CensorNet Professional
0 likes466 views
This document introduces CensorNet Professional, an on-premise web filtering and management software. It provides an overview of CensorNet Ltd's history and products, including the initial open source release of CensorNet in 2005. Key features of CensorNet Professional discussed are real-time content rating, granular policies, reporting, and deployment options like sideways and inline modes. The document also outlines integration capabilities like single sign-on authentication and synchronization with Active Directory. It concludes by thanking the audience and asking if there are any questions.
1 of 13












Recommended
CensorNet MailSafe



CensorNet MailSafetlloyduk
╠²
CensorNet is a company that provides email security solutions including MailSafe. This document provides an overview of CensorNet's products and services, roadmap, customer segmentation, hosted MailSafe offering including features such as spam detection, virus protection, archiving, and disaster recovery. It also describes the unique rules engine, email digest reports, disaster recovery for email, and white label branding options.Barracuda Web Filter Ip 20100629



Barracuda Web Filter Ip 20100629Carolynrahn
╠²
The document summarizes the Barracuda Web Filter which provides integrated content filtering, web security, and malware protection. It regulates internet browsing and application usage according to user-based policies. It is affordable to deploy and maintains scalability through its various appliance models.Cisco Wireless LAN Controller Palo Alto Networks Config Guide



Cisco Wireless LAN Controller Palo Alto Networks Config GuideAlberto Rivai
╠²
The document provides a configuration guide for integrating Cisco WLC 5500, Kiwi Syslogd, and Palo Alto Networks PAN-OS 6.1 to collect user authentication syslog messages from the Cisco WLC and map users to IP addresses in PAN-OS for use in security policies. It outlines configuring the Cisco WLC to send SNMP traps containing authentication information to Kiwi Syslogd, and Kiwi Syslogd to convert and forward the traps to the PAN-OS syslog receiver. It then details the necessary configuration steps in PAN-OS to define a syslog filter to parse and extract the user and IP address from the incoming syslog messages.Why Cant I Access The Portal



Why Cant I Access The PortalDan Usher
╠²
The document discusses authentication approaches in SharePoint, including integrated Windows authentication, forms-based authentication, Active Directory Federation Services, and smart card authentication. It compares the different approaches in terms of user experience, performance, and extending authentication to external users. The document also covers common issues that can prevent access such as misconfigurations of SharePoint policies, accounts, and infrastructure as well as development and branding problems. It emphasizes the importance of documentation, testing, and configuration management to avoid access issues.User expert forum user-id



User expert forum user-idAlberto Rivai
╠²
Palo Alto Networks Expert Forum - User-ID - Melbourne, Australia, 23 October 2013.
Alberto Rivai, CCIE#20068, CISSPIuwne10 S03 L01



Iuwne10 S03 L01Ravi Ranjan
╠²
The document discusses several tools for configuring wireless connections on different operating systems:
NetworkManager is a GUI for configuring wireless on Linux that allows creating simple password-based profiles or richer enterprise profiles. macOS uses AirPort Extreme, which configures parameters for networks in range and allows ad hoc or advanced profiles. Windows uses the Wireless Zero Configuration utility to automatically connect to preferred networks, detect broadcasting networks, and create basic profiles to add to preferred networks.Network and Cloud Security Improvements



Network and Cloud Security ImprovementsSteve Panaghi
╠²
Presentation that I delivered to stakeholders on key areas to improve Network & Cloud Security. The project was approved and completed successfully.User id installation and configuration



User id installation and configurationAlberto Rivai
╠²
This document provides instructions for configuring User-ID on a Palo Alto Networks firewall to map users to IP addresses and enumerate users and groups from an Active Directory server. It discusses using the User-ID agent and agentless methods. For agent-based mapping, it describes installing the agent, configuring permissions, and adding the agent to the firewall. For agentless mapping, it covers configuring the firewall and a service account. It also provides information on integrating User-ID with Microsoft NPS and DHCP through a script to automatically map authenticated wireless users.Palo Alto Networks CASB



Palo Alto Networks CASBAlberto Rivai
╠²
Palo Alto Networks provides a Cloud Access Security Broker (CASB) solution by natively integrating its Aperture, SAML Proxy, Next Generation Firewall (NGFW), and GlobalProtect products. These features work together to enforce security policies as managed devices access cloud services, such as authentication, authorization, and malware detection. The Aperture API also connects directly to software-as-service applications to provide additional data security capabilities like classification, leakage prevention, and threat detection.TechWiseTV Workshop: Cisco ISE 2.1 (Identity Services Engine)



TechWiseTV Workshop: Cisco ISE 2.1 (Identity Services Engine)Robb Boyd
╠²
These are the slides used in the Live Webinar August 3, 2016 at 10:00 am Pacific Time / 1:00 pm Eastern Time. You can listen/watch the replay of that show at techwisetv.com. Just click on 'workshops.' The TechWiseTV Episode is also on that site or on YouTube at https://youtu.be/zZHRLsaKD3U
Demos to checkout:
ISE Streamlined Visibility: https://communities.cisco.com/videos/15260
ISE Context Visibility: https://communities.cisco.com/videos/15264
ISE EasyConnect: https://communities.cisco.com/videos/15285
ISE Threat-centric NAC (AMP): https://communities.cisco.com/videos/15269
ISE Threat-centric NAC (Qualys): https://communities.cisco.com/videos/15270How sdp delivers_zero_trust



How sdp delivers_zero_trustZscaler
╠²
The era of cloud and mobility has changed the way we work and transformed the internet into the transport network for most enterprises. Even so, many continue to rely on security technologies designed for the old world, when users and data were on the network and applications were housed in the data center.
ESG believes that the challenge of using legacy security methods in the cloud era will be a key catalysts for the adoption of a new user- and application-centric approach known as zero trust security. The zero trust model is enabled by the software-defined perimeter (SDP), delivering secure anywhere access to internal applications without the use of VPN technology.Oracle soa cloud project



