Avast installation and operation
1 like181 views
Installation & Operation Avast Free Antivirus 2016 offers an antivirus and anti-malware protection, along with features you're most likely to need, but would rather not think about - like one-click system checks, and unwanted toolbar removal.
1 of 27
Download to read offline






















Recommended
How to remove malware from pc?



How to remove malware from pc?Patrick Presley
?
Dial - 1844-353-5969 toll free for instant suppor on removing malware from pc? How to detect the presence of malware on your system. A guide which helps in removing the malwares form your computer. How to remove malware from your windows computer



How to remove malware from your windows computerTechnetweb
?
Step by step guide for all PC owners that teaches you how to remove malware from your Windows computer.How to uninstall mypc backup



How to uninstall mypc backupcoseanonans
?
Are you in need of uninstalling MYPC BACKUP? Several days ago, one of my friends brought her laptop and asked me to help her remove MYPC BACKUP. She said she uninstalled it through Control Panel Add/ Remove Programs but an error message popped up and stopped its uninstalling. Luckily, it only took me no more than 10 minutes to completely uninstall MYPC BACKUP.
How to-remove- virus



How to-remove- virussecuresolutionusa
?
This document helps you to remove the virus from your PC and laptop. Follow the steps in the document carefully and enjoy.Virus and malware removal instructions



Virus and malware removal instructionsitwebresources
?
This is a virus and malware removal guide for windows based computer systems provided by ITWebResources.com. Self-Help malware removal instructions in 20 easy to follow steps:How to fix windows update error 80072 efe



How to fix windows update error 80072 efeMadisonSmith99
?
Substantially Windows Update Error 80072EFE arises when working with a windows machine. Error 80072EFE is either server- or client-slide linked. Therefore, you can't solve the problem from the server side alone. Fixing browser redirection viruses



Fixing browser redirection virusesscottgelbard123
?
Browser hijacking is a serious nuisance in today¡¯s web surfing experience. Fortunately, avoiding a browser hijacking is not impossible if you stay aware, and take a few simple precautions.
Remove Clickhoofind.com



Remove Clickhoofind.comkingh05
?
http://www.removemalwarethreats.com/2014/10/11/uninstall-clickhoofind-com-from-windows-system Clickhoofind.com is nasty ad ware that destroys your system and steal your all information from your system.Windows 11 virus



Windows 11 virusssuser1eca7d
?
Have you encountered Windows 11 Virus or malware yet? How do you find it? How do you handle it? Do you have some ideas about how to avoid it?How to uninstall mpc cleaner rogue program



How to uninstall mpc cleaner rogue programharoNaroum
?
MPC CLEANER is considered as rogue software which pretends to be a normal antivirus program to attack computers. The program can get into targeted computers in different ways.
How to uninstall shopperz pop up



How to uninstall shopperz pop upharoNaroum
?
Shopperz adware is not a new¨Creleased advertising program. While the release of this adware used to be a hot issue of last year, now it tends to be popular again. As we reflect on 2014, it is clear that this adware has been an typical advertising threat which has infected by a lot of computers around the world. We comb some computer blogs, pore over computer security forums and enlist the help of related information, professional removal tools and effective removal manual guide to deliver users some of the most professional methods of removing this adware. The associated details are below:Remove gangnamgame.net from pc



Remove gangnamgame.net from pcharoNaroum
?
Most of us have had a love-hate experience relationship with online games. We all come up with bizarre ways to play some casual games online when we have browsed the web for a longtime. But when we are approaching to some websites, we usually do not have the ability to figure out whether this site is safe or not. For example, there is a site named Gangnamgame.net which is reported by many net users as it has been regarded as an insecure website recently. The most hateful feature of this site from the victims who get it from free bundles is that it acts like a browser hijacker because it tends to control browser settings forcibly. Is it really dangerous? Keep reading to find answer.
Remove Coup alert



Remove Coup alertkingh05
?
http://www.removemalwarethreats.com/2014/10/09/remove-coupalert-from-pc Coup alert is the most harmful browser hijacker which hijacked your all most popular Internet browsers and does many changes in your system.How to remove smart shopsave.com



How to remove smart shopsave.comcoseanonans
?
I am being bothered by SmartShopSave.com redirect virus when I am browsing the internet. It is said that this is a browser hijacker which will hijack my homepage and search engine and then show me a lot of commercial ads. I am afraid that it will cause other troubles. How can I stop it from keeping hijacking?Uninstall program from window7



Uninstall program from window7sean kingston
?
This tool also provides a feature called ¡°Quick/Multiple uninstall¡± to remove more than one program at the same time.It is very fast and strong software. This Tools avoid Installation Error.Speeding up your pc in 5 easy steps



Speeding up your pc in 5 easy stepsInsynQ-inc
?
Is your PC running sluggish or slow? Allow the InsynQ team to give you a few pointers to speed things up a bit... As seen on http://www.insynq.comRemove Windows Foolproof Protector Automatically From Your System



Remove Windows Foolproof Protector Automatically From Your Systemcostamary
?
http://www.spywareremovalguide.org/fixerror/steps-to-remove-windows-foolproof-protector/832
You can easily remove Enfiltrator Black Box from your PC automatically by Enfiltrator Black Box removal tool. It provides you easy and simple process for removing spyware. Taking a Quiz Using the Respondus Lockdown Browser



