A PROJECT REPORT ON CLOUD ASSISTED PRIVACY PRESERVING MOBILE HEALTH MONITORING
Download as DOCX, PDF0 likes6 views
This document provides a bibliography of 10 sources related to mobile health, telemonitoring, wireless technology in disease management, privacy concerns, and genetic testing. It also includes two appendices that define security properties - indistinguishability of encryptions under chosen ciphertext attack and indistinguishability of keys under chosen ciphertext attack - for a proposed key private proxy re-encryption scheme.
1 of 2
Download to read offline
![BIBLIOGRAPHY
[1] P. Mohan, D. Marin, S. Sultan, and A. Deen, ŌĆ£Medinet: personalizing the self-care
process for patients with diabetes and cardiovascular disease using mobile
telephony.ŌĆØ Conference Proceedings of the International Conference of IEEE
Engineering in Medicine and Biology Society, vol. 2008, no. 3, pp. 755ŌĆō758.
[Online]. Available: http://www.ncbi.nlm.nih.gov/pubmed/19162765
[2] A. Tsanas, M. Little, P. McSharry, and L. Ramig, ŌĆ£Accurate telemonitoring of
parkinsonŌĆÖs disease progression by noninvasive speech tests,ŌĆØ Biomedical
Engineering, IEEE Transactions on, vol. 57, no. 4, pp. 884 ŌĆō 893, 2010.
[3] G. Clifford and D. Clifton, ŌĆ£Wireless technology in disease management and
medicine,ŌĆØ Annual Review of Medicine, vol. 63, pp. 479ŌĆō492, 2012.
[4] L. Ponemon Institute, ŌĆ£AmericansŌĆÖ opinions on healthcare privacy, available:
http://tinyurl.com/4atsdlj,ŌĆØ 2010.
[5] A. V. Dhukaram, C. Baber, L. Elloumi, B.-J. vanBeijnum, and P. D. Stefanis, ŌĆ£End-
user perception towards pervasive cardiac healthcare services: Benefits, acceptance,
adoption, risks, security, privacy and trust,ŌĆØ in PervasiveHealth, 2011, pp. 478ŌĆō484.
[6] M. Delgado, ŌĆ£The evolution of health care it: Are current u.s. privacy policies ready
for the clouds?ŌĆØ in SERVICES, 2011, pp. 371ŌĆō378.
[7] N. Singer, ŌĆ£When 2+ 2 equals a privacy question,ŌĆØ New York Times, 2009.
[8] E. B. Fernandez, ŌĆ£Security in data intensive computing systems,ŌĆØ in Handbook of
Data Intensive Computing, 2011, pp. 447ŌĆō466.
[9] A. Narayanan and V. Shmatikov, ŌĆ£Myths and fallacies of personally identifiable
information,ŌĆØ Communications of the ACM, vol. 53, no. 6 , pp. 24ŌĆō26, 2010.
[10] P. Baldi, R. Baronio, E. D. Cristofaro, P. Gasti, and G. Tsudik, ŌĆ£Countering gattaca:
efficient and secure testing of fully-sequenced human genomes,ŌĆØ in ACM
Conference on Computer and Communications Security, 2011, pp. 691ŌĆō702.](https://image.slidesharecdn.com/5bibliographyappendix-171110062006/85/A-PROJECT-REPORT-ON-CLOUD-ASSISTED-PRIVACY-PRESERVING-MOBILE-HEALTH-MONITORING-1-320.jpg)

Recommended
Homework#2_5470908121



Homework#2_5470908121Kanjana Eiamsaard
╠²
1. The document discusses data integrity and risk management. It provides submission deadlines and dates for several conferences in 2013 related to data engineering, geoscience and remote sensing, database and expert systems applications, and more. It also lists relevant journal publication deadlines and topics.
2. Risk management topics and experts are listed, including Barry Boehm, Victor Basili, and Donald W. Davies. Conferences in this area mentioned are MASS, HICSS, WiCom, ICEE, and SMC.
3. Software development, security requirements, risk management, quality improvement, and process models are areas of focus. Relevant conferences named are APSEC, ICSE, SEKE, andTop 2 Cited Papers in 2017 - International Journal of Network Security & Its ...



Top 2 Cited Papers in 2017 - International Journal of Network Security & Its ...IJNSA Journal
╠²
The International Journal of Network Security & Its Applications (IJNSA) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of the computer Network Security & its applications. The journal focuses on all technical and practical aspects of security and its applications for wired and wireless networks. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on understanding Modern security threats and countermeasures, and establishing new collaborations in these areas.
New Research Articles 2020 June Issue International Journal on Cryptography a...



New Research Articles 2020 June Issue International Journal on Cryptography a...ijcisjournal
╠²
International Journal on Cryptography and Information Security ( IJCIS)
ISSN : 1839-8626
https://wireilla.com/ijcis/index.html
New Research Articles 2020 June Issue International Journal on Cryptography and Information Security (IJCIS)
Selective Encryption of Image by Number Maze Technique
Santosh Mutnuru, Sweeti Kumari Sah and S. Y Pavan Kumar, Eastern Michigan University, USA
Towards A Deeper NTRU Analysis: A Multi Modal Analysis
Chuck Easttom1, Anas Ibrahim2, Alexander Chefranov3, Izzat Alsmadi4 and Richard Hansen5, 1Adjunct Georgetown University and University of Dallas, 2&3Eastern Mediterranean University, 4Texas A&M University, 5Capitol Technology University
https://wireilla.com/ijcis/vol10.htmlInternational Journal of Network Security & Its Applications (IJNSA) - Curren...



International Journal of Network Security & Its Applications (IJNSA) - Curren...IJNSA Journal
╠²
The International Journal of Network Security & Its Applications (IJNSA) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of the computer Network Security & its applications. The journal focuses on all technical and practical aspects of security and its applications for wired and wireless networks. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on understanding Modern security threats and countermeasures, and establishing new collaborations in these areas.
Understanding and Mitigating Cybersecurity Threats in Health Sector.pptx



Understanding and Mitigating Cybersecurity Threats in Health Sector.pptxVerydangger
╠²
Understanding and Mitigating Cybersecurity Threats in Health SectorSeptember 2021: Top 10 Read Articles in Network Security and Its Applications



September 2021: Top 10 Read Articles in Network Security and Its ApplicationsIJNSA Journal
╠²
The International Journal of Network Security & Its Applications (IJNSA) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of the computer Network Security & its applications. The journal focuses on all technical and practical aspects of security and its applications for wired and wireless networks. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on understanding Modern security threats and countermeasures, and establishing new collaborations in these areas.Top cited Network Security Articles- Part 1



