Aix workload manager
- 1. Draft: Aix 5.2 WLM examples for the banking, based on business process prioritization Introduction: This is a short example of how p690 with AIX 5.2ML01 can be configured on the business needs trough WLM. Same ideas can be applied to any type of workload management. There are many other possibilities by dynamic and static lpars, database internal scheduling etc, it is important to use method which will best utilize all features of OS, database, application and workload characteristics. Purpose: WLM can do good job on partitioning machine into separate âsubmachinesâ. Such policy, presented in this paper, is based on the business purpose of the machine. It was essential to do, since applications were migrated from different platforms to new machine (consolidated, to use more appropriate word) it was not 100% clear how these applications will coexist. Also there was no formal consolidation process. There are more than one database instance on the machine with different business importance, resources consumed by one instance must not interfere with behavior of other instances, and e.g. more important database instance must have some minimal volume of the resources available on request. It is usual that machine is organized in batch/interactive class type of organization. Because of some advanced AIX 5.2 WLM features we decide to organize machine into classes based on business importance, and if there is a need for further sub-classification into batch/interactive each business class already have such subclasses defined by WLM. It is important to notice that WLM is not protection against hogs in one class and that WLM limitations on IO and memory can cause more harm than actual hog. So system behavior must be closely monitored. Methodology: Each process is classified automatically on start by WLM based on static rules and inheritance. Because of special nature of the oracle user processes such process actually needs at least one dynamic reclassification after database start to achieve appropriate class. WLM is started at the system boot and each 5 minutes goes dynamic reclassification, and naturally class statistics are collected too. Literature: AIX 5L Workload Manager (WLM), sg245977, Redbook
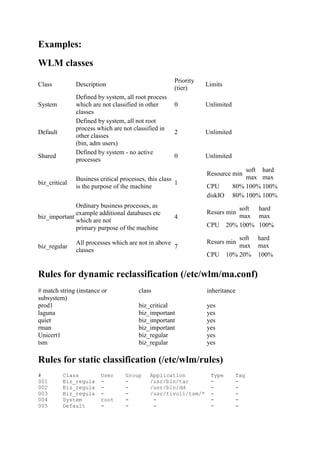
- 2. Examples: WLM classes Priority Class Description Limits (tier) Defined by system, all root process System which are not classified in other 0 Unlimited classes Defined by system, all not root process which are not classified in Default 2 Unlimited other classes (bin, adm users) Defined by system - no active Shared 0 Unlimited processes soft hard Resource min Business critical processes, this class max max biz_critical 1 is the purpose of the machine CPU 80% 100% 100% diskIO 80% 100% 100% Ordinary business processes, as soft hard example additional databases etc Resurs min biz_important 4 max max which are not primary purpose of the machine CPU 20% 100% 100% soft hard All processes which are not in above Resurs min biz_regular 7 max max classes CPU 10% 20% 100% Rules for dynamic reclassification (/etc/wlm/ma.conf) # match string (instance or class inheritance subsystem) prod1 biz_critical yes laguna biz_important yes quiet biz_important yes rman biz_important yes Unicert1 biz_regular yes tsm biz_regular yes Rules for static classification (/etc/wlm/rules) # Class User Group Application Type Tag 001 Biz_regula - - /usr/bin/tar - - 002 Biz_regula - - /usr/bin/dd - - 003 Biz_regula - - /usr/tivoli/tsm/* - - 004 System root - - - - 005 Default - - - - -
