About computers
Download as pptx, pdf1 like506 views
The document discusses computers, focusing on their hardware components and software. It explains that a computer is a system of interconnected parts. Additionally, it touches on the topic of computer hacking.
1 of 5
Download to read offline




Ad
Recommended
Amr Chap 08 Operating Systems & Utility Programs
Amr Chap 08 Operating Systems & Utility Programssharing notes123
╠²
System software consists of operating systems and utility programs. Operating systems control computer hardware resources and are divided into stand-alone, server, and embedded categories. The boot process starts when a computer powers on, involving the BIOS performing POST to check components, then the operating system loads files and the desktop. Utility programs allow maintenance tasks like file management, uninstalling programs, and backing up files.Operating System
Operating Systemjoygracia
╠²
The operating system coordinates and monitors all activities of the computer hardware resources, allows running multiple programs simultaneously, and provides file management and security. It stores memory, monitors system performance, and provides user interfaces. Popular operating systems include Macintosh, Unix, and Windows. The operating system boots the system, allows multitasking of programs, connects the computer to the internet, monitors performances, and enables networking and resource sharing between devices while maintaining security.Ch1kiit [compatibility mode]
Ch1kiit [compatibility mode]Amit Gupta
╠²
This document provides an introduction and overview of operating systems. It defines an operating system as a program that manages computer hardware resources and provides common services for computer programs. It describes the four main components of a computer system: hardware, operating system, application programs, and users. It also outlines some of the key services an operating system provides, such as program execution, I/O operations, file management, and resource allocation. Finally, it discusses the structure and evolution of modern operating systems from early batch and time-sharing systems to current multiprogramming systems.3 evolution of os
3 evolution of osHekmatFaisal
╠²
The document discusses the boot process and evolution of operating systems. It explains that the boot process has two steps: first the POST checks hardware components and then the bootstrap loader loads the OS from the hard drive to RAM. It also summarizes the evolution of operating systems from batch systems of the 1950s, to time-sharing systems with multi-programming, to personal systems like DOS for single-user PCs, to parallel systems using multiple CPUs, distributed systems across networks, and real-time systems which perform tasks within time constraints.2 opreating system
2 opreating systemHekmatFaisal
╠²
The document discusses the key components and functions of an operating system:
1. It manages computer hardware resources and allows for the execution of user programs and applications.
2. It provides services like process management, memory management, file management, I/O management, and protection to programs and users.
3. Operating systems provide an interface between the user and computer system through functions like command interpretation.Operating system main
Operating system mainSwarnima Tiwari
╠²
An operating system acts as an intermediary between a computer user and the computer hardware. It makes the computer system convenient to use by allowing users to execute programs and efficiently allocating hardware resources like CPU time and memory among applications. The main components of a computer system are the hardware, operating system, application programs, and users. Common operating systems include Mac OS, Linux, UNIX, and Windows.Vm
VmI.I.T. Delhi
╠²
A virtual machine treats hardware and the operating system kernel as if they were physical hardware. It provides an interface identical to the underlying physical hardware. Resources of the physical computer are shared to create the illusion of multiple virtual machines, each with their own processor and memory. CPU scheduling and file systems allow for virtual devices like card readers and printers to be provided to each virtual machine.Prova2
Prova2guestfa23fdd9
╠²
This document provides information about memory and devices on a PC. It contains sections that show memory load, usage and paging files to monitor memory, as well as a device summary to view what hardware is installed on the personal computer. The memory section displays critical memory statistics, and the device summary lists the components inside the PC.How to donate toys for tots
How to donate toys for totsSwati Sharma
╠²
This document provides instructions for donating toys to Toys for Tots. It outlines how to donate money, used toys for Christmas, or toys to children's hospitals. Specific steps are given for donating toys to Toys for Tots, which allows people to clean out their homes while helping children in need at the same time. Contact information is provided to access more detailed donation instructions.How to calculate property tax
How to calculate property taxSwati Sharma
╠²
The document provides guidance on calculating property tax services in India, including methods such as using the mill rate and online payment options. It explains that property tax is a levy imposed by the government on an individual's tangible or personal assets. Additional resources and contact information are available on the website.How to decode json in php
How to decode json in phpSwati Sharma
╠²
The document provides information on how to decode JSON strings in PHP using the json_decode() function. It explains the purpose of the function, which is to convert JSON data into a format compatible with PHP. Additionally, it includes an example and a link for further reading.How to amplify wifi signal
How to amplify wifi signalSwati Sharma
╠²
The document provides guidance on how to amplify Wi-Fi signals for home use, including methods for routers and laptops. It emphasizes that laptops generally have stronger Wi-Fi capabilities compared to smartphones. For more details, it directs readers to a specific website resource.How to increase youtube traffic
How to increase youtube trafficSwati Sharma
╠²