Oracle soa cloud projectGopinath Soundarrajan
╠²
Ebizoncloud Oracle SOA Cloud Project Integration with On Permises Legacy Systems and Dev, SIT, Preprod and Prod on Oracle Cloud Services.Vfm packetshaper presentation



Vfm packetshaper presentationvfmindia
╠²
PacketShaper provides deep visibility into application traffic and powerful control capabilities. It can distinguish applications at the packet level, including those masquerading under common ports. PacketShaper leverages WebPulse to classify URLs into over 80 categories. It also offers granular policy controls, integrated compression, and centralized management.VPN



VPNSwarup Kumar Mall
╠²
Virtual Private Networks (VPNs) allow private networks to be connected securely over the public Internet. There are two main methods for implementing VPNs - using IPSec at the network level or SSL at the transport level. IPSec VPNs require client software installation on each workstation while SSL VPNs only require a web browser with SSL support, making SSL VPNs easier to use. VPNs offer benefits over dedicated leased lines such as lower cost, easier setup, and flexibility, but are less secure, reliable, and performant than isolated private networks.Vpn



VpnLan & Wan Solutions
╠²
This document provides an overview of the features included in FortiOS 5.2, including IPsec and SSL VPN capabilities, SSL offloading and inspection, and virtual desktop features for SSL VPN. Key capabilities mentioned are IPsec and SSL VPN configurations, customizable SSL VPN portals, application control and host checking for virtual desktops, and SSL traffic inspection options. Contact information is also provided for certified experts in Fortinet products. RedIRIS Identity Service latest news and developments - Jamie Perez



RedIRIS Identity Service latest news and developments - Jamie PerezEduserv
╠²
The document discusses recent developments of the RedIRIS Identity Service in Spain, including actions taken to improve monitoring of the infrastructure, development of a new infrastructure, and collection of usage statistics. It also covers inter-federation initiatives like STORK and eduGAIN.Firewall



Firewalltrilokchandra prakash
╠²
A firewall is a network security system that monitors incoming and outgoing network traffic and filters out unauthorized access based on a set of rules. It uses access control lists (ACLs) and intrusion detection/prevention systems (IDS/IPS) to monitor traffic and identify potential threats. There are different types of firewalls including packet filtering, application-level gateways, circuit-level gateways, stateful multilayer inspection, and cloud-based firewalls that operate at different layers of the network and provide varying levels of security. Firewalls are a critical component of network security but must be properly configured to balance access needs with threat protection.Cisco Network Insider: Three Ways to Secure your Network



Cisco Network Insider: Three Ways to Secure your NetworkRobb Boyd
╠²
These are the slides from our Tuesday Jun 14, 2016 webinar featuring three building block technologies for quickly adding a ton of value to your security efforts.
Watch the Replay: http://bit.ly/1UhUZ1J
We covered:
- Identity Services Engine (ISE)- visibility and controlŌĆ”along with a solid set of sharing capabilities. Using ISE you can see the device types and control access to the network ŌĆō and share what they see with Stealthwatch.╠²
- Stealthwatch - Visibility with even more network elementsŌĆ”work in conjunction with ISE but adds behavioral analysis Using Stealthwatch you can see the behaviors of the devices and determine if they are infected with malware or ransomware ŌĆō and then use the network to take action to contain from a single screen.╠²
- Cisco Defense Orchestrator (CDO) - Cloud platform that analyzes security policy configurations for Cisco ASA Firewalls and OpenDNS. It identifies and resolves policy inconsistencies, models policy changes to validate their impact, and orchestrates policy changes to achieve consistency and clarity of your security posture.presentation_finals



presentation_finalsShivashish Kumar
╠²
This document discusses the development of a user-friendly application for public-key cryptosystem using OpenSSL. The application aims to allow users to securely transmit data with limited cryptographic knowledge through an easy-to-use interface. It generates key pairs, signs and verifies signatures, encrypts and decrypts data, and combines signature and encryption functions. The application was created using Java, OpenSSL crypto libraries, and supports FIPS 140-2 compliant crypto tokens for security. It provides a simple click-based interface for cryptographic tasks to reduce the effort for users.AAA & RADIUS Protocols



AAA & RADIUS ProtocolsPeter R. Egli
╠²
Short overview of AAA and the RADIUS protocol.
The term AAA (say triple A) subsumes the functions used in network access to allow a user or a computer to access a network and use its resources.
AAA stands for Authentication (is the user authentic?), Authorization (what is the user allowed to do?) and Accounting (track resource usage by the user).
AAA is typically employed at network ingress points to control user's access to the network and resources.
The most prominent protocol for AAA is RADIUS (Remote Authentication Dial In User Service) which defines messages for opening and closing a network session and counting network usage (packet and byte count).
RADIUS usually works in conjunction with an LDAP server that stores the policies and user authorizations in a central repository.
TechWiseTV Workshop: Stealthwatch Learning Network License



TechWiseTV Workshop: Stealthwatch Learning Network LicenseRobb Boyd
╠²
Replay the Live Event: http://cs.co/90068G6ln
Get an inside look at how Stealthwatch Learning Network License can transform your branch network router into a powerful security sensor and enforcer: one capable of quickly detecting threat activity and mitigating attacks, with little to no hands-on management needed.
DonŌĆÖt miss this opportunity to hear from our security experts.
See the Stealthwatch Learning Network License TechWiseTV Episode: http://cs.co/90048G6WYEnd-to-Eend security with Palo Alto Networks (Onur Kasap, Palo Alto Networks)



