Ce hv7 module 18 cryptography
0 likes451 views
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications for training including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It appears to be advertising training and certification courses available at the two listed websites.
1 of 49
Downloaded 106 times



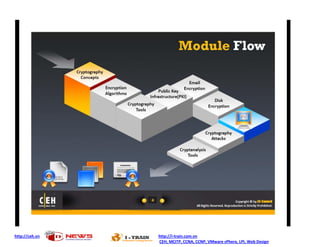

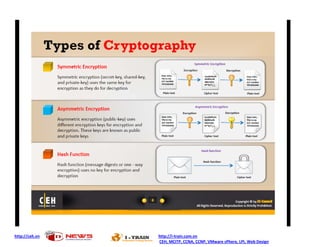

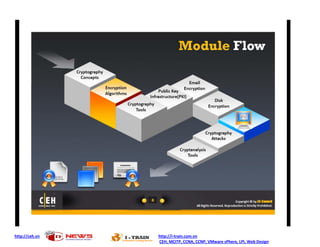



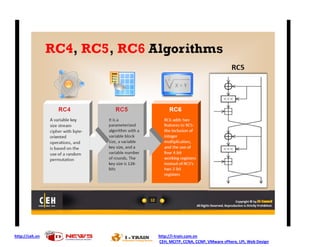





















Ad
Recommended
Ce hv7 module 17 buffer overflow
Ce hv7 module 17 buffer overflowMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn on each line, suggesting these websites provide information on or training for the listed certification courses.Ce hv7 module 11 session hijacking
Ce hv7 module 11 session hijackingFco Javier SantaMar├Ła
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications for training including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design.Part04 basic cryptography
Part04 basic cryptographyLê Liêu
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications for training including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design.Ce hv7 module 12 hacking webservers
Ce hv7 module 12 hacking webserversFco Javier SantaMar├Ła
╠²
The document repeatedly lists two website URLs and several IT certification abbreviations. It appears to be advertising IT training and certification courses available at the websites listed.Ce hv7 module 19 penetration testing
Ce hv7 module 19 penetration testingMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications such as CEH, MCITP, CCNA, CCNP, VMware sPhere and LPI. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn on each line.Ce hv7 module 01 introduction to ethical hacking
Ce hv7 module 01 introduction to ethical hackingFco Javier SantaMar├Ła
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications for training including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design.Ce hv7 module 09 social engineering
Ce hv7 module 09 social engineeringFco Javier SantaMar├Ła
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications for training including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design.Ce hv7 module 07 viruses and worms
Ce hv7 module 07 viruses and wormsFco Javier SantaMar├Ła
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications for training (CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design).Ce hv7 module 09 social engineering
Ce hv7 module 09 social engineeringMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications such as CEH, MCITP, CCNA, CCNP, and VMware, as well as URLs for the websites ceh.vn and i-train.com.vn. It appears to be advertising or promoting IT training and certification courses.Ce hv8 module 13 hacking web applications
Ce hv8 module 13 hacking web applications Mehrdad Jingoism
╠²
The document discusses hacking web applications and is divided into several sections. It begins with concepts of web applications, then covers web application threats. Next it describes the methodology for hacking web applications and the tools used. It then discusses countermeasures, security tools, and concludes with web application penetration testing. The overall objective is to highlight vulnerabilities in web applications and the attacks that exploit them, as well as methods for defense.Ce hv7 module 15 hacking wireless networks
Ce hv7 module 15 hacking wireless networksMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn.Ce hv7 module 06 trojans and backdoors
Ce hv7 module 06 trojans and backdoorsMehrdad Jingoism
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications/training areas including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It appears to be advertising training and certification courses available at the two listed websites across various IT domains.Ce hv7 module 08 sniffers
Ce hv7 module 08 sniffersMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn on each line, suggesting these websites provide information on or training for the listed certification courses.Ce hv7 module 07 viruses and worms
Ce hv7 module 07 viruses and wormsMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications such as CEH, MCITP, CCNA, CCNP, and VMware, as well as URLs for the websites ceh.vn and i-train.com.vn. It appears to be advertising or promoting certification training programs.Ce hv7 module 04 enumeration
Ce hv7 module 04 enumerationMehrdad Jingoism
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications/training areas including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design, but provides no other context or information.Ce hv7 module 13 hacking web applications
Ce hv7 module 13 hacking web applicationsMehrdad Jingoism
╠²
The document repeatedly lists training courses including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs http://ceh.vn and http://i-train.com.vn on each line, suggesting it is advertising an IT training website that offers various certification courses.Cehv8 module 01 introduction to ethical hacking
Cehv8 module 01 introduction to ethical hackingMehrdad Jingoism
╠²
