A Quantitative Comparison of Coverage-Based Greybox Fuzzers
Download as PPTX, PDF0 likes430 views
slides for the paper "A Quantitative Comparison of Coverage-Based Greybox Fuzzers", Proceedings of the 1st IEEE/ACM International Conference on Automation of Software Test (AST 2020), pp.89-92, Seoul, South Korea, July 2020.
1 of 12
Download to read offline









Recommended
One plus 5t architecture



One plus 5t architectureMuhammad Osama Khalid
?
The OnePlus 5T uses the Qualcomm Snapdragon 835 system on chip which features an octa-core CPU called Kryo 280 consisting of four high-performance cores running up to 2.45 GHz and four efficiency cores running up to 1.9 GHz. The Kryo 280 uses a 64-bit ARMv8-A instruction set and employs a multi-level cache hierarchy with separate 4KB L0 caches for each core, 16KB L1 caches, and a shared 2MB L2 cache.Ceph majority commit



Ceph majority commitFei (James) Liu
?
The behavior In original flow:
1) In the case of 3 copies, the client sends the write to the primary, and then the primary forwards to the other two replicas. The primary must wait for the commit until all the replicas from completion. The real write IO latency is the longest latency among three copies.
2) When the data distribution is not uniform, the osd node which owns hottest data will become the bottleneck of total latency.
The behavior In our enhancement:
commit_majority function is not required to wait for all copies of commit to complete: as long as the majority of the commit is completed, the cluster would notify the client to complete.Zero bugs found? Hold my beer AFL! how to improve coverage-guided fuzzing and...



Zero bugs found? Hold my beer AFL! how to improve coverage-guided fuzzing and...Maksim Shudrak
?
Fuzzing remains to be the most effective technique for bugs hunting in memory-unsafe programs. Last year, hundreds of security papers and talks on fuzzing have been published and dozens of them were focused on adapting or improving American Fuzzy Lop in some way. Attracting with its simplicity and efficiency, AFL is the number one choice for the vast majority of security researchers. This high popularity means that hunting for bugs with AFL or a similar tool is becoming less and less fruitful since many projects are already covered by other researchers. It is especially hard when we talk about a project participating in Google OSS-Fuzz program which utilizes AFL to generate a half-trillion test cases per day.
In practice, this means that we can not blindly rely on AFL anymore and should search for better fuzzing techniques. In order to overcome this challenge, we need to understand how AFL and similar fuzzers work and be able to use their weaknesses to find new 0days. This talk is aimed to discuss these weaknesses on real examples, explain how we can do fuzzing better and release a new open-source fuzzer called Manul.
Manul is a high-scalable coverage-guided parallel fuzzer with the ability to search for bugs in open source and black box binaries on Windows and Linux. Manul was able to find 10 0-days in 4 widely-used projects that have been extensively tested by AFL. These vulnerabilities were not found by chance, but by analyzing and addressing issues exist in AFL. Authors will show several of the most critical vulnerabilities and explain why AFL overlooked them.
This talk will be interested for experienced hackers, who are willing to improve their bug hunting capabilities, as well as for new researchers, who are making their first steps on the thorny trail of bug hunting.DEF CON 27 - MAKSIM SHUDRAK - zero bugs found hold my beer afl how to improve...



DEF CON 27 - MAKSIM SHUDRAK - zero bugs found hold my beer afl how to improve...Felipe Prado
?
DEF CON 27 - MAKSIM SHUDRAK - zero bugs found hold my beer afl how to improve coverage guided fuzzing and find new zero days in tough targetsFilesystem Showdown: What a Difference a Decade Makes



Filesystem Showdown: What a Difference a Decade MakesPerforce
?
In the last 10 years, Ext4 has risen in prominence, ReiserFS has fallen to the wayside, ZFS has been ported to Linux, XFS keeps plugging along, and there's a new kid: Btrfs. NTFS has evolved, too. It's now 2016. How do these filesystems stack up against each other? Does it really make that much of a difference? WeˇŻll show you the results of standard, consistent tests across platforms (Linux vs. Windows) and filesystems to see if the differences are worth choosing one over the other. For simplicity's sake, the tests are performed on identical hardware with out-of-the-box settings.BKK16-308 The tool called Auto-Tuned Optimization System (ATOS)



BKK16-308 The tool called Auto-Tuned Optimization System (ATOS)Linaro
?
ATOS is an Auto Tuning Optimization System that is able to find automatically the best performance/size tradeoff from a build system and a training application. The input of ATOS tools are a build command and a run command. From the build command, ATOS will infer an internal build configuration that it will run with different sets of compiler options. These build configurations are executed with the run command from which code size and performance will be extracted.
From the set of build configurations that ATOS explores, one can extract the preferred trade-off between code size and performance. The extracted build configuration can be archived and replayed later in order to generate the optimized executable without any modification into the initial build system.
The nice property of ATOS is that NO modification of the sources or the makefiles are needed. ATOS can work on any large/deep project, as soon as the compiler used is gcc or LLVM under Linux.Creating a SNP calling pipeline



Creating a SNP calling pipelineDan Bolser
?
The document describes creating a SNP calling pipeline for potato data from RNA-Seq experiments. Key steps included aligning reads to the potato genome using BWA or Bowtie, converting SAM to BAM and sorting, generating coverage profiles with SAMtools, and calling SNPs from the BAM files using SAMtools and bcftools. SNPs identified from the RNA-Seq data were then selected for inclusion on an Illumina GoldenGate SNP chip to genotype samples for genetic mapping. Comparison of the SNP chip results to the original RNA-Seq data was performed to evaluate accuracy. Remaining questions around discrepancies in the data were noted for further investigation.Design for Test [DFT]-1 (1).pdf DESIGN DFT![Design for Test [DFT]-1 (1).pdf DESIGN DFT](https://cdn.slidesharecdn.com/ss_thumbnails/designfortestdft-11-231227151941-28a508a3-thumbnail.jpg?width=560&fit=bounds)
![Design for Test [DFT]-1 (1).pdf DESIGN DFT](https://cdn.slidesharecdn.com/ss_thumbnails/designfortestdft-11-231227151941-28a508a3-thumbnail.jpg?width=560&fit=bounds)
![Design for Test [DFT]-1 (1).pdf DESIGN DFT](https://cdn.slidesharecdn.com/ss_thumbnails/designfortestdft-11-231227151941-28a508a3-thumbnail.jpg?width=560&fit=bounds)
![Design for Test [DFT]-1 (1).pdf DESIGN DFT](https://cdn.slidesharecdn.com/ss_thumbnails/designfortestdft-11-231227151941-28a508a3-thumbnail.jpg?width=560&fit=bounds)
Design for Test [DFT]-1 (1).pdf DESIGN DFTjayasreenimmakuri777
?
The document discusses design for test (DFT) techniques. It explains that DFT aims to improve the testability of chip designs by adding mechanisms to control and observe internal nodes for manufacturing testing. This allows testing of each block or component on the chip to identify defective parts. Specifically, it discusses using scan chains to test combinational logic, and techniques like MBIST and boundary scan for testing memories and I/O, respectively. The goal of DFT is to effectively test designs at the component level to improve quality and yield.2.6 latifs 17 dramix pisos sobre pilotes 



