2010 za con_ian_de_villiers
0 likes183 views
This document discusses techniques for attacking and reversing Java applications. It begins by introducing Java archive (JAR) files, which contain compiled Java classes and can be easily extracted. It then outlines some common difficulties in reversing Java applications, such as many classes and libraries, non-clean decompilation, and obfuscated code. The document presents methods for defeating Java application signing and modifying classes. It also introduces newer attack techniques using tools like Burp and JavaSnoop that target serialized objects without requiring reversing. In the end, it claims that both traditional reversing and newer attack methodologies can enable attacking Java applications.
1 of 25
Download to read offline














Ad
Recommended
The jar of joy
The jar of joySensePost
Ėý
The document discusses the techniques and challenges involved in reverse engineering Java applications, particularly focusing on JAR files. It highlights the ease of modifying classes within JARs, the difficulties presented by obfuscation, and newer methodologies that simplify attacks without requiring extensive reversing. The presentation concludes with the assertion that while traditional techniques are still relevant, modern approaches are evolving to facilitate the exploitation of Java applications.Maven - Taming the Beast
Maven - Taming the BeastRoberto Cortez
Ėý
Roberto Cortez's presentation on Maven addresses its challenges such as slowness, complexity, and common pitfalls faced by developers. Highlighting its history and purpose of standardizing project management, he emphasizes the importance of understanding dependencies and build processes. The session also offers practical tips for improving build speed and resolving common issues encountered when using Maven.KYSUC - Keep Your Schema Under Control
KYSUC - Keep Your Schema Under ControlCoimbra JUG
Ėý
The document presents a comprehensive approach to database schema management, focusing on maintaining updated ER models, version-controlled scripts, and efficient deployment strategies. It emphasizes the importance of documentation and continuous integration within database management processes, using tools like Jenkins and Flyway for deployment. Best practices are outlined throughout the presentation for successful database development and maintenance..NET MeetUp Prague 2017 - .NET Standard -- Karel Zikmund
.NET MeetUp Prague 2017 - .NET Standard -- Karel ZikmundKarel Zikmund
Ėý
The document discusses .NET Standard, which is a specification that defines a set of APIs that all .NET platforms must implement. This allows code written for one platform using those APIs to work seamlessly across all other platforms that support the same .NET Standard version. The document outlines the different versions of .NET Standard and shows which platforms support each version. It emphasizes that .NET Standard is for libraries, while applications should target specific platforms like .NET Core or Xamarin. The document also provides an overview of .NET Core and its key advantages like being cross-platform, unified, fast, modern, open source and lightweight.Java buzzwords.pptx
Java buzzwords.pptxBHARATH KUMAR
Ėý
The document discusses the key features of the Java programming language. It describes Java as simple, object-oriented, platform independent, secure, robust, architecture-neutral, portable, interpreted, high-performance, distributed, multi-threaded, and dynamic. Some of its main features include automatic garbage collection, bytecode that runs on any device, secure sandboxes, and support for creating distributed and multi-threaded applications..NET Fringe 2017 - Challenges of Managing CoreFX repo -- Karel Zikmund
.NET Fringe 2017 - Challenges of Managing CoreFX repo -- Karel ZikmundKarel Zikmund
Ėý
The document discusses the challenges of managing the CoreFX repository, which is the core framework of .NET Core, encompassing various base class libraries. It highlights the structure of the CoreFX team, incoming issues, and pull requests, along with triage rules for managing contributions and new API additions. The text also emphasizes the importance of communication and collaboration within the team and with external contributors to improve the development process..NET MeetUp Prague 2017 - Challenges of Managing CoreFX repo -- Karel Zikmund
.NET MeetUp Prague 2017 - Challenges of Managing CoreFX repo -- Karel ZikmundKarel Zikmund
Ėý
This document summarizes the challenges of managing the .NET CoreFX repository. It discusses that the repo contains the base class libraries for .NET Core, is maintained by around 40 Microsoft engineers, and receives hundreds of issues and pull requests monthly. It outlines tools used to manage the large repo and process for evaluating new APIs and code changes. It also discusses efforts to improve communication and involvement with external contributors on issues like onboarding, unclear issues, and driving consensus..NET MeetUp Brno - Challenges of Managing CoreFX repo -- Karel Zikmund
.NET MeetUp Brno - Challenges of Managing CoreFX repo -- Karel ZikmundKarel Zikmund
Ėý
This document summarizes the challenges of managing the .NET CoreFX repository. It discusses that the repo contains the base class libraries for .NET Core, is maintained by around 40 Microsoft engineers, and receives hundreds of issues and pull requests monthly. It outlines strategies for organizing the large repo, prioritizing work, adding new APIs, and involving external contributors through community outreach efforts.2010 za con_ivan_burke
2010 za con_ivan_burkeJohan Klerk
Ėý
This document summarizes research into exploiting Google gadgets for malicious purposes. It describes how the researcher was able to build a basic botnet by taking advantage of vulnerabilities in how Google gadgets communicate and access browser data. They were able to perform man-in-the-middle attacks, harvest browser information, set up basic command and control, and create an anonymous browsing gadget. While not a full-fledged botnet, it demonstrated how Google gadgets meet some key requirements for being exploited in this way, like access to data and stealthy communication channels. The document recommends fixes like Google following standard web protocols and consumers blocking certain agents and cleaning browser histories.Arts railway station tv exp
Arts railway station tv expMezbah Uddin
Ėý
1. ARTS Railway Station TV is a communication medium that displays advertisements and information to passengers at major railway stations in Bangladesh, allowing brands to reach a large captive audience.
