Asynchronous programming FTW!
- 1. ASYNCHRONOUS PROGRAMMING FTW! (SAWYER X)
- 2. DOES THIS SOUND FAMILIAR? "Hi" "Hi, dad" "Got a minute?" "Yes" "I'm looking for a movie Where do I start?" "Go to the cinema website" "What's the address?" "www.whatchamacallit.whatever" "Just a sec..."
- 4. "Well?" "Ah! It loaded! What now?" "Click on new movies" "OK..." ........ "Well?" "Loading" *sounds of clicks*
- 5. "OK, now what?" "Find a movie you want" "Then what?" "Click on it, you'll have instructions" * eternity passes by * "WELL?!?" "Just a sec... it's loading..." /me shoots myself
- 6. ILLUSTRATED (USING WWW::MECHANIZE) $eh>e(cnm_r) mc┬Łgt$ieaul═Š i╠²╠²mc┬Łsces){ f($eh>ucs╠²╠² ╠²╠²$eh>lc(NwMve'═Š ╠²╠²mc┬Łcik'e╠²ois) ╠²╠²i╠²╠²mc┬Łsces){ ╠²╠²f($eh>ucs╠²╠² ╠²╠²╠²╠²m╠²mve╠²╠²mc┬Łfn_nus.. ╠²╠²╠²╠²y@ois=$eh>idipt(.) ╠²╠²} ╠²╠² }
- 7. LET'S TRY THIS AGAIN... "Hi" "Hi, dad" "Got a minute?" "Yes" "I'm looking for a movie What should I do?" "Go to this website, click on new movies Then pick a movie, and click on it" "Thank you" "You're welcome"
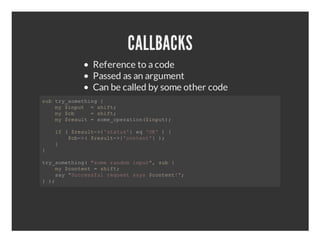
- 9. CALLBACKS Reference to a code Passed as an argument Can be called by some other code sbtysmtig{ u╠²r_oehn╠² ╠²╠²m╠²ipt╠²╠²hf═Š ╠²╠²y$nu╠²=sit ╠²╠²m╠²c╠²╠²╠²╠²hf═Š ╠²╠²y$b╠²╠²=sit ╠²╠²m╠²rsl╠²╠²oeoeain$nu) ╠²╠²y$eut=sm_prto(ipt═Š ╠²╠²i╠²╠²rsl┬Ł{sau'╠²q'K╠²╠² ╠²╠²f($eut>'tts}e╠²O'){ ╠²╠²╠²╠²$b>╠²rsl┬Ł{cnet}) ╠²╠²╠²╠²c┬Ł($eut>'otn'╠²═Š ╠²╠²} ╠²╠² } tysmtig╠²sm╠²admipt,sb{ r_oehn("oerno╠²nu"╠²u╠² ╠²╠²m╠²cnet=sit ╠²╠²y$otn╠²╠²hf═Š ╠²╠²sy"ucsflrqetsy╠²cnet" ╠²╠²a╠²Scesu╠²eus╠²as$otn!═Š }) ╠²═Š
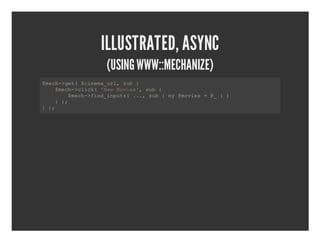
- 10. ILLUSTRATED, ASYNC (USING WWW::MECHANIZE) $eh>e($ieaul╠²u╠² mc┬Łgt╠²cnm_r,sb{ ╠²╠²$eh>lc('e╠²ois,sb{ ╠²╠²mc┬Łcik╠²NwMve'╠²u╠² ╠²╠²╠²╠²$eh>idipt(..╠²u╠²╠²y@ois=@╠²╠² ╠²╠²╠²╠²mc┬Łfn_nus╠².,sb{m╠²mve╠²╠²_}) ╠²╠²}) ╠²╠²╠²═Š }) ╠²═Š
- 11. WHY IS THIS USEFUL? Allow others to decide if something is good or not