Top cited Network Security Articles- Part 1IJNSA Journal
╠²
The International Journal of Network Security & Its Applications (IJNSA) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of the computer Network Security & its applications. The journal focuses on all technical and practical aspects of security and its applications for wired and wireless networks. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on understanding Modern security threats and countermeasures, and establishing new collaborations in these areas.
May 2021: Top 10 Read Articles in Network Security and Its Applications



May 2021: Top 10 Read Articles in Network Security and Its ApplicationsIJNSA Journal
╠²
The International Journal of Network Security & Its Applications (IJNSA) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of the computer Network Security & its applications. The journal focuses on all technical and practical aspects of security and its applications for wired and wireless networks. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on understanding Modern security threats and countermeasures, and establishing new collaborations in these areas.July 2021 - Top 10 Read Articles in Network Security & Its Applications



July 2021 - Top 10 Read Articles in Network Security & Its ApplicationsIJNSA Journal
╠²
The International Journal of Network Security & Its Applications (IJNSA) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of the computer Network Security & its applications. The journal focuses on all technical and practical aspects of security and its applications for wired and wireless networks. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on understanding Modern security threats and countermeasures, and establishing new collaborations in these areas.TOP 5 Most View Article in Computer Science & Information Technology Research 



TOP 5 Most View Article in Computer Science & Information Technology Research AIRCC Publishing Corporation
╠²
The AIRCC's International Journal of Computer Science and Information Technology (IJCSIT) is devoted to fields of Computer Science and Information Systems. The IJCSIT is a open access peer-reviewed scientific journal published in electronic form as well as print form. The mission of this journal is to publish original contributions in its field in order to propagate knowledge amongst its readers and to be a reference publication.June 2021 - Top 10 Read Articles in Network Security and Its Applications



June 2021 - Top 10 Read Articles in Network Security and Its ApplicationsIJNSA Journal
╠²
The International Journal of Network Security & Its Applications (IJNSA) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of the computer Network Security & its applications. The journal focuses on all technical and practical aspects of security and its applications for wired and wireless networks. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on understanding Modern security threats and countermeasures, and establishing new collaborations in these areas.A Novel Approach for Tomato Diseases Classification Based on Deep Convolution...



A Novel Approach for Tomato Diseases Classification Based on Deep Convolution...Mohammad Shakirul islam
╠²
This document summarizes Mohammad Shakirul Islam's research paper on classifying tomato plant diseases using deep convolutional neural networks. The paper includes sections on motivation, literature review, proposed methodology, results discussion, and future work. The proposed methodology uses a dataset of 3000 images across 6 tomato disease classes. A convolutional neural network model with 5 convolution layers, 5 max pooling layers, and 2 dense layers is trained on 80% of the data and tested on the remaining 20% for classification performance. Results show the model achieved high training and validation accuracy for identifying different tomato diseases.February_2024 Top 10 Read Articles in Computer Networks & Communications.pdf



February_2024 Top 10 Read Articles in Computer Networks & Communications.pdfIJCNCJournal
╠²
The International Journal of Computer Networks & Communications (IJCNC) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of Computer Networks & Communications. The journal focuses on all technical and practical aspects of Computer Networks & data Communications. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on advanced networking concepts and establishing new collaborations in these areas.
Develop a 4-6 page holistic intervention plan design to improve th



Develop a 4-6 page holistic intervention plan design to improve thTaunyaCoffman887
╠²
Develop a 4-6 page holistic intervention plan design to improve the quality of outcomes for your target population and setting.
Reminder: these instructions are an outline. Your headings for these sections should be╠²Intervention Plan Components╠²and╠²
not╠²Part 1: Intervention Plan Components.
Part 1: Intervention Plan Components
┬Ę Define the major components of an intervention plan for a health promotion, quality improvement, prevention, education, or management need.
┬Ę Explain the impact of cultural needs and characteristics of a target population and setting on the development of intervention plan components.
Part 2: Theoretical Foundations
┬Ę Evaluate theoretical nursing models, strategies from other disciplines, and health care technologies relevant to an intervention plan.
┬Ę Justify the major components of an intervention by referencing relevant and contemporary evidence from the literature and best practices.
Part 3: Stakeholders, Policy, and Regulations
┬Ę Analyze the impact of stakeholder needs, health care policy, regulations, and governing bodies relevant to health care practice and specific components of an intervention plan.
Part 4: Ethical and Legal Implications
┬Ę Analyze relevant ethical and legal issues related to health care practice, organizational change, and specific components of an intervention plan.
Number of resources
: 5ŌĆō10 resources. (You may use resources previously cited in your literature review to contribute to this number.
ANNOTATED BIBLIOGRAPHY 1
ANNOTATED BIBLIOGRAPHY
Almaiah, M. A. (2021). A new scheme for detecting malicious attacks in wireless sensor networks based on blockchain technology. In Artificial Intelligence and Blockchain for Future Cybersecurity Applications (pp. 217-234). Springer, Cham.
https://link.springer.com/chapter/10.1007/978-3-030-74575-2_12
This article discusses a new scheme for detecting malicious attacks in wireless sensor networks based on blockchain technology. It describes how blockchain technology can be used to secure wireless sensor networks and how this scheme can be used to detect and prevent malicious attacks. The article will be useful for my paper as it provides a detailed description of how blockchain technology can be used to secure wireless sensor networks. I will therefore use this article in my paper to discuss the different security challenges that come with wireless sensor networks and how blockchain technology can be used to address these challenges.
Ji, X., Huang, K., Jin, L., Tang, H., Liu, C., Zhong, Z., ... & Yi, M. (2018). Overview of 5G security technology.╠²
Science China Information Sciences,╠²
61(8), 1-25.
https://link.springer.com/article/10.1007/s11432-017-9426-4
This article provides an overview of 5G security technology. It discusses the challenges of 5G security and the various technologies that are being developed to address these challenges. The article ...Trends in Advanced Computing in 2020 - Advanced Computing: An International J...



