3d password ppt
Download as ppt, pdf143 likes100,502 views
The document proposes a 3D password authentication system as an improvement over traditional textual passwords. A 3D password requires a user to navigate a virtual 3D environment and interact with various virtual objects in a specific sequence. This combines multiple authentication factors like recognition, recall, tokens, and biometrics. The document describes examples of virtual objects, implementation details, advantages of the 3D system, and potential applications.
1 of 23
Downloaded 9,021 times


















Ad
Recommended
3d passwords
3d passwordsshwetaag
╠²
The document describes a 3D password scheme that enhances authentication by combining various methods: knowledge-based, token-based, biometric, and recognition techniques. This innovative system allows users to interact with virtual objects to create unique passwords, making them easier to remember and harder to guess. It also addresses common weaknesses of traditional password methods, including brute force attacks and intrusiveness of biometric systems.3d password by suresh
3d password by sureshsuresh5c2
╠²
The 3D password is a proposed multifactor authentication system that combines recognition, recall, tokens, and biometrics. Users authenticate by navigating a virtual 3D environment and interacting with virtual objects at specific locations in a defined sequence. This provides a very large password space that is difficult to crack through brute force attacks or by observing the user. The system has potential applications where strong authentication is needed, such as for critical systems, military facilities, and personal devices.3D Password
3D PasswordShubham Rungta
╠²
The document discusses a proposed 3D password authentication scheme. It begins with an introduction to common authentication techniques and their drawbacks. It then describes the concept of a 3D virtual environment for creating multi-factor passwords combining recall and recognition. The document outlines the objective to develop a more secure and user-friendly authentication system. It further explains the 3D password scheme, potential attacks and countermeasures, applications, advantages and disadvantages, and future scope.3d password 23 mar 14
3d password 23 mar 14Saddam Ahmed
╠²
This document proposes a 3D password authentication scheme that combines recognition, recall, tokens, and biometrics. The scheme uses a 3D virtual environment containing various interactive objects. A user's 3D password is the combination and sequence of interactions they perform with objects in the environment, such as opening a door, typing on a keyboard, drawing on a whiteboard. The scheme aims to provide stronger authentication through multi-factor authentication in a 3D space while being easier for users to remember. Some advantages include flexibility, strength from many possible passwords, and ease of memory through forming a story. Disadvantages include difficulty for blind users and needing sophisticated technology.3D Password
3D PasswordPreethi AKNR
╠²
3D passwords combine multiple authentication factors by using a 3D virtual environment. Users authenticate by interacting with virtual objects in a specific sequence based on their location. This addresses limitations of traditional passwords that can be cracked or stolen. The 3D password is constructed through a user's interactions in the virtual world, combining what they know, have, and do for strong multi-factor authentication. While providing increased security, 3D passwords also have drawbacks such as increased storage needs and vulnerability to timing attacks if the virtual environment is not carefully designed.3d password ppt
3d password pptmanisha0902
╠²
This document describes 3D passwords as a multifactor authentication method that combines knowledge-based, token-based, and biometric authentication in a virtual 3D environment. A 3D password records a user's interactions with virtual objects in the environment, such as opening a door or typing on a computer, creating a unique sequence. Implementation requires programming languages like C++ and OpenGL to create the 3D virtual world. Attacks are difficult due to the complexity of reproducing all factors, but 3D passwords provide very high security and flexibility compared to traditional passwords.3D-Password: A More Secure Authentication
3D-Password: A More Secure AuthenticationMahesh Gadhwal
╠²
The document describes a 3D password authentication system. A 3D password combines knowledge-based, token-based, and biometric authentication by requiring a user to navigate a virtual 3D environment and interact with virtual objects in a specific sequenced manner. This creates a highly customizable and secure password that is difficult for attackers to crack through brute force or observational attacks. The 3D environment and object interactions construct the user's unique 3D password.3 d password
3 d passwordASHOK KUMAR PALAKI
╠²
This document proposes a 3D password authentication scheme. It combines knowledge-based, token-based, and biometric authentication by having users navigate a 3D virtual environment and interact with various objects in a specific sequence. This constructs their unique 3D password. The document outlines how the system would work, advantages like improved security and usability, potential applications, and considerations for design and addressing attacks.3D Password and its importance
3D Password and its importanceshubhangi singh
╠²
The document discusses different types of authentication techniques such as text passwords, biometric scanning, tokens, and cards. It then introduces 3D passwords as a multifactor authentication method that combines recognition, recall, tokens, and biometrics. A 3D password involves a user navigating a virtual environment and interacting with virtual objects in a certain sequence. This provides stronger security than other methods. The document outlines guidelines for designing 3D environments and discusses applications and attacks on 3D passwords. It concludes that 3D passwords could improve authentication but require further development based on user testing.3D PASSWORD
3D PASSWORDJYoTHiSH o.s
╠²