- 12. m╠²jn╠²╠²uo>e( y$uo=Jn┬Łnw ╠²╠²hss╠²>[w11112222] ╠²╠²ot╠²=╠²q<...╠²...>, ╠²╠²cek╠²>{ ╠²╠²hcs=╠² ╠²╠²╠²╠²Fig=╠² ╠²╠²╠²╠²Pn╠²>{ ╠²╠²╠²╠²╠²╠²o_ucs╠²>sb{ ╠²╠²╠²╠²╠²╠²nsces=╠²u╠² ╠²╠²╠²╠²╠²╠²╠²╠²m╠²╠²jn,$ot╠²dt╠²╠²╠²_ ╠²╠²╠²╠²╠²╠²╠²╠²y($uo╠²hs,$aa)=@═Š ╠²╠²╠²╠²╠²╠²╠²╠²m╠²╠²i,$os╠²ag)=$uo>nlz_igrsl( ╠²╠²╠²╠²╠²╠²╠²╠²y($p╠²ls,$v╠²╠²╠²jn┬Łaayepn_eut ╠²╠²╠²╠²╠²╠²╠²╠²╠²╠²$aa>'ter} ╠²╠²╠²╠²╠²╠²╠²╠²╠²╠²dt┬Ł{sdr', ╠²╠²╠²╠²╠²╠²╠²╠²) ╠²╠²╠²╠²╠²╠²╠²╠²═Š ╠²╠²╠²╠²╠²╠²╠²╠²$ef>e_ot╠²hs,$v╠²═Š ╠²╠²╠²╠²╠²╠²╠²╠²sl┬Łsths($ot╠²ag) ╠²╠²╠²╠²╠²╠²} ╠²╠²╠²╠²╠²╠², ╠²╠²╠²╠²╠²╠²o_al=╠²u╠² ╠²╠²╠²╠²╠²╠²nfi╠²>sb{ ╠²╠²╠²╠²╠²╠²╠²╠²m╠²╠²jn,$ot)=@═Š ╠²╠²╠²╠²╠²╠²╠²╠²y($uo╠²hs╠²╠²╠²_ ╠²╠²╠²╠²╠²╠²╠²╠²$ef>eeehs(hs) ╠²╠²╠²╠²╠²╠²╠²╠²sl┬Łdlt_ot$ot═Š ╠²╠²╠²╠²╠²╠²} ╠²╠²╠²╠²╠²╠², ╠²╠²╠²╠²} ╠²╠²╠²╠² ╠²╠²} ╠²╠² )═Š
- 13. WHY IS THIS USEFUL? Allow others to decide if something is good or not Allow easy stepping
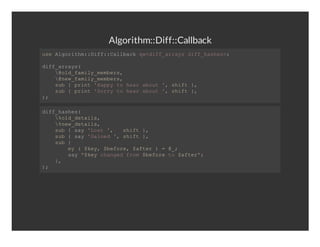
- 14. Algorithm::Diff::Callback ueAgrtm:if:alakq<ifary╠²ifhse> s╠²loih:Df:Clbc╠²wdf_rasdf_ahs═Š df_ras ifary( ╠²╠²odfml_ebr, ╠²╠²@l_aiymmes ╠²╠²nwfml_ebr, ╠²╠²@e_aiymmes ╠²╠²sb{pit'ap╠²oha╠²bu╠²,sit} ╠²╠²u╠²╠²rn╠²Hpyt╠²eraot'╠²hf╠², ╠²╠²sb{pit'or╠²oha╠²bu╠²,sit} ╠²╠²u╠²╠²rn╠²Sryt╠²eraot'╠²hf╠², )═Š df_ahs ifhse( ╠²╠²oddtis ╠²╠²%l_eal, ╠²╠²nwdtis ╠²╠²%e_eal, ╠²╠²sb{sy'ot'╠²╠²hf╠², ╠²╠²u╠²╠²a╠²Ls╠²,╠²sit} ╠²╠²sb{sy'and'╠²hf╠², ╠²╠²u╠²╠²a╠²Gie╠²,sit} ╠²╠²sb{ ╠²╠²u╠² ╠²╠²╠²╠²m╠²╠²ky╠²bfr,$fe╠²╠²╠²_ ╠²╠²╠²╠²y($e,$eoe╠²atr)=@═Š ╠²╠²╠²╠²sy"kycagdfo╠²bfr╠²o$fe" ╠²╠²╠²╠²a╠²$e╠²hne╠²rm$eoet╠²atr═Š ╠²╠²} ╠²╠², )═Š
- 15. WHY IS THIS USEFUL? Allow others to decide if something is good or not Allow easy stepping Allow control by other process (a type of IOC) Allow asynchronous code
- 16. THE EVENT LOOP Create loop Register events Run them Let the user keep registering new events
- 17. m╠²eet╠²╠²..═Š y%vns=(.) wie(){ hl╠²1╠² ╠²╠²frahm╠²eet(ky╠²eet╠²╠² ╠²╠²oec╠²y$vn╠²╠²es%vns){ ╠²╠²╠²╠²$vn┬Ł(═Š ╠²╠²╠²╠²eet>) ╠²╠²} ╠²╠² }