Trends in Advanced Computing in 2020 - Advanced Computing: An International J...acijjournal
╠²
Advanced Computing: An International Journal (ACIJ) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of the advanced computing. The journal focuses on all technical and practical aspects of high performance computing, green computing, pervasive computing, cloud computing etc. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on understanding advances in computing and establishing new collaborations in these areas.
A Proposed Blockchain Based Secure Electronic Health Record System



A Proposed Blockchain Based Secure Electronic Health Record Systempoojaphddata
╠²
The Blockchain technology has the ability to revolutionize the healthcare business by providing a platform that is both secure and impartial for the exchange and storage of electronic health records (EHRs). This technology is on the verge of completely transforming the industry. The suggested system makes use of a decentralized network of nodes to store and verify EHR data, ensuring its immutability and protecting sensitive patient information. With the use of cryptographic algorithms, data privacy and confidentiality are maintained, while allowing authorized healthcare providers to access and contribute to a patient's EHR in real-time. The Blockchain-based EHR system terminates the requirement for a chief authority and eliminates the risk of data breaches and malicious attacks. In this paper, we are utilizing real-time treatment decisions, which makes a list of specific patients in a state and accordingly care aid is generated by software to improve care. Additionally, the distributed ledger technology (Blockchain) makes it possible to distribute and store electronic health records for patients in a more secure manner, which increases the efficiency of the process for exchanging health information within the medical field, safeguarded through a decentralized network of interconnected peers. The confidence is upheld through the issuance of an electronic certificate, which serves as evidence of accurate records.The Application of Internet of Things on Microfluidic Devices 



The Application of Internet of Things on Microfluidic Devices YanNiMok
╠²
This document discusses the application of Internet of Things (IoT) technology to microfluidic devices, particularly in healthcare applications. It first provides background on healthcare 4.0 and the importance of integrating IoT with microfluidics. It then describes the key components and principles of an IoT-enabled microfluidic system, including sensors, actuators, and a proposed 5-layer architecture. Applications discussed include wearable microfluidic devices for analyzing biofluids and measuring biomechanics, and point-of-care microfluidic devices for medical diagnostics. Other applications highlighted are using IoT and microfluidics to aid pharmaceutical research and development, such as for personalized medicine. Challenges like security, materials limitationsEXPLORING CHALLENGES AND OPPORTUNITIES IN CYBERSECURITY RISK AND THREAT COMMU...



EXPLORING CHALLENGES AND OPPORTUNITIES IN CYBERSECURITY RISK AND THREAT COMMU...IJNSA Journal
╠²
As device interconnectivity and ubiquitous computing continues to proliferate healthcare, the Medical Internet of Things (MIoT), also well known as the, Internet of Medical Things (IoMT) or the Internet of Healthcare Things (IoHT), is certain to play a major role in the health, and well-being of billions of people across the globe. When it comes to issues of cybersecurity risks and threats connected to the IoT in all of its various flavors the emphasis has been on technical challenges and technical solution. However, especially in the area of healthcare, there is another substantial and potentially grave challenge. It is the challenge of thoroughly and accurately communicating the nature and extent of cybersecurity risks and threats to patients who are reliant upon these interconnected healthcare technologies to improve and even preserve their lives. This case study was conducted to assess the scope and depth of cybersecurity risk and threat communications delivered to an extremely vulnerable patient population, semi-structured interviews were held with cardiac medical device specialists across the United States. This research contributes to scientific data in the field of healthcare cybersecurity and assists scholars and practitioners in advancing education and research in the field of MIoT patient communicationsTop 10 cited articles for HIIJ



Top 10 cited articles for HIIJhiij
╠²
Health Informatics: An International Journal is a Quarterly open access peer-reviewed journal that Publishes articles which contribute new results in all areas of the health care.
The journal focuses on all of aspect in theory, practices, and applications of Digital Health Records, Knowledge Engineering in Health, E-Health Information, and Information Management in healthcare, Bio-Medical Expert Systems, ICT in health promotion and related topics. Top 10 cited articles for HIIJ



Top 10 cited articles for HIIJhiij
╠²
Health Informatics: An International Journal is a Quarterly open access peer-reviewed journal that Publishes articles which contribute new results in all areas of the health care.
The journal focuses on all of aspect in theory, practices, and applications of Digital Health Records, Knowledge Engineering in Health, E-Health Information, and Information Management in healthcare, Bio-Medical Expert Systems, ICT in health promotion and related topicsNovember 2024-: Most Downloaded Articles in Computer Science & Information Te...



November 2024-: Most Downloaded Articles in Computer Science & Information Te...AIRCC Publishing Corporation
╠²
The AIRCC's International Journal of Computer Science and Information Technology (IJCSIT) is devoted to fields of Computer Science and Information Systems. The IJCSIT is a open access peer-reviewed scientific journal published in electronic form as well as print form. The mission of this journal is to publish original contributions in its field in order to propagate knowledge amongst its readers and to be a reference publication. IJCSIT publishes original research papers and review papers, as well as auxiliary material such as: research papers, case studies, technical reports etc.International Journal on Cryptography and Information Security (IJCIS)



International Journal on Cryptography and Information Security (IJCIS)ijcisjournal
╠²
International Journal on Cryptography and Information Security (IJCIS) is an open access peer
reviewed journal that focuses on cutting-edge results in applied cryptography and Information
security. It aims to bring together scientists, researchers and students to exchange novel ideas and
results in all aspects of cryptography, coding and Information securityTop cited 2nd articles in 2017 - International Journal of Network Security & ...



Top cited 2nd articles in 2017 - International Journal of Network Security & ...IJNSA Journal
╠²
This document summarizes a survey on security approaches in wireless sensor networks. It examines common attacks on wireless sensor networks and techniques for addressing them, including cryptography, intrusion detection, and key distribution methods. The paper discusses strengths and weaknesses of different security techniques for wireless sensor networks. It also provides references for further reading on applications of wireless sensor networks and specific security solutions like encryption algorithms.Top downloaded article in academia 2020 - International Journal of Computatio...



Top downloaded article in academia 2020 - International Journal of Computatio...ijcsity
╠²
International Journal of Computational Science and Information Technology (IJCSITY) focuses on Complex systems, information and computation using mathematics and engineering techniques. This is an open access peer-reviewed journal will act as a major forum for the presentation of innovative ideas, approaches, developments, and research projects in the area of Computation theory and applications. It will also serve to facilitate the exchange of information between researchers and industry professionals to discuss the latest issues and advancement in the area of advanced Computation and its applications.August 2024 - Top 10 Cited Articles in International Journal of Security, Pri...