The document provides services on how to increase YouTube traffic, including strategies for gaining more views, enhancing AdSense earnings, and increasing likes. It emphasizes the importance of understanding the target audience when creating content. The source for more information is provided through a website link.How to connect networking cables
How to connect networking cablesSwati Sharma
╠²
The document introduces www.whatisnetworking.net and details the services related to networking cables and connectors. It explains the types of networking cables and connectors, as well as the connection methods for twisted-pair cabling. For more information, it provides a contact link.How to start learning ethical hacking
How to start learning ethical hackingSwati Sharma
╠²
The document provides an introduction to learning ethical hacking, emphasizing the importance of mastering basic computer hacking tricks as a foundation. It suggests that starting from the essentials is the best method to become skilled in hacking. For more information, it directs readers to the website a2zcomputex.org.Star network
Star networkSwati Sharma
╠²
This document discusses star networks, which is a local area network (LAN) topology where all nodes or devices are connected directly to a central processor or hub. The document lists star network advantages and disadvantages, benefits, and topology as topics and provides a contact URL for more information on star networks.Hackers software
Hackers softwareSwati Sharma
╠²
The document discusses various hacking software available for mobile and Android devices, particularly those that can spy on cell phones. It indicates that many such software options on the market are ineffective or subpar. A link to a website with further information is provided.Temporary jobs for freshers
Temporary jobs for freshersSwati Sharma
╠²
The document provides information about temporary job opportunities for fresh graduates abroad. It encourages individuals to consider their skills and match them with available positions. Additionally, a website link is given for further registration and job listings.What is cms_in_php
What is cms_in_phpSwati Sharma
╠²
CMS in PHP is open-source software that allows users to access and modify its source code for enhancement. Open-source software provides flexibility for programmers to change how applications function, contributing to projects and textbooks that are freely available, including educational resources in fields like math.Adsense revenue for_1000_visits
Adsense revenue for_1000_visitsSwati Sharma
╠²
The document discusses Google AdSense revenue sharing percentages for exhibit and investigate ads, indicating that propagators receive 68% and 51% of the documented income, respectively. These percentages remain consistent regardless of the publisher's location and are not averaged among different publishers. It also mentions various topics related to earning money through Google AdSense.What does ghostwriting mean
What does ghostwriting meanSwati Sharma
╠²
The document discusses various forms of ghostwriting, including services for celebrities, CEOs, and blogs, emphasizing that ghostwriters are paid for their work but do not receive credit. It highlights the nature of ghostwriting as a profession where the writer is compensated without acknowledgment. Additional resources are available at the provided website.How important are meta tags in seo
How important are meta tags in seoSwati Sharma
╠²
Meta tags are snippets of text that describe the content of a webpage, although they do not appear on the page itself. The document discusses the importance and usage of meta tags in SEO for bloggers and provides examples. Additionally, it references the website www.a2zcomputex.org for more information on the topic.How to set up page margins in word 2007
How to set up page margins in word 2007Swati Sharma
╠²
The document provides information about the OSPF (Open Shortest Path First) routing protocol, including its area types, configuration commands, and basic principles. It highlights that OSPF uses link state advertisements for efficient routing updates, making it faster than RIP systems. Additionally, there are sections on OSPF state troubleshooting.What is the main purpose of ospf
What is the main purpose of ospfSwati Sharma
╠²
The document covers the basics of OSPF, including its area types and configuration commands. It also addresses troubleshooting OSPF states. Additional information can be found on the website linked in the document.How earn money from blog
How earn money from blogSwati Sharma
╠²
This document provides tips for earning money from blogging without relying on Adsense. It advises bloggers to carefully choose a niche topic that has wide appeal and isn't already saturated by other popular bloggers. Building an audience and providing unique, high-quality content on the chosen topic are keys to earning income through blog advertising and affiliate marketing on the site over time.What is 4g_technology_in_mobile_phones
What is 4g_technology_in_mobile_phonesSwati Sharma
╠²
4G technology, or fourth generation mobile communication, is a packet-switched wireless system designed for extensive coverage and high data rates, achieving speeds up to 20 Mbps. It aims to be cost-efficient while providing high performance, catering to mobile velocities up to 200 km/hr. The technology utilizes broad channels for improved performance in both uplink and downlink communication.What is a web crawler and how does it work
What is a web crawler and how does it workSwati Sharma
╠²
A web crawler is a systematic program that browses the World Wide Web to collect data and is primarily used by search engines to index web pages for faster searches. This process is known as web crawling or spidering. Various programming languages and tools are mentioned regarding the implementation and testing of web crawlers.How to donate eyes
How to donate eyesSwati Sharma
╠²
The document provides guidance on eye donation in India, including procedures for donating eyes both before and after death. It also offers information on how to register online for eye donation and highlights resources such as NGOs and eye banks involved in the movement. The primary aim is to enhance the collection of eyes across the country."Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays
╠²
What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.Wenn alles versagt - IBM Tape sch├╝tzt, was z├żhlt! Und besonders mit dem neust...
