2016 Presentation Module Wind River Overview FINAL.pptx
- 1. ? 2016 Wind River. All Rights Reserved. 2015 to 2020: Expanding to 5 Billion Devices over the Next Five Years PresenterĪ»s Name PresenterĪ»s Organization
- 2. 2 ? 2016 Wind River. All Rights Reserved. Cover Option 1 2015 to 2020: Expanding to 5 Billion Devices over the Next Five Years
- 3. 3 ? 2016 Wind River. All Rights Reserved. HERITAGE ? 1981: Founded ? 1993: IPO ? 2009: Acquired SCALE ? 1,500+ Employees ? Presence in 20 countries LEADERSHIP ? Leading Commercial Operating System Market Share ? Broadest Portfolio INVESTMENT ? 30+% of Annual Spend Is on R&D ? Rich History of M&A For over 30 years, Wind River has helped the world's most recognizable brands power generation after generation of embedded devices.
- 4. 4 ? 2016 Wind River. All Rights Reserved. Delivering Results for the Biggest Brands in the World Applied Signal BAE Systems Boeing EADS Elbit Group Finmeccanica General Dynamics General Electric Harris Honeywell ITT Alcatel- Lucent ARRIS Avaya Ciena Dialogic Ericsson Fujitsu GENBAND Hitachi ABB Agilent AREVA Bombardier Emerson Electric General Electric Hitachi Medical Invensys KUKA Mitsubishi Industrial Dell Epson Fuji-Xerox IBM Konica Minolta LG Electronics NEC Oki Aerospace and Defense Network Infrastructure Industrial and Medical Mobile and Consumer AWTC Europe BMW Bosch Clarion Continental Daimler Delphi Fiat Fujitsu General Motors Automotive L-3 Communications Lockheed NASA Northrop Grumman Orbital Sciences Raytheon Rockwell Collins Thales U.S. Navy Harmann HKMC Honda Johnson Controls Mobis Nissan PSA Peugeot Citroen Renault Toyota Valeo Group Huawei Hypercom Kapsch Kyocera Motorola NEC Nokia Samsung Tellabs ZTE Mitsubishi Electric Nikon Panasonic Philips Medical Rockwell Automation Schneider Electric Siemens Sirona Dental Systems Toshiba Prima Cinema Qualcomm Ricoh Samsung Sharp SK Telecom Sony Texas Instruments Toshiba Xerox
- 5. 5 ? 2016 Wind River. All Rights Reserved. Our software has been deployed in over 2 billion devices; into environments, systems, and applications subject to the highest standards of safety, security, and performance.
- 6. 6 ? 2016 Wind River. All Rights Reserved. Our software has been deployed in over 2 billion devices; into environments, systems, and applications subject to the highest standards of safety, security, and performance. Read one line of the slide, it will auto advance:
- 7. 7 ? 2016 Wind River. All Rights Reserved. Our software has been deployed in over 2 billion devices; into environments, systems, and applications subject to the highest standards of safety, security, and performance.
- 8. 8 ? 2016 Wind River. All Rights Reserved. Our software has been deployed in over 2 billion devices; into environments, systems, and applications subject to the highest standards of safety, security, and performance.
