3.acknowledgement (gi fi technology)
0 likes122 views
This report summarizes work completed over the past week with help from many individuals. Specifically, the report thanks Professor Mohammad Asif for guidance and support, including allowing extended work in the lab. The department professors and fellow students are also thanked for their valuable guidance and encouragement. Finally, the computer engineering department is thanked for providing excellent facilities.
1 of 2
Download to read offline


Recommended
Gifi



GifiNaga Dinesh
╠²
Gi-Fi allows for wireless transfer of audio and video data at up to 5GB per second within an indoor environment of around 10 meters. It uses a single-chip transceiver operating on the 60GHz band with CMOS processing, providing high-speed data transfer, low power consumption, high security, and cost-effectiveness. Within five years, Gi-Fi is expected to become the dominant wireless networking technology, fully mobile and providing low-cost, high-speed broadband access for transferring large files within seconds to develop wireless homes and offices of the future.Gi fi ppt



Gi fi pptAffan Ahmad
╠²
Gi-Fi is a new wireless technology with less power consumption and ten times faster than the existing technologies.LI FI smart technology by DEBRAJ 



LI FI smart technology by DEBRAJ DebrajMajumdar2
╠²
Li-Fi is a wireless optical networking technology that uses light-emitting diodes (LEDs) for data transmission. It was originally proposed by Professor Harald Haas from the University of Edinburgh. Li-Fi uses visible light communication and is similar to Wi-Fi but instead of radio waves, it uses LED light bulbs and light receivers to transmit data. The technology works by rapidly modulating the LED bulbs faster than what the human eye can detect. Li-Fi has advantages over Wi-Fi like higher speed potential of over 1Gbps, more secure transmission, and no interference with other wireless devices. Some challenges are light cannot pass through objects and developing two-way transmission between devices.Presentation on Gi-Fi



Presentation on Gi-FiNitesh Sah
╠²
The document discusses Gi-Fi technology, a new wireless technology that operates at 60GHz and allows data transfer speeds up to 5GB per second. It provides an introduction to Gi-Fi, compares it to existing technologies like Bluetooth and Wi-Fi, discusses its architecture featuring a single-chip transceiver and how it works. Potential applications of Gi-Fi technology include wireless personal area networks, inter-vehicle communication, and high-speed transfer of large files like videos. Gi-Fi offers benefits over existing technologies like higher speeds, lower power consumption, and is expected to become the dominant wireless networking technology within five years.wireless technology Gi_Fi



wireless technology Gi_FiMuhammed Abdulmahdi
╠²
Gi-Fi is a new wireless technology that offers faster data transfer speeds than Wi-Fi. It uses integrated transceiver chips and small antennas to transmit data at 5 Gbps using the 60GHz frequency band. This allows large files to be transferred within seconds. Gi-Fi has advantages over older technologies like Bluetooth and Wi-Fi in that it provides higher speeds at lower power consumption and cost for short-range communication. Potential applications of Gi-Fi include wireless homes/offices, fast video transfers between devices, and use in household and office appliances. The document predicts that Gi-Fi will become the dominant wireless technology within 5 years.GiFi 



GiFi Muhammed Abdulmahdi
╠²
Gi-Fi is a new wireless technology that offers faster data transfer speeds than Wi-Fi. It uses integrated transceiver chips and small antennas to transmit data at 5 Gbps within seconds. Gi-Fi operates at 60GHz which enables high-speed data rates and transfer of large files. It has advantages over Wi-Fi such as lower power consumption and cost for short-range communication. Gi-Fi is expected to become the dominant wireless technology within 5 years, enabling wireless homes and offices of the future with easy transfer of videos and files.Presentation.pptx



Presentation.pptxAjaySahre
╠²
This document summarizes a seminar presentation on Gi-Fi technology. Gi-Fi is a new wireless technology that operates at 60GHz and allows data transfer rates up to 5 gigabits per second, which is 10 times faster than existing Wi-Fi. It was developed in Australia to overcome the low speeds and high power consumption of Bluetooth and Wi-Fi. The presentation covers the network evolution, advantages of Gi-Fi over other technologies, its architecture and working mechanism, applications like wireless home networks, and the expectation that Gi-Fi will become the dominant wireless standard in the coming years.Gi fi technology ppt



Gi fi technology pptHaripriya Manne
╠²
Gi-Fi is a wireless technology that operates at 60 GHz and allows data transfer speeds of up to 5 gigabits per second within a 10 meter range. It has several advantages over existing wireless technologies like Bluetooth and Wi-Fi, including significantly higher speeds of 5 gigabits per second compared to Bluetooth's 800kbps and Wi-Fi's maximum of 11Mbps. Gi-Fi also uses less power and has a smaller chip size. Potential applications of Gi-Fi include wireless transfer of audio and video data for household appliances, offices, and between vehicles. Researchers expect Gi-Fi to become the dominant wireless technology for networking within five years.Gifi



GifiAishwarya Saseendran
╠²
Gi-Fi is a new wireless technology that provides gigabit wireless data transfer speeds of up to 5Gbps using the 60GHz frequency band. It has several advantages over existing wireless technologies like Bluetooth and Wi-Fi, providing 10 times faster speeds while using only 2mW of power. Potential applications of Gi-Fi include high-speed file transfers for households and offices as well as uses in inter-vehicle communication systems.A Seminar Report On Gi-Fi Technology



A Seminar Report On Gi-Fi TechnologyKate Campbell
╠²
This document provides information about Gi-Fi technology through a seminar report. It begins with an acknowledgment section thanking various people for their support and contributions. It then includes an introduction outlining why Gi-Fi was introduced as an improvement over existing wireless technologies like Wi-Fi and Bluetooth that have slower speeds and higher power consumption. The main body of the report describes what Gi-Fi is, its architecture, how it works at 60GHz using time-division duplexing, and its key advantages like speeds of 5Gbps, low power consumption, high security, low cost and small size. Features of the IEEE 802.15.3C standard are also summarized.wifi versus gifi



wifi versus gifiJYOTI KHICHI
╠²
The document is a seminar report on Gi-Fi technology. It discusses the advantages of Gi-Fi over existing wireless technologies like Wi-Fi and Bluetooth, which have slower data transfer speeds. Gi-Fi allows wireless transfer of data at speeds up to 5 gigabits per second using the 60GHz frequency band and integrated transceiver chips. It has applications in high-speed transfer of videos and files between devices in homes, offices, and vehicles. Within 5 years, Gi-Fi is expected to become the dominant technology for wireless networking due to its high speeds, low power consumption, and low cost.Cse gi-fi-technology-report