Taking a Quiz Using the Respondus Lockdown BrowserDaytona State College Library
?
1) The document provides instructions for downloading and installing the Respondus Lockdown Browser on Windows and Mac systems in order to take online quizzes that require its use.
2) It explains the download and installation process for both Windows and Mac, which involves downloading files from the Respondus website, agreeing to license terms, and installing the browser software.
3) Once installed, students are instructed to log into their online course site and select the quiz that requires Respondus Lockdown Browser to launch and complete the quiz within the locked down browser environment.How to remove mpc cleaner



How to remove mpc cleanercoseanonans
?
MPC CLEANER categorized as adware which enters into the system of user silently after visiting some malicious sites. It is created by cyber criminals and after entering into the system, it displays lots of unwanted pop-up ads. This adware is dreadfully perilous for your computer as it attaches to your web browsers and show numerous such ads and pop-ups messages that lead you to precarious websites.Fixing windows 10 automatic updates install problem



Fixing windows 10 automatic updates install problemscarlet christer
?
In this ppt, learn how to fix windows 10 automatic updates problem. Here we provide you some prominent methods to fix this issues, you can choose any of these methods according to your requirement.MS Teams on IOS



MS Teams on IOSTodd Spodek
?
This document provides 7 steps to join a Microsoft Teams meeting using an iPhone and the Microsoft Teams mobile app. It explains that you do not need a Teams account to join as a guest. If the Teams app is not installed, it guides the user to download and install it from the App Store. Once installed, it describes opening the meeting link in Teams and joining the meeting, where you may have to wait in the virtual lobby to be admitted, and how to access options like chat and participants during the meeting.Basic pc trouble shooting



Basic pc trouble shootingGener Luis Morada
?
Basic troubleshooting steps include remaining calm, checking individual computer modules for defects that could impact the whole system, and using another identical computer for testing if possible. Common issues include failures to start up, freezing at boot up or with error messages, lack of monitor or sound output, inability to connect to the internet, unauthorized messages or connections, and slow performance or freezing during use.Windows 8 problems and solutions



Windows 8 problems and solutionsAkal Technology Inc
?
Windows 8 is a new operating system so chances are there to get surprised with errors. Do not get obsessed, here are bunch of common errors and their solution:How to activate windows 8



How to activate windows 8KevinDRolle
?
How To Activate Windows 8.
Installation of brand new software can be quite a pain if you are a technophobe who just wants the end benefits of new software minus all of the techno mumbo-jumbo. (Read: someone who just wants to know that the car starts, and doesn't particularly care what's going on under the hood). You could live quite a comfortable life without ever having to see a command prompt.
Unfortunately, using the command prompt will be a part of the activation process. (But it's nothing so major that you can't handle).
glary utilities pra que serve



glary utilities pra que serveHelbo46Helbo
?
Glary Utilities is a software that helps maintain and optimize computer performance. It allows users to create system restore points to revert the computer back to an earlier state if issues arise. Regular computer maintenance like updating antivirus software, running disk cleanup monthly, and disk defragmentation yearly can also help fix many problems and prevent slowdowns. The software's activation code allows full use of its features to repair corrupt files, uninstall problematic programs, scan for malware, and restore the system registry.How to repair windows 8



How to repair windows 8Alex Robert
?
Community Q&A
Windows 8 includes a utility called System Restore, which allows you to roll your computer back to a point when it was working properly. The restore points are created automatically when changes are made the the system, but you can manually create one whenever you'd like if you intend on making some changes yourself. If for some reason you aren't able to create restore points, there are several troubleshooting solutions you can try.Black sceen fix instructions



Black sceen fix instructionsJavier Arroyave
?
The document provides instructions to fix a black screen issue on a Point of View 10" Tegra tablet by upgrading the firmware. It is a 12 step process that involves connecting the tablet to a PC with a USB cable, installing USB drivers, running a firmware update file, then rebooting the tablet which will take longer the first time. Disabling antivirus software and fully charging the tablet battery are recommended before beginning the process.Remove Windows Protection Unit - Guideline For Automatic Removal



Remove Windows Protection Unit - Guideline For Automatic Removalcostamary
?
The document provides information about removing the Windows Protection Unit application. It describes the application as a malicious program that can slow system performance and cause security issues. It provides two methods for removing the application: manual removal by deleting registry entries and files, and automatic removal using a removal tool that scans and cleans the system in a simple process. The summary recommends the automatic removal tool as an easy way to remove the dangerous Windows Protection Unit virus in just a few steps.FirmLogix DEVICE DRIVERS Corporate Brochure



FirmLogix DEVICE DRIVERS Corporate BrochureMike Warren
?
This document summarizes FirmLogix's system software development and certification testing services. They offer expertise in areas like audio/video codecs, graphics drivers, wireless and wired networking drivers, and certification for operating systems including Windows, Linux, and embedded platforms. FirmLogix manages the entire Microsoft WHQL certification process using DTM to ensure clients' products get certified quickly so they can display Microsoft logos. They are a system software company that provides drivers, firmware, and certification testing to help clients reduce costs and time to market.