This module introduces ethical hacking and penetration testing. It discusses how ethical hackers play an important role in assessing network security vulnerabilities to help organizations strengthen their defenses against real attackers. The module covers key topics like hacking phases, essential security terminology, types of attacks, elements of information security, why ethical hacking is necessary, top attack vectors, skills of an ethical hacker, and the difference between hacking and ethical hacking. It aims to help students understand security concepts and the role of ethical hackers in enhancing security.Ce hv7 module 16 evading ids, firewalls, and honeypots
Ce hv7 module 16 evading ids, firewalls, and honeypotsMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications such as CEH, MCITP, CCNA, CCNP, VMware sPhere, and LPI. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn.Ce hv7 module 11 session hijacking
Ce hv7 module 11 session hijackingMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn on each line, suggesting these websites provide information on or training for the listed certification courses.Ce hv7 module 12 hacking webservers
Ce hv7 module 12 hacking webserversMehrdad Jingoism
╠²
The document repeatedly lists URLs and certifications for information technology training. It provides the websites http://ceh.vn and http://i-train.com.vn and lists certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. The document appears to be advertising IT training and certification programs.Ce hv7 module 14 sql injection
Ce hv7 module 14 sql injectionMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications such as CEH, MCITP, CCNA, CCNP, VMware sPhere and LPI. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn.Ce hv7 module 10 denial of service
Ce hv7 module 10 denial of serviceMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere and LPI. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn which likely provide information on or registration for the listed certification training courses.Ethical hacking presentation
Ethical hacking presentationSuryansh Srivastava
╠²
This document provides an overview of security and hacking. It defines security as protection from harm and defines differences between security and protection. It then discusses what hacking and hackers are, provides a brief history of hacking from the 1960s to present day, and describes different types of hackers like white hat and black hat hackers. The document also outlines the hacking process and some common tools used. It lists some famous hackers and recent news stories about hacking.Ce hv7 module 03 scanning networks
Ce hv7 module 03 scanning networksZuleima Parada
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications for training (CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design).Ce hv7 module 05 system hacking
Ce hv7 module 05 system hackingZuleima Parada
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications for training (CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design).1
1omid503
╠²
The document lists two website URLs - http://ceh.vn and http://i-train.com.vn - and certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design.Ceh v7 module 05
Ceh v7 module 05Prashant Kumar Gupta
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn.Cehv7module03scanningnetworks 131208152747-phpapp02
Cehv7module03scanningnetworks 131208152747-phpapp02Ayhan Gasanly
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn.Ce hv7 module 03 scanning networks
Ce hv7 module 03 scanning networksMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn.Ce hv7 module 05 system hacking
Ce hv7 module 05 system hackingMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn.More Related Content
Viewers also liked (15)
Ce hv7 module 09 social engineering
Ce hv7 module 09 social engineeringMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications such as CEH, MCITP, CCNA, CCNP, and VMware, as well as URLs for the websites ceh.vn and i-train.com.vn. It appears to be advertising or promoting IT training and certification courses.Ce hv8 module 13 hacking web applications
Ce hv8 module 13 hacking web applications Mehrdad Jingoism
╠²
The document discusses hacking web applications and is divided into several sections. It begins with concepts of web applications, then covers web application threats. Next it describes the methodology for hacking web applications and the tools used. It then discusses countermeasures, security tools, and concludes with web application penetration testing. The overall objective is to highlight vulnerabilities in web applications and the attacks that exploit them, as well as methods for defense.Ce hv7 module 15 hacking wireless networks
Ce hv7 module 15 hacking wireless networksMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn.Ce hv7 module 06 trojans and backdoors
Ce hv7 module 06 trojans and backdoorsMehrdad Jingoism
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications/training areas including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It appears to be advertising training and certification courses available at the two listed websites across various IT domains.Ce hv7 module 08 sniffers
Ce hv7 module 08 sniffersMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn on each line, suggesting these websites provide information on or training for the listed certification courses.Ce hv7 module 07 viruses and worms