End-to-Eend security with Palo Alto Networks (Onur Kasap, Palo Alto Networks)BAKOTECH
╠²
Palo Alto Networks - ąĖąĮąĮąŠą▓ą░čåąĖąŠąĮąĮą░čÅ ą┐ą╗ą░čéč乊čĆą╝ą░ čüąĄč鹥ą▓ąŠą╣ ą▒ąĄąĘąŠą┐ą░čüąĮąŠčüčéąĖ čÅą┤čĆąŠą╝ ą║ąŠč鹊čĆąŠą╣ čÅą▓ą╗čÅąĄčéčüčÅ next generation firewall, ąĮą░ ą▒ą░ąĘąĄ čāąĮąĖą║ą░ą╗čīąĮąŠą╣, čĆą░ąĘčĆą░ą▒ąŠčéą░ąĮąĮąŠą╣ PA Networks č鹥čģąĮąŠą╗ąŠą│ąĖąĖ App-ID, ąŠą▒ąĄčüą┐ąĄčćąĖą▓ą░ąĄčé ą▒ąĄąĘąŠą┐ą░čüąĮąŠčüčéčī čüąĄčéąĖ ąĮą░ čāčĆąŠą▓ąĮąĄ ą┐čĆąĖą╗ąŠąČąĄąĮąĖą╣, ą┐ąŠą╗čīąĘąŠą▓ą░č鹥ą╗ąĄą╣ ąĖ ą║ąŠąĮč鹥ąĮčéą░ čü ąĖčüą┐ąŠą╗čīąĘąŠą▓ą░ąĮąĖąĄą╝ ą║ą░ą║ čäąĖąĘąĖč湥čüą║ąŠą╣ čéą░ą║ ąĖ ą▓ąĖčĆčéčāą░ą╗čīąĮąŠą╣ ą░čĆčģąĖč鹥ą║čéčāčĆčŗ. ąĀąĄčłąĄąĮąĖčÅ čüąĄč鹥ą▓ąŠą╣ ąĘą░čēąĖčéčŗ PAN čüąŠąŠčéą▓ąĄčéčüčéą▓čāčÄčé čüą░ą╝čŗą╝ ą▓čŗčüąŠą║ąĖą╝ čéčĆąĄą▒ąŠą▓ą░ąĮąĖčÅą╝ ą║ čüąĄč鹥ą▓ąŠą╣ ą▒ąĄąĘąŠą┐ą░čüąĮąŠčüčéąĖ, ą║ą░ą║ ą┐ąŠ ą┐čĆąŠąĖąĘą▓ąŠą┤ąĖč鹥ą╗čīąĮąŠčüčéąĖ čéą░ą║ ąĖ ą┐ąŠ čäčāąĮą║čåąĖąŠąĮą░ą╗čīąĮąŠčüčéąĖ, ąĖ čÅą▓ą╗čÅčÄčéčüčÅ ą▒ąĄąĘčāčüą╗ąŠą▓ąĮčŗą╝ąĖ ą╗ąĖą┤ąĄčĆą░ą╝ąĖ ąŠčéčĆą░čüą╗ąĖ, čćč鹊 ą┐ąŠą┤čéą▓ąĄčƹȹ┤ąĄąĮąŠ ąŠčéč湥čéą░ą╝ąĖ Gartner, ą║ąŠą╗ąĖč湥čüčéą▓ąŠą╝ ą┐ąŠą╗čīąĘąŠą▓ą░č鹥ą╗ąĄą╣ ąĖ čĆą░čüčéčāčēąĖą╝ ąŠą▒čŖąĄą╝ąŠą╝ ą┐čĆąŠą┤ą░ąČ ą║ąŠą╝ą┐ą░ąĮąĖąĖ.IRJET- A Defense System Against Application Layer Ddos Attacks with Data Secu...



IRJET- A Defense System Against Application Layer Ddos Attacks with Data Secu...IRJET Journal
╠²
This document proposes a defense system against application layer distributed denial of service (DDoS) attacks that uses data structures to quickly detect and mitigate such attacks. The system uses a CAPTCHA test to determine if a request is part of an attack. Requests from blacklisted IP addresses are blocked, while requests from whitelisted IP addresses are allowed. The experimental results show that the system can reduce malicious requests quickly while posing limited impact on normal users. The system also includes a honey pot technique for file security in cloud storage, where unique codes are generated for uploaded files and must be provided to download files, returning dummy files for invalid codes.Vfm bluecoat proxy sg solution with web filter and reporter



Vfm bluecoat proxy sg solution with web filter and reportervfmindia
╠²
The Bluecoat ProxySG solution provides web filtering, malware protection, and reporting through its integrated WebFilter and WebPulse cloud services which analyze over 2 billion requests per week to provide real-time web ratings and threats intelligence to the ProxySG appliance. The new Reporter 9 interface provides customized dashboards and reporting for up to 150,000 users with scalable log storage and performance.Risico op digitale bedreigingen maximaal verminderen - Bijdrage ASP4all voor ...



Risico op digitale bedreigingen maximaal verminderen - Bijdrage ASP4all voor ...ASP4all
╠²
This document discusses ASP4all's approach to minimizing digital threats. It outlines their expertise in migrating, hosting, and managing mission critical applications. It then details their security approach which employs defense in depth across physical, network, host, application, and data layers to secure systems from threats like DDoS attacks and malware. Their services include tier 3 datacenters, firewalls, web application firewalls, encryption, and audited/patched systems.A Novel Mutual Authentication Algorithm using Visual Cryptography with Novel ...