More Related Content
What's hot (20)
Windows 11 virus



Windows 11 virusssuser1eca7d
?
Have you encountered Windows 11 Virus or malware yet? How do you find it? How do you handle it? Do you have some ideas about how to avoid it?How to uninstall mpc cleaner rogue program



How to uninstall mpc cleaner rogue programharoNaroum
?
MPC CLEANER is considered as rogue software which pretends to be a normal antivirus program to attack computers. The program can get into targeted computers in different ways.
How to uninstall shopperz pop up



How to uninstall shopperz pop upharoNaroum
?
Shopperz adware is not a new¨Creleased advertising program. While the release of this adware used to be a hot issue of last year, now it tends to be popular again. As we reflect on 2014, it is clear that this adware has been an typical advertising threat which has infected by a lot of computers around the world. We comb some computer blogs, pore over computer security forums and enlist the help of related information, professional removal tools and effective removal manual guide to deliver users some of the most professional methods of removing this adware. The associated details are below:Remove gangnamgame.net from pc



Remove gangnamgame.net from pcharoNaroum
?
Most of us have had a love-hate experience relationship with online games. We all come up with bizarre ways to play some casual games online when we have browsed the web for a longtime. But when we are approaching to some websites, we usually do not have the ability to figure out whether this site is safe or not. For example, there is a site named Gangnamgame.net which is reported by many net users as it has been regarded as an insecure website recently. The most hateful feature of this site from the victims who get it from free bundles is that it acts like a browser hijacker because it tends to control browser settings forcibly. Is it really dangerous? Keep reading to find answer.
Remove Coup alert



Remove Coup alertkingh05
?
http://www.removemalwarethreats.com/2014/10/09/remove-coupalert-from-pc Coup alert is the most harmful browser hijacker which hijacked your all most popular Internet browsers and does many changes in your system.How to remove smart shopsave.com



How to remove smart shopsave.comcoseanonans
?
I am being bothered by SmartShopSave.com redirect virus when I am browsing the internet. It is said that this is a browser hijacker which will hijack my homepage and search engine and then show me a lot of commercial ads. I am afraid that it will cause other troubles. How can I stop it from keeping hijacking?Uninstall program from window7



Uninstall program from window7sean kingston
?
This tool also provides a feature called ¡°Quick/Multiple uninstall¡± to remove more than one program at the same time.It is very fast and strong software. This Tools avoid Installation Error.Speeding up your pc in 5 easy steps



Speeding up your pc in 5 easy stepsInsynQ-inc
?
Is your PC running sluggish or slow? Allow the InsynQ team to give you a few pointers to speed things up a bit... As seen on http://www.insynq.comRemove Windows Foolproof Protector Automatically From Your System



Remove Windows Foolproof Protector Automatically From Your Systemcostamary
?
http://www.spywareremovalguide.org/fixerror/steps-to-remove-windows-foolproof-protector/832
You can easily remove Enfiltrator Black Box from your PC automatically by Enfiltrator Black Box removal tool. It provides you easy and simple process for removing spyware. Taking a Quiz Using the Respondus Lockdown Browser



Taking a Quiz Using the Respondus Lockdown BrowserDaytona State College Library
?
1) The document provides instructions for downloading and installing the Respondus Lockdown Browser on Windows and Mac systems in order to take online quizzes that require its use.
2) It explains the download and installation process for both Windows and Mac, which involves downloading files from the Respondus website, agreeing to license terms, and installing the browser software.
3) Once installed, students are instructed to log into their online course site and select the quiz that requires Respondus Lockdown Browser to launch and complete the quiz within the locked down browser environment.How to remove mpc cleaner



How to remove mpc cleanercoseanonans
?
MPC CLEANER categorized as adware which enters into the system of user silently after visiting some malicious sites. It is created by cyber criminals and after entering into the system, it displays lots of unwanted pop-up ads. This adware is dreadfully perilous for your computer as it attaches to your web browsers and show numerous such ads and pop-ups messages that lead you to precarious websites.Fixing windows 10 automatic updates install problem



Fixing windows 10 automatic updates install problemscarlet christer
?
In this ppt, learn how to fix windows 10 automatic updates problem. Here we provide you some prominent methods to fix this issues, you can choose any of these methods according to your requirement.MS Teams on IOS



MS Teams on IOSTodd Spodek
?
This document provides 7 steps to join a Microsoft Teams meeting using an iPhone and the Microsoft Teams mobile app. It explains that you do not need a Teams account to join as a guest. If the Teams app is not installed, it guides the user to download and install it from the App Store. Once installed, it describes opening the meeting link in Teams and joining the meeting, where you may have to wait in the virtual lobby to be admitted, and how to access options like chat and participants during the meeting.Basic pc trouble shooting



Basic pc trouble shootingGener Luis Morada
?
Basic troubleshooting steps include remaining calm, checking individual computer modules for defects that could impact the whole system, and using another identical computer for testing if possible. Common issues include failures to start up, freezing at boot up or with error messages, lack of monitor or sound output, inability to connect to the internet, unauthorized messages or connections, and slow performance or freezing during use.Windows 8 problems and solutions



Windows 8 problems and solutionsAkal Technology Inc
?
Windows 8 is a new operating system so chances are there to get surprised with errors. Do not get obsessed, here are bunch of common errors and their solution:How to activate windows 8



