1 of 42
Downloaded 107 times








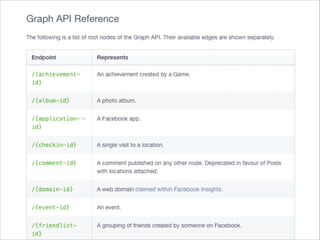




![[3号]!
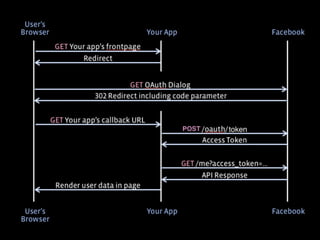
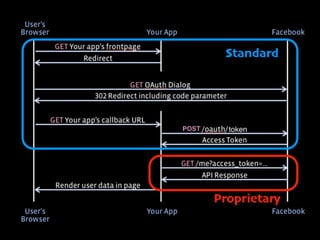
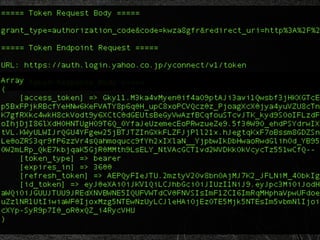
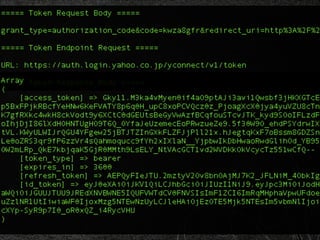
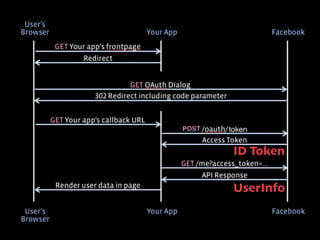
ここまでをフロー図にすると、実はさっきの OAuth のフローとほとんど
さっきの図を元に差分だけ見てみると、access token と同時に ID Toke](https://image.slidesharecdn.com/ayaka-140206000031-phpapp01/85/OAuth-OpenID-Connect-JICS-2014-23-320.jpg)





Ad
Recommended
なぜOpenID Connectが必要となったのか、その歴史的背景
なぜOpenID Connectが必要となったのか、その歴史的背景Tatsuo Kudo
?
Prepared for #DevLOVE
http://devlove.doorkeeper.jp/events/7419
OpenID ConnectとAndroidアプリのログインサイクル
OpenID ConnectとAndroidアプリのログインサイクルMasaru Kurahayashi
?
タイトル:
『OpenID ConnectとAndroidアプリのログインサイクル』
概要:
GoogleやFacebook、Yahoo! JAPANの提供するOAuth、OpenID Connectのシングルサインオン(SSO)を利用する上でトークン、ログイン状態の管理が必要になります。ログイン、ログアウトに加えアプリによってはマルチアカウント利用やアカウント切り替えを必要とするケースもあります。スマフォアプリではネイティブ、WebViewでSSOの認証方法が異なり、実装パターンは多岐にわたります。
これまでID連携の設計や実装サポートしてきたナレッジをもとに、AndroidアプリにおけるSSOからログイン状態の管理まで、アプリの要件にあった実装方法をご紹介します。
Developers Summit 2015 【19-C-5】 Feb. 19, 2015
URL: http://event.shoeisha.jp/devsumi/20150219/session/654OAuth / OpenID Connect (OIDC) の最新動向と Authlete のソリューション
OAuth / OpenID Connect (OIDC) の最新動向と Authlete のソリューションTatsuo Kudo
?
Prepared for MyData Japan 2019
https://mydatajapan.org/events/mydata-japan-2019.htmlパスワードのいらない世界へ 贵滨顿翱认証の最新状况
パスワードのいらない世界へ 贵滨顿翱认証の最新状况FIDO Alliance
?
2019年9月17日(東京)、10月3日(大阪)で開催された、金融ICTカンファレンスにおけるFIDOアライアンス Japan Working Groupによる講演資料OpenID Connect 入門 ?コンシューマーにおけるID連携のトレンド?