Wenn alles versagt - IBM Tape sch├╝tzt, was z├żhlt! Und besonders mit dem neust...Josef Weingand
╠²
IBM LTO10More Related Content
More from Swati Sharma (20)
How to donate toys for tots
How to donate toys for totsSwati Sharma
╠²
This document provides instructions for donating toys to Toys for Tots. It outlines how to donate money, used toys for Christmas, or toys to children's hospitals. Specific steps are given for donating toys to Toys for Tots, which allows people to clean out their homes while helping children in need at the same time. Contact information is provided to access more detailed donation instructions.How to calculate property tax
How to calculate property taxSwati Sharma
╠²
The document provides guidance on calculating property tax services in India, including methods such as using the mill rate and online payment options. It explains that property tax is a levy imposed by the government on an individual's tangible or personal assets. Additional resources and contact information are available on the website.How to decode json in php
How to decode json in phpSwati Sharma
╠²
The document provides information on how to decode JSON strings in PHP using the json_decode() function. It explains the purpose of the function, which is to convert JSON data into a format compatible with PHP. Additionally, it includes an example and a link for further reading.How to amplify wifi signal
How to amplify wifi signalSwati Sharma
╠²
The document provides guidance on how to amplify Wi-Fi signals for home use, including methods for routers and laptops. It emphasizes that laptops generally have stronger Wi-Fi capabilities compared to smartphones. For more details, it directs readers to a specific website resource.How to increase youtube traffic
How to increase youtube trafficSwati Sharma
╠²
The document provides services on how to increase YouTube traffic, including strategies for gaining more views, enhancing AdSense earnings, and increasing likes. It emphasizes the importance of understanding the target audience when creating content. The source for more information is provided through a website link.How to connect networking cables
How to connect networking cablesSwati Sharma
╠²
The document introduces www.whatisnetworking.net and details the services related to networking cables and connectors. It explains the types of networking cables and connectors, as well as the connection methods for twisted-pair cabling. For more information, it provides a contact link.How to start learning ethical hacking
How to start learning ethical hackingSwati Sharma
╠²
The document provides an introduction to learning ethical hacking, emphasizing the importance of mastering basic computer hacking tricks as a foundation. It suggests that starting from the essentials is the best method to become skilled in hacking. For more information, it directs readers to the website a2zcomputex.org.Star network
Star networkSwati Sharma
╠²
This document discusses star networks, which is a local area network (LAN) topology where all nodes or devices are connected directly to a central processor or hub. The document lists star network advantages and disadvantages, benefits, and topology as topics and provides a contact URL for more information on star networks.Hackers software
Hackers softwareSwati Sharma
╠²
The document discusses various hacking software available for mobile and Android devices, particularly those that can spy on cell phones. It indicates that many such software options on the market are ineffective or subpar. A link to a website with further information is provided.Temporary jobs for freshers
Temporary jobs for freshersSwati Sharma
╠²
The document provides information about temporary job opportunities for fresh graduates abroad. It encourages individuals to consider their skills and match them with available positions. Additionally, a website link is given for further registration and job listings.What is cms_in_php
What is cms_in_phpSwati Sharma
╠²
CMS in PHP is open-source software that allows users to access and modify its source code for enhancement. Open-source software provides flexibility for programmers to change how applications function, contributing to projects and textbooks that are freely available, including educational resources in fields like math.Adsense revenue for_1000_visits
Adsense revenue for_1000_visitsSwati Sharma
╠²
The document discusses Google AdSense revenue sharing percentages for exhibit and investigate ads, indicating that propagators receive 68% and 51% of the documented income, respectively. These percentages remain consistent regardless of the publisher's location and are not averaged among different publishers. It also mentions various topics related to earning money through Google AdSense.What does ghostwriting mean
What does ghostwriting meanSwati Sharma
╠²
The document discusses various forms of ghostwriting, including services for celebrities, CEOs, and blogs, emphasizing that ghostwriters are paid for their work but do not receive credit. It highlights the nature of ghostwriting as a profession where the writer is compensated without acknowledgment. Additional resources are available at the provided website.How important are meta tags in seo