- 3. Dynamic reclassification: wlm-oracle.ksh script #!/usr/bin/ksh # Sample script to perform manual assignment of processes whose different # Instances can be differentiated by their output in ps -ef. # # # Examples of this kind of processes are ORACLE database instances. ## Create a configuration file /etc/wlm/ma.conf with the following format: # One line for each combination of: # # where: # o Instance Name is ORACLE instance. # o Class is the name of the class to assign the processes to; # Either `supername' for superclasses or `supername.subname' # for subclasses. # o Inheritance is a flag, which should be set to yes if you # want all processes belonging to a process group, whose # leader is the process being manually assigned, to be # manually assigned too, or no, otherwise. # MANUAL is an array of three positions, which one of them being: # o Position 0: Instance name. # o Position 1: Class name. # o Position 2: Inheritance flag. ############################################################# # Source SG24-5977-01 # 15.06.2003 Version 0 # original # a lot of bugs ... # wrong magic cookie, wlassign processing, space to coma etc ... # ############################################################# # 20.06.2003 version 1 # changes in CONF file # there can be comment lines start with hash # there can be empty lines # changes in script # assignment for each process separately - bug in argument list # comment and empty line processing in conf file # ############################################################# ## # DIRECTORIES ## WLMDIR=/etc/wlm ## # VARIABLES ## CONFFILE=$WLMDIR/ma.conf
- 4. PATH=/usr/bin:/usr/sbin:$PATH ## # FUNCTIONS ## getpids() { #error inst="$1" test -z "$inst" && exit 1 echo $(ps -ef | grep "$inst" | grep -v grep | awk '{ print $2 }') } ## # MAIN - ## egrep -v "^#" $CONFFILE| awk 'NF>0{print}'| (while read LINE do set -A MANUAL $LINE echo "Changing the inheritance attribute on class ${MANUAL[1]}..." OLDINH=`lsclass -f ${MANUAL[1]} | grep inheritance | awk '{ print $3 }' | sed "s/"//g"` [ ! "$OLDINH" ] && OLDINH="no" $ECHO chclass -a inheritance=${MANUAL[2]} ${MANUAL[1]} echo "Refreshing WLM..." wlmcntrl -u echo "Manually assigning the processes to class ${MANUAL[1]}..." echo "Getting PIDS' list for instance ${MANUAL[0]}..." n=0 for p in $(getpids ${MANUAL[0]}) do wlmassign -S ${MANUAL[1]} $p n=$(expr $n + 1) done echo "Assigning $n processes to class ${MANUAL[1]}..." echo "Resetting old inheritance value on class ${MANUAL[1]}..." chclass -a inheritance="$OLDINH" ${MANUAL[1]} echo "Refreshing WLM..." wlmcntrl -u done ) ####################### ##logger WLM updated exit 0



![PATH=/usr/bin:/usr/sbin:$PATH
##
# FUNCTIONS
##
getpids()
{
#error
inst="$1"
test -z "$inst" && exit 1
echo $(ps -ef | grep "$inst" | grep -v grep | awk '{ print $2 }')
}
##
# MAIN -
##
egrep -v "^#" $CONFFILE| awk 'NF>0{print}'| (while read LINE
do
set -A MANUAL $LINE
echo "Changing the inheritance attribute on class ${MANUAL[1]}..."
OLDINH=`lsclass -f ${MANUAL[1]} | grep inheritance | awk '{ print
$3 }' | sed "s/"//g"`
[ ! "$OLDINH" ] && OLDINH="no"
$ECHO chclass -a inheritance=${MANUAL[2]} ${MANUAL[1]}
echo "Refreshing WLM..."
wlmcntrl -u
echo "Manually assigning the processes to class ${MANUAL[1]}..."
echo "Getting PIDS' list for instance ${MANUAL[0]}..."
n=0
for p in $(getpids ${MANUAL[0]})
do
wlmassign -S ${MANUAL[1]} $p
n=$(expr $n + 1)
done
echo "Assigning $n processes to class ${MANUAL[1]}..."
echo "Resetting old inheritance value on class ${MANUAL[1]}..."
chclass -a inheritance="$OLDINH" ${MANUAL[1]}
echo "Refreshing WLM..."
wlmcntrl -u
done
)
#######################
##logger WLM updated
exit 0](https://image.slidesharecdn.com/aixworkloadmanager-130326041847-phpapp02/85/Aix-workload-manager-4-320.jpg)















