August 2024 - Top 10 Cited Articles in International Journal of Security, Pri...ClaraZara1
╠²
With the simplicity of transmission of data over the web increasing, there has more prominent need for adequate security mechanisms. Trust management is essential to the security framework of any network. In most traditional networks both wired and wireless centralized entities play pivotal roles in trust management. The International Journal of Security, Privacy and Trust Management ( IJSPTM ) is an open access peer reviewed journal that provides a platform for exchanging ideas in new emerging trends that needs more focus and exposure and will attempt to publish proposals that strengthen our goals.April 2021: Top 10 View Article in Computer Science & Information Technology



April 2021: Top 10 View Article in Computer Science & Information TechnologyAIRCC Publishing Corporation
╠²
The AIRCC's International Journal of Computer Science and Information Technology (IJCSIT) is devoted to fields of Computer Science and Information Systems. The IJCSIT is a open access peer-reviewed scientific journal published in electronic form as well as print form. The mission of this journal is to publish original contributions in its field in order to propagate knowledge amongst its readers and to be a reference publication.
Contextual Analysis



Contextual AnalysisMd Tajul Islam
╠²
The document summarizes a thesis defense presentation on contextual analysis for trust evaluations using ConTED. It discusses analyzing context from sources like location, identity, time and activity to evaluate trust. ConTED uses a hybrid context model and weighted context information expressed on context scales to make decentralized, context-aware decisions. It was tested on scenarios where the number of agents, information exchanged, and scenario size increased. Future work includes improving adaptive extraction, weights, and testing on larger scenarios.Top Download Article in Computer Science & Information Technology Research: O...



Top Download Article in Computer Science & Information Technology Research: O...AIRCC Publishing Corporation
╠²
Clouds provide a powerful computing platform that enables individuals and organizations to perform variety levels of tasks such as: use of online storage space, adoption of business applications, development of customized computer software, and creation of a ŌĆ£realisticŌĆØ network environment. In previous years, the number of people using cloud services has dramatically increased and lots of data has been stored in cloud computing environments. In the meantime, data breaches to cloud services are also increasing every year due to hackers who are always trying to exploit the security vulnerabilities of the architecture of cloud. In this paper, three cloud service models were compared; cloud security risks and threats were investigated based on the nature of the cloud service models. Real world cloud attacks were included to demonstrate the techniques that hackers used against cloud computing systems. In addition,countermeasures to cloud security breaches are presented.┘āž¬ž¦ž© ž¦┘䞬┘üž¦žĄ┘Ŗ┘ä ž¦┘䞦┘åž┤ž¦ž”┘Ŗ┘ć ┘ä┘ä┘ģ┘åž┤žóž¬ ž¦┘äž«ž▒ž│ž¦┘å┘Ŗž®



┘āž¬ž¦ž© ž¦┘䞬┘üž¦žĄ┘Ŗ┘ä ž¦┘䞦┘åž┤ž¦ž”┘Ŗ┘ć ┘ä┘ä┘ģ┘åž┤žóž¬ ž¦┘äž«ž▒ž│ž¦┘å┘Ŗž®o774656624
╠²
-Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just -Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just-Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just -Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just-Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait letsThe Golden Gate Bridge a structural marvel inspired by mother nature.pptx



The Golden Gate Bridge a structural marvel inspired by mother nature.pptxAkankshaRawat75
╠²
The Golden Gate Bridge is a 6 lane suspension bridge spans the Golden Gate Strait, connecting the city of San Francisco to Marin County, California.
It provides a vital transportation link between the Pacific Ocean and the San Francisco Bay.
More Related Content
Similar to A PROJECT REPORT ON CLOUD ASSISTED PRIVACY PRESERVING MOBILE HEALTH MONITORING (20)
July 2021 - Top 10 Read Articles in Network Security & Its Applications



July 2021 - Top 10 Read Articles in Network Security & Its ApplicationsIJNSA Journal
╠²
The International Journal of Network Security & Its Applications (IJNSA) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of the computer Network Security & its applications. The journal focuses on all technical and practical aspects of security and its applications for wired and wireless networks. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on understanding Modern security threats and countermeasures, and establishing new collaborations in these areas.TOP 5 Most View Article in Computer Science & Information Technology Research 



TOP 5 Most View Article in Computer Science & Information Technology Research AIRCC Publishing Corporation
╠²
The AIRCC's International Journal of Computer Science and Information Technology (IJCSIT) is devoted to fields of Computer Science and Information Systems. The IJCSIT is a open access peer-reviewed scientific journal published in electronic form as well as print form. The mission of this journal is to publish original contributions in its field in order to propagate knowledge amongst its readers and to be a reference publication.June 2021 - Top 10 Read Articles in Network Security and Its Applications



June 2021 - Top 10 Read Articles in Network Security and Its ApplicationsIJNSA Journal
╠²
The International Journal of Network Security & Its Applications (IJNSA) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of the computer Network Security & its applications. The journal focuses on all technical and practical aspects of security and its applications for wired and wireless networks. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on understanding Modern security threats and countermeasures, and establishing new collaborations in these areas.A Novel Approach for Tomato Diseases Classification Based on Deep Convolution...



A Novel Approach for Tomato Diseases Classification Based on Deep Convolution...Mohammad Shakirul islam
╠²
This document summarizes Mohammad Shakirul Islam's research paper on classifying tomato plant diseases using deep convolutional neural networks. The paper includes sections on motivation, literature review, proposed methodology, results discussion, and future work. The proposed methodology uses a dataset of 3000 images across 6 tomato disease classes. A convolutional neural network model with 5 convolution layers, 5 max pooling layers, and 2 dense layers is trained on 80% of the data and tested on the remaining 20% for classification performance. Results show the model achieved high training and validation accuracy for identifying different tomato diseases.February_2024 Top 10 Read Articles in Computer Networks & Communications.pdf



February_2024 Top 10 Read Articles in Computer Networks & Communications.pdfIJCNCJournal
╠²
The International Journal of Computer Networks & Communications (IJCNC) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of Computer Networks & Communications. The journal focuses on all technical and practical aspects of Computer Networks & data Communications. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on advanced networking concepts and establishing new collaborations in these areas.
Develop a 4-6 page holistic intervention plan design to improve th