How to activate windows 8KevinDRolle
?
How To Activate Windows 8.
Installation of brand new software can be quite a pain if you are a technophobe who just wants the end benefits of new software minus all of the techno mumbo-jumbo. (Read: someone who just wants to know that the car starts, and doesn't particularly care what's going on under the hood). You could live quite a comfortable life without ever having to see a command prompt.
Unfortunately, using the command prompt will be a part of the activation process. (But it's nothing so major that you can't handle).
glary utilities pra que serve



glary utilities pra que serveHelbo46Helbo
?
Glary Utilities is a software that helps maintain and optimize computer performance. It allows users to create system restore points to revert the computer back to an earlier state if issues arise. Regular computer maintenance like updating antivirus software, running disk cleanup monthly, and disk defragmentation yearly can also help fix many problems and prevent slowdowns. The software's activation code allows full use of its features to repair corrupt files, uninstall problematic programs, scan for malware, and restore the system registry.How to repair windows 8



How to repair windows 8Alex Robert
?
Community Q&A
Windows 8 includes a utility called System Restore, which allows you to roll your computer back to a point when it was working properly. The restore points are created automatically when changes are made the the system, but you can manually create one whenever you'd like if you intend on making some changes yourself. If for some reason you aren't able to create restore points, there are several troubleshooting solutions you can try.Black sceen fix instructions



Black sceen fix instructionsJavier Arroyave
?
The document provides instructions to fix a black screen issue on a Point of View 10" Tegra tablet by upgrading the firmware. It is a 12 step process that involves connecting the tablet to a PC with a USB cable, installing USB drivers, running a firmware update file, then rebooting the tablet which will take longer the first time. Disabling antivirus software and fully charging the tablet battery are recommended before beginning the process.Remove Windows Protection Unit - Guideline For Automatic Removal



Remove Windows Protection Unit - Guideline For Automatic Removalcostamary
?
The document provides information about removing the Windows Protection Unit application. It describes the application as a malicious program that can slow system performance and cause security issues. It provides two methods for removing the application: manual removal by deleting registry entries and files, and automatic removal using a removal tool that scans and cleans the system in a simple process. The summary recommends the automatic removal tool as an easy way to remove the dangerous Windows Protection Unit virus in just a few steps.Viewers also liked (7)
FirmLogix DEVICE DRIVERS Corporate Brochure



FirmLogix DEVICE DRIVERS Corporate BrochureMike Warren
?
This document summarizes FirmLogix's system software development and certification testing services. They offer expertise in areas like audio/video codecs, graphics drivers, wireless and wired networking drivers, and certification for operating systems including Windows, Linux, and embedded platforms. FirmLogix manages the entire Microsoft WHQL certification process using DTM to ensure clients' products get certified quickly so they can display Microsoft logos. They are a system software company that provides drivers, firmware, and certification testing to help clients reduce costs and time to market.

DBMS



DBMSemran nur
?
The document defines and compares key database concepts:
1. A super key uniquely identifies records in a table but may contain unnecessary fields, while a candidate key is a minimal set of fields that uniquely identify records. The primary key is the chosen candidate key that links tables.
2. A foreign key in one table matches the primary key of another, linking the tables.
3. Other concepts covered include joins, indexes, hashing, triggers and assertions.Audio Drivers



Audio DriversAnil Kumar Pugalia
?
The document discusses Linux audio drivers. It introduces the Linux audio subsystem, including the ALSA sound core in kernel space and its interfaces for user space applications. It describes the vertical components like the sound core and horizontal components like audio codec and controller drivers. It also covers porting an audio driver, which may involve changing pin assignments for standard codecs or implementing new codec drivers.Hdmi



HdmiNIKHIL NAIR
?
HDMI (High-Definition Multimedia Interface) is a digital connection standard that allows transmission of video and audio data between devices such as Blu-ray players, video game consoles, and HDTVs. It transmits encoded video and audio data digitally using TMDS (Transition Minimized Differential Signaling). There are different versions of HDMI from 1.0 to 1.3 that offer increased bandwidth. While HDMI is backward compatible with DVI, HDMI provides additional features like audio and device control capabilities. HDMI specifications include electrical and mechanical requirements for cables and connectors to support various video formats and resolutions.Presentation on Input and Output Devices



Presentation on Input and Output DevicesZobia Aziz
?
Input devices such as keyboards and mice allow users to enter data into a computer. Keyboards allow text entry and have alphanumeric keys as well as special keys. Mice control cursor movement on screen and come in mechanical, optical, and cordless varieties. Optical scanners digitize text and images for computer use. Output devices such as monitors, printers, and speakers allow users to see and hear information from the computer. Monitors display soft copy output while printers produce hard copy printouts.

Similar to Avast installation and operation (20)
How to Fix ESET Antivirus Update Errors?



