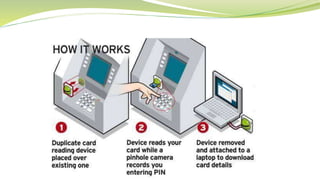
ATM Skimming in the Caribbean
- 1. Giovanni James Regional Legal Adviser Asset Recovery Unit Regional Security System Fusion Centre Paragon, Christ Church Barbados
- 2. What Is ATM Card Skimming?? A method used by criminals to capture data from the magnetic stripe on the back of an ATM card. Devices used are smaller than a deck of cards and are often fastened in close proximity to, or over the top of the ATM’s factory-installed card reader. ATM skimming is a world-wide problem.
- 3. In 2010 Retail Banking Research Limited estimated 1.7 million global ATMs. There are about 49 billion annual worldwide ATM cash withdrawals. The US Secret Service estimates that annual losses from ATM skimming in the USA totals about US $1 billion each year; about US $350,000 a day. Cybercrime now generates over US $1 trillion a year for cybercriminals. It now brings in more money than the drug trade. Did you Know?
- 4. The USA and the Caribbean are considered soft targets. Almost every Caribbean Island has been affected by Card Skimming in varying degrees; with combined losses estimated to be in the millions. Organised crime groups love ATMs
- 6. ď‚— Skimming devices illegally record account data from the magnetic stripe of a credit or debit card. ď‚— PIN numbers are usually capture using hidden devices such as mini cameras, keypad overlays or audio recording devices. ď‚— The average cardholder has no knowledge that the skimming device is there because it does not interfere with the operation of the ATM. ď‚— The data is typically stored in the memory of the skimmer and is downloaded to a PC where it can be used to make fake cards. Skimming
- 7. Other methods of card skimming include: 1. Hidden Card Reader 2. Petrol station pumps where cards are accepted 3. Point of sale machines 4. Contactless Smart card readers
- 8. ATM Skimming Hardware Round-shaped Skimming Device with double- sided tape ATM Skimming Devices with Internal Batteries
- 10. ATM Pin Hole Cameras with Micro SD Memory Card SlotBrochure holder Pin Hole Camera
- 11. ATM PIN capture overlay device pulled back to reveal the legitimate PIN entry pad. Bluetooth-enabled gas pump skimmer.
- 12. Sophisticated ATM Skimmer Transmits Stolen Data Via Text Message
- 13. Many security-savvy persons have learned to be vigilant against ATM card skimmers and hidden devices that can record you entering your PIN at the cash machine. Experts say an increasing form of ATM fraud involves the use of simple devices capable of snatching cash and ATM cards from unsuspected users. Claw-like card & cash trap ATM devices Card reader/writer Adapted 2 Pin USB Charging Cable
- 14. Two network cable card skimming devices, as found attached to this ATM.
- 16. Chip Card ATM Shimmer: Fraud experts in Mexico have discovered an unusual ATM skimming device that can be inserted into the mouth of the cash machine’s card acceptance slot and used to read data directly off of chip-enabled credit or debit cards. The device is a type of skimmer known as a “shimmer,” so named because it acts as a shim that sits between the chip on the card and the chip reader in the ATM — recording the data on the chip as it is read by the ATM.
- 17. ď‚— Skimming devices have the same appearance as genuine fixtures. ď‚— The average skimming attack is a short-term occurrence. ď‚— Usually an hour or two. ď‚— Maximum period of skimming attack on an ATM is usually 24 hours. ď‚— In a 1-2 hour period, criminals can accumulate an average of US $33,000 per incident. ď‚— Skimming usually done at peak transaction times. ď‚— Skimming is a migratory crime. Facts About ATM Skimming
- 18. ď‚— Information Downloaded ď‚— Sale of information ď‚— Card Not Present transactions ď‚— Cloning of cards ď‚— Harvesting What happens to the information on skimming devices?
- 19. Most of the Caribbean region has not fully migrated to the EMV system thus making the region a soft target for ATM Skimming.  Estimate of millions in losses from harvesting of skimmed cards, replacement of skimmed cards and improved security measures.  Significant “soft costs” incurred by FI Risk-Security staff.  Damage to reputation of ATM deployers.  Loss of business.  Fines from the card networks.  Potential lawsuits.  Non-EMV compliant banks will not be refunded by card networks for loses from ATM fraud. Effects of Card Skimming on the Financial Sector
- 20. ď‚— Players are usually involved in Card-Not-Present fraud or cross-border counterfeit fraud (particularly ATM fraud). ď‚— Origin of major card skimmers identified in the region: 1. Eastern Europe- Bulgaria and Romania* 2. Chinese* 3. African- Nigeria* 4. UK 5. USA 6. South America* 7. Locals / Residents * -Most prevalent Who are the major skimmers in our region??
