Anomaly detection and root cause analysis in distributed application transactions
- 1. Anomaly Detection and Root Cause Analysis in Distributed Application Transactions Yuchen Zhao @
- 2. Software is Eating the World
- 5. it°Øs critical to make sure the software is running properly
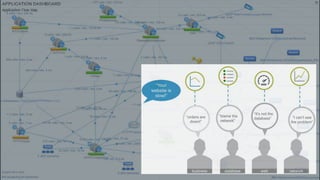
- 7. Monitoring shouldn°Øt be very hard°≠ right?
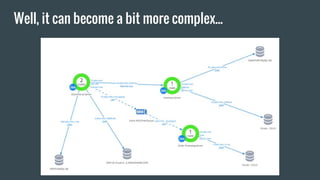
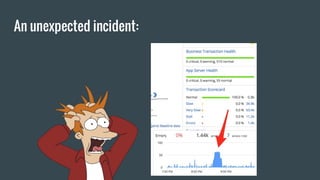
- 8. Well, it can become a bit more complex...
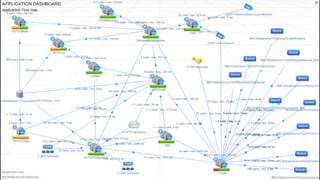
- 12. Keep applications running is hard.
- 14. Challenge 1: Enterprise applications are complex
- 15. Challenge 2: Data is heterogeneous. Its volume is massive and growing
- 16. Challenge 3: Too many signals. Finding anomalies & root causes are non-trival.
- 17. Our solution: Relevant Fields Machine Learning + Engineering
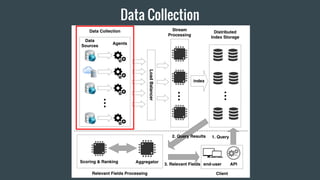
- 18. Q1: How to get & organize data?
- 19. Collect data in the form of Business Transactions
- 21. Q2: Can you give a real use case?
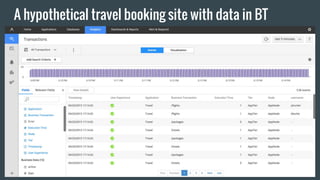
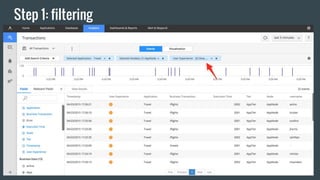
- 22. A hypothetical travel booking site with data in BT
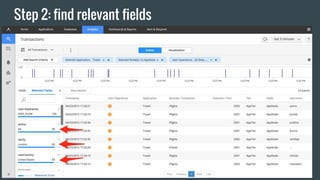
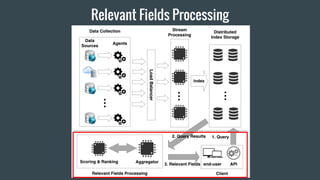
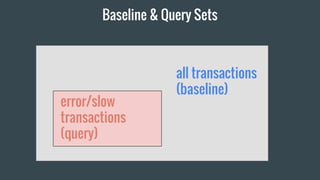
- 26. Step 2: find relevant fields
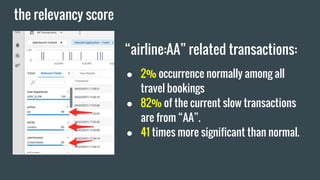
- 27. the relevancy score °∞airline:AA°± related transactions: °Ò 2% occurrence normally among all travel bookings °Ò 82% of the current slow transactions are from °∞AA°±. °Ò 41 times more significant than normal.
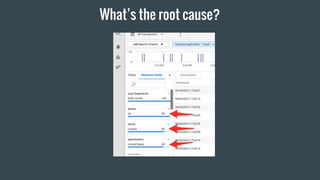
- 28. What°Øs the root cause?
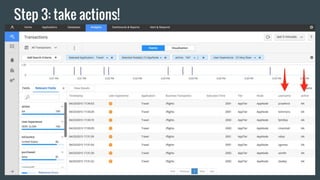
- 29. Step 3: take actions!
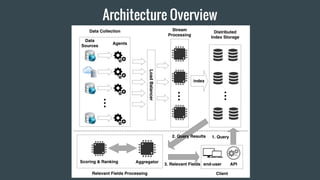
- 30. Q3: What°Øs the design of the system?
- 32. Data Collection
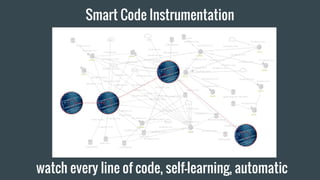
- 33. Smart Code Instrumentation watch every line of code, self-learning, automatic
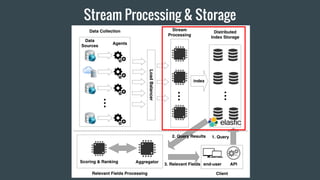
- 34. Stream Processing & Storage
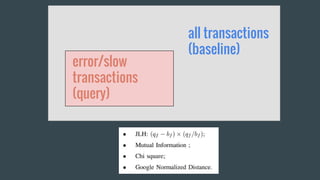
- 37. Q4: How to score the field?
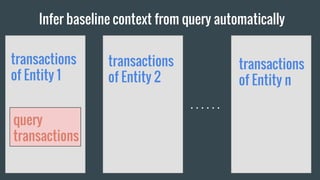
- 40. Infer baseline context from query automatically query transactions transactions of Entity 1 query transactions transactions of Entity 2 transactions of Entity n
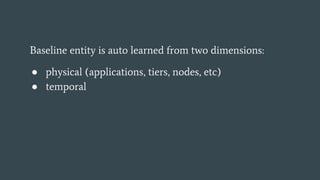
- 41. Baseline entity is auto learned from two dimensions: °Ò physical (applications, tiers, nodes, etc) °Ò temporal
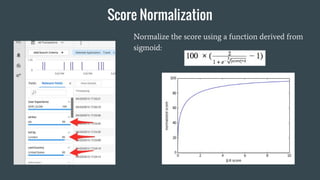
- 42. Score Normalization Normalize the score using a function derived from sigmoid:
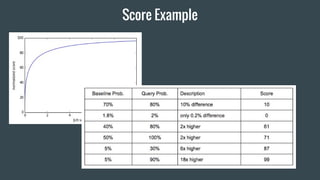
- 43. Score Example
- 44. Fore more details, please check out our demo paper in ICDM 2015: Discovering Anomalies and Root Causes in Applications via Relevant Fields Analysis, in Proceedings of the 15th IEEE International Conference on Data Mining
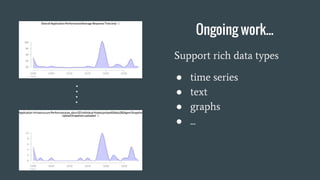
- 45. Ongoing work... Support rich data types °Ò time series °Ò text °Ò graphs °Ò ...
- 46. We°Øre selling!
- 47. We°Øre hiring too! Contact Mara or me yuchen.zhao@appdynamics.com
- 48. Thank you!