ÖÐÎÄ3
1 like432 views
ÎĵµÌṩÁËһЩÓë¼ÒÍ¥³ÉÔ±ºÍÖ°ÒµÏà¹ØµÄÖÐÎĴʻ㡣Ìáµ½Á˲»Í¬¼ÒÍ¥³ÉÔ±µÄÃû³ÆÒÔ¼°ËûÃÇ¿ÉÄܵŤ×÷³¡Ëù¡£»¹Éæ¼°Á˼¸¸öµØ·½µÄ´óѧÃû³Æ¡£
1 of 34































Ad
Recommended
Chinese link textbook Lesson 6 dialogue language in use
Chinese link textbook Lesson 6 dialogue language in use Joanne Chen
?
±¾Îļþ½éÉÜÁËÖÐÎĿγ̵ÚÁù¿ÎµÄ¼ÒÍ¥Ö÷Ì⣬°üÀ¨¼ÒÍ¥³ÉÔ±µÄ»ù±¾´Ê»ãºÍÓ÷¨¡£Í¨¹ýÒ»¶Î×ÔÎÒ½éÉÜ£¬Ñ§Éú½²ÊöÁËËýµÄ¼ÒÍ¥±³¾°ºÍ³ÉÔ±Çé¿ö¡£ÎÄÖл¹²¹³äÁ˶ÔÓÚ¼ÒÍ¥¡¢¹¤×÷ºÍ³èÎïµÄÏà¹Ø¾äÐͺʹʻ㡣ESS project ¨C technical and conceptual challenges
ESS project ¨C technical and conceptual challengesGlobal Risk Forum GRFDavos
?
The document outlines the requirements for the IDRC-ESS project, emphasizing the need for real-time data integration from various sources like sensors and human intelligence for effective disaster management. It describes the infrastructure as independent, user-friendly, and adaptable for different user interfaces and communication channels. The project is partially funded by the European Commission under a specific grant agreement aimed at enhancing security measures.The 129 Greatest Sales Strategists, Entrepreneurs, and Podcasters to Follow T...
The 129 Greatest Sales Strategists, Entrepreneurs, and Podcasters to Follow T...Carolyn Rose Kick
?
The document lists 129 influential sales strategists, entrepreneurs, and podcasters to follow, detailing their contributions, expertise, and insights into sales and entrepreneurship. It includes prominent figures such as Anneke Seley, Aaron Ross, and Trish Bertuzzi among others, providing a brief overview of their work and the value they offer through blogs, tweets, and podcasts. The list is divided into categories, showcasing not just sales experts but also founders, angel investors, and venture capitalists, emphasizing their roles in shaping industry trends.Query-Driven Visualization in the Cloud with MapReduce
Query-Driven Visualization in the Cloud with MapReduce University of Washington
?
This document discusses query-driven visualization in the cloud using MapReduce. It begins by explaining how all science is reducing to a database problem as data is acquired en masse independently of hypotheses. It then discusses why visualization and a cloud approach are useful before reviewing relevant technologies like relational databases, MapReduce, GridFields mesh algebra, and VisTrails workflows. Preliminary results are shown for climatology queries on a shared cloud and core visualization algorithms on a private cluster using MapReduce.Visibility
VisibilitySteven Casey
?
Visibility is a key concern for industrial vehicle designers. It requires thorough analysis of operator tasks and visual needs, active design techniques to improve visibility, and testing with operators. A mining shovel operator emphasizes that visibility is critical to safely and efficiently perform complex tasks. While standards provide minimum requirements, optimizing visibility yields innovative designs that enhance job performance.NewResume
NewResumeJessica Johnson
?
This resume is for Jessica Lynn Johnson, who has experience as an office manager for used car dealerships and possesses skills in areas like customer service, accounting, inventory control, and supervision. She currently works as a cleaner but has over 10 years of experience managing offices for auto-related businesses, demonstrating proficiency with QuickBooks, payroll, scheduling, and managing employees. Her education includes a high school diploma and some pre-law studies.iWelcome case study: ThiemeMeulenhoff - Digital transformation for publisher...
iWelcome case study: ThiemeMeulenhoff - Digital transformation for publisher...Maarten Stultjens
?
Thiememeulenhoff is transitioning from a traditional educational publisher to a digital learning design company, aiming to create a comprehensive learning infrastructure for millions of users. With the help of iwelcome, they are implementing a robust identity and access management solution that ensures secure and scalable access for students and teachers, compliant with EU privacy regulations. This new digital platform not only improves accessibility but also paves the way for future product development and enhanced educational experiences.Health inequalities related to the gender division of working-time in Europe
Health inequalities related to the gender division of working-time in Europesophieproject
?