Cse gi-fi-technology-reportaswath babu
╠²
This document provides information about Gi-Fi technology through a seminar report. It begins with an acknowledgment section thanking various people for their support and contributions. It then includes an introduction outlining why Gi-Fi was introduced as an improvement over existing wireless technologies like Wi-Fi and Bluetooth that have slower speeds and higher power consumption. The main body of the report describes what Gi-Fi is, its architecture, how it works at 60GHz using time-division duplexing, and its key advantages like speeds of 5Gbps, low power consumption, high security, low cost and small size. Features of the IEEE 802.15.3C standard are also summarized.Gi fi technology



Gi fi technologyvalentino jesse
╠²
The document discusses Gi-Fi or gigabit wireless technology, which allows wireless transfer of data at speeds up to 5 gigabits per second using the 57-64GHz frequency band. It operates on a single chip using CMOS processing and costs one-tenth of current wireless technologies. The document covers Gi-Fi features and applications, compares it to Wi-Fi and Bluetooth, and concludes that Gi-Fi will dominate wireless networking within 5 years by providing low-cost, high-speed connectivity for wireless homes and offices.Gifi



GifiSara Tazeen Mahjoor
╠²
This document discusses next generation wireless technology called Gi-Fi or Gigabit Wireless. Gi-Fi allows wireless transfer of data at speeds up to 5 gigabits per second using the 60GHz frequency band. It was developed by Professor Stan Skafidis of Melbourne University to overcome limitations of existing technologies like Bluetooth and Wi-Fi that have slower speeds and higher power consumption. Gi-Fi uses less power than prior standards and is based on the IEEE 802.15.3c standard. It is expected to be the dominant wireless technology for networking within 5 years and enable wireless broadband and high speed transfer of audio, video and large files.Gi - Fi



Gi - FiRaji Perumalla
╠²
Gigabit Wireless is the world's first transceiver integrated on a single chip that operates at 60GHz on the CMOS processGI-FI



GI-FIShubhrika Sehgal
╠²
Gi-Fi(Gigabit Fidelity) or Gigabit Wireless is the world's first transceiver integrated on a single chip that operates at 60GHz on the CMOS process.
Gi fi technology ppt



Gi fi technology pptdeepakisguru
╠²
This document discusses Gigabit wireless (Gi-Fi) technology. It begins with an introduction to Gi-Fi, noting that it operates at 60GHz, allows wireless transfer of audio and video at up to 5GB per second within a 10m range. It then covers the Gi-Fi chip architecture, describing its small antenna and line of sight operation. Applications mentioned include wireless PAN networks, inter-vehicle communication, and high speed file transfers. The conclusion predicts that within 5 years, Gi-Fi will be the dominant wireless technology, providing low-cost, high-speed broadband access for wireless homes and offices.gi-fi (2)



gi-fi (2)Amarendra Kumar
╠²
Gi-Fi is a new wireless technology that offers faster data transfer speeds of up to 5 Gbps over short ranges of 10 meters, which is 10 times faster than current Wi-Fi technologies. It uses the 60GHz frequency band and consists of a single-chip transceiver with an integrated transmitter and receiver. Gi-Fi allows for quick transfer of large files like videos and audio within seconds. It offers advantages over Wi-Fi such as higher speeds, lower power consumption, and lower cost. Potential applications include high-speed data distribution to devices in apartments or media streaming in stadiums.Gi Fi.pptx



Gi Fi.pptxGouthamReddii
╠²
This document summarizes Gi-Fi technology. It begins by discussing currently used wireless technologies like Bluetooth and Wi-Fi. It then introduces Gi-Fi as a technology that operates at 60GHz for wireless transfer of audio and video data at up to 5GB per second within a 10m range. The document describes Gi-Fi's architecture based on the IEEE 802.15.3C standard and features like high speed, low power consumption, security and cost effectiveness. It concludes that Gi-Fi is expected to become the dominant wireless technology within five years, providing low-cost, high-speed broadband access for wireless homes and offices.seminar ppt.pptx



seminar ppt.pptxCHARANBASAVARAJ1
╠²
The document discusses Gi-Fi (Gigabit wireless) technology, which allows wireless transfer of data at speeds up to 5 gigabits per second within a 10 meter range. It provides advantages over existing Bluetooth and Wi-Fi technologies by offering higher data rates, lower power consumption, and operating at 60 GHz frequency for better security and interference immunity. The document outlines the network evolution leading to Gi-Fi, its architecture based on IEEE 802.15.3c standard, working principles, advantages, applications in home appliances and vehicle communication, and concludes that Gi-Fi will become the dominant wireless technology for networking within five years.Gi-fi Technology



Gi-fi TechnologyOECLIB Odisha Electronics Control Library
╠²
This document discusses gigabit wireless (Gi-Fi) technology. It provides an introduction to Gi-Fi, describing it as operating at 60GHz, allowing wireless transfer of audio and video data at up to 5GB per second within a 10m range. The document outlines Gi-Fi's architecture, which supports the IEEE 802.15.3c standard and uses small antennas. Key features of Gi-Fi are also presented, including high speed data transfer, low power consumption, high security, low cost and small size. Potential applications include wireless PAN networks, inter-vehicle communication, file transfers, and use in offices. The conclusion discusses expectations that Gi-Fi will be the dominant wireless technology within five years,1307.0616 gi fiiiiiiiii



1307.0616 gi fiiiiiiiiiHarilal Punalur
╠²
This document discusses the Gi-Fi technology, which provides wireless data transfer speeds of up to 5 Gbps over short ranges of 10 meters. Gi-Fi operates at 60GHz frequency and uses a small, low-power chip to transmit uncompressed HD video wirelessly. It is 10 times faster than existing technologies like Wi-Fi and Bluetooth, and has a variety of applications for wirelessly connecting devices in homes and offices. The document compares Gi-Fi to other wireless technologies and outlines its benefits, such as high data transfer speeds, low power consumption, flexibility and potential to replace wired connections like HDMI cables.Gi fi



Gi fiNITA PAUL
╠²
Gi-Fi is a next generation wireless technology that allows for wireless data transfer speeds of up to 5Gbps using a single-chip transceiver operating at 60GHz. It provides high data transfer rates and low power consumption compared to existing technologies like Bluetooth and Wi-Fi. Gi-Fi has applications in connecting household appliances, transferring video and office files, inter-vehicle communication systems, and broadcasting from sports stadiums. It is expected to become the dominant wireless networking technology in the coming years due to advantages of high speed, low power usage, and cost effectiveness.IJETTCS-2015-03-15-29