- 21. ď‚— Marked increase in the number of foreign nationals travelling through the region with Skimming equipment. ď‚— Both local and foreign accounts are affected. ď‚— Skimmers move from one Caribbean country to the next skimming and harvesting. ď‚— Skimmers connected to international criminal gangs, ď‚— Skimmers travel under the disguise of vacation, alone or in small groups to various islands in the Caribbean, sometimes with families to hide their true intent. ď‚— Skimmers connected to money laundering, drugs, guns, identity and document fraud e.g. fraudulent passports. Recent ATM Skimming trends in the Caribbean
- 22. ď‚— Recent monitoring and arrests in the Caribbean region have revealed the following criminal connections and associations to card skimming: (1) Money invested in the wholesale purchase of drugs. (2) Money used to purchase firearms which are supplied to gang members. (3) Increase in money laundering. (4) Purchase of high end goods for self-use or resale. (5) Skimmers belong to organised criminal gangs associated with drugs, arms dealing, human trafficking to name a few. (6) Migration of international criminal gangs to our region for ATM skimming introduces into local culture new criminal enterprise which State agencies are not equipped to deal with. Connections and Associations to ATM skimming
- 23.  With the ever increasing problem of ATM skimming and cybercrime in the region and the associated crimes for example, money laundering, drug trafficking, arms trafficking to name a few, countries should consider the inclusion of these types of crimes (skimming and cybercrime) in their National Risk Assessment.  Almost every ATM skimming case will have a component of money laundering.  The identification of ATM/payment card crime as a risk should lead to countries/territories identifying their deficiencies in legislation and training.  Identification of these risks should assist countries/territories in addressing these deficiencies in their National Action Plan. National Risk Assessment – ATM Skimming & Cybercrime
- 24.  Recommendations A. AML/CFT POLICIES AND COORDINATION 1. Assessing risks and applying a risk-based approach  Card skimming/ATM Fraud is a significant threat to the region.  It is connected to all the crimes mentioned previously including money laundering.  It involves transnational criminals.  Movement of monies around the globe.  Failing to address these risks in the National Risk Assessment exercise would mean that a country is failing to take corrective or mitigating measures in relation to a significant threat.  This failure may impact issues such as Customer Due Diligence/Knowing Your Customer.  This failure can give rise to the question of whether Customer Due Diligence/ Know your customer mechanisms are working, given, the significant variance from a customer’s usual activity.  Banks may need to enhance the risk profile of ATMs as a product offered.  Are banks reporting Suspicious Activity Reports in relation to these transactions, which may be tied to many other major crimes such as ML, drug trafficking, human trafficking, transnational crime? FATF 40 Recommendations
- 25. 2. National cooperation and coordination The FIU must: ď‚— work with Financial Institutions and other regulators such as the Central Bank to raise awareness of the threat posed by card skimming. ď‚— Monitor the receipt of Suspicious Activity Reports by financial institutions and other regulated entities with ATMs to ensure that SARs are filed. ď‚— Analyse this information in a timely fashion for dissemination to relevant law enforcement agencies for investigation. ď‚— Consideration can be given to creating a multi-agency task force to discuss strategies to mitigate and combat the threat posed by card skimming.
- 26. Financial Institutions (FIs): ď‚— EMV Migration ď‚— Have a plan ď‚— Document the plan ď‚— Educate employees ď‚— Inspect all ATM locations ď‚— Recording keeping and pictorial documentation ď‚— Set ATM standards ď‚— Report Skimming to law enforcement ď‚— Contact other institutions Tips to reduce ATM skimming
- 27. Card Holders ď‚— Familiarise yourself with the look and feel of the ATM fascia of machines ď‚— Contact your card issuer if you have completed a transaction and suspect that your card or PIN may have been compromised. ď‚— Check your card transactions frequently, using online banking and your monthly statement. ď‚— Always protect your PIN and be aware of people around or close to you. ď‚— Ask your card provider if they offer account alert technology that will deliver SMS text communications or emails to you in the event that fraudulent activity is suspected on your payment card. ď‚— Update your address and cell phone information for every card you have, so that you can be reached if there is ever a critical situation that requires your immediate attention. Law enforcement: ď‚— Familiarise officers in particular, border control officers on skimming equipment and methods of concealment. ď‚— Train law enforcement agencies in investigation and prosecution of ATM skimming.
- 28. ď‚— Secure and preserve evidence of card skimming ASAP. ď‚— Establish cooperative, crime prevention liaison with FIs operating in your country. ď‚— Team with other local, regional and international law enforcement agencies in communicating skimming events, dates, locations and images as well as bio-data of know skimmers and their travel plans. ď‚— Consider working with National Financial Associations to build collaborations and maximize resources. ď‚— Identify, investigate and prosecute associated crimes such as money laundering.