Automated Mobile Malware Classification
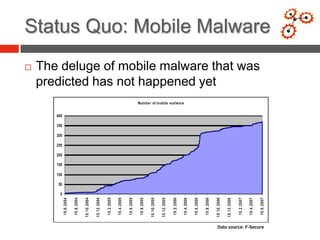
- 2. Status Quo: Mobile Malware ’é© The deluge of mobile malware that was predicted has not happened yet
- 3. Status Quo: Mobile Malware ’é© This does not mean that mobile malware is not a threat ’é© More money moving through GSM means more incentive to build malware ’é© Result: There WERE and WILL be outbreaks
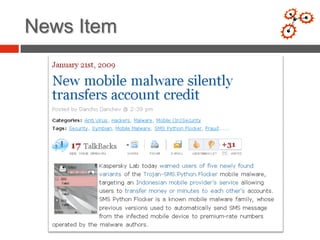
- 4. News Item
- 5. Problem: Variants ’é© A lot of filtering can be done using MD5 ’éż But: Fraudsters learned to obfuscate ’é© Variants are easy to create ’é© In the Windows world: ’éż 20k MD5-different variants of the same malware each month
- 6. Problem: Variants ’é© Ways to determine whether a file is a variant of a known malware are needed. Preferrably: ’éż Fast ’éż Cheap ’éż Reliable ’éż Easily adapted to future threats
- 7. Current approach ’é© Analysis is ’éż Notdone at all ’éż Done manually by a security expert ’éż Done in some ad-hoc automated fashion
- 8. Problem: Variants ’é© Manual approaches do not satisfy our requirements: ’éż Fast: No ’éż Cheap: No ’éż Reliable: Depends on the guy ’éż Easily adaptable Depends on the guy
- 9. Program Comparison ’é© How would we check if a file is a variant ? ’é© Program comparison tools are needed ’é© Surprise: We have built some ’éż In use in the ITSec and AV world since 2004 ’éż ŌĆ×Best PaperŌĆ£ at SSTIC 2005 ’éż GermanyŌĆśs biggest privately funded research prize 2006 ’ü« We beat Siemens and T-Systems
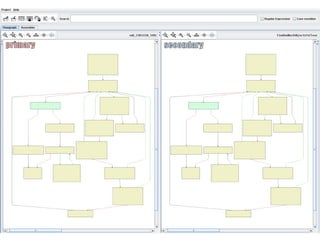
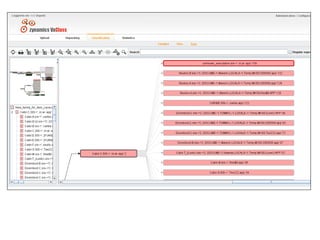
- 10. Program Comparison ’é© Core principle: Comparison is structural ’é© Instructions may change a lot, the program structure only slightly ’é© Graphs are generated from the programs ’é© Comparison happens on these graphs
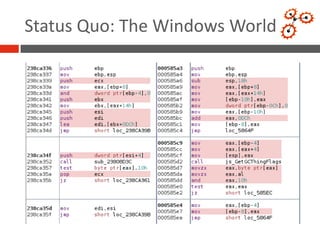
- 11. Status Quo: The Windows World
- 12. Competition
- 13. Program Comparison ’é© Our comparison is strong because ... ’éż The entire program is taken into consideration ’éż Recompiling does not fool us ’éż Stable parts are identified ’éż Large changes do not matter much
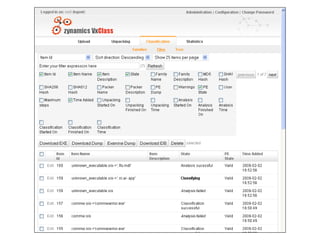
- 14. VxClass for Mobile Malware ’é© VxClass compares executables ’é© A library of known malware is kept ’é© New executables can be checked if they are similar to existing malware ’é© Easy to use, Reliable, Cheap
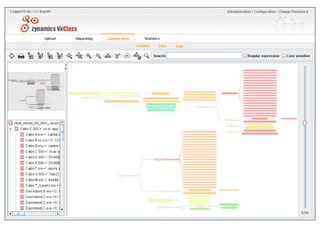
- 15. Case Study ’é© Unknown executable is received ’é© MD5 does not match anything ’é© Is it a variant of an existing piece of malware ?
- 22. Multi-User capability ’é© Web-based ’é© Log in via username/password or SSL certificates ’é© Automation: Interaction via XMLRPC
- 23. Multi-User capability ’é© Different users can upload samples ’é© Three levels of permissions: ’éż Public: All users can download the sample ’éż Protected: All users can see, but not download the sample ’éż Private: No other users can see the sample
- 24. Business Case Basic scenario: ’é© Recognize new malware variants ’é© Limit risk of outbreak ’é© Low-cost ’é© Fast response time
- 25. Business Case Advanced scenario (with shared samples): ’é© Neighborhood watch ’éż Who else has seen this before ? ’éż Where ? ’éż When ? ’éż Who should I talk to ? ’é© Improve communication
- 26. Pricing Telco-Style: Base Fee + Volume ’é© Basic: ’éż 200 Ōé¼ / month ’éż 50 Ōé¼ per uploaded executable ’é© Medium: ’éż 500 Ōé¼ / month ’éż 10 uploads included, 30 Ōé¼ each afterwards ’é© Flat rate: ’éż 999 Ōé¼ / month ’éż No volume fee*
- 27. Pricing ’é© Only available to GSMA members ’é© The basic and medium packages may be shared between business entities
- 28. Pricing This includes ’é© Providing the server / service ’é© Backups ’é© Email support
- 29. Roadmap We will watch and adapt to new threats ’é© Windows Mobile Executables ’é© Of current relevance: .pyc ’é© Widgets ’é© iPhone executables ’é© Android
- 30. Summary ’é© We provide strong methods that identify malware variants ’é© Cheap, Fast, Accurate ’é© Any questions ? Contact us ! info@zynamics.com