How to Fix ESET Antivirus Update Errors?Antivirus Tales
?
Are you dealing with the ESET antivirus update issue? We have helped many users resolve the antivirus update error. So, if updating software is a concern, read this post thoroughly. Here, we will discuss standard solutions to fix the issue. Visit:- https://antivirustales.com/knowledgebase/how-to-fix-eset-antivirus-update-errorRemove adware and_popups



Remove adware and_popupsCHRISLEE PHIL
?
This document provides a 6-step guide to remove pop-up ads from a computer. The steps include uninstalling any malicious programs, resetting browser settings in Internet Explorer, Firefox and Chrome, using AdwCleaner to remove adware, using Junkware Removal Tool to remove browser hijackers, scanning with Malwarebytes Anti-Malware, and using HitmanPro to double check for infections. Each step provides detailed instructions for performing tasks like downloading utilities, running scans, and removing any detected threats.Malwarebytes Installation



Malwarebytes InstallationLorens Tech Solutions
?
Malwarebytes is an Anti-Spam program; Malwarebytes Anti-Malware (MBAM) is an application for computers running under the Microsoft Windows and Apple OS X operating system that finds and removes malware. This slide show instructs you on the installation of the program Malwarebytes.CCleaner Installation and Operation



CCleaner Installation and OperationLorens Tech Solutions
?
CCleaner is a freeware system optimization, privacy and cleaning tool. It removes unused files from your system allowing Windows to run faster and freeing up valuable hard disk space. It also cleans traces of your online activities such as your Internet history. Additionally it contains a fully featured registry cleaner.Close backgrown program



Close backgrown programwasim liam
?
Closing background programs in Windows can free up system resources. This can resolve issues like slow performance or programs conflicting over devices. The document provides instructions for temporarily disabling programs using the system tray, Task Manager, or MSCONFIG. It warns to avoid ending critical system processes and recommends selecting Normal Startup after troubleshooting.Take Care of Your Computer Part 1 -- Disinfection Jan-19-2012



Take Care of Your Computer Part 1 -- Disinfection Jan-19-2012Ted Whittemore
?
Talk on Disinfecting Your Windows PC Using Free Malwarebytes and Spybot, & How to Avoid Infection -- on Jan. 19, 2012 Kinnelon Public Library, NJ -- see the Working Computers Blog Articles:
http://www.kinneloncomputers.com/2012/01/talk-how-to-take-care-of-your-computer.html
and:
http://www.kinneloncomputers.com/2012/01/taking-care-of-your-computer-for-free.html
Fixed: Slow Startup on Windows 10 HP Laptop



Fixed: Slow Startup on Windows 10 HP LaptopDash Milly
?
If your Windows 10 HP laptop takes forever to start up Windows 10, you can follow this helpful guide to fix slow startup on Windows 10 HP laptop issue.Important tips to speed up a slow laptop



Important tips to speed up a slow laptopWalter dushime
?
1. Close unnecessary programs running in the system tray and at startup to free up resources.
2. Keep Windows, drivers, and apps updated to fix issues and improve performance.
3. Delete unnecessary files to free up storage space, aiming to keep hard disk drives under 90% capacity for best performance.How to insert license key for avast antivirus



How to insert license key for avast antivirussophiachristie1090
?
Avast antivirus tool is highly recommended for you. To obtain effective security support from this application, you need to activate license key. For this, you should follow the steps as mentioned below. You can also call Avast support helpline number in order to obtain complete assistance.Microsoft Security Essentials



Microsoft Security EssentialsAgnes Regio
?
A software from Microsoft that runs in the background to protect your personal computer against malware, spyware, viruses as well as other malicious online threats.How to schedule Avast boot-time scan?



How to schedule Avast boot-time scan?Antivirus Support Helpline Canada
?
In this presentation, you will learn how to schedule an Avast boot time scan which is effective. The scanning process runs before the Windows starts and thus there is no chance for rootkits and other modifiers to hide. Learn with Avast Support Canada.How to Remove/Uninstall WinKavApp.exe from PC Efficiently



How to Remove/Uninstall WinKavApp.exe from PC EfficientlyAshok Albert
?
What are the causes of infiltration of WinKavApp.exe in your computer? How does it harm your computer and what are its disadvantages?How to Install Norton Internet Security in Windows 8.1 - RiseZone



How to Install Norton Internet Security in Windows 8.1 - RiseZoneRISEZONE SOLUTIONS
?
This document outlines 31 steps to install and configure Norton Internet Security on Windows 8.1. It details downloading and running the Norton setup file, accepting the license agreement, completing activation by providing an email address, and verifying the installation is complete by checking security settings in the Control Panel. It also describes how to uninstall Norton Internet Security by running the uninstall utility and confirming removal of all user data and subscriptions.How to Resolve Avast Antivirus Update Error



How to Resolve Avast Antivirus Update ErrorKevin Pierce
?
Get the best three methods to resolve Avast antivirus update error on your PC. The update error might arise due to incorrect installation and incompatible OS.
Troubleshoot Can¡¯t Install Sophos Antivirus Issue



Troubleshoot Can¡¯t Install Sophos Antivirus IssueKevin Pierce
?
Why you can¡¯t install Sophos antivirus? Learn it here, and get the best 5 methods to troubleshoot the error. Start by checking your internet connection.
Dosearches virus removal



Dosearches virus removalsakthiprime2
?
Do Searches is a browser hijacker that changes the browser homepage and search engine settings without permission. It displays ads on the homepage and collects search terms. It is distributed through other free software installers. To remove it, use AdwCleaner to remove malicious files, Junkware Removal Tool to remove it from browsers, manually edit browser shortcuts, use Malwarebytes to scan for remaining files, and use HitmanPro as a second scan. Always be careful during software installs and opt out of optional installs you don't want.Solve Stop Code Memory Management on Windows.pptx



