliewang985
╠²
the slides of the MP selection approach CMPS"Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays
╠²
What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.Connecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software
╠²
In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdf
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdfPriyanka Aash
╠²
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing NowA Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdf
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdfPriyanka Aash
╠²
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software
╠²
This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.From Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software
╠²
Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasnŌĆÖt yielding any results, so I expanded my search to second-hand dealer sitesŌĆöonly to realise that periodically checking each one was going to be tedious. ThatŌĆÖs when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platformŌĆÖs structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, IŌĆÖll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME canŌĆÖt buy a car for youŌĆöyetŌĆöit can certainly help you find the one youŌĆÖre after!Enhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule
╠²
║▌║▌▀Ż deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 2025The Future of Product Management in AI ERA.pdf
The Future of Product Management in AI ERA.pdfAlyona Owens
╠²
Hi, IŌĆÖm Aly Owens, I have a special pleasure to stand here as over a decade ago I graduated from CityU as an international student with an MBA program. I enjoyed the diversity of the school, ability to work and study, the network that came with being here, and of course the price tag for students here has always been more affordable than most around.
Since then I have worked for major corporations like T-Mobile and Microsoft and many more, and I have founded a startup. I've also been teaching product management to ensure my students save time and money to get to the same level as me faster avoiding popular mistakes. Today as IŌĆÖve transitioned to teaching and focusing on the startup, I hear everybody being concerned about Ai stealing their jobsŌĆ” WeŌĆÖll talk about it shortly.
But before that, I want to take you back to 1997. One of my favorite movies is ŌĆ£Fifth ElementŌĆØ. It wowed me with futuristic predictions when I was a kid and IŌĆÖm impressed by the number of these predictions that have already come true. Self-driving cars, video calls and smart TV, personalized ads and identity scanning. Sci-fi movies and books gave us many ideas and some are being implemented as we speak. But we often get ahead of ourselves:
Flying cars,Colonized planets, Human-like AI: not yet, Time travel, Mind-machine neural interfaces for everyone: Only in experimental stages (e.g. Neuralink).
Cyberpunk dystopias: Some vibes (neon signs + inequality + surveillance), but not total dystopia (thankfully).
On the bright side, we predict that the working hours should drop as Ai becomes our helper and there shouldnŌĆÖt be a need to work 8 hours/day. Nobody knows for sure but we can require that from legislation. Instead of waiting to see what the government and billionaires come up with, I say we should design our own future.
So, we as humans, when we donŌĆÖt know something - fear takes over. The same thing happened during the industrial revolution. In the Industrial Era, machines didnŌĆÖt steal jobsŌĆöthey transformed them but people were scared about their jobs. The AI era is making similar changes except it feels like robots will take the center stage instead of a human. First off, even when it comes to the hottest space in the military - drones, Ai does a fraction of work. AI algorithms enable real-time decision-making, obstacle avoidance, and mission optimization making drones far more autonomous and capable than traditional remote-controlled aircraft. Key technologies include computer vision for object detection, GPS-enhanced navigation, and neural networks for learning and adaptation. But guess what? There are only 2 companies right now that utilize Ai in drones to make autonomous decisions - Skydio and DJI.
Quantum AI: Where Impossible Becomes Probable
Quantum AI: Where Impossible Becomes ProbableSaikat Basu
╠²
Imagine combining the "brains" of Artificial Intelligence (AI) with the "super muscles" of Quantum Computing. That's Quantum AI!
It's a new field that uses the mind-bending rules of quantum physics to make AI even more powerful.Mastering AI Workflows with FME by Mark Do╠łring
Mastering AI Workflows with FME by Mark Do╠łringSafe Software
╠²
Harness the full potential of AI with FME: From creating high-quality training data to optimizing models and utilizing results, FME supports every step of your AI workflow. Seamlessly integrate a wide range of models, including those for data enhancement, forecasting, image and object recognition, and large language models. Customize AI models to meet your exact needs with FMEŌĆÖs powerful tools for training, optimization, and seamless integrationEIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdf
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdfEarley Information Science
╠²
As AI reshapes expectations in retail and B2B commerce, organizations are recognizing a critical reality: meaningful AI outcomes depend on well-structured, adaptable infrastructure. In this session, Seth Earley is joined by Phil Ryan - AI strategist, search technologist, and founder of Glass Leopard Technologies - for a candid conversation on what it truly means to engineer systems for scale, agility, and intelligence.
Phil draws on more than two decades of experience leading search and AI initiatives for enterprise organizations. Together, he and Seth explore the challenges businesses face when legacy architectures limit personalization, agility, and real-time decisioning - and what needs to change to support agentic technologies and next-best-action capabilities.
