Ccna1 presentation
- 1. 1
- 3. Network Topologies 3 Network topology defines the structure of the network. One part of the topology definition is the physical topology, which is the actual layout of the wire or media. The other part is the logical topology,which defines how the media is accessed by the hosts for sending data.
- 5. 5 One early solution was the creation of local-area network (LAN) standards which provided an open set of guidelines for creating network hardware and software, making equipment from different companies compatible. What was needed was a way for information to move efficiently and quickly, not only within a company, but also from one business to another. The solution was the creation of metropolitan-area networks (MANs) and wide-area networks (WANs).
- 6. OSI Model 6 To address the problem of networks increasing in size and in number, the International Organization for Standardization (ISO) researched many network schemes and recognized that there was a need to create a network model that would help network builders implement networks that could communicate and work together and therefore, released the OSI reference model in 1984.
- 7. The OSI Reference Model 7 7 Application 6 Presentation 5 Session 4 Transport 3 Network 2 Data Link 1 Physical
- 8. 8
- 9. Network and Host Addressing 9 Using the IP address of the destination network, a router can deliver a packet to the correct network. When the packet arrives at a router connected to the destination network, the router uses the IP address to locate the particular computer connected to that network. Accordingly, every IP address has two parts.
- 10. IP Address Classes 10 IP addresses are divided into classes to define the large, medium, and small networks. Class A addresses are assigned to larger networks. Class B addresses are used for medium-sized networks, Class C for small networks. Class D for multicasting Class E for research& development centre
- 11. Introduction to Subnetting 11 Subnetting a network means to use the subnet mask to divide the network and break a large network up into smaller, more efficient and manageable segments, or subnets. With subnetting, the network is not limited to the default Class A, B, or C network masks and there is more flexibility in the network design. Subnet addresses include the network portion, plus a subnet field and a host field.The ability to decide how to divide the original host portion into the new subnet and host fields provides addressing flexibility for the network administrator.
- 12. 12 SIEMENS NIXDORF SIEMENS NIXDORF Host A Host B IP Address: 128.0.10.4 HW Address: 080020021545 ARP Reply ARP Request - Broadcast to all hosts âWhat is the hardware address for IP address 128.0.10.4?â SIEMENS NIXDORF Fig. 32 How does ARP work? (TI1332EU02TI_0004 The Network Layer, 47)
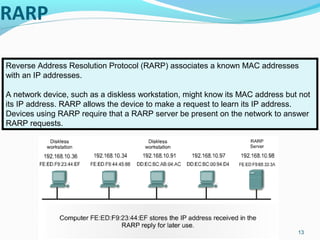
- 13. RARP 13 Reverse Address Resolution Protocol (RARP) associates a known MAC addresses with an IP addresses. A network device, such as a diskless workstation, might know its MAC address but not its IP address. RARP allows the device to make a request to learn its IP address. Devices using RARP require that a RARP server be present on the network to answer RARP requests.
- 14. Introduction to Routers 14 A router is a special type of computer. It has the same basic components as a standard desktop PC. However, routers are designed to perform some very specific functions. Just as computers need operating systems to run software applications, routers need the Internetwork Operating System software (IOS) to run configuration files. These configuration files contain the instructions and parameters that control the flow of traffic in and out of the routers. The many parts of a router are shown below:
- 15. IOS File System Overview 15
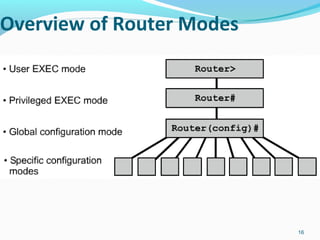
- 16. Overview of Router Modes 16
- 17. Configuring Interfaces 17 An interface needs an IP Address and a Subnet Mask to be configured. All interfaces are âshutdownâ by default. The DCE end of a serial interface needs a clock rate. Router#config t Router(config)#interface serial 0/1 Router(config-if)#ip address 200.100.50.75 255.255.255.240 Router(config-if)#clock rate 56000 (required for serial DCE only) Router(config-if)#no shutdown Router(config-if)#exit Router(config)#int f0/0 Router(config-if)#ip address 150.100.50.25 255.255.255.0 Router(config-if)#no shutdown Router(config-if)#exit Router(config)#exit Router# On older routers, Serial 0/1 would be just Serial 1 and f0/0 would be e0. s = serial e = Ethernet f = fast Ethernet
- 18. Introducing Routing 18 Routing is the process that a router uses to forward packets toward the destination network. A router makes decisions based upon the destination IP address of a packet. All devices along the way use the destination IP address to point the packet in the correct direction so that the packet eventually arrives at its destination. In order to make the correct decisions, routers must learn the direction to remote networks.
- 21. OSPF ïķ (OSPF) Open Shortest Path First. ïķ It is open standard pure link state routing protocol. ïķ It support different vendors. Its maximum hope count is unlimited. Its default AD value is 110. ïķ It support auto summarization. It is a class less routing protocol. ïķ It support Discontiguous, VLSM/CIDR & class less IP addressing . It also support AS no. ïķ It create three separate table for sharing information. ï 1. Neighbor ship table ï 2. Topology table
- 22. OSPF 22
- 24. EIGRP 24 Enhanced Interior Gateway Routing Protocol (EIGRP) is a Cisco- proprietary routing protocol based on Interior Gateway Routing Protocol (IGRP). Unlike IGRP, which is a classful routing protocol, EIGRP supports CIDR and VLSM. Compared to IGRP, EIGRP boasts faster convergence times, improved scalability, and superior handling of routing loops. Furthermore, EIGRP can replace Novell Routing Information Protocol (RIP) and AppleTalk Routing Table Maintenance Protocol (RTMP), serving both IPX and AppleTalk networks with powerful efficiency. EIGRP is often described as a hybrid routing protocol, offering the best of distance vector and link-state algorithms.
- 25. VLANs 25 VLAN implementation combines Layer 2 switching and Layer 3 routing technologies to limit both collision domains and broadcast domains. VLANs can also be used to provide security by creating the VLAN groups according to function and by using routers to communicate between VLANs. A physical port association is used to implement VLAN assignment. Communication between VLANs can occur only through the router. This limits the size of the broadcast domains and uses the router to determine whether one VLAN can talk to another VLAN. This is the only way a switch can break up a broadcast domain!
- 26. Setting up VLAN Implementation 26
- 28. Data Flow Diagram ïZero Level DFD 28
- 29. Data Flow Diagram ïOne Level DFD 29
- 30. ER Diagram 30
- 31. THE END 31