2.6 latifs 17 dramix pisos sobre pilotes Latifs Chile
?
The document summarizes the results of large scale tests conducted to validate the design concept for slab on piles reinforcement using structural fibers. Four slabs were tested under different loading conditions to evaluate bending resistance and cracking behavior. Ultimate loads from the tests were over 2-3 times the maximum allowable design loads, and first cracking occurred at loads meeting design safety standards. The document concludes that the bending design method using structural fibers from Bekaert is safe based on the test results.Jain-DeCO-FCCM-2016



Jain-DeCO-FCCM-2016Abhishek Jain
?
The document describes a DSP block based FPGA accelerator overlay called DeCO that has low interconnect overhead. It presents DeCO as an improvement over previous DSP overlay approaches in terms of lower interconnect area overhead and higher peak performance. DeCO is evaluated through mapping various compute kernels to it and is shown to achieve up to 95% functional unit utilization and 264 GOPS peak performance on Zynq, which is 10x better than prior works. It also has faster configuration time compared to HLS generated implementations.OIF CEI 56-G-FOE-April2015



OIF CEI 56-G-FOE-April2015Deborah Porchivina
?
Tom Palkert of Luxtera and MoSys and the OIF PLL Vice Chair Electrical spoke at the Fiber Optics Expo in Japan on 56G CEI - Electrical Interfaces, port density requirements, applications, PAM-4 vs NRZ results and argumentsJGI_HMMER.pptx



JGI_HMMER.pptxWilliam Arndt
?
William Arndt increased the performance of HMMER3 on Genepool by modifying it to use buffering and multiple threads more efficiently. An example showed that searching a large protein database took 27 minutes using the modified HMMER3 with 32 threads, compared to 25 hours using the original single-threaded version. The modifications avoid repeated reading of input files by buffering sequence and HMM data in memory for reuse across multiple models.MAKER2



MAKER2Shaojun Xie
?
William Arndt increased the performance of HMMER3 on Genepool by modifying it to use buffered I/O and multiple threads more efficiently. The original HMMER3 was inefficient because it read sequence files from disk repeatedly instead of buffering them in memory. The modified version stores sequences and HMMs in buffers that multiple threads can search simultaneously, reducing I/O time from 25% to less than 1% and allowing full utilization of Genepool nodes. Future work includes porting these improvements to other NERSC systems and upgrading algorithms to use modern vector instructions.Porting and Optimization of Numerical Libraries for ARM SVE



Porting and Optimization of Numerical Libraries for ARM SVELinaro
?
By Toshiyuki Imamura, RIKEN AICS
RIKEN and Fujitsu are developing ARM-based numerical libraries optimized with the new feature of ARM-SVE. We present porting status of netlib+SSL-II for ARM-SVE and other OSS. Also, we demonstrate some optimization policies and techniques, especially for the basic numerical linear algebra kernels.
Toshiyuki Imamura Bio
Toshiyuki Imamura is currently a team leader of Large-scale Parallel Numerical Computing Technology at Advanced Institute for Computational Science (AICS), RIKEN. He is in charge of the development of numerical libraries for the post-K project. His research interests include high-performance computing, automatic-tuning technology, eigenvalue computation (algorithm/software/applications), etc. He and his colleagues (Japan Atomic Energy Agency (JAEA) team) were nominated as one of the finalists of Gordon Bell Prize in SC05 and SC06. He is a member of IPSJ, JSIAM, and SIAM.
Email
imamura.toshiyuki@riken.jp
For more info on The Linaro High Performance Computing (HPC) visit https://www.linaro.org/sig/hpc/Low Overhead System Tracing with eBPF



Low Overhead System Tracing with eBPFAkshay Kapoor
?
In the Container world, there is a need to build observability around apps and backing services running in containers. The observability should allow to capture on demand low level metrics at a low overhead. The proposal is to use ebpf as the tracing technology to capture details at kernel & user level, and generate on demand flamegraphs, heat maps for applications & backing services. The Linux kernel has a built-in BPF JIT compiler, and an in-kernel verifier which is used to validate eBPF programs. This allows user defined instrumentation on a live kernel image that can never crash, hang or interfere with the kernel negatively. eBPF provides in-kernel implementation of storage maps such as histograms and hash-maps, which helps in efficient copy of summarized monitoring data from kernel to user space with low overhead.
These features make eBPF programs safe to run in production and allow admins and engineers to collect crucial data from systems for performance analysis and monitoring.Hands-on Experience with IPv6 Routing and Services



Hands-on Experience with IPv6 Routing and ServicesCisco Canada
?
This document provides an agenda and overview for a hands-on lab session on IPv6 routing and services. The lab session will consist of 8 exercises that provide experience with IPv6 addressing, neighbor discovery, static routing, HSRP, EIGRPv6, tunnels, OSPFv3, and BGPv6. The first lab focuses on configuring IPv6 addressing and stateless address autoconfiguration on routers and hosts in a simple site using unique local addresses. Subsequent labs introduce global unicast addressing across multiple sites and additional labs cover various IPv6 routing protocols.×ÔÂÉŇƶŻĄíĄÜĄĂĄČĎň¤±ĄĎ©`ĄÉ?Ą˝ĄŐĄČе÷¤Î¤ż¤á¤ÎĄłĄóĄÝ©`ĄÍĄóĄČÉčĽĆÖ§Ô®ĄÄ©`Ąë



×ÔÂÉŇƶŻĄíĄÜĄĂĄČĎň¤±ĄĎ©`ĄÉ?Ą˝ĄŐĄČе÷¤Î¤ż¤á¤ÎĄłĄóĄÝ©`ĄÍĄóĄČÉčĽĆÖ§Ô®ĄÄ©`ĄëKazushi Yamashina
?
This document discusses FPGA and ROS integration using cReComp. cReComp is a tool that allows defining reusable FPGA components using a specification language and integrating them with ROS. It handles the hardware/software interface and generation of HDL, C++ code and ROS packages from a single specification file. An example is provided of using cReComp to implement an ultrasonic sensor component on an FPGA board running Linux and ROS. The goal is to explore using this approach to implement visual SLAM on an FPGA for low power robotics applications.Usage, Performance and Future Of PL1 at NRB Benoit Ebner