2. The screens provide entertainment to passengers while they wait for their trains, helping to make the time pass more pleasantly.
3. Key advantages of this media include compulsory viewing by waiting passengers, an inability to change the channel to avoid ads, and the ability to display train information that passengers often check.2010 za con_jameel_haffejee
2010 za con_jameel_haffejeeJohan Klerk
Ėý
This document introduces PowerShell and explains why hackers should learn it. PowerShell can be used for tasks like port scanning, brute forcing RDP/SQL, dumping password hashes, and quickly setting up backdoors. It comes preinstalled on many modern Windows systems and provides an unchecked environment for accessing and controlling the operating system through commands and scripting. The document demonstrates various hacking techniques that can be accomplished using PowerShell, such as poking the system, checking for open ports, and gaining complete control over servers after initial access.Arts railway station tv exp
Arts railway station tv expMezbah Uddin
Ėý
1) ARTS Railway Station TV is a communication medium that displays advertisements and information to passengers at major railway stations in Bangladesh, allowing brands to reach a large captive audience.
2) The screens provide entertainment to passengers while they wait for their trains, helping to make the time pass more pleasantly.
3) As passengers are required to wait at the station, the screens have a large guaranteed audience with no ability to change the channel, making it an effective advertising medium.Anexo a demanda impugnacion laudo sunat comprimidoPaola Aliaga
Ėý
Anexo a demanda impugnacion laudo sunat comprimido2010 za con_haroon_meer
2010 za con_haroon_meerJohan Klerk
Ėý
This document appears to be a transcript of a talk given by Haroon Meer on October 17, 2010 about issues in the information security industry. Some of the main points discussed include that the infosec industry hides behind "fig leaves" and only fights battles they can kind of win, rather than taking on important problems. Meer argues that people in infosec think they can't write secure code, but some have shown this is possible. He calls for people to work on problems that really matter and produce more original research, rather than just consuming others' work.Cv paola aliaga 21Paola Aliaga
Ėý
Paola Aliaga es una contadora pÚblica con mÃĄs de 17 aÃąos de experiencia en la SUNAT. Es una lÃder sindical que ha representado a trabajadores en varias organizaciones. Tiene especializaciones en fiscalidad internacional y auditorÃa tributaria. Ha participado en foros de diÃĄlogo social y defensa de derechos laborales. Actualmente es dirigente sindical en ejercicio en SUNAT y coordina enlaces con el Consejo de Alto Nivel AnticorrupciÃģn.2010 za con_georg-christian_pranschke
2010 za con_georg-christian_pranschkeJohan Klerk
Ėý
This document discusses SNMP (Simple Network Management Protocol) and how it can be exploited due to misconfigurations. It begins with an overview of SNMP, including how it works and common vulnerabilities. It then focuses on exploiting SNMP on Cisco appliances, describing how community strings can be brute forced to gain privileged access. The document introduces Frisk-0, a tool that automates brute forcing community strings and downloading device configurations. It concludes with recommendations around securing SNMP-enabled devices by changing defaults, using strong community strings, and implementing access control lists.2010 za con_todor_genov
2010 za con_todor_genovJohan Klerk
Ėý
This document provides an overview of DNSSEC (Domain Name System Security Extensions) by a sysadmin who works for an ISP and does a lot of DNS work. It discusses what DNSSEC is (DNS with public key cryptography to authenticate DNS responses), how it works (each zone has public/private keys and all resource records are signed), new resource records introduced by DNSSEC like DNSKEY, RRSIG, DS, and how the chain of trust is established to validate DNS responses by starting with a trust anchor and delegating trust through signed records.2010 za con_jurgens_van_der_merwe
2010 za con_jurgens_van_der_merweJohan Klerk
Ėý
The document discusses Jurgens van der Merwe, a junior analyst at SensePost whose interests include information security, innovative technologies, music, and skateboarding. It then provides an overview of the Selenium browser automation framework, which allows testing of web applications through programmatically controlling browsers. It can automate workflows, extract data from pages, and more. The document discusses some examples of what can be done with Selenium and also addresses some challenges like latency.2010 za con_roelof_temmingh
2010 za con_roelof_temminghJohan Klerk
Ėý
The document discusses several ideas for automated social engineering and Internet scanning techniques, some of which may pose legal or ethical issues. It describes methods like injecting messages into email threads to trick recipients, using personal details gathered from online surveys to test password strength, and performing port scans, traceroutes, and reverse lookups across all IP addresses on the Internet to identify vulnerabilities. One idea involves storing secret messages in the latency of network pipes like satellite links. The document also briefly mentions some work Andrew actually did with natural language processing, Facebook data, and developing tools for a cybersecurity software program.2010 za con_daniel_cuthbert
2010 za con_daniel_cuthbertJohan Klerk
Ėý
The document provides tips for testing the security of banking applications and frameworks. It suggests focusing on business logic flaws, such as manipulating functions to perform unintended tasks or bypass intended flows. Other tips include exploiting flaws in validation routines, manipulating currency values, and "outwitting" developers by finding ways to upload malicious files that may be executed by administrators. The goal is to identify vulnerabilities in these applications, as many offshore development teams and banks still have limited security knowledge.2010 za con_barry_irwin
2010 za con_barry_irwinJohan Klerk
Ėý
1. Conficker, also known as Downup and Downadup, is a computer worm discovered in November 2008 that spread via Windows security vulnerabilities. It infected millions of computers worldwide at its peak.