A Novel Mutual Authentication Algorithm using Visual Cryptography with Novel ...IRJET Journal
╠²
The document proposes a novel mutual authentication algorithm using visual cryptography. It aims to provide stronger authentication security compared to traditional text-based passwords. The algorithm uses two registered images per user - a security image and password image. During registration, the server generates shares of the images and mails one share to the user. During login, the user uploads their share to authenticate the server, while the server generates a random session share of the password image to authenticate the user by reconstructing and hashing the image. The algorithm provides mutual authentication without third party involvement by using visual cryptography techniques on user-registered images.TechWiseTV Workshop: Tetration Analytics



TechWiseTV Workshop: Tetration AnalyticsRobb Boyd
╠²
Replay the Live Event: http://cs.co/90098Be7h
See firsthand how Cisco Tetration Analytics uses unsupervised machine learning and behavior analysis, along with advanced algorithmic approaches, to provide unprecedented insight into IT infrastructure.
DonŌĆÖt miss this chance to get an up-close look at the analytics platform that lets you see and know exactly whatŌĆÖs happening in any application, any flow, anywhere in your data centerŌĆöall in a matter of seconds.
See the Tetration Analytics TechWiseTV Episode: http://cs.co/90048BefC
Net Motion Mobility Overview - Field Service



Net Motion Mobility Overview - Field Serviceksholes
╠²
This document provides an overview of Mobility XE, a mobile VPN product from NetMotion Wireless. It addresses challenges mobile workers face including connectivity, application performance, and support. Mobility XE enhances productivity by making VPN and application sessions persistent during mobility and optimizing bandwidth. It provides security using AES encryption, authentication methods like Active Directory, and controls like device authentication. The management console allows centralized visibility and control of all device connections, applications, and networks used.Quantum Architecture Overview



Quantum Architecture Overviewjinpeng
╠²
The document discusses Quantum Framework, an open source identity and trust management system. It provides centralized authentication, authorization and administration for both users and network elements. It uses technologies like LDAP, PKI and UDDI to securely manage identities and provide a common registry of network elements. Quantum Framework allows for single sign-on, role-based access controls and dynamic grouping of registered elements.Quantum Architecture Overview



Quantum Architecture Overviewjinpeng
╠²
The document discusses Quantum Framework, an open source identity and trust management system. It provides centralized identity management for both people and network elements. It uses technologies like AAA, PKI, UDDI and SOA to provide single sign-on, role-based access control, and a common registry for network elements. Quantum Framework allows for dynamic integration of network services and applications through different levels of integration with its security, registry and management functions.More Related Content
What's hot (19)
Palo Alto Networks CASB



Palo Alto Networks CASBAlberto Rivai
╠²
Palo Alto Networks provides a Cloud Access Security Broker (CASB) solution by natively integrating its Aperture, SAML Proxy, Next Generation Firewall (NGFW), and GlobalProtect products. These features work together to enforce security policies as managed devices access cloud services, such as authentication, authorization, and malware detection. The Aperture API also connects directly to software-as-service applications to provide additional data security capabilities like classification, leakage prevention, and threat detection.TechWiseTV Workshop: Cisco ISE 2.1 (Identity Services Engine)



TechWiseTV Workshop: Cisco ISE 2.1 (Identity Services Engine)Robb Boyd
╠²
These are the slides used in the Live Webinar August 3, 2016 at 10:00 am Pacific Time / 1:00 pm Eastern Time. You can listen/watch the replay of that show at techwisetv.com. Just click on 'workshops.' The TechWiseTV Episode is also on that site or on YouTube at https://youtu.be/zZHRLsaKD3U
Demos to checkout:
ISE Streamlined Visibility: https://communities.cisco.com/videos/15260
ISE Context Visibility: https://communities.cisco.com/videos/15264
ISE EasyConnect: https://communities.cisco.com/videos/15285
ISE Threat-centric NAC (AMP): https://communities.cisco.com/videos/15269
ISE Threat-centric NAC (Qualys): https://communities.cisco.com/videos/15270How sdp delivers_zero_trust



How sdp delivers_zero_trustZscaler
╠²
The era of cloud and mobility has changed the way we work and transformed the internet into the transport network for most enterprises. Even so, many continue to rely on security technologies designed for the old world, when users and data were on the network and applications were housed in the data center.
ESG believes that the challenge of using legacy security methods in the cloud era will be a key catalysts for the adoption of a new user- and application-centric approach known as zero trust security. The zero trust model is enabled by the software-defined perimeter (SDP), delivering secure anywhere access to internal applications without the use of VPN technology.Oracle soa cloud project



Oracle soa cloud projectGopinath Soundarrajan
╠²
Ebizoncloud Oracle SOA Cloud Project Integration with On Permises Legacy Systems and Dev, SIT, Preprod and Prod on Oracle Cloud Services.Vfm packetshaper presentation



Vfm packetshaper presentationvfmindia
╠²
PacketShaper provides deep visibility into application traffic and powerful control capabilities. It can distinguish applications at the packet level, including those masquerading under common ports. PacketShaper leverages WebPulse to classify URLs into over 80 categories. It also offers granular policy controls, integrated compression, and centralized management.VPN



VPNSwarup Kumar Mall
╠²
Virtual Private Networks (VPNs) allow private networks to be connected securely over the public Internet. There are two main methods for implementing VPNs - using IPSec at the network level or SSL at the transport level. IPSec VPNs require client software installation on each workstation while SSL VPNs only require a web browser with SSL support, making SSL VPNs easier to use. VPNs offer benefits over dedicated leased lines such as lower cost, easier setup, and flexibility, but are less secure, reliable, and performant than isolated private networks.Vpn



VpnLan & Wan Solutions
╠²
This document provides an overview of the features included in FortiOS 5.2, including IPsec and SSL VPN capabilities, SSL offloading and inspection, and virtual desktop features for SSL VPN. Key capabilities mentioned are IPsec and SSL VPN configurations, customizable SSL VPN portals, application control and host checking for virtual desktops, and SSL traffic inspection options. Contact information is also provided for certified experts in Fortinet products. RedIRIS Identity Service latest news and developments - Jamie Perez



RedIRIS Identity Service latest news and developments - Jamie PerezEduserv
╠²
The document discusses recent developments of the RedIRIS Identity Service in Spain, including actions taken to improve monitoring of the infrastructure, development of a new infrastructure, and collection of usage statistics. It also covers inter-federation initiatives like STORK and eduGAIN.Firewall