IJETTCS-2015-03-15-29abhishek pratap singh
╠²
Gi-Fi is a new wireless technology that offers data transfer rates up to 5Gbps over short ranges of up to 10 meters. It utilizes a small chip operating at 60GHz frequency that is currently mostly unused. This chip integrates both a transmitter and receiver onto a single CMOS chip for the first time. Gi-Fi allows transfer of large files like HD movies between devices in seconds, while consuming only 2 watts of power. It has potential applications for fast transfer of data between devices like phones, cameras and computers.GIFI TECHNOLOGY



GIFI TECHNOLOGYVuha Kothagorla
╠²
Gi-Fi is a new wireless technology that operates at 60GHz and allows data transfer rates up to 5 gigabits per second, which is 10 times faster than current wireless technologies. It uses a single-chip transceiver and small antennas to integrate transmitting and receiving capabilities. Gi-Fi works within short ranges of about 10 meters but provides high data security due to oxygen absorption at 60GHz. It is expected to be commercially available next year and become the dominant wireless technology within 5 years due to its high speeds, low power consumption, security, and low cost.Gi fi Technology (next generation wireless technology)



Gi fi Technology (next generation wireless technology)Uday Wankhade
╠²
Gi-Fi is a new wireless technology that allows data transfer speeds up to 5 gigabits per second over short ranges of about 10 meters. It operates at 60GHz frequency using CMOS chip technology. Gi-Fi provides significantly faster speeds than existing wireless technologies like Bluetooth and Wi-Fi while using less power. It is well-suited for applications like wireless transfer of high-definition video between devices in homes and offices. The presenter predicted that within five years, Gi-Fi will become the dominant technology for wireless networking due to its high speeds, low power use, and lower equipment costs compared to other technologies.Gifi wireless Technology



Gifi wireless TechnologyTofik Kaida
╠²
Gi-Fi is a new wireless technology that operates at 60GHz and allows data transfer rates up to 5 gigabits per second over short ranges of around 10 meters. It is integrated onto a single chip using CMOS technology. Gi-Fi provides faster transfer speeds than existing technologies like Bluetooth and Wi-Fi while using less power. Potential applications include wireless transfer between household appliances, office devices, and high-definition video and audio content. Gi-Fi is expected to become the dominant wireless networking technology within the next five years.Gi fi



Gi fiSrihari
╠²
The document introduces Gi-Fi (Gigabit Fidelity) technology, which utilizes a single-chip integrated transceiver operating at 60GHz to allow for wireless transfer of audio and video data at speeds up to 5 gigabits per second over short ranges. This new technology aims to address limitations of existing wireless technologies like Bluetooth and Wi-Fi by providing faster speeds, lower power consumption, and short-range connectivity at a lower cost. The document discusses the development, working principles, advantages, and potential applications of Gi-Fi technology.4.report (gi fi technology)



4.report (gi fi technology)JIEMS Akkalkuwa
╠²
Gi-Fi is a new wireless technology that was developed at the National Information and Communication Technology Research center in Australia. It allows for wireless transfer of audio and video data at speeds of up to 5 gigabits per second, which is 10 times faster than current wireless transfer rates. Gi-Fi operates at 60GHz on a single chip using CMOS process and can transfer large files like videos within seconds. It provides higher data transfer speeds than Wi-Fi and WiMax, along with lower power consumption and cost for short range indoor transmissions.2.index (gi fi technology)



2.index (gi fi technology)JIEMS Akkalkuwa
╠²
The document discusses Gi-Fi technology which aims to provide wireless connectivity at gigabit speeds. It begins with an introduction to Gi-Fi and covers existing wireless technologies like Wi-Max, Wi-Fi, and Bluetooth. The proposed Gi-Fi system is described along with its fundamental technologies such as frequency-division duplex, time-division duplex, and methods for digital video and audio transmission. Advantages of Gi-Fi include higher speeds while disadvantages include shorter range. Applications and conclusions are discussed along with references.More Related Content
Similar to 3.acknowledgement (gi fi technology) (20)
Gifi



GifiAishwarya Saseendran
╠²
Gi-Fi is a new wireless technology that provides gigabit wireless data transfer speeds of up to 5Gbps using the 60GHz frequency band. It has several advantages over existing wireless technologies like Bluetooth and Wi-Fi, providing 10 times faster speeds while using only 2mW of power. Potential applications of Gi-Fi include high-speed file transfers for households and offices as well as uses in inter-vehicle communication systems.A Seminar Report On Gi-Fi Technology



A Seminar Report On Gi-Fi TechnologyKate Campbell
╠²
This document provides information about Gi-Fi technology through a seminar report. It begins with an acknowledgment section thanking various people for their support and contributions. It then includes an introduction outlining why Gi-Fi was introduced as an improvement over existing wireless technologies like Wi-Fi and Bluetooth that have slower speeds and higher power consumption. The main body of the report describes what Gi-Fi is, its architecture, how it works at 60GHz using time-division duplexing, and its key advantages like speeds of 5Gbps, low power consumption, high security, low cost and small size. Features of the IEEE 802.15.3C standard are also summarized.wifi versus gifi



wifi versus gifiJYOTI KHICHI
╠²
The document is a seminar report on Gi-Fi technology. It discusses the advantages of Gi-Fi over existing wireless technologies like Wi-Fi and Bluetooth, which have slower data transfer speeds. Gi-Fi allows wireless transfer of data at speeds up to 5 gigabits per second using the 60GHz frequency band and integrated transceiver chips. It has applications in high-speed transfer of videos and files between devices in homes, offices, and vehicles. Within 5 years, Gi-Fi is expected to become the dominant technology for wireless networking due to its high speeds, low power consumption, and low cost.Cse gi-fi-technology-report



Cse gi-fi-technology-reportaswath babu
╠²
This document provides information about Gi-Fi technology through a seminar report. It begins with an acknowledgment section thanking various people for their support and contributions. It then includes an introduction outlining why Gi-Fi was introduced as an improvement over existing wireless technologies like Wi-Fi and Bluetooth that have slower speeds and higher power consumption. The main body of the report describes what Gi-Fi is, its architecture, how it works at 60GHz using time-division duplexing, and its key advantages like speeds of 5Gbps, low power consumption, high security, low cost and small size. Features of the IEEE 802.15.3C standard are also summarized.Gi fi technology



Gi fi technologyvalentino jesse
╠²
The document discusses Gi-Fi or gigabit wireless technology, which allows wireless transfer of data at speeds up to 5 gigabits per second using the 57-64GHz frequency band. It operates on a single chip using CMOS processing and costs one-tenth of current wireless technologies. The document covers Gi-Fi features and applications, compares it to Wi-Fi and Bluetooth, and concludes that Gi-Fi will dominate wireless networking within 5 years by providing low-cost, high-speed connectivity for wireless homes and offices.Gifi