2. The outbreak began slowly in late 2008 and accelerated in early 2009, as variants Conficker A, B, and C incorporated techniques like domain generation algorithms and peer-to-peer networking to spread. Estimates put global infections between 3-12 million machines by early 2009.
3. Responses included Microsoft forming a "Conficker Cabal" in February 2009 to mitigate the threat, and variants like Conficker C beginning to use 50,000 domain names and peer-to-peer networks to coordinate infected2010 za con_stephen_kreusch
2010 za con_stephen_kreuschJohan Klerk
Ėý
This document provides an overview of data loss prevention (DLP) systems. It defines DLP and describes how it can identify, monitor, and protect data in use, in motion, and at rest. It discusses typical DLP implementations for networks and endpoints/storage and how policies are defined. Common criticisms of DLP are outlined as well as the value it can provide by focusing on data security and improving communication between security and business teams. Lessons learned emphasize the importance of people, process, and technology in DLP deployments.Training management
Training managementMezbah Uddin
Ėý
This document describes a school management system project that aims to ease the academic and management processes for educational institutions. The system allows students to choose from available courses, view course details, and apply for courses online. It includes modules for administration, student registration, attendance tracking, counseling, and updating student information. The project uses technologies like HTML, CSS, PHP, MySQL, and frameworks like Bootstrap. It is intended to benefit schools, universities, students, and parents by facilitating online admission applications and student counseling management.Java Serialization Facts and Fallacies
Java Serialization Facts and FallaciesRoman Elizarov
Ėý
The document discusses Java serialization and common myths surrounding it. It summarizes that Java serialization allows for flexible evolution of classes while maintaining backwards compatibility through the use of serialVersionUID. It debunks common myths that Java serialization is slow, inflexible, or that changing private fields breaks compatibility. The document explains that serialization performance depends more on how streams are used rather than the underlying implementation.Java Introduction
Java Introductionsunmitraeducation
Ėý
The document provides an introduction and history of Java, outlining how it was developed in the 1990s as a platform-independent language by James Gosling at Sun Microsystems, and discusses some key advantages of Java like being object-oriented, portable, robust, and having built-in support for security and multithreading. It also describes the Java Development Kit (JDK) which contains tools for developing Java programs and the Java Runtime Environment (JRE) which allows running of Java applications and includes the Java Virtual Machine.Rapid With Spring Roo
Rapid With Spring RooMorten Lileng
Ėý
Roo is a productivity tool that allows for easy creation of Enterprise Java applications. It generates infrastructure code like entities, controllers, and services through simple shell commands. Roo uses AspectJ for automatic code generation and integrates with Spring technologies like dependency injection and MVC. It aims to help developers build RESTful services quickly without needing to write infrastructure code from scratch.java completed units.docx
java completed units.docxSATHYAKALAKSKPRCASBS
Ėý
This document provides an overview of the history and features of the Java programming language. It discusses how Java was originally developed by Sun Microsystems in 1991 and was designed to be portable, simple, reliable and secure. Some key features of Java discussed include its object-oriented nature, portability through bytecode, robustness through features like garbage collection, and support for web-based applications through applets. The document also compares Java to C and C++, noting differences like Java's lack of pointers and multiple inheritance. Finally, it discusses how Java became associated with the Internet and World Wide Web through its use in interactive applets and applications.java full 1.docx
java full 1.docxSATHYAKALAKSKPRCASBS
Ėý
Java was originally developed by Sun Microsystems in 1991 and was originally called Oak. It was designed to be simple, portable, and reliable. Some key features of Java include being platform independent through bytecode, object-oriented design, robust and secure features like memory management and exception handling, and being distributed and interactive through multithreading. Subsequent versions of Java like J2SE 5.0 added additional features like generics and annotations to improve development, and JDBC and XML processing to support databases and web services.java full.docx
java full.docxSATHYAKALAKSKPRCASBS
Ėý
This document provides an overview of the history and features of the Java programming language. It discusses that Java was originally developed by Sun Microsystems in 1991 and was designed to be portable, simple, secure, and robust. Some key features of Java include being object-oriented, platform independent through bytecode compilation, having automatic memory management, and being well-suited for web and internet applications through applets. The document also compares Java to C and C++, noting differences like Java not supporting pointers or multiple inheritance. It describes how Java works with web browsers and HTML to enable interactive content on web pages through applets.More Related Content
Viewers also liked (16)
2010 za con_ivan_burke
2010 za con_ivan_burkeJohan Klerk
Ėý
This document summarizes research into exploiting Google gadgets for malicious purposes. It describes how the researcher was able to build a basic botnet by taking advantage of vulnerabilities in how Google gadgets communicate and access browser data. They were able to perform man-in-the-middle attacks, harvest browser information, set up basic command and control, and create an anonymous browsing gadget. While not a full-fledged botnet, it demonstrated how Google gadgets meet some key requirements for being exploited in this way, like access to data and stealthy communication channels. The document recommends fixes like Google following standard web protocols and consumers blocking certain agents and cleaning browser histories.Arts railway station tv exp
Arts railway station tv expMezbah Uddin
Ėý
1. ARTS Railway Station TV is a communication medium that displays advertisements and information to passengers at major railway stations in Bangladesh, allowing brands to reach a large captive audience.