Usage, Performance and Future Of PL1 at NRB Benoit EbnerNRB
?
When Peter Elderon visited NRB to present the evolution of PL1, Benoit Ebner made this presentation on how this programmation language is used at NRB.Fuzzing for CPS Mutation Testing



Fuzzing for CPS Mutation TestingLionel Briand
?
This document summarizes a research paper on using grey-box fuzzing (MOTIF) for mutation testing of C/C++ code in cyber-physical systems (CPS). It introduces mutation testing and grey-box fuzzing, and proposes MOTIF which generates a fuzzing driver to test functions with live mutants. An empirical evaluation compares MOTIF to symbolic execution-based mutation testing on three subject programs. MOTIF killed more mutants within 10,000 seconds and was able to test programs that symbolic execution could not handle due to limitations like floating-point values. Seed inputs alone killed few mutants, showing the importance of fuzzing. MOTIF is an effective approach for mutation testing of CPS software.New features in Ruby 2.5



New features in Ruby 2.5Ireneusz Skrobi?
?
Ruby 2.5 includes new features such as allowing rescue/else/ensure blocks directly in do/end, yield_self, Hash slicing methods, and Struct classes that accept keyword arguments. It also provides performance improvements like removing trace instructions for 5-10% faster execution and optimizing block passing. Additionally, there are other notable changes like Thread exceptions defaulting to report, SecureRandom preferring OS sources, and updates to standard libraries, Unicode version, RubyGems, and RDoc.Odoo Performance Limits



Odoo Performance LimitsOdoo
?
1. The document describes load testing done on an Odoo implementation to determine system limits and size requirements. Tests were run using Locust and varied the number of requests per second, users, and sessions to identify bottlenecks.
2. Testing showed the initial limit was around 500 requests/second. Further tests found that sessions stored in NFS caused issues, so they were changed to store in PostgreSQL.
3. Load balanced and monolithic architectures were compared, finding the load balanced setup using 4 servers performed similarly to a single server with 40 cores for the monolithic setup.Dynamische Routingprotokolle Aufzucht und Pflege - OSPF



Dynamische Routingprotokolle Aufzucht und Pflege - OSPFMaximilan Wilhelm
?
Herzlichen Gl¨ąckwunsch! Sie d¨ąrfen ein Netzwerk mit mehr als 2 Routern administrieren. Dieser Vortrag erl?utert, warum statisches Routing keine L?sung ist und schneller als einem lieb ist zum Problem werden kann. Als Einf¨ąhrung in dynamisches Routing und OSPF, erkl?rt dieser Vortrag wie sich Router gegenseitig finden, Routen austauschen, was eine Area ist und wie die Link-State Datenbank funktioniert.
OSPF wird praktisch am Beispiel des Bird Internet Routing Daemons und in Zusammenspiel mit klassischen Herstellern gezeigt.ĄŐĄˇĄ¸ĄóĄ°ĄÄ©`Ąë´ˇąół˘¤ÎŔűÓäňÖ§Ô®¤ą¤ëĄÄ©`ĄëąółÜłúłú4µţ¤Ë¤č¤ëĄŐĄˇĄ¸ĄóĄ°˝ĚÓý¤ÎĘÔ¤ß



ĄŐĄˇĄ¸ĄóĄ°ĄÄ©`Ąë´ˇąół˘¤ÎŔűÓäňÖ§Ô®¤ą¤ëĄÄ©`ĄëąółÜłúłú4µţ¤Ë¤č¤ëĄŐĄˇĄ¸ĄóĄ°˝ĚÓý¤ÎĘÔ¤ßNorihiro Yoshida
?
µÚ8»Ř ŚgĽůµÄIT˝ĚÓýĄ·ĄóĄÝĄ¸Ą¦Ąŕ rePiT2022Extracting a Micro State Transition Table Using KLEE



Extracting a Micro State Transition Table Using KLEENorihiro Yoshida
?
"Extracting a Micro State Transition Table Using KLEE", 2nd International KLEE Workshop on Symbolic Execution (KLEE 2021)

Ą˝ĄŐĄČĄ¦Ą§Ą˘é_°k¤Ë¤Ş¤±¤ë®bѧ…f„“ĄŐĄ©©`ĄéĄŕ ĄŞ©`Ą×ĄËĄóĄ°ŮYÁĎNorihiro Yoshida
?
Ą˝ĄŐĄČĄ¦Ą§Ą˘é_°k¤Ë¤Ş¤±¤ë®bѧ…f„“ĄŐĄ©©`ĄéĄŕ ĄŞ©`Ą×ĄËĄóĄ°ŮYÁĎĄł©`ĄÉĄŻĄí©`Ąó —Ęłö?‰ä¸üąÜŔíĄÄ©`ĄëČş¤Îé_°k



Ął©`ĄÉĄŻĄí©`Ąó —Ęłö?‰ä¸üąÜŔíĄÄ©`ĄëČş¤Îé_°kNorihiro Yoshida
?
Ą˝ĄŐĄČĄ¦Ą§Ą˘żŞ°k¤Ë¤Ş¤±¤ë˛úѧд´ĄŐĄ©©`ĄéĄŕŁ¨ĄÝĄąĄż©`°k±íŁ© Proactive Clone Recommendation System for Extract Method Refactoring



Proactive Clone Recommendation System for Extract Method RefactoringNorihiro Yoshida
?
ˇ°Extract Methodˇ± refactoring is commonly used for
merging code clones into a single new method. In this position
paper, we propose a proactive clone recommendation system for
ˇ°Extract Methodˇ± refactoring. The proposed system that has
been implemented as Eclipse plug-in monitors code modifications
on the fly. Once the proposed system detects an ˇ°Extract Methodˇ±
refactoring instance based on the analysis of code modifications,
it recommends code clones of the refactored code as refactoring
candidates. The preliminary user study shows that the users are
able to refactor a greater number of clones in less time compared
to a code clone analysis environment GemX.Code Search Based on Deep Neural Network and Code Mutation



Code Search Based on Deep Neural Network and Code MutationNorihiro Yoshida
?
şÝşÝߣs for the paper "Code Search Based on Deep Neural Network and Code Mutation" in the Proceeding of the 13th International Workshop on Software Clones (IWSC 2019), in conjunction with the 26th edition of the IEEE International Conference on Software Analysis, Evolution, and Reengineering (SANER 2019), Hangzhou, China, February 2019.»úеѧϰĄ·ĄąĄĆĄŕ¤Ë¤Ş¤±¤ëĽĽĘőµÄ¸şŐ®¤Ë¤Ä¤¤¤Ć



»úеѧϰĄ·ĄąĄĆĄŕ¤Ë¤Ş¤±¤ëĽĽĘőµÄ¸şŐ®¤Ë¤Ä¤¤¤ĆNorihiro Yoshida
?
µÚ1»Ř»úеѧϰą¤Ń§Ąď©`ĄŻĄ·ĄçĄĂĄ×Ł¨˛Ńł˘ł§·ˇ2018Ł©When, why and for whom do practitioners detect technical debts?: An experienc...