This document introduces 3D passwords as a multifactor authentication scheme. It discusses how 3D passwords combine recognition, recall, tokens, and biometrics by having users navigate a virtual 3D environment and interact with virtual objects. The sequence and types of interactions form the user's unique 3D password. Examples of virtual objects include computers, fingerprint scanners, whiteboards, and more. The document outlines the design of 3D environments and passwords to make them memorable yet difficult to guess or crack. It also discusses potential applications and attacks against 3D passwords.3D PASSWORD
3D PASSWORDramyasaikondapi
╠²
This document discusses 3D password based authentication. It provides an introduction to 3D passwords, explaining that they combine existing authentication schemes like passwords, patterns and biometrics into a single virtual 3D environment. It describes some of the virtual objects that could be used, like computers, lights, TVs and cars. The document outlines how 3D passwords work by having users interact with and perform actions on different objects in a specific sequence. It also discusses advantages like high security and flexibility, and disadvantages such as being difficult for blind people and expensive to implement.3D Password
3D PasswordAnkit Nagar
╠²
The document introduces the 3D password, a multifactor authentication scheme that combines various techniques such as biometrics, text, and graphical passwords within a 3D virtual environment. Users can select their preferred authentication methods to create a unique password through interactive actions within the environment. Despite its advantages, such as flexibility and strength, it also presents challenges like vulnerability to shoulder surfing attacks and difficulties for visually impaired users.SEMINAR REPORT ON 3D PASSWORD
SEMINAR REPORT ON 3D PASSWORDKarishma Khan
╠²
This document discusses 3D passwords as a new authentication technique that combines existing methods like text passwords, graphical passwords, and biometrics into a single 3D virtual environment. The user interacts with various objects in the virtual world to create their unique 3D password. When logging in, they must recreate the same sequence of interactions. This makes 3D passwords more secure by increasing the number of possible passwords and making them difficult for attackers to guess. The document outlines how a 3D password system would work, including designing the virtual environment, recording the user's interactions as their password, and guidelines for the virtual world design like real-life similarity, unique distinguishable objects, and appropriate size.3D Password PPT
3D Password PPTSeminar Links
╠²
The 3D password is a multifactor authentication scheme that combines various traditional authentication methods within a 3D virtual environment, allowing users to interact with objects to construct their password through specific sequences of actions. This system enhances security by integrating biometric, token, and recall-based validation, making it difficult for unauthorized users to replicate. Applications include critical systems like military facilities and ATM machines, and while it faces potential attacks, its design aims to be robust against common threats.3D PASSWORD
3D PASSWORDAkhi Balakrishnan
╠²
For more secure authentication, a 3-D password is proposed that combines multiple authentication factors into a 3D virtual environment. The user navigates and interacts with virtual objects to construct their password. This multi-factor approach includes textual passwords, graphical passwords, and biometrics within a 3D space. The environment design and included objects determine the large key space size, making passwords difficult to crack compared to traditional methods. However, 3D passwords also require more sophisticated technology and programming.3D Password Presentation
3D Password PresentationSambit Mishra
╠²
The document presents an overview of 3D passwords as a novel authentication scheme that combines various methods in a customizable 3D virtual environment. It discusses their advantages, such as enhanced security and user choice, as well as disadvantages including complexity and costs. The conclusion emphasizes the significant potential of 3D passwords to create a larger password space compared to traditional methods.3d password
3d passwordshivi123456
╠²
The document proposes a 3D password authentication scheme. It involves a virtual 3D environment with various interactive objects. A user's authentication is based on the combination and sequence of their interactions with objects as they navigate the environment. The 3D password aims to combine recognition, recall, tokens, and biometrics for strong authentication that is difficult to crack through brute force or shoulder surfing attacks.3D PASSWORD SEMINAR
3D PASSWORD SEMINARKarishma Khan
╠²
The document presents a 3D password authentication scheme that integrates knowledge-based, biometrics, and token-based methods within a virtual environment. This system enhances security by requiring users to interact with specific virtual objects in a defined sequence to create a unique password. While it offers high security and flexibility, challenges include complexity, high costs, and accessibility issues for certain users.3D password
3D passwordanuradha srivastava
╠²
Authentication validates a user's identity by using something they know, have, or are. Common authentication methods include passwords which are something known, tokens like keys which are something had, and biometrics like fingerprints which are something a user is. A 3D password aims to improve authentication security by combining recognition, recall, tokens, and biometrics within a virtual 3D environment that requires users to interact with objects in a specific sequence.3D Password M Sc BHU Sem 1
3D Password M Sc BHU Sem 1Swagato Dey
╠²
This document discusses 3D passwords as an authentication method. It begins by describing traditional authentication methods like knowledge-based, token-based, and biometric authentication. It then introduces the concept of 3D passwords, which combine recognition, recall, tokens, and biometrics within a 3D virtual environment. The document outlines the advantages of 3D passwords and potential applications. It also discusses threats like brute force, shoulder surfing, and timing attacks along with countermeasures. In conclusion, the document argues that 3D passwords can improve authentication by making passwords difficult to crack.SRAVYA
SRAVYApvpsit
╠²