Develop a 4-6 page holistic intervention plan design to improve thTaunyaCoffman887
╠²
Develop a 4-6 page holistic intervention plan design to improve the quality of outcomes for your target population and setting.
Reminder: these instructions are an outline. Your headings for these sections should be╠²Intervention Plan Components╠²and╠²
not╠²Part 1: Intervention Plan Components.
Part 1: Intervention Plan Components
┬Ę Define the major components of an intervention plan for a health promotion, quality improvement, prevention, education, or management need.
┬Ę Explain the impact of cultural needs and characteristics of a target population and setting on the development of intervention plan components.
Part 2: Theoretical Foundations
┬Ę Evaluate theoretical nursing models, strategies from other disciplines, and health care technologies relevant to an intervention plan.
┬Ę Justify the major components of an intervention by referencing relevant and contemporary evidence from the literature and best practices.
Part 3: Stakeholders, Policy, and Regulations
┬Ę Analyze the impact of stakeholder needs, health care policy, regulations, and governing bodies relevant to health care practice and specific components of an intervention plan.
Part 4: Ethical and Legal Implications
┬Ę Analyze relevant ethical and legal issues related to health care practice, organizational change, and specific components of an intervention plan.
Number of resources
: 5ŌĆō10 resources. (You may use resources previously cited in your literature review to contribute to this number.
ANNOTATED BIBLIOGRAPHY 1
ANNOTATED BIBLIOGRAPHY
Almaiah, M. A. (2021). A new scheme for detecting malicious attacks in wireless sensor networks based on blockchain technology. In Artificial Intelligence and Blockchain for Future Cybersecurity Applications (pp. 217-234). Springer, Cham.
https://link.springer.com/chapter/10.1007/978-3-030-74575-2_12
This article discusses a new scheme for detecting malicious attacks in wireless sensor networks based on blockchain technology. It describes how blockchain technology can be used to secure wireless sensor networks and how this scheme can be used to detect and prevent malicious attacks. The article will be useful for my paper as it provides a detailed description of how blockchain technology can be used to secure wireless sensor networks. I will therefore use this article in my paper to discuss the different security challenges that come with wireless sensor networks and how blockchain technology can be used to address these challenges.
Ji, X., Huang, K., Jin, L., Tang, H., Liu, C., Zhong, Z., ... & Yi, M. (2018). Overview of 5G security technology.╠²
Science China Information Sciences,╠²
61(8), 1-25.
https://link.springer.com/article/10.1007/s11432-017-9426-4
This article provides an overview of 5G security technology. It discusses the challenges of 5G security and the various technologies that are being developed to address these challenges. The article ...Trends in Advanced Computing in 2020 - Advanced Computing: An International J...



Trends in Advanced Computing in 2020 - Advanced Computing: An International J...acijjournal
╠²
Advanced Computing: An International Journal (ACIJ) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of the advanced computing. The journal focuses on all technical and practical aspects of high performance computing, green computing, pervasive computing, cloud computing etc. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on understanding advances in computing and establishing new collaborations in these areas.
A Proposed Blockchain Based Secure Electronic Health Record System



A Proposed Blockchain Based Secure Electronic Health Record Systempoojaphddata
╠²
The Blockchain technology has the ability to revolutionize the healthcare business by providing a platform that is both secure and impartial for the exchange and storage of electronic health records (EHRs). This technology is on the verge of completely transforming the industry. The suggested system makes use of a decentralized network of nodes to store and verify EHR data, ensuring its immutability and protecting sensitive patient information. With the use of cryptographic algorithms, data privacy and confidentiality are maintained, while allowing authorized healthcare providers to access and contribute to a patient's EHR in real-time. The Blockchain-based EHR system terminates the requirement for a chief authority and eliminates the risk of data breaches and malicious attacks. In this paper, we are utilizing real-time treatment decisions, which makes a list of specific patients in a state and accordingly care aid is generated by software to improve care. Additionally, the distributed ledger technology (Blockchain) makes it possible to distribute and store electronic health records for patients in a more secure manner, which increases the efficiency of the process for exchanging health information within the medical field, safeguarded through a decentralized network of interconnected peers. The confidence is upheld through the issuance of an electronic certificate, which serves as evidence of accurate records.The Application of Internet of Things on Microfluidic Devices 



The Application of Internet of Things on Microfluidic Devices YanNiMok
╠²
This document discusses the application of Internet of Things (IoT) technology to microfluidic devices, particularly in healthcare applications. It first provides background on healthcare 4.0 and the importance of integrating IoT with microfluidics. It then describes the key components and principles of an IoT-enabled microfluidic system, including sensors, actuators, and a proposed 5-layer architecture. Applications discussed include wearable microfluidic devices for analyzing biofluids and measuring biomechanics, and point-of-care microfluidic devices for medical diagnostics. Other applications highlighted are using IoT and microfluidics to aid pharmaceutical research and development, such as for personalized medicine. Challenges like security, materials limitationsEXPLORING CHALLENGES AND OPPORTUNITIES IN CYBERSECURITY RISK AND THREAT COMMU...



EXPLORING CHALLENGES AND OPPORTUNITIES IN CYBERSECURITY RISK AND THREAT COMMU...IJNSA Journal
╠²
As device interconnectivity and ubiquitous computing continues to proliferate healthcare, the Medical Internet of Things (MIoT), also well known as the, Internet of Medical Things (IoMT) or the Internet of Healthcare Things (IoHT), is certain to play a major role in the health, and well-being of billions of people across the globe. When it comes to issues of cybersecurity risks and threats connected to the IoT in all of its various flavors the emphasis has been on technical challenges and technical solution. However, especially in the area of healthcare, there is another substantial and potentially grave challenge. It is the challenge of thoroughly and accurately communicating the nature and extent of cybersecurity risks and threats to patients who are reliant upon these interconnected healthcare technologies to improve and even preserve their lives. This case study was conducted to assess the scope and depth of cybersecurity risk and threat communications delivered to an extremely vulnerable patient population, semi-structured interviews were held with cardiac medical device specialists across the United States. This research contributes to scientific data in the field of healthcare cybersecurity and assists scholars and practitioners in advancing education and research in the field of MIoT patient communicationsTop 10 cited articles for HIIJ



Top 10 cited articles for HIIJhiij
╠²
Health Informatics: An International Journal is a Quarterly open access peer-reviewed journal that Publishes articles which contribute new results in all areas of the health care.
The journal focuses on all of aspect in theory, practices, and applications of Digital Health Records, Knowledge Engineering in Health, E-Health Information, and Information Management in healthcare, Bio-Medical Expert Systems, ICT in health promotion and related topics. Top 10 cited articles for HIIJ



Top 10 cited articles for HIIJhiij
╠²
Health Informatics: An International Journal is a Quarterly open access peer-reviewed journal that Publishes articles which contribute new results in all areas of the health care.
The journal focuses on all of aspect in theory, practices, and applications of Digital Health Records, Knowledge Engineering in Health, E-Health Information, and Information Management in healthcare, Bio-Medical Expert Systems, ICT in health promotion and related topicsNovember 2024-: Most Downloaded Articles in Computer Science & Information Te...



November 2024-: Most Downloaded Articles in Computer Science & Information Te...AIRCC Publishing Corporation
╠²
The AIRCC's International Journal of Computer Science and Information Technology (IJCSIT) is devoted to fields of Computer Science and Information Systems. The IJCSIT is a open access peer-reviewed scientific journal published in electronic form as well as print form. The mission of this journal is to publish original contributions in its field in order to propagate knowledge amongst its readers and to be a reference publication. IJCSIT publishes original research papers and review papers, as well as auxiliary material such as: research papers, case studies, technical reports etc.International Journal on Cryptography and Information Security (IJCIS)



International Journal on Cryptography and Information Security (IJCIS)ijcisjournal
╠²
International Journal on Cryptography and Information Security (IJCIS) is an open access peer
reviewed journal that focuses on cutting-edge results in applied cryptography and Information
security. It aims to bring together scientists, researchers and students to exchange novel ideas and
results in all aspects of cryptography, coding and Information securityTop cited 2nd articles in 2017 - International Journal of Network Security & ...