When, why and for whom do practitioners detect technical debts?: An experienc...Norihiro Yoshida
?
First International Workshop on Technical Debt Analytics (TDA 2016), in conjunction with the 23rd Asia-Pacific Software Engineering Conference (APSEC 2016), University of Waikato, Hamilton, New Zealand, 6th December 2016.More Related Content
Similar to A Quantitative Comparison of Coverage-Based Greybox Fuzzers (14)
2.6 latifs 17 dramix pisos sobre pilotes 



2.6 latifs 17 dramix pisos sobre pilotes Latifs Chile
?
The document summarizes the results of large scale tests conducted to validate the design concept for slab on piles reinforcement using structural fibers. Four slabs were tested under different loading conditions to evaluate bending resistance and cracking behavior. Ultimate loads from the tests were over 2-3 times the maximum allowable design loads, and first cracking occurred at loads meeting design safety standards. The document concludes that the bending design method using structural fibers from Bekaert is safe based on the test results.Jain-DeCO-FCCM-2016



Jain-DeCO-FCCM-2016Abhishek Jain
?
The document describes a DSP block based FPGA accelerator overlay called DeCO that has low interconnect overhead. It presents DeCO as an improvement over previous DSP overlay approaches in terms of lower interconnect area overhead and higher peak performance. DeCO is evaluated through mapping various compute kernels to it and is shown to achieve up to 95% functional unit utilization and 264 GOPS peak performance on Zynq, which is 10x better than prior works. It also has faster configuration time compared to HLS generated implementations.OIF CEI 56-G-FOE-April2015



OIF CEI 56-G-FOE-April2015Deborah Porchivina
?
Tom Palkert of Luxtera and MoSys and the OIF PLL Vice Chair Electrical spoke at the Fiber Optics Expo in Japan on 56G CEI - Electrical Interfaces, port density requirements, applications, PAM-4 vs NRZ results and argumentsJGI_HMMER.pptx



JGI_HMMER.pptxWilliam Arndt
?
William Arndt increased the performance of HMMER3 on Genepool by modifying it to use buffering and multiple threads more efficiently. An example showed that searching a large protein database took 27 minutes using the modified HMMER3 with 32 threads, compared to 25 hours using the original single-threaded version. The modifications avoid repeated reading of input files by buffering sequence and HMM data in memory for reuse across multiple models.MAKER2



MAKER2Shaojun Xie
?
William Arndt increased the performance of HMMER3 on Genepool by modifying it to use buffered I/O and multiple threads more efficiently. The original HMMER3 was inefficient because it read sequence files from disk repeatedly instead of buffering them in memory. The modified version stores sequences and HMMs in buffers that multiple threads can search simultaneously, reducing I/O time from 25% to less than 1% and allowing full utilization of Genepool nodes. Future work includes porting these improvements to other NERSC systems and upgrading algorithms to use modern vector instructions.Porting and Optimization of Numerical Libraries for ARM SVE



Porting and Optimization of Numerical Libraries for ARM SVELinaro
?
By Toshiyuki Imamura, RIKEN AICS
RIKEN and Fujitsu are developing ARM-based numerical libraries optimized with the new feature of ARM-SVE. We present porting status of netlib+SSL-II for ARM-SVE and other OSS. Also, we demonstrate some optimization policies and techniques, especially for the basic numerical linear algebra kernels.
Toshiyuki Imamura Bio
Toshiyuki Imamura is currently a team leader of Large-scale Parallel Numerical Computing Technology at Advanced Institute for Computational Science (AICS), RIKEN. He is in charge of the development of numerical libraries for the post-K project. His research interests include high-performance computing, automatic-tuning technology, eigenvalue computation (algorithm/software/applications), etc. He and his colleagues (Japan Atomic Energy Agency (JAEA) team) were nominated as one of the finalists of Gordon Bell Prize in SC05 and SC06. He is a member of IPSJ, JSIAM, and SIAM.
Email
imamura.toshiyuki@riken.jp
For more info on The Linaro High Performance Computing (HPC) visit https://www.linaro.org/sig/hpc/Low Overhead System Tracing with eBPF



Low Overhead System Tracing with eBPFAkshay Kapoor
?
In the Container world, there is a need to build observability around apps and backing services running in containers. The observability should allow to capture on demand low level metrics at a low overhead. The proposal is to use ebpf as the tracing technology to capture details at kernel & user level, and generate on demand flamegraphs, heat maps for applications & backing services. The Linux kernel has a built-in BPF JIT compiler, and an in-kernel verifier which is used to validate eBPF programs. This allows user defined instrumentation on a live kernel image that can never crash, hang or interfere with the kernel negatively. eBPF provides in-kernel implementation of storage maps such as histograms and hash-maps, which helps in efficient copy of summarized monitoring data from kernel to user space with low overhead.
These features make eBPF programs safe to run in production and allow admins and engineers to collect crucial data from systems for performance analysis and monitoring.Hands-on Experience with IPv6 Routing and Services



Hands-on Experience with IPv6 Routing and ServicesCisco Canada
?
This document provides an agenda and overview for a hands-on lab session on IPv6 routing and services. The lab session will consist of 8 exercises that provide experience with IPv6 addressing, neighbor discovery, static routing, HSRP, EIGRPv6, tunnels, OSPFv3, and BGPv6. The first lab focuses on configuring IPv6 addressing and stateless address autoconfiguration on routers and hosts in a simple site using unique local addresses. Subsequent labs introduce global unicast addressing across multiple sites and additional labs cover various IPv6 routing protocols.×ÔÂÉŇƶŻĄíĄÜĄĂĄČĎň¤±ĄĎ©`ĄÉ?Ą˝ĄŐĄČе÷¤Î¤ż¤á¤ÎĄłĄóĄÝ©`ĄÍĄóĄČÉčĽĆÖ§Ô®ĄÄ©`Ąë



