Bug Bounty - Play For Money
- 1. { Bug Bounty Play for Money
- 2. #Whoami
- 3. Shubham Gupta (@hackerspider1) Just another random lazy guy interested in security Security Consultant at Pyramid Cyber Security & Forensic Bug Bounty Hunter {Just do when I need money BCA Graduate {Doesnât Matter Penetration tester
- 4. Lucky Enough
- 7. ï Introduction ï History ï Why bug hunting? ï How to do bug hunting? ï Quick Tips ï POC ï Pros and Cons of bug hunting. ï Q&A Agenda
- 8. What is #Bug Bounty âĒ Also calls as VRP (Vulnerability Reward Program) âĒ Company (Security Team/Vendor) Create Program. Offer Cash , HOF , Swag. Acknowledge Your Work. âĒ Researchers / Bug Hunter Hit Target and Get Bugs. Sometimes Duplicates , Sometime $$$ , Sometime Swag. Recheck Bug After Fix.
- 9. A Brief History of Bug Bounty Programs. - 1995 (Net Scape) - 2004 (FIREFOX) - 2005 - 2007 - 2010 - 2011 - 2012 - 2013 -2013 (Cobalt) - 2013 (Synac k)
- 10. Why bug hunting? ï Chances of finding bugs to put on your cv. ï Possibility of getting job. ï lots of money in very less time ï Cool T-shirts, Hoodies, Mugs and many more swags ï Recognition ï Connections ï Less security breaches ï Enjoyment ï Person will Learn to work hard because of Competition
- 11. Bug Bounty Programs And Platforms âĒ Popular Programs - Google (Min 100$ & Max 20000$) - Yahoo (Min 50$ & Max 15000$) - Facebook Min 500$ - Want to know More ïķ Github ïķ Twitter ïķ Microsoft
- 13. Popular Platform BugCrowd Managed Security Program for Company 27125 World Wide Researcher 200+ Programs HackerOne Security Inbox for Company 133+ Public Program 6.91M Paid Synack Everyone Want To Join Cobalt
- 14. How to kickoff for hunting bugs?
- 15. How to do bug hunting? ï Bug hunting is all about Exploring Weaknesses and Experimentation. ï It requires 30% programming knowledge and 70% logical out of box thinking. ï Try each and every Combination to exploit bug . ï Dig dipper. ï Try more to find logical bugs it will increase your chance for higher payouts and reduce chances for Duplicates.
- 16. Quick Tips
- 17. How to Write Report? Title Issue Information Step by step instruction to reproduce the bug Impact Mitigation
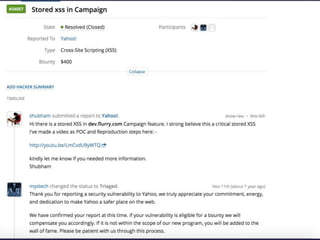
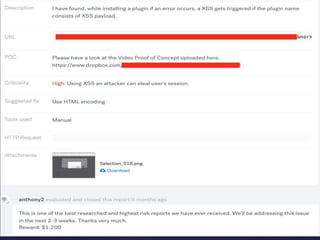
- 18. POC
- 20. Video Demo
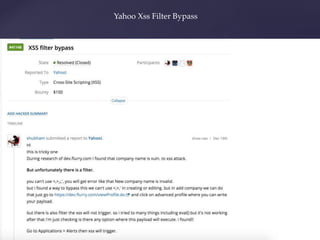
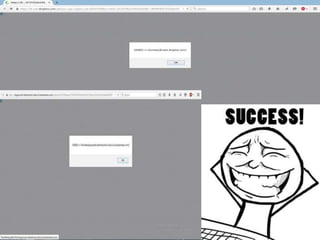
- 21. Yahoo Xss Filter Bypass
- 22. SVG XSS ï One of the most unique bug of 2015 and easy to find. ï Most of the web based projects include svg for a clear and interactive user experience. ï To verify this answer I created an svg file with an XSS vector below and started testing the websites that allow images .
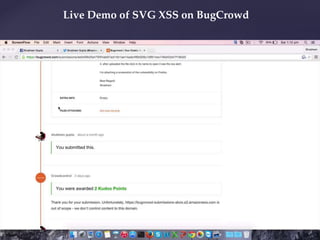
- 24. Live Demo of SVG XSS on BugCrowd
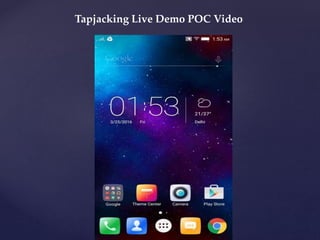
- 25. Tapjacking Live Demo POC Video
Editor's Notes
- #2: Before I start giving my presentation I just want to know how many of you are familiar with bug bo unty
- #3: So ladies and gentleman Iâm going to present the bug bounty play for money
- #5: Iâm lucky enough to find vuln. In google, yahoo, twitter actually there are so many company I donât remember all of the name u can find all of them.
- #9: Lets start with what is bug bounty? Bug bounty is also called as VRP vuln. Reward program bassically there are two section in bug bounty Company and researcher in professional we
- #23: the page will render the content of the xml as html , so resulting on a xss vulnerability.
- #24: 23
- #26: UI Redressing (Tap jacking) attack may trick users into tapping a specifically crafted malicious App popup window (e.g. toast view), making it a gateway for varied threats such as framing attack. Using this technique, a malicious App could potentially trick a user into making purchases, clicking on ads, installing Apps, or even wiping all of the data from the phone.