- 18. m╠²eet═Š%vns=(.) y%vns╠²eet╠²╠²..═Š wie(){ hl╠²1╠² ╠²╠²frahm╠²eet(ky╠²eet╠²╠² ╠²╠²oec╠²y$vn╠²╠²es%vns){ ╠²╠²╠²╠²$vn┬Ł(═Š ╠²╠²╠²╠²eet>) ╠²╠²} ╠²╠² } wie(){ hl╠²1╠² ╠²╠²frahm╠²eet(ky╠²eet╠²╠² ╠²╠²oec╠²y$vn╠²╠²es%vns){ ╠²╠²╠²╠²i╠²╠²eet{eet{tm'╠²=tm╠²╠² ╠²╠²╠²╠²f($vns$vn}'ie}<╠²ie){ ╠²╠²╠²╠²╠²╠²$vns$vn}'oe}>) ╠²╠²╠²╠²╠²╠²eet{eet{cd'┬Ł(═Š ╠²╠²╠²╠²} ╠²╠²╠²╠² ╠²╠²} ╠²╠² } sbadeet{ u╠²d_vn╠² ╠²╠²m╠²╠²tm,$oe)=@═Š ╠²╠²y($ie╠²cd╠²╠²╠²_ ╠²╠²$vns$d{tm'╠²╠²tm═Š ╠²╠²eet{i}'ie}=$ie ╠²╠²$vns$d{cd'╠²╠²cd═Š ╠²╠²eet{i}'oe}=$oe ╠²╠²$d+ ╠²╠²i+═Š }
- 19. EVENT TYPES Timers (one-time, recurring, sleep replacement) I/O (input output, including networking)
- 20. FUCK TALK LET'S GO PROGRAMMING
- 21. IO::ASYNC Loop interface: IO::Async::Loop You can connect to hosts using it You can add listeners to it (handles, sockets, etc.) Explicitly call "run" when ready
- 22. ueI:Ayc:tem s╠²O:sn:Sra═Š ueI:Ayc:op s╠²O:sn:Lo═Š ╠² m╠²lo╠²╠²O:sn:Lo┬Łnw y$op=I:Ayc:op>e═Š $op>onc( lo┬Łcnet ╠²╠²hs╠²╠²╠²=╠²sm.te.ot, ╠²╠²ot╠²╠²╠²>"oeohrhs" ╠²╠²srie╠²=╠²24, ╠²╠²evc╠²╠²>135 ╠²╠²sctp╠²=╠²sra' ╠²╠²okye╠²>'tem, ╠²╠² ╠²╠²o_tem=╠²u╠²╠².╠², ╠²╠²nsra╠²>sb{..} ╠²╠² ╠²╠²o_eov_ro╠²>sb{ ╠²╠²nrsleerr=╠²u╠² ╠²╠²╠²╠²de"antrsle┬Ł$[1" ╠²╠²╠²╠²i╠²Cno╠²eov╠²╠²_┬Ł] ╠²╠²} ╠²╠², ╠²╠²o_onc_ro╠²>sb{ ╠²╠²ncneterr=╠²u╠² ╠²╠²╠²╠²de"antcnet┬Ł$[]fie╠²_┬Ł] ╠²╠²╠²╠²i╠²Cno╠²onc╠²╠²_0╠²ald$[1" ╠²╠²} ╠²╠², )═Š $op>u═Š lo┬Łrn
- 23. o_tem=╠²u╠² nsra╠²>sb{ ╠²╠²m╠²╠²sra╠²╠²╠²_ ╠²╠²y($tem)=@═Š ╠²╠²$tem>ofgr( ╠²╠²sra┬Łcniue ╠²╠²╠²╠²o_ed=╠²u╠² ╠²╠²╠²╠²nra╠²>sb{ ╠²╠²╠²╠²╠²╠²m╠²╠²sl,$ufe,$o╠²╠²╠²_ ╠²╠²╠²╠²╠²╠²y($ef╠²bfrf╠²ef)=@═Š ╠²╠²╠²╠²╠²╠²wie╠²{bfrf╠²~s^.)/){ ╠²╠²╠²╠²╠²╠²hl($$ufe}=╠²/(*n/╠²╠² ╠²╠²╠²╠²╠²╠²╠²╠²sy"eevdaln╠²1═Š ╠²╠²╠²╠²╠²╠²╠²╠²a╠²Rcie╠²╠²ie$" ╠²╠²╠²╠²╠²╠²} ╠²╠²╠²╠²╠²╠² ╠²╠²╠²╠²╠²╠²rtr╠²═Š ╠²╠²╠²╠²╠²╠²eun0 ╠²╠²╠²╠²} ╠²╠²╠²╠² ╠²╠²) ╠²╠²═Š ╠²╠²$tem>rt(A╠²nta╠²iehr'═Š ╠²╠²sra┬Łwie'niiilln╠²ee) ╠²╠²$op>d(sra) ╠²╠²lo┬Ład$tem═Š }
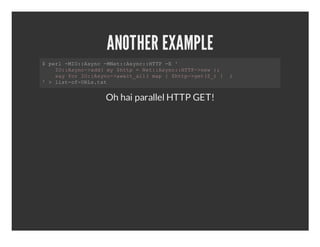
- 24. ANOTHER EXAMPLE $pr╠²MO:sn╠²Me:Ayc:TP┬Ł╠² ╠²el┬ŁI:Ayc┬ŁNt:sn:HT╠²E' ╠²╠²I:Ayc>d(m╠²ht╠²╠²e:Ayc:TP>e╠²═Š ╠²╠²O:sn┬Ład╠²y$tp=Nt:sn:HT┬Łnw) ╠²╠²syfrI:Ayc>wi_l(mp{$tp>e(_╠²╠²) ╠²╠²a╠²o╠²O:sn┬Łaatal╠²a╠²╠²ht┬Łgt$)}╠² '>ls┬ŁfUL.x ╠²╠²ito┬ŁRstt Oh hai parallel HTTP GET!