- 9. ? 2016 Wind River. All Rights Reserved. An Intel Company Make the reality of a software-defined world safe, secure and reliable. Transform our customerĪ»s business to deliver the promise of a software-defined world. WE ASPIRE TO . . . OUR FOCUS IS TO . . . 9
- 10. 10 ? 2016 Wind River. All Rights Reserved. The Internet of Things
- 11. 11 ? 2016 Wind River. All Rights Reserved. 11 ? 2016 Wind River. All Rights Reserved. IoT in 2014 : The Peak of Inflated Expectations Are you ready to ride the wave? We were here
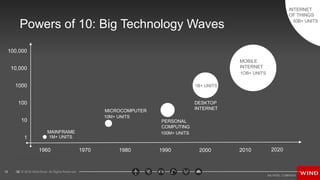
- 12. 12 ? 2016 Wind River. All Rights Reserved. 12 Powers of 10: Big Technology Waves 100,000 1 10 100 1000 10,000 1960 1970 1980 1990 2000 2010 MAINFRAME 1M+ UNITS MICROCOMPUTER 10M+ UNITS PERSONAL COMPUTING 100M+ UNITS DESKTOP INTERNET 1B+ UNITS 2020 MOBILE INTERNET 1OB+ UNITS INTERNET OF THINGS 50B+ UNITS SOURCES: KPCB, ITU, MS RESEARCH 12
- 13. 13 ? 2016 Wind River. All Rights Reserved. Favorable Conditions: Why Now? 13 ? 2016 Wind River. All Rights Reserved. COST OF PROCESSING 60X PAST 10 YEARS COST OF SENSORS 2X PAST 10 YEARS COST OF BANDWIDTH 40X PAST 10 YEARS
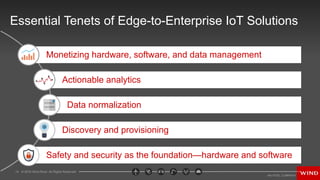
- 14. 14 ? 2016 Wind River. All Rights Reserved. Essential Tenets of Edge-to-Enterprise IoT Solutions Monetizing hardware, software, and data management Actionable analytics Data normalization Discovery and provisioning Safety and security as the foundationĪ¬hardware and software
- 15. 15 ? 2016 Wind River. All Rights Reserved. For over 30 years, Wind River has partnered with our customers to lock down their machine data. How will we help our customers unlock that machine data to safely and securely capitalize on the IoT opportunity? ? 2016 Wind River. All Rights Reserved. 14
- 16. 16 ? 2016 Wind River. All Rights Reserved. 16 ? 2016 Wind River. All Rights Reserved. 50% of the worldĪ»s energy will be delivered by systems running Wind River technology. 85% of all commercial flight will take place on aircraft powered by Wind River. Wind River technology will power over 1M unmanned air, sea, and ground vehicles. Wind River will enable the virtualization of 50% of all purpose-built network elements. 125 million vehicles will leverage Wind River technology under the hood and in the cockpit. The number of developers building on our platform will increase by a factor of 10. Wind River will connect 50 million legacy devices through our gateway platforms. We will become the de facto standard for IMA implementations. We will expand our manned aircraft leadership into critical and autonomous unmanned systems. When NFV is in broad deployment in 2017, Wind River will be in 50% of implementations. We will be a key provider of software into all connected dashes and intelligent auto platforms. HereĪ»s how weĪ»ll do it: Wind River will simulate each of these systems and devices in the cloud.
- 17. 17 ? 2016 Wind River. All Rights Reserved. 17 ? 2016 Wind River. All Rights Reserved. In other words, in five short years we expect to capture 10% of the emerging IoT market that analysts predict will create 10 to 20 trillion dollars in value.
- 18. 18 ? 2016 Wind River. All Rights Reserved. There Are Two Types of IoT Consumer Commercial
- 19. We are laser-focused on those markets where our DNA is closely aligned with the value proposition of our customers. 19 ? 2016 Wind River. All Rights Reserved.
- 20. 20 ? 2016 Wind River. All Rights Reserved. Aerospace & Defense TAM $2.017B SAM: $561M Automotive Industrial Network Infrastructure TAM $500M SAM: $240M TAM $450M SAM: $130M TAM $450M SAM: $140M 19 ? 2016 Wind River. All Rights Reserved.
- 21. 21 ? 2016 Wind River. All Rights Reserved. Two Business Interests Driving IoT Demand Business Optimization ? Maximizing value of existing assets and investments ? Introduction of new efficiencies ? Positive shifts in OpEx and CapEx Business Transformation ? Access to new revenue streams ? Transitioning business models ? Positive shifts in value creation and value capture
- 22. 22 ? 2016 Wind River. All Rights Reserved. Where are you on the path? 22 ? 2016 Wind River. All Rights Reserved.
- 23. ? 2016 Wind River. All Rights Reserved. Thank you
Editor's Notes
- #2: NB: Critical themes in this sequence are Standards and Certification. Stress these themes. Read one line of the slide, it will auto advance: Our software has been deployed in over two billion devices
- #3: Read the slide: For over thirty years, Wind River has helped the world's most recognizable brands power generation after generation of embedded devices. Color spot: We spend more on R&D than our nearest embedded competitorĪ»s revenue; relative to the size of our market, we spend a lot.
- #5: NB: Critical themes in this sequence are Standards and Certification. Stress these themes. Read one line of the slide, it will auto advance: Our software has been deployed in over two billion devices
- #6: Read this line of the slide, it will auto advance: into environments, systems, and applications
- #7: Read this line of the slide, it will auto advance: subject to the highest standards of safety
- #8: Read this line of the slide, and then youĪ»ll need to click: safety, security, and performance. Next slide: Our world is changingĪŁ
- #9: read the slide
- #10: Because the Internet of Things is already changing the world. The world of tech, the world of business.