Ce hv7 module 07 viruses and wormsMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications such as CEH, MCITP, CCNA, CCNP, and VMware, as well as URLs for the websites ceh.vn and i-train.com.vn. It appears to be advertising or promoting certification training programs.Ce hv7 module 04 enumeration
Ce hv7 module 04 enumerationMehrdad Jingoism
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications/training areas including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design, but provides no other context or information.Ce hv7 module 13 hacking web applications
Ce hv7 module 13 hacking web applicationsMehrdad Jingoism
╠²
The document repeatedly lists training courses including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs http://ceh.vn and http://i-train.com.vn on each line, suggesting it is advertising an IT training website that offers various certification courses.Cehv8 module 01 introduction to ethical hacking
Cehv8 module 01 introduction to ethical hackingMehrdad Jingoism
╠²
This module introduces ethical hacking and penetration testing. It discusses how ethical hackers play an important role in assessing network security vulnerabilities to help organizations strengthen their defenses against real attackers. The module covers key topics like hacking phases, essential security terminology, types of attacks, elements of information security, why ethical hacking is necessary, top attack vectors, skills of an ethical hacker, and the difference between hacking and ethical hacking. It aims to help students understand security concepts and the role of ethical hackers in enhancing security.Ce hv7 module 16 evading ids, firewalls, and honeypots
Ce hv7 module 16 evading ids, firewalls, and honeypotsMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications such as CEH, MCITP, CCNA, CCNP, VMware sPhere, and LPI. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn.Ce hv7 module 11 session hijacking
Ce hv7 module 11 session hijackingMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn on each line, suggesting these websites provide information on or training for the listed certification courses.Ce hv7 module 12 hacking webservers
Ce hv7 module 12 hacking webserversMehrdad Jingoism
╠²
The document repeatedly lists URLs and certifications for information technology training. It provides the websites http://ceh.vn and http://i-train.com.vn and lists certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. The document appears to be advertising IT training and certification programs.Ce hv7 module 14 sql injection
Ce hv7 module 14 sql injectionMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications such as CEH, MCITP, CCNA, CCNP, VMware sPhere and LPI. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn.Ce hv7 module 10 denial of service
Ce hv7 module 10 denial of serviceMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere and LPI. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn which likely provide information on or registration for the listed certification training courses.Ethical hacking presentation
Ethical hacking presentationSuryansh Srivastava
╠²
This document provides an overview of security and hacking. It defines security as protection from harm and defines differences between security and protection. It then discusses what hacking and hackers are, provides a brief history of hacking from the 1960s to present day, and describes different types of hackers like white hat and black hat hackers. The document also outlines the hacking process and some common tools used. It lists some famous hackers and recent news stories about hacking.Similar to Ce hv7 module 18 cryptography (20)
Ce hv7 module 03 scanning networks
Ce hv7 module 03 scanning networksZuleima Parada
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications for training (CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design).Ce hv7 module 05 system hacking
Ce hv7 module 05 system hackingZuleima Parada
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications for training (CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design).1
1omid503
╠²
The document lists two website URLs - http://ceh.vn and http://i-train.com.vn - and certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design.Ceh v7 module 05
Ceh v7 module 05Prashant Kumar Gupta
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn.Cehv7module03scanningnetworks 131208152747-phpapp02
Cehv7module03scanningnetworks 131208152747-phpapp02Ayhan Gasanly
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn.Ce hv7 module 03 scanning networks
Ce hv7 module 03 scanning networksMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn.Ce hv7 module 05 system hacking
Ce hv7 module 05 system hackingMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn.Ce hv7 module 01 introduction to ethical hacking
Ce hv7 module 01 introduction to ethical hackingZuleima Parada
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications for training (CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design).Ce hv7 module 03 scanning networks
Ce hv7 module 03 scanning networksFco Javier SantaMar├Ła