- 25. POE Loop interface: POE::Kernel Runs "sessions" (POE::Session) Each session is a context of events Each session has an ID and heap Call events in a current or different session Explicitly call POE::Kernel->run when ready
- 26. POE uePE╠²#At┬ŁnldsPE:enladPE:eso. s╠²O═Š╠²╠²uoicue╠²O:Kre╠²n╠²O:Ssin #..dfn╠²alak╠²us(etsie╠². ╠².╠²eieclbcssb╠²nx╠²ld).. fr(.1){ o╠²1.0╠² ╠²╠²PE:eso┬Łcet( ╠²╠²O:Ssin>rae ╠²╠²╠²╠²iln_tts=╠² ╠²╠²╠²╠²niesae╠²>{ ╠²╠²╠²╠²╠²╠²_tr╠²╠²=╠²&ade_tr, ╠²╠²╠²╠²╠²╠²sat╠²╠²>hnlrsat ╠²╠²╠²╠²╠²╠²iceet=╠²&ade_nrmn, ╠²╠²╠²╠²╠²╠²nrmn╠²>hnlriceet ╠²╠²╠²╠²╠²╠²_tp╠²╠²=╠²&ade_tp ╠²╠²╠²╠²╠²╠²so╠²╠²╠²>hnlrso, ╠²╠²╠²╠²} ╠²╠²╠²╠² ╠²╠²) ╠²╠²═Š } PE:enl>u(═Š O:Kre┬Łrn)
- 27. sbhnlrsat{ u╠²ade_tr╠² ╠²m╠²╠²kre,$ep╠²ssin)=@[KRE,HA,SSIN] ╠²y($enl╠²ha,$eso╠²╠²╠²_╠²ENL╠²EP╠²ESO╠²═Š ╠²sy"eso╠²,$eso┬ŁI,"hssatd═Š ╠²a╠²Ssin"╠²ssin>D╠²╠²a╠²tre" ╠²$ep>'on'╠²╠²═Š ╠²ha┬Ł{cut}=0 ╠²$enl>il(iceet) ╠²kre┬Łyed'nrmn'═Š } sbhnlriceet{ u╠²ade_nrmn╠² ╠²m╠²╠²kre,$ep╠²ssin)=@[KRE,HA,SSIN] ╠²y($enl╠²ha,$eso╠²╠²╠²_╠²ENL╠²EP╠²ESO╠²═Š ╠²sy"eso╠²,$eso┬ŁI,"cutdt╠²,+$ep>'on'═Š ╠²a╠²Ssin"╠²ssin>D╠²╠²one╠²o"╠²+ha┬Ł{cut} ╠²$enl>il(iceet)i╠²ha┬Ł{cut}<1═Š ╠²kre┬Łyed'nrmn'╠²f$ep>'on'╠²╠²0 } sbhnlrso╠² u╠²ade_tp{ ╠²sy"eso╠²,$[ESO]>D╠²╠²a╠²tpe" ╠²a╠²Ssin"╠²_SSIN┬ŁI,"hssopd═Š }
- 28. sbhnlrsat{ u╠²ade_tr╠² ╠²m╠²╠²kre,$ep╠²ssin)=@[KRE,HA,SSIN] ╠²y($enl╠²ha,$eso╠²╠²╠²_╠²ENL╠²EP╠²ESO╠²═Š ╠²sy"eso╠²,$eso┬ŁI,"hssatd═Š ╠²a╠²Ssin"╠²ssin>D╠²╠²a╠²tre" ╠²$ep>'on'╠²╠²═Š ╠²ha┬Ł{cut}=0 ╠²$enl>il(iceet) ╠²kre┬Łyed'nrmn'═Š } sbhnlriceet{ u╠²ade_nrmn╠² ╠²m╠²╠²kre,$ep╠²ssin)=@[KRE,HA,SSIN] ╠²y($enl╠²ha,$eso╠²╠²╠²_╠²ENL╠²EP╠²ESO╠²═Š ╠²sy"eso╠²,$eso┬ŁI,"cutdt╠²,+$ep>'on'═Š ╠²a╠²Ssin"╠²ssin>D╠²╠²one╠²o"╠²+ha┬Ł{cut} ╠²$enl>il(iceet)i╠²ha┬Ł{cut}<1═Š ╠²kre┬Łyed'nrmn'╠²f$ep>'on'╠²╠²0 } sbhnlrso╠² u╠²ade_tp{ ╠²sy"eso╠²,$[ESO]>D╠²╠²a╠²tpe.n═Š ╠²a╠²Ssin"╠²_SSIN┬ŁI,"hssopd" } fr(.1){ o╠²1.0╠² ╠²╠²PE:eso┬Łcet( ╠²╠²O:Ssin>rae ╠²╠²╠²╠²iln_tts=╠² ╠²╠²╠²╠²niesae╠²>{ ╠²╠²╠²╠²╠²╠²_tr╠²╠²=╠²&ade_tr, ╠²╠²╠²╠²╠²╠²sat╠²╠²>hnlrsat ╠²╠²╠²╠²╠²╠²iceet=╠²&ade_nrmn, ╠²╠²╠²╠²╠²╠²nrmn╠²>hnlriceet ╠²╠²╠²╠²╠²╠²_tp╠²╠²=╠²&ade_tp ╠²╠²╠²╠²╠²╠²so╠²╠²╠²>hnlrso, ╠²╠²╠²╠²} ╠²╠²╠²╠² ╠²╠²) ╠²╠²═Š } PE:enl>u(═Š O:Kre┬Łrn)
- 29. MORE CONDENSED uePE s╠²O═Š fr(.1){ o╠²1.0╠² ╠²╠²m╠²cut=0 ╠²╠²y$on╠²╠²═Š ╠²╠²PE:eso┬Łcet( ╠²╠²O:Ssin>rae ╠²╠²╠²╠²iln_tts=╠² ╠²╠²╠²╠²niesae╠²>{ ╠²╠²╠²╠²╠²╠²_tr╠²╠²=╠²u╠² ╠²╠²╠²╠²╠²╠²sat╠²╠²>sb{ ╠²╠²╠²╠²╠²╠²╠²╠²sy"eso╠²,$[ESO]>D╠²╠²a╠²tre" ╠²╠²╠²╠²╠²╠²╠²╠²a╠²Ssin"╠²_SSIN┬ŁI,"hssatd═Š ╠²╠²╠²╠²╠²╠²╠²╠²PE:enl>il(iceet) ╠²╠²╠²╠²╠²╠²╠²╠²O:Kre┬Łyed'nrmn'═Š ╠²╠²╠²╠²╠²╠²} ╠²╠²╠²╠²╠²╠², ╠²╠²╠²╠²╠²╠²iceet=╠²u╠² ╠²╠²╠²╠²╠²╠²nrmn╠²>sb{ ╠²╠²╠²╠²╠²╠²╠²╠²PE:enl>il(iceet)i╠²+cut<1═Š ╠²╠²╠²╠²╠²╠²╠²╠²O:Kre┬Łyed'nrmn'╠²f+$on╠²╠²0 ╠²╠²╠²╠²╠²╠²╠²╠²sy"eso╠²,$[ESO]>D╠²╠²one╠²o$on" ╠²╠²╠²╠²╠²╠²╠²╠²a╠²Ssin"╠²_SSIN┬ŁI,"cutdt╠²cut═Š ╠²╠²╠²╠²╠²╠²} ╠²╠²╠²╠²╠²╠², ╠²╠²╠²╠²╠²╠²_tp╠²╠²=╠²u╠² ╠²╠²╠²╠²╠²╠²so╠²╠²╠²>sb{ ╠²╠²╠²╠²╠²╠²╠²╠²sy"eso╠²,$[ESO]>D╠²╠²a╠²tpe" ╠²╠²╠²╠²╠²╠²╠²╠²a╠²Ssin"╠²_SSIN┬ŁI,"hssopd═Š ╠²╠²╠²╠²╠²╠²} ╠²╠²╠²╠²╠²╠², ╠²╠²╠²╠²} ╠²╠²╠²╠² ╠²╠²) ╠²╠²═Š } PE:enl>u(═Š O:Kre┬Łrn)
- 30. REFLEX Written by author of POE "How POE would be written if I had Moose back then" Stresses composability, reusability Includes plenty of additional roles
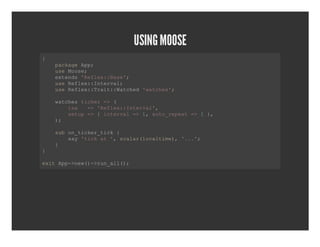
- 31. USING MOOSE { ╠²╠²pcaeAp ╠²╠²akg╠²p═Š ╠²╠²ueMoe ╠²╠²s╠²os═Š ╠²╠²etns'elx:ae═Š ╠²╠²xed╠²Rfe:Bs' ╠²╠²ueRfe:Itra═Š ╠²╠²s╠²elx:nevl ╠²╠²ueRfe:Tat:ace╠²wths═Š ╠²╠²s╠²elx:ri:Wthd'ace' ╠² ╠²╠²wthstce╠²>( ╠²╠²ace╠²ikr=╠² ╠²╠²╠²╠²ia╠²=╠²Rfe:Itra' ╠²╠²╠²╠²s╠²╠²>'elx:nevl, ╠²╠²╠²╠²stp=╠²╠²nevl=╠²,at_eet=╠²╠², ╠²╠²╠²╠²eu╠²>{itra╠²>1╠²uorpa╠²>1} ╠²╠²) ╠²╠²═Š ╠² ╠²╠²sbo_ikrtc╠² ╠²╠²u╠²ntce_ik{ ╠²╠²╠²╠²sy'ika╠²,saa(oatm)╠²..═Š ╠²╠²╠²╠²a╠²tc╠²t'╠²clrlclie,'.' ╠²╠²} ╠²╠² } ╠² ei╠²p┬Łnw)>u_l(═Š xtAp>e(┬Łrnal)