Solve Stop Code Memory Management on Windows.pptxGevitaChinnaiah
?
This document provides 9 methods for fixing the MEMORY_MANAGEMENT stop code error in Windows 10. It begins by explaining what memory management is and some potential causes of the error, such as software issues, hardware conflicts, RAM errors, or outdated drivers. The 9 methods provided to resolve the error include scanning for malware, running the Windows Memory Diagnostic tool, updating drivers, checking for disk errors, repairing system files, clearing temporary files, uninstalling recently installed applications, installing pending Windows updates, and resetting Windows 10.Panda antivirus helpline number



Panda antivirus helpline numberjohnlee69629
?
Installation and uninstallation related issues are most common issues faced by our customers. They have faith in us. They call us and we serve them in a matter of seconds.
Panda antivirus helpline number



Panda antivirus helpline numberjohnlee69629
?
The document outlines 11 steps to install Panda Free Antivirus on a computer. It includes downloading the installation file from the Panda website, saving it to the desktop, running the installer, selecting language and installation options, accepting agreements, and restarting after installation. It also provides a toll-free number and website URL for support in case of issues with installing or uninstalling Panda Antivirus.Windows 10: How to reset default settings 



Windows 10: How to reset default settings Xoom Telecom
?
Windows 10 is latest and is more or less popular. But if you have any problem in operating and you are not finding the root of the cause. Then resetting will fix the issue if you can afford it. It will delete current apps or software and saved data from your pc. You have to reinstall them all. So think twice before resetting to default settings.Recently uploaded (20)
World Information Architecture Day 2025 - UX at a Crossroads



World Information Architecture Day 2025 - UX at a CrossroadsJoshua Randall
?
User Experience stands at a crossroads: will we live up to our potential to design a better world? or will we be co-opted by ¡°product management¡± or another business buzzword?
Looking backwards, this talk will show how UX has repeatedly failed to create a better world, drawing on industry data from Nielsen Norman Group, Baymard, MeasuringU, WebAIM, and others.
Looking forwards, this talk will argue that UX must resist hype, say no more often and collaborate less often (you read that right), and become a true profession ¡ª in order to be able to design a better world.DevNexus - Building 10x Development Organizations.pdf



DevNexus - Building 10x Development Organizations.pdfJustin Reock
?
Developer Experience is Dead! Long Live Developer Experience!
In this keynote-style session, we¡¯ll take a detailed, granular look at the barriers to productivity developers face today and modern approaches for removing them. 10x developers may be a myth, but 10x organizations are very real, as proven by the influential study performed in the 1980s, ¡®The Coding War Games.¡¯
Right now, here in early 2025, we seem to be experiencing YAPP (Yet Another Productivity Philosophy), and that philosophy is converging on developer experience. It seems that with every new method, we invent to deliver products, whether physical or virtual, we reinvent productivity philosophies to go alongside them.
But which of these approaches works? DORA? SPACE? DevEx? What should we invest in and create urgency behind today so we don¡¯t have the same discussion again in a decade?BoxLang JVM Language : The Future is Dynamic



BoxLang JVM Language : The Future is DynamicOrtus Solutions, Corp
?
Just like life, our code must evolve to meet the demands of an ever-changing world. Adaptability is key in developing for the web, tablets, APIs, or serverless applications. Multi-runtime development is the future, and that future is dynamic. Enter BoxLang: Dynamic. Modular. Productive. (www.boxlang.io)
BoxLang transforms development with its dynamic design, enabling developers to write expressive, functional code effortlessly. Its modular architecture ensures flexibility, allowing easy integration into your existing ecosystems.
Interoperability at Its Core
BoxLang boasts 100% interoperability with Java, seamlessly blending traditional and modern development practices. This opens up new possibilities for innovation and collaboration.
Multi-Runtime Versatility
From a compact 6MB OS binary to running on our pure Java web server, CommandBox, Jakarta EE, AWS Lambda, Microsoft Functions, WebAssembly, Android, and more, BoxLang is designed to adapt to any runtime environment. BoxLang combines modern features from CFML, Node, Ruby, Kotlin, Java, and Clojure with the familiarity of Java bytecode compilation. This makes it the go-to language for developers looking to the future while building a solid foundation.
Empowering Creativity with IDE Tools
Unlock your creative potential with powerful IDE tools designed for BoxLang, offering an intuitive development experience that streamlines your workflow. Join us as we redefine JVM development and step into the era of BoxLang. Welcome to the future.
Inside Freshworks' Migration from Cassandra to ScyllaDB by Premkumar Patturaj



Inside Freshworks' Migration from Cassandra to ScyllaDB by Premkumar PatturajScyllaDB
?
Freshworks migrated from Cassandra to ScyllaDB to handle growing audit log data efficiently. Cassandra required frequent scaling, complex repairs, and had non-linear scaling. ScyllaDB reduced costs with fewer machines and improved operations. Using Zero Downtime Migration (ZDM), they bulk-migrated data, performed dual writes, and validated consistency.How Discord Indexes Trillions of Messages: Scaling Search Infrastructure by V...



How Discord Indexes Trillions of Messages: Scaling Search Infrastructure by V...ScyllaDB
?
This talk shares how Discord scaled their message search infrastructure using Rust, Kubernetes, and a multi-cluster Elasticsearch architecture to achieve better performance, operability, and reliability, while also enabling new search features for Discord users.30B Images and Counting: Scaling Canva's Content-Understanding Pipelines by K...