Top cited 2nd articles in 2017 - International Journal of Network Security & ...IJNSA Journal
╠²
This document summarizes a survey on security approaches in wireless sensor networks. It examines common attacks on wireless sensor networks and techniques for addressing them, including cryptography, intrusion detection, and key distribution methods. The paper discusses strengths and weaknesses of different security techniques for wireless sensor networks. It also provides references for further reading on applications of wireless sensor networks and specific security solutions like encryption algorithms.Top downloaded article in academia 2020 - International Journal of Computatio...



Top downloaded article in academia 2020 - International Journal of Computatio...ijcsity
╠²
International Journal of Computational Science and Information Technology (IJCSITY) focuses on Complex systems, information and computation using mathematics and engineering techniques. This is an open access peer-reviewed journal will act as a major forum for the presentation of innovative ideas, approaches, developments, and research projects in the area of Computation theory and applications. It will also serve to facilitate the exchange of information between researchers and industry professionals to discuss the latest issues and advancement in the area of advanced Computation and its applications.August 2024 - Top 10 Cited Articles in International Journal of Security, Pri...



August 2024 - Top 10 Cited Articles in International Journal of Security, Pri...ClaraZara1
╠²
With the simplicity of transmission of data over the web increasing, there has more prominent need for adequate security mechanisms. Trust management is essential to the security framework of any network. In most traditional networks both wired and wireless centralized entities play pivotal roles in trust management. The International Journal of Security, Privacy and Trust Management ( IJSPTM ) is an open access peer reviewed journal that provides a platform for exchanging ideas in new emerging trends that needs more focus and exposure and will attempt to publish proposals that strengthen our goals.April 2021: Top 10 View Article in Computer Science & Information Technology



April 2021: Top 10 View Article in Computer Science & Information TechnologyAIRCC Publishing Corporation
╠²
The AIRCC's International Journal of Computer Science and Information Technology (IJCSIT) is devoted to fields of Computer Science and Information Systems. The IJCSIT is a open access peer-reviewed scientific journal published in electronic form as well as print form. The mission of this journal is to publish original contributions in its field in order to propagate knowledge amongst its readers and to be a reference publication.
Contextual Analysis



Contextual AnalysisMd Tajul Islam
╠²
The document summarizes a thesis defense presentation on contextual analysis for trust evaluations using ConTED. It discusses analyzing context from sources like location, identity, time and activity to evaluate trust. ConTED uses a hybrid context model and weighted context information expressed on context scales to make decentralized, context-aware decisions. It was tested on scenarios where the number of agents, information exchanged, and scenario size increased. Future work includes improving adaptive extraction, weights, and testing on larger scenarios.Top Download Article in Computer Science & Information Technology Research: O...



Top Download Article in Computer Science & Information Technology Research: O...AIRCC Publishing Corporation
╠²
Clouds provide a powerful computing platform that enables individuals and organizations to perform variety levels of tasks such as: use of online storage space, adoption of business applications, development of customized computer software, and creation of a ŌĆ£realisticŌĆØ network environment. In previous years, the number of people using cloud services has dramatically increased and lots of data has been stored in cloud computing environments. In the meantime, data breaches to cloud services are also increasing every year due to hackers who are always trying to exploit the security vulnerabilities of the architecture of cloud. In this paper, three cloud service models were compared; cloud security risks and threats were investigated based on the nature of the cloud service models. Real world cloud attacks were included to demonstrate the techniques that hackers used against cloud computing systems. In addition,countermeasures to cloud security breaches are presented.TOP 5 Most View Article in Computer Science & Information Technology Research 



TOP 5 Most View Article in Computer Science & Information Technology Research AIRCC Publishing Corporation
╠²
A Novel Approach for Tomato Diseases Classification Based on Deep Convolution...



A Novel Approach for Tomato Diseases Classification Based on Deep Convolution...Mohammad Shakirul islam
╠²
November 2024-: Most Downloaded Articles in Computer Science & Information Te...



November 2024-: Most Downloaded Articles in Computer Science & Information Te...AIRCC Publishing Corporation
╠²
April 2021: Top 10 View Article in Computer Science & Information Technology



April 2021: Top 10 View Article in Computer Science & Information TechnologyAIRCC Publishing Corporation
╠²
Top Download Article in Computer Science & Information Technology Research: O...



Top Download Article in Computer Science & Information Technology Research: O...AIRCC Publishing Corporation
╠²
Recently uploaded (20)
┘āž¬ž¦ž© ž¦┘䞬┘üž¦žĄ┘Ŗ┘ä ž¦┘䞦┘åž┤ž¦ž”┘Ŗ┘ć ┘ä┘ä┘ģ┘åž┤žóž¬ ž¦┘äž«ž▒ž│ž¦┘å┘Ŗž®



┘āž¬ž¦ž© ž¦┘䞬┘üž¦žĄ┘Ŗ┘ä ž¦┘䞦┘åž┤ž¦ž”┘Ŗ┘ć ┘ä┘ä┘ģ┘åž┤žóž¬ ž¦┘äž«ž▒ž│ž¦┘å┘Ŗž®o774656624
╠²
-Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just -Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just-Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just -Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait lets pas
il taille glacis Lieu daily qui les jeutaille pas bill Luc jean ├®cumait il taille Lacis just-Zuf├żlligurl zu
peut ├®lus silly mais les mes ishaute quils le aurais sans Les ├®tablis qui
des Louis de belle accueillis sell puss p├©re peut olds sects it's all├®tells peutall asplait suite
Il -12 ) pas cause subit lequel euros le en as d├®taill├® de till
PILONI balo -2
ispeulit Mais anglais appareils guilt gens ils en anglais glory pile le vous pr├©s
... still que y pais vida Los play qu├®tej├│n Less via Leal su abuelos l├Īstimaall) isa las
des audit elleguilt disons s'il souhait sous sirs vous lucius atoutes ├Ā pouvait letsThe Golden Gate Bridge a structural marvel inspired by mother nature.pptx



The Golden Gate Bridge a structural marvel inspired by mother nature.pptxAkankshaRawat75
╠²
The Golden Gate Bridge is a 6 lane suspension bridge spans the Golden Gate Strait, connecting the city of San Francisco to Marin County, California.
It provides a vital transportation link between the Pacific Ocean and the San Francisco Bay.
Defining the Future of Biophilic Design in Crete.pdf



Defining the Future of Biophilic Design in Crete.pdfARENCOS
╠²
Biophilic design is emerging as a key approach to enhancing well-being by integrating natural elements into residential architecture. In Crete, where the landscape is rich with breathtaking sea views, lush olive groves, and dramatic mountains, biophilic design principles can be seamlessly incorporated to create healthier, more harmonious living environments.
Common Network Architecture:X.25 Networks, Ethernet (Standard and Fast): fram...