How important are meta tags in seoSwati Sharma
╠²
Meta tags are snippets of text that describe the content of a webpage, although they do not appear on the page itself. The document discusses the importance and usage of meta tags in SEO for bloggers and provides examples. Additionally, it references the website www.a2zcomputex.org for more information on the topic.How to set up page margins in word 2007
How to set up page margins in word 2007Swati Sharma
╠²
The document provides information about the OSPF (Open Shortest Path First) routing protocol, including its area types, configuration commands, and basic principles. It highlights that OSPF uses link state advertisements for efficient routing updates, making it faster than RIP systems. Additionally, there are sections on OSPF state troubleshooting.What is the main purpose of ospf
What is the main purpose of ospfSwati Sharma
╠²
The document covers the basics of OSPF, including its area types and configuration commands. It also addresses troubleshooting OSPF states. Additional information can be found on the website linked in the document.How earn money from blog
How earn money from blogSwati Sharma
╠²
This document provides tips for earning money from blogging without relying on Adsense. It advises bloggers to carefully choose a niche topic that has wide appeal and isn't already saturated by other popular bloggers. Building an audience and providing unique, high-quality content on the chosen topic are keys to earning income through blog advertising and affiliate marketing on the site over time.What is 4g_technology_in_mobile_phones
What is 4g_technology_in_mobile_phonesSwati Sharma
╠²
4G technology, or fourth generation mobile communication, is a packet-switched wireless system designed for extensive coverage and high data rates, achieving speeds up to 20 Mbps. It aims to be cost-efficient while providing high performance, catering to mobile velocities up to 200 km/hr. The technology utilizes broad channels for improved performance in both uplink and downlink communication.What is a web crawler and how does it work
What is a web crawler and how does it workSwati Sharma
╠²
A web crawler is a systematic program that browses the World Wide Web to collect data and is primarily used by search engines to index web pages for faster searches. This process is known as web crawling or spidering. Various programming languages and tools are mentioned regarding the implementation and testing of web crawlers.How to donate eyes
How to donate eyesSwati Sharma
╠²
The document provides guidance on eye donation in India, including procedures for donating eyes both before and after death. It also offers information on how to register online for eye donation and highlights resources such as NGOs and eye banks involved in the movement. The primary aim is to enhance the collection of eyes across the country.Recently uploaded (20)
"Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays
╠²
What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.Wenn alles versagt - IBM Tape sch├╝tzt, was z├żhlt! Und besonders mit dem neust...
Wenn alles versagt - IBM Tape sch├╝tzt, was z├żhlt! Und besonders mit dem neust...Josef Weingand
╠²
IBM LTO109-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software
╠²
This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical Universes
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical UniversesSaikat Basu
╠²
Embark on a cosmic journey exploring the intersection of quantum
computing, consciousness, and ancient wisdom. Together we'll uncover the
recursive patterns that bind our reality.Smarter Aviation Data Management: Lessons from Swedavia Airports and Sweco
Smarter Aviation Data Management: Lessons from Swedavia Airports and SwecoSafe Software
╠²
Managing airport and airspace data is no small task, especially when youŌĆÖre expected to deliver it in AIXM format without spending a fortune on specialized tools. But what if there was a smarter, more affordable way?
Join us for a behind-the-scenes look at how Sweco partnered with Swedavia, the Swedish airport operator, to solve this challenge using FME and Esri.
Learn how they built automated workflows to manage periodic updates, merge airspace data, and support data extracts ŌĆō all while meeting strict government reporting requirements to the Civil Aviation Administration of Sweden.
Even better? Swedavia built custom services and applications that use the FME Flow REST API to trigger jobs and retrieve results ŌĆō streamlining tasks like securing the quality of new surveyor data, creating permdelta and baseline representations in the AIS schema, and generating AIXM extracts from their AIS data.
To conclude, FME expert Dean Hintz will walk through a GeoBorders reading workflow and highlight recent enhancements to FMEŌĆÖs AIXM (Aeronautical Information Exchange Model) processing and interpretation capabilities.