2. The screens provide entertainment to passengers while they wait for their trains, helping to make the time pass more pleasantly.
3. Key advantages of this media include compulsory viewing by waiting passengers, an inability to change the channel to avoid ads, and the ability to display train information that passengers often check.2010 za con_jameel_haffejee
2010 za con_jameel_haffejeeJohan Klerk
Ėý
This document introduces PowerShell and explains why hackers should learn it. PowerShell can be used for tasks like port scanning, brute forcing RDP/SQL, dumping password hashes, and quickly setting up backdoors. It comes preinstalled on many modern Windows systems and provides an unchecked environment for accessing and controlling the operating system through commands and scripting. The document demonstrates various hacking techniques that can be accomplished using PowerShell, such as poking the system, checking for open ports, and gaining complete control over servers after initial access.Arts railway station tv exp
Arts railway station tv expMezbah Uddin
Ėý
1) ARTS Railway Station TV is a communication medium that displays advertisements and information to passengers at major railway stations in Bangladesh, allowing brands to reach a large captive audience.
2) The screens provide entertainment to passengers while they wait for their trains, helping to make the time pass more pleasantly.
3) As passengers are required to wait at the station, the screens have a large guaranteed audience with no ability to change the channel, making it an effective advertising medium.Anexo a demanda impugnacion laudo sunat comprimidoPaola Aliaga
Ėý
Anexo a demanda impugnacion laudo sunat comprimido2010 za con_haroon_meer
2010 za con_haroon_meerJohan Klerk
Ėý
This document appears to be a transcript of a talk given by Haroon Meer on October 17, 2010 about issues in the information security industry. Some of the main points discussed include that the infosec industry hides behind "fig leaves" and only fights battles they can kind of win, rather than taking on important problems. Meer argues that people in infosec think they can't write secure code, but some have shown this is possible. He calls for people to work on problems that really matter and produce more original research, rather than just consuming others' work.Cv paola aliaga 21Paola Aliaga
Ėý
Paola Aliaga es una contadora pÚblica con mÃĄs de 17 aÃąos de experiencia en la SUNAT. Es una lÃder sindical que ha representado a trabajadores en varias organizaciones. Tiene especializaciones en fiscalidad internacional y auditorÃa tributaria. Ha participado en foros de diÃĄlogo social y defensa de derechos laborales. Actualmente es dirigente sindical en ejercicio en SUNAT y coordina enlaces con el Consejo de Alto Nivel AnticorrupciÃģn.2010 za con_georg-christian_pranschke
2010 za con_georg-christian_pranschkeJohan Klerk
Ėý
This document discusses SNMP (Simple Network Management Protocol) and how it can be exploited due to misconfigurations. It begins with an overview of SNMP, including how it works and common vulnerabilities. It then focuses on exploiting SNMP on Cisco appliances, describing how community strings can be brute forced to gain privileged access. The document introduces Frisk-0, a tool that automates brute forcing community strings and downloading device configurations. It concludes with recommendations around securing SNMP-enabled devices by changing defaults, using strong community strings, and implementing access control lists.2010 za con_todor_genov
2010 za con_todor_genovJohan Klerk
Ėý
This document provides an overview of DNSSEC (Domain Name System Security Extensions) by a sysadmin who works for an ISP and does a lot of DNS work. It discusses what DNSSEC is (DNS with public key cryptography to authenticate DNS responses), how it works (each zone has public/private keys and all resource records are signed), new resource records introduced by DNSSEC like DNSKEY, RRSIG, DS, and how the chain of trust is established to validate DNS responses by starting with a trust anchor and delegating trust through signed records.2010 za con_jurgens_van_der_merwe
2010 za con_jurgens_van_der_merweJohan Klerk
Ėý
The document discusses Jurgens van der Merwe, a junior analyst at SensePost whose interests include information security, innovative technologies, music, and skateboarding. It then provides an overview of the Selenium browser automation framework, which allows testing of web applications through programmatically controlling browsers. It can automate workflows, extract data from pages, and more. The document discusses some examples of what can be done with Selenium and also addresses some challenges like latency.2010 za con_roelof_temmingh
2010 za con_roelof_temminghJohan Klerk
Ėý