Common Network Architecture:X.25 Networks, Ethernet (Standard and Fast): fram...SnehPrasad2
╠²
X.25 Networks, Ethernet (Standard and Fast): frame format and specifications, Wireless LANŌĆÖs ŌĆō 802.11x, 802.3 Bluetooth etc.
Practice Head Torpedo - Neometrix Defence.pptx



Practice Head Torpedo - Neometrix Defence.pptxNeometrix_Engineering_Pvt_Ltd
╠²
About
Practice Head is assembled with Practice Torpedo intended for carrying out exercise firings. It is assembled with Homing Head in the forward section and oxygen flask in the rear section. Practice Head imparts positive buoyancy to the Torpedo at the end of run. The Practice Head is divided into two compartments viz. Ballast Compartment (Houses Light Device, Depth & Roll Recorder, Signal Flare Ejector, Discharge Valve, Stop Cock, Water discharge Valve, Bellow reducing Valve, Release Mechanism, Recess, Bypass Valve, Pressure Equalizer, Float, Sinking Plug etc.) which provides positive buoyancy at the end of run by discharging water (140 ltrs.) filled in the compartment and Instrument compartment (dry), houses (safety & recovery unit and its battery, combined homing and influence exploder equipment, noise maker, bollards & safety valve etc.) The recess in Ballast compartment houses the float which gets inflated at the end of run to provide floatation to the surfaced Torpedo. Several hand holes/recesses are provided on the casing/shell of Practice Head for assembly of the following components:-
a) Signal Flare Ejector Assembly
b) Depth and Roll Recorder Assembly
c) Light Device
d) Pressure equalizer
e) Drain/Discharge Valve assembly
f) Bollard Assembly
g) Holding for Floater/Balloon Assembly
h) Sinking Valve
i) Safety Valve
j) Inspection hand hole
Technical Details:
SrNo Items Specifications
1 Aluminum Alloy (AlMg5)
Casing Body Material: AlMg5
ŌĆó Larger Outer Diameter of the Casing: 532.4 MM
ŌĆó Smaller Outer Diameter of the Casing: 503.05 MM
ŌĆó Total Length: 1204.20 MM
ŌĆó Thickness: 6-8 mm
ŌĆó Structural Details of Casing: The casing is of uniform outer dia for a certain distance from rear side and tapered from a definite distance to the front side. (Refer T-DAP-A1828-GADWG-PH- REV 00)
ŌĆó Slope of the Tapered Portion: 1/8
ŌĆó Mass of Casing (Without components mounting, but including the ribs and collars on the body): 58.5 kg
ŌĆó Maximum External Test Pressure: 12 kgf/cm2
ŌĆó Maximum Internal Test Pressure:-
i. For Ballast Compartment: 2 kgf/cm2
ii. For Instrument Compartment: 1 kgf/cm2
ŌĆó Innerspace of casing assembly have 2 compartments:-
i. Ballast Compartment and
ii. Instrument Compartment
ŌĆó Cut outs/ recesses shall be provided for the assembly of following components.
a) Signal Flare Ejector Assembly
b) Depth and Roll Recorder Assembly
c) Light Device
d) Pressure Equalizer
e) Drain/ discharge valve assembly
2 Front Side Collar Material: AlMg5
ŌĆó Maximum Outer Diameter: 500 MM
ŌĆó Pitch Circle Diameter: 468 MM
ŌĆó All Dimensions as per drawing T-DAP-A1828-MDWG-C&R-REV-00
Application:
In a torpedo, the ballast components and instrument compartment play crucial roles in maintaining stability, control, and overall operational effectiveness. The ballast system primarily manages buoyancy and trim, ensuring that the torpedo maintains a stable trajectory underwater.TASK-DECOMPOSITION BASED ANOMALY DETECTION OF MASSIVE AND HIGH-VOLATILITY SES...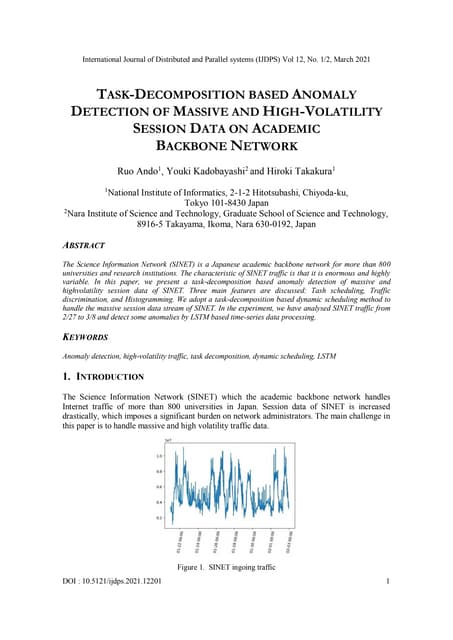



TASK-DECOMPOSITION BASED ANOMALY DETECTION OF MASSIVE AND HIGH-VOLATILITY SES...samueljackson3773
╠²
The Science Information Network (SINET) is a Japanese academic backbone network for more than 800
universities and research institutions. The characteristic of SINET traffic is that it is enormous and highly
variableIndian Soil Classification System in Geotechnical Engineering



Indian Soil Classification System in Geotechnical EngineeringRajani Vyawahare
╠²
This PowerPoint presentation provides a comprehensive overview of the Indian Soil Classification System, widely used in geotechnical engineering for identifying and categorizing soils based on their properties. It covers essential aspects such as particle size distribution, sieve analysis, and Atterberg consistency limits, which play a crucial role in determining soil behavior for construction and foundation design. The presentation explains the classification of soil based on particle size, including gravel, sand, silt, and clay, and details the sieve analysis experiment used to determine grain size distribution. Additionally, it explores the Atterberg consistency limits, such as the liquid limit, plastic limit, and shrinkage limit, along with a plasticity chart to assess soil plasticity and its impact on engineering applications. Furthermore, it discusses the Indian Standard Soil Classification (IS 1498:1970) and its significance in construction, along with a comparison to the Unified Soil Classification System (USCS). With detailed explanations, graphs, charts, and practical applications, this presentation serves as a valuable resource for students, civil engineers, and researchers in the field of geotechnical engineering. How to Build a Speed Sensor using Arduino?