This document outlines a presentation on health inequalities related to gender differences in working time in Europe. It discusses how welfare state regimes influence the gender division of labor, family roles, and working hours. Research presented found that long working hours and family demands were associated with poorer health, especially for women in Continental and Southern European countries. Nordic and Eastern European countries saw fewer associations between working hours/family demands and health outcomes for both men and women. The conceptual framework examines how welfare states, labor markets, family models, and public services influence the gender division of work and health.Cognitive & Language Development
Cognitive & Language DevelopmentANiS ADiBaH
?
This document discusses suitable activities for cognitive and language development in infants and toddlers. It recommends games, music, art, reading, and hands-on activities. Specific examples of activities are given, such as peek-a-boo, block play, and obstacle courses to develop motor skills. Music is said to build movement and rhythm skills. Art helps with expression and language. Reading exposes children to books and stories. Hands-on activities satisfy curiosity about the environment. The document emphasizes that these activities should be developmentally appropriate and help children's cognitive development.ThreadFix and SD Elements Unifying Security Requirements and Vulnerability Ma...
ThreadFix and SD Elements Unifying Security Requirements and Vulnerability Ma...Denim Group
?
The document discusses the integration of SD Elements and Threadfix for managing security requirements and vulnerabilities throughout the software development lifecycle, emphasizing the importance of early detection of security issues to reduce costs. It outlines the process of identifying threats and countermeasures, the efficiency of automation, and the business value gained from using these tools. Additionally, it highlights the benefits of prioritization and compliance reporting through these integrated systems.HTML5 Top 10 Threats - Silent Attacks and Stealth Exploits
HTML5 Top 10 Threats - Silent Attacks and Stealth ExploitsShreeraj Shah
?
This document discusses the top 10 threats posed by HTML5, including stealth attacks and silent exploits. It describes how Cross-Site Request Forgery (CSRF) attacks can be conducted using XMLHttpRequest (XHR) calls and bypassing Cross-Origin Resource Sharing (CORS) protections. It also explains how XHR allows cross-domain requests and binary data transfers, which can enable CSRF and information harvesting attacks. The document provides examples of how CSRF can be used over XHR to perform unauthorized actions on a user's behalf without their knowledge.Application Security Guide for Beginners
Application Security Guide for Beginners Checkmarx
?
The document provides an overview of application security concepts and terms for beginners. It defines key terms like the software development lifecycle (SDLC) and secure SDLC, which incorporates security best practices into each stage of development. It also describes common application security testing methods like static application security testing (SAST) and dynamic application security testing (DAST). Finally, it outlines some common application security threats like SQL injection, cross-site scripting, and cross-site request forgery and their potential impacts.Terrorism in fata,Pakistan
Terrorism in fata,PakistanComsats Universoty Islamabad
?
The document provides information on terrorism in the Federally Administered Tribal Areas (FATA) of Pakistan. It discusses the geography of FATA, major militant groups operating there like Tehrik-i-Taliban Pakistan, Lashkar-e-Islam and Jamaat-ul-Ahrar, military operations against these groups, and root causes of militancy such as weak governance and proximity to conflict in Afghanistan.Running a High-Efficiency,
High-Visibility Application Security Program with...
Running a High-Efficiency,
High-Visibility Application Security Program with...Denim Group
?
This document discusses the state of application security and the integration of Prevoty's runtime application self-protection (RASP) technology with Threadfix to enhance vulnerability management. It highlights the rising attacks on web applications and the backlog of vulnerabilities that organizations face, emphasizing the need for modern security practices. Additionally, it outlines the benefits of RASP in providing real-time protection and insights into application threats.European fund market mid year review 2015
European fund market mid year review 2015Jerome Couteur
?
The mid-year review of the European fund market for 2015 highlights a volatile landscape marked by both high net sales of €80bn in April and significant redemptions in June, resulting in a total of €227bn net flows, down 14% from the previous year. Mixed asset products emerged as the most successful asset class, driven by retail savers seeking yield, while passive funds, though growing in net sales share, still accounted for only a small portion of total assets under management. Key markets like Italy and Spain show promising trends, with firms like BlackRock leading inflows amidst a competitive environment for retail investors.More Related Content
Viewers also liked (7)
Cognitive & Language Development
Cognitive & Language DevelopmentANiS ADiBaH
?
This document discusses suitable activities for cognitive and language development in infants and toddlers. It recommends games, music, art, reading, and hands-on activities. Specific examples of activities are given, such as peek-a-boo, block play, and obstacle courses to develop motor skills. Music is said to build movement and rhythm skills. Art helps with expression and language. Reading exposes children to books and stories. Hands-on activities satisfy curiosity about the environment. The document emphasizes that these activities should be developmentally appropriate and help children's cognitive development.ThreadFix and SD Elements Unifying Security Requirements and Vulnerability Ma...