GifiSara Tazeen Mahjoor
╠²
This document discusses next generation wireless technology called Gi-Fi or Gigabit Wireless. Gi-Fi allows wireless transfer of data at speeds up to 5 gigabits per second using the 60GHz frequency band. It was developed by Professor Stan Skafidis of Melbourne University to overcome limitations of existing technologies like Bluetooth and Wi-Fi that have slower speeds and higher power consumption. Gi-Fi uses less power than prior standards and is based on the IEEE 802.15.3c standard. It is expected to be the dominant wireless technology for networking within 5 years and enable wireless broadband and high speed transfer of audio, video and large files.Gi - Fi



Gi - FiRaji Perumalla
╠²
Gigabit Wireless is the world's first transceiver integrated on a single chip that operates at 60GHz on the CMOS processGI-FI



GI-FIShubhrika Sehgal
╠²
Gi-Fi(Gigabit Fidelity) or Gigabit Wireless is the world's first transceiver integrated on a single chip that operates at 60GHz on the CMOS process.
Gi fi technology ppt



Gi fi technology pptdeepakisguru
╠²
This document discusses Gigabit wireless (Gi-Fi) technology. It begins with an introduction to Gi-Fi, noting that it operates at 60GHz, allows wireless transfer of audio and video at up to 5GB per second within a 10m range. It then covers the Gi-Fi chip architecture, describing its small antenna and line of sight operation. Applications mentioned include wireless PAN networks, inter-vehicle communication, and high speed file transfers. The conclusion predicts that within 5 years, Gi-Fi will be the dominant wireless technology, providing low-cost, high-speed broadband access for wireless homes and offices.gi-fi (2)



gi-fi (2)Amarendra Kumar
╠²
Gi-Fi is a new wireless technology that offers faster data transfer speeds of up to 5 Gbps over short ranges of 10 meters, which is 10 times faster than current Wi-Fi technologies. It uses the 60GHz frequency band and consists of a single-chip transceiver with an integrated transmitter and receiver. Gi-Fi allows for quick transfer of large files like videos and audio within seconds. It offers advantages over Wi-Fi such as higher speeds, lower power consumption, and lower cost. Potential applications include high-speed data distribution to devices in apartments or media streaming in stadiums.Gi Fi.pptx



Gi Fi.pptxGouthamReddii
╠²
This document summarizes Gi-Fi technology. It begins by discussing currently used wireless technologies like Bluetooth and Wi-Fi. It then introduces Gi-Fi as a technology that operates at 60GHz for wireless transfer of audio and video data at up to 5GB per second within a 10m range. The document describes Gi-Fi's architecture based on the IEEE 802.15.3C standard and features like high speed, low power consumption, security and cost effectiveness. It concludes that Gi-Fi is expected to become the dominant wireless technology within five years, providing low-cost, high-speed broadband access for wireless homes and offices.seminar ppt.pptx



seminar ppt.pptxCHARANBASAVARAJ1
╠²
The document discusses Gi-Fi (Gigabit wireless) technology, which allows wireless transfer of data at speeds up to 5 gigabits per second within a 10 meter range. It provides advantages over existing Bluetooth and Wi-Fi technologies by offering higher data rates, lower power consumption, and operating at 60 GHz frequency for better security and interference immunity. The document outlines the network evolution leading to Gi-Fi, its architecture based on IEEE 802.15.3c standard, working principles, advantages, applications in home appliances and vehicle communication, and concludes that Gi-Fi will become the dominant wireless technology for networking within five years.Gi-fi Technology



Gi-fi TechnologyOECLIB Odisha Electronics Control Library
╠²
This document discusses gigabit wireless (Gi-Fi) technology. It provides an introduction to Gi-Fi, describing it as operating at 60GHz, allowing wireless transfer of audio and video data at up to 5GB per second within a 10m range. The document outlines Gi-Fi's architecture, which supports the IEEE 802.15.3c standard and uses small antennas. Key features of Gi-Fi are also presented, including high speed data transfer, low power consumption, high security, low cost and small size. Potential applications include wireless PAN networks, inter-vehicle communication, file transfers, and use in offices. The conclusion discusses expectations that Gi-Fi will be the dominant wireless technology within five years,1307.0616 gi fiiiiiiiii



1307.0616 gi fiiiiiiiiiHarilal Punalur
╠²
This document discusses the Gi-Fi technology, which provides wireless data transfer speeds of up to 5 Gbps over short ranges of 10 meters. Gi-Fi operates at 60GHz frequency and uses a small, low-power chip to transmit uncompressed HD video wirelessly. It is 10 times faster than existing technologies like Wi-Fi and Bluetooth, and has a variety of applications for wirelessly connecting devices in homes and offices. The document compares Gi-Fi to other wireless technologies and outlines its benefits, such as high data transfer speeds, low power consumption, flexibility and potential to replace wired connections like HDMI cables.Gi fi



Gi fiNITA PAUL
╠²
Gi-Fi is a next generation wireless technology that allows for wireless data transfer speeds of up to 5Gbps using a single-chip transceiver operating at 60GHz. It provides high data transfer rates and low power consumption compared to existing technologies like Bluetooth and Wi-Fi. Gi-Fi has applications in connecting household appliances, transferring video and office files, inter-vehicle communication systems, and broadcasting from sports stadiums. It is expected to become the dominant wireless networking technology in the coming years due to advantages of high speed, low power usage, and cost effectiveness.IJETTCS-2015-03-15-29



IJETTCS-2015-03-15-29abhishek pratap singh
╠²
Gi-Fi is a new wireless technology that offers data transfer rates up to 5Gbps over short ranges of up to 10 meters. It utilizes a small chip operating at 60GHz frequency that is currently mostly unused. This chip integrates both a transmitter and receiver onto a single CMOS chip for the first time. Gi-Fi allows transfer of large files like HD movies between devices in seconds, while consuming only 2 watts of power. It has potential applications for fast transfer of data between devices like phones, cameras and computers.GIFI TECHNOLOGY



GIFI TECHNOLOGYVuha Kothagorla
╠²
Gi-Fi is a new wireless technology that operates at 60GHz and allows data transfer rates up to 5 gigabits per second, which is 10 times faster than current wireless technologies. It uses a single-chip transceiver and small antennas to integrate transmitting and receiving capabilities. Gi-Fi works within short ranges of about 10 meters but provides high data security due to oxygen absorption at 60GHz. It is expected to be commercially available next year and become the dominant wireless technology within 5 years due to its high speeds, low power consumption, security, and low cost.Gi fi Technology (next generation wireless technology)