3D passwords provide a more secure authentication method that combines recognition, recall, tokens, and biometrics. A 3D password involves a user authenticating in a virtual 3D environment by interacting with virtual objects like typing on a keyboard or using an ATM. This authentication method is more difficult to crack than traditional passwords since there is no fixed procedure and unauthorized individuals would have trouble replicating the exact interactions. When combined with biometric or token verification, 3D passwords become nearly unbreakable.3D Password
3D PasswordZishan Mohsin
╠²
This document proposes a 3D password authentication scheme that combines existing schemes like knowledge-based, token-based, and biometric-based authentication. It involves users navigating a 3D virtual environment using inputs to perform a sequence of actions and interactions that form their unique 3D password. Guidelines for designing the virtual environment emphasize real-life similarity, object uniqueness, three-dimensional space, and system importance. Potential applications include critical servers, military facilities, and computers. Security analysis covers the password space size and distribution knowledge, while attacks and countermeasures address brute force, shoulder surfing, and timing attacks.3d password - Report
3d password - Report Sunanda Bansal
╠²
The document discusses weaknesses in current authentication systems like textual passwords being vulnerable to dictionary attacks. It then introduces 3D passwords as a proposed multifactor authentication scheme. 3D passwords combine existing authentication methods like passwords, biometrics, etc. into a 3D virtual environment. Users authenticate by navigating and interacting with objects in the environment in a sequence that makes up their unique 3D password. The design of the virtual environment and selected objects determine the large password space, making 3D passwords more secure against guessing attacks.3 d password
3 d password blogger at indiandswad
╠²
The document discusses 3-D passwords, which combine multiple authentication factors like passwords, biometrics, and tokens into a single virtual 3D environment. A 3-D password requires a user to navigate a virtual world and interact with various objects in a specific sequence. This makes 3-D passwords very difficult to guess compared to standard text passwords. The document outlines how a 3-D password works, provides examples of virtual objects, and discusses potential applications and advantages like improved security and ease of memory, while also noting challenges like vulnerability to recording attacks.Graphical password authentication system ppts
Graphical password authentication system pptsNimisha_Goel
╠²
This document discusses different types of authentication systems including token-based, biometric-based, knowledge-based, recognition-based, pure recall-based, cued recall-based, and hybrid systems. It then focuses on graphical passwords, describing how they work by having users select images in a specific order. The document outlines a project to create an Android application for graphical password authentication to unlock private files using a cued recall system where users must select images in the correct sequence from a random grid. It discusses security considerations like guessing attacks and proposes that this approach provides stronger passwords while increasing the workload for attackers.3D password
3D passwordJaya Sinha
╠²
The document proposes a 3D password authentication scheme. It discusses drawbacks of existing authentication methods like textual and graphical passwords. The 3D password scheme combines recognition, recall, tokens, and biometrics in a 3D virtual environment. Users interact with virtual objects in the environment to create a password. This provides a large password space and flexibility. The document outlines guidelines for designing the 3D environment and applications like critical servers, airplanes, and nuclear facilities that could benefit from the strong authentication of 3D passwords.3D-Password
3D-Password Devyani Vaidya
╠²
The document proposes a 3D password authentication system that combines multiple authentication factors like recognition, recall, tokens, and biometrics. It aims to address weaknesses in existing systems by providing a large password space and flexibility for users to select authentication methods. The system presents a 3D virtual environment containing objects. A user's interactions and sequence of interactions in navigating and manipulating objects comprise their unique 3D password.Graphical User Authentication
Graphical User AuthenticationSarthak Gupta
╠²
Graphical passwords are an alternative authentication method that uses images instead of text. They are easier for users to remember but take longer to set up and log in. While more secure than text passwords, most schemes are vulnerable to shoulder surfing. However, techniques like movable frames could add security by countering observation. Overall, graphical passwords balance usability and security but require more development to address issues and achieve widespread adoption.3 d ppt
3 d pptdwivedibrothers
╠²
The document discusses 3-D password technology for more secure authentication. It describes existing authentication systems like textual passwords, graphical passwords, biometrics, and token-based systems. A 3-D password presents a virtual environment where the user interacts with virtual objects in a certain sequence and combination to authenticate. The virtual environment and objects can mimic real-life scenarios. 3-D passwords offer flexibility, strength, and ease of memorization while respecting privacy. Their main applications are for critical systems like servers, military facilities, and banks. The document also covers potential attacks and countermeasures for 3-D passwords.3D Password ppt
3D Password ppt Devyani Vaidya
╠²
The document proposes a 3D password authentication system that combines recognition, recall, tokens, and biometrics by having users navigate a virtual 3D environment and interact with virtual objects in a specific sequence. This addresses weaknesses in traditional text passwords that are vulnerable to dictionary attacks. The 3D password would be more secure and customizable than existing authentication methods.More Related Content
What's hot (20)
3D Password and its importance
3D Password and its importanceshubhangi singh
╠²