OpenID Connect 入門 ?コンシューマーにおけるID連携のトレンド?Masaru Kurahayashi
?
[参考情報]
【永久保存版】OAuth 2.0 / OpenID Connect シーケンスまとめ
URL:https://qiita.com/kura_lab/items/812a62b5aa3427bdb49d
タイトル:
『OpenID Connect 入門 ?コンシューマー領域におけるID連携のトレンド?』
概要:
コンシューマー領域におけるID連携のトレンドであるOpenID Connectの概要と仕様のポイントについてご紹介します。
OpenID TechNight Vol.13 - ID連携入門 Aug. 26, 2015
URL:https://openid.doorkeeper.jp/events/29487認証の課題とID連携の実装 ?ハンズオン?
認証の課題とID連携の実装 ?ハンズオン?Masaru Kurahayashi
?
タイトル:
『認証の課題とID連携の実装
?ハンズオン?』
概要:
FIDO、ID連携(OAuth?OpenID Connect)をはじめとした最近の技術をご紹介します。FIDOは端末とサーバー間でユーザー認証を安全に連携するための仕組みです。OpenID Connectはユーザーの認証と認可を連携するためのID連携の仕組みで、OAuth 2.0を拡張した仕様であり、HTTP通信やJSONなど基礎的なWeb技術によって構成されています。FIDOとID連携の技術を学んだ後、実習ではGolangを用いてWebアプリケーション上にOpenID Connectを実装します。実装の注意点とそのリスク、仕様に施されているセキュリティー対策についてハンズオンを行いながら解説します。
セキュリティ?キャンプ全国大会2019 専門講義 選択コース B4 認証の課題とID連携の実装 ?ハンズオン? Aug 15, 2019
URL:https://www.ipa.go.jp/jinzai/camp/2019/zenkoku2019_program_list.html#list_d3-b4IDA,VC,DID関連仕様 最新情報 - OpenID BizDay #15
IDA,VC,DID関連仕様 最新情報 - OpenID BizDay #15OpenID Foundation Japan
?
OpenID BizDay #15 講演資料
IDA,VC,DID関連仕様 最新情報これからのネイティブアプリにおけるOpenID Connectの活用
これからのネイティブアプリにおけるOpenID Connectの活用Masaru Kurahayashi
?
タイトル:
『これからのネイティブアプリにおけるOpenID Connectの活用』
概要:
近年モバイルアプリケーションの多くはログインを必須としています。自社他社提供のWeb APIの利用にあたりクライアントサイド、サーバーサイドのそれぞれにおいて認証の仕組みを理解し、正しい認証の実装が求められます。
本セッションではユーザーとデバイスの2つの視点でモバイルにおける認証をご紹介します。
ユーザー認証のパートでは、OAuth 2.0ベースのID連携の問題点に触れ、その課題を解決するためのOpenID Connectの仕様について解説します。
デバイス認証のパートでは、スマートフォンやタブレットを識別するための仕様の解説と活用方法について解説します。
Developers Summit 2014 【13-C-5】 Feb. 13, 2014
URL: https://event.shoeisha.jp/devsumi/20140213/session/383/OpenID Connect のビジネスチャンス
OpenID Connect のビジネスチャンスOpenID Foundation Japan
?
http://nosurrender.jp/idit2013/program.html#TE03
クラウドの普及とともにID連携技術が益々重要性を増してきました。OpenID Connectの技術解説とともにエンタープライズIT市場におけるビジネス展開の方法について説明します。
講師:
一般社団法人 OpenIDファウンデーション?ジャパン
山中進吾
工藤達雄OpenID Connect入門
OpenID Connect入門土岐 孝平
?
OpenID Connectの概要と合わせて、ある程度データのやり取りを具体的に押さえたいという方を対象とした資料です。本資料をベースにして書籍を出版しました。https://www.amazon.co.jp/dp/B08SCCDLJH20231109_OpenID_TechNight_OpenID_Federation.pdf
20231109_OpenID_TechNight_OpenID_Federation.pdfOpenID Foundation Japan
?