Gi fi Technology (next generation wireless technology)Uday Wankhade
╠²
Gi-Fi is a new wireless technology that allows data transfer speeds up to 5 gigabits per second over short ranges of about 10 meters. It operates at 60GHz frequency using CMOS chip technology. Gi-Fi provides significantly faster speeds than existing wireless technologies like Bluetooth and Wi-Fi while using less power. It is well-suited for applications like wireless transfer of high-definition video between devices in homes and offices. The presenter predicted that within five years, Gi-Fi will become the dominant technology for wireless networking due to its high speeds, low power use, and lower equipment costs compared to other technologies.Gifi wireless Technology



Gifi wireless TechnologyTofik Kaida
╠²
Gi-Fi is a new wireless technology that operates at 60GHz and allows data transfer rates up to 5 gigabits per second over short ranges of around 10 meters. It is integrated onto a single chip using CMOS technology. Gi-Fi provides faster transfer speeds than existing technologies like Bluetooth and Wi-Fi while using less power. Potential applications include wireless transfer between household appliances, office devices, and high-definition video and audio content. Gi-Fi is expected to become the dominant wireless networking technology within the next five years.Gi fi



Gi fiSrihari
╠²
The document introduces Gi-Fi (Gigabit Fidelity) technology, which utilizes a single-chip integrated transceiver operating at 60GHz to allow for wireless transfer of audio and video data at speeds up to 5 gigabits per second over short ranges. This new technology aims to address limitations of existing wireless technologies like Bluetooth and Wi-Fi by providing faster speeds, lower power consumption, and short-range connectivity at a lower cost. The document discusses the development, working principles, advantages, and potential applications of Gi-Fi technology.More from JIEMS Akkalkuwa (20)
4.report (gi fi technology)



4.report (gi fi technology)JIEMS Akkalkuwa
╠²
Gi-Fi is a new wireless technology that was developed at the National Information and Communication Technology Research center in Australia. It allows for wireless transfer of audio and video data at speeds of up to 5 gigabits per second, which is 10 times faster than current wireless transfer rates. Gi-Fi operates at 60GHz on a single chip using CMOS process and can transfer large files like videos within seconds. It provides higher data transfer speeds than Wi-Fi and WiMax, along with lower power consumption and cost for short range indoor transmissions.2.index (gi fi technology)



2.index (gi fi technology)JIEMS Akkalkuwa
╠²
The document discusses Gi-Fi technology which aims to provide wireless connectivity at gigabit speeds. It begins with an introduction to Gi-Fi and covers existing wireless technologies like Wi-Max, Wi-Fi, and Bluetooth. The proposed Gi-Fi system is described along with its fundamental technologies such as frequency-division duplex, time-division duplex, and methods for digital video and audio transmission. Advantages of Gi-Fi include higher speeds while disadvantages include shorter range. Applications and conclusions are discussed along with references.1.frontpage (gi fi technology)



1.frontpage (gi fi technology)JIEMS Akkalkuwa
╠²
This seminar report discusses Gi-Fi technology and was submitted to the Computer Engineering Department at JAMIA INSTITUTE OF ENGINEERING & MANAG. STUDIES in Akkalkuwa, Maharashtra, India. The report was guided by Master Mohammad Rauf and submitted by Mr. MOHAMMAD ASIF of the Computer Engineering Department to fulfill degree requirements at JAMIA INSTITUTE and North Maharashtra University.4 (data security in local network using)



4 (data security in local network using)JIEMS Akkalkuwa
╠²
The document discusses data security in local networks using distributed firewalls. It describes how distributed firewalls work to overcome issues with traditional firewalls, which rely on a single entry point. Distributed firewalls are centrally managed from a network server but installed on endpoints throughout the network. This allows security policies to be defined and pushed centrally while filtering traffic both from the internet and internally. It also discusses how distributed firewalls use pull and push techniques to update endpoints with the latest security policies from the central management server.3 (data security in local network using)



3 (data security in local network using)JIEMS Akkalkuwa
╠²
This document acknowledges those who helped with a project report over the course of a week. It thanks the project guide Professor Asif Mohammad for his guidance and for allowing extended time in the lab. It also thanks other professors for their guidance and fellow students for their support. Finally, it acknowledges the Computer Engineering Department for providing excellent facilities and encouragement during the project.2 (data security in local network using)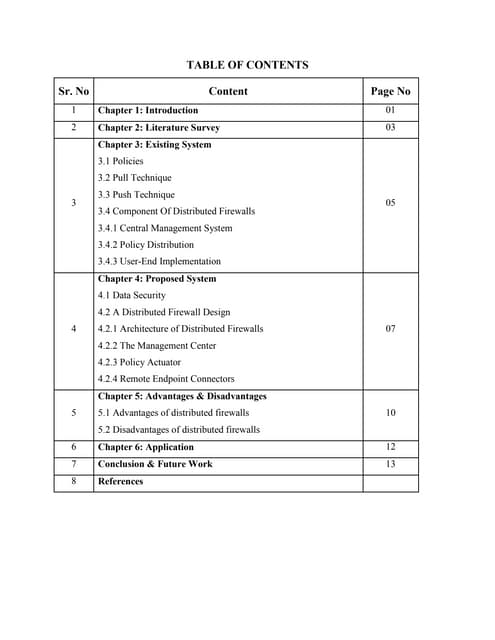



2 (data security in local network using)JIEMS Akkalkuwa
╠²
This document outlines the table of contents for a paper on distributed firewalls. It includes chapters on the introduction, literature survey, existing systems including policies, techniques and components, the proposed distributed firewall design with its architecture, management center, policy actuator and remote connectors. It also covers the advantages and disadvantages of distributed firewalls, applications of the system, and conclusions and future work.1 (data security in local network using)



1 (data security in local network using)JIEMS Akkalkuwa
╠²
This document is a seminar report submitted to the Computer Engineering Department at Jamia Institute of Engineering & Management Studies on data security in local networks using distributed firewalls. The report was guided by Professor Mohammad Asif Khan and submitted by Usama to the Computer Engineering Department at Jamia Institute as part of an academic requirement for North Maharashtra University.4.report (biometric security system)



4.report (biometric security system)JIEMS Akkalkuwa
╠²
This document provides an introduction to biometric security systems. It discusses how biometrics has evolved from early manual criminal identification techniques to modern automated systems. It describes some of the first commercial biometric devices used over 25 years ago for timekeeping and access control. It then summarizes several common biometric modalities used in existing security systems, including fingerprint, face, signature, voice, and gait recognition.3.abstact (biometric security system)