The document discusses different types of authentication techniques such as text passwords, biometric scanning, tokens, and cards. It then introduces 3D passwords as a multifactor authentication method that combines recognition, recall, tokens, and biometrics. A 3D password involves a user navigating a virtual environment and interacting with virtual objects in a certain sequence. This provides stronger security than other methods. The document outlines guidelines for designing 3D environments and discusses applications and attacks on 3D passwords. It concludes that 3D passwords could improve authentication but require further development based on user testing.3D PASSWORD
3D PASSWORDJYoTHiSH o.s
╠²
This document introduces 3D passwords as a multifactor authentication scheme. It discusses how 3D passwords combine recognition, recall, tokens, and biometrics by having users navigate a virtual 3D environment and interact with virtual objects. The sequence and types of interactions form the user's unique 3D password. Examples of virtual objects include computers, fingerprint scanners, whiteboards, and more. The document outlines the design of 3D environments and passwords to make them memorable yet difficult to guess or crack. It also discusses potential applications and attacks against 3D passwords.3D PASSWORD
3D PASSWORDramyasaikondapi
╠²
This document discusses 3D password based authentication. It provides an introduction to 3D passwords, explaining that they combine existing authentication schemes like passwords, patterns and biometrics into a single virtual 3D environment. It describes some of the virtual objects that could be used, like computers, lights, TVs and cars. The document outlines how 3D passwords work by having users interact with and perform actions on different objects in a specific sequence. It also discusses advantages like high security and flexibility, and disadvantages such as being difficult for blind people and expensive to implement.3D Password
3D PasswordAnkit Nagar
╠²
The document introduces the 3D password, a multifactor authentication scheme that combines various techniques such as biometrics, text, and graphical passwords within a 3D virtual environment. Users can select their preferred authentication methods to create a unique password through interactive actions within the environment. Despite its advantages, such as flexibility and strength, it also presents challenges like vulnerability to shoulder surfing attacks and difficulties for visually impaired users.SEMINAR REPORT ON 3D PASSWORD
SEMINAR REPORT ON 3D PASSWORDKarishma Khan
╠²
This document discusses 3D passwords as a new authentication technique that combines existing methods like text passwords, graphical passwords, and biometrics into a single 3D virtual environment. The user interacts with various objects in the virtual world to create their unique 3D password. When logging in, they must recreate the same sequence of interactions. This makes 3D passwords more secure by increasing the number of possible passwords and making them difficult for attackers to guess. The document outlines how a 3D password system would work, including designing the virtual environment, recording the user's interactions as their password, and guidelines for the virtual world design like real-life similarity, unique distinguishable objects, and appropriate size.3D Password PPT
3D Password PPTSeminar Links
╠²
The 3D password is a multifactor authentication scheme that combines various traditional authentication methods within a 3D virtual environment, allowing users to interact with objects to construct their password through specific sequences of actions. This system enhances security by integrating biometric, token, and recall-based validation, making it difficult for unauthorized users to replicate. Applications include critical systems like military facilities and ATM machines, and while it faces potential attacks, its design aims to be robust against common threats.3D PASSWORD
3D PASSWORDAkhi Balakrishnan
╠²
For more secure authentication, a 3-D password is proposed that combines multiple authentication factors into a 3D virtual environment. The user navigates and interacts with virtual objects to construct their password. This multi-factor approach includes textual passwords, graphical passwords, and biometrics within a 3D space. The environment design and included objects determine the large key space size, making passwords difficult to crack compared to traditional methods. However, 3D passwords also require more sophisticated technology and programming.3D Password Presentation
3D Password PresentationSambit Mishra
╠²
The document presents an overview of 3D passwords as a novel authentication scheme that combines various methods in a customizable 3D virtual environment. It discusses their advantages, such as enhanced security and user choice, as well as disadvantages including complexity and costs. The conclusion emphasizes the significant potential of 3D passwords to create a larger password space compared to traditional methods.3d password
3d passwordshivi123456
╠²
The document proposes a 3D password authentication scheme. It involves a virtual 3D environment with various interactive objects. A user's authentication is based on the combination and sequence of their interactions with objects as they navigate the environment. The 3D password aims to combine recognition, recall, tokens, and biometrics for strong authentication that is difficult to crack through brute force or shoulder surfing attacks.3D PASSWORD SEMINAR
3D PASSWORD SEMINARKarishma Khan
╠²
The document presents a 3D password authentication scheme that integrates knowledge-based, biometrics, and token-based methods within a virtual environment. This system enhances security by requiring users to interact with specific virtual objects in a defined sequence to create a unique password. While it offers high security and flexibility, challenges include complexity, high costs, and accessibility issues for certain users.3D password
3D passwordanuradha srivastava
╠²
Authentication validates a user's identity by using something they know, have, or are. Common authentication methods include passwords which are something known, tokens like keys which are something had, and biometrics like fingerprints which are something a user is. A 3D password aims to improve authentication security by combining recognition, recall, tokens, and biometrics within a virtual 3D environment that requires users to interact with objects in a specific sequence.3D Password M Sc BHU Sem 1
3D Password M Sc BHU Sem 1Swagato Dey
╠²