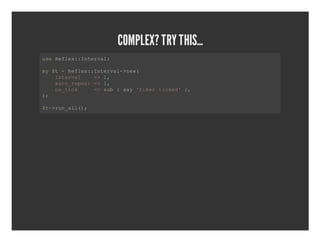
- 32. COMPLEX? TRY THIS... ueRfe:Itra═Š s╠²elx:nevl ╠² m╠²t=Rfe:Itra┬Łnw y$╠²╠²elx:nevl>e( ╠²╠²itra╠²╠²=╠², ╠²╠²nevl╠²╠²>1 ╠²╠²at_eet=╠², ╠²╠²uorpa╠²>1 ╠²╠²o_ik╠²╠²=╠²u╠²╠²a╠²tmrtce'} ╠²╠²ntc╠²╠²╠²>sb{sy'ie╠²ikd╠², )═Š ╠² $┬Łrnal) t>u_l(═Š
- 33. ANYEVENT AnyEvent is very thin and very fast Was written to support as many loops as possible ... that conform to the author's rules of compatibility Does not use a loop handler, simply runs Does use conditional variables Has AE for faster performance
- 34. ueAyvn═Š s╠²nEet m╠²cut=0 y$on╠²╠²═Š m╠²c╠²╠²=Ayvn┬Łcnvr y$v╠²╠²╠²nEet>oda═Š m╠²t╠²╠²=Ayvn┬Łtmr y$╠²╠²╠²╠²nEet>ie( ╠²╠²atr╠²╠²>2 ╠²╠²fe╠²╠²=╠², ╠²╠²itra╠²>06 ╠²╠²nevl=╠²., ╠²╠²c╠²╠²╠²╠²>sb{ ╠²╠²b╠²╠²╠²=╠²u╠² ╠²╠²╠²╠²sy'h╠²iei╠²o:'╠²nEet>o═Š ╠²╠²╠²╠²a╠²Tetm╠²snw╠²,Ayvn┬Łnw ╠²╠²╠²╠²+$on╠²=1╠²n╠²c┬Łsn═Š ╠²╠²╠²╠²+cut=╠²0ad$v>ed ╠²╠²} ╠²╠², )═Š $v>ev c┬Łrc═Š
- 35. m╠²w╠²w=Ayvn┬Łi( y$═Š$╠²╠²nEet>o ╠²╠²f╠²╠²>SDN ╠²╠²h╠²=╠²*TI, ╠²╠²pl╠²>'' ╠²╠²ol=╠²r, ╠²╠²c╠²╠²>sb{ ╠²╠²b╠²=╠²u╠² ╠²╠²╠²╠²cop(m╠²ipt=╠²═Š ╠²╠²╠²╠²hm╠²╠²y$nu╠²╠²) ╠²╠²╠²╠²sy"ed╠²ipt═Š ╠²╠²╠²╠²a╠²ra:$nu" ╠²╠²╠²╠²udf$═Š ╠²╠²╠²╠²ne╠²w ╠²╠²} ╠²╠², )═Š
- 36. USAGES OF ASYNCHRONOUS CODE GUI Services (HTTP/SMTP/etc.) Performance Off-loading tasks
- 37. THANK YOU








![m╠²jn╠²╠²uo>e(
y$uo=Jn┬Łnw
╠²╠²hss╠²>[w11112222]
╠²╠²ot╠²=╠²q<...╠²...>,
╠²╠²cek╠²>{
╠²╠²hcs=╠²
╠²╠²╠²╠²Fig=╠²
╠²╠²╠²╠²Pn╠²>{
╠²╠²╠²╠²╠²╠²o_ucs╠²>sb{
╠²╠²╠²╠²╠²╠²nsces=╠²u╠²
╠²╠²╠²╠²╠²╠²╠²╠²m╠²╠²jn,$ot╠²dt╠²╠²╠²_
╠²╠²╠²╠²╠²╠²╠²╠²y($uo╠²hs,$aa)=@═Š
╠²╠²╠²╠²╠²╠²╠²╠²m╠²╠²i,$os╠²ag)=$uo>nlz_igrsl(
╠²╠²╠²╠²╠²╠²╠²╠²y($p╠²ls,$v╠²╠²╠²jn┬Łaayepn_eut
╠²╠²╠²╠²╠²╠²╠²╠²╠²╠²$aa>'ter}
╠²╠²╠²╠²╠²╠²╠²╠²╠²╠²dt┬Ł{sdr',
╠²╠²╠²╠²╠²╠²╠²╠²)
╠²╠²╠²╠²╠²╠²╠²╠²═Š
╠²╠²╠²╠²╠²╠²╠²╠²$ef>e_ot╠²hs,$v╠²═Š
╠²╠²╠²╠²╠²╠²╠²╠²sl┬Łsths($ot╠²ag)