3.abstact (biometric security system)JIEMS Akkalkuwa
╠²
This document acknowledges those who helped with a project report over one week. It thanks the project guide Professor Mohammad Asif for his guidance and support, including allowing extended time in the lab. It also thanks other professors in the department for their guidance and fellow students for their support. Finally, it acknowledges the computer engineering department for providing excellent facilities and encouragement during the project.2.index (biometric security system)



2.index (biometric security system)JIEMS Akkalkuwa
╠²
This document provides an index and overview of biometric identification techniques. It discusses existing systems like fingerprint, face, signature, voice, gait, and keystroke identification. It proposes new ear, iris, and retina recognition systems. It covers the advantages and disadvantages of biometric systems. Applications of these systems are discussed along with conclusions and future work.1.front page (biometric security system)



1.front page (biometric security system)JIEMS Akkalkuwa
╠²
This seminar report discusses biometric security systems and was submitted to the Computer Engineering Department at JAMIA INSTITUTE OF ENGINEERING & MANAGEMENT STUDIES in Akkalkuwa, Maharashtra, India. The report was guided by Assistant Professor Khan Ashraf of the Computer Engineering Department and submitted by Mr. Mohammad Asif to fulfill degree requirements.4 (mobile computing)



4 (mobile computing)JIEMS Akkalkuwa
╠²
This document provides an overview of mobile computing. It discusses how mobile computing allows transmission of data without a fixed physical link, enabling users to transmit data from remote locations. Chapter 1 introduces mobile computing and its applications in the real world. Chapter 2 discusses collaboration among mobile devices and how mobile devices can act as a local cloud. Chapter 3 covers existing cellular network architecture. Chapter 4 proposes guidelines for using mobile computing devices on networks. Chapter 5 discusses advantages like increased productivity and disadvantages like security concerns. Chapter 6 gives examples of applications for mobile computing in fields like emergency services and taxi dispatch. The future scope and conclusion discuss potential advances in artificial intelligence and integrated circuitry.3 (mobile computing)



3 (mobile computing)JIEMS Akkalkuwa
╠²
The document acknowledges those who helped with a project report over one week. It thanks the project guide, Mr. Mohammad Asif, for his guidance and for allowing extra time in the lab. It also thanks other professors and fellow students for their support. Finally, it expresses gratitude to the entire computer engineering department for facilities and encouragement during the project.2 (mobile computing)



2 (mobile computing)JIEMS Akkalkuwa
╠²
This document outlines the table of contents for a research paper on mobile computing. It includes 7 chapters that cover an introduction, literature survey, existing systems, proposed systems, advantages and disadvantages of mobile computing with examples, applications for estate agents, emergency services, credit card verification, taxi/truck dispatching, and email/paging, and a conclusion and future work section. References are provided on the final page.1 (mobile computing)



1 (mobile computing)JIEMS Akkalkuwa
╠²
This report on mobile computing was submitted to the Computer Engineering Department at Jamia Institute of Engineering & Management Studies by Kasab Sk. Akleem, guided by Mr. Mohammad Asif, an assistant professor in the Computer Engineering Department. The report provides an overview of mobile computing for the Computer Engineering Department at Jamia Institute of Engineering & Management Studies.4.content (stenography)



4.content (stenography)JIEMS Akkalkuwa
╠²
The document provides an introduction to stenography, which is the ancient art of hiding messages so they are not detectable. It discusses how stenography aims to hide the existence of a message, while cryptography scrambles it so it cannot be understood. It then reviews traditional stenography methods used before digital means, and outlines some key terms like cover image and stego image. The document proposes an edge adaptive scheme for digital image stenography and discusses advantages like messages not attracting attention. It also reviews some applications of stenography like digital watermarking and discusses the technique's future scope.3.abstract (stenography)



3.abstract (stenography)JIEMS Akkalkuwa
╠²
Steganography is the art of hiding information to conceal its existence. It provides better security than cryptography by hiding the existence of the message, not just its contents. Original messages can be hidden within carriers, like digital images, such that the changes to the carrier are not observable. Combining the secret image with the carrier image produces a hidden image that is difficult to detect without retrieval. This paper will provide an in-depth look at steganography concepts and techniques by introducing the reader to its history and analyzing the performance of some steganography tools.2.index (stenography)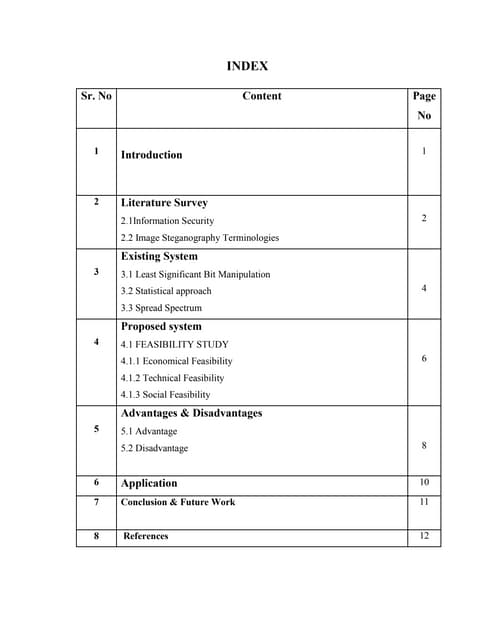



2.index (stenography)JIEMS Akkalkuwa
╠²
This document outlines a proposed system for image steganography and discusses existing steganography techniques like least significant bit manipulation, statistical approaches, and spread spectrum. It covers the feasibility study in economic, technical, and social aspects and analyzes the advantages and disadvantages of steganography. The document concludes with potential applications and outlines future work.1.front (stenography)



1.front (stenography)JIEMS Akkalkuwa
╠²
This seminar report is about stenography and was submitted to the Computer Engineering Department at JAMIA INSTITUTE OF ENGINEERING & MANAGEMENT STUDIES in Akkalkuwa, Maharashtra. The report was guided by Mr. Mohammad Asif and submitted by Amir Suhail Hundekari to fulfill their course requirements for the Computer Engineering Department at JAMIA INSTITUTE.4.report (cyber crime)



