Chameleon PCI Presentation
- 1. Facing the Challenges of PCI Compliance Presented by:
- 2. The Need
- 3. What is credit card compromise? To gain access to: Card Numbers Expiration Dates CVV2/CVC2/CID Track Data An unauthorized individual taking advantage of a flaw in a system that processes, transmits or stores cardholder data.
- 4. Theft of Payment Card Data Is Thriving The Perpetrators Script Kiddies International Crime Syndicates Malicious Third Parties Employees The Tools Scanners * Port Vulnerability Web Application * Available online The Gaps Weak Configurations Operating System Flaws Programming Errors Lack of Staff training Flawed Policies Negligence Poor Change Control Application-Induced Backdoors Nearby Systems/Networks Utilize To Find
- 5. And It’s Easier Than Many Think Breach investigations have located compromised cardholder data on popular public facing web sites:
- 6. Selling Cardholder Information is Lucrative CREDIT CARDS NUMBERS ARE SOLD ON THE BLACK- MARKET FOR PROFIT Once compromised…
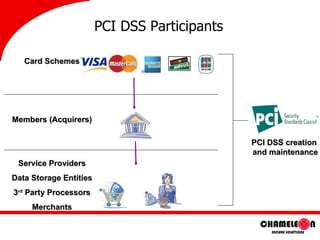
- 7. PCI DSS Participants Card Schemes Members (Acquirers) Service Providers Data Storage Entities 3 rd Party Processors Merchants PCI DSS creation and maintenance
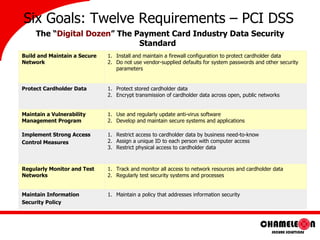
- 8. Six Goals: Twelve Requirements – PCI DSS The “ Digital Dozen ” The Payment Card Industry Data Security Standard Build and Maintain a Secure Network Install and maintain a firewall configuration to protect cardholder data Do not use vendor-supplied defaults for system passwords and other security parameters Protect Cardholder Data Protect stored cardholder data Encrypt transmission of cardholder data across open, public networks Maintain a Vulnerability Management Program Use and regularly update anti-virus software Develop and maintain secure systems and applications Implement Strong Access Control Measures Restrict access to cardholder data by business need-to-know Assign a unique ID to each person with computer access Restrict physical access to cardholder data Regularly Monitor and Test Networks Track and monitor all access to network resources and cardholder data Regularly test security systems and processes Maintain Information Security Policy Maintain a policy that addresses information security
- 9. Non-Compliance: Risks, Fines, Fees, Costs, Loss Non-compliant, compromised business could expect the following: Damage to their brand/reputation Investigation costs Remediation costs Fines and fees - Non-compliance (each brand issues separate fines) -Re-issuance -Fraud loss Ongoing compliance audits Victim notification costs Financial loss Data loss Charge-backs for fraudulent transactions Operations disruption Sensitive info disclosure Denial of service to customers Individual executives held liable Possibility of business closure
- 10. PCI Compliance: Sound Business Practice Fundamental Best Security Practices Avoid fraud Maps that supports other compliance regimes Upholds Brand Name Adds value to name Increases consumer confidence Improves reputation Clarifies Where Data Is Stored Helps to understand own system better
- 11.  PCI DSS Compliance Can Protect Against Fines Members receive “ Safe Harbor ” For Compromised Merchants Found To Be PCI-Compliant At Time Of Breach