╠²╠²╠²╠²╠²╠²}
╠²╠²╠²╠²╠²╠²,
╠²╠²╠²╠²╠²╠²o_al=╠²u╠²
╠²╠²╠²╠²╠²╠²nfi╠²>sb{
╠²╠²╠²╠²╠²╠²╠²╠²m╠²╠²jn,$ot)=@═Š
╠²╠²╠²╠²╠²╠²╠²╠²y($uo╠²hs╠²╠²╠²_
╠²╠²╠²╠²╠²╠²╠²╠²$ef>eeehs(hs)
╠²╠²╠²╠²╠²╠²╠²╠²sl┬Łdlt_ot$ot═Š
╠²╠²╠²╠²╠²╠²}
╠²╠²╠²╠²╠²╠²,
╠²╠²╠²╠²}
╠²╠²╠²╠²
╠²╠²}
╠²╠²
)═Š](https://image.slidesharecdn.com/async-ftw-121006073203-phpapp01/85/Asynchronous-programming-FTW-12-320.jpg)




![ueI:Ayc:tem
s╠²O:sn:Sra═Š
ueI:Ayc:op
s╠²O:sn:Lo═Š
╠²
m╠²lo╠²╠²O:sn:Lo┬Łnw
y$op=I:Ayc:op>e═Š
$op>onc(
lo┬Łcnet
╠²╠²hs╠²╠²╠²=╠²sm.te.ot,
╠²╠²ot╠²╠²╠²>"oeohrhs"
╠²╠²srie╠²=╠²24,
╠²╠²evc╠²╠²>135
╠²╠²sctp╠²=╠²sra'
╠²╠²okye╠²>'tem,
╠²╠²
╠²╠²o_tem=╠²u╠²╠².╠²,
╠²╠²nsra╠²>sb{..}
╠²╠²
╠²╠²o_eov_ro╠²>sb{
╠²╠²nrsleerr=╠²u╠²
╠²╠²╠²╠²de"antrsle┬Ł$[1"
╠²╠²╠²╠²i╠²Cno╠²eov╠²╠²_┬Ł]
╠²╠²}
╠²╠²,
╠²╠²o_onc_ro╠²>sb{
╠²╠²ncneterr=╠²u╠²
╠²╠²╠²╠²de"antcnet┬Ł$[]fie╠²_┬Ł]
╠²╠²╠²╠²i╠²Cno╠²onc╠²╠²_0╠²ald$[1"
╠²╠²}
╠²╠²,
)═Š
$op>u═Š
lo┬Łrn](https://image.slidesharecdn.com/async-ftw-121006073203-phpapp01/85/Asynchronous-programming-FTW-22-320.jpg)



![sbhnlrsat{
u╠²ade_tr╠²
╠²m╠²╠²kre,$ep╠²ssin)=@[KRE,HA,SSIN]
╠²y($enl╠²ha,$eso╠²╠²╠²_╠²ENL╠²EP╠²ESO╠²═Š
╠²sy"eso╠²,$eso┬ŁI,"hssatd═Š
╠²a╠²Ssin"╠²ssin>D╠²╠²a╠²tre"
╠²$ep>'on'╠²╠²═Š
╠²ha┬Ł{cut}=0
╠²$enl>il(iceet)
╠²kre┬Łyed'nrmn'═Š
}
sbhnlriceet{
u╠²ade_nrmn╠²
╠²m╠²╠²kre,$ep╠²ssin)=@[KRE,HA,SSIN]
╠²y($enl╠²ha,$eso╠²╠²╠²_╠²ENL╠²EP╠²ESO╠²═Š
╠²sy"eso╠²,$eso┬ŁI,"cutdt╠²,+$ep>'on'═Š
╠²a╠²Ssin"╠²ssin>D╠²╠²one╠²o"╠²+ha┬Ł{cut}
╠²$enl>il(iceet)i╠²ha┬Ł{cut}<1═Š
╠²kre┬Łyed'nrmn'╠²f$ep>'on'╠²╠²0
}
sbhnlrso╠²
u╠²ade_tp{
╠²sy"eso╠²,$[ESO]>D╠²╠²a╠²tpe"
╠²a╠²Ssin"╠²_SSIN┬ŁI,"hssopd═Š
}](https://image.slidesharecdn.com/async-ftw-121006073203-phpapp01/85/Asynchronous-programming-FTW-27-320.jpg)
![sbhnlrsat{
u╠²ade_tr╠²
╠²m╠²╠²kre,$ep╠²ssin)=@[KRE,HA,SSIN]
╠²y($enl╠²ha,$eso╠²╠²╠²_╠²ENL╠²EP╠²ESO╠²═Š
╠²sy"eso╠²,$eso┬ŁI,"hssatd═Š