「OpenID Federation」
OpenID TechNight vol.20 ~ 分散型 ID 技術勉強会 ~ 2023/11/09(木)
今なら間に合う分散型IDとEntra Verified ID
今なら間に合う分散型IDとEntra Verified IDNaohiro Fujie
?
6/30のOffice365勉強会のEntra Verified ID特集の資料です。
分散型ID、Entra Verified IDの解説をしています。プロトコルから见る滨顿连携
プロトコルから见る滨顿连携Naohiro Fujie
?
CLR/H Tokyo 2014/11/29資料
ID連携プロトコル(ws-federation/SAML2.0/OpenID Connect)の解説Azure ADと外部アプリのID連携/SSO - Deep Dive
Azure ADと外部アプリのID連携/SSO - Deep DiveNaohiro Fujie
?
2016年3月18日に開催された「Active Directory & Security Conference 2016」で使用したスライド。
SAML/OpenID ConnectのアプリケーションとAzure ADのSSO設定について解説します。碍别测肠濒辞补办入门
碍别测肠濒辞补办入门Hiroyuki Wada
?
OSSセキュリティ技術の会 第三回勉強会
碍别测肠濒辞补办入门
https://secureoss-sig.connpass.com/event/90917/
Azure ADアプリケーションを使用した認証のあれやこれ
Azure ADアプリケーションを使用した認証のあれやこれDevTakas
?
Microsoft365 Virtual Marathonの発表で使用したスライドです
Demo: https://github.com/Takas0522/m365-vm-2021-demosブロックチェーンを用いた自己主権型デジタル滨顿管理
ブロックチェーンを用いた自己主権型デジタル滨顿管理LFDT Tokyo Meetup
?
講演者 : 日立製作所 池川航史氏
2023年7月26日開催 WebX - Hyperledger Workshopで講演IoT キットハンズオンのソースコード解説します クラウド編 Part1 Section3
IoT キットハンズオンのソースコード解説します クラウド編 Part1 Section3Yoshitaka Seo
?
Techfair 2016年7月 (2016年7月30日開催) セッション資料
Docs.com サービス停止のため、資料を引っ越しました。
狠狠撸share 公開時点では古い内容ですが、記録?参考として公開します。More Related Content
What's hot (20)
IDA,VC,DID関連仕様 最新情報 - OpenID BizDay #15
IDA,VC,DID関連仕様 最新情報 - OpenID BizDay #15OpenID Foundation Japan
?
OpenID BizDay #15 講演資料
IDA,VC,DID関連仕様 最新情報これからのネイティブアプリにおけるOpenID Connectの活用
これからのネイティブアプリにおけるOpenID Connectの活用Masaru Kurahayashi
?
タイトル:
『これからのネイティブアプリにおけるOpenID Connectの活用』
概要:
近年モバイルアプリケーションの多くはログインを必須としています。自社他社提供のWeb APIの利用にあたりクライアントサイド、サーバーサイドのそれぞれにおいて認証の仕組みを理解し、正しい認証の実装が求められます。
本セッションではユーザーとデバイスの2つの視点でモバイルにおける認証をご紹介します。
ユーザー認証のパートでは、OAuth 2.0ベースのID連携の問題点に触れ、その課題を解決するためのOpenID Connectの仕様について解説します。
デバイス認証のパートでは、スマートフォンやタブレットを識別するための仕様の解説と活用方法について解説します。
Developers Summit 2014 【13-C-5】 Feb. 13, 2014
URL: https://event.shoeisha.jp/devsumi/20140213/session/383/OpenID Connect のビジネスチャンス
OpenID Connect のビジネスチャンスOpenID Foundation Japan
?
http://nosurrender.jp/idit2013/program.html#TE03
クラウドの普及とともにID連携技術が益々重要性を増してきました。OpenID Connectの技術解説とともにエンタープライズIT市場におけるビジネス展開の方法について説明します。
講師:
一般社団法人 OpenIDファウンデーション?ジャパン
山中進吾
工藤達雄OpenID Connect入門
OpenID Connect入門土岐 孝平
?