The document discusses several ideas for automated social engineering and Internet scanning techniques, some of which may pose legal or ethical issues. It describes methods like injecting messages into email threads to trick recipients, using personal details gathered from online surveys to test password strength, and performing port scans, traceroutes, and reverse lookups across all IP addresses on the Internet to identify vulnerabilities. One idea involves storing secret messages in the latency of network pipes like satellite links. The document also briefly mentions some work Andrew actually did with natural language processing, Facebook data, and developing tools for a cybersecurity software program.2010 za con_daniel_cuthbert
2010 za con_daniel_cuthbertJohan Klerk
Ėý
The document provides tips for testing the security of banking applications and frameworks. It suggests focusing on business logic flaws, such as manipulating functions to perform unintended tasks or bypass intended flows. Other tips include exploiting flaws in validation routines, manipulating currency values, and "outwitting" developers by finding ways to upload malicious files that may be executed by administrators. The goal is to identify vulnerabilities in these applications, as many offshore development teams and banks still have limited security knowledge.2010 za con_barry_irwin
2010 za con_barry_irwinJohan Klerk
Ėý
1. Conficker, also known as Downup and Downadup, is a computer worm discovered in November 2008 that spread via Windows security vulnerabilities. It infected millions of computers worldwide at its peak.
2. The outbreak began slowly in late 2008 and accelerated in early 2009, as variants Conficker A, B, and C incorporated techniques like domain generation algorithms and peer-to-peer networking to spread. Estimates put global infections between 3-12 million machines by early 2009.
3. Responses included Microsoft forming a "Conficker Cabal" in February 2009 to mitigate the threat, and variants like Conficker C beginning to use 50,000 domain names and peer-to-peer networks to coordinate infected2010 za con_stephen_kreusch
2010 za con_stephen_kreuschJohan Klerk
Ėý
This document provides an overview of data loss prevention (DLP) systems. It defines DLP and describes how it can identify, monitor, and protect data in use, in motion, and at rest. It discusses typical DLP implementations for networks and endpoints/storage and how policies are defined. Common criticisms of DLP are outlined as well as the value it can provide by focusing on data security and improving communication between security and business teams. Lessons learned emphasize the importance of people, process, and technology in DLP deployments.Training management
Training managementMezbah Uddin
Ėý
This document describes a school management system project that aims to ease the academic and management processes for educational institutions. The system allows students to choose from available courses, view course details, and apply for courses online. It includes modules for administration, student registration, attendance tracking, counseling, and updating student information. The project uses technologies like HTML, CSS, PHP, MySQL, and frameworks like Bootstrap. It is intended to benefit schools, universities, students, and parents by facilitating online admission applications and student counseling management.Similar to 2010 za con_ian_de_villiers (20)
Java Serialization Facts and Fallacies
Java Serialization Facts and FallaciesRoman Elizarov
Ėý
The document discusses Java serialization and common myths surrounding it. It summarizes that Java serialization allows for flexible evolution of classes while maintaining backwards compatibility through the use of serialVersionUID. It debunks common myths that Java serialization is slow, inflexible, or that changing private fields breaks compatibility. The document explains that serialization performance depends more on how streams are used rather than the underlying implementation.Java Introduction
Java Introductionsunmitraeducation
Ėý
The document provides an introduction and history of Java, outlining how it was developed in the 1990s as a platform-independent language by James Gosling at Sun Microsystems, and discusses some key advantages of Java like being object-oriented, portable, robust, and having built-in support for security and multithreading. It also describes the Java Development Kit (JDK) which contains tools for developing Java programs and the Java Runtime Environment (JRE) which allows running of Java applications and includes the Java Virtual Machine.Rapid With Spring Roo
Rapid With Spring RooMorten Lileng
Ėý
Roo is a productivity tool that allows for easy creation of Enterprise Java applications. It generates infrastructure code like entities, controllers, and services through simple shell commands. Roo uses AspectJ for automatic code generation and integrates with Spring technologies like dependency injection and MVC. It aims to help developers build RESTful services quickly without needing to write infrastructure code from scratch.java completed units.docx
java completed units.docxSATHYAKALAKSKPRCASBS
Ėý
