Avl tree-hash-table
- 1. AVL TREE & Hash Table Waseem Usman (BSCS-S16-LC-023) Irfan Khan (BSCS-S16-LC-007) Asad Tahir (BSCS-S16-LC-019) Zafeer Ramzan (BSCS-S16-LC-002)
- 2. AVL TREE A binary search tree x is called an AVL tree, if: âĒ b(x.key) â {â1, 0, 1}, and âĒ x.leftChild and x.rightChild are both AVL trees = the height balance of every node must be -1, 0, or 1 A B C D E 0 0 0 0 1 âĒ Named after their inventor Adelson, Velski & Landis, AVL trees are height balancing binary search tree.
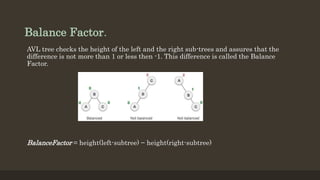
- 3. Balance Factor. AVL tree checks the height of the left and the right sub-trees and assures that the difference is not more than 1 or less then -1. This difference is called the Balance Factor. BalanceFactor = height(left-subtree) â height(right-subtree)
- 4. AVL ROTATIONS To balance itself, an AVL tree may perform the following four kinds of rotations â âĒ Left rotation âĒ Right rotation âĒ Left-Right rotation âĒ Right-Left rotation The first two rotations are single rotations and the next two rotations are double rotations. To have an unbalanced tree, we at least need a tree of height 2. With this simple tree, let's understand them one by one.
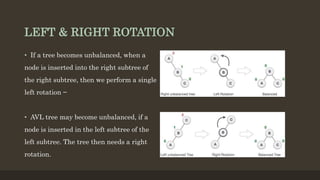
- 5. LEFT & RIGHT ROTATION âĒ If a tree becomes unbalanced, when a node is inserted into the right subtree of the right subtree, then we perform a single left rotation â âĒ AVL tree may become unbalanced, if a node is inserted in the left subtree of the left subtree. The tree then needs a right rotation.
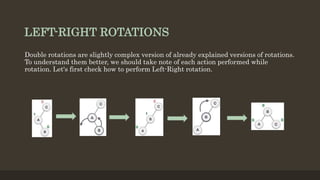
- 6. LEFT-RIGHT ROTATIONS Double rotations are slightly complex version of already explained versions of rotations. To understand them better, we should take note of each action performed while rotation. Let's first check how to perform Left-Right rotation.
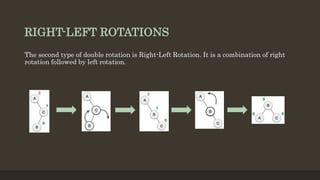
- 7. RIGHT-LEFT ROTATIONS The second type of double rotation is Right-Left Rotation. It is a combination of right rotation followed by left rotation.
- 8. HASH TABLE Asad Tahir Zafeer Ramzan
- 9. HASHING âĒ Searching technique based on hash table. âĒ It is the application of a function to the key value that results in mapping the range of possible key values into smaller range of relative address. âĒ If two different Keys have assign same address then Collision occurs. Data { Key H(K) Hash Function Address K1 K2 H(K) Address{Collision
- 10. TYPES OF HASHING FUNCTIONS âĒ Direct Hashing. âĒ Modulo - Division Hashing. âĒ Mid - Square Hashing. âĒ Folding Hashing. âĒ Pseudo Random Hashing. âĒ Subtraction Hashing.
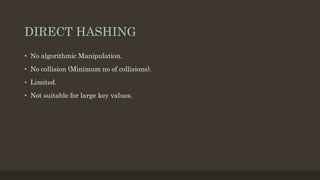
- 11. DIRECT HASHING âĒ No algorithmic Manipulation. âĒ No collision (Minimum no of collisions). âĒ Limited. âĒ Not suitable for large key values.
- 12. MODULO - DIVISION HASHING âĒ Also known as Division - Remainder. âĒ Works with any list size. âĒ If list size is a prime no than fewer collisions. âĒ In Which â K â is a Key and â n â is a List size. H(K) = K mod n
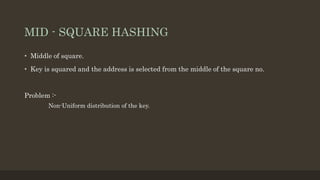
- 13. MID - SQUARE HASHING âĒ Middle of square. âĒ Key is squared and the address is selected from the middle of the square no. Problem :- Non-Uniform distribution of the key.
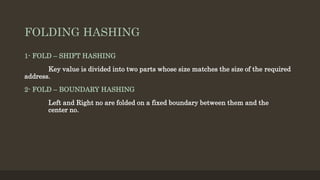
- 14. FOLDING HASHING 1- FOLD â SHIFT HASHING Key value is divided into two parts whose size matches the size of the required address. 2- FOLD â BOUNDARY HASHING Left and Right no are folded on a fixed boundary between them and the center no.
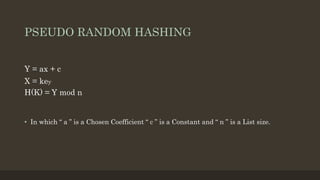
- 15. PSEUDO RANDOM HASHING âĒ In which â a â is a Chosen Coefficient â c â is a Constant and â n â is a List size. Y = ax + c X = key H(K) = Y mod n
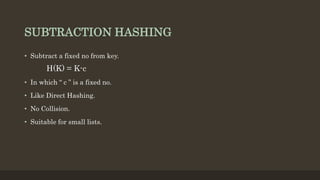
- 16. SUBTRACTION HASHING âĒ Subtract a fixed no from key. âĒ In which â c â is a fixed no. âĒ Like Direct Hashing. âĒ No Collision. âĒ Suitable for small lists. H(K) = K-c
- 17. THANK YOU