4.report (cyber crime)JIEMS Akkalkuwa
╠²
This document discusses cyber crime and provides definitions and classifications of both conventional and cyber crimes. It begins by defining conventional crime and noting that crime has always been a part of human society. It then defines cyber crime, noting that a computer can be either a tool or target of criminal activity. Various types of cyber crimes are outlined such as those involving financial crimes, pornography, intellectual property crimes, and hacking. Prevention and security measures to address cyber crime are also discussed such as user access controls, firewalls, intrusion detection systems, and response mechanisms.Recently uploaded (20)
TASK-DECOMPOSITION BASED ANOMALY DETECTION OF MASSIVE AND HIGH-VOLATILITY SES...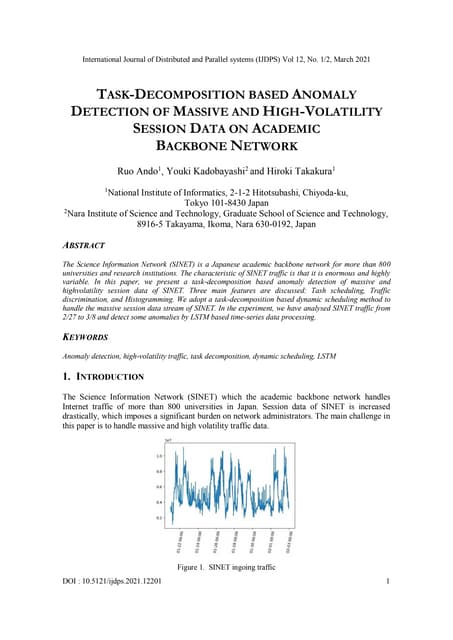



TASK-DECOMPOSITION BASED ANOMALY DETECTION OF MASSIVE AND HIGH-VOLATILITY SES...samueljackson3773
╠²
The Science Information Network (SINET) is a Japanese academic backbone network for more than 800
universities and research institutions. The characteristic of SINET traffic is that it is enormous and highly
variableAI-Powered Power Converter Design Workflow.pdf



AI-Powered Power Converter Design Workflow.pdfAleksandr Terlo
╠²
Blending human expertise with AI-driven optimization for efficient power converter design.Turbocor Product and Technology Review.pdf



Turbocor Product and Technology Review.pdfTotok Sulistiyanto
╠²
High Efficiency Chiller System in HVACDefining the Future of Biophilic Design in Crete.pdf



Defining the Future of Biophilic Design in Crete.pdfARENCOS
╠²
Biophilic design is emerging as a key approach to enhancing well-being by integrating natural elements into residential architecture. In Crete, where the landscape is rich with breathtaking sea views, lush olive groves, and dramatic mountains, biophilic design principles can be seamlessly incorporated to create healthier, more harmonious living environments.
Design and Analysis of Algorithms Unit 5



Design and Analysis of Algorithms Unit 5sureshkumara29
╠²
Algorithm design techniques include:
Brute Force
Greedy Algorithms
Divide-and-Conquer
Dynamic Programming
Reduction / Transform-and-Conquer
Backtracking and Branch-and-Bound
Randomization
Approximation
Recursive Approach
What is an algorithm?
An Algorithm is a procedure to solve a particular problem in a finite number of steps for a finite-sized input.
The algorithms can be classified in various ways. They are:
Implementation Method
Design Method
Design Approaches
Other Classifications
In this article, the different algorithms in each classification method are discussed.
The classification of algorithms is important for several reasons:
Organization: Algorithms can be very complex and by classifying them, it becomes easier to organize, understand, and compare different algorithms.
Problem Solving: Different problems require different algorithms, and by having a classification, it can help identify the best algorithm for a particular problem.
Performance Comparison: By classifying algorithms, it is possible to compare their performance in terms of time and space complexity, making it easier to choose the best algorithm for a particular use case.
Reusability: By classifying algorithms, it becomes easier to re-use existing algorithms for similar problems, thereby reducing development time and improving efficiency.
Research: Classifying algorithms is essential for research and development in computer science, as it helps to identify new algorithms and improve existing ones.
Overall, the classification of algorithms plays a crucial role in computer science and helps to improve the efficiency and effectiveness of solving problems.
Classification by Implementation Method: There are primarily three main categories into which an algorithm can be named in this type of classification. They are:
Recursion or Iteration: A recursive algorithm is an algorithm which calls itself again and again until a base condition is achieved whereas iterative algorithms use loops and/or data structures like stacks, queues to solve any problem. Every recursive solution can be implemented as an iterative solution and vice versa.
Example: The Tower of Hanoi is implemented in a recursive fashion while Stock Span problem is implemented iteratively.
Exact or Approximate: Algorithms that are capable of finding an optimal solution for any problem are known as the exact algorithm. For all those problems, where it is not possible to find the most optimized solution, an approximation algorithm is used. Approximate algorithms are the type of algorithms that find the result as an average outcome of sub outcomes to a problem.
Example: For NP-Hard Problems, approximation algorithms are used. Sorting algorithms are the exact algorithms.
Serial or Parallel or Distributed Algorithms: In serial algorithms, one instruction is executed at a time while parallel algorithms are those in which we divide the problem into subproblems and execute them on different processors. AIR FILTER system in internal combustion engine system.ppt



AIR FILTER system in internal combustion engine system.pptthisisparthipan1
╠²
air filter system in ic engine Taykon-Kalite belgeleri



Taykon-Kalite belgeleriTAYKON
╠²
Kalite Politikam─▒z
Taykon ├ćelik i├¦in kalite, hayallerinizi bizlerle payla┼¤t─▒─¤─▒n─▒z an ba┼¤lar. Proje ├¦iziminden detaylar─▒n ├¦├Čz├╝m├╝ne, detaylar─▒n ├¦├Čz├╝m├╝nden ├╝retime, ├╝retimden montaja, montajdan teslime hayallerinizin ger├¦ekle┼¤ti─¤ini g├Črd├╝─¤├╝n├╝z ana kadar ge├¦en t├╝m a┼¤amalar─▒, ├¦al─▒┼¤anlar─▒, t├╝m teknik donan─▒m ve ├¦evreyi i├¦ine al─▒r KAL─░TE.ESIT135 Problem Solving Using Python Notes of Unit-2 and Unit-3



ESIT135 Problem Solving Using Python Notes of Unit-2 and Unit-3prasadmutkule1
╠²
ESIT135 Problem Solving Using Python Notes of Unit-2 and Unit-3Helium Boosting & Decanting With Hydro Test Machine