OpenID Connectの概要と合わせて、ある程度データのやり取りを具体的に押さえたいという方を対象とした資料です。本資料をベースにして書籍を出版しました。https://www.amazon.co.jp/dp/B08SCCDLJH20231109_OpenID_TechNight_OpenID_Federation.pdf
20231109_OpenID_TechNight_OpenID_Federation.pdfOpenID Foundation Japan
?
「OpenID Federation」
OpenID TechNight vol.20 ~ 分散型 ID 技術勉強会 ~ 2023/11/09(木)
今なら間に合う分散型IDとEntra Verified ID
今なら間に合う分散型IDとEntra Verified IDNaohiro Fujie
?
6/30のOffice365勉強会のEntra Verified ID特集の資料です。
分散型ID、Entra Verified IDの解説をしています。プロトコルから见る滨顿连携
プロトコルから见る滨顿连携Naohiro Fujie
?
CLR/H Tokyo 2014/11/29資料
ID連携プロトコル(ws-federation/SAML2.0/OpenID Connect)の解説Azure ADと外部アプリのID連携/SSO - Deep Dive
Azure ADと外部アプリのID連携/SSO - Deep DiveNaohiro Fujie
?
2016年3月18日に開催された「Active Directory & Security Conference 2016」で使用したスライド。
SAML/OpenID ConnectのアプリケーションとAzure ADのSSO設定について解説します。碍别测肠濒辞补办入门
碍别测肠濒辞补办入门Hiroyuki Wada
?
OSSセキュリティ技術の会 第三回勉強会
碍别测肠濒辞补办入门
https://secureoss-sig.connpass.com/event/90917/
Azure ADアプリケーションを使用した認証のあれやこれ
Azure ADアプリケーションを使用した認証のあれやこれDevTakas
?
Microsoft365 Virtual Marathonの発表で使用したスライドです
Demo: https://github.com/Takas0522/m365-vm-2021-demosブロックチェーンを用いた自己主権型デジタル滨顿管理
ブロックチェーンを用いた自己主権型デジタル滨顿管理LFDT Tokyo Meetup
?
講演者 : 日立製作所 池川航史氏
2023年7月26日開催 WebX - Hyperledger Workshopで講演Similar to 池澤あやかと学ぼう!: はじめてのOAuthとOpenID Connect - JICS 2014 (18)
IoT キットハンズオンのソースコード解説します クラウド編 Part1 Section3
IoT キットハンズオンのソースコード解説します クラウド編 Part1 Section3Yoshitaka Seo
?
Techfair 2016年7月 (2016年7月30日開催) セッション資料
Docs.com サービス停止のため、資料を引っ越しました。
狠狠撸share 公開時点では古い内容ですが、記録?参考として公開します。IoT キットハンズオンのソースコード解説します クラウド編 Part1 Section2
IoT キットハンズオンのソースコード解説します クラウド編 Part1 Section2Yoshitaka Seo
?
Techfair 2016年7月 (2016年7月30日開催) セッション資料
Docs.com サービス停止のため、資料を引っ越しました。
狠狠撸share 公開時点では古い内容ですが、記録?参考として公開します。OAuth 2.0による認可の流れ
OAuth 2.0による認可の流れTakeshi Mikami
?
テーマ: OAuth 2.0による認可の流れ
内容:
- OAuth 2.0とは
- 認証と認可
- OAuth 2.0で考えるロール
- OAuth 2.0による認可フローSIerは如何にしてGitHub Enterpriseを導入するにようになったか
SIerは如何にしてGitHub Enterpriseを導入するにようになったかYou_Kinjoh
?
Developers Summit 2016
セッション
『【19-C-2】【ユーザ企業が語る!】チーム開発をサポートし、生産性や品質の向上を実現するソフトウェア開発環境とは?』
事例発表
『SIerは如何にしてGitHub Enterpriseを導入するにようになったか』
http://event.shoeisha.jp/devsumi/20160218/
http://event.shoeisha.jp/devsumi/20160218/session/1037/
LUIS x Azure Bot Service
LUIS x Azure Bot ServiceKazumi OHIRA
?