Firewalltrilokchandra prakash
╠²
A firewall is a network security system that monitors incoming and outgoing network traffic and filters out unauthorized access based on a set of rules. It uses access control lists (ACLs) and intrusion detection/prevention systems (IDS/IPS) to monitor traffic and identify potential threats. There are different types of firewalls including packet filtering, application-level gateways, circuit-level gateways, stateful multilayer inspection, and cloud-based firewalls that operate at different layers of the network and provide varying levels of security. Firewalls are a critical component of network security but must be properly configured to balance access needs with threat protection.Cisco Network Insider: Three Ways to Secure your Network



Cisco Network Insider: Three Ways to Secure your NetworkRobb Boyd
╠²
These are the slides from our Tuesday Jun 14, 2016 webinar featuring three building block technologies for quickly adding a ton of value to your security efforts.
Watch the Replay: http://bit.ly/1UhUZ1J
We covered:
- Identity Services Engine (ISE)- visibility and controlŌĆ”along with a solid set of sharing capabilities. Using ISE you can see the device types and control access to the network ŌĆō and share what they see with Stealthwatch.╠²
- Stealthwatch - Visibility with even more network elementsŌĆ”work in conjunction with ISE but adds behavioral analysis Using Stealthwatch you can see the behaviors of the devices and determine if they are infected with malware or ransomware ŌĆō and then use the network to take action to contain from a single screen.╠²
- Cisco Defense Orchestrator (CDO) - Cloud platform that analyzes security policy configurations for Cisco ASA Firewalls and OpenDNS. It identifies and resolves policy inconsistencies, models policy changes to validate their impact, and orchestrates policy changes to achieve consistency and clarity of your security posture.presentation_finals



presentation_finalsShivashish Kumar
╠²
This document discusses the development of a user-friendly application for public-key cryptosystem using OpenSSL. The application aims to allow users to securely transmit data with limited cryptographic knowledge through an easy-to-use interface. It generates key pairs, signs and verifies signatures, encrypts and decrypts data, and combines signature and encryption functions. The application was created using Java, OpenSSL crypto libraries, and supports FIPS 140-2 compliant crypto tokens for security. It provides a simple click-based interface for cryptographic tasks to reduce the effort for users.AAA & RADIUS Protocols



AAA & RADIUS ProtocolsPeter R. Egli
╠²
Short overview of AAA and the RADIUS protocol.
The term AAA (say triple A) subsumes the functions used in network access to allow a user or a computer to access a network and use its resources.
AAA stands for Authentication (is the user authentic?), Authorization (what is the user allowed to do?) and Accounting (track resource usage by the user).
AAA is typically employed at network ingress points to control user's access to the network and resources.
The most prominent protocol for AAA is RADIUS (Remote Authentication Dial In User Service) which defines messages for opening and closing a network session and counting network usage (packet and byte count).
RADIUS usually works in conjunction with an LDAP server that stores the policies and user authorizations in a central repository.
TechWiseTV Workshop: Stealthwatch Learning Network License



TechWiseTV Workshop: Stealthwatch Learning Network LicenseRobb Boyd
╠²
Replay the Live Event: http://cs.co/90068G6ln
Get an inside look at how Stealthwatch Learning Network License can transform your branch network router into a powerful security sensor and enforcer: one capable of quickly detecting threat activity and mitigating attacks, with little to no hands-on management needed.
DonŌĆÖt miss this opportunity to hear from our security experts.
See the Stealthwatch Learning Network License TechWiseTV Episode: http://cs.co/90048G6WYEnd-to-Eend security with Palo Alto Networks (Onur Kasap, Palo Alto Networks)



End-to-Eend security with Palo Alto Networks (Onur Kasap, Palo Alto Networks)BAKOTECH
╠²
Palo Alto Networks - ąĖąĮąĮąŠą▓ą░čåąĖąŠąĮąĮą░čÅ ą┐ą╗ą░čéč乊čĆą╝ą░ čüąĄč鹥ą▓ąŠą╣ ą▒ąĄąĘąŠą┐ą░čüąĮąŠčüčéąĖ čÅą┤čĆąŠą╝ ą║ąŠč鹊čĆąŠą╣ čÅą▓ą╗čÅąĄčéčüčÅ next generation firewall, ąĮą░ ą▒ą░ąĘąĄ čāąĮąĖą║ą░ą╗čīąĮąŠą╣, čĆą░ąĘčĆą░ą▒ąŠčéą░ąĮąĮąŠą╣ PA Networks č鹥čģąĮąŠą╗ąŠą│ąĖąĖ App-ID, ąŠą▒ąĄčüą┐ąĄčćąĖą▓ą░ąĄčé ą▒ąĄąĘąŠą┐ą░čüąĮąŠčüčéčī čüąĄčéąĖ ąĮą░ čāčĆąŠą▓ąĮąĄ ą┐čĆąĖą╗ąŠąČąĄąĮąĖą╣, ą┐ąŠą╗čīąĘąŠą▓ą░č鹥ą╗ąĄą╣ ąĖ ą║ąŠąĮč鹥ąĮčéą░ čü ąĖčüą┐ąŠą╗čīąĘąŠą▓ą░ąĮąĖąĄą╝ ą║ą░ą║ čäąĖąĘąĖč湥čüą║ąŠą╣ čéą░ą║ ąĖ ą▓ąĖčĆčéčāą░ą╗čīąĮąŠą╣ ą░čĆčģąĖč鹥ą║čéčāčĆčŗ. ąĀąĄčłąĄąĮąĖčÅ čüąĄč鹥ą▓ąŠą╣ ąĘą░čēąĖčéčŗ PAN čüąŠąŠčéą▓ąĄčéčüčéą▓čāčÄčé čüą░ą╝čŗą╝ ą▓čŗčüąŠą║ąĖą╝ čéčĆąĄą▒ąŠą▓ą░ąĮąĖčÅą╝ ą║ čüąĄč鹥ą▓ąŠą╣ ą▒ąĄąĘąŠą┐ą░čüąĮąŠčüčéąĖ, ą║ą░ą║ ą┐ąŠ ą┐čĆąŠąĖąĘą▓ąŠą┤ąĖč鹥ą╗čīąĮąŠčüčéąĖ čéą░ą║ ąĖ ą┐ąŠ čäčāąĮą║čåąĖąŠąĮą░ą╗čīąĮąŠčüčéąĖ, ąĖ čÅą▓ą╗čÅčÄčéčüčÅ ą▒ąĄąĘčāčüą╗ąŠą▓ąĮčŗą╝ąĖ ą╗ąĖą┤ąĄčĆą░ą╝ąĖ ąŠčéčĆą░čüą╗ąĖ, čćč鹊 ą┐ąŠą┤čéą▓ąĄčƹȹ┤ąĄąĮąŠ ąŠčéč湥čéą░ą╝ąĖ Gartner, ą║ąŠą╗ąĖč湥čüčéą▓ąŠą╝ ą┐ąŠą╗čīąĘąŠą▓ą░č鹥ą╗ąĄą╣ ąĖ čĆą░čüčéčāčēąĖą╝ ąŠą▒čŖąĄą╝ąŠą╝ ą┐čĆąŠą┤ą░ąČ ą║ąŠą╝ą┐ą░ąĮąĖąĖ.IRJET- A Defense System Against Application Layer Ddos Attacks with Data Secu...