This document discusses 3D passwords as an authentication method. It begins by describing traditional authentication methods like knowledge-based, token-based, and biometric authentication. It then introduces the concept of 3D passwords, which combine recognition, recall, tokens, and biometrics within a 3D virtual environment. The document outlines the advantages of 3D passwords and potential applications. It also discusses threats like brute force, shoulder surfing, and timing attacks along with countermeasures. In conclusion, the document argues that 3D passwords can improve authentication by making passwords difficult to crack.SRAVYA
SRAVYApvpsit
╠²
3D passwords provide a more secure authentication method that combines recognition, recall, tokens, and biometrics. A 3D password involves a user authenticating in a virtual 3D environment by interacting with virtual objects like typing on a keyboard or using an ATM. This authentication method is more difficult to crack than traditional passwords since there is no fixed procedure and unauthorized individuals would have trouble replicating the exact interactions. When combined with biometric or token verification, 3D passwords become nearly unbreakable.3D Password
3D PasswordZishan Mohsin
╠²
This document proposes a 3D password authentication scheme that combines existing schemes like knowledge-based, token-based, and biometric-based authentication. It involves users navigating a 3D virtual environment using inputs to perform a sequence of actions and interactions that form their unique 3D password. Guidelines for designing the virtual environment emphasize real-life similarity, object uniqueness, three-dimensional space, and system importance. Potential applications include critical servers, military facilities, and computers. Security analysis covers the password space size and distribution knowledge, while attacks and countermeasures address brute force, shoulder surfing, and timing attacks.3d password - Report
3d password - Report Sunanda Bansal
╠²
The document discusses weaknesses in current authentication systems like textual passwords being vulnerable to dictionary attacks. It then introduces 3D passwords as a proposed multifactor authentication scheme. 3D passwords combine existing authentication methods like passwords, biometrics, etc. into a 3D virtual environment. Users authenticate by navigating and interacting with objects in the environment in a sequence that makes up their unique 3D password. The design of the virtual environment and selected objects determine the large password space, making 3D passwords more secure against guessing attacks.3 d password
3 d password blogger at indiandswad
╠²
The document discusses 3-D passwords, which combine multiple authentication factors like passwords, biometrics, and tokens into a single virtual 3D environment. A 3-D password requires a user to navigate a virtual world and interact with various objects in a specific sequence. This makes 3-D passwords very difficult to guess compared to standard text passwords. The document outlines how a 3-D password works, provides examples of virtual objects, and discusses potential applications and advantages like improved security and ease of memory, while also noting challenges like vulnerability to recording attacks.Graphical password authentication system ppts
Graphical password authentication system pptsNimisha_Goel
╠²
This document discusses different types of authentication systems including token-based, biometric-based, knowledge-based, recognition-based, pure recall-based, cued recall-based, and hybrid systems. It then focuses on graphical passwords, describing how they work by having users select images in a specific order. The document outlines a project to create an Android application for graphical password authentication to unlock private files using a cued recall system where users must select images in the correct sequence from a random grid. It discusses security considerations like guessing attacks and proposes that this approach provides stronger passwords while increasing the workload for attackers.3D password
3D passwordJaya Sinha
╠²
The document proposes a 3D password authentication scheme. It discusses drawbacks of existing authentication methods like textual and graphical passwords. The 3D password scheme combines recognition, recall, tokens, and biometrics in a 3D virtual environment. Users interact with virtual objects in the environment to create a password. This provides a large password space and flexibility. The document outlines guidelines for designing the 3D environment and applications like critical servers, airplanes, and nuclear facilities that could benefit from the strong authentication of 3D passwords.3D-Password
3D-Password Devyani Vaidya
╠²
The document proposes a 3D password authentication system that combines multiple authentication factors like recognition, recall, tokens, and biometrics. It aims to address weaknesses in existing systems by providing a large password space and flexibility for users to select authentication methods. The system presents a 3D virtual environment containing objects. A user's interactions and sequence of interactions in navigating and manipulating objects comprise their unique 3D password.Graphical User Authentication
Graphical User AuthenticationSarthak Gupta
╠²
Graphical passwords are an alternative authentication method that uses images instead of text. They are easier for users to remember but take longer to set up and log in. While more secure than text passwords, most schemes are vulnerable to shoulder surfing. However, techniques like movable frames could add security by countering observation. Overall, graphical passwords balance usability and security but require more development to address issues and achieve widespread adoption.Similar to 3d password ppt (20)
3 d ppt
3 d pptdwivedibrothers
╠²
The document discusses 3-D password technology for more secure authentication. It describes existing authentication systems like textual passwords, graphical passwords, biometrics, and token-based systems. A 3-D password presents a virtual environment where the user interacts with virtual objects in a certain sequence and combination to authenticate. The virtual environment and objects can mimic real-life scenarios. 3-D passwords offer flexibility, strength, and ease of memorization while respecting privacy. Their main applications are for critical systems like servers, military facilities, and banks. The document also covers potential attacks and countermeasures for 3-D passwords.3D Password ppt