※ Docs.com 終了に伴い移行。2016/11/22 の投稿です。
----
第2回 Cogbot勉強会!~ Cognitive Servicesで自然言語処理 (https://cogbot.connpass.com/event/43615/) のハンズオン資料です。
Azure Bot Service で Cognitive Services の LUIS を使ってみるハンズオンです。ハードウェアこわい - HTML5オールスタース?
ハードウェアこわい - HTML5オールスタース?Wakasa Masao
?
奥别产エンジニアがこのスライドをみるとハードウェアがこわくなるものです。こわいものなので作者にハードウェアを送らないようにしてください。こわいので。Ad
More from Nov Matake (20)
#idcon vol.29 - #fidcon WebAuthn, Next Stage
#idcon vol.29 - #fidcon WebAuthn, Next StageNov Matake
?
Nov Matake gave a keynote presentation at FIDCon about the next stage of WebAuthn and Passkeys on Apple platforms. He demonstrated syncing Passkeys across devices and using them for autofill on websites. Some challenges remain around credential changes and re-authentication. Syncing Passkeys across different operating systems like Windows, Android, and ChromeOS will also need to be addressed to make the experience better for users.FedCM - OpenID TechNight vol.19
FedCM - OpenID TechNight vol.19Nov Matake
?
The document discusses authentication for browser-based and native apps using app-specific, IDP, and third-party backend APIs. It asks questions about obtaining and storing tokens for each API and passing tokens. Answers recommend using OAuth 2.0 for tokens, storing them in keychain/backend server, and passing as bearer tokens. Best practices are proposed like using a mediator flow and letting IDPs handle user interactions.Safari (ITP) & Chrome (SameSite=Lax as default) が Federation に与える影響 - OpenID ...
Safari (ITP) & Chrome (SameSite=Lax as default) が Federation に与える影響 - OpenID ...Nov Matake
?
OpenID TechNight vol.17 での発表スライドです。
https://openid.connpass.com/event/183577/
録画はこちら。
https://www.youtube.com/watch?v=0856pHMoTDsSign in with Apple
Sign in with Apple Nov Matake
?
This document summarizes differences between Sign in with Apple (SIWA) and OpenID Connect (OIDC) and OAuth 2.0 standards. It notes several ways SIWA specifications and behaviors deviate from or violate OIDC standards, including not supporting standard authentication methods, response types, and claims. It also describes SIWA's characteristic identifier design which links multiple apps and services from the same developer together under a single user consent. Developer teams are limited to 10 linked apps/services and must create a new team for additional apps.FIDO @ LINE - #idcon vol.24
FIDO @ LINE - #idcon vol.24Nov Matake
?
This document discusses LINE Corporation's LINE FIDO authentication solution and compares FIDO U2F, FIDO2, and FIDO UAF standards. It outlines the key components of each standard including message formats, protocol specifications, assertion data, and how they ensure interoperability across authenticators. It also mentions potential applications of LINE FIDO in areas like finance and IoT, as well as features like enrollment to address device loss.W3C Web Authentication - #idcon vol.24
W3C Web Authentication - #idcon vol.24Nov Matake
?
The document discusses the W3C Web Authentication standard (also known as FIDO 2.0) for passwordless strong authentication on the web. It provides an overview of the key components and actors in the standard like FIDO authenticators, user agents, relying parties. It then summarizes the basic flows of registration and authentication in 2 phases. During registration, a key pair is generated on the authenticator and the public key is registered with the FIDO server. During authentication, the authenticator performs local authentication using the registered key and sends an assertion to the server for remote authentication.NIST SP 800-63C - Federation and Assertions (FINAL)
NIST SP 800-63C - Federation and Assertions (FINAL)Nov Matake
?
OIDF-J?JIPDEC共催OpenID BizDay#11「NIST SP 800-63-3を読む」
https://www.jipdec.or.jp/topics/event/20171013.htmlOPTiM StoreにおけるSCIM & OIDC活用事例 - ID&IT 2016
OPTiM StoreにおけるSCIM & OIDC活用事例 - ID&IT 2016Nov Matake
?