IRJET- A Defense System Against Application Layer Ddos Attacks with Data Secu...IRJET Journal
╠²
This document proposes a defense system against application layer distributed denial of service (DDoS) attacks that uses data structures to quickly detect and mitigate such attacks. The system uses a CAPTCHA test to determine if a request is part of an attack. Requests from blacklisted IP addresses are blocked, while requests from whitelisted IP addresses are allowed. The experimental results show that the system can reduce malicious requests quickly while posing limited impact on normal users. The system also includes a honey pot technique for file security in cloud storage, where unique codes are generated for uploaded files and must be provided to download files, returning dummy files for invalid codes.Vfm bluecoat proxy sg solution with web filter and reporter



Vfm bluecoat proxy sg solution with web filter and reportervfmindia
╠²
The Bluecoat ProxySG solution provides web filtering, malware protection, and reporting through its integrated WebFilter and WebPulse cloud services which analyze over 2 billion requests per week to provide real-time web ratings and threats intelligence to the ProxySG appliance. The new Reporter 9 interface provides customized dashboards and reporting for up to 150,000 users with scalable log storage and performance.Risico op digitale bedreigingen maximaal verminderen - Bijdrage ASP4all voor ...



Risico op digitale bedreigingen maximaal verminderen - Bijdrage ASP4all voor ...ASP4all
╠²
This document discusses ASP4all's approach to minimizing digital threats. It outlines their expertise in migrating, hosting, and managing mission critical applications. It then details their security approach which employs defense in depth across physical, network, host, application, and data layers to secure systems from threats like DDoS attacks and malware. Their services include tier 3 datacenters, firewalls, web application firewalls, encryption, and audited/patched systems.A Novel Mutual Authentication Algorithm using Visual Cryptography with Novel ...



A Novel Mutual Authentication Algorithm using Visual Cryptography with Novel ...IRJET Journal
╠²
The document proposes a novel mutual authentication algorithm using visual cryptography. It aims to provide stronger authentication security compared to traditional text-based passwords. The algorithm uses two registered images per user - a security image and password image. During registration, the server generates shares of the images and mails one share to the user. During login, the user uploads their share to authenticate the server, while the server generates a random session share of the password image to authenticate the user by reconstructing and hashing the image. The algorithm provides mutual authentication without third party involvement by using visual cryptography techniques on user-registered images.TechWiseTV Workshop: Tetration Analytics



TechWiseTV Workshop: Tetration AnalyticsRobb Boyd
╠²
Replay the Live Event: http://cs.co/90098Be7h
See firsthand how Cisco Tetration Analytics uses unsupervised machine learning and behavior analysis, along with advanced algorithmic approaches, to provide unprecedented insight into IT infrastructure.
DonŌĆÖt miss this chance to get an up-close look at the analytics platform that lets you see and know exactly whatŌĆÖs happening in any application, any flow, anywhere in your data centerŌĆöall in a matter of seconds.
See the Tetration Analytics TechWiseTV Episode: http://cs.co/90048BefC
Similar to CensorNet Professional (20)
Net Motion Mobility Overview - Field Service



Net Motion Mobility Overview - Field Serviceksholes
╠²
This document provides an overview of Mobility XE, a mobile VPN product from NetMotion Wireless. It addresses challenges mobile workers face including connectivity, application performance, and support. Mobility XE enhances productivity by making VPN and application sessions persistent during mobility and optimizing bandwidth. It provides security using AES encryption, authentication methods like Active Directory, and controls like device authentication. The management console allows centralized visibility and control of all device connections, applications, and networks used.Quantum Architecture Overview



Quantum Architecture Overviewjinpeng
╠²
The document discusses Quantum Framework, an open source identity and trust management system. It provides centralized authentication, authorization and administration for both users and network elements. It uses technologies like LDAP, PKI and UDDI to securely manage identities and provide a common registry of network elements. Quantum Framework allows for single sign-on, role-based access controls and dynamic grouping of registered elements.Quantum Architecture Overview



Quantum Architecture Overviewjinpeng
╠²
The document discusses Quantum Framework, an open source identity and trust management system. It provides centralized identity management for both people and network elements. It uses technologies like AAA, PKI, UDDI and SOA to provide single sign-on, role-based access control, and a common registry for network elements. Quantum Framework allows for dynamic integration of network services and applications through different levels of integration with its security, registry and management functions.Secure Decisions - Cyber Security Sensemaking



