A Dive Into ELF Binaries
- 1. A Dive Into ELF Binaries Null Ahmedabad 23rd Dec 2018 By Bhashit Pandya
- 2. Who am I ‚óè Information Security Consultant ‚óè Scriptologist ‚óè Not a bug hunter!! ‚óè Explorer
- 3. Today we will: ‚óè ask, why to understand them? ‚óè know about executable files. ‚óè peep into the internals. ‚óè see, how to read and analyse it. ‚óè check out some tools.
- 4. Its a sunday morning!!!
- 5. I knew..
- 6. Motivation ‚óè What if you encounter a linux bin? ‚óè What if you are given a file to reverse and patch the file? ‚óè What if you have a software to crack? ‚óè What if you know that this file is vulnerable which can grant you a root access?
- 7. What are executables? ‚óè Not a simple text files. ‚óè Complied and linked against the syscall or WinAPI. ‚óè Has relocatable tables. ‚óè Number of sections to define itself. What are some binary file formats?
- 8. ELF Binary ‚óè Initially developed by Unix System Laboratories for ABI support for unix os. ‚óè Named as System V Release 4 (SVR4) ‚óè Quickly adopted by different vendors of unix systems because of its support for endiannesses and address size. ‚óè Independent of CPU and instruction sets. ‚óè In 1999, it was chosen as a standard binary file format
- 9. ELF Binary Format ‚óè It is just one of the binary format. ‚óè Short abbrevation for Executable and Linkable Format. ‚óè Mostly linux executables are in ELF Format. How to detect them? Will See..
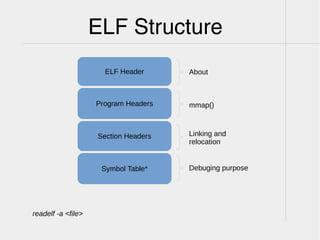
- 10. ELF Structure ELF Header Section Headers Program Headers Symbol Table* readelf -a <file> About Linking and relocation mmap() Debuging purpose
- 12. It Worked!!
- 14. ELF Parsing 1. Examine ELF Header {load_elf_binary()} 2. Loops into Program Header entries to check for an interpreter and executable stack. 3. Initialize Program headers attributes to a new program. 4. {flush_old_exec()} It clears up state in the kernel that refers to prev program. 5. Location of the executable file for the program is updated at /proc/pid/exe 6. Thread name is created using {_set_task_comm()} 7. Kernel Memory tracking structure is created.
- 15. ELF Parsing (Cont..) 1. Code loops through PT_LOAD seg and maps to process addr space. 2.Additional pages are also being loaded such as virtual dynamic shared object (vDSO) and empty page for backward compatibility reasons. 3.Security attributes are being added. 4.Final preparation for running is to setup the rest of the stack {create_elf_tables()}
- 16. Loading ELF ‚óè Check format information of ELF Header. ‚óè Read the ELF Program Header. ‚óè Map all the values of PT_LOAD segment into new program memory. ‚óè Leave space for interpreter BSS segment (object or statically allocated var).
- 17. Basically Loading ELF ‚óè Base Address ‚óè It helps the code to load into memory. ‚óè When ESP values are assigned to base address, the execution of the program starts. ‚óè The code segment of the ELF File is loaded into the memory to execute.
- 18. Patching The Imported Calls! 1. Most programs are dynamically linked. (shared libs are to be located and linked in run-time.) 2. The ELF Handler write ELF Interpreter filename to a new space. 3. Loads the ELF program into memory. 4. ELF Interpreter take care of the linkage program from the user space and resolves the program undefined symbols. 5. The interpreter starts the execution of the new program itself. (AT_ENTRY which holds the entry point of text seg. which was set during preparation)
- 19. Patching the calls ‚óè Execution begins with ELF interpreter. ‚óè Finds the linkage requirements. ‚óè Loads those shared libs. ‚óè Resolves the undefined symbols. ‚óè Starts the execution of the new program.
- 20. Resources Reversing and Exploiting Resources ‚óè Infecting the Procedure Linkage Table. ‚óè http://phrack.org/issues/56/7.html ‚óè More about ELF ‚óè https://smshaker.files.wordpress.com/2008/0 1/reveng-02.pdf
- 21. Thank you!