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications for training (CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design).Ce hv7 module 06 trojans and backdoors
Ce hv7 module 06 trojans and backdoorsFco Javier SantaMar├Ła
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications for training (CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design).Ce hv7 module 05 system hacking
Ce hv7 module 05 system hackingFco Javier SantaMar├Ła
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications for training (CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design).Ce hv7 module 04 enumeration
Ce hv7 module 04 enumerationFco Javier SantaMar├Ła
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and certifications for training including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design.Ce hv7 module 10 denial of service
Ce hv7 module 10 denial of serviceFco Javier SantaMar├Ła
╠²
The document repeatedly lists two website URLs (http://ceh.vn and http://i-train.com.vn) and several IT certification abbreviations (CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design).Introduction to Ethical Hacking
Introduction to Ethical HackingTiago Monteiro
╠²
The document repeatedly lists training courses for various IT certifications such as CEH, MCITP, CCNA, CCNP, VMware sPhere, and LPI, and provides URLs for the websites ceh.vn and i-train.com.vn.Cehv7module01introductiontoethicalhacking 130224024140-phpapp02
Cehv7module01introductiontoethicalhacking 130224024140-phpapp02Ayhan Gasanly
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn on each line, suggesting these websites provide information on or training for the listed IT certification courses.2 footprinting ve ke┼¤if
2 footprinting ve ke┼¤iffarukdemir47
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn on each line, suggesting these websites provide information on or training for the listed certification courses.introduction to ethical hacking
introduction to ethical hackingMahant Patel
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn on each line, suggesting these websites provide information on or training for the listed IT certification courses.Ce hv7 module 02 footprinting and reconnaissance
Ce hv7 module 02 footprinting and reconnaissanceMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn on each line, suggesting these websites provide information on or training for the listed certification courses.Ce hv7 module 01 introduction to ethical hacking
Ce hv7 module 01 introduction to ethical hackingMehrdad Jingoism
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn on each line, suggesting these websites provide information on or training for the listed IT certification courses.Cehv7module02 2002-20footprinting-20and-20reconnaissance-130717015247-phpapp01
Cehv7module02 2002-20footprinting-20and-20reconnaissance-130717015247-phpapp01Ayhan Gasanly
╠²
The document repeatedly lists training courses for various IT certifications including CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, and Web Design. It also provides URLs for the websites http://ceh.vn and http://i-train.com.vn on each line, suggesting these websites provide information on or training for the listed certification courses.Ad
Recently uploaded (20)
The Future of Technology: 2025-2125 by Saikat Basu.pdf
The Future of Technology: 2025-2125 by Saikat Basu.pdfSaikat Basu
╠²
A peek into the next 100 years of technology. From Generative AI to Global AI networks to Martian Colonisation to Interstellar exploration to Industrial Nanotechnology to Artificial Consciousness, this is a journey you don't want to miss. Which ones excite you the most? Which ones are you apprehensive about? Feel free to comment! Let the conversation begin!Powering Multi-Page Web Applications Using Flow Apps and FME Data Streaming
Powering Multi-Page Web Applications Using Flow Apps and FME Data StreamingSafe Software
╠²
Unleash the potential of FME Flow to build and deploy advanced multi-page web applications with ease. Discover how Flow Apps and FMEŌĆÖs data streaming capabilities empower you to create interactive web experiences directly within FME Platform. Without the need for dedicated web-hosting infrastructure, FME enhances both data accessibility and user experience. Join us to explore how to unlock the full potential of FME for your web projects and seamlessly integrate data-driven applications into your workflows.From Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software
╠²
Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasnŌĆÖt yielding any results, so I expanded my search to second-hand dealer sitesŌĆöonly to realise that periodically checking each one was going to be tedious. ThatŌĆÖs when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platformŌĆÖs structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, IŌĆÖll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME canŌĆÖt buy a car for youŌĆöyetŌĆöit can certainly help you find the one youŌĆÖre after!GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdf
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdfPriyanka Aash
╠²
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing NowŌĆ£Key Requirements to Successfully Implement Generative AI in Edge DevicesŌĆöOpt...