This document provides an overview of the history and features of the Java programming language. It discusses how Java was originally developed by Sun Microsystems in 1991 and was designed to be portable, simple, reliable and secure. Some key features of Java discussed include its object-oriented nature, portability through bytecode, robustness through features like garbage collection, and support for web-based applications through applets. The document also compares Java to C and C++, noting differences like Java's lack of pointers and multiple inheritance. Finally, it discusses how Java became associated with the Internet and World Wide Web through its use in interactive applets and applications.java full 1.docx
java full 1.docxSATHYAKALAKSKPRCASBS
Ėý
Java was originally developed by Sun Microsystems in 1991 and was originally called Oak. It was designed to be simple, portable, and reliable. Some key features of Java include being platform independent through bytecode, object-oriented design, robust and secure features like memory management and exception handling, and being distributed and interactive through multithreading. Subsequent versions of Java like J2SE 5.0 added additional features like generics and annotations to improve development, and JDBC and XML processing to support databases and web services.java full.docx
java full.docxSATHYAKALAKSKPRCASBS
Ėý
This document provides an overview of the history and features of the Java programming language. It discusses that Java was originally developed by Sun Microsystems in 1991 and was designed to be portable, simple, secure, and robust. Some key features of Java include being object-oriented, platform independent through bytecode compilation, having automatic memory management, and being well-suited for web and internet applications through applets. The document also compares Java to C and C++, noting differences like Java not supporting pointers or multiple inheritance. It describes how Java works with web browsers and HTML to enable interactive content on web pages through applets.java full 1 (Recovered).docx
java full 1 (Recovered).docxSATHYAKALAKSKPRCASBS
Ėý
This document summarizes the evolution of Java, including its origins in 1991, key features like portability and object-orientation, differences from C/C++, and enhancements in later versions. It discusses how Java was designed to be simple, reliable, and portable by compiling to bytecode and avoiding pointers. It also covers Java's support for distributed applications, multithreading, and dynamic features. Later sections summarize additional features introduced in J2SE 5.0 like generics and annotations, as well as enhancements in Java SE 6 like scripting language integration and XML processing.The Java Story
The Java StoryDavid Parsons
Ėý
The document provides an overview of the Java programming language, including its history, key characteristics, and major versions. It began as an object-oriented language created by Sun Microsystems in 1995 to control electronic devices. Java's main advantages are that it is simple, portable, robust, secure, high-performance, and can create distributed applications. It uses a virtual machine to run the same byte code on different operating systems. The document also discusses Java APIs, editions, and learning resources.Curso de ProgramaciÃģn Java Intermedio
Curso de ProgramaciÃģn Java IntermedioUniversidad de Occidente
Ėý
This document is a draft for an intermediate Java programming course, outlining its content, objectives, and key principles of Java technology. It covers topics such as object-oriented programming, Java history, and various Java components, showcasing the language's platform independence and portability across different systems. The material is intended to be a resource for further development and sharing of knowledge in the Java programming community.Introduction to Spring & Spring BootFramework
Introduction to Spring & Spring BootFrameworkKongu Engineering College, Perundurai, Erode
Ėý
Rod Johnson created the Spring Framework, an open-source Java application framework. Spring is considered a flexible, low-cost framework that improves coding efficiency. It helps developers perform functions like creating database transaction methods without transaction APIs. Spring removes configuration work so developers can focus on writing business logic. The Spring Framework uses inversion of control (IoC) and dependency injection (DI) principles to manage application objects and dependencies between them.oop unit1.pptx
oop unit1.pptxsureshkumara29
Ėý
The document discusses the fundamentals of object-oriented programming and Java. It covers key concepts like abstraction, encapsulation, inheritance and polymorphism. It also describes the basic structure of a Java program, including classes, objects, methods and variables. It explains how to set up a Java development environment, compile and run a simple Java program.CS8392 OOP
CS8392 OOPDhanalakshmiVelusamy1
Ėý