Helium Boosting & Decanting With Hydro Test MachinePaskals Fluid Systems Pvt. Ltd.
╠²
About:
A helium boosting and decanting system is typically used in various industrial applications, particularly in the production and handling of gases, including helium including leak test of reciprocating cylinder. HereŌĆÖs a brief overview of its components and functions:
Components
1. Helium Storage Tanks: High-pressure tanks that store helium@ 150 bars.
2. Boosting Pumps: Designed to boost helium pressure up to 150 bar, ensuring efficient flow throughout the system.
3. Decanting Unit: Separates liquid helium from gas, facilitating decanting at pressures of up to 2 bars.
4. Pressure Regulators: Maintain and control the pressure of helium during transport.
5. Control Valves: automatic control valve is provided for the flow and direction of helium through the system.
6. Piping and Fittings: High-quality, corrosion-resistant materials for safe transport.
Functions
ŌĆó Boosting Pressure: The system boosts helium pressure up to 150 bar for various applications.
ŌĆó Decanting: Safely decants helium, separating liquid from gas at pressures of up to 2 bar.
ŌĆó Safety Measures: Equipped with relief valves and emergency shut-off systems to handle high pressures safely.
ŌĆó Monitoring and Control: Sensors and automated controls monitor pressure and flow rates.
Application:
ŌĆó Cryogenics: Cooling superconducting magnets in MRI machines and particle accelerators.
ŌĆó Welding: Used as a shielding gas in welding processes.
ŌĆó Research: Crucial for various scientific applications, including laboratories and space exploration.
Key Features:
ŌĆó Helium Storage & Boosting System
ŌĆó Decanting System
ŌĆó Pressure Regulation & Monitoring
ŌĆó Valves & Flow Control
ŌĆó Filtration & Safety Components
ŌĆó Structural & Material Specifications
ŌĆó Automation & Electrical Components
Unit 1- Review of Basic Concepts-part 1.pptx



Unit 1- Review of Basic Concepts-part 1.pptxSujataSonawane11
╠²
DS, ADT, Algorithms, Asymptotic Notations are summarized. AO Star Algorithm in Artificial Intellligence



AO Star Algorithm in Artificial Intellligencevipulkondekar
╠²
AO Star Algorithm in Artificial IntellligenceIoT-based-Electrical-Motor-Fault-Detection-System.pptx



IoT-based-Electrical-Motor-Fault-Detection-System.pptxatharvapardeshi03
╠²
IoT-based-Electrical-Motor-Fault-Detection-System.pptxINVESTIGATION OF PUEA IN COGNITIVE RADIO NETWORKS USING ENERGY DETECTION IN D...



INVESTIGATION OF PUEA IN COGNITIVE RADIO NETWORKS USING ENERGY DETECTION IN D...csijjournal
╠²
Primary User Emulation Attack (PUEA) is one of the major threats to the spectrum sensing in cognitive
radio networks. This paper studies the PUEA using energy detection that is based on the energy of the
received signal. It discusses the impact of increasing the number of attackers on the performance of
secondary user. Moreover, studying how the malicious user can emulate the Primary User (PU) signal is
made. This is the first analytical method to study PUEA under a different number of attackers. The
detection of the PUEA increases with increasing the number of attackers and decreases when changing the
channel from lognormal to Rayleigh fading.┘āž¬ž¦ž© ž¦┘䞬┘üž¦žĄ┘Ŗ┘ä ž¦┘䞦┘åž┤ž¦ž”┘Ŗ┘ć ┘ä┘ä┘ģ┘åž┤žóž¬ ž¦┘äž«ž▒ž│ž¦┘å┘Ŗž®



┘āž¬ž¦ž© ž¦┘䞬┘üž¦žĄ┘Ŗ┘ä ž¦┘䞦┘åž┤ž¦ž”┘Ŗ┘ć ┘ä┘ä┘ģ┘åž┤žóž¬ ž¦┘äž«ž▒ž│ž¦┘å┘Ŗž®o774656624
╠²
-Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just -Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just-Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just -Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just-Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait letsDesigning Flex and Rigid-Flex PCBs to Prevent Failure



Designing Flex and Rigid-Flex PCBs to Prevent FailureEpec Engineered Technologies
╠²
Flex and rigid-flex printed circuit boards (PCBs) can be considered at the basic level some of the most complex PCBs in the industry. With that in mind, itŌĆÖs incredibly easy to make a mistake, to leave something out, or to create a design that was doomed from the start.
Such design failures can end up leading to an eventual failure by delamination, short circuits, damage to the flex portions, and many other things. The easiest way to circumvent these is to start at the beginning, to design with preventing failure in mind rather than trying to fix existing designs to accommodate for problems.
In this webinar, we cover how to design flex and rigid-flex PCBs with failure prevention in mind to save time, money, and headaches, and what failure can look like.
For more information on our flex and rigid-flex PCB solutions, visit https://www.epectec.com/flex.ESIT135 Problem Solving Using Python Notes of Unit-3



ESIT135 Problem Solving Using Python Notes of Unit-3prasadmutkule1
╠²
ESIT135 Problem Solving Using Python Notes of Unit-3 The Golden Gate Bridge a structural marvel inspired by mother nature.pptx



The Golden Gate Bridge a structural marvel inspired by mother nature.pptxAkankshaRawat75
╠²
The Golden Gate Bridge is a 6 lane suspension bridge spans the Golden Gate Strait, connecting the city of San Francisco to Marin County, California.
It provides a vital transportation link between the Pacific Ocean and the San Francisco Bay.
3.acknowledgement (gi fi technology)
- 1. ACKNOWLEDGEMENT This report is spanned over a period of one week and the number of people who had helped us is outstanding. To begin with, we would like to thank our project guide Professor MOHAMMAD ASIF who has helped us throughout the period and has helped us through the times of need. Inspire of their busy schedules, it was very kind of them to spare some of their precious time and give us valuable suggestions which ultimately formed heart of this report. Professor MOHAMMAD ASIF (Professor of Computer Engineering) was a great source of inspiration and allowed us to work in the lab for extended hours. We also extend our thanks to all the professors of our department for their valuable guidance. We would also like to thank our fellow students for their support and good wishes. Finally we thank entire computer engineering department for excellent facilities and encouragement given during the course of report.
- 2. ABSTRACT Gi-Fi stands for Gigabit fidelity. Gi-Fi is a wireless transmission system which is ten times faster than other technology and its chip delivers short-range multi gigabit data transfer in a local environment. Gi-Fi is a wireless technology which promises high speed short range data transfers with speeds of up to 5 Gbps within a range of 10 meters. The Gi-Fi operates on the 60GHz frequency band. This frequency band is currently mostly unused. This wireless technology named as Gi-Fi. The benefits and features of this new technology can be helpful for use in development of the next generation of devices and places. In this paper, the comparison is perform between Gi- Fi and some of existing technologies with very high speed large files transfers within seconds it is expected that Gi-Fi to be the preferred wireless technology used in home and office of future. Gi- Fi is developed on an integrated wireless transceiver chip. It has both transmitter & receiver, integrated on a single chip which is fabricated using the CMOS (complementary metalŌĆōoxideŌĆō semiconductor) process and it also consists of a small antenna. Gi-Fi allows transferring large videos, audio files, data files, etc. within few seconds.