ŌĆ£Key Requirements to Successfully Implement Generative AI in Edge DevicesŌĆöOpt...Edge AI and Vision Alliance
╠²
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/key-requirements-to-successfully-implement-generative-ai-in-edge-devices-optimized-mapping-to-the-enhanced-npx6-neural-processing-unit-ip-a-presentation-from-synopsys/
Gordon Cooper, Principal Product Manager at Synopsys, presents the ŌĆ£Key Requirements to Successfully Implement Generative AI in Edge DevicesŌĆöOptimized Mapping to the Enhanced NPX6 Neural Processing Unit IPŌĆØ tutorial at the May 2025 Embedded Vision Summit.
In this talk, Cooper discusses emerging trends in generative AI for edge devices and the key role of transformer-based neural networks. He reviews the distinct attributes of transformers, their advantages over conventional convolutional neural networks and how they enable generative AI.
Cooper then covers key requirements that must be met for neural processing units (NPU) to support transformers and generative AI in edge device applications. He uses transformer-based generative AI examples to illustrate the efficient mapping of these workloads onto the enhanced Synopsys ARC NPX NPU IP family.Techniques for Automatic Device Identification and Network Assignment.pdf
Techniques for Automatic Device Identification and Network Assignment.pdfPriyanka Aash
╠²
Techniques for Automatic Device Identification and Network AssignmentUsing the SQLExecutor for Data Quality Management: aka One man's love for the...
Using the SQLExecutor for Data Quality Management: aka One man's love for the...Safe Software
╠²
The SQLExecutor is one of FMEŌĆÖs most powerful and flexible transformers. Pivvot maintains a robust internal metadata hierarchy used to support ingestion and curation of thousands of external data sources that must be managed for quality before entering our platform. By using the SQLExecutor, Pivvot can efficiently detect problems and perform analysis before data is extracted from our staging environment, removing the need for rollbacks or cycles waisted on a failed job. This presentation will walk through three distinct examples of how Pivvot uses the SQLExecutor to engage its metadata hierarchy and integrate with its Data Quality Management workflows efficiently and within the source postgres database. Spatial Validation ŌĆōValidating spatial prerequisites before entering a production environment. Reference Data Validation - Dynamically validate domain-ed columns across any table and multiple columns per table. Practical De-duplication - Removing identical or near-identical well point locations from two distinct source datasets in the same table.FIDO Seminar: Authentication for a Billion Consumers - Amazon.pptx
FIDO Seminar: Authentication for a Billion Consumers - Amazon.pptxFIDO Alliance
╠²
FIDO Seminar: Authentication for a Billion Consumers - AmazonImproving Data Integrity: Synchronization between EAM and ArcGIS Utility Netw...
Improving Data Integrity: Synchronization between EAM and ArcGIS Utility Netw...Safe Software
╠²
Utilities and water companies play a key role in the creation of clean drinking water. The creation and maintenance of clean drinking water is becoming a critical problem due to pollution and pressure on the environment. A lot of data is necessary to create clean drinking water. For fieldworkers, two types of data are key: Asset data in an asset management system (EAM for example) and Geographic data in a GIS (ArcGIS Utility Network ). Keeping this type of data up to date and in sync is a challenge for many organizations, leading to duplicating data and creating a bulk of extra attributes and data to keep everything in sync. Using FME, it is possible to synchronize Enterprise Asset Management (EAM) data with the ArcGIS Utility Network in real time. Changes (creation, modification, deletion) in ArcGIS Pro are relayed to EAM via FME, and vice versa. This ensures continuous synchronization of both systems without daily bulk updates, minimizes risks, and seamlessly integrates with ArcGIS Utility Network services. This presentation focuses on the use of FME at a Dutch water company, to create a sync between the asset management and GIS.CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025
CapCut Pro Crack For PC Latest Version {Fully Unlocked} 2025pcprocore
╠²
¤æēØŚĪØŚ╝ØśüØŚ▓:ØŚ¢ØŚ╝ØŚĮØśå ØŚ╣ØŚČØŚ╗ØŚĖ & ØŚĮØŚ«ØśĆØśüØŚ▓ ØŚČØŚ╗ØśüØŚ╝ ØŚÜØŚ╝ØŚ╝ØŚ┤ØŚ╣ØŚ▓ ØŚ╗ØŚ▓Øśä ØśüØŚ«ØŚ»> https://pcprocore.com/ ¤æłŌŚĆ
CapCut Pro Crack is a powerful tool that has taken the digital world by storm, offering users a fully unlocked experience that unleashes their creativity. With its user-friendly interface and advanced features, itŌĆÖs no wonder why aspiring videographers are turning to this software for their projects."How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays
╠²
We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. WeŌĆÖll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.OpenPOWER Foundation & Open-Source Core Innovations
OpenPOWER Foundation & Open-Source Core InnovationsIBM
╠²
penPOWER offers a fully open, royalty-free CPU architecture for custom chip design.