This document provides an overview of object-oriented programming concepts in Java including abstraction, encapsulation, inheritance, and polymorphism. It discusses key Java concepts like classes, objects, methods, and access specifiers. It also covers Java fundamentals like variables, data types, operators, control flow statements, comments, and arrays. Additionally, it describes the Java runtime environment, how to set up a Java development environment, compile and run a simple Java program. The document is intended as an introduction to object-oriented programming and the Java programming language.01 java intro
01 java introDeepal Shah
Ėý
Java can be used to create both standalone applications and web applications like applets. It is compiled to bytecode that runs on any system with a Java Virtual Machine, making it cross-platform. The document discusses Java's usage, safety features, performance compared to C++, standard libraries and key packages like JDBC, RMI, Servlets, EJBs, and how to compile and run basic Java programs and applets.Hybernat and structs, spring classes in mumbai
Hybernat and structs, spring classes in mumbaiVibrant Technologies & Computers
Ėý
The document provides an extensive overview of the Spring Framework, detailing its application layering architecture, which separates responsibilities into presentation, service, domain, and persistence layers. It discusses the integration of various components such as dependency injection, aspect-oriented programming (AOP), and DAO support, emphasizing Spring's lightweight nature and its advantages over traditional EJB solutions. The text also highlights Spring's capabilities in simplifying coding practices, enhancing testability, and facilitating the management of business logic in Java applications.Java online training from hyderabad
Java online training from hyderabadrevanthonline
Ėý
This document provides information about Revanth Online Training and their Core Java, Advanced Java, and J2EE online training courses. The Core Java course is 30 hours and covers topics like OOPs, strings, packages, exceptions, multithreading, I/O streams, generics and collections. The Advanced Java course also lasts 30 hours and covers JDBC, servlets, JSP, servers and databases. The 45-hour J2EE course covers topics like RMI, EJB, JNDI, JMS, and more. It provides the course content and duration for each topic.java basics concepts and the keywords needed
java basics concepts and the keywords neededPriyadharshiniG41
Ėý
Java is a purely object-oriented programming language developed by James Gosling and Patrick Naughton at Sun Microsystems, initiated as a project for digital devices in 1991 and renamed from Oak to Java in 1995. It has become widely used for internet programming, mobile applications, and e-business solutions, characterized by its 'write once, run anywhere' capability due to platform independence. Key concepts include the Java Virtual Machine (JVM), which allows Java programs to run on any hardware platform, and core object-oriented principles such as encapsulation, inheritance, and polymorphism.JAVA INTRODUCTION - 1
JAVA INTRODUCTION - 1Infoviaan Technologies
Ėý
Java is an object-oriented programming language that is high-level, robust, secure, portable and multi-threaded. It was developed by James Gosling at Sun Microsystems in the early 1990s. Java code is compiled into bytecode that runs on a Java Virtual Machine (JVM) making Java platform independent. The JVM interprets the bytecode and performs tasks like memory management and security.Introduction to Java 7 (OSCON 2012)
Introduction to Java 7 (OSCON 2012)Martijn Verburg
Ėý
This document provides an overview and agenda for a session on the "Well-Grounded Java Developer". The session will cover introductions to Java 7 features like Project Coin, NIO.2, and Method Handles. It will also cover polyglot and functional programming and modern Java concurrency practices like Fork/Join. The session aims to help developers code more rapidly, concisely, and take advantage of compiler, JVM, and GC improvements in Java 7.GETTING STARTED WITH JAVA(beginner)
GETTING STARTED WITH JAVA(beginner)HarshithaAllu
Ėý
The document provides an introduction to Java, highlighting its features, runtime environment, and installation process. It details the differences between Java and C++, along with new features introduced in various Java versions. Additionally, it covers the structure of Java programs, the role of the Java Virtual Machine (JVM), and tools for Java development.BP-9 Share Customization Best Practices
BP-9 Share Customization Best PracticesAlfresco Software
Ėý
This document outlines best practices for customizing Alfresco Share, focusing on recommendations for methodology, team structure, project organization, and packaging. Key suggestions include using iterative customization processes, dividing teams by tier, and adhering to specific namespace and development tools to ensure effective implementation. The document emphasizes the importance of testing, documentation, and leveraging existing frameworks for successful customization projects.Ad