This document discusses the OPTiM Store, which uses SCIM and OpenID Connect (OIDC) for provisioning and federation between systems like Active Directory and SaaS applications. It outlines the processes for tenant contracting, client registration, and credential exchange to enable synchronization of user identities and attributes from a SaaS application to the OPTiM Store using SCIM, and authentication from the store to SaaS using OIDC single sign-on.NIST SP 800-63C #idcon vol.22
NIST SP 800-63C #idcon vol.22Nov Matake
?
The document discusses standards for identity federation and assertions. It defines four levels of federation assurance (FAL) based on the type of assertion used and how it is presented. FAL1 uses front-channel or back-channel bearer assertions signed by the identity provider. FAL2 adds encryption of assertions to the relying party. FAL3 encrypts assertions to the relying party for both front and back-channel. FAL4 uses holder-of-key assertions, where the assertion contains a public key and proof of possession, signed and encrypted to the relying party. The document provides definitions and discusses security considerations for federation and assertions.NIST SP 800-63-3 #idcon vol.22
NIST SP 800-63-3 #idcon vol.22Nov Matake
?
SP 800-63-3 is an update to NIST's digital identity guidelines. It introduces a new framework that separates assurance levels into three components: Identity Assurance Level (IAL), Authenticator Assurance Level (AAL), and Federation Assurance Level (FAL). This provides more flexibility and granularity over the previous version's single Level of Assurance (LOA). The document outlines the recommended requirements and mappings between the new IAL, AAL, FAL framework and the legacy LOA model from SP 800-63-2.ID連携入門 (実習編) - Security Camp 2016
ID連携入門 (実習編) - Security Camp 2016Nov Matake
?
The document discusses OAuth and OpenID Connect protocols. It provides diagrams illustrating the flows of OAuth authorization code grant, implicit grant and hybrid grant flows. It also compares OAuth and OpenID Connect, noting that OpenID Connect builds upon OAuth by adding an identity layer. Key aspects of OpenID Connect like ID tokens and their claims are outlined. Examples of OAuth and OpenID Connect implementations are provided at the end.ID連携概要 - OpenID TechNight vol.13
ID連携概要 - OpenID TechNight vol.13Nov Matake
?
This document contains information about Nov Matake, including that he is a security engineer at GREE Inc. and evangelist for the OpenID Foundation. It discusses concepts related to digital identity including entity, identity, authentication, authorization, access control, and identity proofing. It also compares identity providers and relying parties in the context of single sign-on using services like Facebook and Disqus.FIDO alliance #idcon vol.18
FIDO alliance #idcon vol.18Nov Matake
?
The document discusses the FIDO Alliance and its specifications for passwordless and two-factor authentication. It describes the FIDO Alliance's role in defining specifications, issuing vendor codes, and operating a certification program called FIDO Ready. The specifications cover areas like registration, authentication, and key generation in interactions between users' devices, authenticators, clients, and relying parties.OpenID Connect 101 @ OpenID TechNight vol.11
OpenID Connect 101 @ OpenID TechNight vol.11Nov Matake
?
The document is a presentation on OpenID Connect 101 by Nov Matake of OpenID Foundation Japan. It provides an overview of OpenID Connect, including how it uses OAuth 2.0 with an added identity layer, the code flow process, ID tokens and their contents, scopes, discovery, and dynamic client registration. It also discusses password leaks, two-factor authentication, and security best practices.MIT-KIT Intro at #idcon sattelite
MIT-KIT Intro at #idcon satteliteNov Matake
?
The document provides an overview of the MIT Kerberos & Internet Trust Consortium (MIT-KIT). It discusses the history and success of Kerberos authentication. The mission of MIT-KIT has expanded to address broader issues in identity, authorization, and privacy on the internet. It envisions an emerging personal data ecosystem where individuals control their own data. MIT-KIT is working on various open source components and standards to help realize this vision, including projects around OpenPDS and implementing the NSTIC Identity Ecosystem Steering Group framework.Self isssued-idp
Self isssued-idpNov Matake
?