30B Images and Counting: Scaling Canva's Content-Understanding Pipelines by K...ScyllaDB
?
Scaling content understanding for billions of images is no easy feat. This talk dives into building extreme label classification models, balancing accuracy & speed, and optimizing ML pipelines for scale. You'll learn new ways to tackle real-time performance challenges in massive data environments.Both Feet on the Ground - Generative Artificial Intelligence



Both Feet on the Ground - Generative Artificial IntelligencePete Nieminen
?
High-level presentation for executives and board professionals about Generative AI, its current uses and governance models.Unlock AI Creativity: Image Generation with DALL¡¤E



Unlock AI Creativity: Image Generation with DALL¡¤EExpeed Software
?
Discover the power of AI image generation with DALL¡¤E, an advanced AI model that transforms text prompts into stunning, high-quality visuals. This presentation explores how artificial intelligence is revolutionizing digital creativity, from graphic design to content creation and marketing. Learn about the technology behind DALL¡¤E, its real-world applications, and how businesses can leverage AI-generated art for innovation. Whether you're a designer, developer, or marketer, this guide will help you unlock new creative possibilities with AI-driven image synthesis.AIXMOOC 2.3 - Modelli di reti neurali con esperimenti di addestramento



AIXMOOC 2.3 - Modelli di reti neurali con esperimenti di addestramentoAlessandro Bogliolo
?
Lezione tenuta da Alessandro Bogliolo nell'ambito del MOOC dell'Universit¨¤ di Urbino dedicato a LLMs e IA generativa
https://mooc.uniurb.it/aixmooc SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOT



SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOTTanmaiArni
?
SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOTEaseUS Partition Master Crack 2025 + Serial Key



EaseUS Partition Master Crack 2025 + Serial Keykherorpacca127
?
https://ncracked.com/7961-2/
Note: >> Please copy the link and paste it into Google New Tab now Download link
EASEUS Partition Master Crack is a professional hard disk partition management tool and system partition optimization software. It is an all-in-one PC and server disk management toolkit for IT professionals, system administrators, technicians, and consultants to provide technical services to customers with unlimited use.
EASEUS Partition Master 18.0 Technician Edition Crack interface is clean and tidy, so all options are at your fingertips. Whether you want to resize, move, copy, merge, browse, check, convert partitions, or change their labels, you can do everything with a few clicks. The defragmentation tool is also designed to merge fragmented files and folders and store them in contiguous locations on the hard drive.
L01 Introduction to Nanoindentation - What is hardness



L01 Introduction to Nanoindentation - What is hardnessRostislavDaniel
?
Introduction to Nanoindentation[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
[Webinar] Scaling Made Simple: Getting Started with No-Code Web AppsSafe Software
?
Ready to simplify workflow sharing across your organization without diving into complex coding? With FME Flow Apps, you can build no-code web apps that make your data work harder for you ¡ª fast.
In this webinar, we¡¯ll show you how to:
Build and deploy Workspace Apps to create an intuitive user interface for self-serve data processing and validation.
Automate processes using Automation Apps. Learn to create a no-code web app to kick off workflows tailored to your needs, trigger multiple workspaces and external actions, and use conditional filtering within automations to control your workflows.
Create a centralized portal with Gallery Apps to share a collection of no-code web apps across your organization.
Through real-world examples and practical demos, you¡¯ll learn how to transform your workflows into intuitive, self-serve solutions that empower your team and save you time. We can¡¯t wait to show you what¡¯s possible!DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (ƽɽÒã)



DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (ƽɽÒã)Tsuyoshi Hirayama
?
DAO UTokyo 2025
–|¾©´óѧÇéˆóѧh ¥Ö¥í¥Ã¥¯¥Á¥§©`¥óÑо¿¥¤¥Ë¥·¥¢¥Æ¥£¥Ö
https://utbciii.com/2024/12/12/announcing-dao-utokyo-2025-conference/
Session 1 :DLT mass adoption
IBM Tsuyoshi Hirayama (ƽɽÒã)MIND Revenue Release Quarter 4 2024 - Finacial Presentation



MIND Revenue Release Quarter 4 2024 - Finacial PresentationMIND CTI
?
MIND Revenue Release Quarter 4 2024 - Finacial PresentationTechnology use over time and its impact on consumers and businesses.pptx



Technology use over time and its impact on consumers and businesses.pptxkaylagaze
?
In this presentation, I explore how technology has changed consumer behaviour and its impact on consumers and businesses. I will focus on internet access, digital devices, how customers search for information and what they buy online, video consumption, and lastly consumer trends.The Future of Repair: Transparent and Incremental by Botond De?nes



The Future of Repair: Transparent and Incremental by Botond De?nesScyllaDB
?
Regularly run repairs are essential to keep clusters healthy, yet having a good repair schedule is more challenging than it should be. Repairs often take a long time, preventing running them often. This has an impact on data consistency and also limits the usefulness of the new repair based tombstone garbage collection. We want to address these challenges by making repairs incremental and allowing for automatic repair scheduling, without relying on external tools.Replacing RocksDB with ScyllaDB in Kafka Streams by Almog Gavra