2010 za con_ian_de_villiers
- 1. The JAR of Joy SensePost - 2010
- 2. `whoami` âĒâŊ SensePost âĒâŊ ian@sensepost.com ââŊBreak some stuff ââŊWrite reports about breaking some stuff ââŊAbuse the staff SensePost - 2010
- 3. Why This Talk ? âĒâŊ import disclaimer; âĒâŊ Not ground breaking stuff â no 0-day âĒâŊ Java applications and applets appear to be popular again âĒâŊ Reversing Java applications can be difficult âĒâŊ Tips for reversing Java in less time (in my experience in any case)âĶ SensePost - 2010
- 4. The JAR File âĒâŊ Java ARchive âĒâŊ Used to distribute Java applications / applets etc. âĒâŊ ZIP file containing compiled classes, libraries, settings, certificates, * âĒâŊ Trivial to extract âĒâŊ Normally disclose a vast amount of information SensePost - 2010
- 5. Attacking Java is fun âĒâŊ Trivial to reverse engineer âĒâŊ Compiled applications are vulnerable to virtually all attacks traditional web apps are vulnerable toâĶ âĒâŊ âĶbut all wrapped up in increased sense of developer smugness âĒâŊ Repurposed Java applications make *awesome* attack tools SensePost - 2010
- 6. Difficulties Attacking Java âĒâŊ Many classes and libraries in JAR files of complex applications âĒâŊ Class files often do not decompile cleanly âĒâŊ Impossible to fix all java sources in large application âĒâŊ Applets and applications are frequently signed âĒâŊ Obfuscated Code âĒâŊ Frequently have to rely on other tools tooâĶ SensePost - 2010
- 7. âĒâŊ Certificate information stored in META-INF âĒâŊ MANIFEST.MF contains hashes for resources âĒâŊ These files can easily be deletedâĶ Defeating Signing SensePost - 2010
- 8. âĒâŊ Now possible to modify classes in JAR file âĒâŊ Signing normally used specifically for Java applets ââŊAllow applets to access network resources ââŊAllow applets to read / write files âĒâŊ However, the applet runs on *my* machine ââŊCan specify own security modelâĶ What this Means SensePost - 2010
- 9. Obfuscation âĒâŊ Defeating Java obfuscation is difficult âĒâŊ Depends on the obfuscation mechanism used âĒâŊ In most cases, virtually impossibleâĶ âĒâŊ âĶ however, the newer attack methodologies outlined later will help âĶbut wait â there is moreâĶ SensePost - 2010
- 10. Obfuscation âĒâŊ A bunch of classes depending on reflection methods and serialized objects can not normally be obfuscatedâĶ âĒâŊ âĶ in obfuscated applications this provides us with a nice area to attack ï SensePost - 2010
- 11. Java Quick Kills âĒâŊ Not necessary to fix all compiler errors âĒâŊ Only need to fix specific classes with functionality you need ââŊSanitisation libraries ââŊNetwork Stream libraries âĒâŊ Updated classes can be recompiled with the original JAR file to satisfy dependancies SensePost - 2010
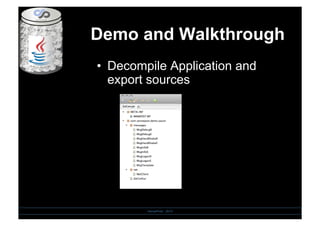
- 12. Demo and Walkthrough SensePost - 2010 âĒâŊ Decompile Application and export sources
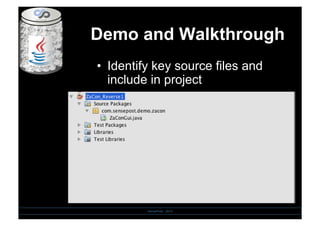
- 13. Demo and Walkthrough SensePost - 2010 âĒâŊ Identify key source files and include in project
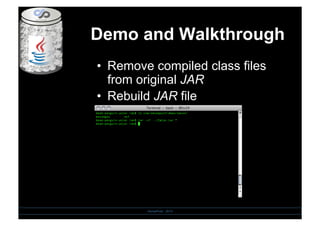
- 14. Demo and Walkthrough SensePost - 2010 âĒâŊ Remove compiled class files from original JAR âĒâŊ Rebuild JAR file
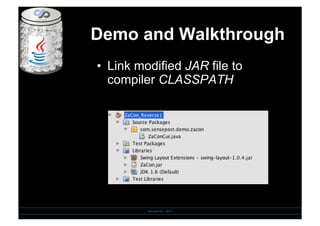
- 15. Demo and Walkthrough SensePost - 2010 âĒâŊ Link modified JAR file to compiler CLASSPATH
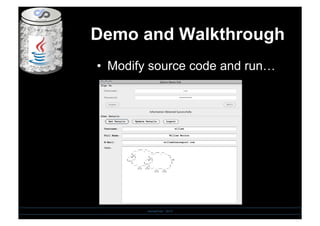
- 16. Demo and Walkthrough SensePost - 2010 âĒâŊ Modify source code and runâĶ
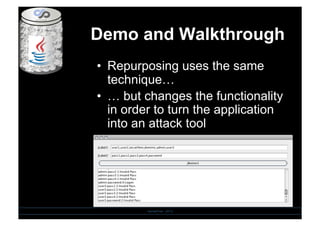
- 17. Demo and Walkthrough SensePost - 2010 âĒâŊ Repurposing uses the same techniqueâĶ âĒâŊ âĶ but changes the functionality in order to turn the application into an attack tool
- 18. Newer Attack Methods âĒâŊ New research and toolsets make reversing and recompiling unneccessaryâĶ ï âĒâŊ Also make it easier to attack obfuscated applications âĒâŊ Cannot always be used for repurposing ï SensePost - 2010
- 19. BlackHat Europe â 2010 âĒâŊ Manish Saindane ââŊ Demonstrated attacks against serialized objects ââŊ Provided Burp plug-in to view and modify serialized objects http://www.blackhat.com/html/bh-eu-10/bh-eu-10-archives.html SensePost - 2010
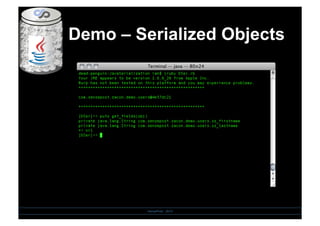
- 20. Demo â Serialized Objects SensePost - 2010
- 21. BlackHat Las Vegas â 2010 âĒâŊ Arshan Dabirsiaghi ââŊ JavaSnoop : How to Hack Anything Written in Java âĒâŊ Stephen de Vries ââŊ Hacking Java Clients âĒâŊ Both talks outlined new methods for attacking Java Applications http://www.blackhat.com/html/bh-us-10/bh-us-10-archives.html SensePost - 2010
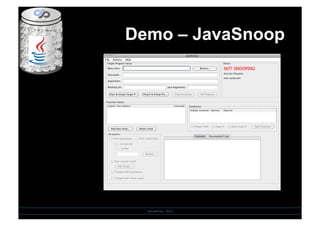
- 22. Demo â JavaSnoop SensePost - 2010
- 23. In Summary âĒâŊ Java reversing is fun âĒâŊ Java reversing can be easy âĒâŊ Newer attack methodologies no longer require attackers to reverse the application âĒâŊ Traditional reversing techniques still normally apply for repurposing applications SensePost - 2010
- 24. Ta Muchly âĒâŊ ZaCon folkses ï SensePost - 2010