Secure Decisions - Cyber Security SensemakingAnita D'Amico
╠²
Secure Decisions is a company that helps analyze security data and decision processes to enhance cybersecurity. They develop visual analytics tools to help cyber analysts make sense of network and software vulnerability data. Some of their products include tools that visualize wireless network security data, software vulnerabilities from multiple scanners, and network flows and alerts. They also provide consulting services and have developed technologies like a cyber decision support system and a testbed for evaluating network monitoring algorithms. Their goal is to transition research into tools that can help operators in both government and commercial organizations.Cyberoam SSL VPN



Cyberoam SSL VPNAjay Nawani
╠²
The document discusses Cyberoam's SSL VPN product. It provides an overview of the business need for SSL VPNs and secure remote access. It then describes Cyberoam's SSL VPN solution, including its key features like support for multiple applications and devices, endpoint security checks, auditing and logging. Finally, it discusses Cyberoam's virtual appliance offerings and the benefits for both MSSPs and organizations.11 palo alto user-id concepts



11 palo alto user-id conceptsMostafa El Lathy
╠²
https://www.facebook.com/MostafaElLathyIT
mostafa.it@hotmail.com
https://www.youtube.com/channel/UCAEiVvBP3DbIKUcoZBcaHvQOperations: Security Crash Course ŌĆö Best Practices for Securing your Company



Operations: Security Crash Course ŌĆö Best Practices for Securing your CompanyAmazon Web Services
╠²
All companies should build with security and protection of customer data as the number one priority. This talk will cover a wide range of best practices from MFA, root accounts, encrypting laptops, inventory management, MDM, and incident response. You'll learn key principles of how to build a secure organization to protect your data. Don't wait until your first security incident before putting these best practices in place.ip pier solution



ip pier solutionAlexey Stankus
╠²
This document discusses security challenges on the internet including a rise in bot traffic, DDoS attacks, and the transition to HTTPS. It then outlines the capabilities needed in a security system, including protection from layer 3, 4, and 7 DDoS attacks, bot detection without CAPTCHAs, and HTTPS filtering without disclosing traffic. Finally, it describes different modes of operation for an active bot protection system and traffic filtration techniques for HTTPS, including options that meet PCI compliance.Start Up Austin 2017: Security Crash Course and Best Pratices



Start Up Austin 2017: Security Crash Course and Best PraticesAmazon Web Services
╠²
1. The document discusses various security best practices for visibility, least permissions, encryption, keeping systems updated, application security, office IT, and databases. It covers aggregating logs in a central location, limiting permissions through processes/files and SSH security, using encryption for data in transit and at rest, automating updates, and implementing security measures in development pipelines and the office.Operations: Security



Operations: SecurityAmazon Web Services
╠²
Will St. Clair: AWS San Francisco Startup Day, 9/7/17
Operations: Security Crash Course & Best Practices! All companies should build with security and protection of customer data as the number one priority. This talk will cover a wide range of best practices from MFA, root accounts, encrypting laptops, inventory management, MDM, and incident response. You'll learn key principles of how to build a secure organization to protect your data. Don't wait until your first security incident before putting these best practices in place.Cortana Analytics Workshop: Cortana Analytics -- Security, Privacy & Compliance



Cortana Analytics Workshop: Cortana Analytics -- Security, Privacy & ComplianceMSAdvAnalytics
╠²
Eric Golpe. Security, privacy, and compliance concerns can be significant hurdles to cloud adoption. Azure can help customers move to the cloud with confidence by providing a trusted foundation, demonstrating compliance with security standards, and making strong commitments to safeguard the privacy of customer data. This presentation will educate you in the fundamentals of Azure security as they pertain to the Cortana Analytics Suite, including capabilities in place for threat defense, network security, access control, and data protection as well as data privacy and compliance. Go to https://channel9.msdn.com/ to find the recording of this session. How to deploy Windows Mobile to 40,000 users



How to deploy Windows Mobile to 40,000 usersjasonlan
╠²
This document summarizes a presentation about deploying mobile devices at large scale using Microsoft Exchange Server and Windows Mobile. The presentation covers infrastructure requirements, procurement considerations, provisioning tools, device management, support needs, and lessons learned from Microsoft's internal deployment of over 40,000 mobile devices. Effective planning of infrastructure, standardized device selection, centralized management capabilities, and end-user support are key to a successful large-scale mobile rollout.System Center Mobile Device Manager



System Center Mobile Device ManagerJohn Rhoton
╠²
This document discusses mobile device management (MDM) and provides an overview of key concepts. It describes the challenges of managing mobility in enterprises and different MDM approaches, such as those from Microsoft, HP, and others. The document outlines the benefits of MDM, including improved security, lower costs, and easier administration and deployment of applications. It also provides details on Microsoft's System Center Mobile Device Manager solution, covering components like enrollment servers, VPN, and how it extends management capabilities to mobile devices.Cyberoam Firewall Presentation



Cyberoam Firewall PresentationManoj Kumar Mishra
╠²
Cyberoam UTM appliances enables small offices to shift from plain firewall to comprehensive UTM protection with cost effective, which gives powerful security to protect your network from malware, spam, trojan, DoS, DDoS, Phishing, pharming and intrusions. Large organizations can implement uniform security and gain high visibility into remote and branch offices with centralized management and Layer 8 Identity-based security.Technet System Center Mobile Device Manager Presentation



Technet System Center Mobile Device Manager Presentationjasonlan
╠²
This is the presentation delivered at the 2 recent Technet events in Manchester and London as well as our EMEA Enterprise event in DublinOverview of Microsoft Exchange Online



Overview of Microsoft Exchange OnlineMicrosoft Private Cloud
╠²
Exchange Online provides cloud-based email and calendaring services with benefits of lower costs, simplified management, and increased security and reliability compared to on-premises email. Key features include business-class messaging, 24/7 support, Active Directory integration, large mailbox sizes up to 25GB, and geo-redundant data centers. Optional services include archiving, coexistence with on-premises email, and a low-cost subscription for deskless users. The presentation provides an overview of Exchange Online and its capabilities.Twofactorauthentication 120625115723-phpapp01