- #11: Last year Gartner placed IoT at the top of their Hype Cycle; Gartner calls this Ī░The Peak of Inflated ExpectationsĪ▒. Up next? Ī░The Trough of DisillusionmentĪ▒: this is where the hype around a technology falls away, and the hard work of delivering on the promise of a technology sets in. EveryoneĪ»s tired of hearing about it, and they want to start seeing impact. Business impact. ThatĪ»s the step our industry needs to take before we can reach the Ī░Plateau of ProductivityĪ▒, that long tail running off to the right of the Hype Cycle. Reasonable people can debate where IoT is on the Hype Cycle, or how prepared one company is to capitalize on IoT vs. anotherĪŁ. But the question everyone needs to ask themselves isĪŁ Are you ready to ride the wave?
- #12: Because that wave will be *big*. In all likelihood bigger than any analyst or company has yet predicted. This next significant wave of technological advancement and innovation will arrive in just five years. Over the last 50 years, weĪ»ve seen each successive era of computing act as a 10x multiplier in terms of units shipped. Interestingly, the rate at which these waves of technology are arriving appears to be accelerating. If this pattern holds true, the 50B device estimates for the The Internet of Things by 2020 will be just the beginning. And Ī░Units shippedĪ▒ is just one part of the reason why IoT is generating *so much hype*ĪŁ.
- #13: In addition to the emergence of necessary technologies, including IPv6 (which provides enough potential IP addressability for every atom on earth 100 times over) weĪ»ve seen costs fall dramatically for the critical ingredients of the IoT era: cost, sensors, and bandwidth.
- #14: Safety and Security With IoT in the commercial space bringing intelligence and data-responsive capabilities to critical infrastructure, the need for Safety and Security approaches that work from hardware on up through system of systems is paramount. Specific Safety Examples: Vehicle to Infrastructure or Vehicle to Vehicle connectivity, Smart Manufacturing scenarios involving heavy machinery handling in environments where people are present, Smart Building scenarios in which basic aspects of the way that people live and work are increasingly automated and/or managed through virtual interfaces rather than physical ones. Specific security examples: Discovery and Partitioning Discovery being the process of one or or more types of cloud locating a new device as it comes online, and provisioning being the process of that device being supplied with the connectivity and access it is entitled to on a given network or in a given environment. Safety and Security must remain paramount even as new paradigms for device discovery and provisioning emerge, and Cloud Operators and Device Manufacturers push toward aggressive targets for the seamlessness and duration of the discovery and provisioning process. Data Normalization The capacity to unlock machine data on devices which may or may not be IP Addressable, to assess and validate that data, supply it with necessary meta data, and deliver structured, enriched data to enterprise systems safely and securely. Gateways play a critical role in this step, and while the process seems straightforward only 85% of todayĪ»s data is structured in this way and many brownfield systems are characterized in part by the extent to which theyĪ»ve locked that machine data down. Actionable Analytics Actionable Analytics: interpreting data in real-time or through in order to derive insights that can be acted on to transform or optimize your business, may require leveraging or supplementing our customerĪ»s proprietary algorithms in order to deliver value. While basic analytics capabilities are readily available through commercial or open source channels, these donĪ»t always reflect the decades of proprietary insight into device or machine performance that a manufacturer has developed on their own. Monetizing Finally, youĪ»ll need a monetization strategy for IoT that is consistent with your business objectives. This may involve monetizing data or cloud-based compute/control, shifting from hardware sales to Ī░As a ServiceĪ▒ models, or other approaches.
- #15: So, whatĪ»s wind river doing to help our customers take advantage of these conditions? Unlocking machine data
- #16: Maybe a Grey Mask over this?
- #18: We know there are two broad fields of play in IoT. Consumer: characterized by things like the Nest thermostat, wearables, smart refrigerators, and so on. Commercial characterized by the sorts of devices Wind River has focused on for 30 years now: Smart Factory, Smart City, Smart Transportation, and the next generation of Intelligent Systems for Aerospace and Defense, Unmanned, and Civil Avionics. WeĪ»re focused on the commercial segment of the IoT market.
- #22: Have this conversation.