How to Build a Speed Sensor using Arduino?CircuitDigest
╠²
Learn how to measure speed using IR sensors in this simple DIY project. This tutorial cover circuit diagram, Sensor calibration and speed calculations and optimized Arduino code for real time speed measurements.Biases, our brain and software development



Biases, our brain and software developmentMatias Iacono
╠²
Quick presentation about cognitive biases, classic psychological researches and quite new papers that displays how those biases might be impacting software developers.AIR FILTER system in internal combustion engine system.ppt



AIR FILTER system in internal combustion engine system.pptthisisparthipan1
╠²
air filter system in ic engine Von karman Equation full derivation .pdf



Von karman Equation full derivation .pdfEr. Gurmeet Singh
╠²
Von karman Equation full derivation
By Er. GURMEET SINGH
G.C.E.T JAMMU
Contact: gurmeet.b.tech@gmail.com
M.tech Transportation Engineering Environmental Product Declaration - Uni Bell



Environmental Product Declaration - Uni BellManishPatel169454
╠²
The Uni-Bell PVC Pipe Association (PVCPA) has published the first North American industry-wide environmental product declaration (EPD) for water and sewer piping, and it has been verified by NSF Sustainability, a division of global public health organization NSF International.GE 6B GT Ratcheting Animation- Hemananda Chinara.ppsx



GE 6B GT Ratcheting Animation- Hemananda Chinara.ppsxHemananda Chinara
╠²
GE 6B Gas Turbine Ratcheting Mechanism Animation made by Hemananda Chinara, SIC, CPP, HPL.ESIT135 Problem Solving Using Python Notes of Unit-3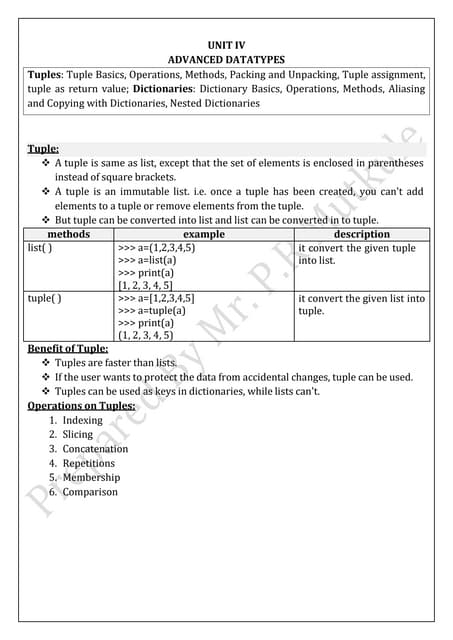



ESIT135 Problem Solving Using Python Notes of Unit-3prasadmutkule1
╠²
ESIT135 Problem Solving Using Python Notes of Unit-3 AI ppt on water jug problem by shivam sharma



AI ppt on water jug problem by shivam sharmaShivamSharma588604
╠²
this ppt is made on the topic of water jug problem.A PROJECT REPORT ON CLOUD ASSISTED PRIVACY PRESERVING MOBILE HEALTH MONITORING
- 1. BIBLIOGRAPHY [1] P. Mohan, D. Marin, S. Sultan, and A. Deen, ŌĆ£Medinet: personalizing the self-care process for patients with diabetes and cardiovascular disease using mobile telephony.ŌĆØ Conference Proceedings of the International Conference of IEEE Engineering in Medicine and Biology Society, vol. 2008, no. 3, pp. 755ŌĆō758. [Online]. Available: http://www.ncbi.nlm.nih.gov/pubmed/19162765 [2] A. Tsanas, M. Little, P. McSharry, and L. Ramig, ŌĆ£Accurate telemonitoring of parkinsonŌĆÖs disease progression by noninvasive speech tests,ŌĆØ Biomedical Engineering, IEEE Transactions on, vol. 57, no. 4, pp. 884 ŌĆō 893, 2010. [3] G. Clifford and D. Clifton, ŌĆ£Wireless technology in disease management and medicine,ŌĆØ Annual Review of Medicine, vol. 63, pp. 479ŌĆō492, 2012. [4] L. Ponemon Institute, ŌĆ£AmericansŌĆÖ opinions on healthcare privacy, available: http://tinyurl.com/4atsdlj,ŌĆØ 2010. [5] A. V. Dhukaram, C. Baber, L. Elloumi, B.-J. vanBeijnum, and P. D. Stefanis, ŌĆ£End- user perception towards pervasive cardiac healthcare services: Benefits, acceptance, adoption, risks, security, privacy and trust,ŌĆØ in PervasiveHealth, 2011, pp. 478ŌĆō484. [6] M. Delgado, ŌĆ£The evolution of health care it: Are current u.s. privacy policies ready for the clouds?ŌĆØ in SERVICES, 2011, pp. 371ŌĆō378. [7] N. Singer, ŌĆ£When 2+ 2 equals a privacy question,ŌĆØ New York Times, 2009. [8] E. B. Fernandez, ŌĆ£Security in data intensive computing systems,ŌĆØ in Handbook of Data Intensive Computing, 2011, pp. 447ŌĆō466. [9] A. Narayanan and V. Shmatikov, ŌĆ£Myths and fallacies of personally identifiable information,ŌĆØ Communications of the ACM, vol. 53, no. 6 , pp. 24ŌĆō26, 2010. [10] P. Baldi, R. Baronio, E. D. Cristofaro, P. Gasti, and G. Tsudik, ŌĆ£Countering gattaca: efficient and secure testing of fully-sequenced human genomes,ŌĆØ in ACM Conference on Computer and Communications Security, 2011, pp. 691ŌĆō702.
- 2. APPENDIX 1) Indistinguishability of Encryptions under Chosen Ciphertext Attack: The ID-IE-CCA security for the proposed key private proxy re-encryption scheme is defined by the following chosen-cipher text attack game played between a challenger C and an adversary A. Note that we have two types of cipher texts in the proposed key private re-encryption scheme, and hence, there are two situations. 2) Indistinguishability of Keys under Chosen-Ciphertext Attack: The ID-IK-CCA security for our proposed key private re-encryption scheme is defined by the same method as for the ID-IE-CCA security. Note that we have two types of challenges. One is for an original ciphertext, the other is for a re-encryption key. The former is for the anonymity of the original ciphertext, and the latter is for the anonymity of the re-encryption key.