ThreadFix and SD Elements Unifying Security Requirements and Vulnerability Ma...Denim Group
?
The document discusses the integration of SD Elements and Threadfix for managing security requirements and vulnerabilities throughout the software development lifecycle, emphasizing the importance of early detection of security issues to reduce costs. It outlines the process of identifying threats and countermeasures, the efficiency of automation, and the business value gained from using these tools. Additionally, it highlights the benefits of prioritization and compliance reporting through these integrated systems.HTML5 Top 10 Threats - Silent Attacks and Stealth Exploits
HTML5 Top 10 Threats - Silent Attacks and Stealth ExploitsShreeraj Shah
?
This document discusses the top 10 threats posed by HTML5, including stealth attacks and silent exploits. It describes how Cross-Site Request Forgery (CSRF) attacks can be conducted using XMLHttpRequest (XHR) calls and bypassing Cross-Origin Resource Sharing (CORS) protections. It also explains how XHR allows cross-domain requests and binary data transfers, which can enable CSRF and information harvesting attacks. The document provides examples of how CSRF can be used over XHR to perform unauthorized actions on a user's behalf without their knowledge.Application Security Guide for Beginners
Application Security Guide for Beginners Checkmarx
?
The document provides an overview of application security concepts and terms for beginners. It defines key terms like the software development lifecycle (SDLC) and secure SDLC, which incorporates security best practices into each stage of development. It also describes common application security testing methods like static application security testing (SAST) and dynamic application security testing (DAST). Finally, it outlines some common application security threats like SQL injection, cross-site scripting, and cross-site request forgery and their potential impacts.Terrorism in fata,Pakistan
Terrorism in fata,PakistanComsats Universoty Islamabad
?
The document provides information on terrorism in the Federally Administered Tribal Areas (FATA) of Pakistan. It discusses the geography of FATA, major militant groups operating there like Tehrik-i-Taliban Pakistan, Lashkar-e-Islam and Jamaat-ul-Ahrar, military operations against these groups, and root causes of militancy such as weak governance and proximity to conflict in Afghanistan.Running a High-Efficiency,
High-Visibility Application Security Program with...
Running a High-Efficiency,
High-Visibility Application Security Program with...Denim Group
?
This document discusses the state of application security and the integration of Prevoty's runtime application self-protection (RASP) technology with Threadfix to enhance vulnerability management. It highlights the rising attacks on web applications and the backlog of vulnerabilities that organizations face, emphasizing the need for modern security practices. Additionally, it outlines the benefits of RASP in providing real-time protection and insights into application threats.European fund market mid year review 2015
European fund market mid year review 2015Jerome Couteur
?
The mid-year review of the European fund market for 2015 highlights a volatile landscape marked by both high net sales of €80bn in April and significant redemptions in June, resulting in a total of €227bn net flows, down 14% from the previous year. Mixed asset products emerged as the most successful asset class, driven by retail savers seeking yield, while passive funds, though growing in net sales share, still accounted for only a small portion of total assets under management. Key markets like Italy and Spain show promising trends, with firms like BlackRock leading inflows amidst a competitive environment for retail investors.ÖÐÎÄ3
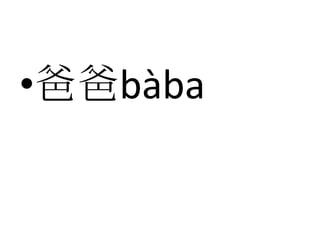
- 2. °Ö°Ö²ú¨¤²ú²¹
- 4. ÂèÂè³¾¨¡³¾²¹
- 6. ¸ç¸ç²µ¨¥²µ±ð
- 10. ÃÃÃ󾨨¾±³¾±ð¾±
- 11. El ni?opeque?o
- 12. µÜµÜ»å¨¬»å¾±
- 14. Ò¯Ò¯²â¨¦²â±ð
- 16. ÄÌÄ̲Ԩ£¾±²Ô²¹¾±
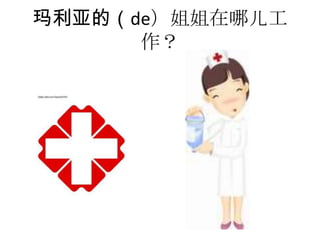
- 22. Ò½Ôº²â¨©²â³Ü¨¤²Ô
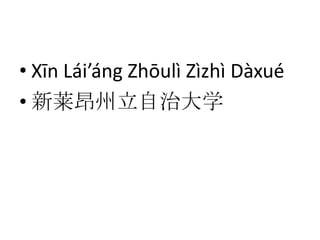
- 33. Universidad Aut¨®noma de Nuevo Le¨®n