3D Password ppt Devyani Vaidya
╠²
The document proposes a 3D password authentication system that combines recognition, recall, tokens, and biometrics by having users navigate a virtual 3D environment and interact with virtual objects in a specific sequence. This addresses weaknesses in traditional text passwords that are vulnerable to dictionary attacks. The 3D password would be more secure and customizable than existing authentication methods.3dpasswordppt
3dpasswordpptDivyaprathapraju Divyaprathapraju
╠²
The document proposes a 3D password authentication system that combines recognition, recall, tokens, and biometrics by having users navigate a virtual 3D environment and interact with virtual objects in a specific sequence. This addresses weaknesses in traditional text passwords that are vulnerable to dictionary attacks. The 3D password would be more secure and customizable than existing authentication methods.3d pass words
3d pass wordsmkanth
╠²
The document proposes a new 3D virtual environment authentication method that combines existing authentication approaches like passwords, graphics, biometrics, and tokens. Users navigate a 3D space and interact with virtual objects in a specific sequence and manner to create their unique 3D password. This large password space provides stronger security than traditional methods. The document discusses designing the 3D environment, potential applications, security analysis, and benefits like reflecting user preferences.Ppt on 3d password (2)
Ppt on 3d password (2)ASIM MIRZA
╠²
The document describes a 3D password authentication system. It begins with an introduction that outlines the need for more secure passwords beyond simple text passwords due to weaknesses in memorability. It then discusses existing security systems like text, graphical and biometric passwords. The document proposes a 3D password that combines recognition, recall, tokens and biometrics for multifactor authentication in an interactive 3D virtual environment containing various objects. It provides guidelines for implementation, examples of applications, and advantages of the 3D password system being difficult to crack without knowing the specific object interaction sequence.Deepak 3 dpassword (2)
Deepak 3 dpassword (2)Deepak Choudhary
╠²
The document proposes a 3D password authentication system that combines existing authentication methods. It describes designing a 3D virtual environment containing various objects that users can interact with. The sequence and type of interactions construct the user's unique 3D password. This allows passwords to incorporate text, graphics, biometrics, tokens, and more. Guidelines for the virtual environment include making objects distinct and interactions realistic. Critical systems are suggested domains due to the large possible password space. Security depends on password space size and unpredictability of user selections.Vivek
VivekVivek Gupta
╠²
The document discusses 3D passwords as a new authentication method. It begins by covering traditional authentication methods like knowledge-based, token-based, and biometrics-based authentication. It then introduces 3D passwords as a multifactor authentication that combines recognition, recall, tokens, and biometrics within a 3D virtual environment. The document provides examples of how a 3D password would work and highlights advantages like flexibility, strength from many possible combinations, and ease of memorization through a story-like format. It also discusses attacks against 3D passwords and potential applications where high security is needed.3d pswdbysuresh-120112091037-phpapp02
3d pswdbysuresh-120112091037-phpapp02bujjiflute
╠²
This document proposes a 3D password authentication system that combines recognition, recall, tokens, and biometrics. It discusses drawbacks of existing password and graphical password systems. The proposed 3D password system uses a virtual 3D environment where the password is a sequence of interactions with virtual objects. This provides a large password space and makes passwords easier to remember. The system records the object locations, actions, and sequence to authenticate users. It has applications for critical systems and offers advantages like flexibility, strength, ease of use, and privacy. Potential attacks and countermeasures are also discussed.3dpassword
3dpasswordDivyaprathapraju Divyaprathapraju
╠²
The document proposes a new authentication technique called 3D Password that aims to overcome limitations of existing authentication schemes like textual and graphical passwords. A 3D Password uses a 3D virtual environment containing real-time object scenarios for authentication. It is a multi-factor authentication that combines benefits of different schemes like passwords, biometrics, and tokens. Users can choose the authentication schemes that make up their 3D Password based on their preferences and needs. The 3D Password is described as more advanced and secure than other techniques as it is easy to use but difficult to break given its large possible password combinations from the 3D virtual environment.3D Password by Kuldeep Dhakad
3D Password by Kuldeep Dhakadkuldeepdhakad
╠²
The document proposes a 3D password authentication system that combines recognition, recall, tokens, and biometrics. Users navigate a virtual 3D environment and authenticate by interacting with virtual objects in a specific sequence. This provides a highly secure authentication method that is difficult to crack through brute force or shoulder surfing attacks. The 3D password system offers flexibility to include different authentication factors and a vast password space that is easy for users to remember.3D Passwrd
3D PasswrdRakshita Paliwal
╠²
The document proposes a 3D password authentication system that combines multiple existing authentication factors. Users can select whether their password is based on recall, biometrics, recognition, tokens, or a combination. In the system, users navigate a virtual 3D environment and interact with virtual objects, with their interactions forming their unique password. The system aims to provide strong, flexible authentication while respecting user privacy. Some example interactions include typing on a virtual keyboard, using a fingerprint scanner, or drawing on a whiteboard. The system has advantages like password strength and ease of memorization but also challenges like cost and accessibility for blind users.Graphical authintication