Replacing RocksDB with ScyllaDB in Kafka Streams by Almog GavraScyllaDB
?
Learn how Responsive replaced embedded RocksDB with ScyllaDB in Kafka Streams, simplifying the architecture and unlocking massive availability and scale. The talk covers unbundling stream processors, key ScyllaDB features tested, and lessons learned from the transition.Early Adopter's Guide to AI Moderation (Preview)



Early Adopter's Guide to AI Moderation (Preview)nick896721
?
Early Adopter's Guide to AI Moderation preview by User Interviews.Avast installation and operation
- 1. Avast Installation & Operation Avast Free Antivirus 2016 offers an antivirus and anti- malware protection, along with features you're most likely to need, but would rather not think about - like one-click system checks, and unwanted toolbar removal. John Lorens 847-687-1329 johnlorens@gmail.com www.lorenstechsolutions.com 1
- 2. Download the latest Free version of Avast from a trusted site line CNET. Enter words like Avast, CNET, Free download. Click on this hyperlink in green to access the software. 2
- 3. Your browser takes you to this trusted CNET site. Click on the green Download Now button to access the software. Do not bother with other promotional links. 3
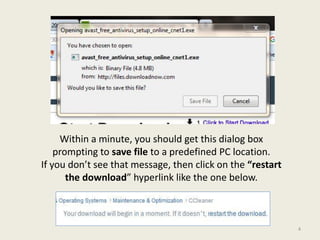
- 4. Within a minute, you should get this dialog box prompting to save file to a predefined PC location. If you don¡¯t see that message, then click on the ¡°restart the download¡± hyperlink like the one below. 4
- 5. Your computer will save the executable setup file. Double click on this file below to begin the installation. 5
- 6. Uncheck the 2 boxes above before you proceed. Click on Customize instead of Install to proceed. 6
- 7. These 2 boxes should be unchecked before proceeding Select Customize , not Install 7
- 8. Let Avast be loaded in the default directory as above. Uncheck the boxes above as the picture shows. Then click on Install to proceed. 8
- 9. Let Avast install itself while leaving the computer on. It may take a few minutes Installation is complete when you get this message 9
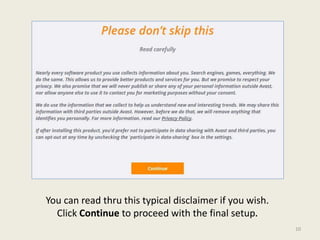
- 10. You can read thru this typical disclaimer if you wish. Click Continue to proceed with the final setup. 10
- 11. Click the hyperlink No, I don¡¯t want to protect phone to proceed with the setup Click Run smart Scan to clean up any software drivers that are out of date 11
- 12. Avast will scan your PC to check for viruses, outdated software, and any other upgrades needed. Only need to do this the 1st time. Avast will report on findings Click on Resolve All to proceed with the fixes. 12
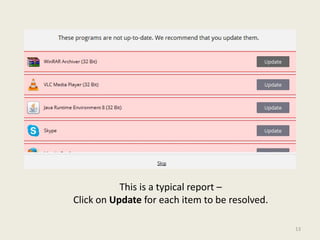
- 13. This is a typical report ¨C Click on Update for each item to be resolved. 13
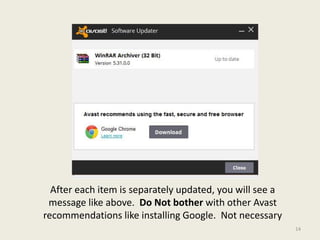
- 14. After each item is separately updated, you will see a message like above. Do Not bother with other Avast recommendations like installing Google. Not necessary 14
- 15. Continue addressing the items one by one. 15
- 16. Skip any Toolbar items 16
- 17. Skip these pages as it requires you to pay for that feature. Not necessary 17
- 18. Skip this as well ¨C it requires a paid version of Avast¡ not necessary. 18
- 19. Avast places an Icon on your desktop. Double click icon to run the program. Repeat any time in the future. Avast opens to display the toolbar above. Click once on upper Scan (magnifying glass) Skip Smart Scan as you already did it. Instead click on Scan for viruses. 19
- 20. For the 1st scan operation, choose full system scan from the drop-down menu. In the future, you can select Quick scan Click Start 20
- 21. The Full system scan will take a while Click on Start to resolve all Treats detected 21
- 22. Click on Apply to fix, heal, remove all virus threats 22
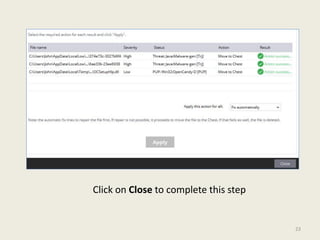
- 23. Click on Close to complete this step 23
- 24. During 1st scan, you can also perform a ¡°boot-time¡± scan. Helpful for the 1st time. Note that when you click on Yes, your PC will reboot, run thru a DOS like display to scan the Boot file & eventually return to the Windows desktop. 24
- 25. In the future, just Double click on this icon to run the program. When Avast opens, Click once on the upper Scan. Click on Scan for viruses, choose Quick Scan & Start. 25
- 26. After the quicker scan, you can choose Apply to remove any threats, or just close the program when no threats are found. 26
- 27. 27 John Lorens Program / Project Manager Computer Engineer johnlorens@gmail.com 847-687-1329 www.lorenstechsolutions.com www.linkedin.com/in/johnlorens/