╠²a╠²Ssin"╠²ssin>D╠²╠²a╠²tre"
╠²$ep>'on'╠²╠²═Š
╠²ha┬Ł{cut}=0
╠²$enl>il(iceet)
╠²kre┬Łyed'nrmn'═Š
}
sbhnlriceet{
u╠²ade_nrmn╠²
╠²m╠²╠²kre,$ep╠²ssin)=@[KRE,HA,SSIN]
╠²y($enl╠²ha,$eso╠²╠²╠²_╠²ENL╠²EP╠²ESO╠²═Š
╠²sy"eso╠²,$eso┬ŁI,"cutdt╠²,+$ep>'on'═Š
╠²a╠²Ssin"╠²ssin>D╠²╠²one╠²o"╠²+ha┬Ł{cut}
╠²$enl>il(iceet)i╠²ha┬Ł{cut}<1═Š
╠²kre┬Łyed'nrmn'╠²f$ep>'on'╠²╠²0
}
sbhnlrso╠²
u╠²ade_tp{
╠²sy"eso╠²,$[ESO]>D╠²╠²a╠²tpe.n═Š
╠²a╠²Ssin"╠²_SSIN┬ŁI,"hssopd"
}
fr(.1){
o╠²1.0╠²
╠²╠²PE:eso┬Łcet(
╠²╠²O:Ssin>rae
╠²╠²╠²╠²iln_tts=╠²
╠²╠²╠²╠²niesae╠²>{
╠²╠²╠²╠²╠²╠²_tr╠²╠²=╠²&ade_tr,
╠²╠²╠²╠²╠²╠²sat╠²╠²>hnlrsat
╠²╠²╠²╠²╠²╠²iceet=╠²&ade_nrmn,
╠²╠²╠²╠²╠²╠²nrmn╠²>hnlriceet
╠²╠²╠²╠²╠²╠²_tp╠²╠²=╠²&ade_tp
╠²╠²╠²╠²╠²╠²so╠²╠²╠²>hnlrso,
╠²╠²╠²╠²}
╠²╠²╠²╠²
╠²╠²)
╠²╠²═Š
}
PE:enl>u(═Š
O:Kre┬Łrn)](https://image.slidesharecdn.com/async-ftw-121006073203-phpapp01/85/Asynchronous-programming-FTW-28-320.jpg)
![MORE CONDENSED
uePE
s╠²O═Š
fr(.1){
o╠²1.0╠²
╠²╠²m╠²cut=0
╠²╠²y$on╠²╠²═Š
╠²╠²PE:eso┬Łcet(
╠²╠²O:Ssin>rae
╠²╠²╠²╠²iln_tts=╠²
╠²╠²╠²╠²niesae╠²>{
╠²╠²╠²╠²╠²╠²_tr╠²╠²=╠²u╠²
╠²╠²╠²╠²╠²╠²sat╠²╠²>sb{
╠²╠²╠²╠²╠²╠²╠²╠²sy"eso╠²,$[ESO]>D╠²╠²a╠²tre"
╠²╠²╠²╠²╠²╠²╠²╠²a╠²Ssin"╠²_SSIN┬ŁI,"hssatd═Š
╠²╠²╠²╠²╠²╠²╠²╠²PE:enl>il(iceet)
╠²╠²╠²╠²╠²╠²╠²╠²O:Kre┬Łyed'nrmn'═Š
╠²╠²╠²╠²╠²╠²}
╠²╠²╠²╠²╠²╠²,
╠²╠²╠²╠²╠²╠²iceet=╠²u╠²
╠²╠²╠²╠²╠²╠²nrmn╠²>sb{
╠²╠²╠²╠²╠²╠²╠²╠²PE:enl>il(iceet)i╠²+cut<1═Š
╠²╠²╠²╠²╠²╠²╠²╠²O:Kre┬Łyed'nrmn'╠²f+$on╠²╠²0
╠²╠²╠²╠²╠²╠²╠²╠²sy"eso╠²,$[ESO]>D╠²╠²one╠²o$on"
╠²╠²╠²╠²╠²╠²╠²╠²a╠²Ssin"╠²_SSIN┬ŁI,"cutdt╠²cut═Š
╠²╠²╠²╠²╠²╠²}
╠²╠²╠²╠²╠²╠²,
╠²╠²╠²╠²╠²╠²_tp╠²╠²=╠²u╠²
╠²╠²╠²╠²╠²╠²so╠²╠²╠²>sb{
╠²╠²╠²╠²╠²╠²╠²╠²sy"eso╠²,$[ESO]>D╠²╠²a╠²tpe"
╠²╠²╠²╠²╠²╠²╠²╠²a╠²Ssin"╠²_SSIN┬ŁI,"hssopd═Š
╠²╠²╠²╠²╠²╠²}
╠²╠²╠²╠²╠²╠²,
╠²╠²╠²╠²}
╠²╠²╠²╠²
╠²╠²)
╠²╠²═Š
}
PE:enl>u(═Š
O:Kre┬Łrn)](https://image.slidesharecdn.com/async-ftw-121006073203-phpapp01/85/Asynchronous-programming-FTW-29-320.jpg)