Key themes from the webinar include:
Composability as a prerequisite for AI╠²- Why modular, loosely coupled systems are essential for adapting to rapid innovation and evolving business needs
Search and relevance as foundational to AI╠²- How techniques honed-in enterprise search have laid the groundwork for more responsive and intelligent customer experiences
From MDM and CDP to agentic systems╠²- How data platforms are evolving to support richer customer context and dynamic orchestration
Engineering for business alignment╠²- Why successful AI programs require architectural decisions grounded in measurable outcomes
The conversation is practical and forward-looking, connecting deep technical understanding with real-world business needs. Whether youŌĆÖre modernizing your commerce stack or exploring how AI can enhance product discovery, personalization, or customer journeys, this session provides a clear-eyed view of the capabilities, constraints, and priorities that matter most.Ad
Dc 11 Brucepotter
- 1. Bluesniff - The Next Wardriving Frontier Bruce Potter <gdead@shmoo.com> Brian Caswell <bmc@shmoo.com>
- 2. Bluetooth Basics NOT 802.11! NOT a relative of 802.11! Cable replacement technology Low power for embedded devices More BT radios than 802.11 radios in existence Phones, headsets, laptops, mice, keyboards Master / Slave architecture
- 3. Bluetooth Protocol Uses 2.4 GHz ISM band, same as 802.11b/g Generally low power Class 3 (1mW) for most devices Some Class 1(100mW) devices exist Frequency Hopping Spread Spectrum Uses a pre-defined hopping pattern Back in the day, FHSS was a ŌĆ£securityŌĆØ mechanism Resists interference 1MHz wide, hopping every 625 microseconds
- 4. Bluetooth Protocol A real disaster of a protocol stack Heck, the core spec is 1024 pages.. Good reading! Specifies from Layer 1 to Layer 7 High points RF-level sync Inquiry/request Service discovery Low power modes
- 5. Bluetooth Security Pairing Using a shared secret (PIN), exchange random number to form key Key used to derive session key for future comms Used for Trusted <-> Trusted comms
- 6. Bluetooth Security Authentication / Authorization Per connection AA Per service AA Encryption Ditto ItŌĆÖs all OPTIONAL! Left to the developer/user to decide This ends wellŌĆ” :(
- 7. Bluetooth Profiles Profiles exist to ease interoperability *wink* *wink* Keyboard, file transfer, handsfree (and headset), etcŌĆ”
- 8. Bluetooth vs. 802.11b More at stake Compromise 802.11 security = Access to network Compromise BT Security = Gateway directly to App level functionality More personalized information Phone conversations, calendar info, etc Less interesting for Joe 12-pack, more interesting for executives
- 9. Discovery of 802.11 Direct Sequence Spread spectrum Transmitters always in the same ŌĆ£placeŌĆØ in a channel DSSS pretty easy to find Granted, transmitters may be on different channels Cisco - hardware channel switching RF Monitor Prism 2 - firmware channel switching RF Monitor Orinoco - need external channel hopper
- 10. Discovery of 802.11 Beacons ŌĆ£ IŌĆÖm hereŌĆØ every 100ms Can be turned off for ŌĆ£cloakingŌĆØ Fools Netstumbler DoesnŌĆÖt fool Kismet or Airsnort Regular traffic Windows boxen are noisy Regardless of OS, generally frequent traffic
- 11. Discovery of Bluetooth FHSS harder to ŌĆ£findŌĆØ Must align with hopping pattern BT uses 1/2 the normal hop time to Jump Around Still averages 2.5 to 10 secs to find known device Devices can be Discoverable Respond to inquiry requests
- 12. Discovery of Bluetooth Devices can also be non-discoverable Must be directly probed by MAC addr Little to no traffic for extended periods of time (esp in low power mode) Cannot easily be listened to b/c receiver cannot sync on hopping pattern Sophisticated RF gear can find and intercept traffic Currently no one can make a standard card do this
- 13. Bluetooth Attacks Interception of traffic during pairing Brute force guess the PIN to recover key Know the PIN b/c itŌĆÖs imbedded More likely poorly developed software In BT, security is ŌĆ£optionalŌĆØ Or simply bad defaults File sharing with no AA/E in discoverable mode was the DEFAULT for my BT driver on my PDA Just like the early days of 802.11b
- 14. Bluetooth Tracking Even Class 3 devices can be intercepted at a distance If your phone/PDA/earpiece is BT enabled, attacker can follow you using commodity gear Like your own RFID tag
- 15. Bluetooth Wardriving Used to walk around hitting ŌĆ£scanŌĆØ button on BT driver UI Does not find non-discoverable devices Needs new tools to catch on Same voyeuristic appeal of 802.11 wardriving As it becomes popular, BT developers and users will get a swift kick in the butt to make things more secure
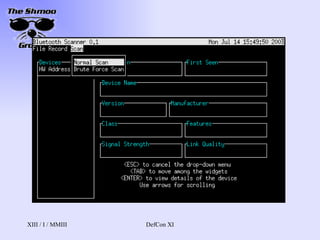
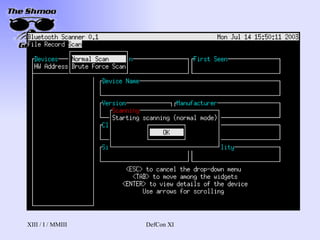
- 16. Redfang Released by @Stake, Spring 2003 Looks for devices that do not want to be discovered Brute forces through MAC addresses attempting to find devices First 3 octets fixed, rotates through last three Can take a long time, since FHSS sync can take ~10 seconds per MAC The only way so farŌĆ”
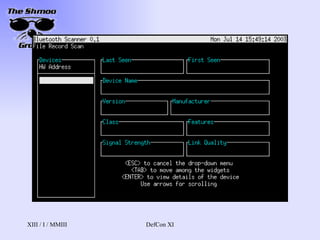
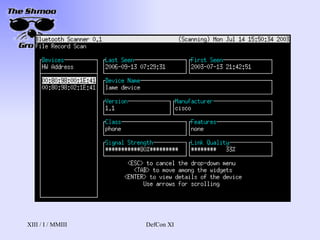
- 17. Bluesniff http://bluesniff.shmoo.com/ Our tool (heh.. he said toolŌĆ”) Focused on providing a UI Front-end for Redfang Also finds devices in discoverable mode Yes, people leave things to be discovered Making BT wardrivers easier and more efficient will raise awareness of BT security issues
- 18. ╠²
- 19. ╠²
- 20. ╠²
- 21. ╠²
- 22. Future work Integration with WiFi scanning tools (namely Airsnort) New scanning methods