Graphical authinticationTapesh Chalisgaonkar
╠²
The document proposes a 3-D graphical authentication system as an alternative to traditional textual passwords. It describes users having difficulty with passwords that are hard to remember but easy to crack. The proposed system uses a 3-D virtual environment where the password is a sequence of interactions with objects. This combines elements of recognition, recall, tokens, and biometrics. Guidelines for designing the virtual environment include making it similar to real life and ensuring objects are unique and distinguishable. The system could protect critical systems by offering a very large password space through its multi-factor approach.3d password ppt presentation innovative idea
3d password ppt presentation innovative ideaAmarNath514531
╠²
The 3D password is a multifactor authentication system that combines various existing authentication methods into a virtual environment where users interact with objects to create a unique password based on their actions. This system enhances security by utilizing biometrics, recognition, and recall, making it difficult to crack due to its dynamic nature. Applications range from critical systems like military facilities to everyday use in ATMs and personal devices.3d
3dDivyaprathapraju Divyaprathapraju
╠²
The document proposes a new 3D password authentication technique that aims to overcome limitations of existing authentication schemes like textual and graphical passwords. A 3D password involves navigating a 3D virtual environment and interacting with virtual objects in a certain sequence. This provides a large password space and allows combining multiple authentication factors like passwords, biometrics and smart cards. The document discusses designing 3D environments, creating 3D passwords, applications and advantages like increased security. Potential limitations include requiring sophisticated technology and being difficult for blind users.3dpswd 130320115940-phpapp01-converted
3dpswd 130320115940-phpapp01-convertedMaheshbabu319
╠²
This document proposes a 3D password authentication method that combines multiple existing authentication schemes. A 3D virtual environment would contain various interactive objects like computers, fingerprint scanners, and whiteboards. A user's 3D password would consist of a sequence of actions with different objects, such as typing a text password on a computer or drawing on a whiteboard. This multi-factor approach makes 3D passwords very hard to crack compared to standard passwords. The document discusses guidelines for designing effective 3D environments and lists examples of applications and advantages, such as easy memorization and a large possible password space. However, it also notes some disadvantages like expense and difficulties for blind users.3D - password
3D - passwordBhavikParmar24
╠²
The document discusses the concept of a 3D password as a multifactor authentication method that enhances security by allowing users to navigate and interact within a virtual environment. It outlines how actions and interactions with various virtual objects create a unique password, providing higher security and flexibility compared to traditional passwords. However, it also identifies challenges such as complexity and accessibility issues, along with the need for advanced programming and resources.3dpassword by janapriya
3dpassword by janapriyajanapriyanaidu
╠²
The document describes a 3D password authentication system that combines knowledge-based, token-based, and biometric authentication. The system presents a virtual 3D environment containing objects the user must interact with in a specific sequence. This provides stronger security than typical passwords by requiring the user to navigate the virtual space and interact with objects at particular locations. The 3D password scheme is difficult to crack as it has no fixed procedure and incorporates multiple authentication factors.3dpassword11.pptx.......................
3dpassword11.pptx.......................abhishekB96
╠²
The document presents a 3D password authentication system that combines knowledge-based, token-based, and biometric authentication methods into a multifactor scheme. It describes a virtual environment where users interact with various objects to create customizable passwords, improving security and usability. Advantages include high security and flexibility, while challenges include complexity and cost.New era of authentication
New era of authenticationsunil kumar
╠²
This document proposes a new 3D password authentication scheme that combines multiple existing authentication methods into a 3D virtual environment to provide stronger security. It describes how a 3D password would be composed of a sequence of actions and interactions with various objects in the virtual world. This increases the complexity of guessing passwords compared to traditional text-based passwords. The document also analyzes the potential password key space, security advantages, and applications of the 3D password scheme for critical systems that require strong authentication.3 dpswd
3 dpswdHeena Chugh
╠²
3-D passwords combine multiple authentication methods like passwords, biometrics, and tokens into a 3-D virtual environment. To log in, a user navigates the environment and interacts with virtual objects in a specific sequence. This creates a large number of possible passwords that are difficult for attackers to guess. The document provides guidelines for designing effective 3-D virtual environments, such as making objects unique and scaling the environment based on the system's security needs. 3-D passwords could protect critical systems and are more secure than traditional text passwords.Ad
3d password ppt
- 2. INTRODUCTION ’éŚCurrent Authentification suffer from many weakness.Textual passwords are commonly used,users do not follow their requirements.Users tends to choose meaningful words from dictionaries,which makes the textual passwords easy to break and vulnerable to dictionary or brute force attacks.In this paper,we present and evaluate our contribution i.e. the 3D password
- 3. Existing System ’üČTextual password ’üČGraphical Password ’üČBiometrics ’üČToken Based
- 4. PASSWORD ŌĆóHow secure is your password? Now with the technology change, fast processors and many tools on the Internet, cracking password has become a Child's Play. Ten years back Klein performed such tests and he could crack 10-15 passwords per day.