It enables both lightweight FPGA cores (like Microwatt) and high-performance processors (like POWER10).
Developers have full access to source code, specs, and tools for end-to-end chip creation.
It supports AI, HPC, cloud, and embedded workloads with proven performance.
Backed by a global community, it fosters innovation, education, and collaboration.Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdf
Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdfcaoyixuan2019
╠²
A presentation at Internetware 2025.FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptx
FIDO Seminar: Targeting Trust: The Future of Identity in the Workforce.pptxFIDO Alliance
╠²
FIDO Seminar: Targeting Trust: The Future of Identity in the WorkforceFIDO Seminar: New Data: Passkey Adoption in the Workforce.pptx
FIDO Seminar: New Data: Passkey Adoption in the Workforce.pptxFIDO Alliance
╠²
FIDO Seminar: New Data: Passkey Adoption in the WorkforceCoordinated Disclosure for ML - What's Different and What's the Same.pdf
Coordinated Disclosure for ML - What's Different and What's the Same.pdfPriyanka Aash
╠²
Coordinated Disclosure for ML - What's Different and What's the SameOpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC
╠²
The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.Wenn alles versagt - IBM Tape sch├╝tzt, was z├żhlt! Und besonders mit dem neust...
Wenn alles versagt - IBM Tape sch├╝tzt, was z├żhlt! Und besonders mit dem neust...Josef Weingand
╠²
IBM LTO10OWASP Barcelona 2025 Threat Model Library
OWASP Barcelona 2025 Threat Model LibraryPetraVukmirovic
╠²
Threat Model Library Launch at OWASP Barcelona 2025
https://owasp.org/www-project-threat-model-library/9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software
╠²
This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.ŌĆ£Key Requirements to Successfully Implement Generative AI in Edge DevicesŌĆöOpt...
ŌĆ£Key Requirements to Successfully Implement Generative AI in Edge DevicesŌĆöOpt...Edge AI and Vision Alliance
╠²
Ad
Ce hv7 module 18 cryptography
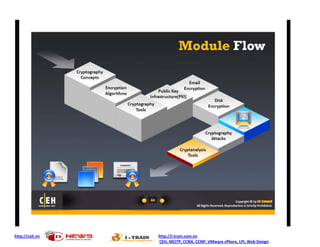
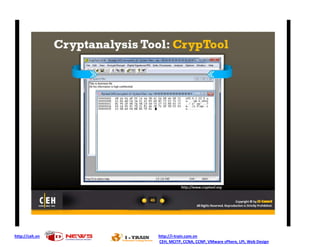
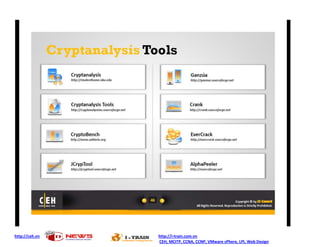
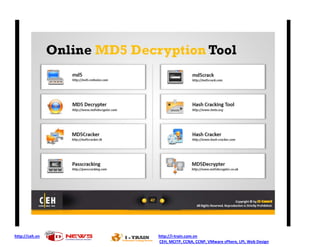
- 1. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 2. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 3. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 4. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 5. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 6. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 7. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 8. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 9. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 10. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 11. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 12. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 13. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 14. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 15. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 16. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 17. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 18. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 19. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 20. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 21. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 22. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 23. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 24. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 25. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 26. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 27. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 28. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 29. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 30. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 31. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 32. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 33. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 34. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 35. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 36. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 37. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 38. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 39. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 40. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 41. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 42. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 43. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 44. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 45. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 46. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 47. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 48. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
- 49. http://ceh.vn http://i-train.com.vn CEH, MCITP, CCNA, CCNP, VMware sPhere, LPI, Web Design