Discover how airports like Swedavia are harnessing the power of FME to simplify aviation data management, and how you can too.Curietech AI in action - Accelerate MuleSoft development
Curietech AI in action - Accelerate MuleSoft developmentshyamraj55
╠²
CurieTech AI in Action ŌĆō Accelerate MuleSoft Development
Overview:
This presentation demonstrates how CurieTech AIŌĆÖs purpose-built agents empower MuleSoft developers to create integration workflows faster, more accurately, and with less manual effort
linkedin.com
+12
curietech.ai
+12
meetups.mulesoft.com
+12
.
Key Highlights:
Dedicated AI agents for every stage: Coding, Testing (MUnit), Documentation, Code Review, and Migration
curietech.ai
+7
curietech.ai
+7
medium.com
+7
DataWeave automation: Generate mappings from tables or samplesŌĆö95%+ complete within minutes
linkedin.com
+7
curietech.ai
+7
medium.com
+7
Integration flow generation: Auto-create Mule flows based on specificationsŌĆöspeeds up boilerplate development
curietech.ai
+1
medium.com
+1
Efficient code reviews: Gain intelligent feedback on flows, patterns, and error handling
youtube.com
+8
curietech.ai
+8
curietech.ai
+8
Test & documentation automation: Auto-generate MUnit test cases, sample data, and detailed docs from code
curietech.ai
+5
curietech.ai
+5
medium.com
+5
Why Now?
Achieve 10├Ś productivity gains, slashing development time from hours to minutes
curietech.ai
+3
curietech.ai
+3
medium.com
+3
Maintain high accuracy with code quality matching or exceeding manual efforts
curietech.ai
+2
curietech.ai
+2
curietech.ai
+2
Ideal for developers, architects, and teams wanting to scale MuleSoft projects with AI efficiency
Conclusion:
CurieTech AI transforms MuleSoft development into an AI-accelerated workflowŌĆöletting you focus on innovation, not repetition.Coordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash
╠²
Coordinated Disclosure for ML - What's Different and What's the SamePyCon SG 25 - Firecracker Made Easy with Python.pdf
PyCon SG 25 - Firecracker Made Easy with Python.pdfMuhammad Yuga Nugraha
╠²
Explore the ease of managing Firecracker microVM with the firecracker-python. In this session, I will introduce the basics of Firecracker microVM and demonstrate how this custom SDK facilitates microVM operations easily. We will delve into the design and development process behind the SDK, providing a behind-the-scenes look at its creation and features. While traditional Firecracker SDKs were primarily available in Go, this module brings a simplicity of Python to the table.Salesforce Summer '25 Release Frenchgathering.pptx.pdf
Salesforce Summer '25 Release Frenchgathering.pptx.pdfyosra Saidani
╠²
Salesforce Summer '25 Release Frenchgathering.pptx.pdfCapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025pcprocore
╠²
¤æēØŚĪØŚ╝ØśüØŚ▓:ØŚ¢ØŚ╝ØŚĮØśå ØŚ╣ØŚČØŚ╗ØŚĖ & ØŚĮØŚ«ØśĆØśüØŚ▓ ØŚČØŚ╗ØśüØŚ╝ ØŚÜØŚ╝ØŚ╝ØŚ┤ØŚ╣ØŚ▓ ØŚ╗ØŚ▓Øśä ØśüØŚ«ØŚ»> https://pcprocore.com/ ¤æłŌŚĆ
CapCut Pro Crack is a powerful tool that has taken the digital world by storm, offering users a fully unlocked experience that unleashes their creativity. With its user-friendly interface and advanced features, itŌĆÖs no wonder why aspiring videographers are turning to this software for their projects.AI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D
╠²
This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.AI VIDEO MAGAZINE - June 2025 - r/aivideo
AI VIDEO MAGAZINE - June 2025 - r/aivideo1pcity Studios, Inc
╠²
AI VIDEO MAGAZINE - r/aivideo community newsletter ŌĆō Exclusive Tutorials: How to make an AI VIDEO from scratch, PLUS: How to make AI MUSIC, Hottest ai videos of 2025, Exclusive Interviews, New Tools, Previews, and MORE - JUNE 2025 ISSUE -Raman Bhaumik - Passionate Tech Enthusiast
Raman Bhaumik - Passionate Tech EnthusiastRaman Bhaumik
╠²
A Junior Software Developer with a flair for innovation, Raman Bhaumik excels in delivering scalable web solutions. With three years of experience and a solid foundation in Java, Python, JavaScript, and SQL, she has streamlined task tracking by 20% and improved application stability.EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdf
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdfEarley Information Science
╠²
As AI reshapes expectations in retail and B2B commerce, organizations are recognizing a critical reality: meaningful AI outcomes depend on well-structured, adaptable infrastructure. In this session, Seth Earley is joined by Phil Ryan - AI strategist, search technologist, and founder of Glass Leopard Technologies - for a candid conversation on what it truly means to engineer systems for scale, agility, and intelligence.