Twofactorauthentication 120625115723-phpapp01Hai Nguyen
╠²
PortalGuard is a contextual authentication platform that provides single sign-on, password management, two-factor authentication, and real-time reporting capabilities. It offers a tokenless two-factor authentication approach that sends one-time passwords (OTPs) to users' mobile phones via SMS, email, or transparent tokens. The authentication process involves a user entering their username, being sent an OTP, entering both the OTP and their password, and gaining access if authenticated. PortalGuard is configurable by user or group and supports RADIUS for VPN authentication with network devices in a multi-step process. It has technical requirements including .NET framework and specific Windows and IIS versions.Istio Service Mesh



Istio Service MeshLew Tucker
╠²
As more applications are being developed as a set of microservices, containers and platforms such as Kubernetes make many things much easier, but still leave untouched many operational issues such as traffic management and visibility, service authentication, security and policy. Istio, is a new service mesh that attempts to address many of these. We will discuss the architecture of Istio and the benefits it may offer to new microservice-based systems in a multicloud world.Cloud Computing Environment using Secured Access Control Technique



Cloud Computing Environment using Secured Access Control TechniqueIRJET Journal
╠²
This document proposes a new technique called Storage Correctness and Small-grained Access Provision (SCSAP) for secure cloud computing environments. SCSAP aims to improve on existing access control techniques by providing more fine-grained user access and ensuring correctness of outsourced cloud data storage through a token granting system. The technique constructs hierarchical user access formations and includes algorithmic phases for small-grained data access and efficient storage. If implemented, SCSAP could provide stronger security, access control and data integrity than prior cloud storage solutions.VMworld 2013: VMware Compliance Reference Architecture Framework Overview 



VMworld 2013: VMware Compliance Reference Architecture Framework Overview VMworld
╠²
VMworld 2013
Jerry Breaud, VMware
Allen Shortnacy, VMware
Learn more about VMworld and register at http://www.vmworld.com/index.jspa?src=socmed-vmworld-slideshareCensorNet Professional
- 1. CensorNet LtdAn introduction to CensorNetProfessionalOn-premise web filtering & managementPresented by:XXXXXXXXXXXXXProduct ManagerEmail: xxxx.xxxxx@censornet.comTel: XXXXXXXX
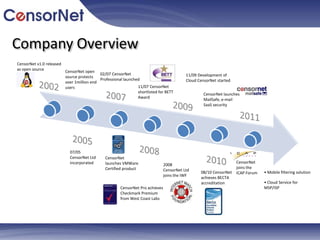
- 2. Company OverviewCensorNet v1.0 released as open sourceCensorNet open source protects over 1million end users02/07 CensorNet Professional launched11/09 Development of Cloud CensorNet started11/07 CensorNet shortlisted for BETT AwardCensorNet launches MailSafe, e-mail SaaS security07/05 CensorNet Ltd incorporatedCensorNet launches VMWare Certified productCensorNet joins the ICAP Forum2008 CensorNet Ltd joins the IWF08/10 CensorNet achieves BECTA accreditationŌĆó Mobile filtering solutionŌĆó Cloud Service for MSP/ISPCensorNet Pro achieves Checkmark Premium from West Coast Labs
- 3. RoadmapMailSafePolicy Based EncryptionCensorNet Pro 2.0CloudCN release (MSP)CloudCN beta trialsCensorNetMediaManagerCloudCN RemoteWorker2Client SoftwareCloudCN mobile clientsMailSafeSalesforceCensorNetProtocol ControlMailSafeCalendaringMailSafeAdvanced ArchivingCensorNetPureSight
- 6. OverviewReal-time rating of content
- 10. Reports engine
- 11. Over 36 template reports
- 13. HTTP 1.1 Proxy Server
- 18. Over 100 URL categories
- 19. Cloud based URL lookupsContent Filtering Life CycleCore filter modules Redirect module
- 20. Custom URL module
- 24. MIME type module
- 26. SafeSearch moduleDynamic on-demand filtering
- 27. Granular policiesTime based controlDetailed reportingEase of managementKey features Per user group
- 28. Per computer group (IP/MAC/Host)
- 29. Unlimited number of policies
- 30. Over 130 categories of URL
- 31. Report builder
- 32. Over 36 template reports
- 34. Schedule reports
- 35. Manage unblock requests
- 36. Notify users after action
- 39. Schedule unlimited policies
- 40. 7 day 24 x7 period
- 41. Daily Time QuotasDeployment optionsSideways Mode Browser proxy settings configured by group policy
- 42. CensorNet is not in the data flow path
- 43. Single sign on authentication is possible
- 44. Most common deployment type1. Sideways2. InlineInline Mode Transparent interception ŌĆō proxy settings not required
- 45. CensorNet directly in the data path
- 46. User auth not possible but user identification can be achieved with tools3. Mixed
- 47. IntegrationUser AuthenticationComputer managementAdditional toolsSingle sign-on Transparent NTLM
- 48. Win 2000-2008
- 50. Win 2008r2Identification MAC address (single subnet)
- 51. IP address (multiple subnet)
- 52. Hostname (reverse DNS)SynchronisationActive Directory synch toolRemote users Remote Worker toolBasic auth Kerberos
- 53. Windows NT/SAMBA
- 55. LDAP
- 57. NoneUser identificationADAgent for identifying users in inline mode
- 58. CNLoginAgent for identifying users in inline mode or alternative to SSOSynchronisationProbe network for new devices wizard
- 59. Import from CSVManagement Web based control panel
- 60. System alerts by e-mail
- 62. RSS news feed
- 63. Access to Live Support desk
- 64. Online help / Knowledge Base
- 67. Automatic Active Directory synchronisation
- 68. Automatic computer detection tool
- 69. Bulk ImportThank youAny questions?