This document discusses a self-issued open ID provider that allows identity in devices without central identity provider servers. It generates ID tokens on the device using a self-signed key pair stored securely on the device. The subject ("sub") claim in the ID token is calculated from the public key. This allows each device to have a unique ID token tied to the key pair, with no need for client registration or API access tokens.Ad
池澤あやかと学ぼう!: はじめてのOAuthとOpenID Connect - JICS 2014
- 5. 2010年8月31日 Twitter API Basic 認証廃止 OAuth 1.0 へ完全移行
- 6. パスワード漏洩例
- 19. ? OpenID Connect OAuth 2.0 + Identity Layer
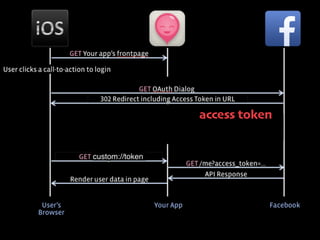
- 23. [3号]! ここまでをフロー図にすると、実はさっきの OAuth のフローとほとんど さっきの図を元に差分だけ見てみると、access token と同時に ID Toke
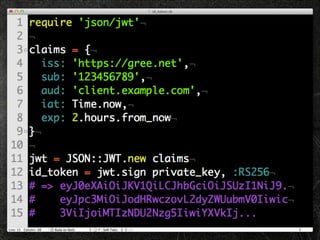
- 24. ID Token 認証イベントのアサーション (JSON Web Token) iss – Issuer sub – Subject, End-user Identi?er aud – Audience, Client ID iat - issued at exp - expiry
- 26. Implicit = 暗黙の
- 28. access token
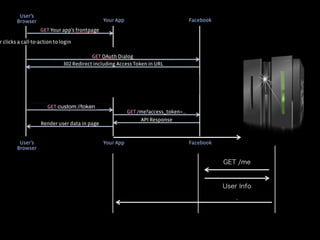
- 31. Weak Point GET /me User Info :
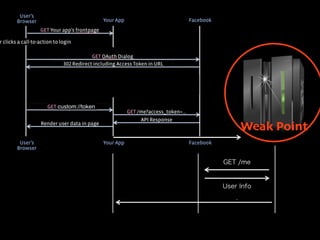
- 32. Weak Point Token Replace GET /me User Info :
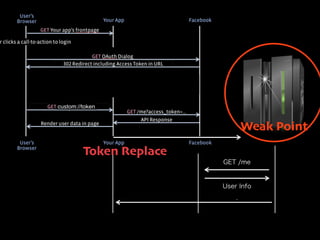
- 33. Weak Point Token Replace GET /me Di?erent User Data User Info :
- 35. ID Token
- 36. ID Token
- 38. ID Token 認証イベントのアサーション (JSON Web Token) iss – Issuer sub – Subject, End-user Identi?er aud – Audience, Client ID iat - issued at exp - expiry
- 39. 誰が (issuer = IdP) 誰を (subject = end-user) 誰のために (audience = client) 認証したのか
- 42. 会員組織 ?入会メリット デジタル?アイデンティティ業界をリードする企業?組織が多数参加する OIDF-Jコミュニティの?一員となることにより、新たなビジネス機会が広がります。 ● ワーキンググループを通じた、業界イニシアティブへの参画。 企業や業界を超えた標準仕様の作成や、ビジネスモデルの創出に関する検討。 ● IDを軸とする会員企業間のコラボレーション。 ● 技術者コミュニティや会員企業間の情報交換を通じた、いち早いOpenID関連の技術情報、ビジネストレンド情報の?入?手。 ● 会員企業限定のセミナー、交流流会(ネットワーキング)、フォーラムへの参加。 ?入会?金金 20万円 年年会費 10万円 お問い合わせは事務局まで 03-6274-1451 contact@openid.or.jp *会員規約は別紙参照 *?入会は法?人もしくは団体(部署単位での?一社複数?入会等は可能) *?入会はお申込書の提出が必要 Copyright ? 2013 OpenID Foundation Japan. All Rights Reserved. 6