×ÔÂÉŇƶŻĄíĄÜĄĂĄČĎň¤±ĄĎ©`ĄÉ?Ą˝ĄŐĄČе÷¤Î¤ż¤á¤ÎĄłĄóĄÝ©`ĄÍĄóĄČÉčĽĆÖ§Ô®ĄÄ©`ĄëKazushi Yamashina
?
This document discusses FPGA and ROS integration using cReComp. cReComp is a tool that allows defining reusable FPGA components using a specification language and integrating them with ROS. It handles the hardware/software interface and generation of HDL, C++ code and ROS packages from a single specification file. An example is provided of using cReComp to implement an ultrasonic sensor component on an FPGA board running Linux and ROS. The goal is to explore using this approach to implement visual SLAM on an FPGA for low power robotics applications.Usage, Performance and Future Of PL1 at NRB Benoit Ebner



Usage, Performance and Future Of PL1 at NRB Benoit EbnerNRB
?
When Peter Elderon visited NRB to present the evolution of PL1, Benoit Ebner made this presentation on how this programmation language is used at NRB.Fuzzing for CPS Mutation Testing



Fuzzing for CPS Mutation TestingLionel Briand
?
This document summarizes a research paper on using grey-box fuzzing (MOTIF) for mutation testing of C/C++ code in cyber-physical systems (CPS). It introduces mutation testing and grey-box fuzzing, and proposes MOTIF which generates a fuzzing driver to test functions with live mutants. An empirical evaluation compares MOTIF to symbolic execution-based mutation testing on three subject programs. MOTIF killed more mutants within 10,000 seconds and was able to test programs that symbolic execution could not handle due to limitations like floating-point values. Seed inputs alone killed few mutants, showing the importance of fuzzing. MOTIF is an effective approach for mutation testing of CPS software.New features in Ruby 2.5



New features in Ruby 2.5Ireneusz Skrobi?
?
Ruby 2.5 includes new features such as allowing rescue/else/ensure blocks directly in do/end, yield_self, Hash slicing methods, and Struct classes that accept keyword arguments. It also provides performance improvements like removing trace instructions for 5-10% faster execution and optimizing block passing. Additionally, there are other notable changes like Thread exceptions defaulting to report, SecureRandom preferring OS sources, and updates to standard libraries, Unicode version, RubyGems, and RDoc.Odoo Performance Limits



Odoo Performance LimitsOdoo
?
1. The document describes load testing done on an Odoo implementation to determine system limits and size requirements. Tests were run using Locust and varied the number of requests per second, users, and sessions to identify bottlenecks.
2. Testing showed the initial limit was around 500 requests/second. Further tests found that sessions stored in NFS caused issues, so they were changed to store in PostgreSQL.
3. Load balanced and monolithic architectures were compared, finding the load balanced setup using 4 servers performed similarly to a single server with 40 cores for the monolithic setup.Dynamische Routingprotokolle Aufzucht und Pflege - OSPF



Dynamische Routingprotokolle Aufzucht und Pflege - OSPFMaximilan Wilhelm
?
Herzlichen Gl¨ąckwunsch! Sie d¨ąrfen ein Netzwerk mit mehr als 2 Routern administrieren. Dieser Vortrag erl?utert, warum statisches Routing keine L?sung ist und schneller als einem lieb ist zum Problem werden kann. Als Einf¨ąhrung in dynamisches Routing und OSPF, erkl?rt dieser Vortrag wie sich Router gegenseitig finden, Routen austauschen, was eine Area ist und wie die Link-State Datenbank funktioniert.
OSPF wird praktisch am Beispiel des Bird Internet Routing Daemons und in Zusammenspiel mit klassischen Herstellern gezeigt.More from Norihiro Yoshida (12)
ĄŐĄˇĄ¸ĄóĄ°ĄÄ©`Ąë´ˇąół˘¤ÎŔűÓäňÖ§Ô®¤ą¤ëĄÄ©`ĄëąółÜłúłú4µţ¤Ë¤č¤ëĄŐĄˇĄ¸ĄóĄ°˝ĚÓý¤ÎĘÔ¤ß



ĄŐĄˇĄ¸ĄóĄ°ĄÄ©`Ąë´ˇąół˘¤ÎŔűÓäňÖ§Ô®¤ą¤ëĄÄ©`ĄëąółÜłúłú4µţ¤Ë¤č¤ëĄŐĄˇĄ¸ĄóĄ°˝ĚÓý¤ÎĘÔ¤ßNorihiro Yoshida
?
µÚ8»Ř ŚgĽůµÄIT˝ĚÓýĄ·ĄóĄÝĄ¸Ą¦Ąŕ rePiT2022Extracting a Micro State Transition Table Using KLEE



Extracting a Micro State Transition Table Using KLEENorihiro Yoshida
?
"Extracting a Micro State Transition Table Using KLEE", 2nd International KLEE Workshop on Symbolic Execution (KLEE 2021)

Ą˝ĄŐĄČĄ¦Ą§Ą˘é_°k¤Ë¤Ş¤±¤ë®bѧ…f„“ĄŐĄ©©`ĄéĄŕ ĄŞ©`Ą×ĄËĄóĄ°ŮYÁĎNorihiro Yoshida
?
Ą˝ĄŐĄČĄ¦Ą§Ą˘é_°k¤Ë¤Ş¤±¤ë®bѧ…f„“ĄŐĄ©©`ĄéĄŕ ĄŞ©`Ą×ĄËĄóĄ°ŮYÁĎĄł©`ĄÉĄŻĄí©`Ąó —Ęłö?‰ä¸üąÜŔíĄÄ©`ĄëČş¤Îé_°k



Ął©`ĄÉĄŻĄí©`Ąó —Ęłö?‰ä¸üąÜŔíĄÄ©`ĄëČş¤Îé_°kNorihiro Yoshida
?
Ą˝ĄŐĄČĄ¦Ą§Ą˘żŞ°k¤Ë¤Ş¤±¤ë˛úѧд´ĄŐĄ©©`ĄéĄŕŁ¨ĄÝĄąĄż©`°k±íŁ© Proactive Clone Recommendation System for Extract Method Refactoring



Proactive Clone Recommendation System for Extract Method RefactoringNorihiro Yoshida
?
ˇ°Extract Methodˇ± refactoring is commonly used for
merging code clones into a single new method. In this position
paper, we propose a proactive clone recommendation system for
ˇ°Extract Methodˇ± refactoring. The proposed system that has
been implemented as Eclipse plug-in monitors code modifications
on the fly. Once the proposed system detects an ˇ°Extract Methodˇ±
refactoring instance based on the analysis of code modifications,
it recommends code clones of the refactored code as refactoring
candidates. The preliminary user study shows that the users are
able to refactor a greater number of clones in less time compared
to a code clone analysis environment GemX.Code Search Based on Deep Neural Network and Code Mutation