Phil draws on more than two decades of experience leading search and AI initiatives for enterprise organizations. Together, he and Seth explore the challenges businesses face when legacy architectures limit personalization, agility, and real-time decisioning - and what needs to change to support agentic technologies and next-best-action capabilities.
Key themes from the webinar include:
Composability as a prerequisite for AI╠²- Why modular, loosely coupled systems are essential for adapting to rapid innovation and evolving business needs
Search and relevance as foundational to AI╠²- How techniques honed-in enterprise search have laid the groundwork for more responsive and intelligent customer experiences
From MDM and CDP to agentic systems╠²- How data platforms are evolving to support richer customer context and dynamic orchestration
Engineering for business alignment╠²- Why successful AI programs require architectural decisions grounded in measurable outcomes
The conversation is practical and forward-looking, connecting deep technical understanding with real-world business needs. Whether youŌĆÖre modernizing your commerce stack or exploring how AI can enhance product discovery, personalization, or customer journeys, this session provides a clear-eyed view of the capabilities, constraints, and priorities that matter most.AI Agents and FME: A How-to Guide on Generating Synthetic Metadata
AI Agents and FME: A How-to Guide on Generating Synthetic MetadataSafe Software
╠²
In the world of AI agents, semantics is king. Good metadata is thus essential in an organization's AI readiness checklist. But how do we keep up with the massive influx of new data? In this talk we go over the tips and tricks in generating synthetic metadata for the consumption of human users and AI agents alike.From Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software
╠²
Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasnŌĆÖt yielding any results, so I expanded my search to second-hand dealer sitesŌĆöonly to realise that periodically checking each one was going to be tedious. ThatŌĆÖs when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platformŌĆÖs structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, IŌĆÖll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME canŌĆÖt buy a car for youŌĆöyetŌĆöit can certainly help you find the one youŌĆÖre after!Using the SQLExecutor for Data Quality Management: aka One man's love for the...
Using the SQLExecutor for Data Quality Management: aka One man's love for the...Safe Software
╠²
The SQLExecutor is one of FMEŌĆÖs most powerful and flexible transformers. Pivvot maintains a robust internal metadata hierarchy used to support ingestion and curation of thousands of external data sources that must be managed for quality before entering our platform. By using the SQLExecutor, Pivvot can efficiently detect problems and perform analysis before data is extracted from our staging environment, removing the need for rollbacks or cycles waisted on a failed job. This presentation will walk through three distinct examples of how Pivvot uses the SQLExecutor to engage its metadata hierarchy and integrate with its Data Quality Management workflows efficiently and within the source postgres database. Spatial Validation ŌĆōValidating spatial prerequisites before entering a production environment. Reference Data Validation - Dynamically validate domain-ed columns across any table and multiple columns per table. Practical De-duplication - Removing identical or near-identical well point locations from two distinct source datasets in the same table.GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdf
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdfPriyanka Aash
╠²
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing NowMastering AI Workflows with FME by Mark Do╠łring
Mastering AI Workflows with FME by Mark Do╠łringSafe Software
╠²
Harness the full potential of AI with FME: From creating high-quality training data to optimizing models and utilizing results, FME supports every step of your AI workflow. Seamlessly integrate a wide range of models, including those for data enhancement, forecasting, image and object recognition, and large language models. Customize AI models to meet your exact needs with FMEŌĆÖs powerful tools for training, optimization, and seamless integrationAd
About computers
- 3. ’é× About Computer And Its Parts, ’é× About Computer Software, ’é× About Computer Hacking
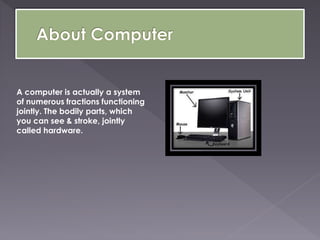
- 4. A computer is actually a system of numerous fractions functioning jointly. The bodily parts, which you can see & stroke, jointly called hardware.