- 6. 3D PASSWORD
- 7. ŌĆóThe 3D passwords which are more customizable, and very interesting way of authentication. ŌĆóA 3D password is a multifactor authentication scheme that combine RECOGNITION +RECALL +TOKENS +BIOMETRICS in one authentication system.
- 8. ’éŚThe 3D password presents a virtual environment containing various virtual objects. ’éŚ The user walks through the environment and interacts with the objects. ’éŚIt is the combination and sequence of user interactions that occur in the 3D environment.
- 9. Brief Description of System ’éŚThe user is presented with this 3d virtual environment where the user navigates and interacts with various objects. ’éŚThe sequence of actions and interactions towards the objects inside the 3d environment constructs the userŌĆÖs 3d password.
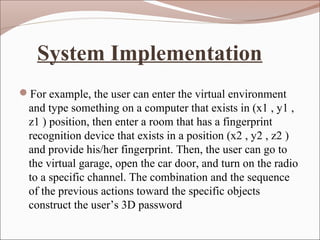
- 10. System Implementation ’éŚFor example, the user can enter the virtual environment and type something on a computer that exists in (x1 , y1 , z1 ) position, then enter a room that has a fingerprint recognition device that exists in a position (x2 , y2 , z2 ) and provide his/her fingerprint. Then, the user can go to the virtual garage, open the car door, and turn on the radio to a specific channel. The combination and the sequence of the previous actions toward the specific objects construct the userŌĆÖs 3D password
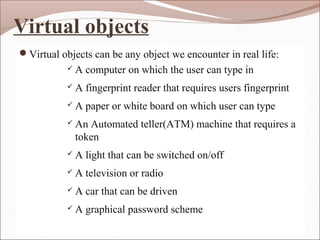
- 11. Virtual objects ’éŚVirtual objects can be any object we encounter in real life: ’ā╝ A computer on which the user can type in ’ā╝ A fingerprint reader that requires users fingerprint ’ā╝ A paper or white board on which user can type ’ā╝ An Automated teller(ATM) machine that requires a token ’ā╝ A light that can be switched on/off ’ā╝ A television or radio ’ā╝ A car that can be driven ’ā╝ A graphical password scheme
- 12. Snapshot of a proof - of - concept virtual art gallery , which contains 36 pictures and six computers
- 14. 3D Virtual Environment ŌĆó3-D virtual environment affects the usability, effectiveness, and acceptability of a 3-D password system. ŌĆó 3-D environment reflects the administration needs and the security requirements. 3D Virtual Environment
- 15. The design of 3D virtual environments should follow these guidelines: ’ü▒Real Life Similarity ’ü▒Object Uniqueness & Distinction ’ü▒3D Virtual Environment Size ’ü▒Number of objects & their types ’ü▒System Importance
- 16. Advantages ’āś Flexibility ’āś Strength ’āś Ease to Memorize ’āś Respect of Privacy
- 17. Applications The 3D passwordŌĆÖs main application domains are protecting critical systems and resources. ’é¦ Critical Servers ’é¦ Nuclear Reactors & military Facilities ’é¦ Airplanes and missile Guiding
- 18. A small virtual environment can be used in the following systems like- ’üČAtm ’üČPersonal digital assistance ’üČDesktop computers & laptops ’üČWeb authentication etc.
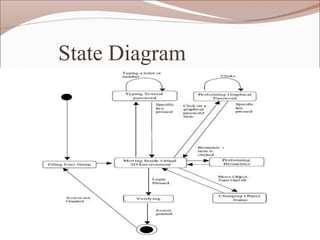
- 19. State Diagram
- 20. Attacks and Countermeasures ’üČBrute Force Attack ’üČWell studied Attack ’üČ Shoulder-surfing Attack
- 21. Conclusion ŌĆóThe authentication can be improved with 3d password ,because the unauthorized person may not interact with same object at a particular location as the legitimate user. ŌĆóIt is difficult to crack ,because it has no fixed number of steps and a particular procedure. ŌĆóAdded with biometrics and token verification this schema becomes almost unbreakable.
- 22. QUERIES