Code Search Based on Deep Neural Network and Code MutationNorihiro Yoshida
?
şÝşÝߣs for the paper "Code Search Based on Deep Neural Network and Code Mutation" in the Proceeding of the 13th International Workshop on Software Clones (IWSC 2019), in conjunction with the 26th edition of the IEEE International Conference on Software Analysis, Evolution, and Reengineering (SANER 2019), Hangzhou, China, February 2019.»úеѧϰĄ·ĄąĄĆĄŕ¤Ë¤Ş¤±¤ëĽĽĘőµÄ¸şŐ®¤Ë¤Ä¤¤¤Ć



»úеѧϰĄ·ĄąĄĆĄŕ¤Ë¤Ş¤±¤ëĽĽĘőµÄ¸şŐ®¤Ë¤Ä¤¤¤ĆNorihiro Yoshida
?
µÚ1»Ř»úеѧϰą¤Ń§Ąď©`ĄŻĄ·ĄçĄĂĄ×Ł¨˛Ńł˘ł§·ˇ2018Ł©When, why and for whom do practitioners detect technical debts?: An experienc...



When, why and for whom do practitioners detect technical debts?: An experienc...Norihiro Yoshida
?
First International Workshop on Technical Debt Analytics (TDA 2016), in conjunction with the 23rd Asia-Pacific Software Engineering Conference (APSEC 2016), University of Waikato, Hamilton, New Zealand, 6th December 2016.Revisiting the Relationship Between Code Smells and Refactoring



Revisiting the Relationship Between Code Smells and RefactoringNorihiro Yoshida
?
şÝşÝߣs for the paper "Revisiting the Relationship Between Code Smells and Refactoring" in the Proceedings of the 24th IEEE International Conference on Program Comprehension (ICPC 2016), Austin, TX, USA, May 2016 Mining the Modern Code Review Repositories: A Dataset of People, Process and ...



Mining the Modern Code Review Repositories: A Dataset of People, Process and ...Norihiro Yoshida
?
şÝşÝߣs for the data paper "Mining the Modern Code Review Repositories: A Dataset of People, Process and Product" in the proceedings of the 13th International Conference on Mining Software Repositories (MSR 2016), Austin, TX, May 2016.IWESEP 2013



IWESEP 2013Norihiro Yoshida
?
1) The document proposes a technique to support on-demand code reuse without interrupting coding tasks. It builds a source code corpus from open source projects and allows users to search for and complete code snippets without specifying search keywords.
2) An evaluation found the system can build large corpora from millions of lines of code within hours and return search results within 500ms. Precision is high for short inputs and highly similar code, but lower for less similar code.
3) Future work includes improving partitioning of code into keys and values, matching rules, and ranking search results to better support reuse of less similar code.MSR2013



MSR2013Norihiro Yoshida
?
This document describes two datasets for analyzing open source software code review processes. The datasets contain information about who submits and reviews code patches, the types of roles reviewers perform, review activity metrics, and reviewer statistics. Example applications include social network analysis of collaboration between reviewers and analyzing how reviewers' roles relate to privileges like testing code. The datasets are available online and are aimed to provide more detailed information about reviewers compared to downloading full review repository JSON files.

Recently uploaded (20)
Water Industry Process Automation & Control Monthly - March 2025.pdf



Water Industry Process Automation & Control Monthly - March 2025.pdfWater Industry Process Automation & Control
?
Welcome to the March 2025 issue of WIPAC Monthly the magazine brought to you by the LinkedIn Group WIPAC Monthly.
In this month's edition, on top of the month's news from the water industry we cover subjects from the intelligent use of wastewater networks, the use of machine learning in water quality as well as how, we as an industry, need to develop the skills base in developing areas such as Machine Learning and Artificial Intelligence.
Enjoy the latest editionFrankfurt University of Applied Science urkunde



Frankfurt University of Applied Science urkundeLisa Emerson
?
Duplicate Frankfurt University of Applied Science urkunde, make a Frankfurt UAS degree.Industrial Construction shed PEB MFG.pdf



Industrial Construction shed PEB MFG.pdfPLINTH & ROOFS
?
"Zen and the Art of Industrial Construction"
Once upon a time in Gujarat, Plinth and Roofs was working on a massive industrial shed project. Everything was going smoothlyˇŞblueprints were flawless, steel structures were rising, and even the cement was behaving. That is, until...
Meet Ramesh, the Stressed Engineer.
Ramesh was a perfectionist. He measured bolts with the precision of a Swiss watchmaker and treated every steel beam like his own child. But as the deadline approached, RameshˇŻs stress levels skyrocketed.
One day, he called Parul, the total management & marketing mastermind.
? Ramesh (panicking): "Parul maˇŻam! The roof isn't aligning by 0.2 degrees! This is a disaster!"
? Parul (calmly): "Ramesh, have you tried... meditating?"
? Ramesh: "Meditating? MaˇŻam, I have 500 workers on-site, and you want me to sit cross-legged and hum ˇ®OmˇŻ?"
? Parul: "Exactly. Mystic of Seven can help!"
Reluctantly, Ramesh agreed to a 5-minute guided meditation session.
? He closed his eyes.
??ˇá? He breathed deeply.
? He chanted "Om Namah Roofaya" (his custom version of a mantra).
When he opened his eyes, a miracle happened!
? His mind was clear.
? The roof magically aligned (okay, maybe the team just adjusted it while he was meditating).
? And for the first time, Ramesh smiled instead of calculating load capacities in his head.
? Lesson Learned: Sometimes, even in industrial construction, a little bit of mindfulness goes a long way.
From that day on, Plinth and Roofs introduced tea breaks with meditation sessions, and productivity skyrocketed!
Moral of the story: "When in doubt, breathe it out!"
#PlinthAndRoofs #MysticOfSeven #ZenConstruction #MindfulEngineeringLecture -3 Cold water supply system.pptx



Lecture -3 Cold water supply system.pptxrabiaatif2
?
The presentation on Cold Water Supply explored the fundamental principles of water distribution in buildings. It covered sources of cold water, including municipal supply, wells, and rainwater harvesting. Key components such as storage tanks, pipes, valves, and pumps were discussed for efficient water delivery. Various distribution systems, including direct and indirect supply methods, were analyzed for residential and commercial applications. The presentation emphasized water quality, pressure regulation, and contamination prevention. Common issues like pipe corrosion, leaks, and pressure drops were addressed along with maintenance strategies. Diagrams and case studies illustrated system layouts and best practices for optimal performance.Syntax Directed Definitions Synthesized Attributes and Inherited Attributes



Syntax Directed Definitions Synthesized Attributes and Inherited AttributesGunjalSanjay
?
Syntax Directed Definitions
US Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...



US Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...Thane Heins NOBEL PRIZE WINNING ENERGY RESEARCHER
?
Preface: The ReGenX Generator innovation operates with a US Patented Frequency Dependent Load
Current Delay which delays the creation and storage of created Electromagnetic Field Energy around
the exterior of the generator coil. The result is the created and Time Delayed Electromagnetic Field
Energy performs any magnitude of Positive Electro-Mechanical Work at infinite efficiency on the
generator's Rotating Magnetic Field, increasing its Kinetic Energy and increasing the Kinetic Energy of
an EV or ICE Vehicle to any magnitude without requiring any Externally Supplied Input Energy. In
Electricity Generation applications the ReGenX Generator innovation now allows all electricity to be
generated at infinite efficiency requiring zero Input Energy, zero Input Energy Cost, while producing
zero Greenhouse Gas Emissions, zero Air Pollution and zero Nuclear Waste during the Electricity
Generation Phase. In Electric Motor operation the ReGen-X Quantum Motor now allows any
magnitude of Work to be performed with zero Electric Input Energy.
Demonstration Protocol: The demonstration protocol involves three prototypes;
1. Protytpe #1, demonstrates the ReGenX Generator's Load Current Time Delay when compared
to the instantaneous Load Current Sine Wave for a Conventional Generator Coil.
2. In the Conventional Faraday Generator operation the created Electromagnetic Field Energy
performs Negative Work at infinite efficiency and it reduces the Kinetic Energy of the system.
3. The Magnitude of the Negative Work / System Kinetic Energy Reduction (in Joules) is equal to
the Magnitude of the created Electromagnetic Field Energy (also in Joules).
4. When the Conventional Faraday Generator is placed On-Load, Negative Work is performed and
the speed of the system decreases according to Lenz's Law of Induction.
5. In order to maintain the System Speed and the Electric Power magnitude to the Loads,
additional Input Power must be supplied to the Prime Mover and additional Mechanical Input
Power must be supplied to the Generator's Drive Shaft.
6. For example, if 100 Watts of Electric Power is delivered to the Load by the Faraday Generator,
an additional >100 Watts of Mechanical Input Power must be supplied to the Generator's Drive
Shaft by the Prime Mover.
7. If 1 MW of Electric Power is delivered to the Load by the Faraday Generator, an additional >1
MW Watts of Mechanical Input Power must be supplied to the Generator's Drive Shaft by the
Prime Mover.
8. Generally speaking the ratio is 2 Watts of Mechanical Input Power to every 1 Watt of Electric
Output Power generated.
9. The increase in Drive Shaft Mechanical Input Power is provided by the Prime Mover and the
Input Energy Source which powers the Prime Mover.
10. In the Heins ReGenX Generator operation the created and Time Delayed Electromagnetic Field
Energy performs Positive Work at infinite efficiency and it increases the Kinetic Energy of the
system.
Integration of Additive Manufacturing (AM) with IoT : A Smart Manufacturing A...



Integration of Additive Manufacturing (AM) with IoT : A Smart Manufacturing A...ASHISHDESAI85
?
Combining 3D printing with Internet of Things (IoT) enables the creation of smart, connected, and customizable objects that can monitor, control, and optimize their performance, potentially revolutionizing various industries. oT-enabled 3D printers can use sensors to monitor the quality of prints during the printing process. If any defects or deviations from the desired specifications are detected, the printer can adjust its parameters in real time to ensure that the final product meets the required standards.Env and Water Supply Engg._Dr. Hasan.pdf



Env and Water Supply Engg._Dr. Hasan.pdfMahmudHasan747870
?
Core course, namely Environment and Water Supply Engineering. Full lecture notes are in book format for the BSc in Civil Engineering program. How to Make an RFID Door Lock System using Arduino



How to Make an RFID Door Lock System using ArduinoCircuitDigest
?
Learn how to build an RFID-based door lock system using Arduino to enhance security with contactless access control.How to Build a Maze Solving Robot Using Arduino



How to Build a Maze Solving Robot Using ArduinoCircuitDigest
?
Learn how to make an Arduino-powered robot that can navigate mazes on its own using IR sensors and "Hand on the wall" algorithm.
This step-by-step guide will show you how to build your own maze-solving robot using Arduino UNO, three IR sensors, and basic components that you can easily find in your local electronics shop.Sachpazis: Foundation Analysis and Design: Single Piles



Sachpazis: Foundation Analysis and Design: Single PilesDr.Costas Sachpazis
?
¦Ń. ¦Ş?¦Ň¦Ó¦Á? ¦˛¦Á¦Ö¦Đ?¦Ć¦Ç?: Foundation Analysis and Design: Single Piles
Welcome to this comprehensive presentation on "Foundation Analysis and Design," focusing on Single PilesˇŞStatic Capacity, Lateral Loads, and Pile/Pole Buckling. This presentation will explore the fundamental concepts, equations, and practical considerations for designing and analyzing pile foundations.
We'll examine different pile types, their characteristics, load transfer mechanisms, and the complex interactions between piles and surrounding soil. Throughout this presentation, we'll highlight key equations and methodologies for calculating pile capacities under various conditions.US Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...



US Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...Thane Heins NOBEL PRIZE WINNING ENERGY RESEARCHER
?
Preface: The ReGenX Generator innovation operates with a US Patented Frequency Dependent Load Current Delay which delays the creation and storage of created Electromagnetic Field Energy around the exterior of the generator coil. The result is the created and Time Delayed Electromagnetic Field Energy performs any magnitude of Positive Electro-Mechanical Work at infinite efficiency on the generator's Rotating Magnetic Field, increasing its Kinetic Energy and increasing the Kinetic Energy of an EV or ICE Vehicle to any magnitude without requiring any Externally Supplied Input Energy. In Electricity Generation applications the ReGenX Generator innovation now allows all electricity to be generated at infinite efficiency requiring zero Input Energy, zero Input Energy Cost, while producing zero Greenhouse Gas Emissions, zero Air Pollution and zero Nuclear Waste during the Electricity Generation Phase. In Electric Motor operation the ReGen-X Quantum Motor now allows any magnitude of Work to be performed with zero Electric Input Energy.
Demonstration Protocol: The demonstration protocol involves three prototypes;
1. Protytpe #1, demonstrates the ReGenX Generator's Load Current Time Delay when compared to the instantaneous Load Current Sine Wave for a Conventional Generator Coil.
2. In the Conventional Faraday Generator operation the created Electromagnetic Field Energy performs Negative Work at infinite efficiency and it reduces the Kinetic Energy of the system.
3. The Magnitude of the Negative Work / System Kinetic Energy Reduction (in Joules) is equal to the Magnitude of the created Electromagnetic Field Energy (also in Joules).
4. When the Conventional Faraday Generator is placed On-Load, Negative Work is performed and the speed of the system decreases according to Lenz's Law of Induction.
5. In order to maintain the System Speed and the Electric Power magnitude to the Loads, additional Input Power must be supplied to the Prime Mover and additional Mechanical Input Power must be supplied to the Generator's Drive Shaft.
6. For example, if 100 Watts of Electric Power is delivered to the Load by the Faraday Generator, an additional >100 Watts of Mechanical Input Power must be supplied to the Generator's Drive Shaft by the Prime Mover.
7. If 1 MW of Electric Power is delivered to the Load by the Faraday Generator, an additional >1 MW Watts of Mechanical Input Power must be supplied to the Generator's Drive Shaft by the Prime Mover.
8. Generally speaking the ratio is 2 Watts of Mechanical Input Power to every 1 Watt of Electric Output Power generated.
9. The increase in Drive Shaft Mechanical Input Power is provided by the Prime Mover and the Input Energy Source which powers the Prime Mover.
10. In the Heins ReGenX Generator operation the created and Time Delayed Electromagnetic Field Energy performs Positive Work at infinite efficiency and it increases the Kinetic Energy of the system.Water Industry Process Automation & Control Monthly - March 2025.pdf



Water Industry Process Automation & Control Monthly - March 2025.pdfWater Industry Process Automation & Control
?
US Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...



US Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...Thane Heins NOBEL PRIZE WINNING ENERGY RESEARCHER
?
US Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...



US Patented ReGenX Generator, ReGen-X Quatum Motor EV Regenerative Accelerati...Thane Heins NOBEL PRIZE WINNING ENERGY RESEARCHER
?
A Quantitative Comparison of Coverage-Based Greybox Fuzzers
- 1. A Quantitative Comparison of Coverage-Based Greybox Fuzzers Natsuki Tsuzuki, Nagoya University, Japan Norihiro Yoshida, Nagoya University, Japan Koji Toda, Fukuoka Institute of Technology, Japan Kenji Fujiwara, National Institute of Technology, Toyota College , Japan Ryota Yamamoto, Nagoya University, Japan Hiroaki Takada, Nagoya University, Japan 1
- 2. Many Coverage-Based Greybox Fuzzers ? AFL (originally developed by Zalewski in ˇ®13) ? AFLFast (B?hme et al., CCS ˇ®16, TSE ˇ®19) ? AFLGo (B?hme et al., CCSˇŻ 17) ? FairFuzz (Lemieux & Sen, ASE ˇ®18) https://www.pikrepo.com/ 2
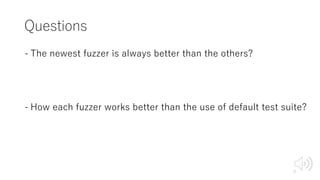
- 3. Questions - The newest fuzzer is always better than the others? - How each fuzzer works better than the use of default test suite? 3
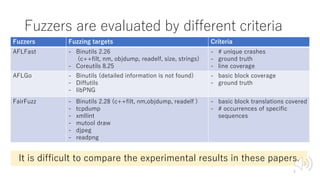
- 4. Fuzzers are evaluated by different criteria Fuzzers Fuzzing targets Criteria AFLFast - Binutils 2.26 (c++filt, nm, objdump, readelf, size, strings) - Coreutils 8.25 - # unique crashes - ground truth - line coverage AFLGo - Binutils (detailed information is not found) - Diffutils - libPNG - basic block coverage - ground truth FairFuzz - Binutils 2.28 (c++filt, nm,objdump, readelf ) - tcpdump - xmllint - mutool draw - djpeg - readpng - basic block translations covered - # occurrences of specific sequences It is difficult to compare the experimental results in these papers. 4
- 5. Research Overview We prepared a unified collection of fuzzing targets and then compared the existing fuzzers. Evaluation measures: - The number of executed paths - Branch coverage 5
- 6. Research Questions RQ1 Is a newer AFL-based fuzzer able to execute significantly a larger number of paths? RQ2 Does an AFL-based fuzzer improve branch coverage? RQ3 Does a newer AFL-based fuzzer always achieve higher coverage? 6
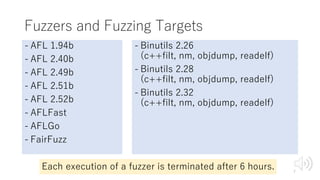
- 7. Fuzzers and Fuzzing Targets - AFL 1.94b - AFL 2.40b - AFL 2.49b - AFL 2.51b - AFL 2.52b - AFLFast - AFLGo - FairFuzz - Binutils 2.26 (c++filt, nm, objdump, readelf) - Binutils 2.28 (c++filt, nm, objdump, readelf) - Binutils 2.32 (c++filt, nm, objdump, readelf) Each execution of a fuzzer is terminated after 6 hours. 7
- 8. Significance test (# paths) We used Steel-Dwass test for judging the significance. AFL 1.94b AFL 2.40b AFL 2.49b AFL 2.51b AFL 2.52b AFLFast AFLGo FairFuzz AFL 1.94b - ? AFL 2.40b - ? AFL 2.49b - ? AFL 2.51b - ? AFL 2.52b - ? AFLFast - AFLGo - ? FairFuzz ? ? ? ? ? ? - Answer to RQ1: In most cases, the newest fuzzer FairFuzz executes significantly larger number of paths. 8
- 9. Branch coverage in the non-use and use of fuzzers Answer to RQ2: The fuzzers can improve branch coverage. 9
- 10. Significance test (branch coverage) We used Steel-Dwass test for judging the significance. AFL 1.94b AFL 2.40b AFL 2.49b AFL 2.51b AFL 2.52b AFLFast AFLGo FairFuzz AFL 1.94b - AFL 2.40b - AFL 2.49b - AFL 2.51b - AFL 2.52b - AFLFast - AFLGo - FairFuzz - Answer to RQ3: The newer fuzzer does not always achieve higher branch coverage. 10
- 11. Discussion The results are different between the number of paths and branch coverage. Newer fuzzers are unoptimized for quality assurance process based on branch coverage. The use of fuzzers can improve branch coverage. 11
- 12. Thank you for listening! E-mail: yoshida AT ertl.jp 12








